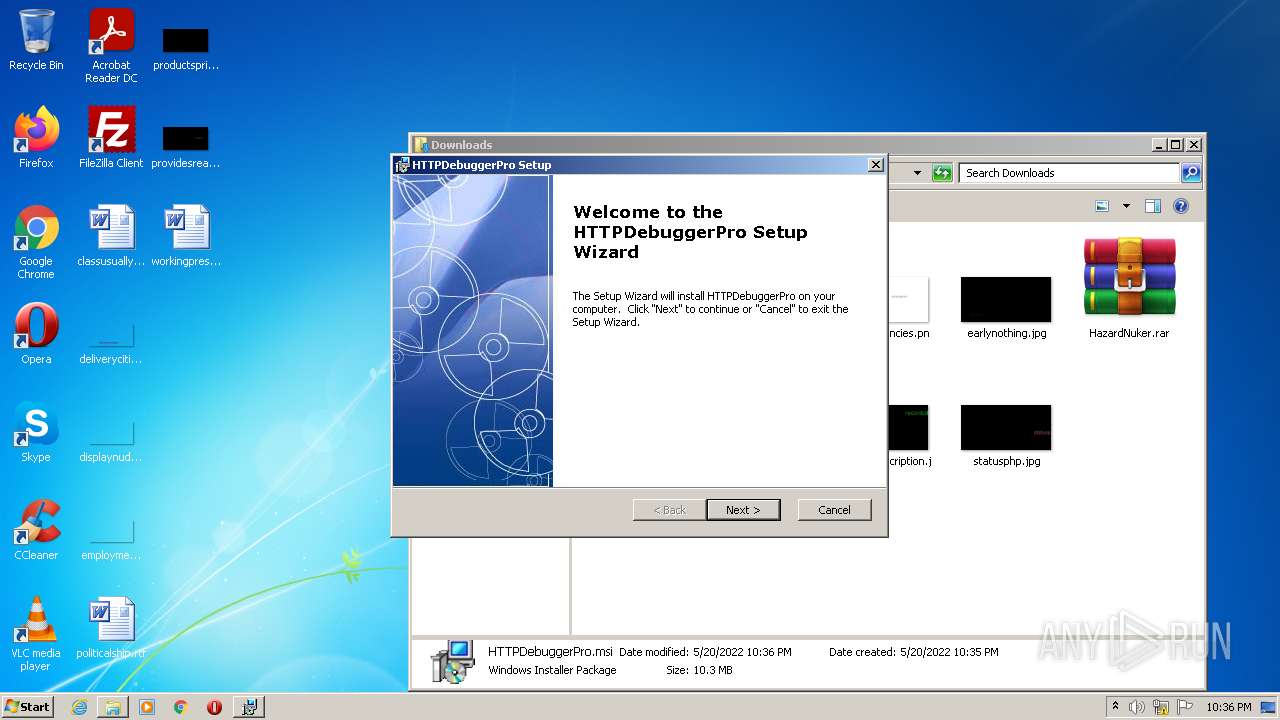
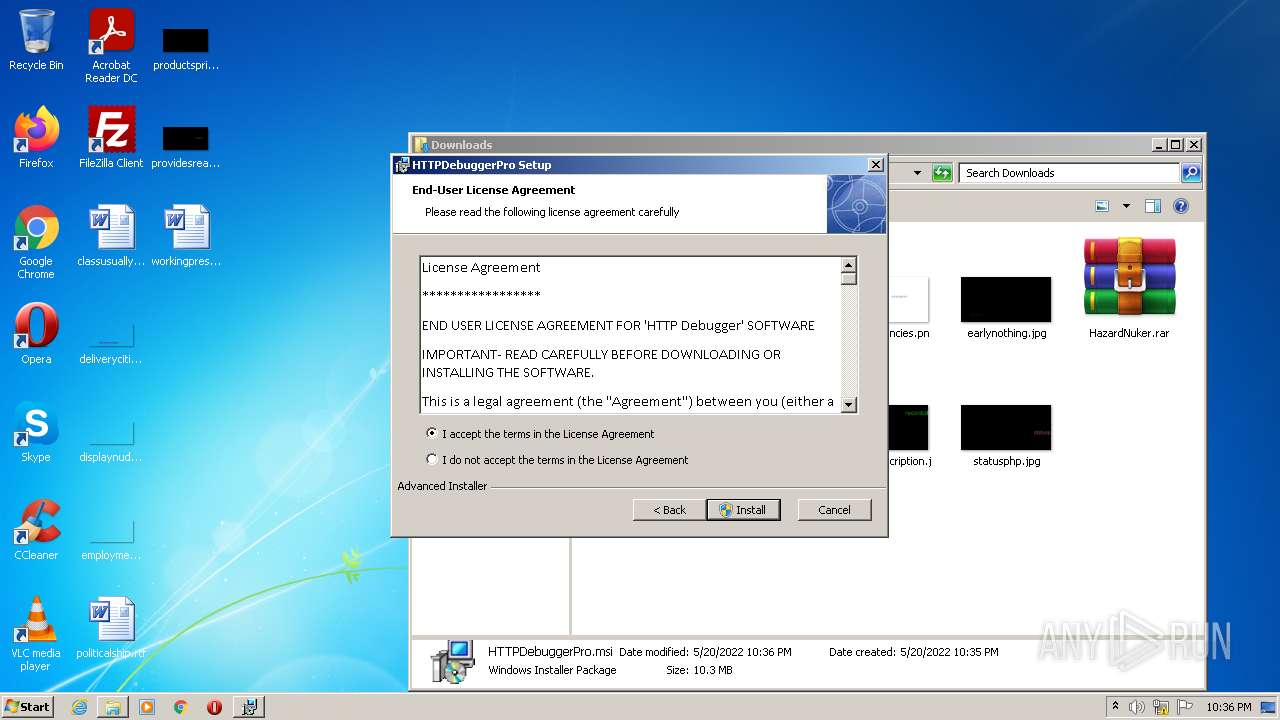
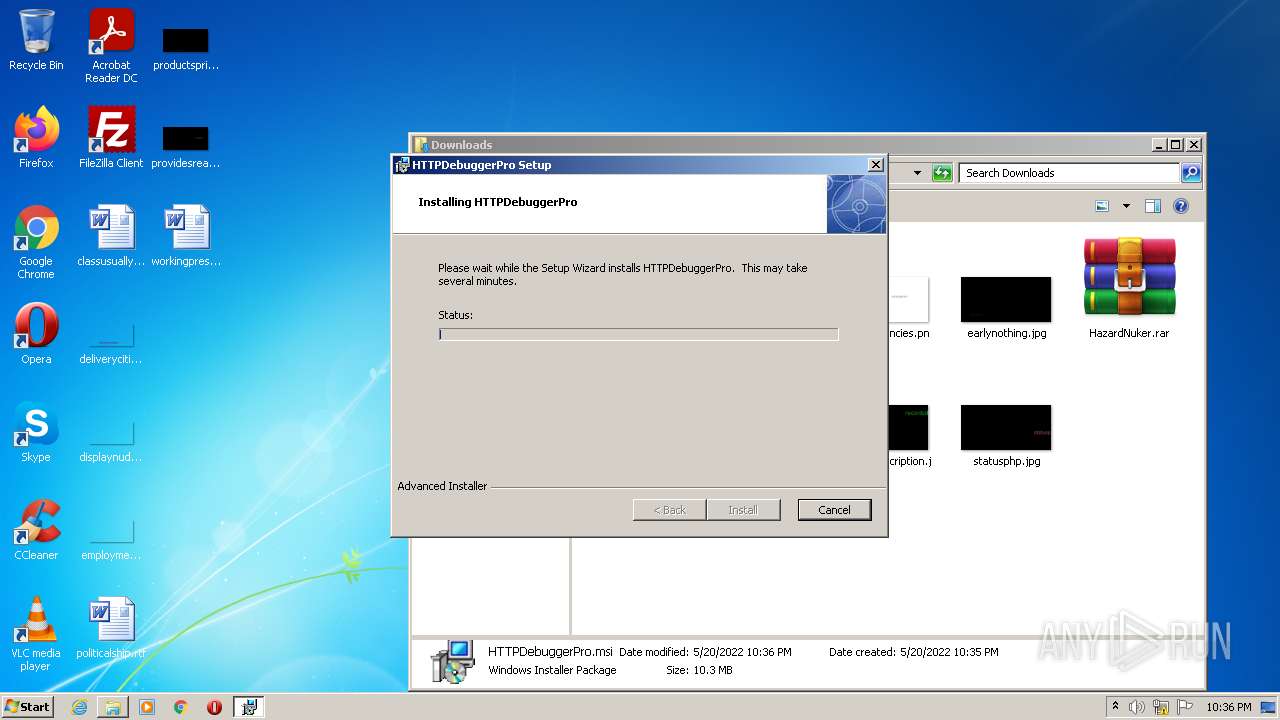
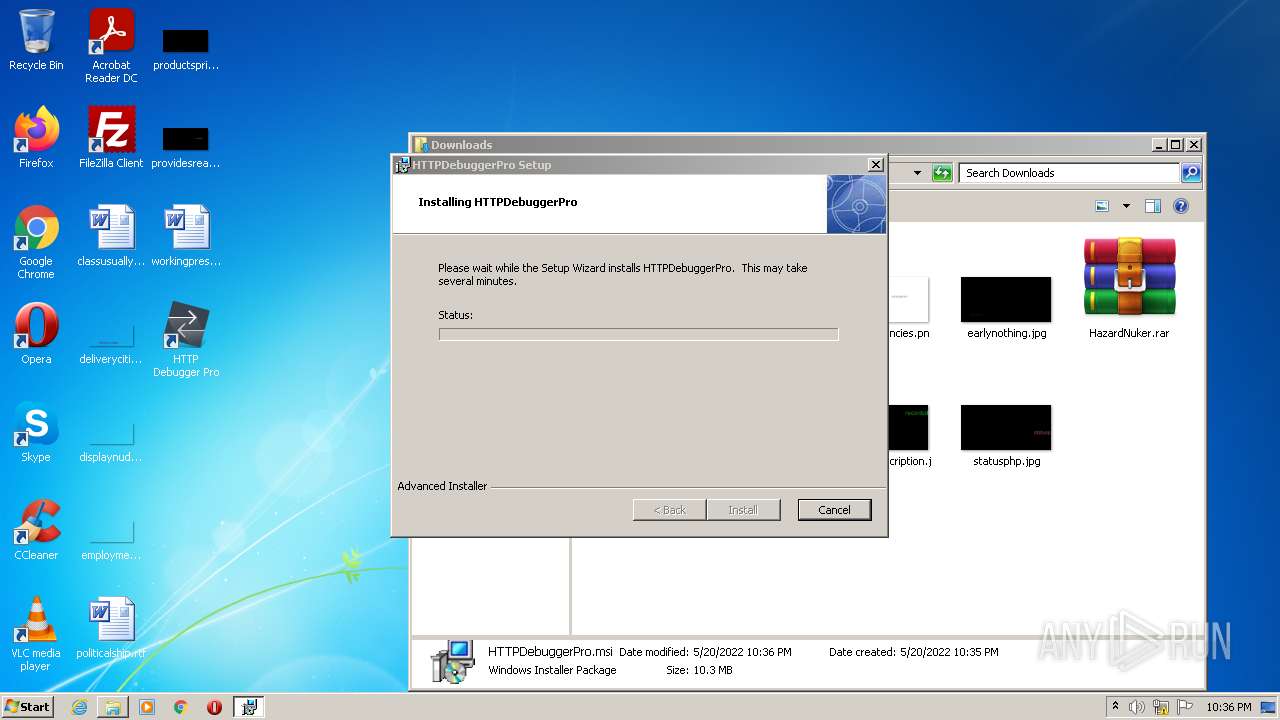
| URL: | https://cdn.discordapp.com/attachments/951802854165864448/976065781680971796/HazardNuker.rar |
| Full analysis: | https://app.any.run/tasks/37a8184a-6255-45d1-8579-c32e18a8ff99 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 20, 2022, 21:35:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | AB0E7AA5B21F25A27CCF3B2642DC79B9 |
| SHA1: | 92ECDEA5A5D5F4BBA178F96B497E1FC7825EC6BB |
| SHA256: | D5F6003E222C149816A9D18F1063ABF4D74347CA24C99CEA486F049CB3E58F90 |
| SSDEEP: | 3:N8cCWdy6//hE9ipT3OcGHdUzocka:2cry6XhE8pildUV |
MALICIOUS
Drops executable file immediately after starts
- msiexec.exe (PID: 968)
- msiexec.exe (PID: 288)
- HTTPDebuggerSvc.exe (PID: 3720)
- HazardNuker.exe (PID: 3752)
- Qasim_Haxor.exe (PID: 772)
Loads dropped or rewritten executable
- HTTPDebuggerUI.exe (PID: 3568)
- MsiExec.exe (PID: 3524)
- certutil.exe (PID: 2176)
Application was dropped or rewritten from another process
- HTTPDebuggerUI.exe (PID: 3568)
- HTTPDebuggerSvc.exe (PID: 2800)
- HTTPDebuggerSvc.exe (PID: 3720)
- certutil.exe (PID: 2176)
- AsyncClient.exe (PID: 2664)
- Qasim_Haxor.exe (PID: 772)
Changes settings of System certificates
- HTTPDebuggerSvc.exe (PID: 3720)
Actions looks like stealing of personal data
- HTTPDebuggerSvc.exe (PID: 3720)
Steals credentials from Web Browsers
- HTTPDebuggerSvc.exe (PID: 3720)
Writes to a start menu file
- Qasim_Haxor.exe (PID: 772)
- WScript.exe (PID: 3972)
ASYNCRAT detected by memory dumps
- AsyncClient.exe (PID: 2664)
- HazardNuker.exe (PID: 684)
Changes the autorun value in the registry
- Qasim_Haxor.exe (PID: 772)
- WScript.exe (PID: 3972)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3216)
Reads the computer name
- msiexec.exe (PID: 288)
- MsiExec.exe (PID: 3848)
- MsiExec.exe (PID: 3280)
- HTTPDebuggerSvc.exe (PID: 3720)
- HTTPDebuggerSvc.exe (PID: 2800)
- HTTPDebuggerUI.exe (PID: 3568)
- WinRAR.exe (PID: 1868)
- certutil.exe (PID: 2176)
- HazardNuker.exe (PID: 3752)
- AsyncClient.exe (PID: 2664)
- WScript.exe (PID: 3972)
- Qasim_Haxor.exe (PID: 772)
- HazardNuker.exe (PID: 684)
Checks supported languages
- msiexec.exe (PID: 288)
- MsiExec.exe (PID: 3848)
- MsiExec.exe (PID: 3280)
- HTTPDebuggerSvc.exe (PID: 3720)
- HTTPDebuggerSvc.exe (PID: 2800)
- HTTPDebuggerUI.exe (PID: 3568)
- certutil.exe (PID: 2176)
- WScript.exe (PID: 3972)
- WinRAR.exe (PID: 1868)
- HazardNuker.exe (PID: 3752)
- Qasim_Haxor.exe (PID: 772)
- AsyncClient.exe (PID: 2664)
- HazardNuker.exe (PID: 684)
Reads Windows owner or organization settings
- msiexec.exe (PID: 968)
- msiexec.exe (PID: 288)
Reads the Windows organization settings
- msiexec.exe (PID: 968)
- msiexec.exe (PID: 288)
Executed as Windows Service
- vssvc.exe (PID: 2160)
- HTTPDebuggerSvc.exe (PID: 3720)
Drops a file with a compile date too recent
- msiexec.exe (PID: 968)
- msiexec.exe (PID: 288)
- HTTPDebuggerSvc.exe (PID: 3720)
- HazardNuker.exe (PID: 3752)
- Qasim_Haxor.exe (PID: 772)
Executable content was dropped or overwritten
- msiexec.exe (PID: 968)
- msiexec.exe (PID: 288)
- HTTPDebuggerSvc.exe (PID: 3720)
- HazardNuker.exe (PID: 3752)
- Qasim_Haxor.exe (PID: 772)
Creates a directory in Program Files
- msiexec.exe (PID: 288)
Creates/Modifies COM task schedule object
- MsiExec.exe (PID: 3524)
Reads Environment values
- vssvc.exe (PID: 2160)
- HTTPDebuggerSvc.exe (PID: 2800)
- HTTPDebuggerSvc.exe (PID: 3720)
- netsh.exe (PID: 3540)
- Qasim_Haxor.exe (PID: 772)
Creates files in the program directory
- HTTPDebuggerSvc.exe (PID: 3720)
Creates files in the driver directory
- HTTPDebuggerSvc.exe (PID: 3720)
Creates files in the Windows directory
- HTTPDebuggerSvc.exe (PID: 3720)
Creates or modifies windows services
- HTTPDebuggerSvc.exe (PID: 3720)
Reads Microsoft Outlook installation path
- HTTPDebuggerUI.exe (PID: 3568)
Reads internet explorer settings
- HTTPDebuggerUI.exe (PID: 3568)
Executes scripts
- HazardNuker.exe (PID: 3752)
Uses NETSH.EXE for network configuration
- Qasim_Haxor.exe (PID: 772)
Creates files in the user directory
- Qasim_Haxor.exe (PID: 772)
- WScript.exe (PID: 3972)
INFO
Checks supported languages
- chrome.exe (PID: 3216)
- chrome.exe (PID: 3072)
- chrome.exe (PID: 1384)
- chrome.exe (PID: 3244)
- chrome.exe (PID: 2216)
- chrome.exe (PID: 1400)
- chrome.exe (PID: 3520)
- chrome.exe (PID: 3876)
- chrome.exe (PID: 3584)
- chrome.exe (PID: 2364)
- chrome.exe (PID: 2132)
- chrome.exe (PID: 3040)
- chrome.exe (PID: 2716)
- chrome.exe (PID: 3616)
- chrome.exe (PID: 3148)
- chrome.exe (PID: 1148)
- chrome.exe (PID: 3244)
- chrome.exe (PID: 2996)
- chrome.exe (PID: 3136)
- chrome.exe (PID: 2136)
- msiexec.exe (PID: 968)
- chrome.exe (PID: 3052)
- MsiExec.exe (PID: 3524)
- vssvc.exe (PID: 2160)
- taskmgr.exe (PID: 1972)
- netsh.exe (PID: 3540)
Application launched itself
- chrome.exe (PID: 3216)
- msiexec.exe (PID: 288)
Reads the computer name
- chrome.exe (PID: 1384)
- chrome.exe (PID: 3520)
- chrome.exe (PID: 3584)
- chrome.exe (PID: 1400)
- chrome.exe (PID: 3216)
- chrome.exe (PID: 3244)
- chrome.exe (PID: 2996)
- chrome.exe (PID: 3148)
- chrome.exe (PID: 2136)
- msiexec.exe (PID: 968)
- vssvc.exe (PID: 2160)
- netsh.exe (PID: 3540)
- taskmgr.exe (PID: 1972)
Reads the hosts file
- chrome.exe (PID: 3520)
- chrome.exe (PID: 3216)
Reads settings of System Certificates
- chrome.exe (PID: 3520)
- chrome.exe (PID: 3216)
- msiexec.exe (PID: 968)
- msiexec.exe (PID: 288)
- HTTPDebuggerSvc.exe (PID: 3720)
- HTTPDebuggerUI.exe (PID: 3568)
Checks Windows Trust Settings
- chrome.exe (PID: 3216)
- msiexec.exe (PID: 968)
- msiexec.exe (PID: 288)
- HTTPDebuggerUI.exe (PID: 3568)
- WScript.exe (PID: 3972)
Reads the date of Windows installation
- chrome.exe (PID: 2136)
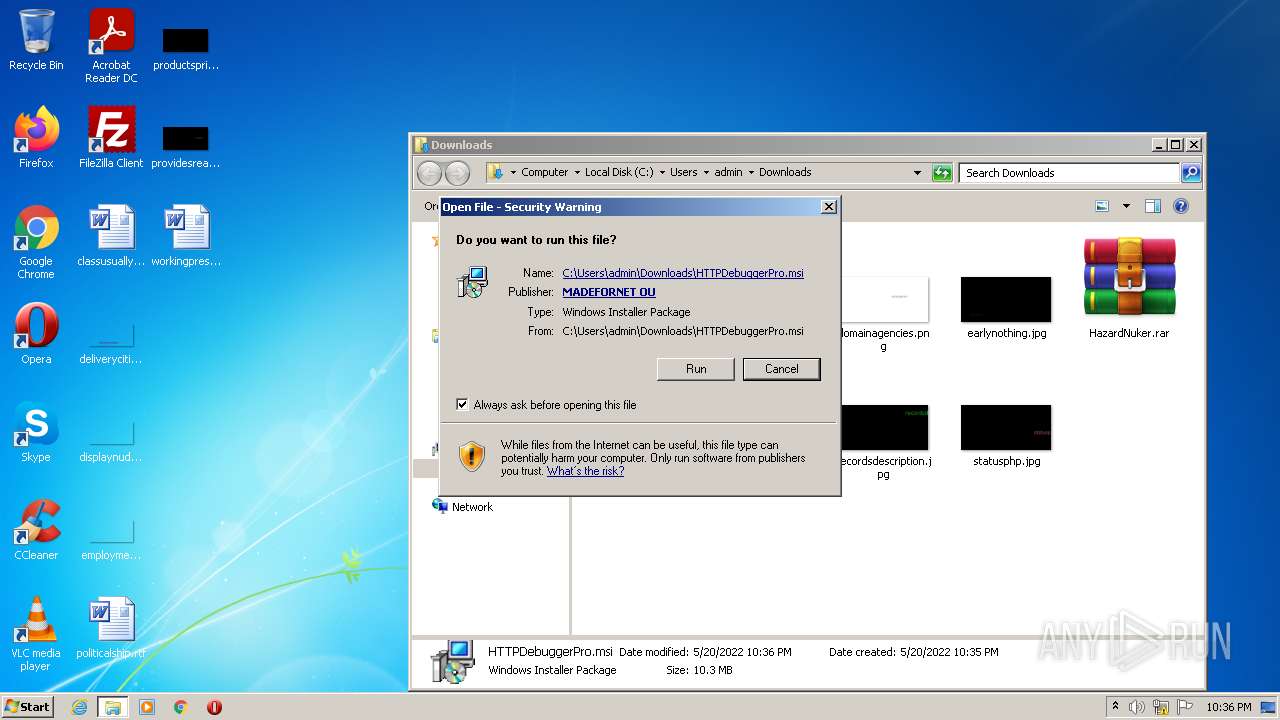
Manual execution by user
- msiexec.exe (PID: 968)
- WinRAR.exe (PID: 1868)
- HazardNuker.exe (PID: 3752)
- taskmgr.exe (PID: 1972)
- HazardNuker.exe (PID: 684)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3848)
- MsiExec.exe (PID: 3280)
Creates files in the program directory
- msiexec.exe (PID: 288)
Creates a software uninstall entry
- msiexec.exe (PID: 288)
Searches for installed software
- msiexec.exe (PID: 288)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(2664) AsyncClient.exe
C2 (1)zzzpmax.ddns.net
Ports (1)6666
Version0.5.7B
Autorunfalse
MutexAsyncMutex_6SI8OkPnk
CertificateMIIE8jCCAtqgAwIBAgIQAOCB0uFeWGNTR7e/rDPz5zANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI2MjAyNzUzWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAO2Ia0ENoTR7yQenNsmu24HqrIvYhHV/uQJicLwOPkf6pOO8zTzcA4J1RqsrKyISi6nQ6V1xfrud...
Server_SignatureKFDm7Mf3iCC4t3rZYlvFrxCZ/OPQM2G+OeLOudzvwR2Q/lmBozM/KEKQYJa/aGGzhHFJ7sL1pErUpi5QU6W8mwXp3g2Up1RTZtF3IMFvabB8Khw/6NWQ2soQ3GpXUzLz9ecNRzW6lxGmilEgl1LboTfTq4DX2GGCsndsZA6fK2MtLYK597Mewik3z82Z+1hXIvUgdQPLOcJwrsgfVwX7bL/S7w1QyVnPDZNpMNoYkno3blgQY5xqEh7osp7//ypRWxy4vruxonU2Td3t3B5Vux6sxbaX0xEP1sx0qG5mfIcj...
AntiVMfalse
PasteBinnull
bdosfalse
BotnetDefault
Aes_Keyf39cd55440e69989c78340677bd005b757d2c79c4305f9d5af651acb4f13b0ec
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Install_Folder%AppData%
Total processes
83
Monitored processes
39
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | "C:\Users\admin\Downloads\HazardNuker\HazardNuker.exe" | C:\Users\admin\Downloads\HazardNuker\HazardNuker.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 772 | "C:\Users\admin\AppData\Local\Temp\Qasim_Haxor.exe" | C:\Users\admin\AppData\Local\Temp\Qasim_Haxor.exe | HazardNuker.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 968 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Downloads\HTTPDebuggerPro.msi" | C:\Windows\System32\msiexec.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1148 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,15463952557316075695,3952015374093675289,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2640 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1384 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1036,15463952557316075695,3952015374093675289,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgACAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1056 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1036,15463952557316075695,3952015374093675289,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3268 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1868 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\HazardNuker.rar" C:\Users\admin\Downloads\ | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1972 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,15463952557316075695,3952015374093675289,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1872 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
33 742
Read events
32 974
Write events
754
Delete events
14
Modification events
| (PID) Process: | (3216) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3216) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3216) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3216) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3216) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3216) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3216) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3216) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3216) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (3216) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
33
Suspicious files
50
Text files
109
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-6288099A-C90.pma | — | |
MD5:— | SHA256:— | |||
| 3072 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 3216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\b600ce11-2784-4419-a1e1-053293ca0ab7.tmp | text | |
MD5:— | SHA256:— | |||
| 3216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 3216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF104b63.TMP | text | |
MD5:81F483F77EE490F35306A4F94DB2286B | SHA256:82434CE3C9D13F509EBEEBE3A7A1A1DE9AB4557629D9FC855761E0CFA45E8BCE | |||
| 3216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\6851ba61-4464-4cd1-bb48-37c6ee5c8c5a.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF104b43.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
| 3216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:7721CDA9F5B73CE8A135471EB53B4E0E | SHA256:DD730C576766A46FFC84E682123248ECE1FF1887EC0ACAB22A5CE93A450F4500 | |||
| 3216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old~RF104cca.TMP | text | |
MD5:109A25C32EE1132ECD6D9F3ED9ADF01A | SHA256:DA6028DB9485C65E683643658326F02B1D0A1566DE14914EF28E5248EB94F0DD | |||
| 3216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | text | |
MD5:EF1D5606A483BB6C72C81A3F649BEB18 | SHA256:BA083E7585ADA9936944FE56BC0141A544F18A01C3424E5C9F02375B34FE3D45 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
61
DNS requests
30
Threats
4
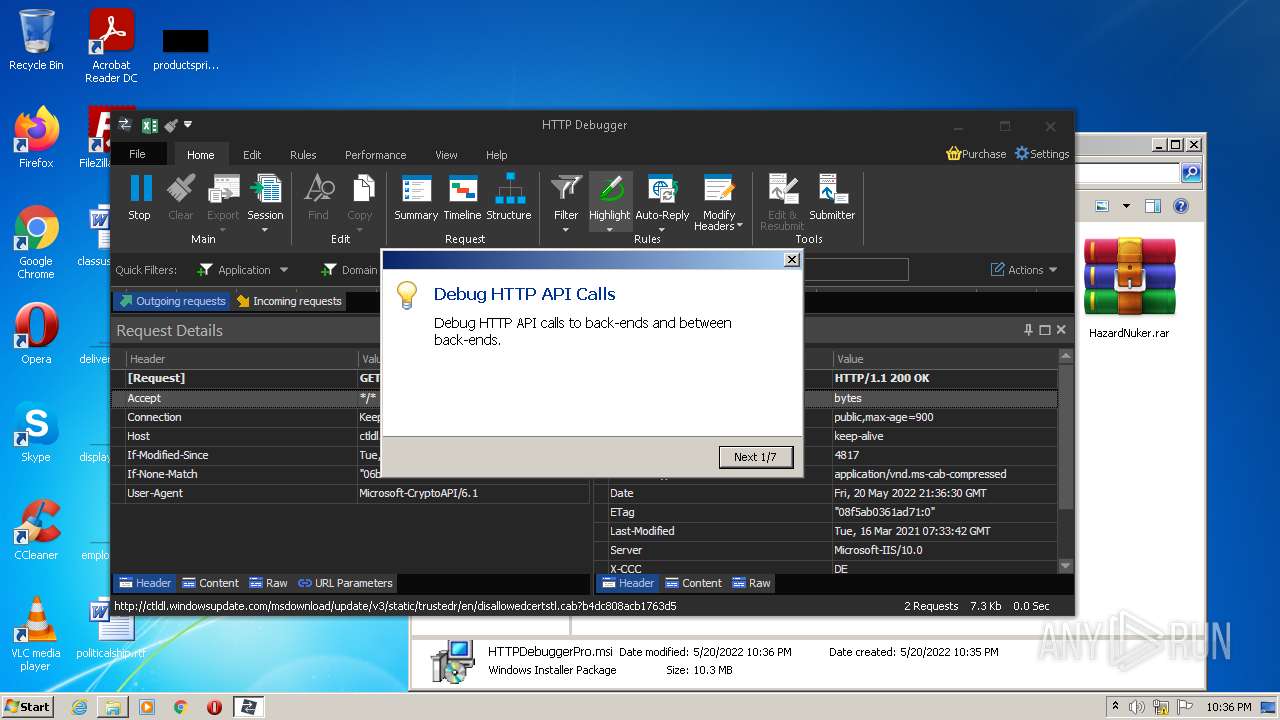
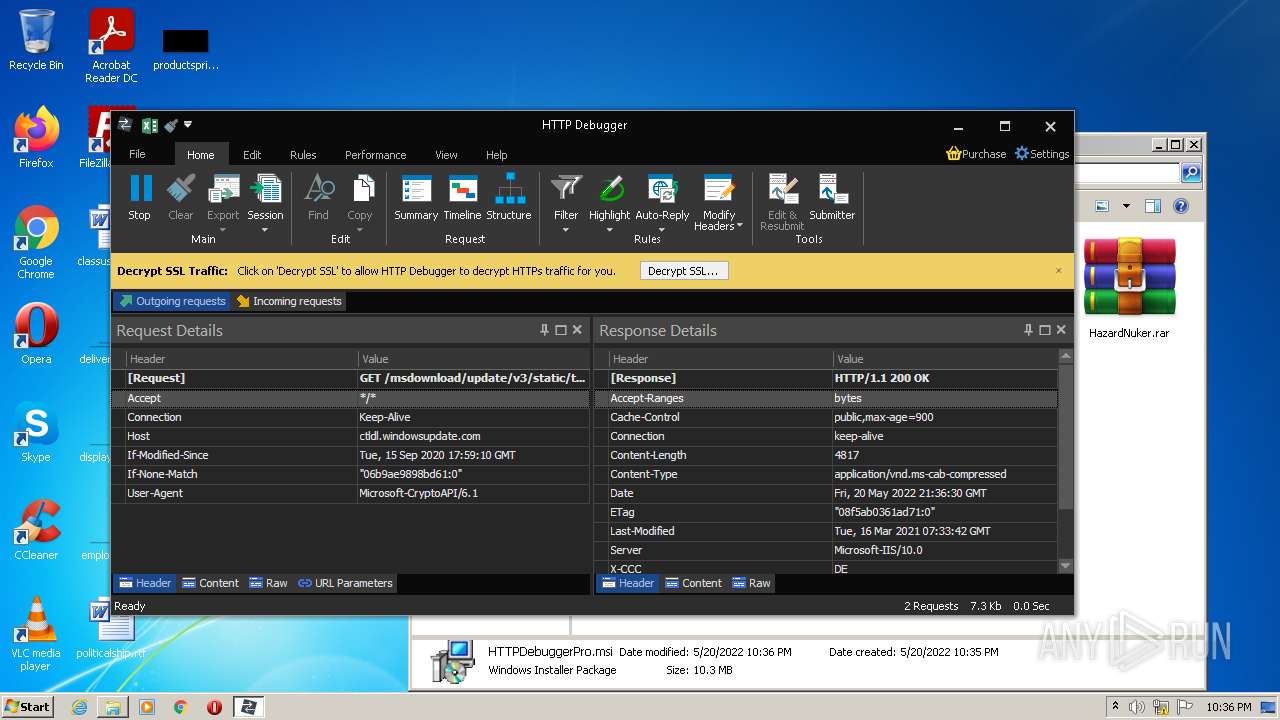
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3568 | HTTPDebuggerUI.exe | GET | 200 | 92.123.195.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b4dc808acb1763d5 | unknown | compressed | 4.70 Kb | whitelisted |
3568 | HTTPDebuggerUI.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3520 | chrome.exe | 142.250.184.195:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3520 | chrome.exe | 142.250.185.164:443 | www.google.com | Google Inc. | US | whitelisted |
3520 | chrome.exe | 142.250.185.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
3520 | chrome.exe | 142.250.186.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3520 | chrome.exe | 188.114.96.10:443 | www.httpdebugger.com | Cloudflare Inc | US | malicious |
3520 | chrome.exe | 142.250.185.142:443 | consent.google.pl | Google Inc. | US | whitelisted |
3520 | chrome.exe | 142.250.185.72:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3520 | chrome.exe | 142.250.186.138:443 | content-autofill.googleapis.com | Google Inc. | US | whitelisted |
3520 | chrome.exe | 52.222.206.6:443 | cdn.amplitude.com | Amazon.com, Inc. | US | suspicious |
3520 | chrome.exe | 142.250.185.238:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
cdn.discordapp.com |
| shared |
clients2.google.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.google.com |
| malicious |
www.gstatic.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.httpdebugger.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3520 | chrome.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
3520 | chrome.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |