| File name: | wow.exe |
| Full analysis: | https://app.any.run/tasks/c27e83ca-b78d-46b4-8a7c-2e193dd21d09 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | December 17, 2024, 20:21:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | B2C17E4AAA1AB07E2BE2C6E08120C7FE |
| SHA1: | 67EB0FBAFB9D75D7E95DC8429C09A99E73ED5C74 |
| SHA256: | D6427E58DFA1A8BFB69F510D4C3806C36CBB7FCFAC82984CAFCD2FF539631F0D |
| SSDEEP: | 196608:+7C92OaZ2NtTeRi/BqyndOugBe0vGEmop:lnNtKRi5qEOfCw |
MALICIOUS
METERPRETER has been found (auto)
- wow.exe (PID: 6808)
METERPRETER has been detected (SURICATA)
- wow.exe (PID: 6808)
METASPLOIT has been detected (SURICATA)
- wow.exe (PID: 6808)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 4052)
Changes powershell execution policy (Bypass)
- wow.exe (PID: 6808)
Bypass execution policy to execute commands
- powershell.exe (PID: 4052)
Changes the autorun value in the registry
- reg.exe (PID: 4816)
XMRig has been detected
- ksoftriqd.exe (PID: 6264)
Connects to the CnC server
- ksoftriqd.exe (PID: 6264)
MINER has been detected (SURICATA)
- ksoftriqd.exe (PID: 6264)
Uses Task Scheduler to run other applications
- powershell.exe (PID: 4052)
SUSPICIOUS
The process drops C-runtime libraries
- wow.exe (PID: 6388)
Process drops legitimate windows executable
- wow.exe (PID: 6388)
Executable content was dropped or overwritten
- wow.exe (PID: 6388)
- wow.exe (PID: 6808)
- powershell.exe (PID: 4052)
- 18arge9.exe (PID: 1016)
Reads the date of Windows installation
- wow.exe (PID: 6808)
Process drops python dynamic module
- wow.exe (PID: 6388)
Loads Python modules
- wow.exe (PID: 6808)
Process requests binary or script from the Internet
- wow.exe (PID: 6808)
- powershell.exe (PID: 4052)
Reads security settings of Internet Explorer
- wow.exe (PID: 6808)
- GameBar.exe (PID: 6520)
Potential Corporate Privacy Violation
- wow.exe (PID: 6808)
- ksoftriqd.exe (PID: 6264)
- powershell.exe (PID: 4052)
Connects to unusual port
- wow.exe (PID: 6808)
- sys.exe (PID: 6896)
- sup.exe (PID: 6880)
Application launched itself
- wow.exe (PID: 6388)
The process executes Powershell scripts
- wow.exe (PID: 6808)
Connects to the server without a host name
- powershell.exe (PID: 4052)
- wow.exe (PID: 6808)
Starts POWERSHELL.EXE for commands execution
- wow.exe (PID: 6808)
Uses NETSH.EXE to change the status of the firewall
- powershell.exe (PID: 4052)
Using 'findstr.exe' to search for text patterns in files and output
- powershell.exe (PID: 4052)
- cmd.exe (PID: 6680)
Drops a system driver (possible attempt to evade defenses)
- 18arge9.exe (PID: 1016)
Starts SC.EXE for service management
- cmd.exe (PID: 6820)
- cmd.exe (PID: 6800)
- cmd.exe (PID: 6688)
- cmd.exe (PID: 6860)
Uses REG/REGEDIT.EXE to modify registry
- powershell.exe (PID: 4052)
Starts CMD.EXE for commands execution
- 18arge9.exe (PID: 1016)
The executable file from the user directory is run by the CMD process
- ksoftriqd.exe (PID: 6264)
The process executes via Task Scheduler
- 18arge9.exe (PID: 4308)
- 18arge9.exe (PID: 8188)
INFO
The sample compiled with english language support
- wow.exe (PID: 6388)
Reads the computer name
- wow.exe (PID: 6388)
- GameBar.exe (PID: 6520)
- wow.exe (PID: 6808)
- sys.exe (PID: 6896)
- sup.exe (PID: 6880)
- 18arge9.exe (PID: 1016)
- ksoftriqd.exe (PID: 6264)
Checks supported languages
- wow.exe (PID: 6388)
- sup.exe (PID: 6880)
- sys.exe (PID: 6896)
- ph.exe (PID: 6948)
- wow.exe (PID: 6808)
- GameBar.exe (PID: 6520)
- 18arge9.exe (PID: 1016)
- ksoftriqd.exe (PID: 6264)
Create files in a temporary directory
- wow.exe (PID: 6388)
- 18arge9.exe (PID: 1016)
Checks proxy server information
- wow.exe (PID: 6808)
- powershell.exe (PID: 4052)
The process uses the downloaded file
- wow.exe (PID: 6808)
- powershell.exe (PID: 4052)
Process checks computer location settings
- wow.exe (PID: 6808)
PyInstaller has been detected (YARA)
- wow.exe (PID: 6808)
- wow.exe (PID: 6388)
Reads Microsoft Office registry keys
- wow.exe (PID: 6808)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4052)
Disables trace logs
- powershell.exe (PID: 4052)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4052)
The executable file from the user directory is run by the Powershell process
- 18arge9.exe (PID: 1016)
Creates files or folders in the user directory
- 18arge9.exe (PID: 1016)
The sample compiled with japanese language support
- 18arge9.exe (PID: 1016)
Drops encrypted VBS script (Microsoft Script Encoder)
- 18arge9.exe (PID: 1016)
Drops encrypted JS script (Microsoft Script Encoder)
- 18arge9.exe (PID: 1016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:12:17 20:15:46+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 176640 |
| InitializedDataSize: | 152576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
146
Monitored processes
36
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1016 | "C:\Users\admin\AppData\Roaming\18arge9.exe" | C:\Users\admin\AppData\Roaming\18arge9.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1140 | "C:\Windows\System32\GameBarPresenceWriter.exe" -ServerName:Windows.Gaming.GameBar.Internal.PresenceWriterServer | C:\Windows\System32\GameBarPresenceWriter.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Gamebar Presence Writer Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | findstr TCP | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | sc delete npf | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2736 | cmd.exe /c start C:\Users\admin\AppData\Local\Temp\tilhai\ksoftriqd.exe | C:\Windows\System32\cmd.exe | — | 18arge9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3224 | "C:\WINDOWS\system32\schtasks.exe" /create /F /sc minute /mo 1 /tn BrowserUpdate /tr C:\Users\admin\AppData\Roaming\18arge9.exe | C:\Windows\System32\schtasks.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | "C:\WINDOWS\system32\findstr.exe" TCP | C:\Windows\System32\findstr.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4024 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 18arge9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4052 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Downloads\haus\ldr.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wow.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 076
Read events
14 061
Write events
15
Delete events
0
Modification events
| (PID) Process: | (6520) GameBar.exe | Key: | \REGISTRY\A\{74ef0290-bcfc-7af0-dfff-2c1d22c02d03}\LocalState |
| Operation: | write | Name: | InstalledVersionMajor |
Value: 02002F76BB5DC150DB01 | |||
| (PID) Process: | (6520) GameBar.exe | Key: | \REGISTRY\A\{74ef0290-bcfc-7af0-dfff-2c1d22c02d03}\LocalState |
| Operation: | write | Name: | InstalledVersionMinor |
Value: 22002F76BB5DC150DB01 | |||
| (PID) Process: | (6520) GameBar.exe | Key: | \REGISTRY\A\{74ef0290-bcfc-7af0-dfff-2c1d22c02d03}\LocalState |
| Operation: | write | Name: | InstalledVersionBuild |
Value: 616D2F76BB5DC150DB01 | |||
| (PID) Process: | (6520) GameBar.exe | Key: | \REGISTRY\A\{74ef0290-bcfc-7af0-dfff-2c1d22c02d03}\LocalState |
| Operation: | write | Name: | InstalledVersionRevision |
Value: 00002F76BB5DC150DB01 | |||
| (PID) Process: | (6520) GameBar.exe | Key: | \REGISTRY\A\{74ef0290-bcfc-7af0-dfff-2c1d22c02d03}\LocalState |
| Operation: | write | Name: | PreviousAppTerminationFromSuspended |
Value: 002F76BB5DC150DB01 | |||
| (PID) Process: | (6520) GameBar.exe | Key: | \REGISTRY\A\{74ef0290-bcfc-7af0-dfff-2c1d22c02d03}\LocalState |
| Operation: | write | Name: | CurrentDisplayMonitor |
Value: 670061006D00650000002640C05DC150DB01 | |||
| (PID) Process: | (6520) GameBar.exe | Key: | \REGISTRY\A\{74ef0290-bcfc-7af0-dfff-2c1d22c02d03}\LocalState |
| Operation: | write | Name: | StartupTipIndex |
Value: 01000000000000002F57C75DC150DB01 | |||
| (PID) Process: | (6520) GameBar.exe | Key: | \REGISTRY\A\{74ef0290-bcfc-7af0-dfff-2c1d22c02d03}\LocalState |
| Operation: | write | Name: | InstalledVersionMajor |
Value: 0200432D9F62C150DB01 | |||
| (PID) Process: | (6520) GameBar.exe | Key: | \REGISTRY\A\{74ef0290-bcfc-7af0-dfff-2c1d22c02d03}\LocalState |
| Operation: | write | Name: | InstalledVersionMinor |
Value: 2200432D9F62C150DB01 | |||
| (PID) Process: | (6520) GameBar.exe | Key: | \REGISTRY\A\{74ef0290-bcfc-7af0-dfff-2c1d22c02d03}\LocalState |
| Operation: | write | Name: | InstalledVersionBuild |
Value: 616D432D9F62C150DB01 | |||
Executable files
42
Suspicious files
7
Text files
36
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6388 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI63882\_multiprocessing.pyd | executable | |
MD5:1386DBC6DCC5E0BE6FEF05722AE572EC | SHA256:0AE3BF383FF998886F97576C55D6BF0A076C24395CF6FCD2265316E9A6E8C007 | |||
| 6388 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI63882\_asyncio.pyd | executable | |
MD5:2859C39887921DAD2FF41FEDA44FE174 | SHA256:AEBC378DB08617EA81A0A3A3BC044BCC7E6303E314630392DD51BAB12F879BD9 | |||
| 6388 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI63882\VCRUNTIME140.dll | executable | |
MD5:F12681A472B9DD04A812E16096514974 | SHA256:D66C3B47091CEB3F8D3CC165A43D285AE919211A0C0FCB74491EE574D8D464F8 | |||
| 6388 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI63882\_ctypes.pyd | executable | |
MD5:6A9CA97C039D9BBB7ABF40B53C851198 | SHA256:E662D2B35BB48C5F3432BDE79C0D20313238AF800968BA0FAA6EA7E7E5EF4535 | |||
| 6388 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI63882\_queue.pyd | executable | |
MD5:FF8300999335C939FCCE94F2E7F039C0 | SHA256:2F71046891BA279B00B70EB031FE90B379DBE84559CF49CE5D1297EA6BF47A78 | |||
| 6388 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI63882\_lzma.pyd | executable | |
MD5:337B0E65A856568778E25660F77BC80A | SHA256:613DE58E4A9A80EFF8F8BC45C350A6EAEBF89F85FFD2D7E3B0B266BF0888A60A | |||
| 6388 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI63882\_brotli.cp311-win_amd64.pyd | executable | |
MD5:D9FC15CAF72E5D7F9A09B675E309F71D | SHA256:1FCD75B03673904D9471EC03C0EF26978D25135A2026020E679174BDEF976DCF | |||
| 6388 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI63882\VCRUNTIME140_1.dll | executable | |
MD5:75E78E4BF561031D39F86143753400FF | SHA256:1758085A61527B427C4380F0C976D29A8BEE889F2AC480C356A3F166433BF70E | |||
| 6388 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI63882\_overlapped.pyd | executable | |
MD5:01AD7CA8BC27F92355FD2895FC474157 | SHA256:A083E83F609ED7A2FC18A95D44D8F91C9DC74842F33E19E91988E84DB94C3B5B | |||
| 6388 | wow.exe | C:\Users\admin\AppData\Local\Temp\_MEI63882\_ssl.pyd | executable | |
MD5:069BCCC9F31F57616E88C92650589BDD | SHA256:CB42E8598E3FA53EEEBF63F2AF1730B9EC64614BDA276AB2CD1F1C196B3D7E32 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
96
TCP/UDP connections
38 497
DNS requests
11
Threats
125
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.24:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6808 | wow.exe | GET | — | 31.41.244.11:80 | http://31.41.244.11/files/6989783370/AwT7h8g.exe | unknown | — | — | unknown |
6808 | wow.exe | GET | — | 31.41.244.11:80 | http://31.41.244.11/files/6989783370/8oMoEDZ.exe | unknown | — | — | unknown |
6808 | wow.exe | GET | — | 193.143.1.180:80 | http://193.143.1.180/download/av.exe | unknown | — | — | unknown |
6808 | wow.exe | GET | — | 193.143.1.180:80 | http://193.143.1.180/download/GOLD.exe | unknown | — | — | unknown |
6808 | wow.exe | GET | — | 104.168.101.23:1234 | http://104.168.101.23:1234/windows/net.exe | unknown | — | — | unknown |
6808 | wow.exe | GET | — | 93.176.52.107:80 | http://93.176.52.107/Quas_Autre_ncrypt.exe | unknown | — | — | malicious |
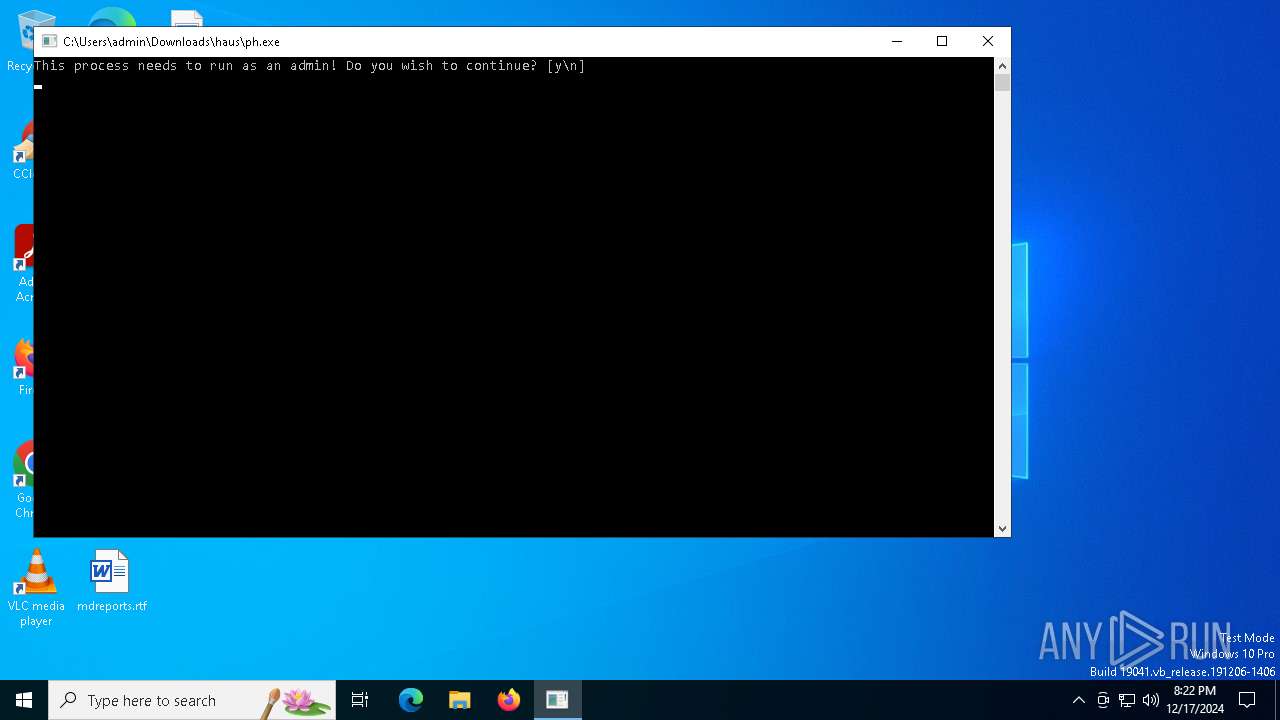
6808 | wow.exe | GET | 200 | 104.168.101.23:1234 | http://104.168.101.23:1234/windows/ph.exe | unknown | — | — | unknown |
6808 | wow.exe | GET | — | 92.127.156.174:8880 | http://92.127.156.174:8880/master.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.24.77.24:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6808 | wow.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
6808 | wow.exe | 31.41.244.11:80 | — | Red Bytes LLC | RU | unknown |
6808 | wow.exe | 193.143.1.180:80 | — | LLC Baxet | RU | unknown |
6808 | wow.exe | 192.3.179.166:443 | — | AS-COLOCROSSING | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
e4l4.com |
| malicious |
hardcore-cartwright.194-26-192-76.plesk.page |
| unknown |
lsks.volamngayxua.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6808 | wow.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
6808 | wow.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 2 |
6808 | wow.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 14 |
6808 | wow.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6808 | wow.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6808 | wow.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6808 | wow.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
6808 | wow.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6808 | wow.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
5 ETPRO signatures available at the full report