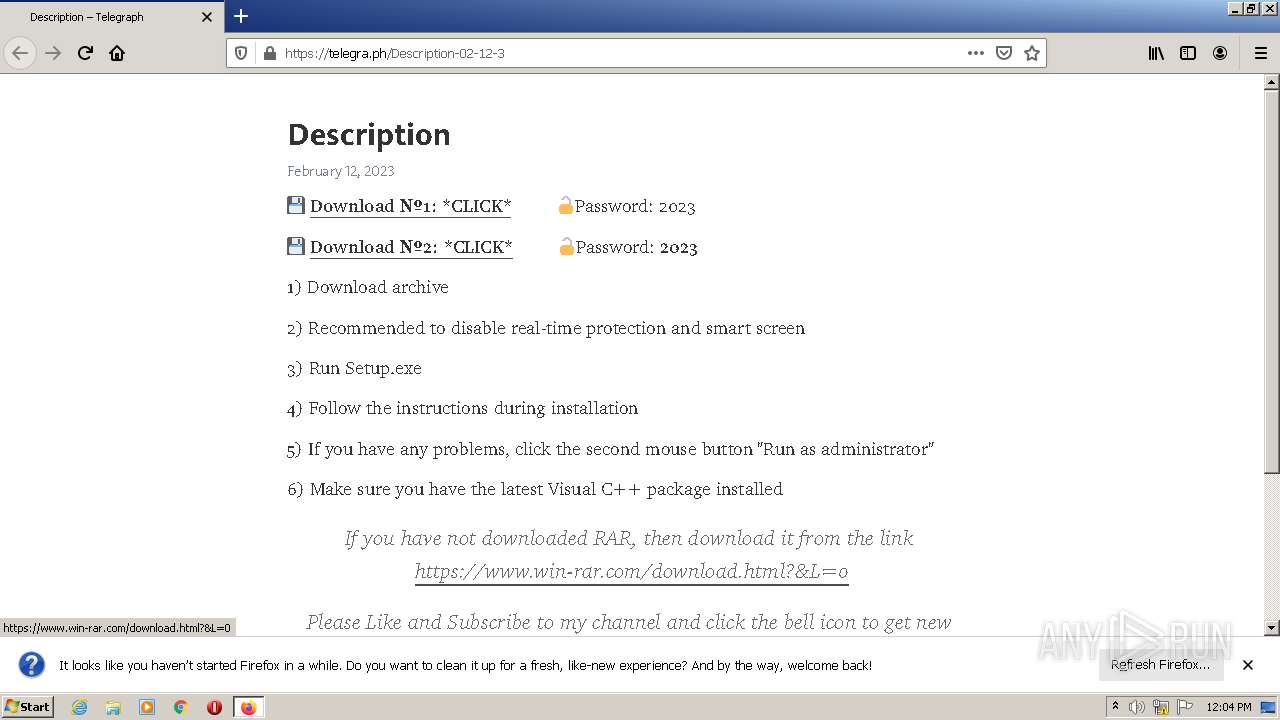
| URL: | https://telegra.ph/Description-02-12-3 |
| Full analysis: | https://app.any.run/tasks/6a3f8813-21f7-44fa-a6d0-f809b21aed33 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 01, 2023, 11:04:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C80841E0E670CAA92A3C72064534ADFC |
| SHA1: | 95CAC71FC81D3A1E5C211867B7A0CF1C68F6DB45 |
| SHA256: | D5B7E953E82E7CBF31D27986893A6946E9B6F2243FBE305D78D69C2768934985 |
| SSDEEP: | 3:N8I0c7oYW:2IDW |
MALICIOUS
Changes the autorun value in the registry
- oneetx.exe (PID: 3880)
AMADEY was detected
- oneetx.exe (PID: 3880)
Connects to the CnC server
- oneetx.exe (PID: 3880)
AMADEY detected by memory dumps
- oneetx.exe (PID: 3880)
Uses Task Scheduler to run other applications
- oneetx.exe (PID: 3880)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 3128)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- firefox.exe (PID: 2456)
Reads the Internet Settings
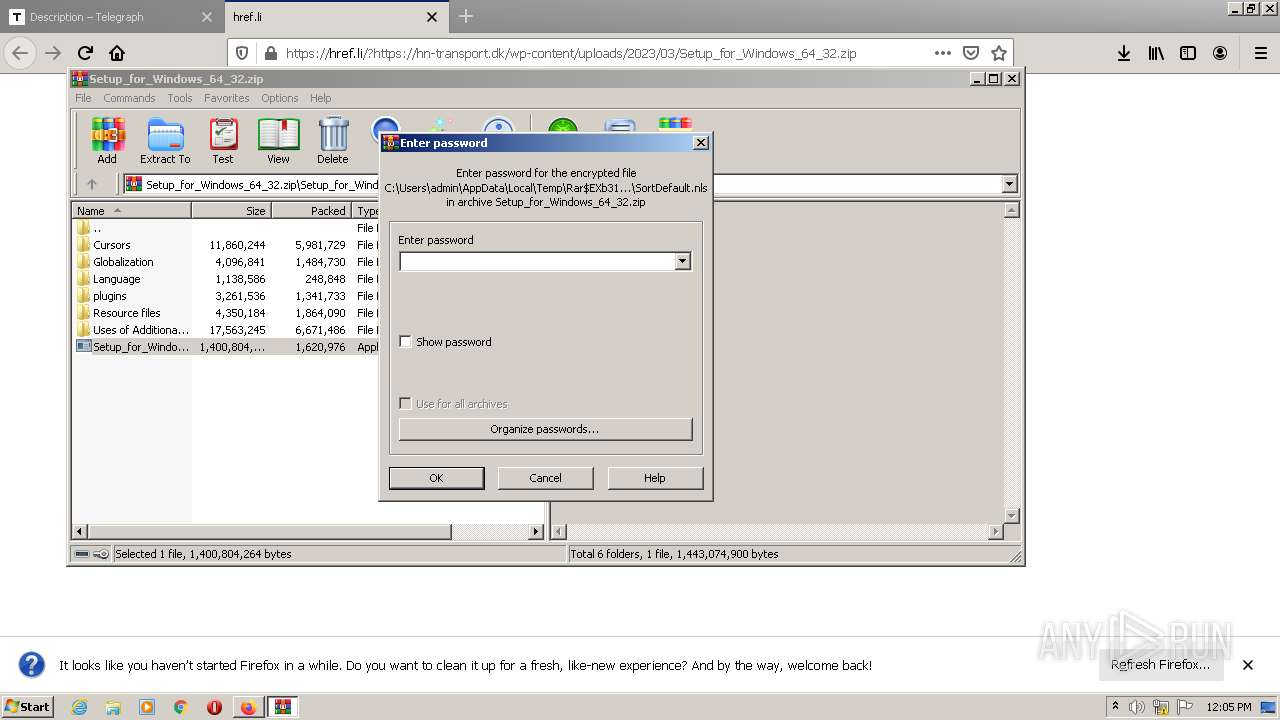
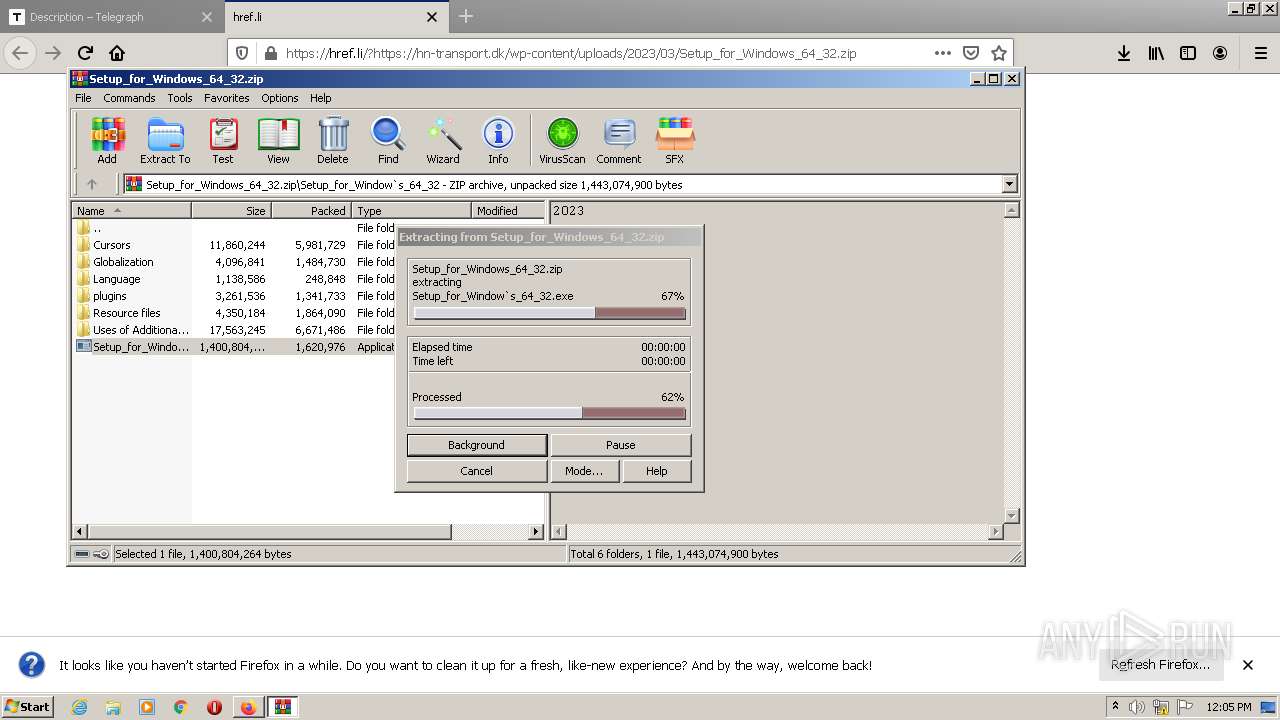
- Setup_for_Window`s_64_32.exe (PID: 1412)
- oneetx.exe (PID: 3880)
Starts itself from another location
- Setup_for_Window`s_64_32.exe (PID: 1412)
Application launched itself
- cmd.exe (PID: 2836)
Starts CMD.EXE for commands execution
- oneetx.exe (PID: 3880)
- cmd.exe (PID: 2836)
Uses RUNDLL32.EXE to load library
- oneetx.exe (PID: 3880)
The process executes via Task Scheduler
- oneetx.exe (PID: 3608)
- oneetx.exe (PID: 2880)
- oneetx.exe (PID: 1872)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2836)
Connects to the server without a host name
- oneetx.exe (PID: 3880)
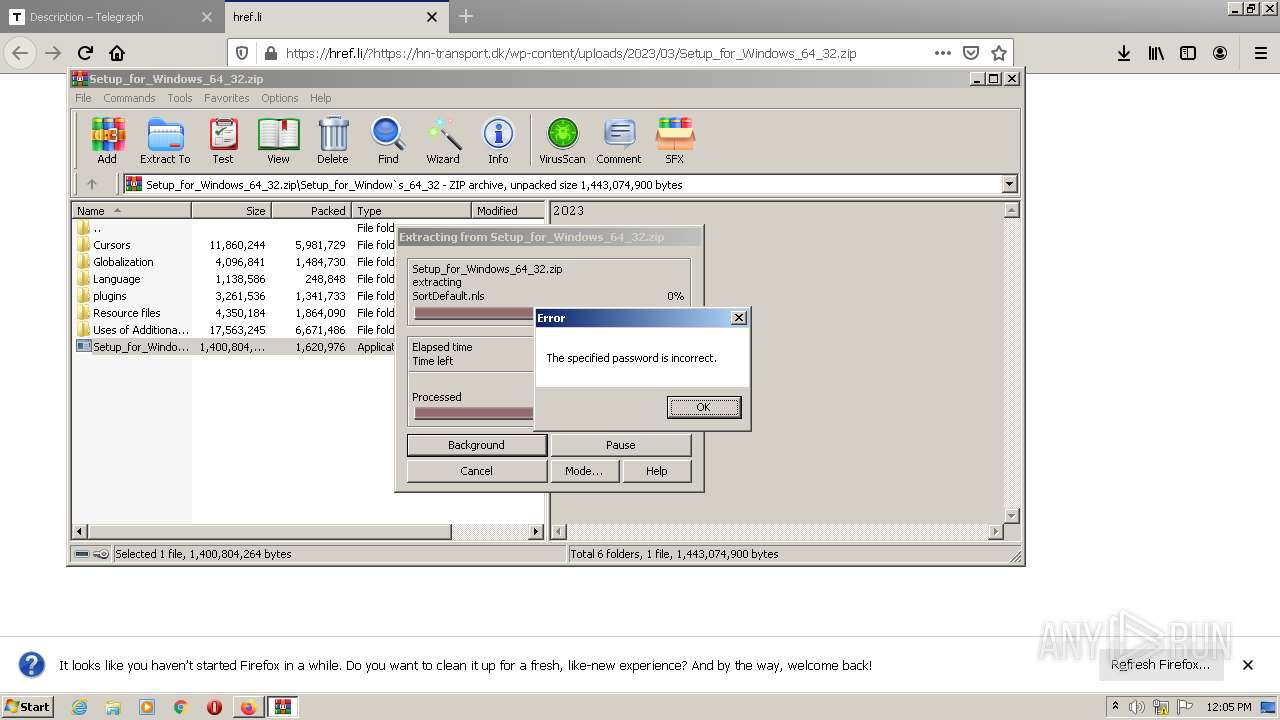
Executable content was dropped or overwritten
- oneetx.exe (PID: 3880)
Process requests binary or script from the Internet
- oneetx.exe (PID: 3880)
INFO
Application launched itself
- firefox.exe (PID: 616)
- firefox.exe (PID: 2456)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3128)
- firefox.exe (PID: 2456)
The process checks LSA protection
- Setup_for_Window`s_64_32.exe (PID: 1412)
- oneetx.exe (PID: 3880)
Create files in a temporary directory
- firefox.exe (PID: 2456)
- Setup_for_Window`s_64_32.exe (PID: 1412)
- oneetx.exe (PID: 3880)
The process uses the downloaded file
- WinRAR.exe (PID: 3128)
- firefox.exe (PID: 2456)
Checks supported languages
- Setup_for_Window`s_64_32.exe (PID: 1412)
- oneetx.exe (PID: 3880)
- oneetx.exe (PID: 3608)
- oneetx.exe (PID: 1872)
- oneetx.exe (PID: 2880)
Reads the computer name
- Setup_for_Window`s_64_32.exe (PID: 1412)
- oneetx.exe (PID: 3880)
Reads the machine GUID from the registry
- Setup_for_Window`s_64_32.exe (PID: 1412)
- oneetx.exe (PID: 3880)
Checks proxy server information
- oneetx.exe (PID: 3880)
Creates files or folders in the user directory
- oneetx.exe (PID: 3880)
Manual execution by a user
- WinRAR.exe (PID: 3128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(3880) oneetx.exe
C2 (1)http://77.91.78.118
Version3.69
Options
Drop directoryeb256e24ee
Drop nameoneetx.exe
Strings (117)SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Startup
Rem
cmd /C RMDIR /s/q
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
rundll32
/Delete /TN "
Programs
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%USERPROFILE%
\App
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
&og=
cred.dll|clip.dll|
d1
e1
e0
Main
http://
https://
exe
dll
cmd
ps1
<c>
<d>
Plugins/
+++
#
|
&unit=
=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
rb
wb
Content-Type: multipart/form-data; boundary=----
------
Content-Disposition: form-data; name="data"; filename="
"
Content-Type: application/octet-stream
------
--
?scr=1
.jpg
Content-Type: application/x-www-form-urlencoded
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
ComputerName
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\BasicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
2019
2022
2016
CurrentBuild
&&
echo Y|CACLS "
" /P "
:N"
CACLS "
" /P "
:R" /E
:F" /E
&&Exit
..\
\
:::
rundll32.exe
/k
"taskkill /f /im "
" && timeout 1 && del
&& Exit"
" && ren
&&
Powershell.exe
-executionpolicy remotesigned -File "
"
("j;o9i<$B�5%HuFUo
Total processes
65
Monitored processes
24
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://telegra.ph/Description-02-12-3" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
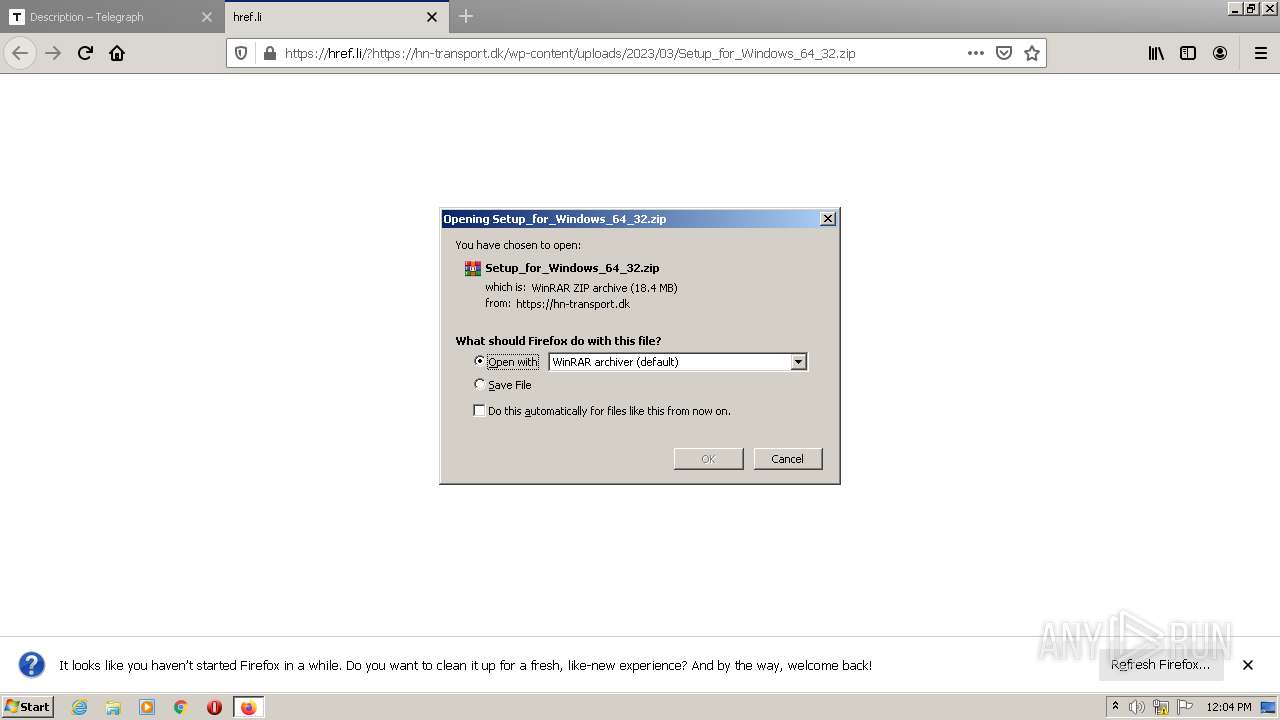
| 1412 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3128.11683\Setup_for_Window`s_64_32\Setup_for_Window`s_64_32.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3128.11683\Setup_for_Window`s_64_32\Setup_for_Window`s_64_32.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1804 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2456.20.431269848\1323302398" -childID 3 -isForBrowser -prefsHandle 3632 -prefMapHandle 3624 -prefsLen 7307 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2456 "\\.\pipe\gecko-crash-server-pipe.2456" 3644 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1864 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2456.34.1320238731\1128696838" -childID 5 -isForBrowser -prefsHandle 4044 -prefMapHandle 4040 -prefsLen 7799 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2456 "\\.\pipe\gecko-crash-server-pipe.2456" 4060 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1872 | C:\Users\admin\AppData\Local\Temp\eb256e24ee\oneetx.exe | C:\Users\admin\AppData\Local\Temp\eb256e24ee\oneetx.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2384 | C:\Windows\system32\cmd.exe /S /D /c" echo Y" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2456 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://telegra.ph/Description-02-12-3 | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2472 | CACLS "..\eb256e24ee" /P "admin:R" /E | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2836 | "C:\Windows\System32\cmd.exe" /k echo Y|CACLS "oneetx.exe" /P "admin:N"&&CACLS "oneetx.exe" /P "admin:R" /E&&echo Y|CACLS "..\eb256e24ee" /P "admin:N"&&CACLS "..\eb256e24ee" /P "admin:R" /E&&Exit | C:\Windows\System32\cmd.exe | — | oneetx.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2880 | C:\Users\admin\AppData\Local\Temp\eb256e24ee\oneetx.exe | C:\Users\admin\AppData\Local\Temp\eb256e24ee\oneetx.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
26 026
Read events
25 834
Write events
192
Delete events
0
Modification events
| (PID) Process: | (616) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 09611C1E1E000000 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: AD681C1E1E000000 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|ServicesSettingsServer |
Value: https://firefox.settings.services.mozilla.com/v1 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SecurityContentSignatureRootHash |
Value: 97:E8:BA:9C:F1:2F:B3:DE:53:CC:42:A4:E6:57:7E:D6:4D:F4:93:C2:47:B4:14:FE:A0:36:81:8D:38:23:56:0E | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
58
Suspicious files
266
Text files
448
Unknown types
52
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2456 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\places.sqlite-wal | sqlite-wal | |
MD5:— | SHA256:— | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Local\Temp\mz_etilqs_Fq6E4VzfMttFqXa | binary | |
MD5:— | SHA256:— | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:— | SHA256:— | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4 | jsonlz4 | |
MD5:B17F8D93B0C43D6B72DC03752C20A2D9 | SHA256:ADA0F70D374223FB63C2F19471FAB45D986A681E2485692E63F00F5071F19D76 | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\settings\main\ms-language-packs\asrouter.ftl.tmp | text | |
MD5:C460716B62456449360B23CF5663F275 | SHA256:0EC0F16F92D876A9C1140D4C11E2B346A9292984D9A854360E54E99FDCD99CC0 | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-new.bin | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
40
DNS requests
117
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2456 | firefox.exe | POST | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com/ | US | der | 1.74 Kb | whitelisted |
2456 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | text | 8 b | whitelisted |
2456 | firefox.exe | POST | 200 | 2.16.186.90:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | shared |
2456 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | US | text | 8 b | whitelisted |
2456 | firefox.exe | POST | 200 | 2.16.186.90:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | shared |
2456 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2456 | firefox.exe | POST | — | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3 | US | — | — | whitelisted |
2456 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2456 | firefox.exe | POST | — | 2.16.186.90:80 | http://r3.o.lencr.org/ | unknown | — | — | shared |
2456 | firefox.exe | POST | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com/ | US | der | 1.74 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2456 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2456 | firefox.exe | 149.154.164.13:443 | telegra.ph | Telegram Messenger Inc | GB | suspicious |
2456 | firefox.exe | 35.241.9.150:443 | firefox.settings.services.mozilla.com | GOOGLE | US | suspicious |
2456 | firefox.exe | 2.16.186.90:80 | r3.o.lencr.org | Akamai International B.V. | DE | whitelisted |
2456 | firefox.exe | 192.124.249.22:80 | ocsp.godaddy.com | SUCURI-SEC | US | suspicious |
2456 | firefox.exe | 142.250.186.138:443 | safebrowsing.googleapis.com | GOOGLE | US | whitelisted |
2456 | firefox.exe | 52.40.44.47:443 | location.services.mozilla.com | AMAZON-02 | US | unknown |
2456 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | suspicious |
— | — | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | suspicious |
— | — | 142.250.186.138:443 | safebrowsing.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
telegra.ph |
| malicious |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
r3.o.lencr.org |
| shared |
ocsp.godaddy.com |
| whitelisted |
a1887.dscq.akamai.net |
| whitelisted |
ocsp.godaddy.com.akadns.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2456 | firefox.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
3880 | oneetx.exe | A Network Trojan was detected | AV TROJAN Agent.DHOA System Info Exfiltration |
3880 | oneetx.exe | Unknown Classtype | ET MALWARE Amadey CnC Check-In |
3880 | oneetx.exe | A Network Trojan was detected | ET MALWARE Amadey Bot Activity (POST) |
3880 | oneetx.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
3880 | oneetx.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .dll file with no User-Agent |
3880 | oneetx.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
3880 | oneetx.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .dll file with no User-Agent |
3880 | oneetx.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3880 | oneetx.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |