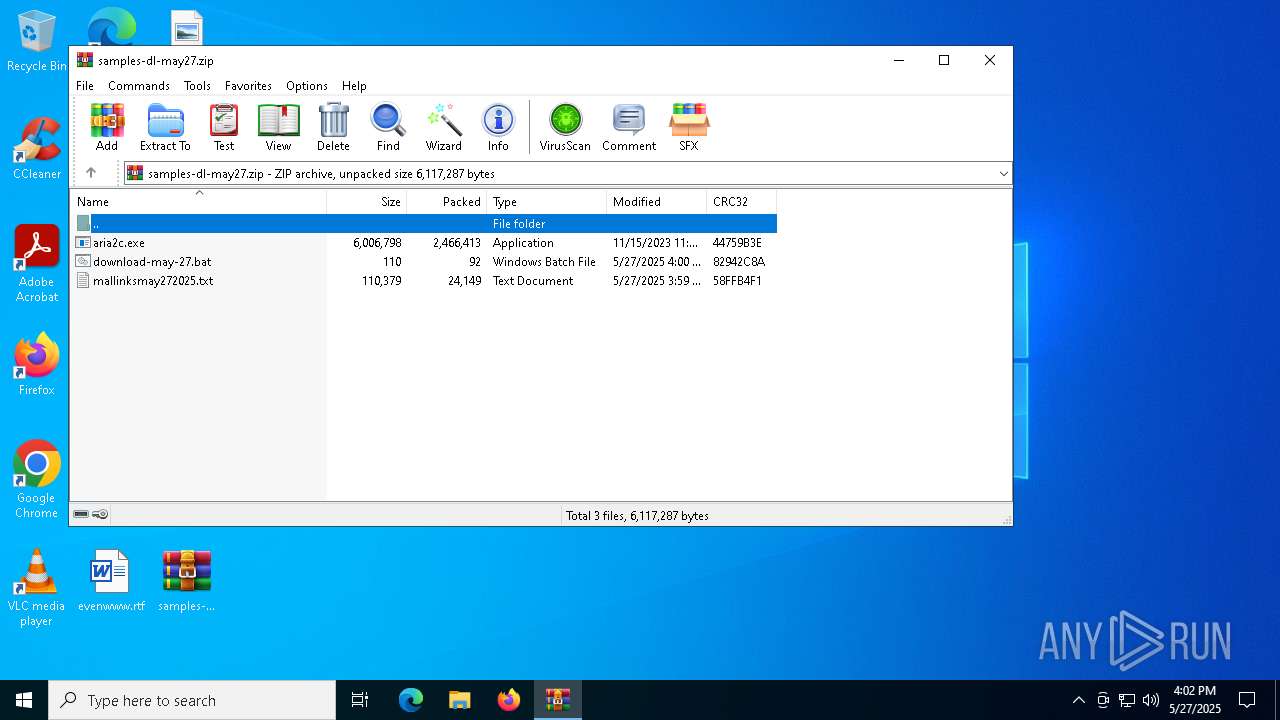
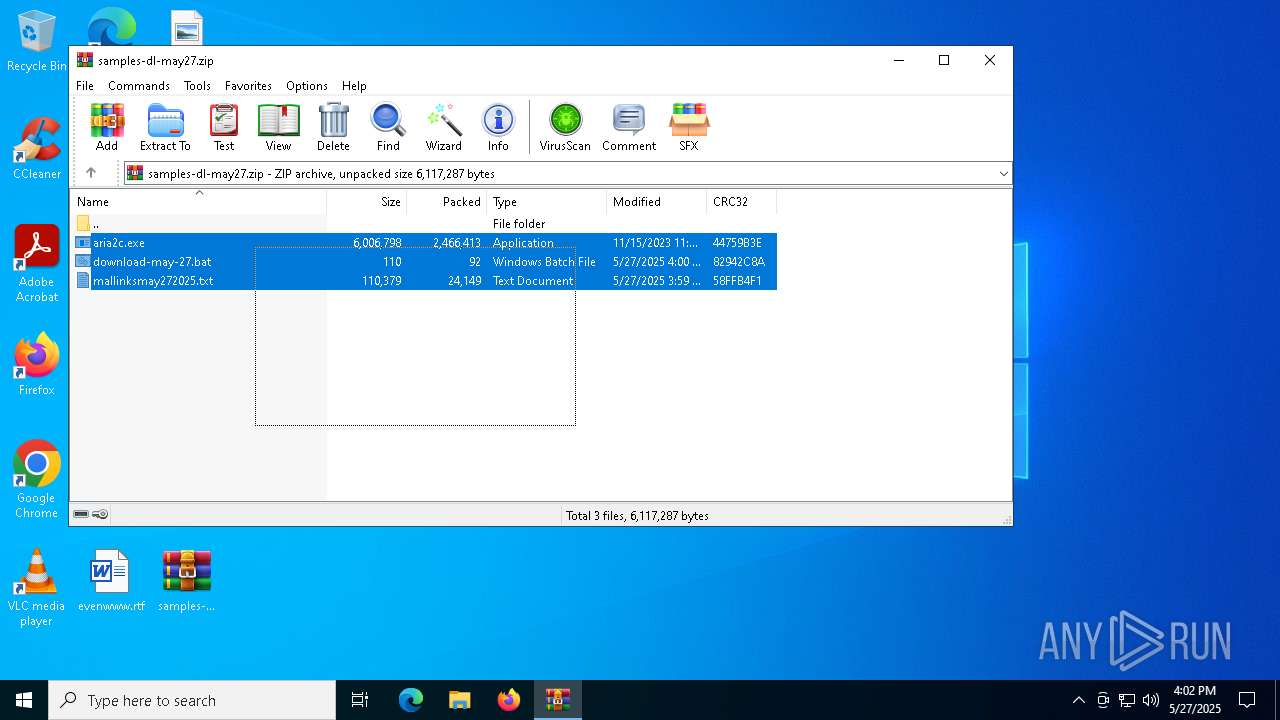
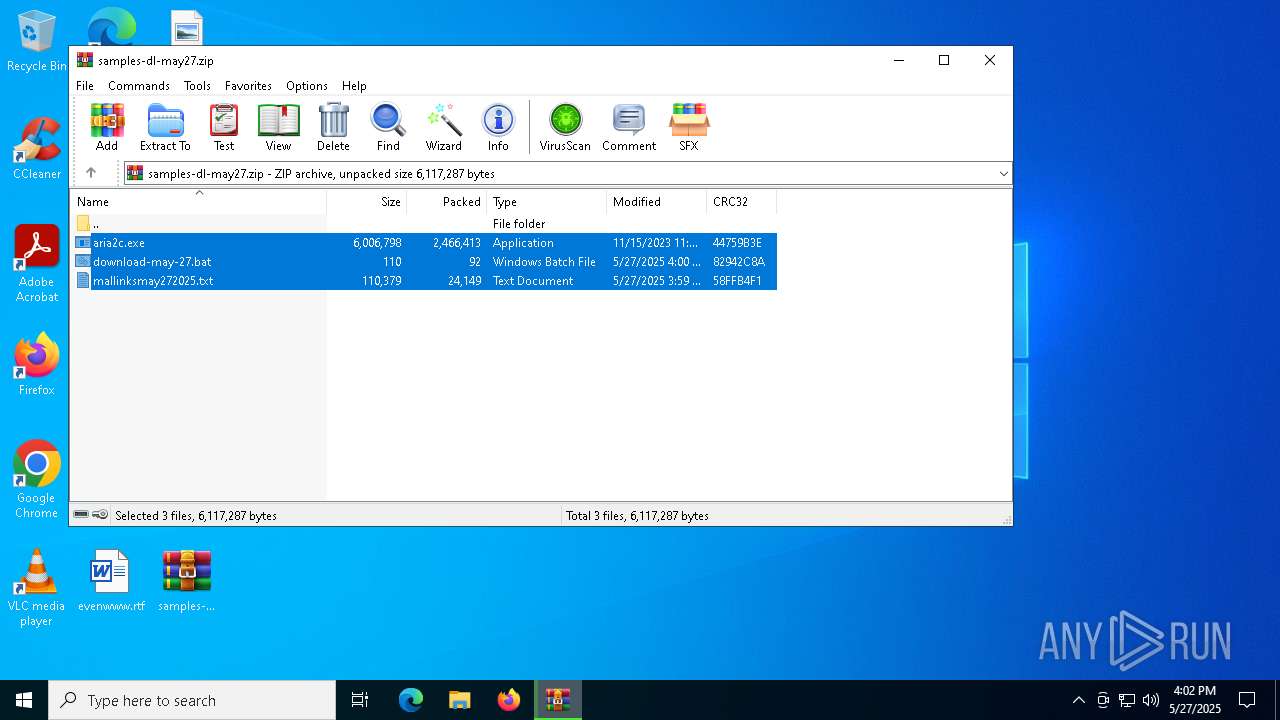
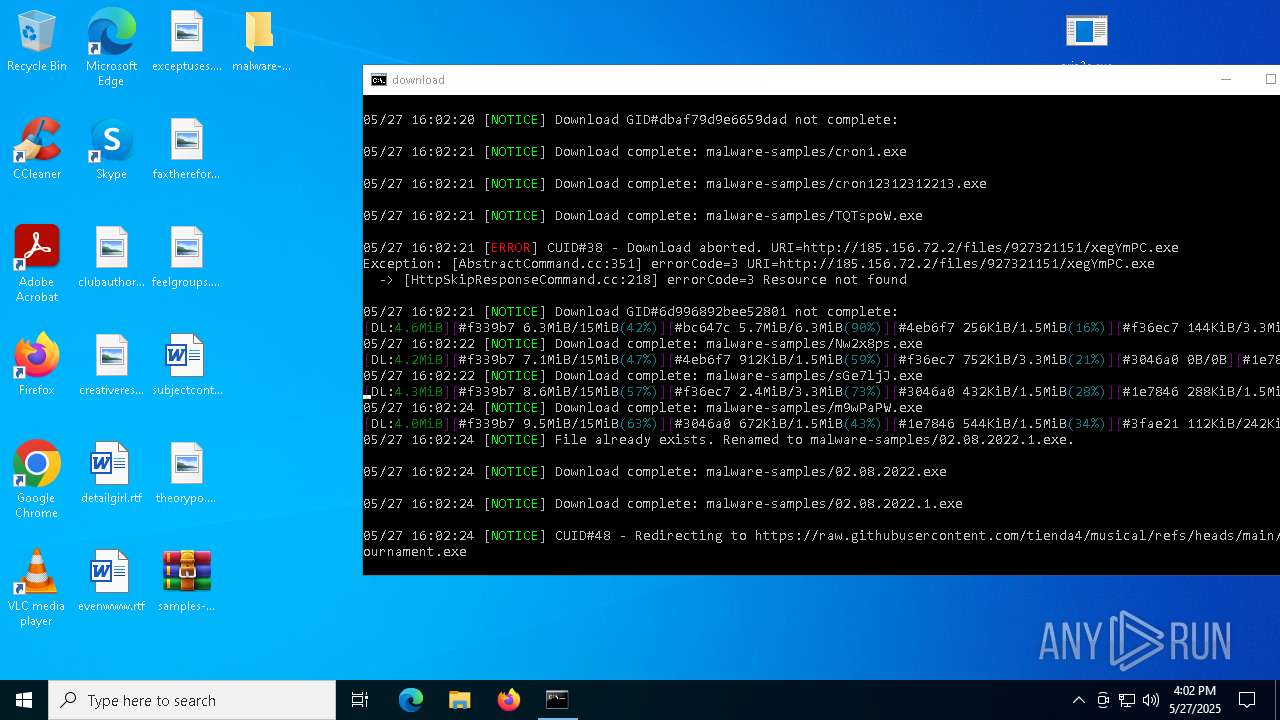
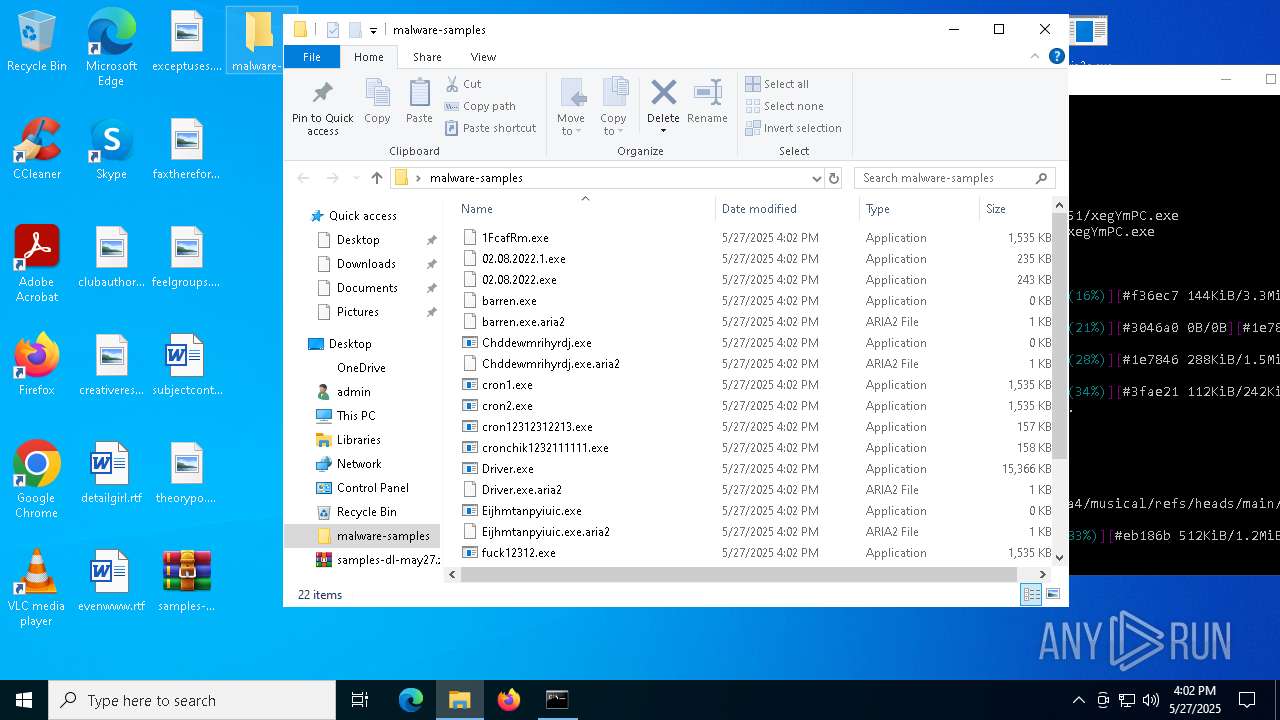
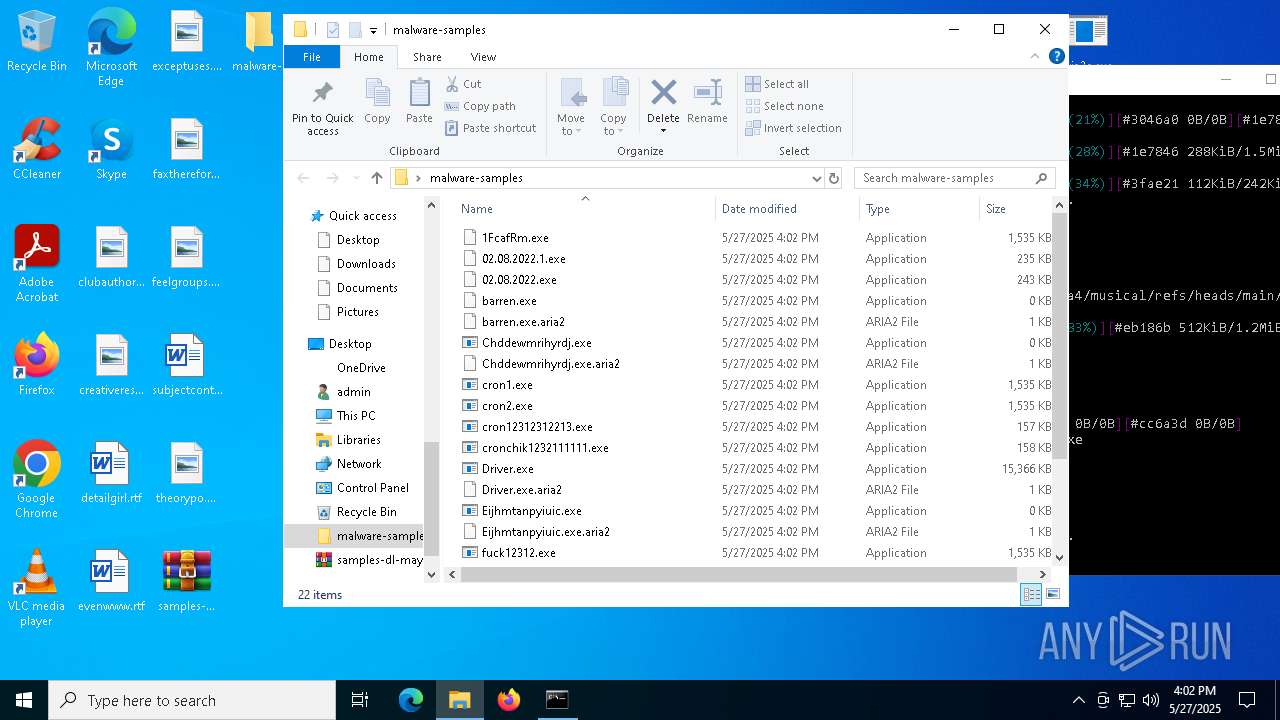
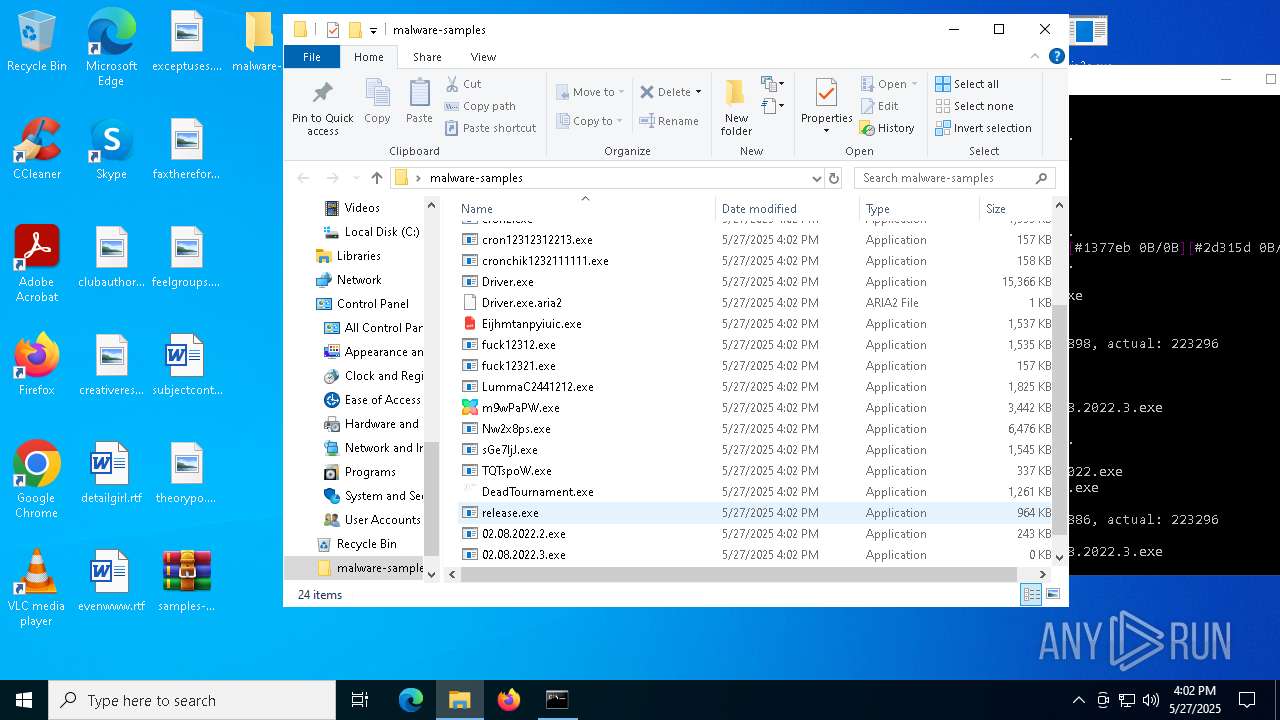
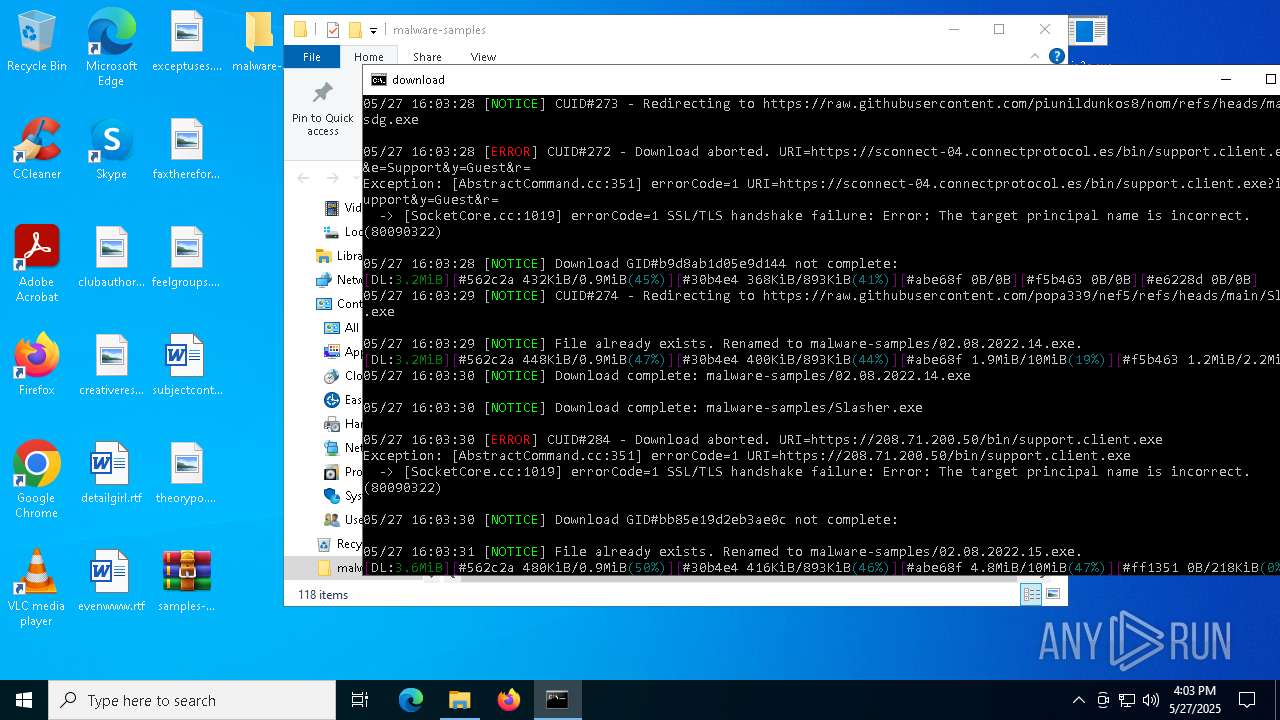
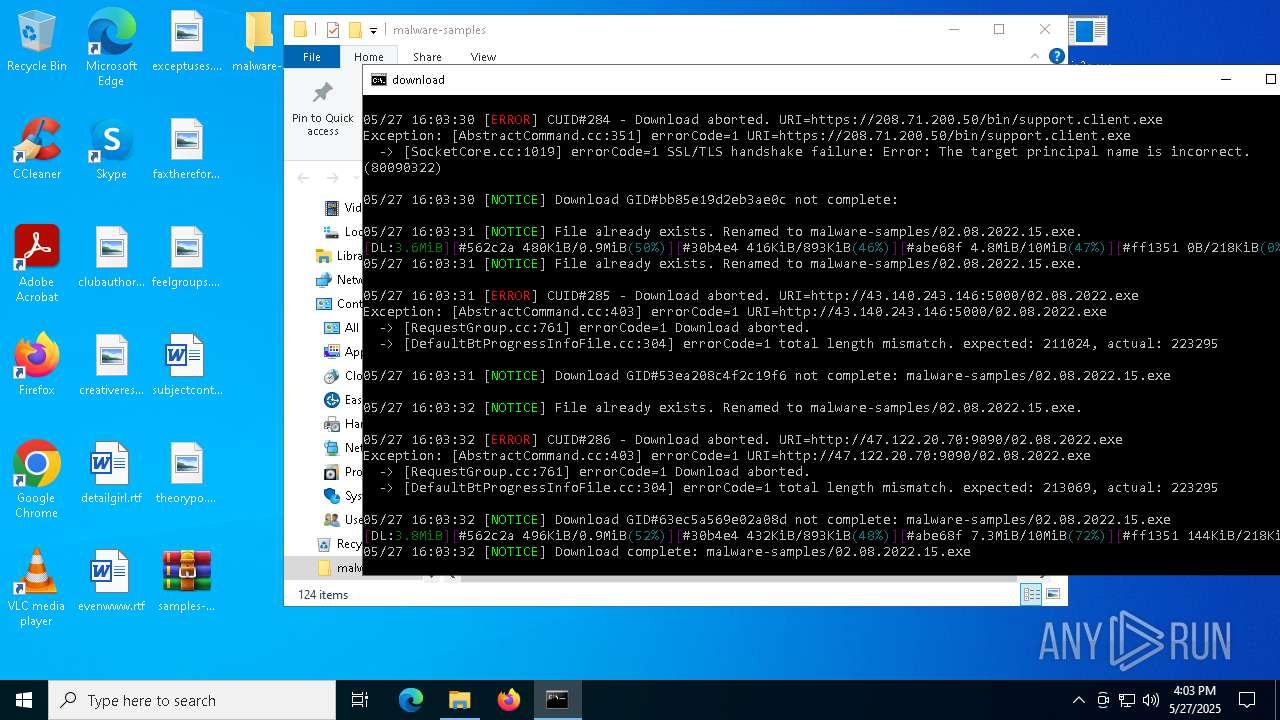
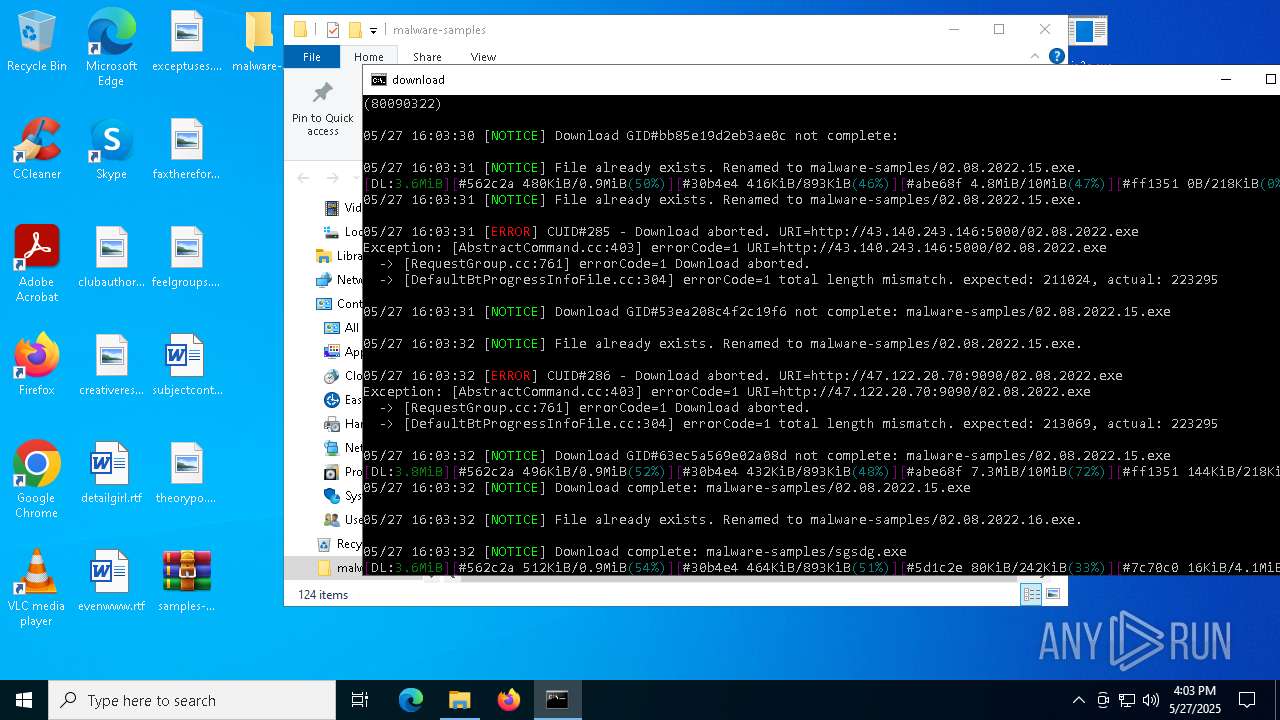
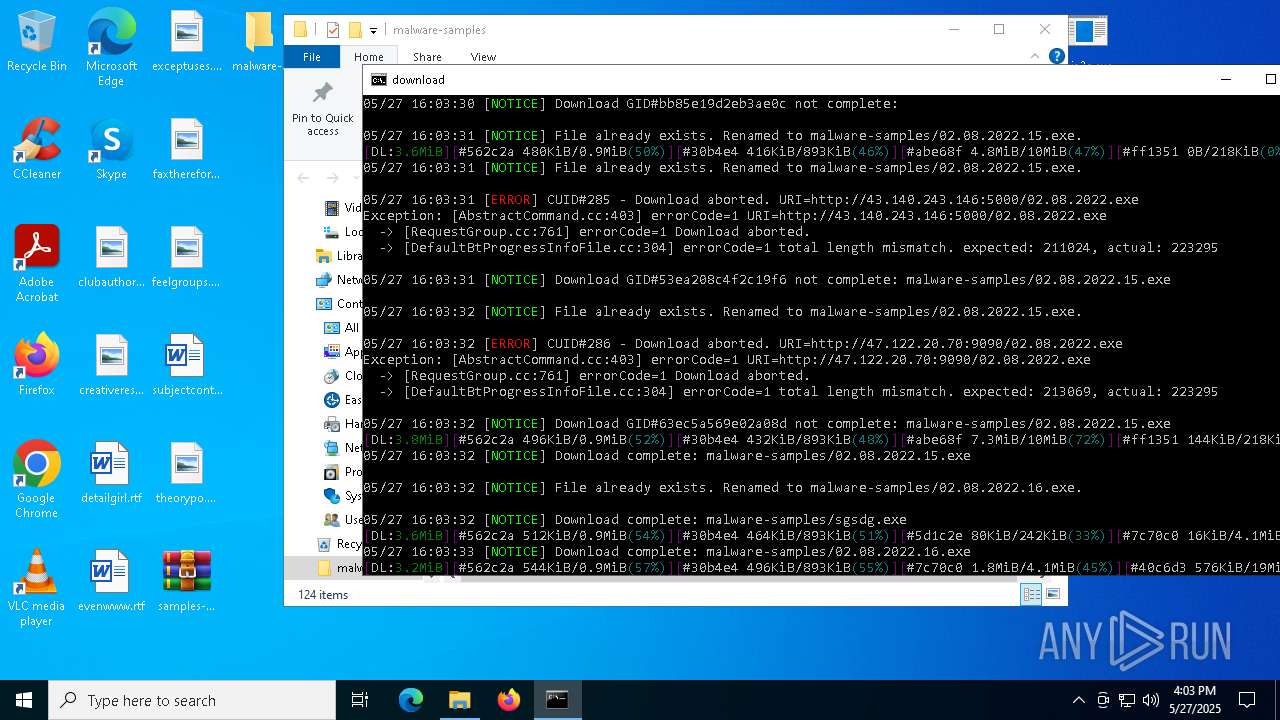
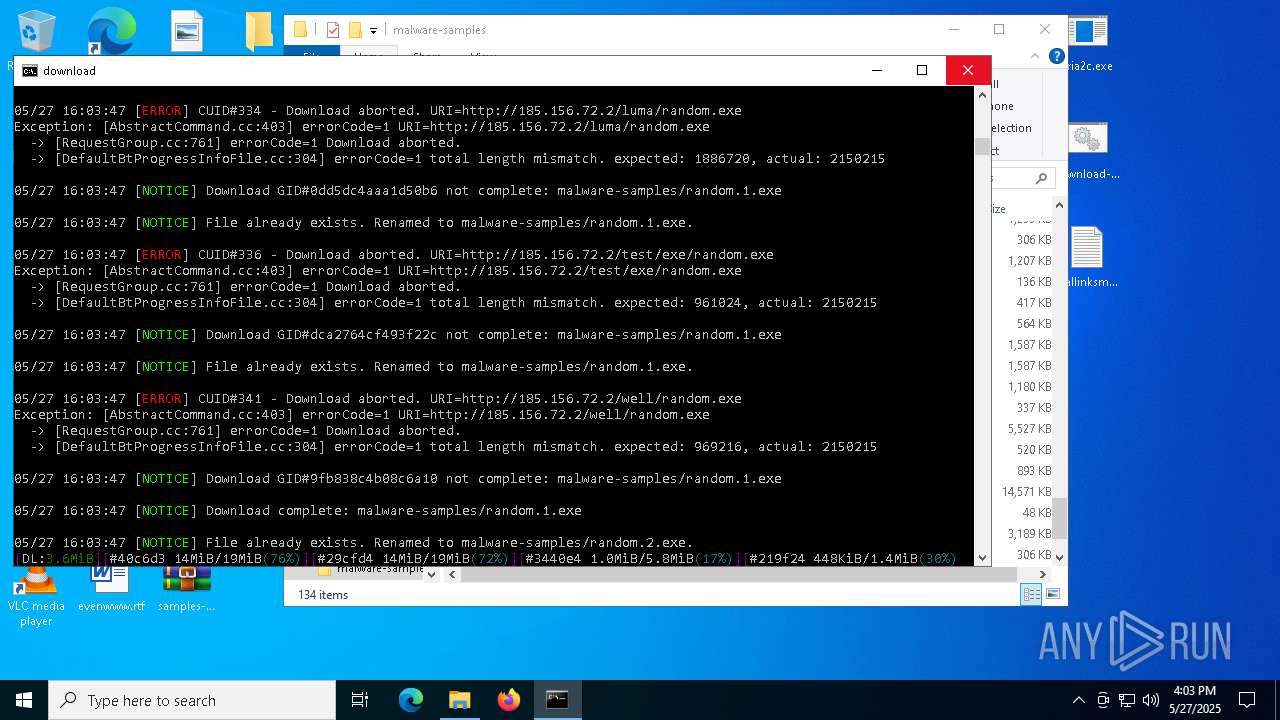
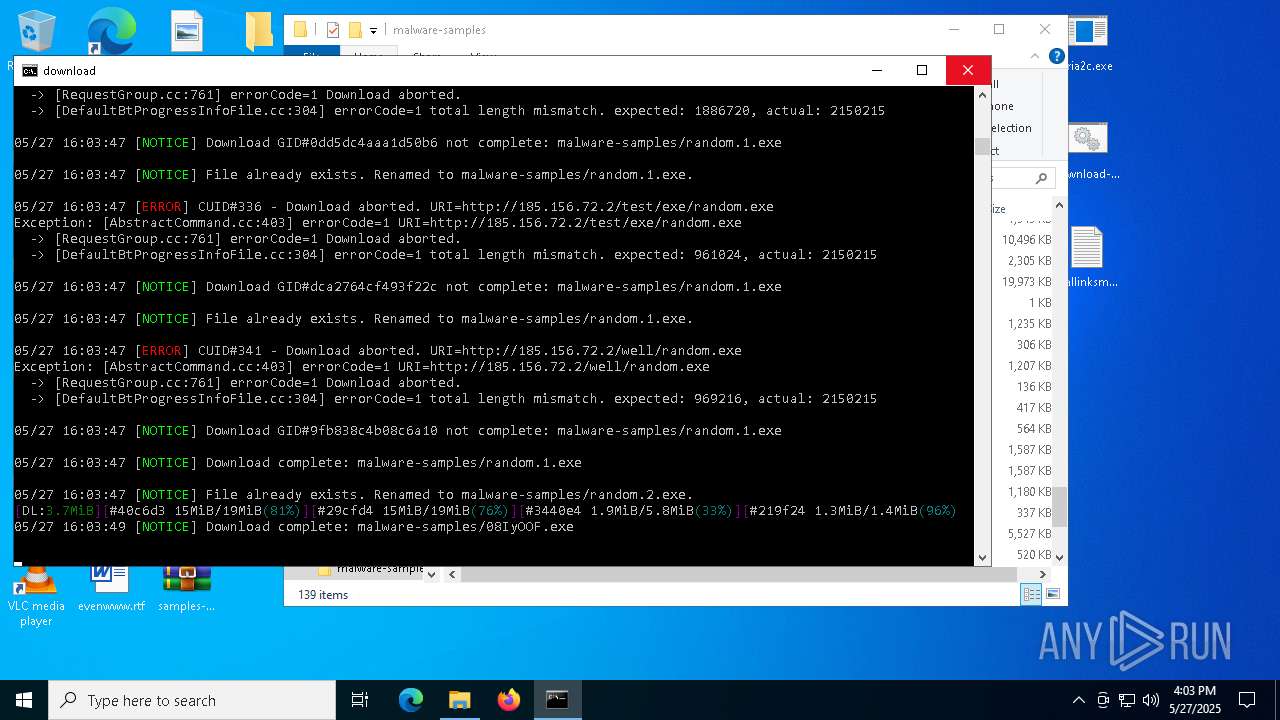
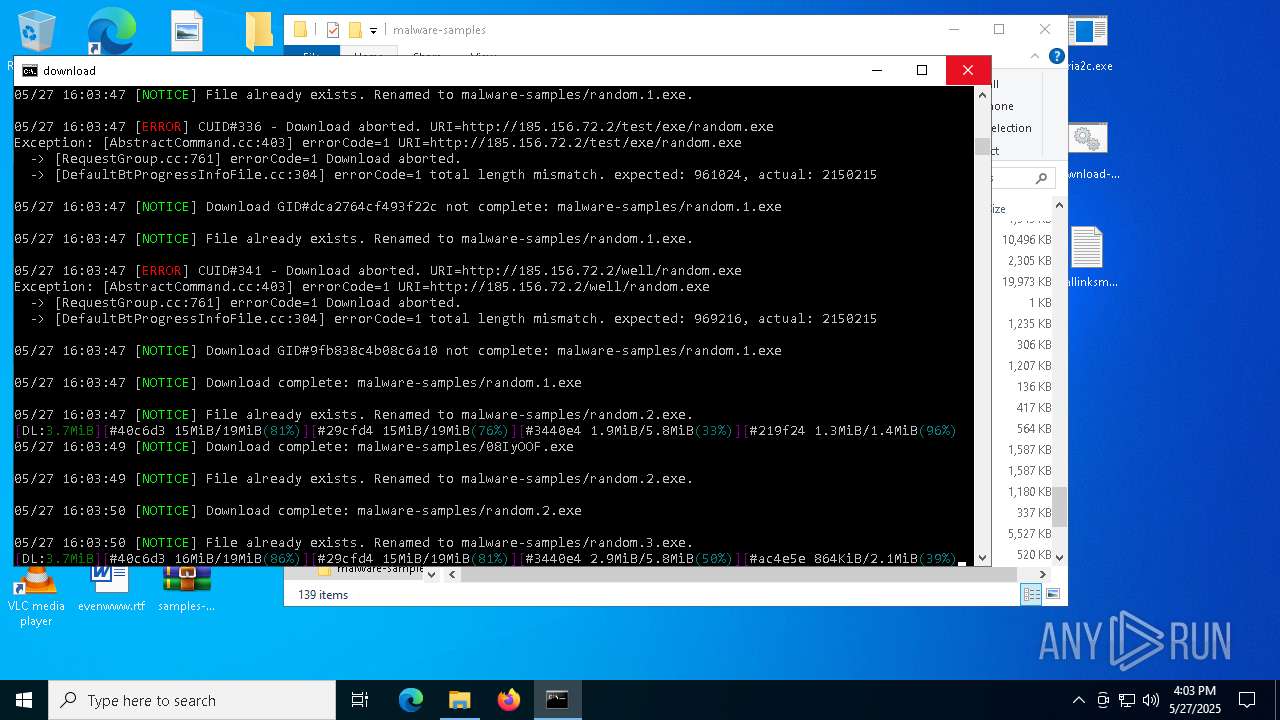
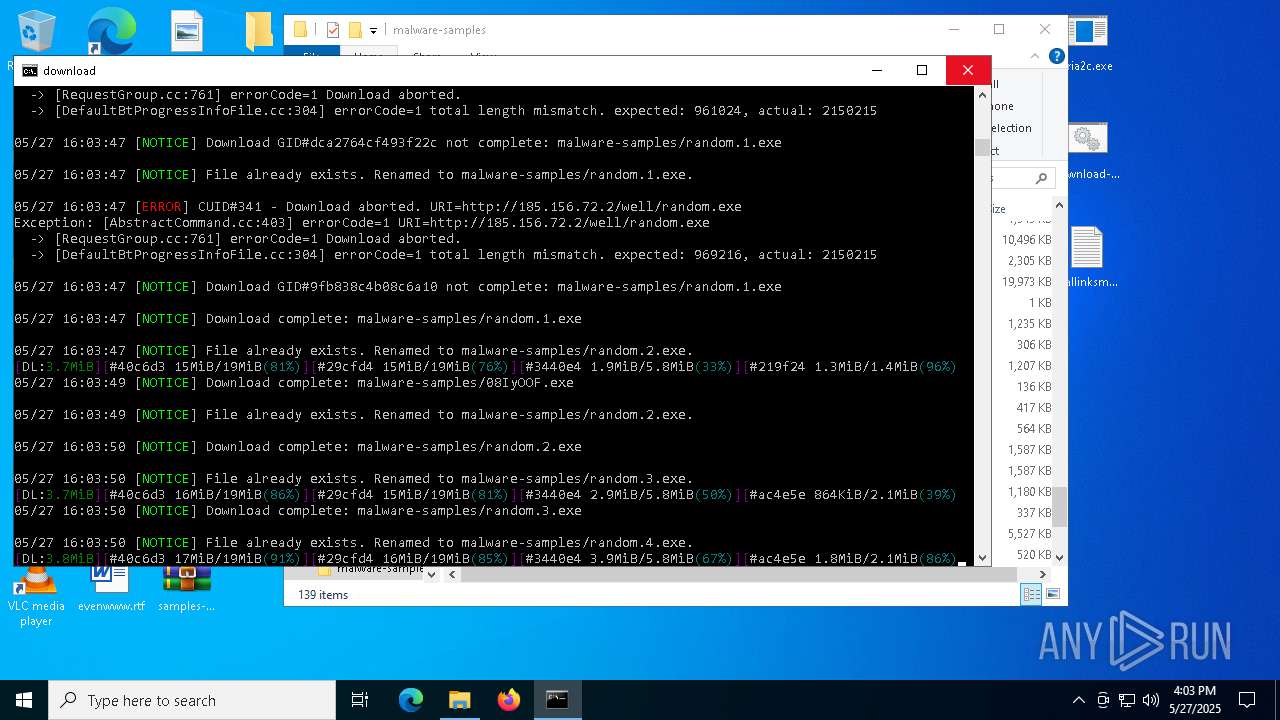
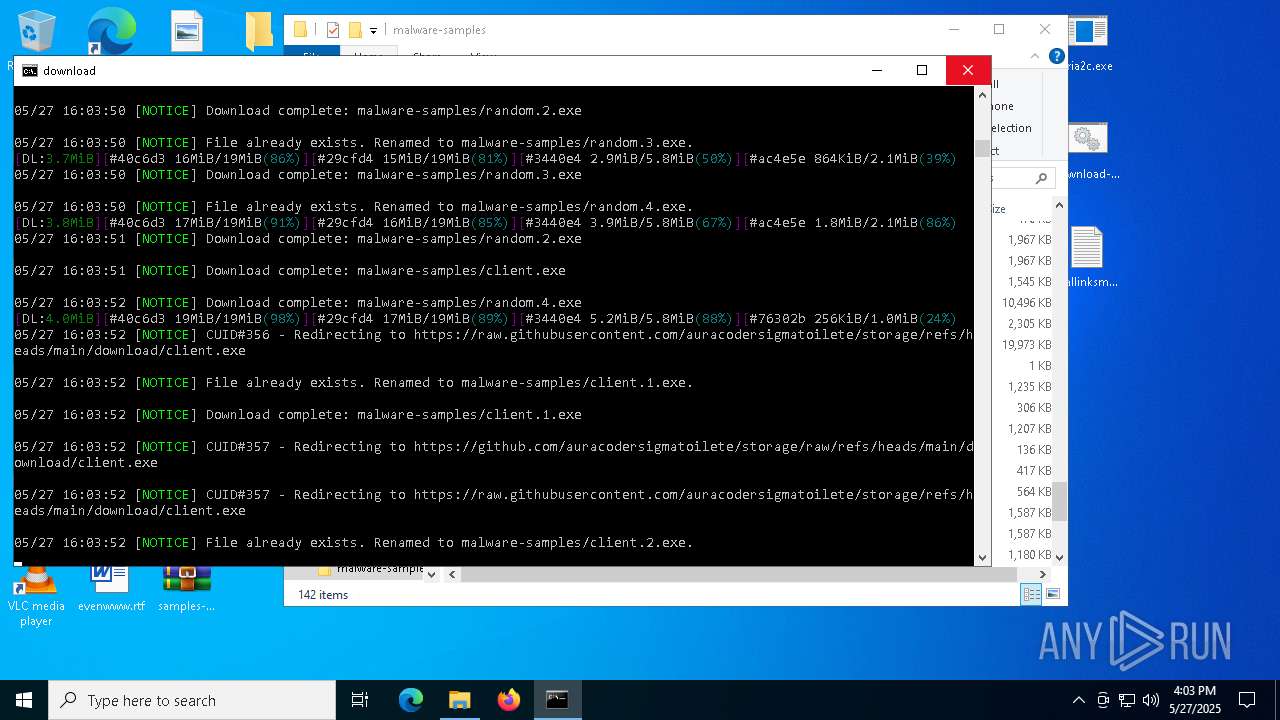
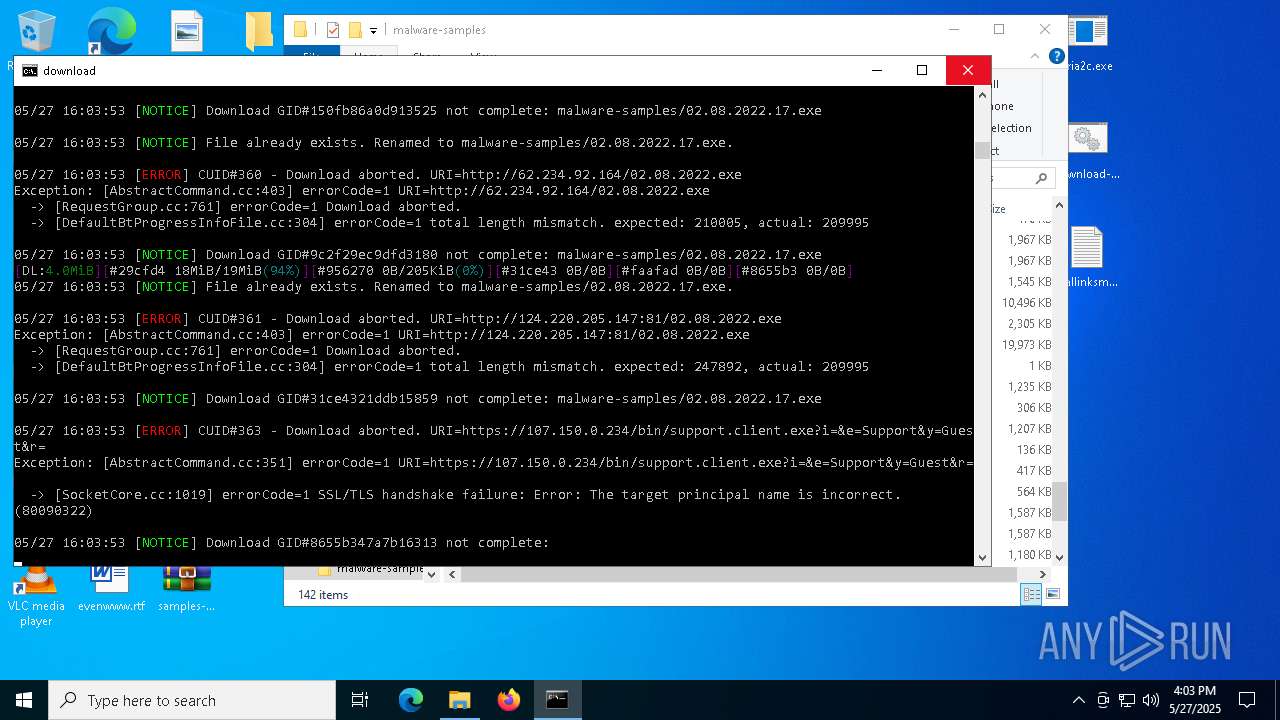
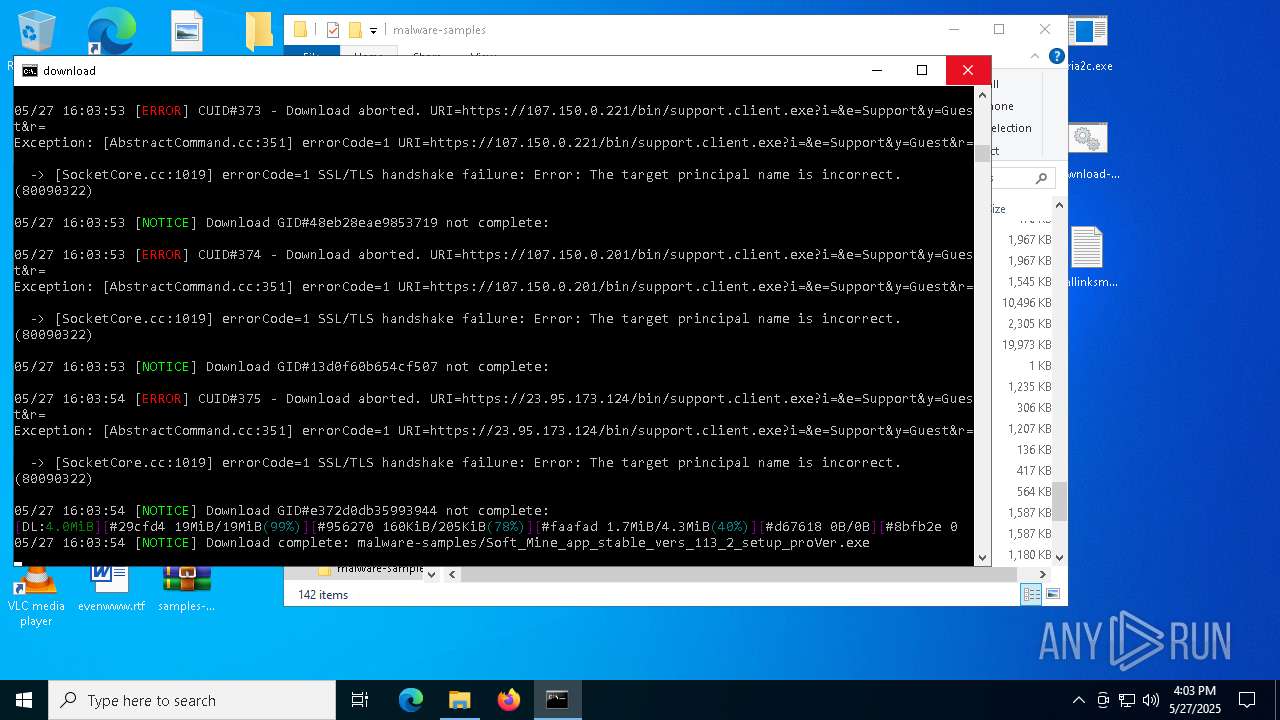
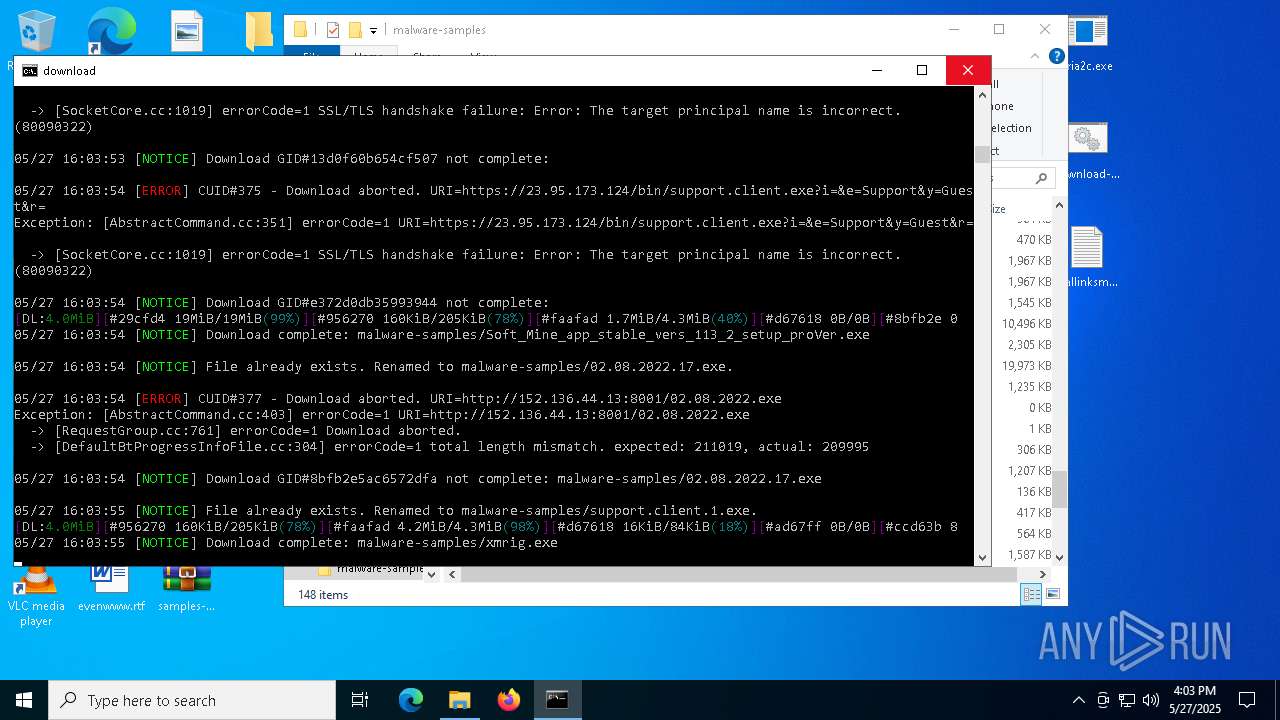
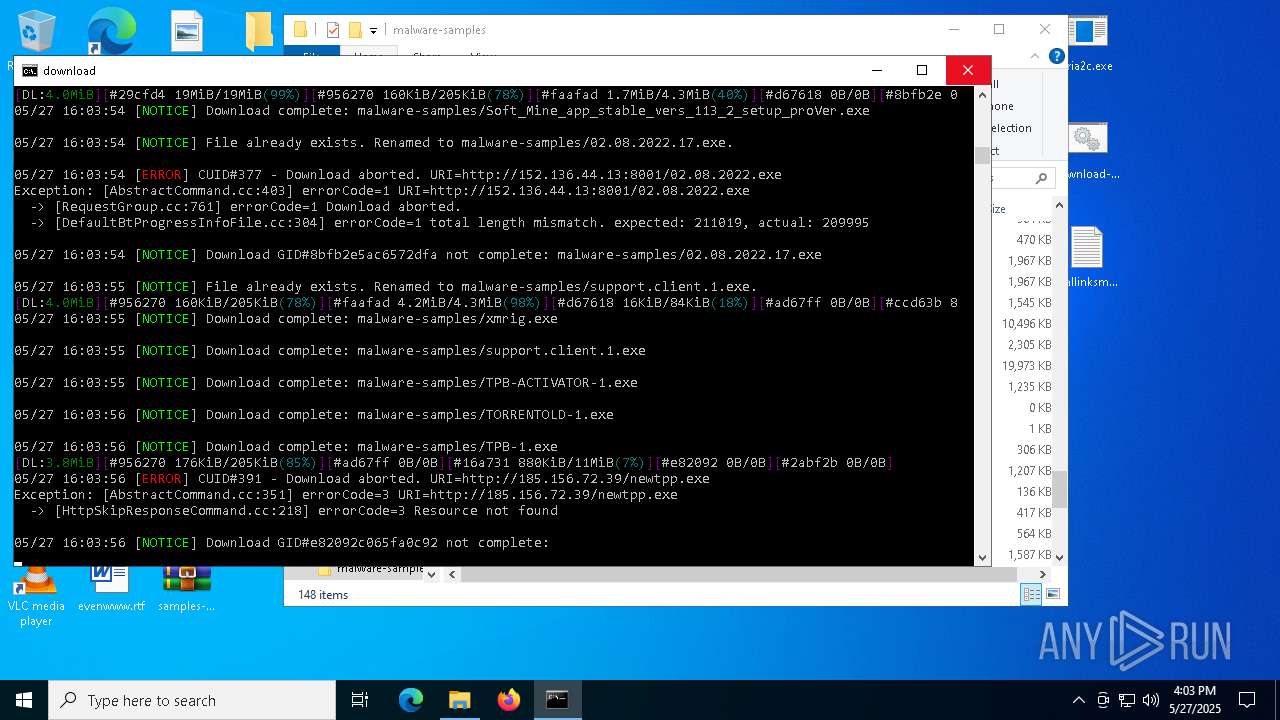
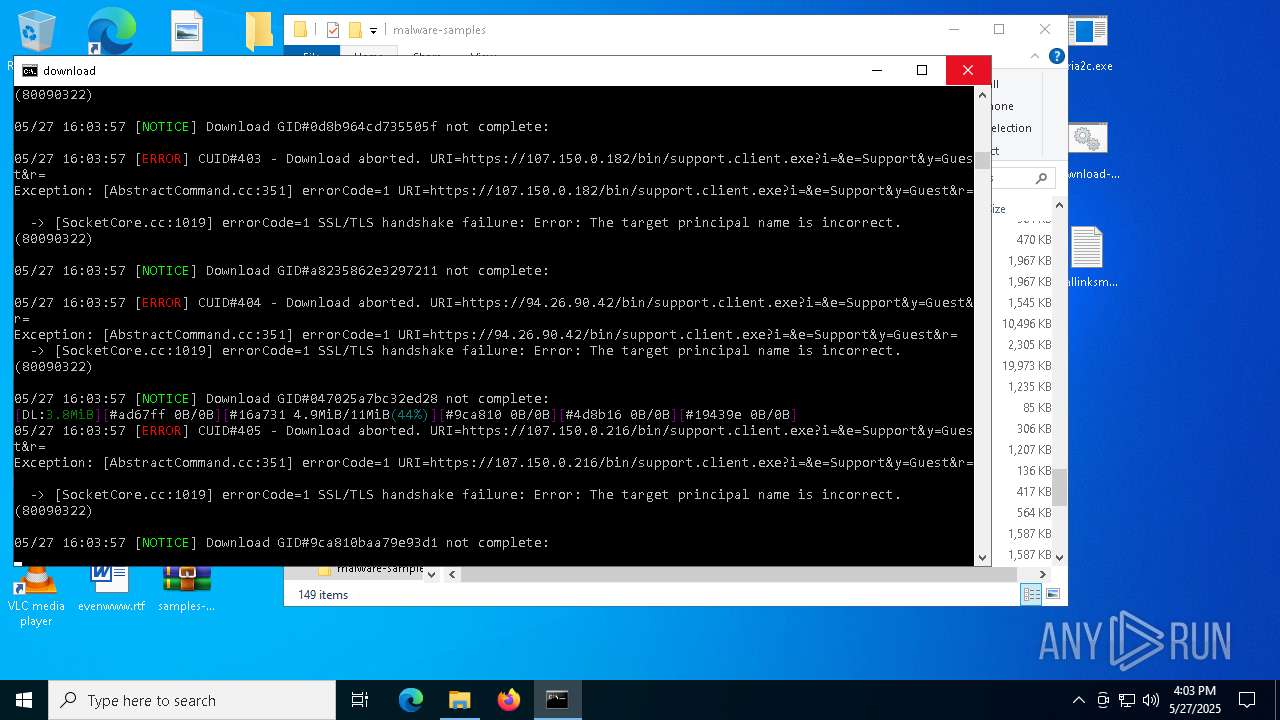
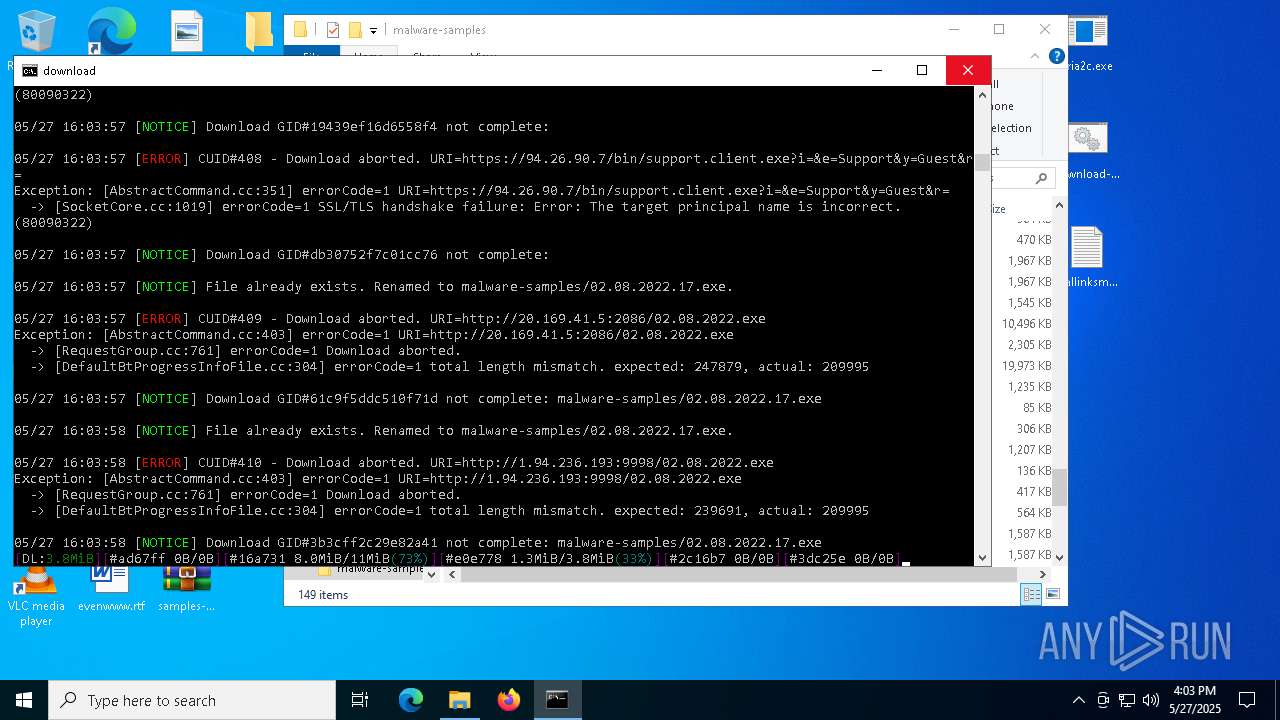
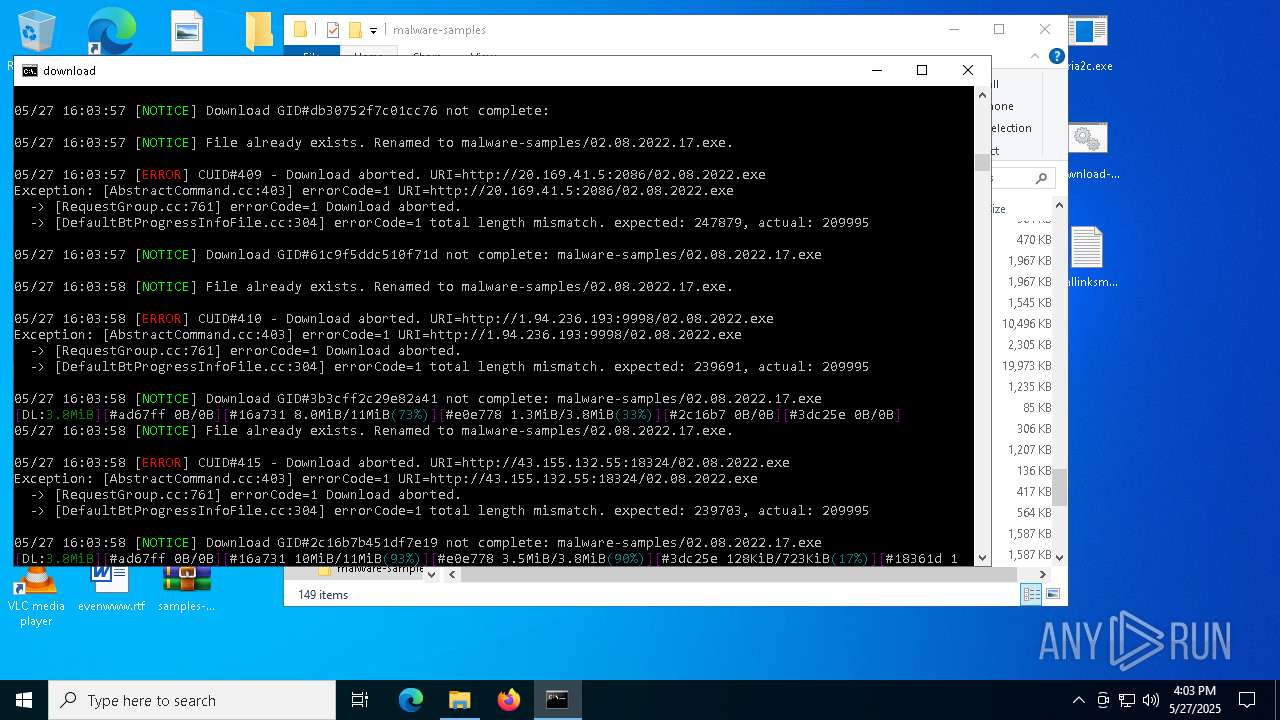
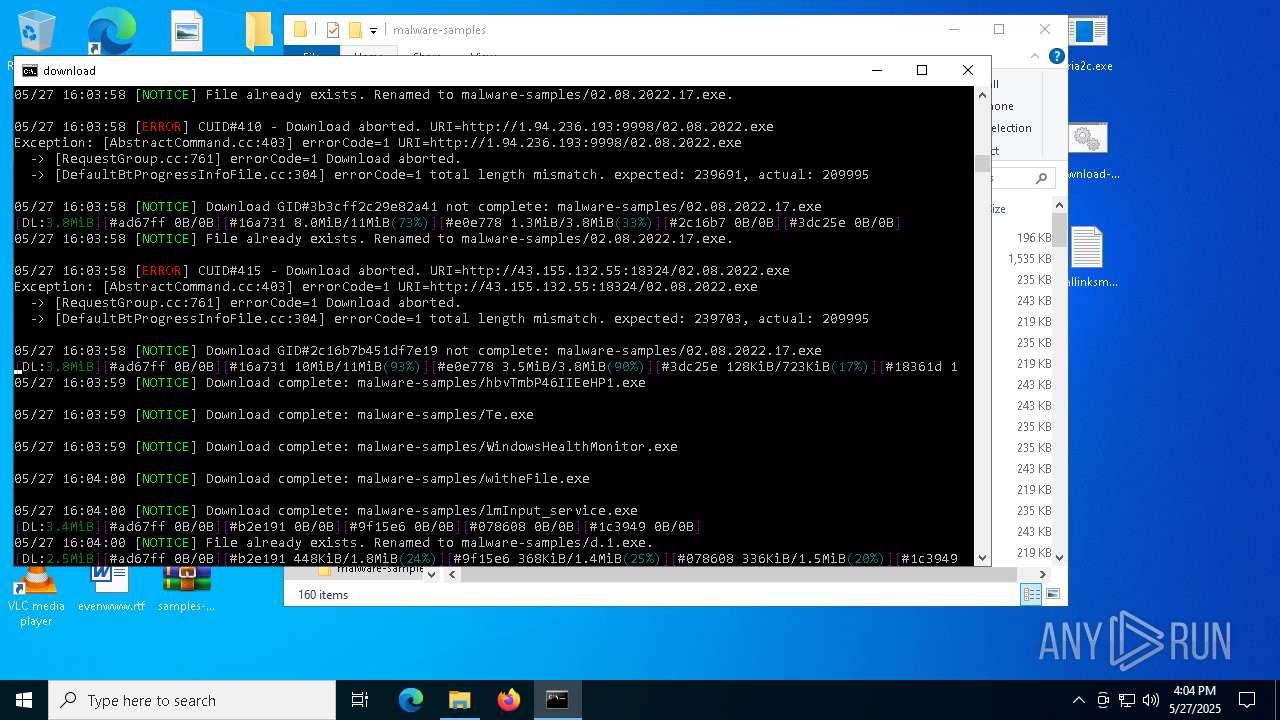
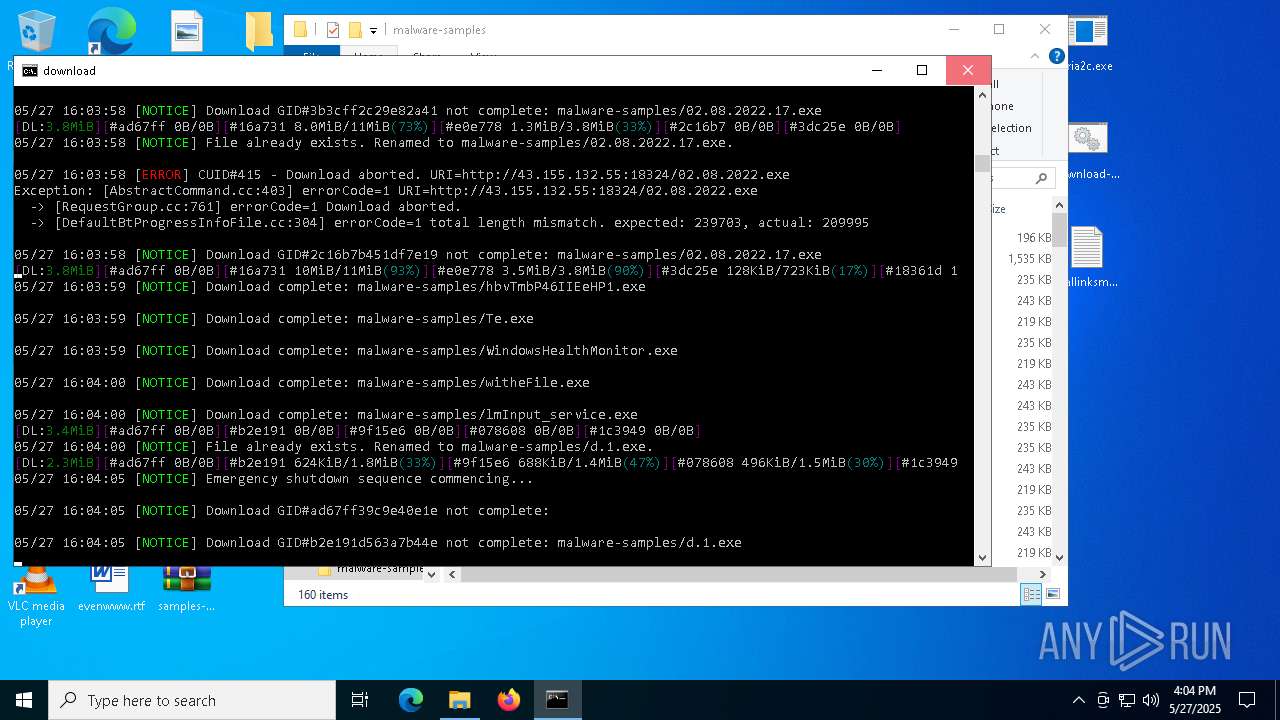
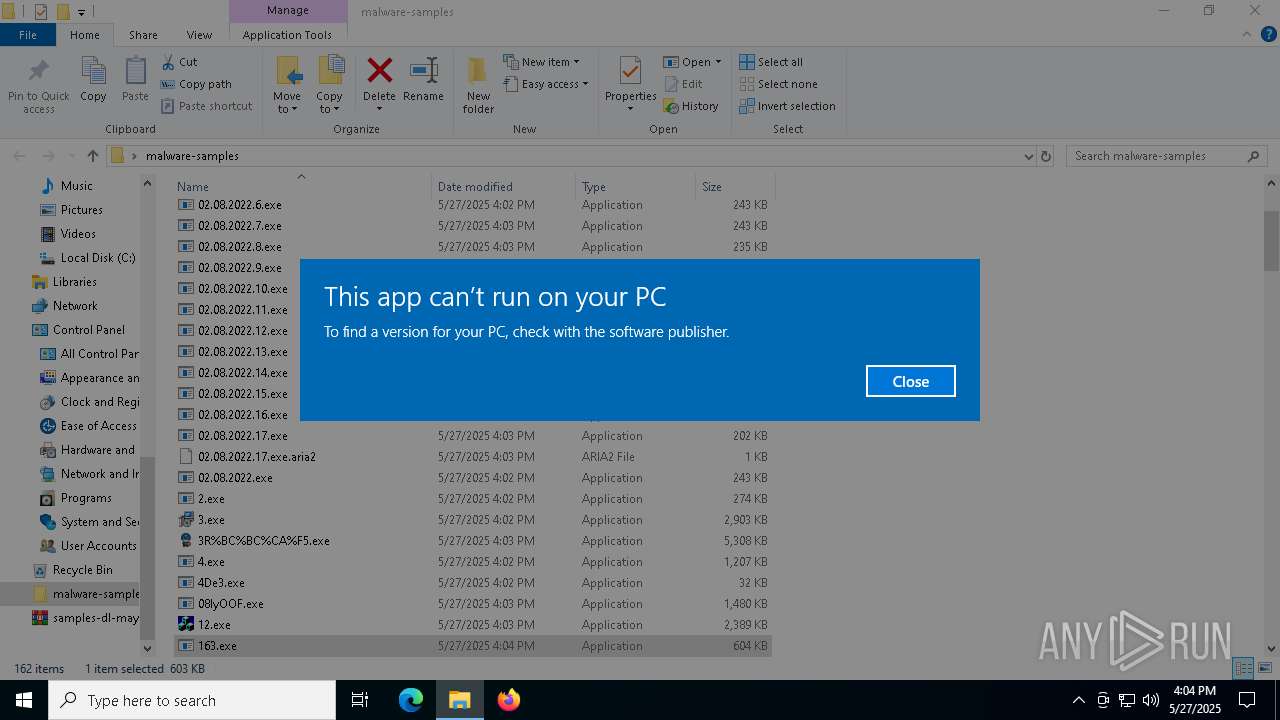
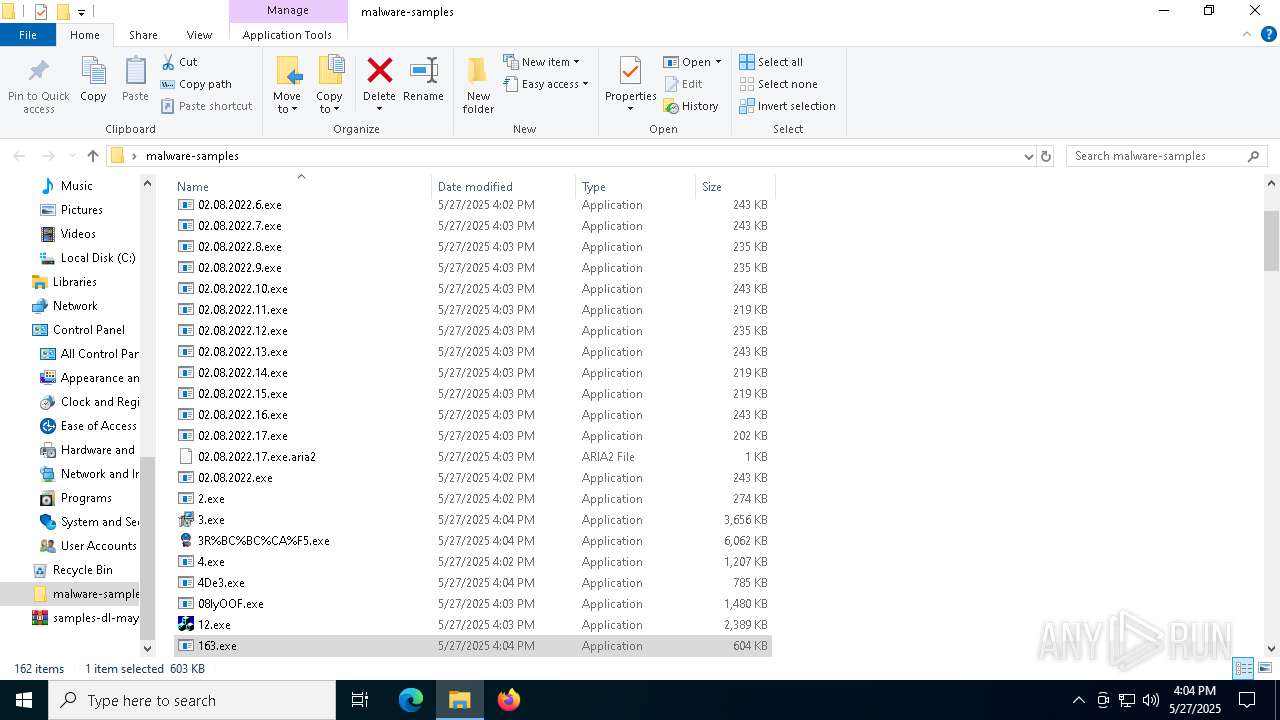
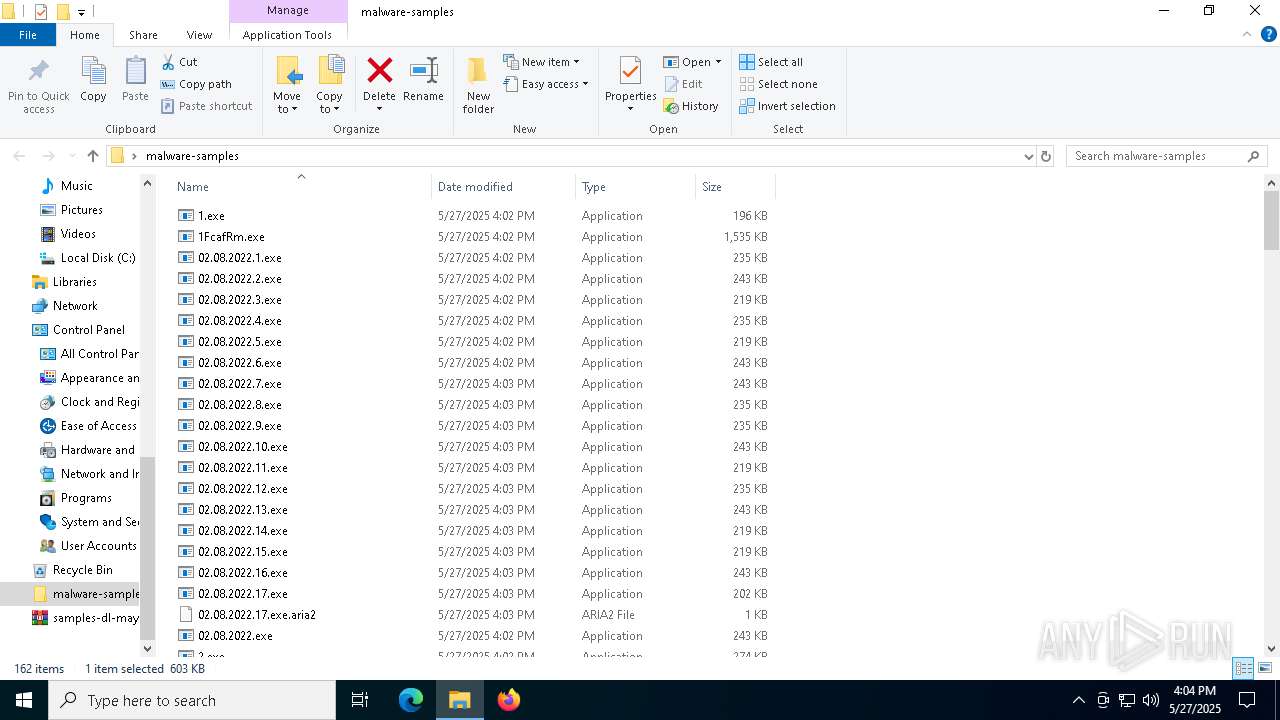
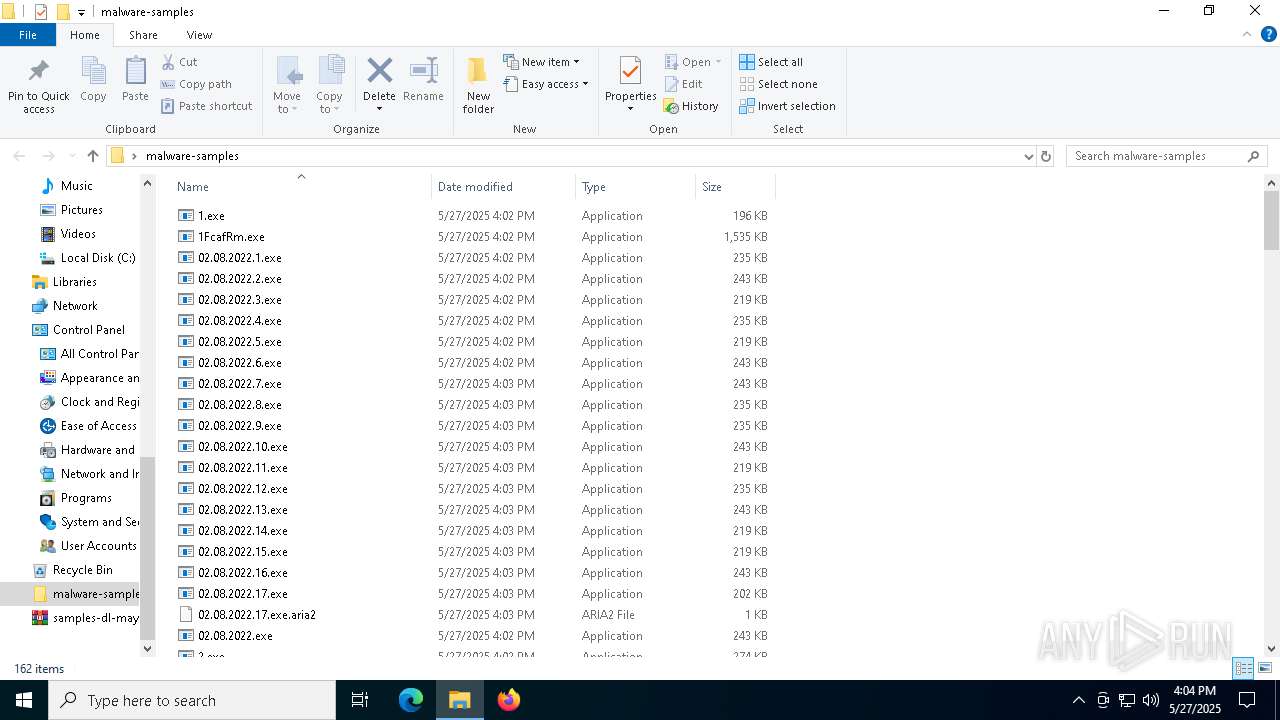
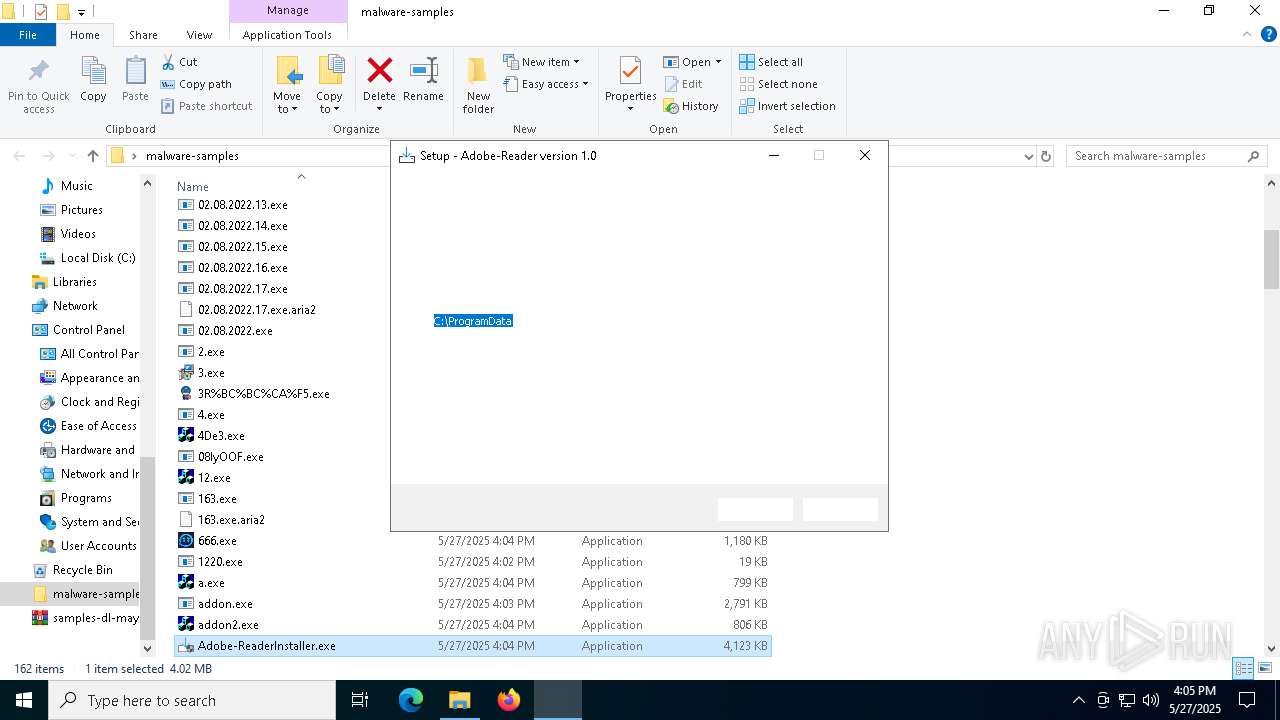
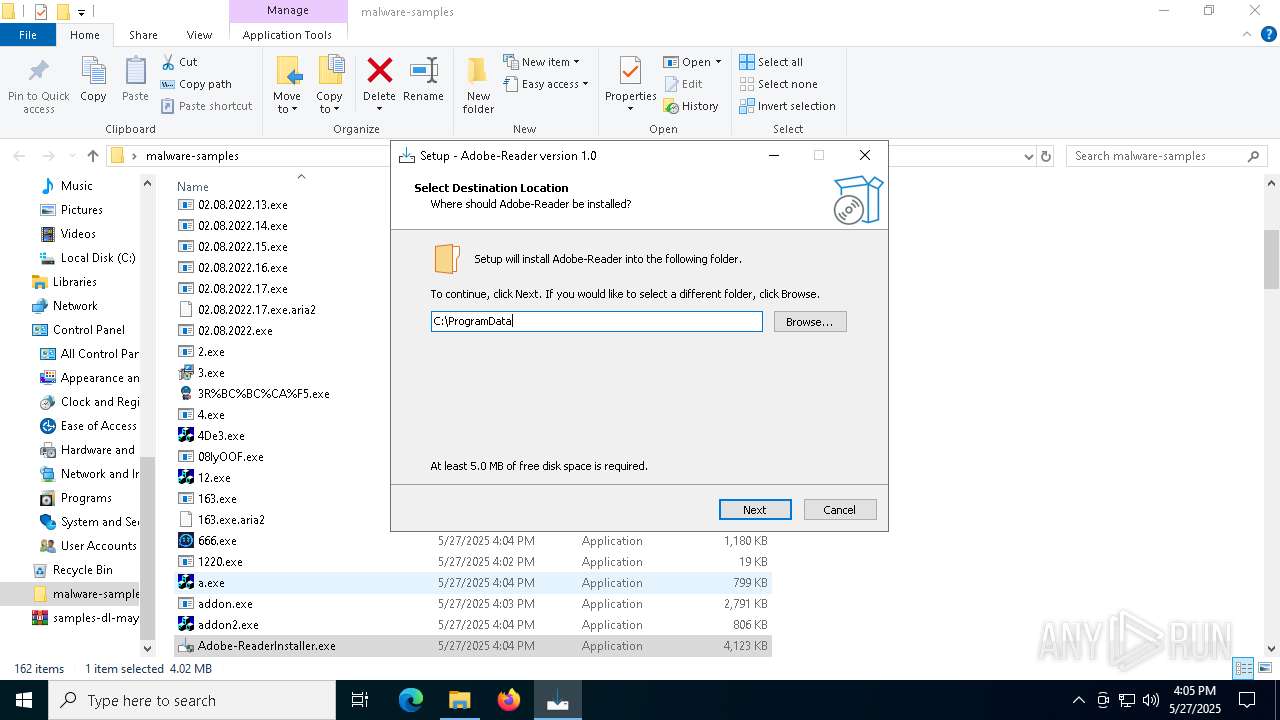
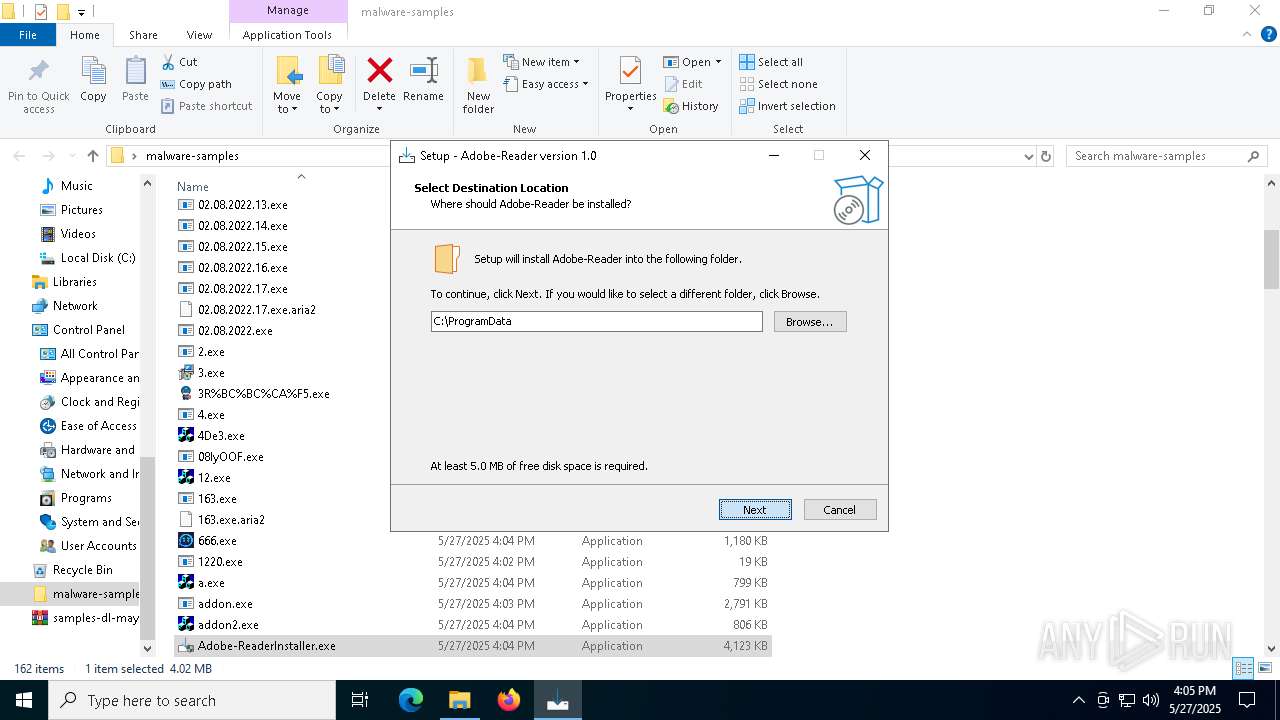
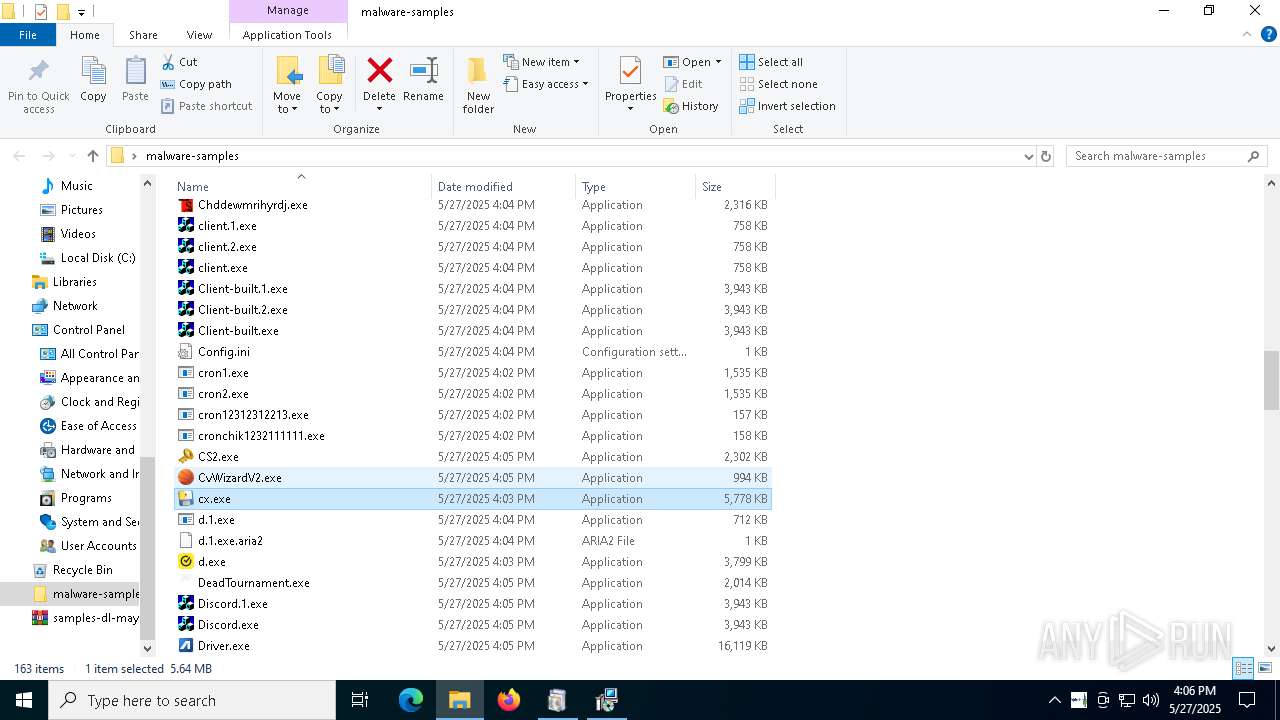
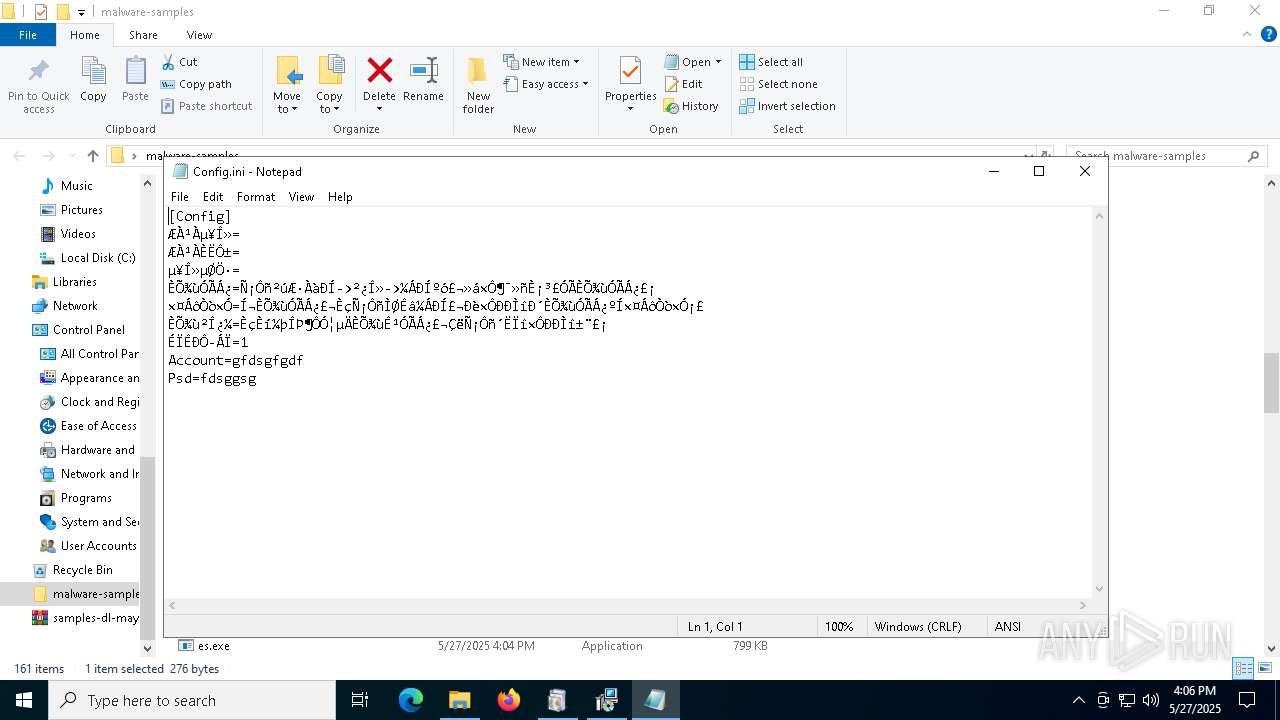
| File name: | samples-dl-may27.zip |
| Full analysis: | https://app.any.run/tasks/741435b8-a626-4acc-8697-2abb3fb70a05 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 27, 2025, 16:01:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 7F6DCB290253B59AB864C5C99B17A5E9 |
| SHA1: | D45C5CA1CD129D6D04BD4789F73258CB49E65ABE |
| SHA256: | D61AB4ADCC785F807C1C088E5E914899475F43CAFCED8D6E8AE9D2EE0DE3F66A |
| SSDEEP: | 98304:pX2tW4JauFgws9X5h+EylxkZUlnQ0APPIrOGxx+7tuJdhaTabw9kaNFF8m7yvp7l:xAWGQ1K |
MALICIOUS
LUMMA has been found (auto)
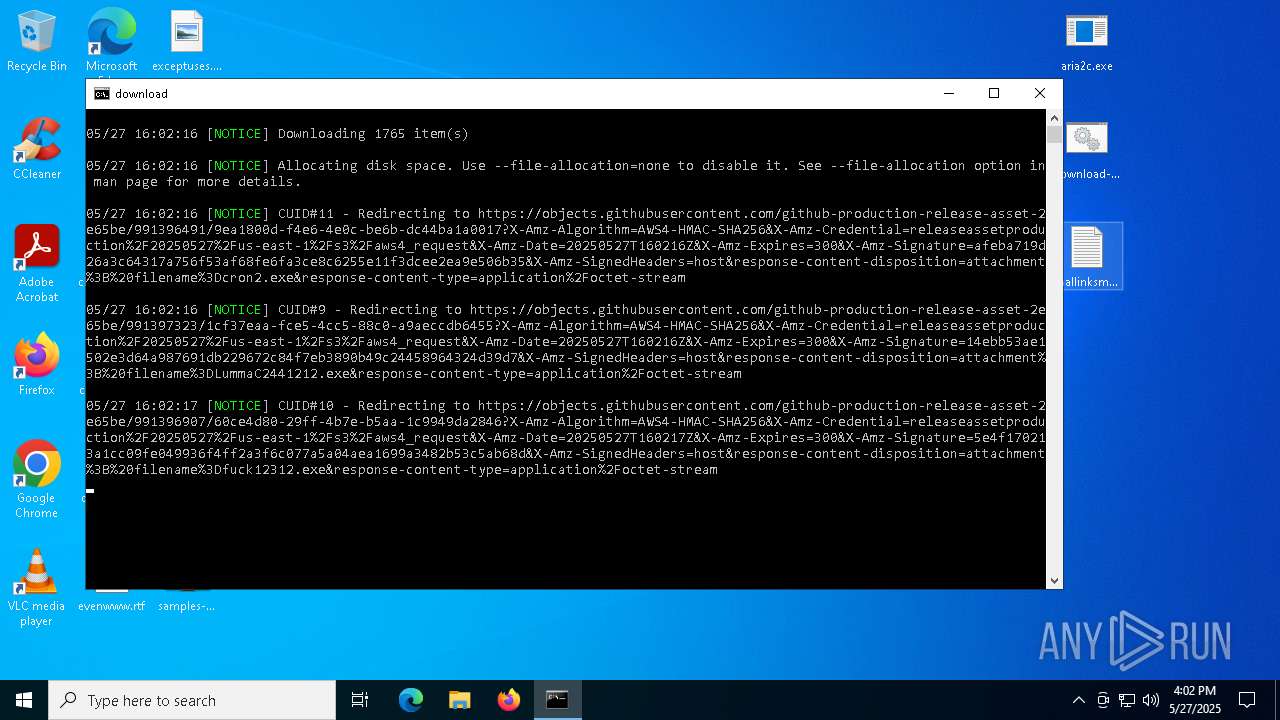
- aria2c.exe (PID: 2600)
- BrowserSetup.exe (PID: 7596)
- LummaC2441212.exe (PID: 4304)
QUASAR has been found (auto)
- aria2c.exe (PID: 2600)
GHOSTSOCKS has been found (auto)
- aria2c.exe (PID: 2600)
GENERIC has been found (auto)
- aria2c.exe (PID: 2600)
- aria2c.exe (PID: 2600)
- aria2c.exe (PID: 2600)
- aria2c.exe (PID: 2600)
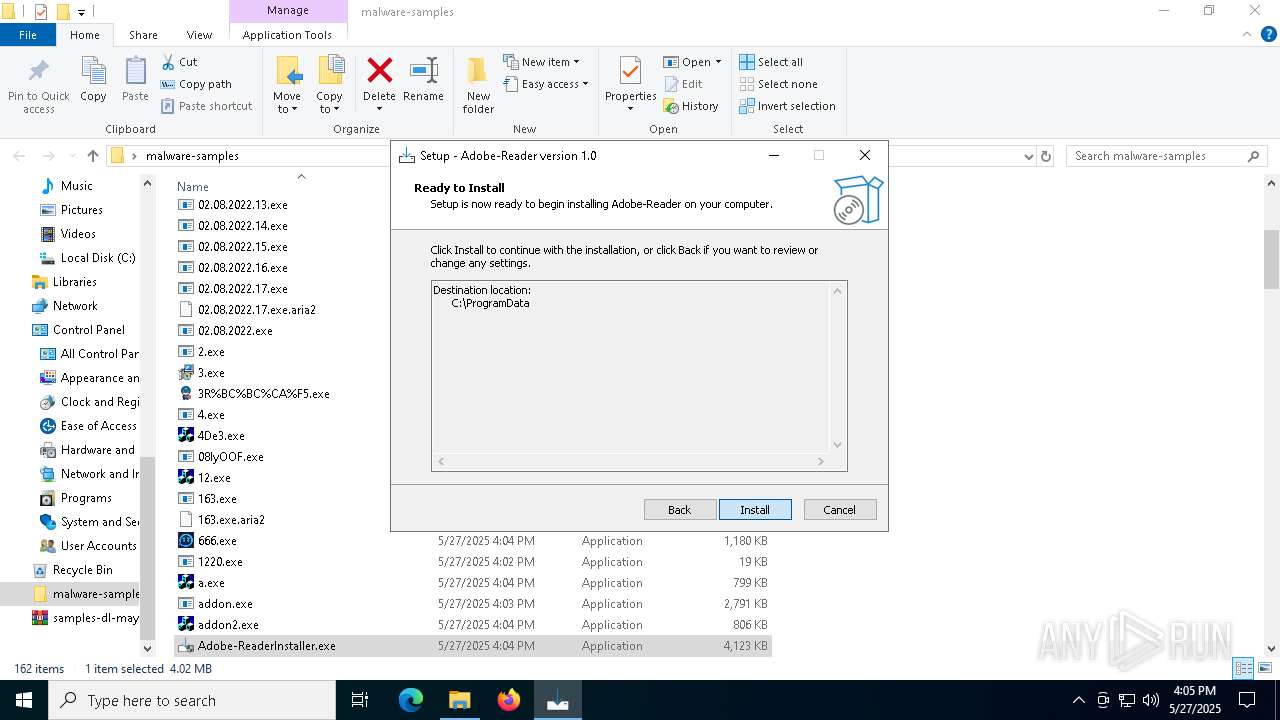
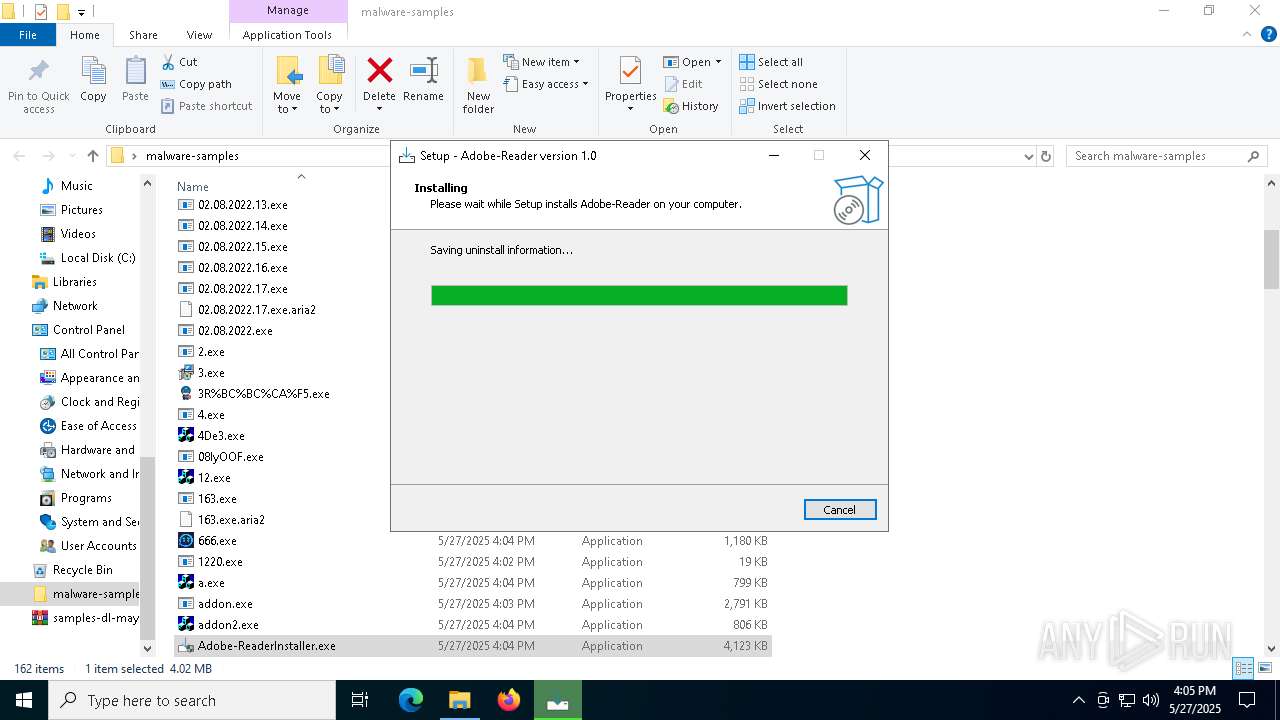
- Adobe-ReaderInstaller.exe (PID: 1128)
- Alli_AI_stable_latest_release_ver_801_Setup_win.exe (PID: 236)
- ._cache_Eijhmtanpyiuic.exe (PID: 7772)
VALLEY has been found (auto)
- aria2c.exe (PID: 2600)
LOKI has been found (auto)
- aria2c.exe (PID: 2600)
DCRAT has been found (auto)
- aria2c.exe (PID: 2600)
STEALER has been found (auto)
- aria2c.exe (PID: 2600)
- ayin.v0.1.0.exe (PID: 5444)
Executing a file with an untrusted certificate
- 3.exe (PID: 7156)
- 3.exe (PID: 2560)
- Alli_AI_stable_latest_release_ver_801_Setup_win.exe (PID: 5608)
- ._cache_Alli_AI_stable_latest_release_ver_801_Setup_win.exe (PID: 444)
- Alli_AI_stable_latest_release_ver_801_Setup_win.exe (PID: 236)
- 293a3abfea.exe (PID: 8136)
- Gamma_app_stable_vers_107_2_setup_proVer (8).exe (PID: 5256)
- ._cache_Gamma_app_stable_vers_107_2_setup_proVer (8).exe (PID: 3264)
- Gamma_app_stable_vers_107_2_setup_proVer (8).exe (PID: 1116)
- m9wPaPW.exe (PID: 4672)
- ._cache_m9wPaPW.exe (PID: 8112)
- Nationalbankdirektrernes.exe (PID: 7604)
- ._cache_m9wPaPW.exe (PID: 7532)
- ._cache_Nationalbankdirektrernes.exe (PID: 5744)
- ._cache_m9wPaPW.exe (PID: 8076)
Registers / Runs the DLL via REGSVR32.EXE
- 3.tmp (PID: 2064)
- ._cache_m9wPaPW.tmp (PID: 7556)
LUMMA has been detected (YARA)
- MSBuild.exe (PID: 632)
- MSBuild.exe (PID: 1748)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 1748)
- MSBuild.exe (PID: 8120)
- ._cache_LummaC2441212.exe (PID: 1748)
- MSBuild.exe (PID: 3708)
Connects to the CnC server
- svchost.exe (PID: 2196)
- saren.exe (PID: 892)
- d.exe (PID: 7644)
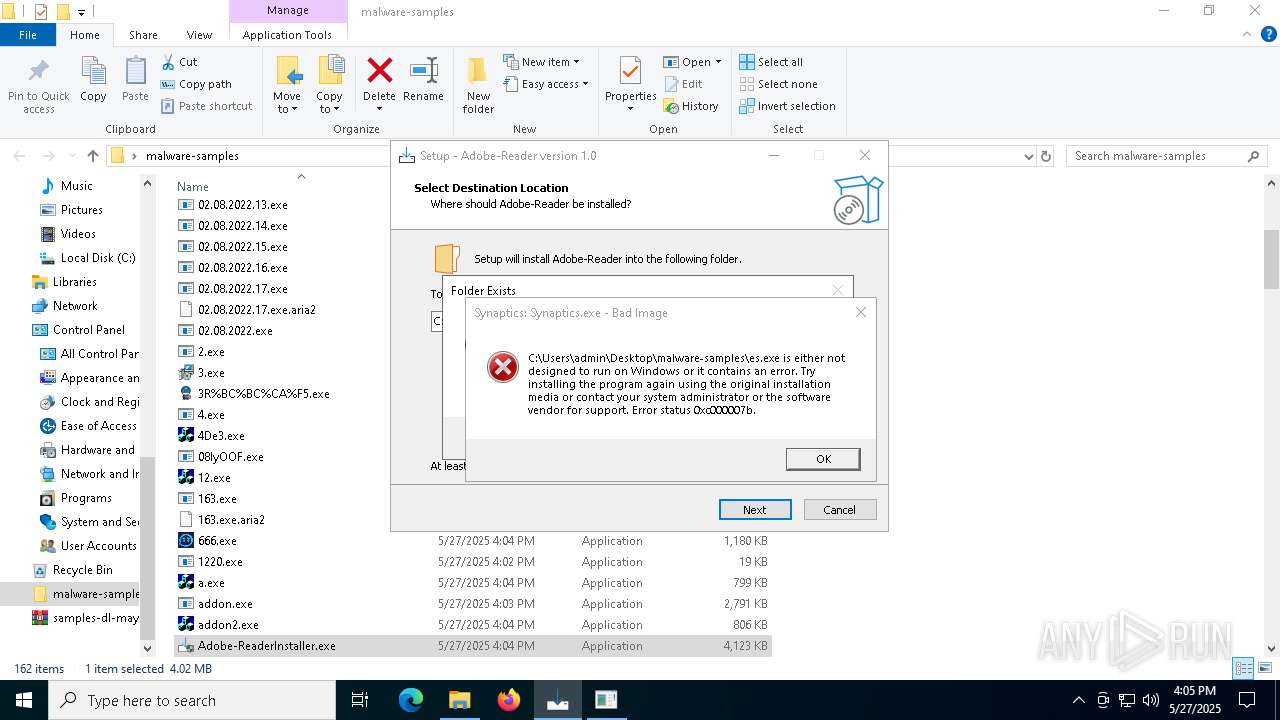
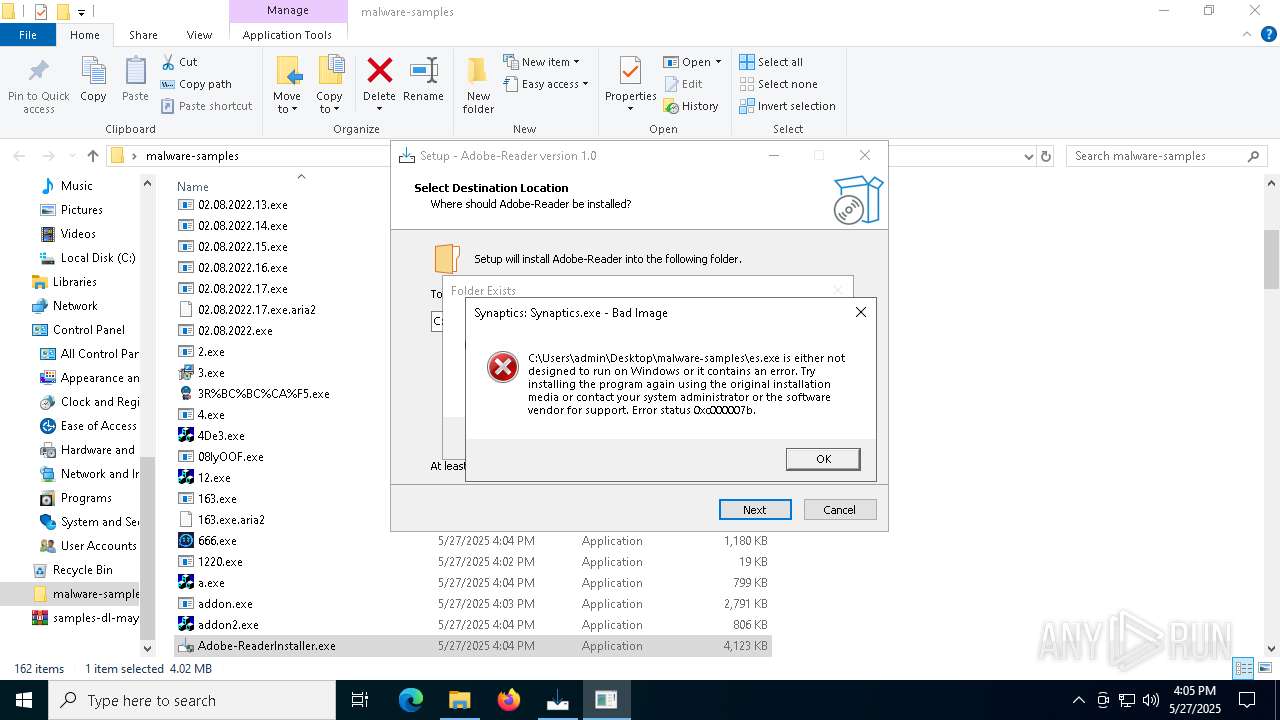
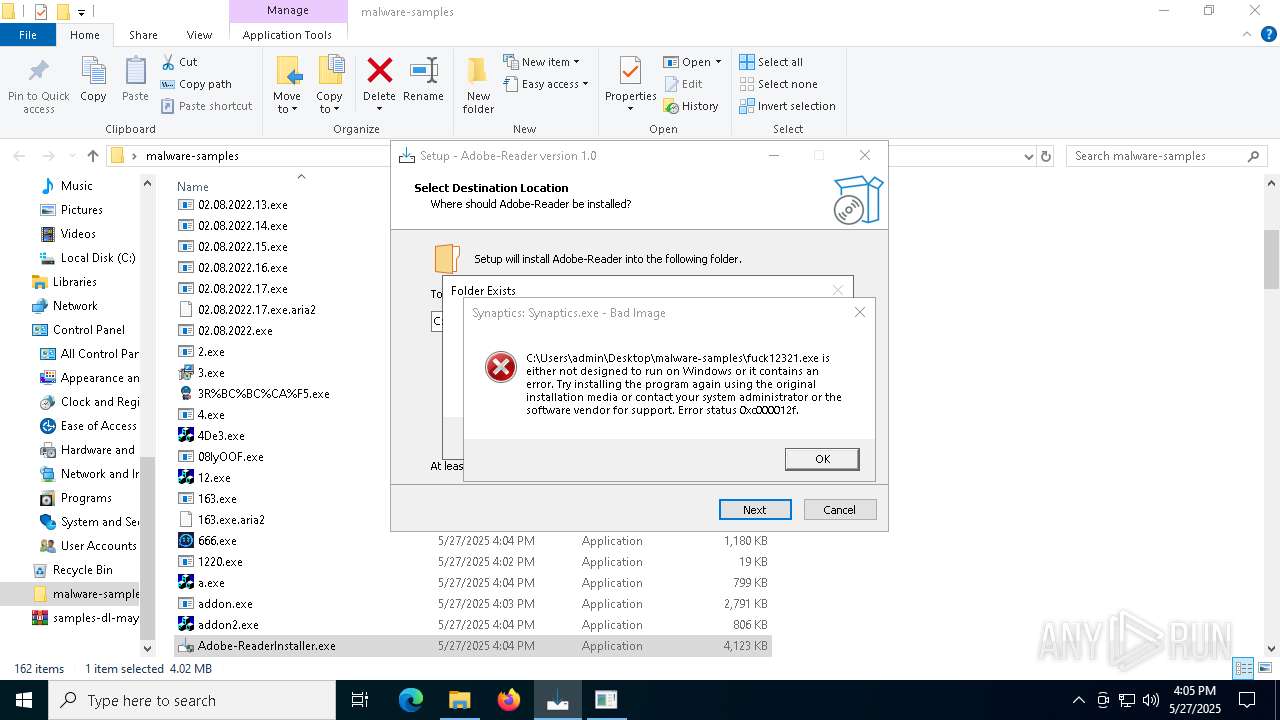
XRED has been detected (YARA)
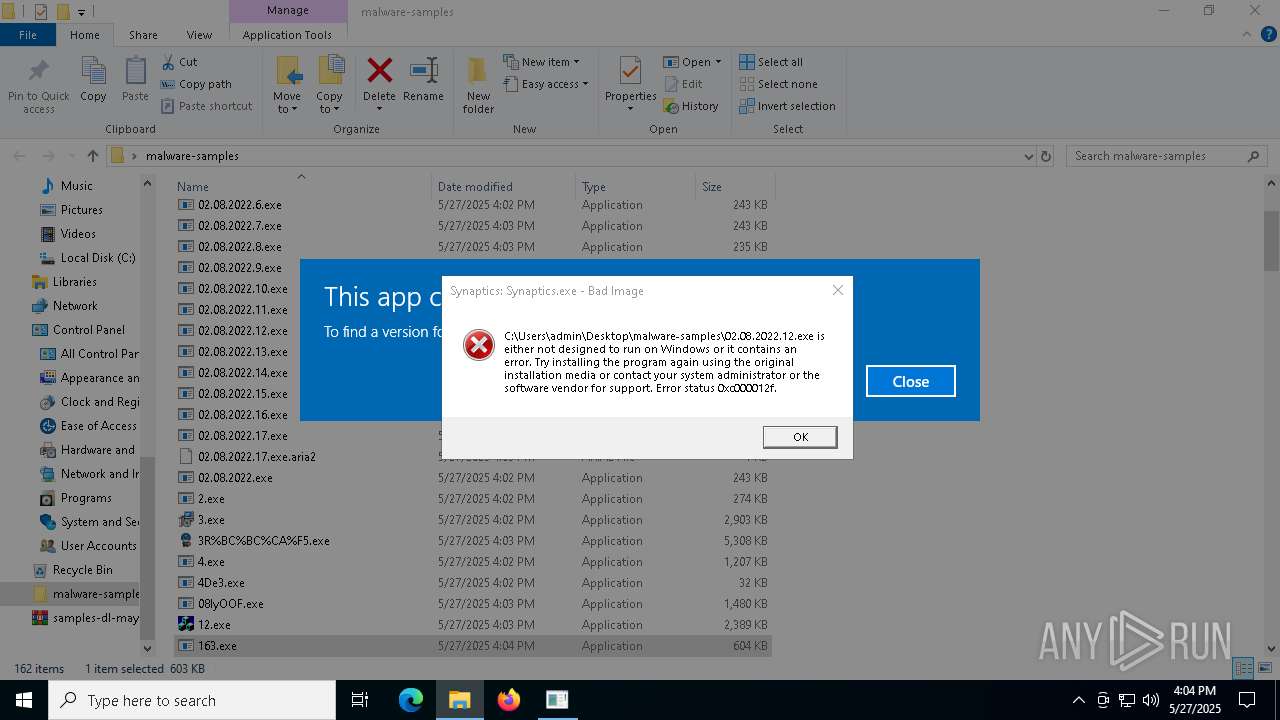
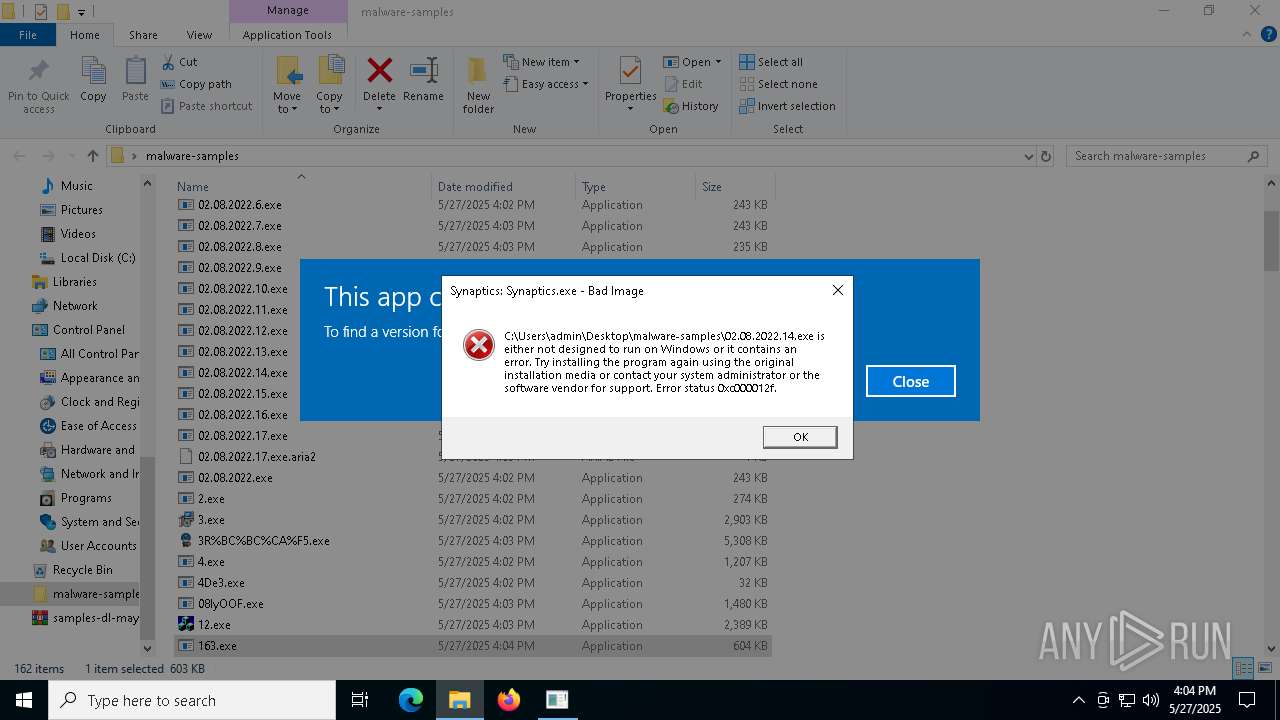
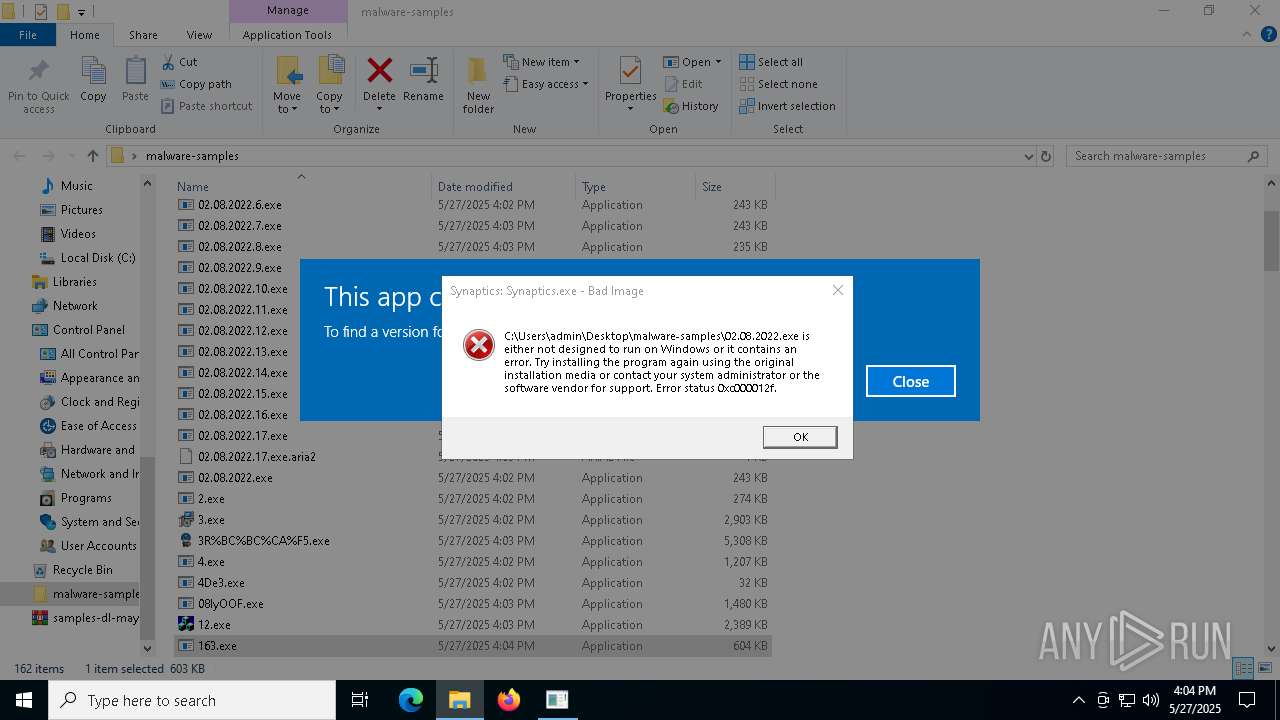
- Synaptics.exe (PID: 920)
BABAR has been found (auto)
- 666.exe (PID: 6256)
Run PowerShell with an invisible window
- powershell.exe (PID: 1852)
- powershell.exe (PID: 3156)
NJRAT has been detected (YARA)
- svhost.exe (PID: 2332)
COBALTSTRIKE has been detected (YARA)
- 1220.exe (PID: 856)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 4276)
- addon.exe (PID: 5952)
Starts CMD.EXE for self-deleting
- ._cache_addon2.exe (PID: 4212)
- addon.exe (PID: 5952)
Changes Windows Defender settings
- addon.exe (PID: 5952)
- wscript.exe (PID: 632)
Adds path to the Windows Defender exclusion list
- addon.exe (PID: 5952)
- wscript.exe (PID: 632)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 896)
Bypass execution policy to execute commands
- powershell.exe (PID: 5392)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 632)
Deletes shadow copies
- cmd.exe (PID: 5292)
AMADEY has been detected (SURICATA)
- saren.exe (PID: 892)
Signed with known abused certificate
- explorer.exe (PID: 5492)
- BrowserSetup.exe (PID: 7596)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegSvcs.exe (PID: 7828)
- RegSvcs.exe (PID: 7832)
- RegSvcs.exe (PID: 5984)
NETSUPPORT has been found (auto)
- Gamma_app_stable_vers_107_2_setup_proVer (8).exe (PID: 1116)
GCLEANER has been detected (SURICATA)
- 293a3abfea.exe (PID: 8136)
GULOADER has been found (auto)
- Nationalbankdirektrernes.exe (PID: 7604)
REDLINE has been detected (SURICATA)
- d.exe (PID: 7644)
METASTEALER has been detected (SURICATA)
- d.exe (PID: 7644)
VIDAR has been found (auto)
- random.1.exe (PID: 7272)
SUSPICIOUS
Starts CMD.EXE for commands execution
- explorer.exe (PID: 5492)
- addon.exe (PID: 5548)
- powershell.exe (PID: 1852)
- ._cache_addon2.exe (PID: 4212)
- addon.exe (PID: 5952)
- ._cache_AsyncClient.1.exe (PID: 4428)
- WmiPrvSE.exe (PID: 7668)
- ._cache_CvWizardV2.exe (PID: 7284)
- ._cache_Eijhmtanpyiuic.exe (PID: 7772)
- ._cache_random.2.exe (PID: 7836)
- cmd.exe (PID: 7544)
Potential Corporate Privacy Violation
- aria2c.exe (PID: 2600)
- powershell.exe (PID: 3156)
- saren.exe (PID: 892)
Executable content was dropped or overwritten
- aria2c.exe (PID: 2600)
- 1.exe (PID: 4724)
- 3.tmp (PID: 4244)
- 3.exe (PID: 7156)
- 3.exe (PID: 2560)
- 3.tmp (PID: 2064)
- 3R%BC%BC%CA%F5.exe (PID: 5800)
- 7z.exe (PID: 6208)
- E4B.tmp.exe (PID: 5772)
- 12.exe (PID: 2644)
- ._cache_12.exe (PID: 5384)
- Synaptics.exe (PID: 920)
- explorer.exe (PID: 5492)
- 4De3.exe (PID: 5156)
- svhost.exe (PID: 2332)
- ._cache_666.exe (PID: 7052)
- 666.exe (PID: 6256)
- csrss2.exe (PID: 4112)
- a.exe (PID: 6372)
- addon2.exe (PID: 6252)
- ._cache_addon2.exe (PID: 5984)
- Adobe-ReaderInstaller.exe (PID: 1128)
- ._cache_Adobe-ReaderInstaller.tmp (PID: 3976)
- ._cache_Adobe-ReaderInstaller.exe (PID: 1568)
- addon.exe (PID: 5952)
- powershell.exe (PID: 3156)
- agodee2.exe (PID: 4988)
- agodhh3.exe (PID: 840)
- Alli_AI_stable_latest_release_ver_801_Setup_win.exe (PID: 236)
- agodee.exe (PID: 3268)
- amnew.exe (PID: 1852)
- alphamm.exe (PID: 1052)
- ._cache_Alli_AI_stable_latest_release_ver_801_Setup_win.exe (PID: 444)
- AntiSpyware.1.exe (PID: 6760)
- AsyncClient.1.exe (PID: 7148)
- ._cache_AntiSpyware.1.exe (PID: 4272)
- AntiSpyware.exe (PID: 6136)
- server.exe (PID: 5084)
- saren.exe (PID: 892)
- ayin.v0.1.0.exe (PID: 5444)
- AsyncClient.2.exe (PID: 4244)
- ._cache_Alli_AI_stable_latest_release_ver_801_Setup_win.tmp (PID: 4756)
- ._cache_amnew.exe (PID: 5328)
- barren.exe (PID: 1568)
- ._cache_AsyncClient.1.exe (PID: 4428)
- bd.exe (PID: 3176)
- bk_0.1.4.7.exe (PID: 7200)
- ._cache_bd.exe (PID: 7192)
- csrss2.exe (PID: 7260)
- ._cache_barren.exe (PID: 7352)
- catee.exe (PID: 7624)
- BrowserSetup.exe (PID: 7596)
- cx.exe (PID: 6576)
- CvWizardV2.exe (PID: 7248)
- Eijhmtanpyiuic.exe (PID: 7360)
- ._cache_CvWizardV2.exe (PID: 7284)
- Gamma_app_stable_vers_107_2_setup_proVer (8).exe (PID: 1116)
- ._cache_Gamma_app_stable_vers_107_2_setup_proVer (8).exe (PID: 3264)
- ._cache_Gamma_app_stable_vers_107_2_setup_proVer (8).tmp (PID: 5216)
- LummaC2441212.exe (PID: 4304)
- m9wPaPW.exe (PID: 4672)
- ._cache_m9wPaPW.exe (PID: 8112)
- Nationalbankdirektrernes.exe (PID: 7604)
- obihh3.exe (PID: 7008)
- ._cache_m9wPaPW.exe (PID: 7532)
- ._cache_m9wPaPW.tmp (PID: 8020)
- ._cache_m9wPaPW.tmp (PID: 7556)
- ._cache_Eijhmtanpyiuic.exe (PID: 7772)
- ._cache_Nationalbankdirektrernes.exe (PID: 5744)
- ._cache_m9wPaPW.exe (PID: 8076)
- random.1.exe (PID: 7272)
- random.2.exe (PID: 7896)
- ._cache_random.2.exe (PID: 7836)
- ._cache_random.1.exe (PID: 1852)
- ._cache_random.1.tmp (PID: 4068)
Connects to the server without a host name
- aria2c.exe (PID: 2600)
- explorer.exe (PID: 5492)
- 4.exe (PID: 5228)
- saren.exe (PID: 892)
- 293a3abfea.exe (PID: 8136)
Connects to unusual port
- aria2c.exe (PID: 2600)
- 3R%BC%BC%CA%F5.exe (PID: 5800)
- svhost.exe (PID: 2332)
- 1220.exe (PID: 856)
- 1220.exe (PID: 4172)
- ._cache_a.exe (PID: 2040)
- RuntimeBroker.exe (PID: 5600)
- server.exe (PID: 5084)
- X64.exe (PID: 7476)
- CvWizardV2.exe (PID: 4736)
- d.exe (PID: 7644)
Process drops legitimate windows executable
- aria2c.exe (PID: 2600)
- 1.exe (PID: 4724)
- E4B.tmp.exe (PID: 5772)
- addon2.exe (PID: 6252)
- ._cache_addon2.exe (PID: 5984)
- explorer.exe (PID: 5492)
- cx.exe (PID: 6576)
- ._cache_Gamma_app_stable_vers_107_2_setup_proVer (8).tmp (PID: 5216)
Process requests binary or script from the Internet
- aria2c.exe (PID: 2600)
- powershell.exe (PID: 3156)
- saren.exe (PID: 892)
The process creates files with name similar to system file names
- aria2c.exe (PID: 2600)
Contacting a server suspected of hosting an Exploit Kit
- aria2c.exe (PID: 2600)
Possible Social Engineering Attempted
- aria2c.exe (PID: 2600)
Crypto Currency Mining Activity Detected
- aria2c.exe (PID: 2600)
Starts a Microsoft application from unusual location
- 1.exe (PID: 4724)
- E4B.tmp.exe (PID: 5772)
- ._cache_addon2.exe (PID: 5984)
- ._cache_addon2.exe (PID: 4212)
- d.exe (PID: 7644)
Starts itself from another location
- 1.exe (PID: 4724)
- E4B.tmp.exe (PID: 5772)
- 4De3.exe (PID: 5156)
- ._cache_AntiSpyware.1.exe (PID: 4272)
- ._cache_amnew.exe (PID: 5328)
Drops 7-zip archiver for unpacking
- 3.tmp (PID: 2064)
Starts POWERSHELL.EXE for commands execution
- regsvr32.exe (PID: 896)
- addon.exe (PID: 5548)
- addon.exe (PID: 5952)
- wscript.exe (PID: 632)
- regsvr32.exe (PID: 2432)
- ._cache_m9wPaPW.tmp (PID: 7556)
- regsvr32.exe (PID: 7008)
The process bypasses the loading of PowerShell profile settings
- regsvr32.exe (PID: 896)
The process hide an interactive prompt from the user
- regsvr32.exe (PID: 896)
- wscript.exe (PID: 632)
There is functionality for taking screenshot (YARA)
- MSBuild.exe (PID: 632)
- MSBuild.exe (PID: 1748)
- Synaptics.exe (PID: 920)
- ._cache_666.exe (PID: 7052)
- csrss2.exe (PID: 4112)
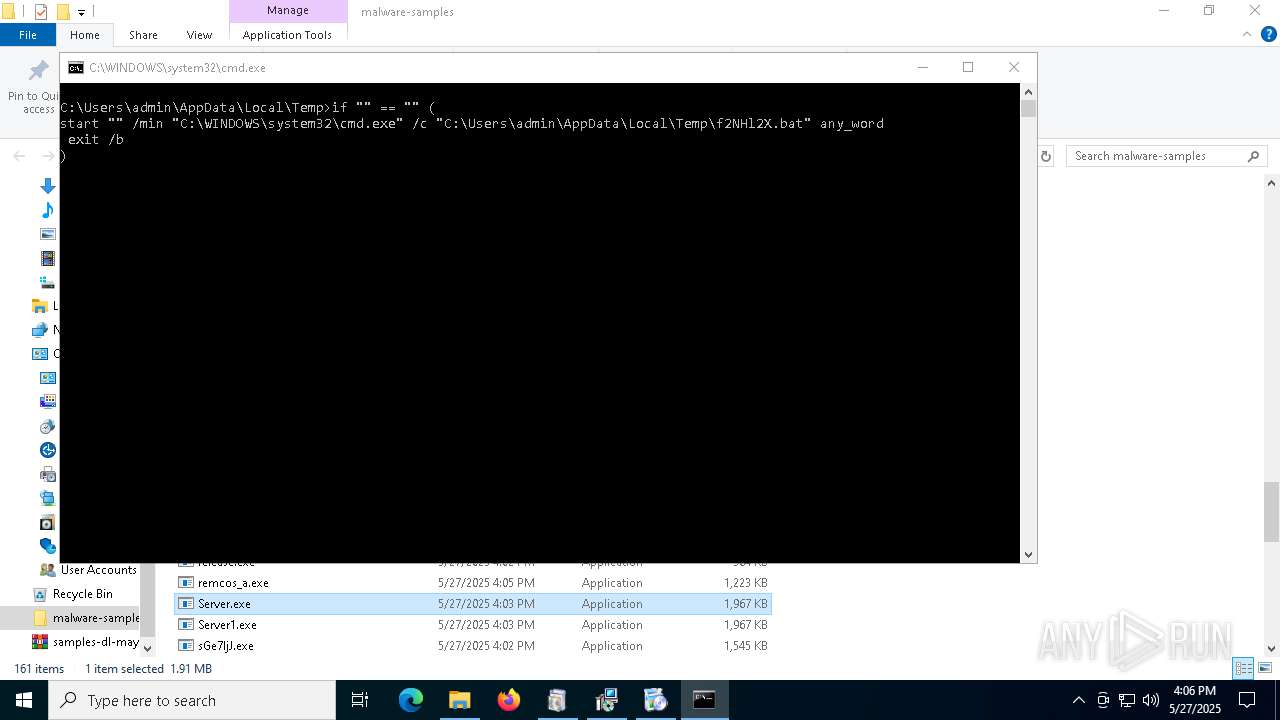
Executing commands from a ".bat" file
- explorer.exe (PID: 5492)
- ._cache_AsyncClient.1.exe (PID: 4428)
- ._cache_CvWizardV2.exe (PID: 7284)
- ._cache_random.2.exe (PID: 7836)
- cmd.exe (PID: 7544)
Contacting a server suspected of hosting an CnC
- MSBuild.exe (PID: 1748)
- svchost.exe (PID: 2196)
- saren.exe (PID: 892)
- MSBuild.exe (PID: 8120)
- MSBuild.exe (PID: 3708)
- ._cache_LummaC2441212.exe (PID: 1748)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 920)
There is functionality for communication over UDP network (YARA)
- Synaptics.exe (PID: 920)
Uses NETSH.EXE to add a firewall rule or allowed programs
- svhost.exe (PID: 2332)
- server.exe (PID: 5084)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 2564)
- net.exe (PID: 5868)
- cmd.exe (PID: 6240)
- net.exe (PID: 6584)
Starts process via Powershell
- powershell.exe (PID: 1852)
- powershell.exe (PID: 3156)
Application launched itself
- ._cache_addon2.exe (PID: 5984)
- ._cache_alphamm.exe (PID: 5036)
- cx.exe (PID: 6576)
- cmd.exe (PID: 7544)
Lists all scheduled tasks
- schtasks.exe (PID: 6824)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5756)
- cmd.exe (PID: 6512)
- cmd.exe (PID: 780)
- cmd.exe (PID: 7892)
Hides command output
- cmd.exe (PID: 5756)
- cmd.exe (PID: 6512)
Windows service management via SC.EXE
- sc.exe (PID: 5964)
- sc.exe (PID: 3896)
- sc.exe (PID: 1240)
- sc.exe (PID: 2516)
- sc.exe (PID: 6908)
Stops a currently running service
- sc.exe (PID: 4896)
- sc.exe (PID: 5728)
- sc.exe (PID: 6436)
- sc.exe (PID: 2344)
- sc.exe (PID: 2288)
The process deletes folder without confirmation
- addon.exe (PID: 5952)
Query Microsoft Defender preferences
- addon.exe (PID: 5952)
Probably obfuscated PowerShell command line is found
- addon.exe (PID: 5952)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 4224)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 4692)
- cmd.exe (PID: 5728)
- cmd.exe (PID: 2664)
Script adds exclusion path to Windows Defender
- addon.exe (PID: 5952)
- wscript.exe (PID: 632)
Executes as Windows Service
- VSSVC.exe (PID: 5748)
Process uninstalls Windows update
- wusa.exe (PID: 4988)
The process executes VB scripts
- ._cache_Adobe-ReaderInstaller.tmp (PID: 3976)
Downloads file from URI via Powershell
- powershell.exe (PID: 3156)
Found IP address in command line
- powershell.exe (PID: 3156)
Checks for external IP
- svchost.exe (PID: 2196)
- RegSvcs.exe (PID: 5984)
- RegSvcs.exe (PID: 7036)
- RegSvcs.exe (PID: 7828)
- RegSvcs.exe (PID: 7832)
Executes application which crashes
- ._cache_agodee.exe (PID: 5800)
- ._cache_agodhh3.exe (PID: 7136)
- ._cache_alphamm.exe (PID: 2984)
- core.exe (PID: 5756)
The process executes via Task Scheduler
- regsvr32.exe (PID: 2432)
- WmiPrvSE.exe (PID: 7668)
- saren.exe (PID: 7684)
- UserOOBEBroker.exe (PID: 7696)
- saren.exe (PID: 3684)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- server.exe (PID: 5084)
Probably fake Windows Update file has been dropped
- server.exe (PID: 5084)
Starts SC.EXE for service management
- addon.exe (PID: 5952)
The executable file from the user directory is run by the CMD process
- X64.exe (PID: 7476)
- CvWizardV2.exe (PID: 4736)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RegSvcs.exe (PID: 7036)
- RegSvcs.exe (PID: 5984)
- RegSvcs.exe (PID: 7832)
- RegSvcs.exe (PID: 7828)
The process drops C-runtime libraries
- cx.exe (PID: 6576)
Process drops python dynamic module
- cx.exe (PID: 6576)
Executing commands from ".cmd" file
- ._cache_Eijhmtanpyiuic.exe (PID: 7772)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5720)
Starts application with an unusual extension
- ._cache_Eijhmtanpyiuic.exe (PID: 7772)
Malware-specific behavior (creating "System.dll" in Temp)
- ._cache_Nationalbankdirektrernes.exe (PID: 5744)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 7888)
Get information on the list of running processes
- regsvr32.exe (PID: 7008)
INFO
Creates files in the program directory
- MusNotifyIcon.exe (PID: 1280)
Reads the time zone
- MusNotifyIcon.exe (PID: 1280)
- WmiPrvSE.exe (PID: 5352)
Reads the software policy settings
- WaaSMedicAgent.exe (PID: 5640)
- SIHClient.exe (PID: 6808)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Checks supported languages
- aria2c.exe (PID: 2600)
Reads the computer name
- aria2c.exe (PID: 2600)
Reads the machine GUID from the registry
- aria2c.exe (PID: 2600)
The sample compiled with english language support
- explorer.exe (PID: 5492)
- aria2c.exe (PID: 2600)
- 1.exe (PID: 4724)
- 3.tmp (PID: 2064)
- 3R%BC%BC%CA%F5.exe (PID: 5800)
- E4B.tmp.exe (PID: 5772)
- 12.exe (PID: 2644)
- ._cache_12.exe (PID: 5384)
- addon2.exe (PID: 6252)
- ._cache_addon2.exe (PID: 5984)
- ._cache_Adobe-ReaderInstaller.tmp (PID: 3976)
- agodee2.exe (PID: 4988)
- agodee.exe (PID: 3268)
- agodhh3.exe (PID: 840)
- alphamm.exe (PID: 1052)
- ._cache_Alli_AI_stable_latest_release_ver_801_Setup_win.tmp (PID: 4756)
- ayin.v0.1.0.exe (PID: 5444)
- catee.exe (PID: 7624)
- saren.exe (PID: 892)
- BrowserSetup.exe (PID: 7596)
- cx.exe (PID: 6576)
- ._cache_Gamma_app_stable_vers_107_2_setup_proVer (8).tmp (PID: 5216)
- Nationalbankdirektrernes.exe (PID: 7604)
- obihh3.exe (PID: 7008)
- ._cache_Eijhmtanpyiuic.exe (PID: 7772)
Creates files or folders in the user directory
- explorer.exe (PID: 5492)
The sample compiled with turkish language support
- aria2c.exe (PID: 2600)
- 12.exe (PID: 2644)
- Synaptics.exe (PID: 920)
The sample compiled with chinese language support
- aria2c.exe (PID: 2600)
- bd.exe (PID: 3176)
- ._cache_m9wPaPW.tmp (PID: 7556)
Manual execution by a user
- 1.exe (PID: 4724)
- 2.exe (PID: 6476)
- 3.exe (PID: 7156)
- 1FcafRm.exe (PID: 732)
- 3R%BC%BC%CA%F5.exe (PID: 5800)
- cmd.exe (PID: 7048)
- 4.exe (PID: 5228)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2852)
Compiled with Borland Delphi (YARA)
- 4.exe (PID: 5228)
- Synaptics.exe (PID: 920)
- svhost.exe (PID: 2332)
- ._cache_666.exe (PID: 7052)
- csrss2.exe (PID: 4112)
NsPack has been detected
- ._cache_666.exe (PID: 7052)
Attempting to use instant messaging service
- RegSvcs.exe (PID: 7036)
- RegSvcs.exe (PID: 7828)
- MSBuild.exe (PID: 4724)
Manages system restore points
- SrTasks.exe (PID: 1748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(632) MSBuild.exe
C2 (9)escczlv.top/bufi
citellcagt.top/gjtu
korxddl.top/qidz
narrathfpt.top/tekq
localixbiw.top/zlpa
greengwjz.top/zdka
bogtkr.top/zhyk
harumseeiw.top/tqmn
diecam.top/laur
(PID) Process(1748) MSBuild.exe
C2 (8)escczlv.top/bufi
citellcagt.top/gjtu
korxddl.top/qidz
ordntx.top/pxla
narrathfpt.top/tekq
localixbiw.top/zlpa
bogtkr.top/zhyk
diecam.top/laur
NjRat
(PID) Process(2332) svhost.exe
C246.158.253.80
Ports6522
BotnetMyBot
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\214067972532959fc4990b7a0cbcf20a
SplitterY262SUCZ4UJJ
Version0.7d
CobalStrike
(PID) Process(856) 1220.exe
C2101.132.147.63:7415/DAbv
HeadersUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; BOIE9;SVSE)
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:15 13:00:24 |
| ZipCRC: | 0x44759b3e |
| ZipCompressedSize: | 2466413 |
| ZipUncompressedSize: | 6006798 |
| ZipFileName: | aria2c.exe |
Total processes
430
Monitored processes
309
Malicious processes
57
Suspicious processes
20
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "cmd.exe" /c schtasks /query /tn "WinServiceTask" | C:\Windows\System32\cmd.exe | — | ._cache_addon2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | timeout 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | "C:\Users\admin\Desktop\malware-samples\Alli_AI_stable_latest_release_ver_801_Setup_win.exe" | C:\Users\admin\Desktop\malware-samples\Alli_AI_stable_latest_release_ver_801_Setup_win.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: HIGH Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 240 | C:\WINDOWS\System32\svchost.exe -k WerSvcGroup | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | "C:\Users\admin\Desktop\malware-samples\._cache_Alli_AI_stable_latest_release_ver_801_Setup_win.exe" | C:\Users\admin\Desktop\malware-samples\._cache_Alli_AI_stable_latest_release_ver_801_Setup_win.exe | Alli_AI_stable_latest_release_ver_801_Setup_win.exe | ||||||||||||
User: admin Company: Handy Software Integrity Level: HIGH Description: Handy Viewer Version: 2.8.0.0 Modules
| |||||||||||||||
| 496 | "C:\Users\admin\Desktop\malware-samples\08IyOOF.exe" | C:\Users\admin\Desktop\malware-samples\08IyOOF.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 632 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | 1FcafRm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
Lumma(PID) Process(632) MSBuild.exe C2 (9)escczlv.top/bufi citellcagt.top/gjtu korxddl.top/qidz narrathfpt.top/tekq localixbiw.top/zlpa greengwjz.top/zdka bogtkr.top/zhyk harumseeiw.top/tqmn diecam.top/laur | |||||||||||||||
| 632 | "wscript.exe" "C:\Users\admin\AppData\Local\Temp\is-5C215.tmp\1.vbs" | C:\Windows\SysWOW64\wscript.exe | — | ._cache_Adobe-ReaderInstaller.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 632 | "C:\Users\admin\Desktop\malware-samples\._cache_agodee2.exe" | C:\Users\admin\Desktop\malware-samples\._cache_agodee2.exe | — | agodee2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
488 174
Read events
486 915
Write events
1 188
Delete events
71
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000030308 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\samples-dl-may27.zip | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010013000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C000000120000000000000063006C007500620061007500740068006F0072002E0070006E0067003E002000200000001A00000000000000630072006500610074006900760065007200650073006F006C007500740069006F006E002E0070006E0067003E002000200000001200000000000000640065007400610069006C006700690072006C002E007200740066003E002000200000000F000000000000006500760065006E007700770077002E007200740066003E00200020000000120000000000000065007800630065007000740075007300650073002E006A00700067003E0020002000000014000000000000006600610078007400680065007200650066006F00720065002E0070006E0067003E0020002000000012000000000000006600650065006C00670072006F007500700073002E006A00700067003E0020002000000017000000000000007300750062006A0065006300740063006F006E007400610069006E0073002E007200740066003E0020002000000010000000000000007400680065006F007200790070006F002E0070006E0067003E002000200000001800000000000000730061006D0070006C00650073002D0064006C002D006D0061007900320037002E007A00690070003E002000200000000E000000000000006100720069006100320063002E006500780065003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001300000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000000400000A040110000006041000000001200 | |||
Executable files
669
Suspicious files
77
Text files
126
Unknown types
351
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1280 | MusNotifyIcon.exe | C:\ProgramData\USOShared\Logs\User\NotifyIcon.f3d745d5-b7a9-4e8b-94de-6fd51e01cc2c.1.etl | etl | |
MD5:98581A5D7A3A3E179C22666C918EA4AE | SHA256:E7F2A2A69F11C13DF3DD2877C23B021B105F80F2EA034534A26972B499C04C38 | |||
| 2600 | aria2c.exe | C:\Users\admin\Desktop\malware-samples\Driver.exe.aria2 | pi2 | |
MD5:85F5A3B71B78C0C659258FCC0AD3D500 | SHA256:4F2197BCA6C82AD7F57AFE1EAACCD16EC6E1CC4874E9907E42C71F92676D4E4E | |||
| 2852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2852.4147\aria2c.exe | executable | |
MD5:6C5EA5A82D756BCA4A9610C8D2260D2F | SHA256:B9CD71B275AF11B63C33457B0F43F2F2675937070C563E195F223EFD7FA4C74B | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 5492 | explorer.exe | C:\Users\admin\Desktop\mallinksmay272025.txt | text | |
MD5:960F39655FA1EA1F204469942987016B | SHA256:2117B60A42000C6A7B89D60E2B5DC8D78B168DD6F7D657CE3A3AADDC744A9F6C | |||
| 2600 | aria2c.exe | C:\Users\admin\Desktop\malware-samples\cron2.exe.aria2 | pi2 | |
MD5:06595A2476773AA13E51A72C65418D9D | SHA256:20D0169750E5541F82C24579992CACD7CA7A8EAF1480C52AD19DCE36F4B592FD | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:2B1A8311E31BD2B2F1A6DBAF74459F67 | SHA256:AD21748535FF32133EB1A901ABC49BF21E94248D2E4CE2699D1BBEF744956167 | |||
| 2600 | aria2c.exe | C:\Users\admin\Desktop\malware-samples\Nw2x8ps.exe.aria2 | pi2 | |
MD5:AE6D8644B390F9B6BF96370F7ADB4790 | SHA256:FFF8D6A6A542BD3C9A3F2268441483153B54E91AF37A0E0B8D6D3B67F10DEA3C | |||
| 5492 | explorer.exe | C:\Users\admin\Desktop\aria2c.exe | executable | |
MD5:6C5EA5A82D756BCA4A9610C8D2260D2F | SHA256:B9CD71B275AF11B63C33457B0F43F2F2675937070C563E195F223EFD7FA4C74B | |||
| 5492 | explorer.exe | C:\Users\admin\Desktop\download-may-27.bat | text | |
MD5:FF483EF6FA55AB60C93EE5F7661B60B0 | SHA256:E7FA1BA63DC3940C007BD72ACFB56F384A599A1611F2965A9F32043F89D2C52A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
250
TCP/UDP connections
401
DNS requests
82
Threats
735
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2600 | aria2c.exe | GET | 200 | 195.82.146.131:80 | http://195.82.146.131/HthsDb74/Plugins/Driver.exe | unknown | — | — | malicious |
2600 | aria2c.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/7787589409/Nw2x8ps.exe | unknown | — | — | malicious |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2600 | aria2c.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2600 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
2600 | aria2c.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2600 | aria2c.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2600 | aria2c.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2600 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
2600 | aria2c.exe | Misc activity | ET INFO Packed Executable Download |
2600 | aria2c.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2600 | aria2c.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2600 | aria2c.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 35 |