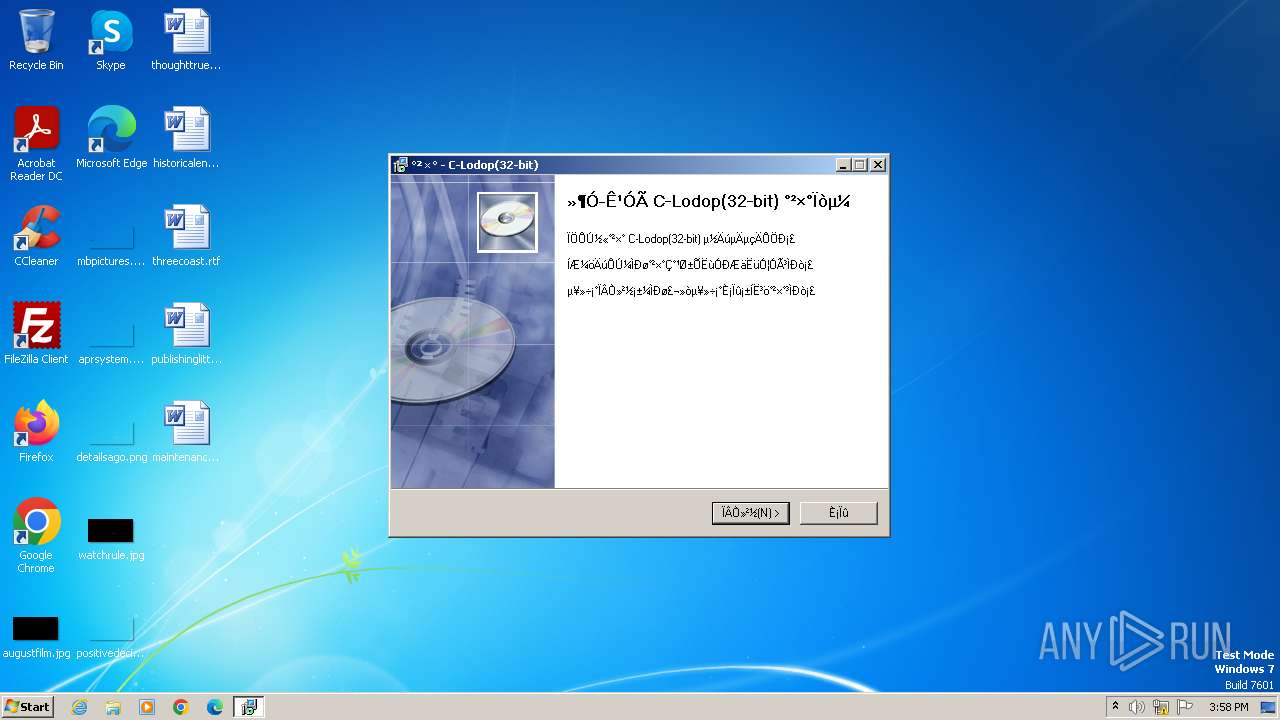
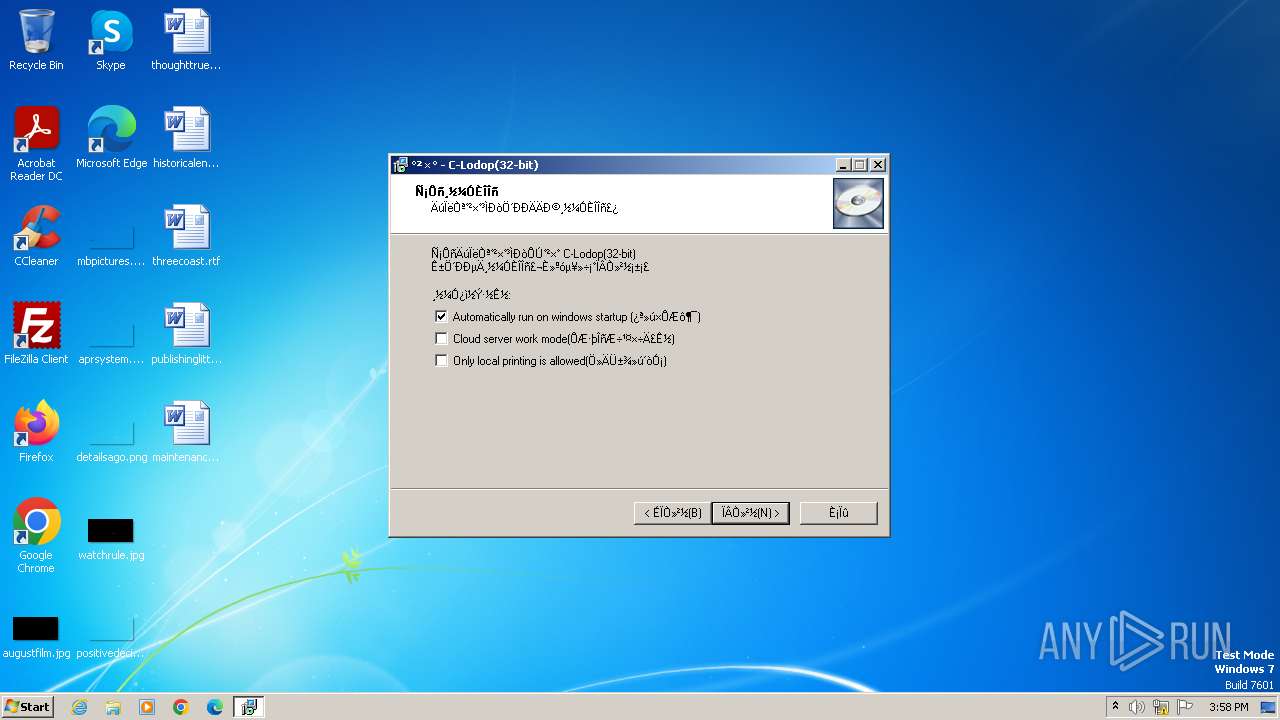
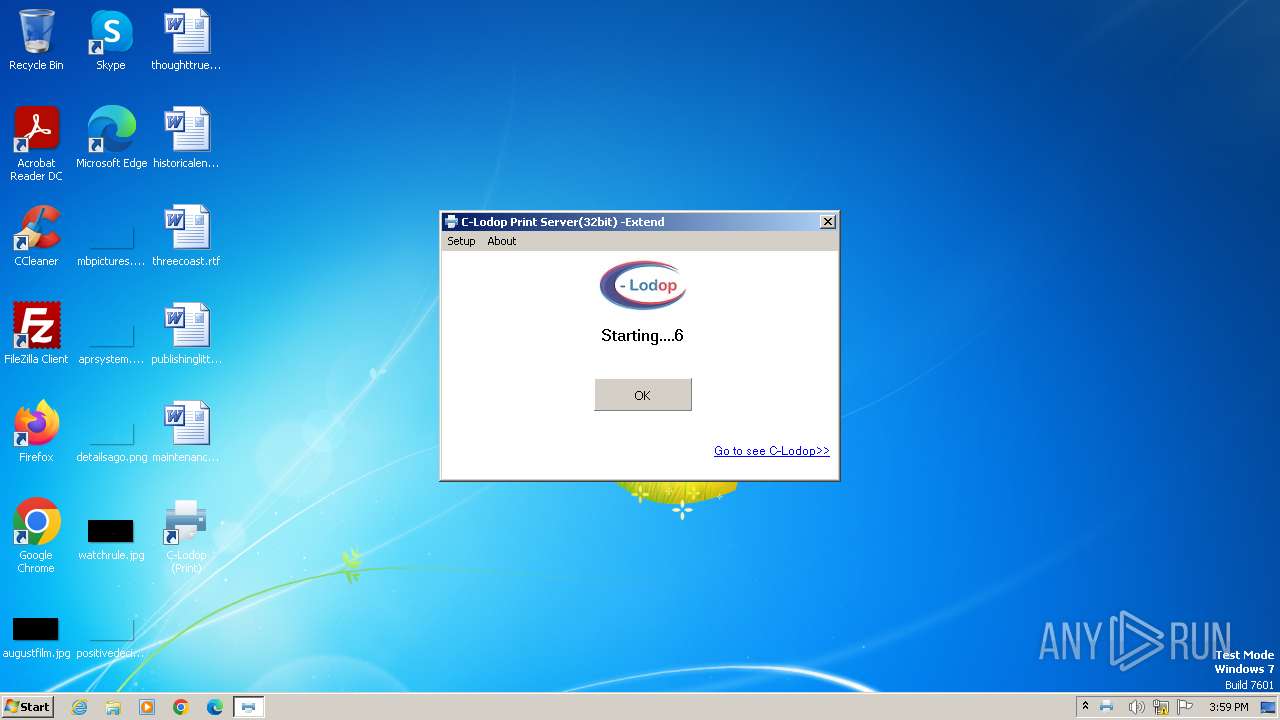
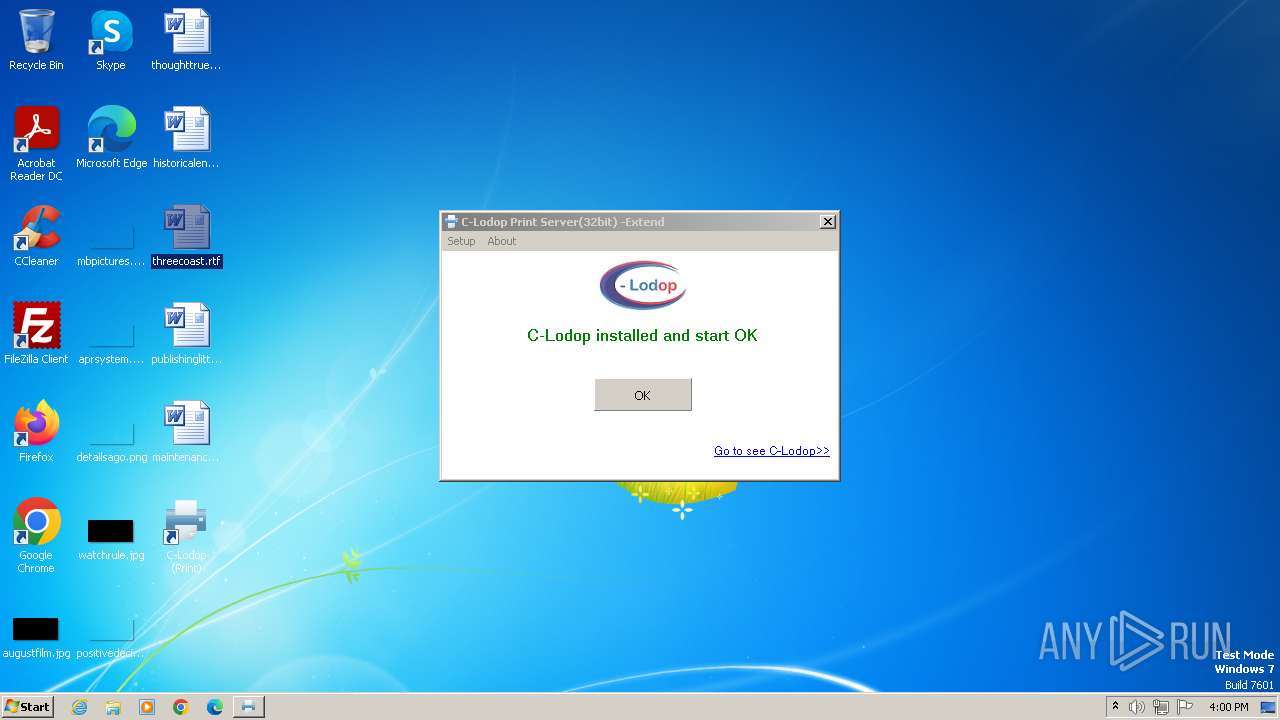
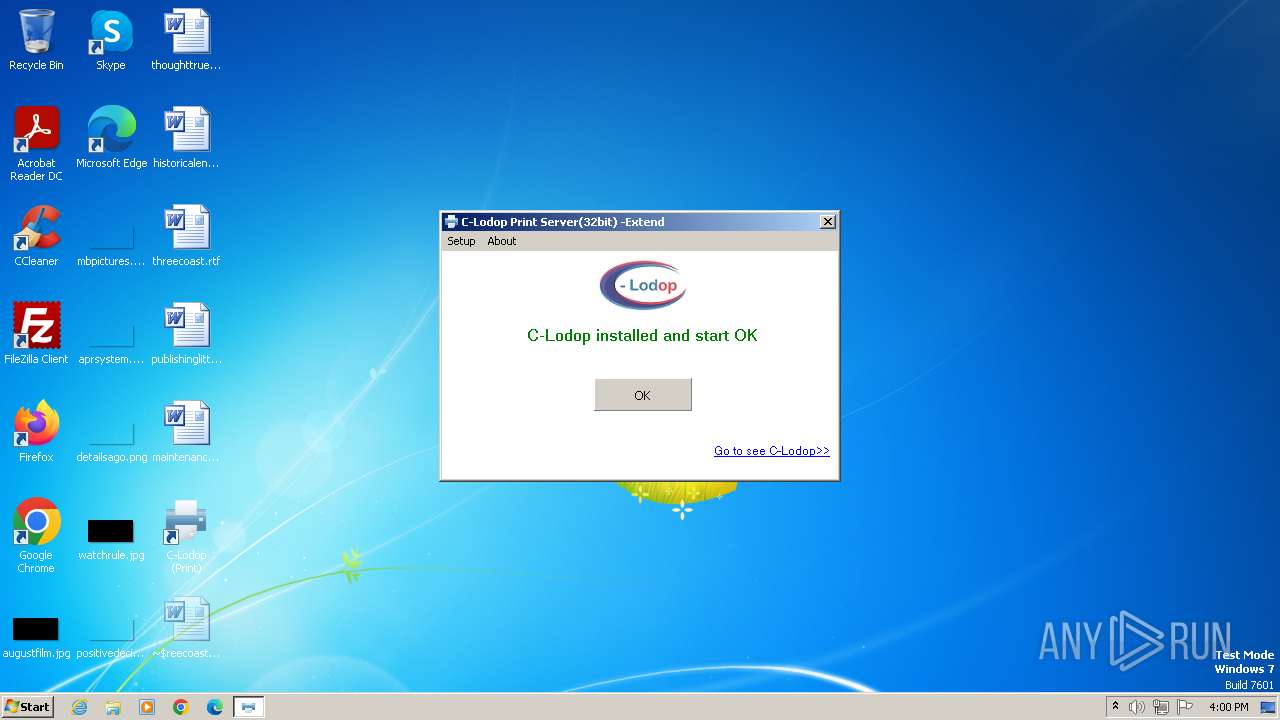
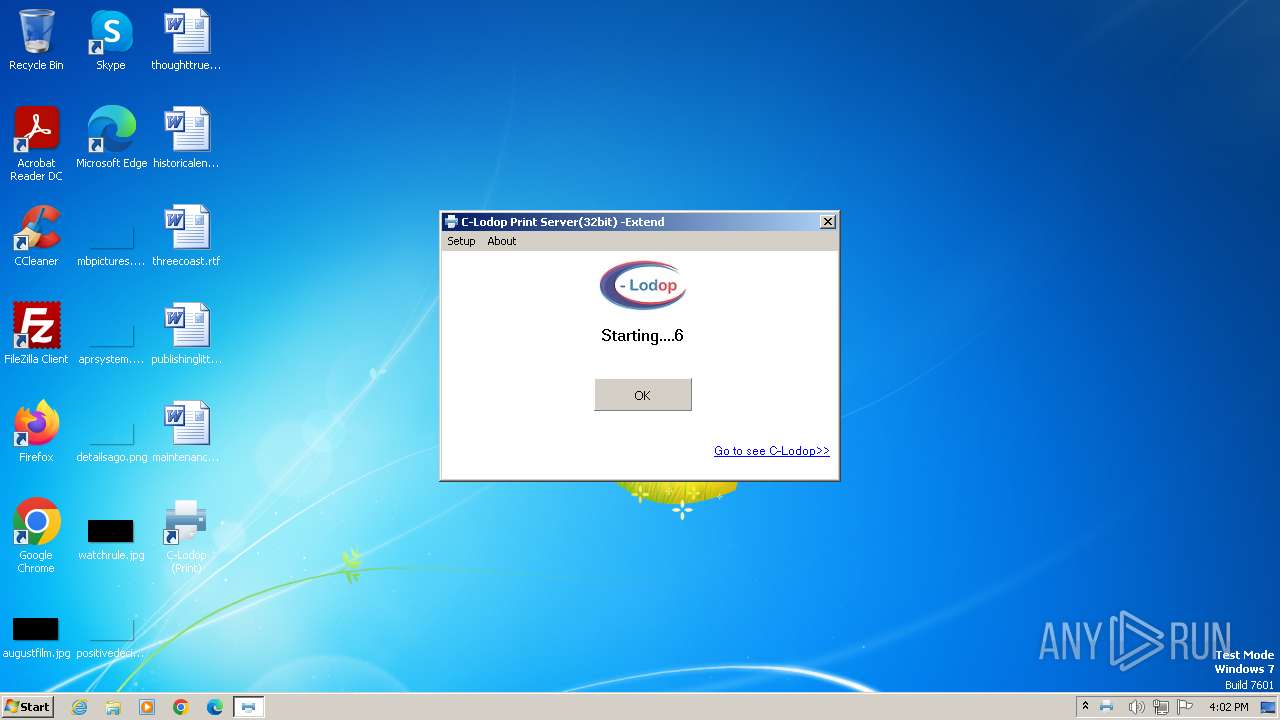
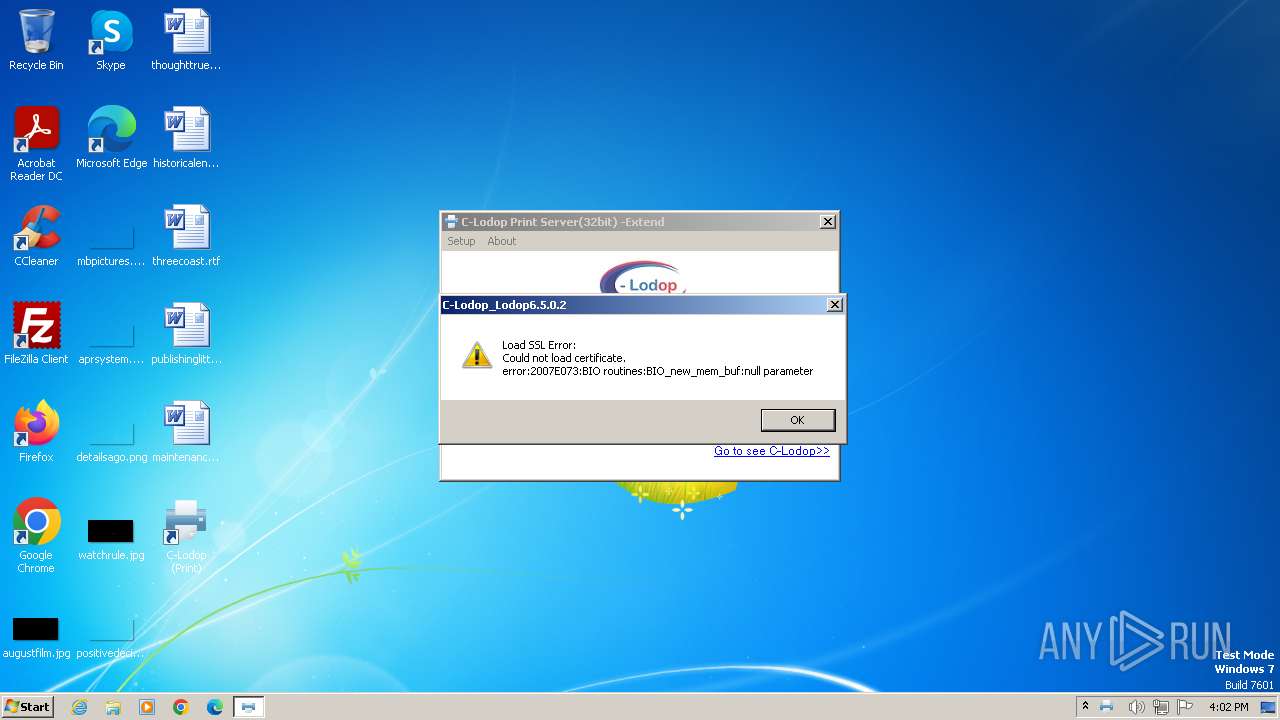
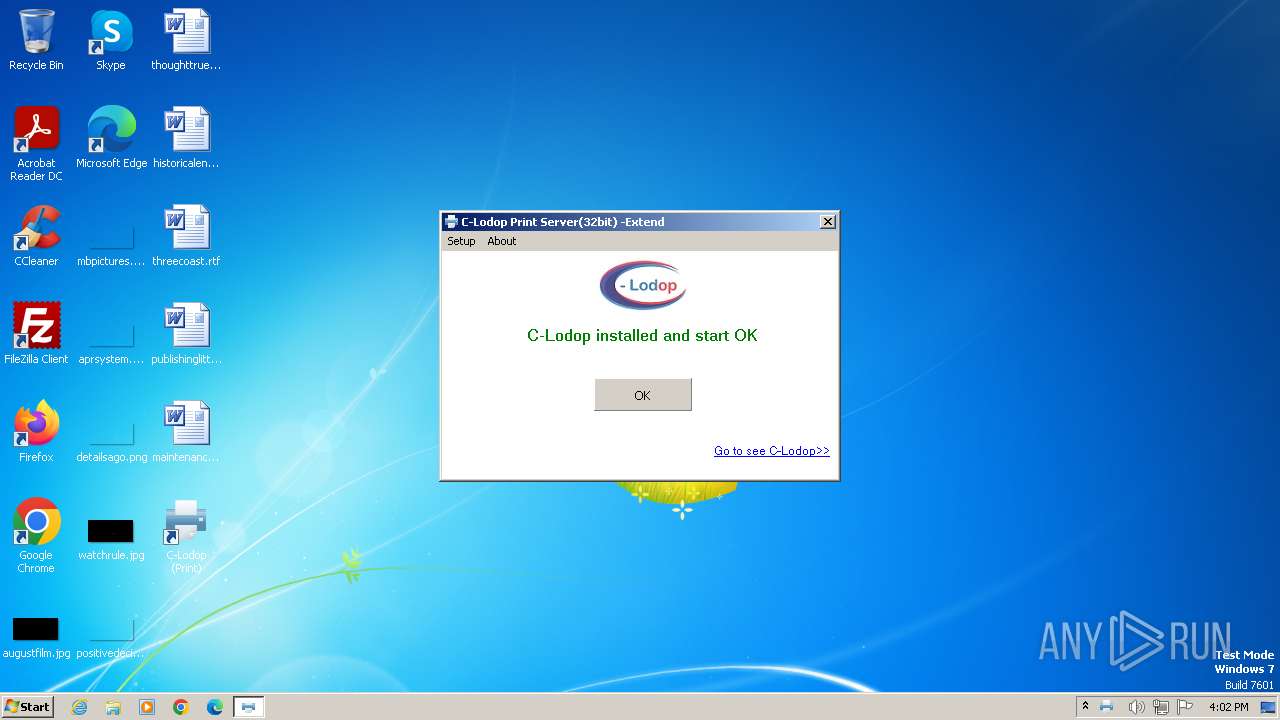
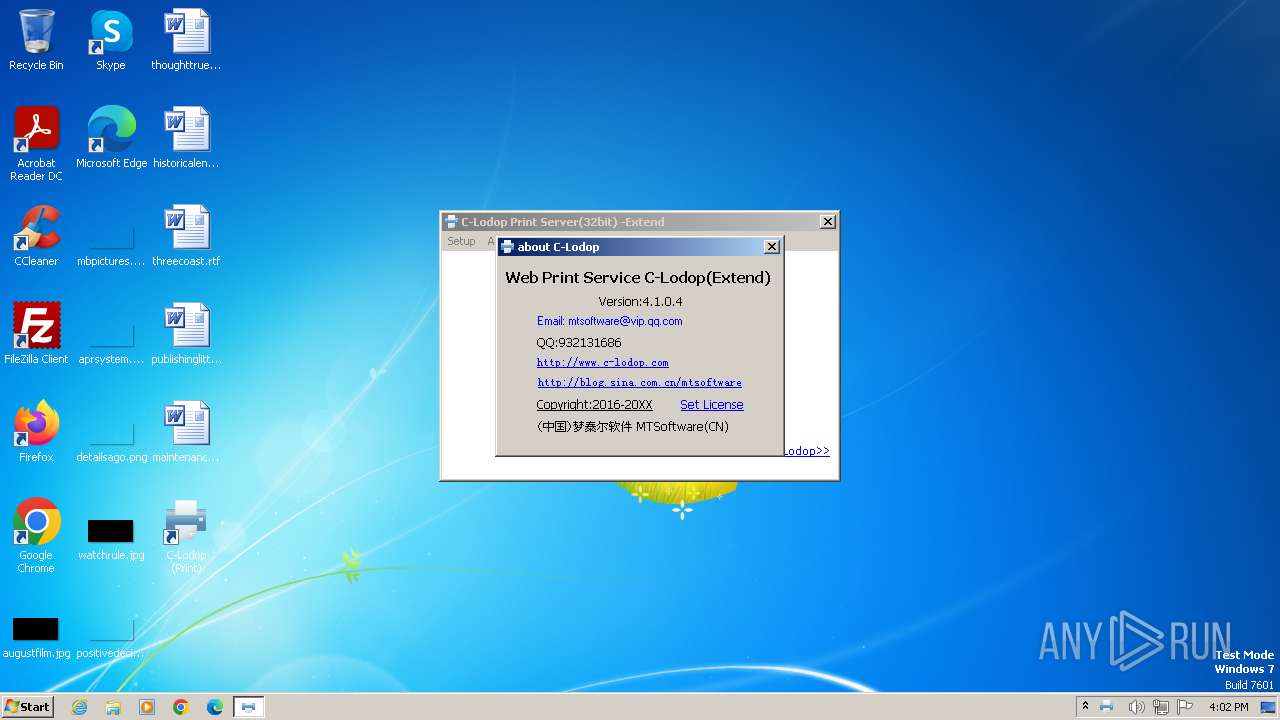
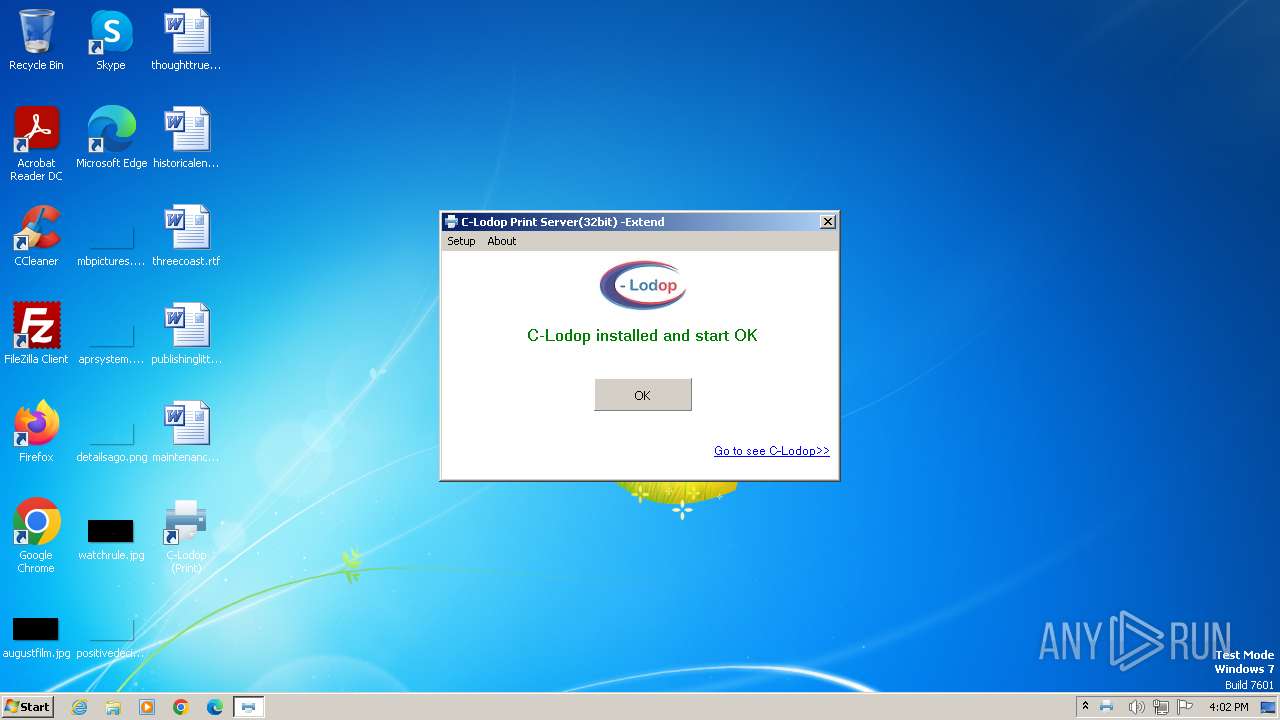
| File name: | CLodop_Setup_for_Win32NT_4.102.exe |
| Full analysis: | https://app.any.run/tasks/7b1ae710-8b84-45c9-bda3-6c49a160490a |
| Verdict: | Malicious activity |
| Threats: | Metamorfo is a trojan malware family that has been active since 2018. It remains a top threat, focusing on stealing victims’ financial information, including banking credentials and other data. The malware is known for targeting users in Brazil. |
| Analysis date: | December 05, 2023, 15:58:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A05746DDB5E9034297CDF60A093F5E60 |
| SHA1: | 531C8A60AF53249570925AC45BAA0D6B5B4BEC4D |
| SHA256: | D5C0CF0953687C85629E6451E00B0A0CC17549894B365795921301A44FC2FF76 |
| SSDEEP: | 98304:BCKHdWhqxR/sezSNh/aopjkZglcczIdMH4kGHGnYBTrYqPC:eEYe+NgoHlcc02Y/SMTVC |
MALICIOUS
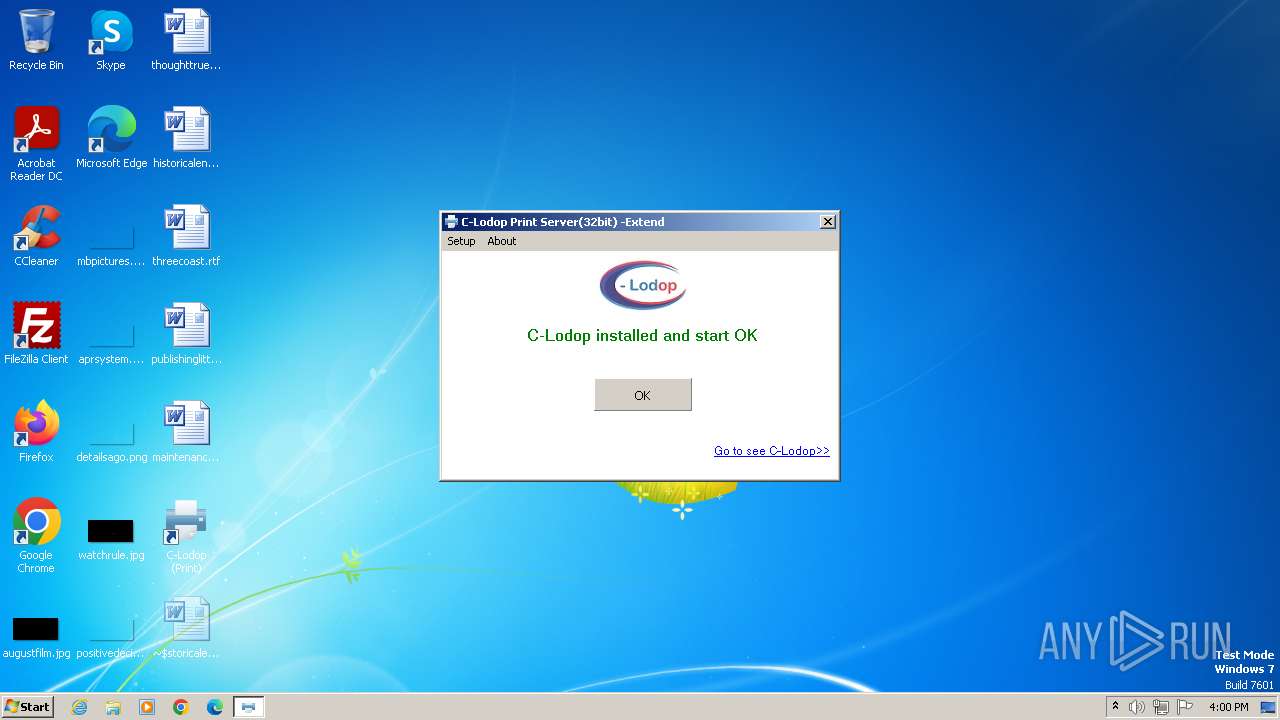
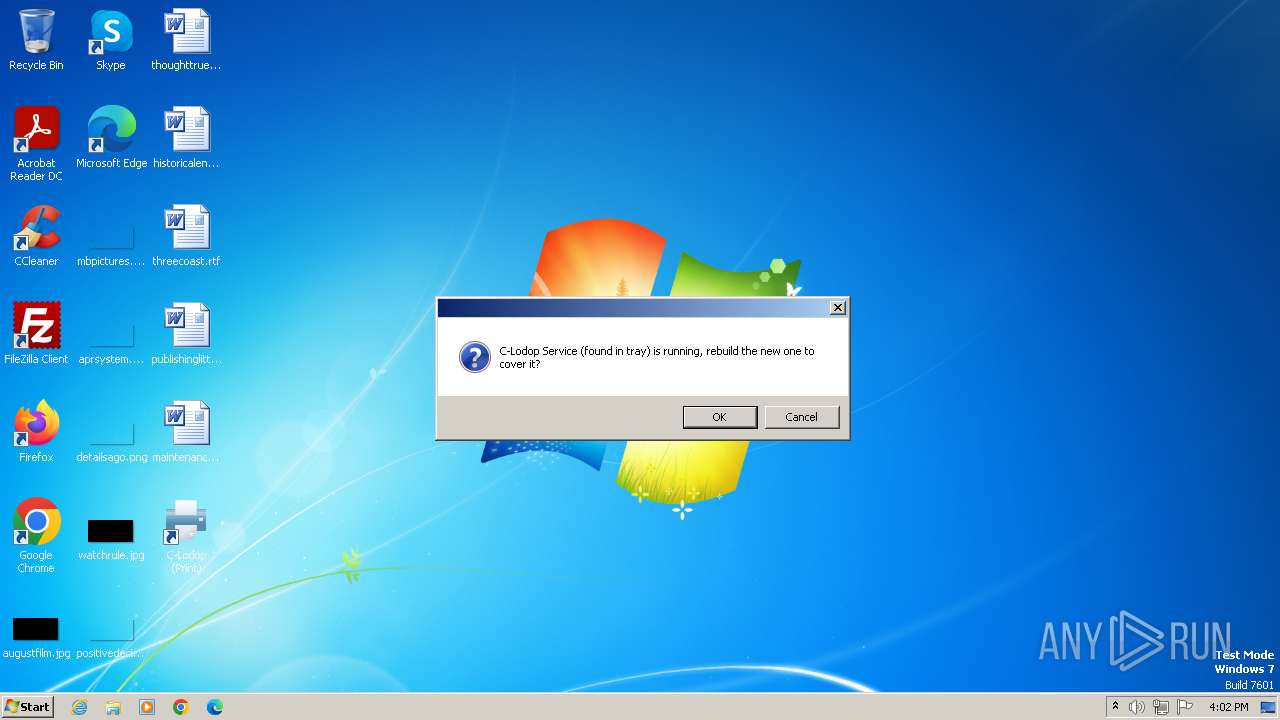
Drops the executable file immediately after the start
- CLodop_Setup_for_Win32NT_4.102.exe (PID: 2780)
- is-VKN0P.tmp (PID: 2628)
- CLodopPrint32.exe (PID: 2076)
METAMORFO has been detected (YARA)
- CLodopPrint32.exe (PID: 2076)
- CLodopPrint32_backup.exe (PID: 3996)
- CLodopPrint32_backup.exe (PID: 1936)
- CLodopPrint32.exe (PID: 4032)
SUSPICIOUS
Process drops legitimate windows executable
- is-VKN0P.tmp (PID: 2628)
The process drops C-runtime libraries
- is-VKN0P.tmp (PID: 2628)
Reads the Windows owner or organization settings
- is-VKN0P.tmp (PID: 2628)
Reads the Internet Settings
- CLodopPrint32.exe (PID: 2076)
- CLodopPrint32.exe (PID: 4032)
Executes as Windows Service
- CLodopService32.exe (PID: 2532)
Starts itself from another location
- CLodopPrint32.exe (PID: 2076)
- CLodopPrint32.exe (PID: 4032)
Changes Internet Explorer settings (feature browser emulation)
- CLodopPrint32.exe (PID: 4032)
INFO
Checks supported languages
- is-VKN0P.tmp (PID: 2628)
- CLodop_Setup_for_Win32NT_4.102.exe (PID: 2780)
- CLodopPrint32.exe (PID: 2076)
- CLodopService32.exe (PID: 1560)
- CLodopPrint32_backup.exe (PID: 3996)
- wmpnscfg.exe (PID: 1860)
- CLodopPrint32.exe (PID: 4032)
- CLodopService32.exe (PID: 2532)
- CLodopPrint32_backup.exe (PID: 1936)
Create files in a temporary directory
- CLodop_Setup_for_Win32NT_4.102.exe (PID: 2780)
- is-VKN0P.tmp (PID: 2628)
- CLodopPrint32.exe (PID: 2076)
Reads the computer name
- is-VKN0P.tmp (PID: 2628)
- CLodopPrint32.exe (PID: 2076)
- CLodopService32.exe (PID: 1560)
- CLodopService32.exe (PID: 2532)
- wmpnscfg.exe (PID: 1860)
- CLodopPrint32_backup.exe (PID: 3996)
- CLodopPrint32.exe (PID: 4032)
- CLodopPrint32_backup.exe (PID: 1936)
Creates files in the program directory
- is-VKN0P.tmp (PID: 2628)
- CLodopPrint32.exe (PID: 2076)
Manual execution by a user
- wmpnscfg.exe (PID: 1860)
- WINWORD.EXE (PID: 3560)
- WINWORD.EXE (PID: 1296)
- CLodopPrint32.exe (PID: 4032)
- WINWORD.EXE (PID: 3380)
Reads the machine GUID from the registry
- CLodopPrint32.exe (PID: 2076)
- CLodopPrint32.exe (PID: 4032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 36864 |
| InitializedDataSize: | 15872 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x97f8 |
| OSVersion: | 1 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.1.0.4 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | ASCII |
| Comments: | 此安装程序由 Inno Setup 构建。 |
| CompanyName: | MTSoftware(CN) |
| FileDescription: | C-Lodop(32-bit) Setup |
| FileVersion: | 4.1.0.4 |
| LegalCopyright: |
Total processes
63
Monitored processes
16
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1296 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\threecoast.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1560 | "C:\Program Files\MountTaiSoftware\CLodop32\CLodopService32.exe" -INSTALL -SILENT | C:\Program Files\MountTaiSoftware\CLodop32\CLodopService32.exe | — | CLodopPrint32.exe | |||||||||||
User: admin Company: (中国)梦泰尔软件 MTSoftware(CN) Integrity Level: HIGH Description: C-Lodop 云打印“免登录”启动服务 Exit code: 0 Version: 3.0.0.5 Modules
| |||||||||||||||
| 1616 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1860 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1936 | "C:\Program Files\MountTaiSoftware\CLodop32\CLodopPrint32_backup.exe" | C:\Program Files\MountTaiSoftware\CLodop32\CLodopPrint32_backup.exe | CLodopPrint32.exe | ||||||||||||
User: admin Company: (中国)梦泰尔软件 MTSoftware(CN) Integrity Level: MEDIUM Description: Web打印服务C-Lodop Exit code: 0 Version: 4.1.0.4 Modules
| |||||||||||||||
| 2004 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2076 | "C:\Program Files\MountTaiSoftware\CLodop32\CLodopPrint32.exe" setup_noauto | C:\Program Files\MountTaiSoftware\CLodop32\CLodopPrint32.exe | is-VKN0P.tmp | ||||||||||||
User: admin Company: (中国)梦泰尔软件 MTSoftware(CN) Integrity Level: HIGH Description: Web打印服务C-Lodop Exit code: 0 Version: 4.1.0.4 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\MountTaiSoftware\CLodop32\CLodopPrint32_backup.exe" | C:\Program Files\MountTaiSoftware\CLodop32\CLodopPrint32_backup.exe | — | CLodopPrint32.exe | |||||||||||
User: admin Company: (中国)梦泰尔软件 MTSoftware(CN) Integrity Level: HIGH Description: Web打印服务C-Lodop Exit code: 0 Version: 4.1.0.4 Modules
| |||||||||||||||
| 2532 | "C:\Program Files\MountTaiSoftware\CLodop32\CLodopService32.exe" | C:\Program Files\MountTaiSoftware\CLodop32\CLodopService32.exe | — | services.exe | |||||||||||
User: SYSTEM Company: (中国)梦泰尔软件 MTSoftware(CN) Integrity Level: SYSTEM Description: C-Lodop 云打印“免登录”启动服务 Exit code: 0 Version: 3.0.0.5 Modules
| |||||||||||||||
| 2628 | "C:\Users\admin\AppData\Local\Temp\is-47C1I.tmp\is-VKN0P.tmp" /SL4 $26013A "C:\Users\admin\AppData\Local\Temp\CLodop_Setup_for_Win32NT_4.102.exe" 4302233 51200 | C:\Users\admin\AppData\Local\Temp\is-47C1I.tmp\is-VKN0P.tmp | — | CLodop_Setup_for_Win32NT_4.102.exe | |||||||||||
User: admin Integrity Level: HIGH Description: 安装/卸载 Exit code: 0 Version: 51.46.0.0 Modules
| |||||||||||||||
Total events
8 954
Read events
8 378
Write events
139
Delete events
437
Modification events
| (PID) Process: | (2628) is-VKN0P.tmp | Key: | HKEY_CURRENT_USER\Software\MountTaiSoftware\C-Lodop |
| Operation: | write | Name: | OnlyLocalPrint |
Value: false | |||
| (PID) Process: | (2628) is-VKN0P.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MountTaiSoftware\C-Lodop |
| Operation: | write | Name: | OnlyLocalPrint |
Value: false | |||
| (PID) Process: | (2076) CLodopPrint32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLodop.protocol |
| Operation: | write | Name: | URL Protocol |
Value: | |||
| (PID) Process: | (2076) CLodopPrint32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLodop.protocol\Application |
| Operation: | write | Name: | ApplicationName |
Value: Web打印服务C-Lodop | |||
| (PID) Process: | (2076) CLodopPrint32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLodop.protocol\Application |
| Operation: | write | Name: | ApplicationCompany |
Value: MTSoftware | |||
| (PID) Process: | (2076) CLodopPrint32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLodop.protocol\Application |
| Operation: | write | Name: | ApplicationDescription |
Value: Web打印服务C-Lodop | |||
| (PID) Process: | (2076) CLodopPrint32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLodop.protocol\Application |
| Operation: | write | Name: | ApplicationIcon |
Value: C:\Program Files\MountTaiSoftware\CLodop32\CLodopPrint32.exe,0 | |||
| (PID) Process: | (2076) CLodopPrint32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2076) CLodopPrint32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2076) CLodopPrint32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
20
Suspicious files
26
Text files
128
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2628 | is-VKN0P.tmp | C:\Users\admin\AppData\Local\Temp\is-IM0D7.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
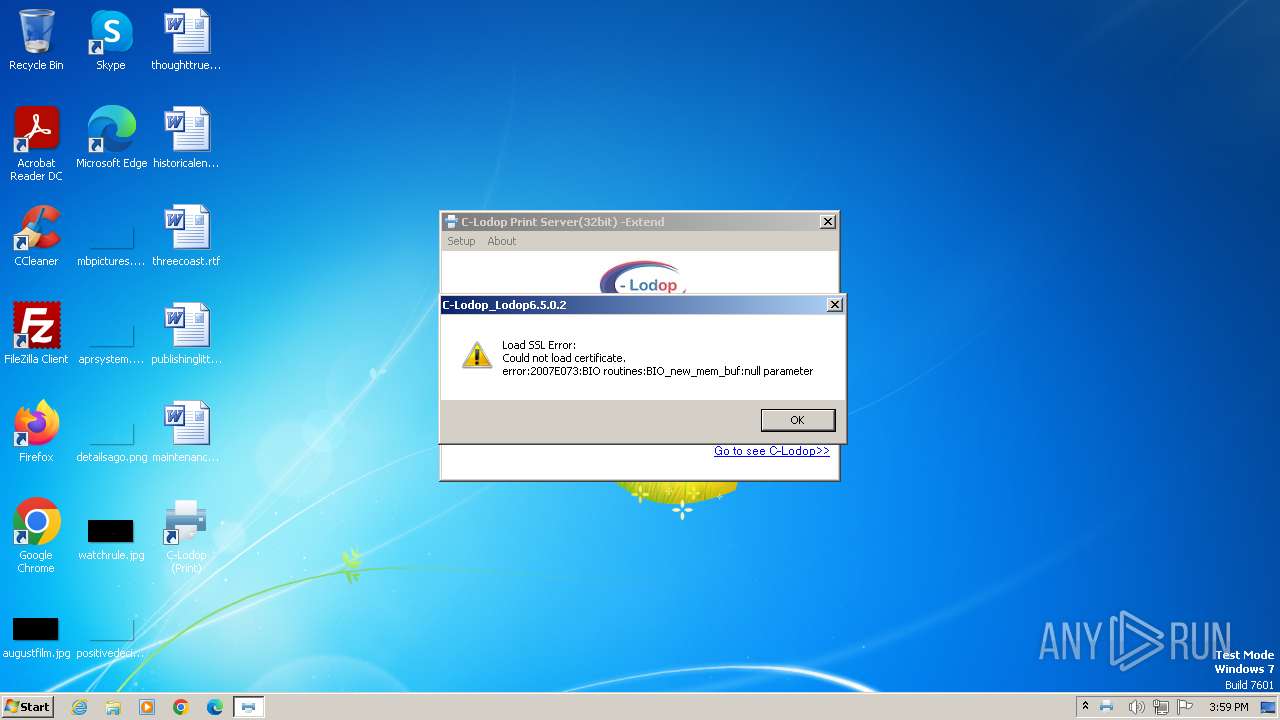
| 2628 | is-VKN0P.tmp | C:\Program Files\MountTaiSoftware\CLodop32\SSL\is-O66B1.tmp | — | |
MD5:— | SHA256:— | |||
| 2628 | is-VKN0P.tmp | C:\Program Files\MountTaiSoftware\CLodop32\SSL\localhost_c_bak.pem | — | |
MD5:— | SHA256:— | |||
| 2628 | is-VKN0P.tmp | C:\Program Files\MountTaiSoftware\CLodop32\SSL\is-5JV1R.tmp | — | |
MD5:— | SHA256:— | |||
| 2628 | is-VKN0P.tmp | C:\Program Files\MountTaiSoftware\CLodop32\SSL\localhost_c_bak.key | — | |
MD5:— | SHA256:— | |||
| 2628 | is-VKN0P.tmp | C:\Users\admin\AppData\Local\Temp\is-IM0D7.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:C594B792B9C556EA62A30DE541D2FB03 | SHA256:5DCC1E0A197922907BCA2C4369F778BD07EE4B1BBBDF633E987A028A314D548E | |||
| 2628 | is-VKN0P.tmp | C:\Program Files\MountTaiSoftware\CLodop32\is-5PLPP.tmp | executable | |
MD5:2976C5EBBFD55691CCE2527B7E6C8308 | SHA256:6630790AF959021AF2C50405DD40FBF6BF283DD04E0622A8BFE5A69CA5BAB496 | |||
| 2628 | is-VKN0P.tmp | C:\Program Files\MountTaiSoftware\CLodop32\CLodopPrint32.exe | executable | |
MD5:D2FB89B2FF3316182A5AF04C2AD79115 | SHA256:C5990D0C4FFB1DA0EF5916A629D3F12730703F8468E60CF203712A0C4EE4D47B | |||
| 2628 | is-VKN0P.tmp | C:\Users\admin\AppData\Local\Temp\is-IM0D7.tmp\TaskDll.dll | executable | |
MD5:3A57389802E43A5BC4F13E99742C218E | SHA256:25CD485DD2A9E692637A6860ED3F75F810D8883781D169EE4954170FB800DCA6 | |||
| 2628 | is-VKN0P.tmp | C:\Program Files\MountTaiSoftware\CLodop32\is-9M4B1.tmp | executable | |
MD5:D2FB89B2FF3316182A5AF04C2AD79115 | SHA256:C5990D0C4FFB1DA0EF5916A629D3F12730703F8468E60CF203712A0C4EE4D47B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
8
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2076 | CLodopPrint32.exe | GET | 200 | 121.196.197.102:80 | http://ssl.lodop.net/localhost_c.key | unknown | text | 1.73 Kb | unknown |
2076 | CLodopPrint32.exe | GET | 200 | 121.196.197.102:80 | http://ssl.lodop.net/localhost_c_date | unknown | text | 10 b | unknown |
2076 | CLodopPrint32.exe | GET | — | 121.196.197.102:80 | http://ssl.lodop.net/localhost_c.pem | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
868 | svchost.exe | 23.35.228.137:80 | — | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 88.221.124.138:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
2076 | CLodopPrint32.exe | 121.196.197.102:80 | ssl.lodop.net | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |
ssl.lodop.net |
| unknown |