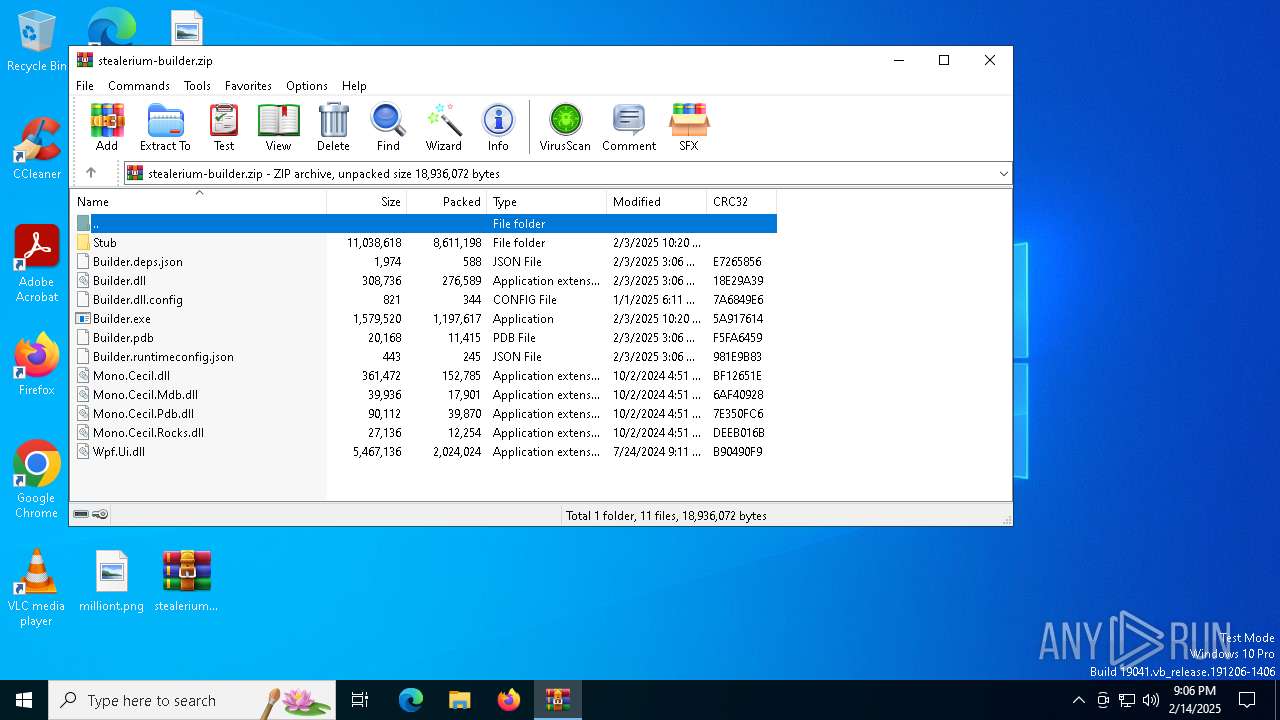
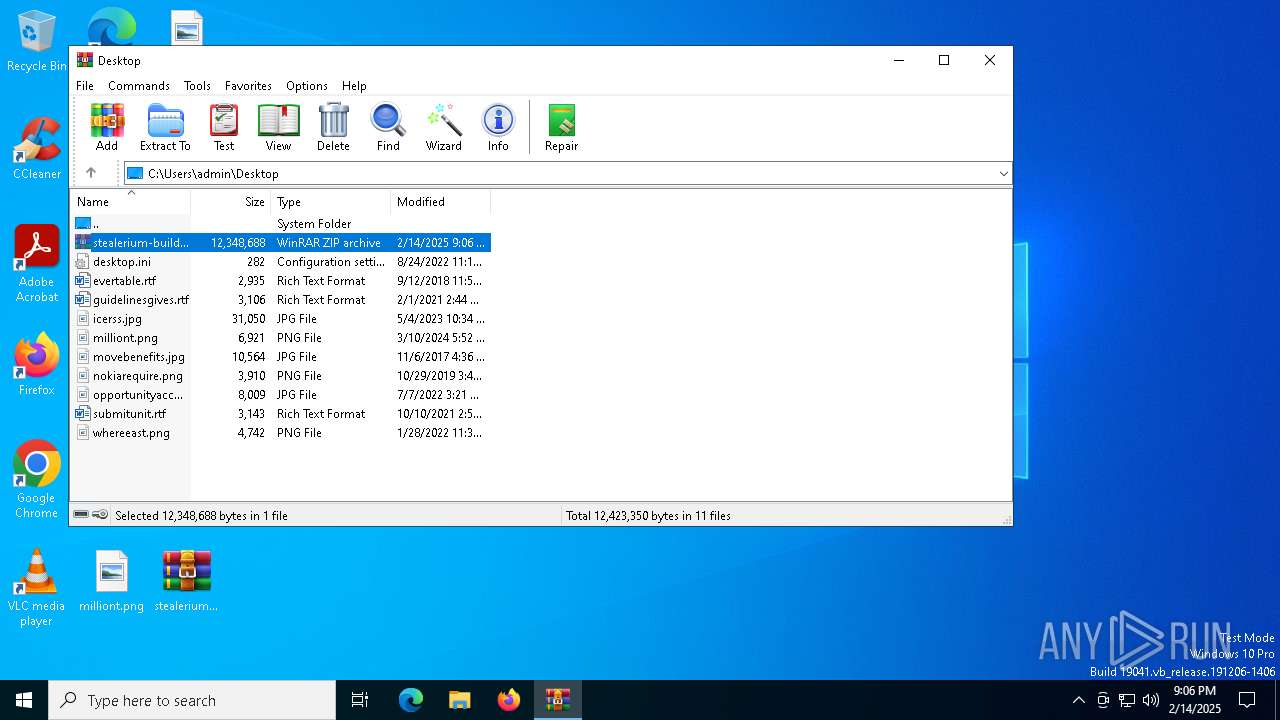
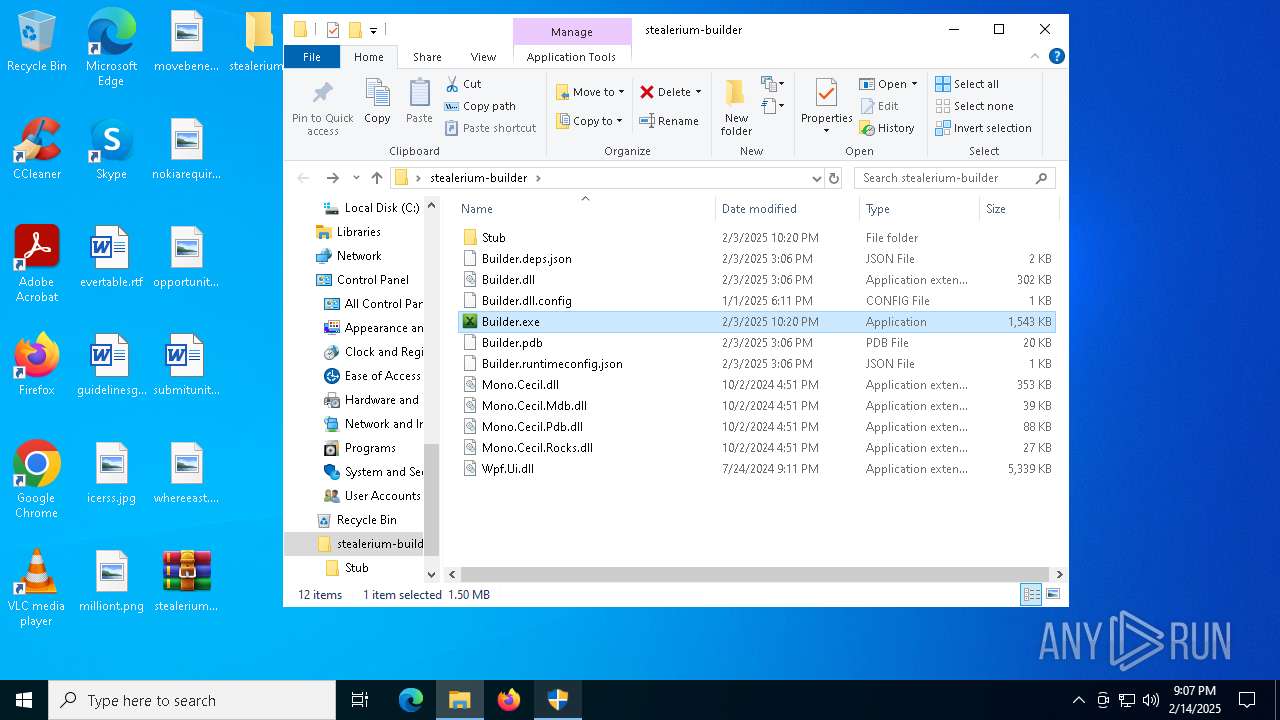
| File name: | stealerium-builder.zip |
| Full analysis: | https://app.any.run/tasks/b548b1bb-c774-455c-9160-248e4e98e82c |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 14, 2025, 21:06:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B9F561D0FE7D8D8FC13809B642AA5049 |
| SHA1: | 345B339FC11754BDC2E3266F4CF2EA0AA52E28BF |
| SHA256: | D59B0FA6CFF2624D176D4DE70272C197D5CB2B9D9AD7CC916D07D5B5A200AC5E |
| SSDEEP: | 98304:Tav2z53j37r35RNy2JY2Zuq6NpBKUEuwImpa/78WKie3IzbifhJhTKSqxiVPiRwg:9zKQG9pyRXXOCTpWcyYPQX5 |
MALICIOUS
Stealerium has been detected
- WinRAR.exe (PID: 6324)
- Builder.exe (PID: 2136)
- ._cache_Builder.exe (PID: 2676)
- Hyxcsgl.exe (PID: 4740)
- Caiyusdgkujgte.exe (PID: 5252)
- tmpA7F6.exe (PID: 6632)
- Synaptics.exe (PID: 6660)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- cmd.exe (PID: 5112)
- timeout.exe (PID: 5452)
- conhost.exe (PID: 3912)
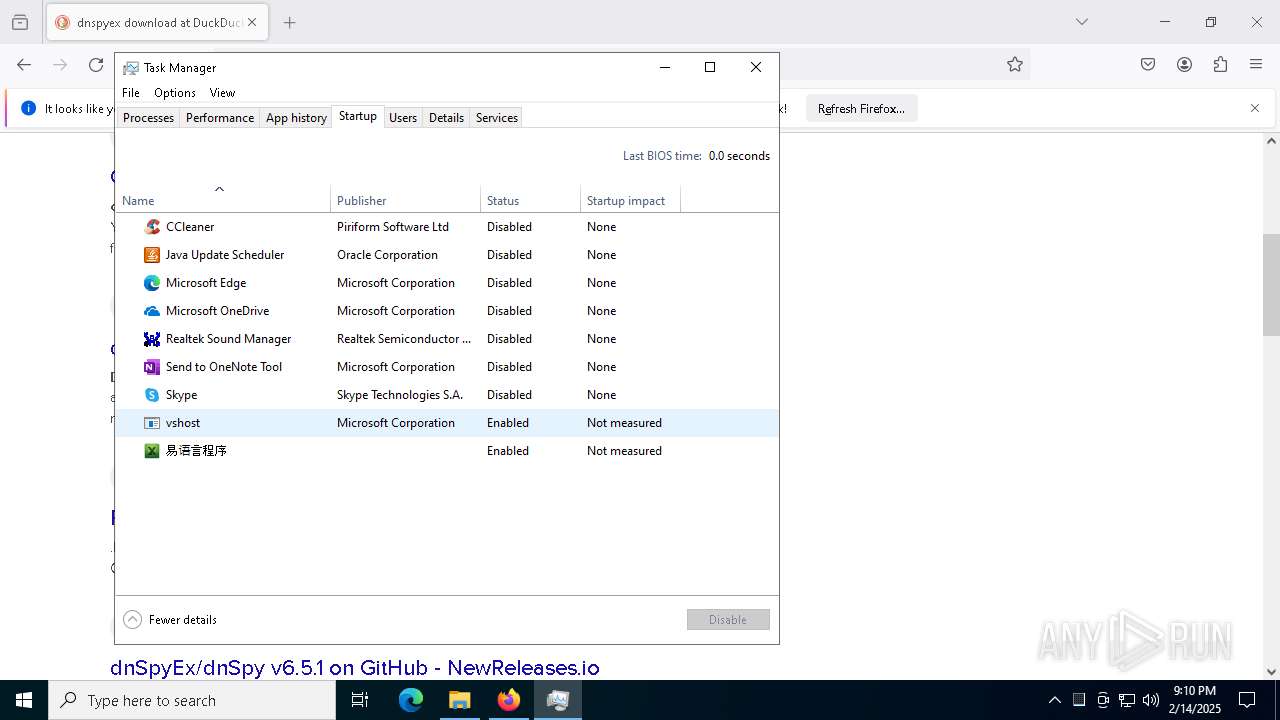
- vshost.exe (PID: 5340)
- WerFault.exe (PID: 6656)
- tmpD262.exe (PID: 6188)
- Builder.exe (PID: 7072)
- ._cache_Builder.exe (PID: 5892)
- Hyxcsgl.exe (PID: 1080)
- Caiyusdgkujgte.exe (PID: 6220)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
- tmp5EF2.exe (PID: 3584)
- WerFault.exe (PID: 3824)
XRED mutex has been found
- Builder.exe (PID: 2136)
- Caiyusdgkujgte.exe (PID: 5252)
- Synaptics.exe (PID: 6660)
- Builder.exe (PID: 7072)
- Caiyusdgkujgte.exe (PID: 6220)
Changes the autorun value in the registry
- Builder.exe (PID: 2136)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
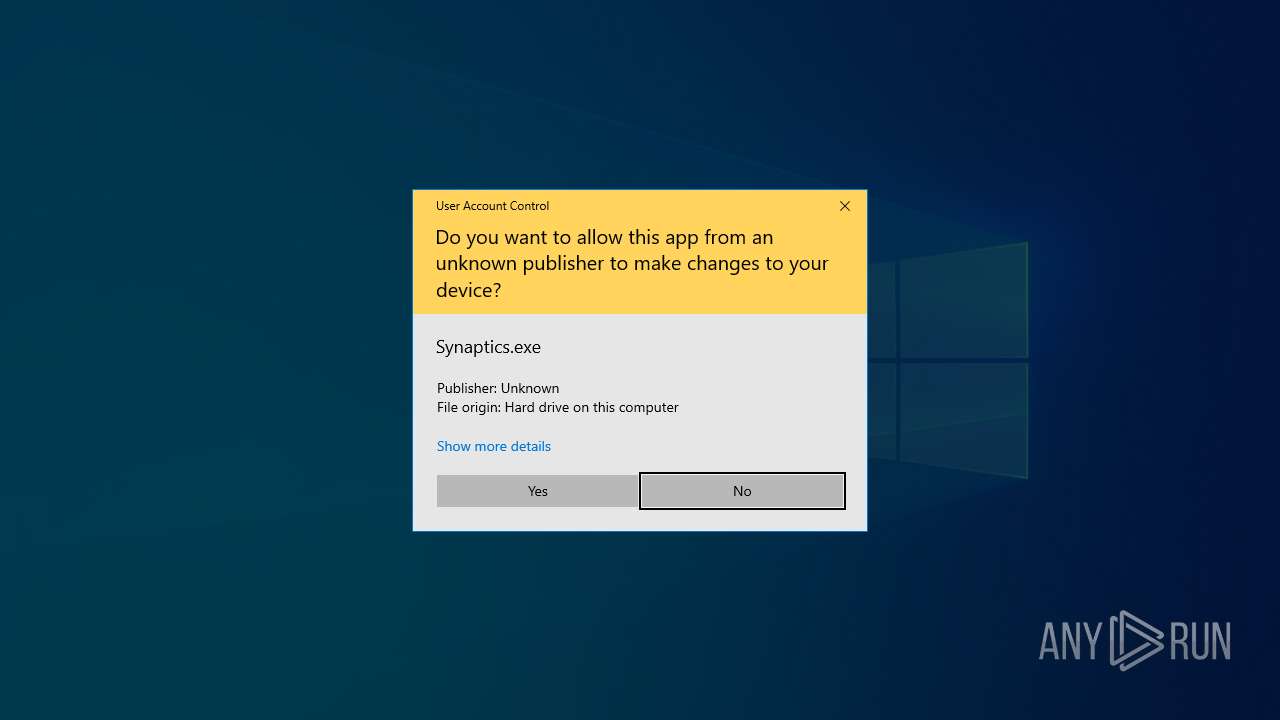
Executing a file with an untrusted certificate
- tmpA7F6.exe (PID: 6632)
- tmpD262.exe (PID: 6188)
- tmp5EF2.exe (PID: 3584)
XRED has been detected (YARA)
- Synaptics.exe (PID: 6660)
ASYNCRAT has been detected (YARA)
- vshost.exe (PID: 5340)
SUSPICIOUS
Reads security settings of Internet Explorer
- Builder.exe (PID: 2136)
- ._cache_Builder.exe (PID: 2676)
- Caiyusdgkujgte.exe (PID: 5252)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- Synaptics.exe (PID: 6660)
- vshost.exe (PID: 5340)
- Builder.exe (PID: 7072)
- ._cache_Builder.exe (PID: 5892)
- Caiyusdgkujgte.exe (PID: 6220)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
Executable content was dropped or overwritten
- Builder.exe (PID: 2136)
- ._cache_Builder.exe (PID: 2676)
- Caiyusdgkujgte.exe (PID: 5252)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- vshost.exe (PID: 5340)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
Starts a Microsoft application from unusual location
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- tmpA7F6.exe (PID: 6632)
- tmpD262.exe (PID: 6188)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
- tmp5EF2.exe (PID: 3584)
Process drops legitimate windows executable
- Caiyusdgkujgte.exe (PID: 5252)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- vshost.exe (PID: 5340)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
Reads the date of Windows installation
- ._cache_Builder.exe (PID: 2676)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- vshost.exe (PID: 5340)
- ._cache_Builder.exe (PID: 5892)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
Executes application which crashes
- tmpA7F6.exe (PID: 6632)
- tmpD262.exe (PID: 6188)
- tmp5EF2.exe (PID: 3584)
Starts CMD.EXE for commands execution
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
The process creates files with name similar to system file names
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
Executing commands from a ".bat" file
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5112)
The executable file from the user directory is run by the CMD process
- vshost.exe (PID: 5340)
There is functionality for taking screenshot (YARA)
- Synaptics.exe (PID: 6660)
There is functionality for communication over UDP network (YARA)
- Synaptics.exe (PID: 6660)
There is functionality for communication dyndns network (YARA)
- Synaptics.exe (PID: 6660)
Connects to unusual port
- vshost.exe (PID: 5340)
Checks Windows Trust Settings
- Synaptics.exe (PID: 6660)
INFO
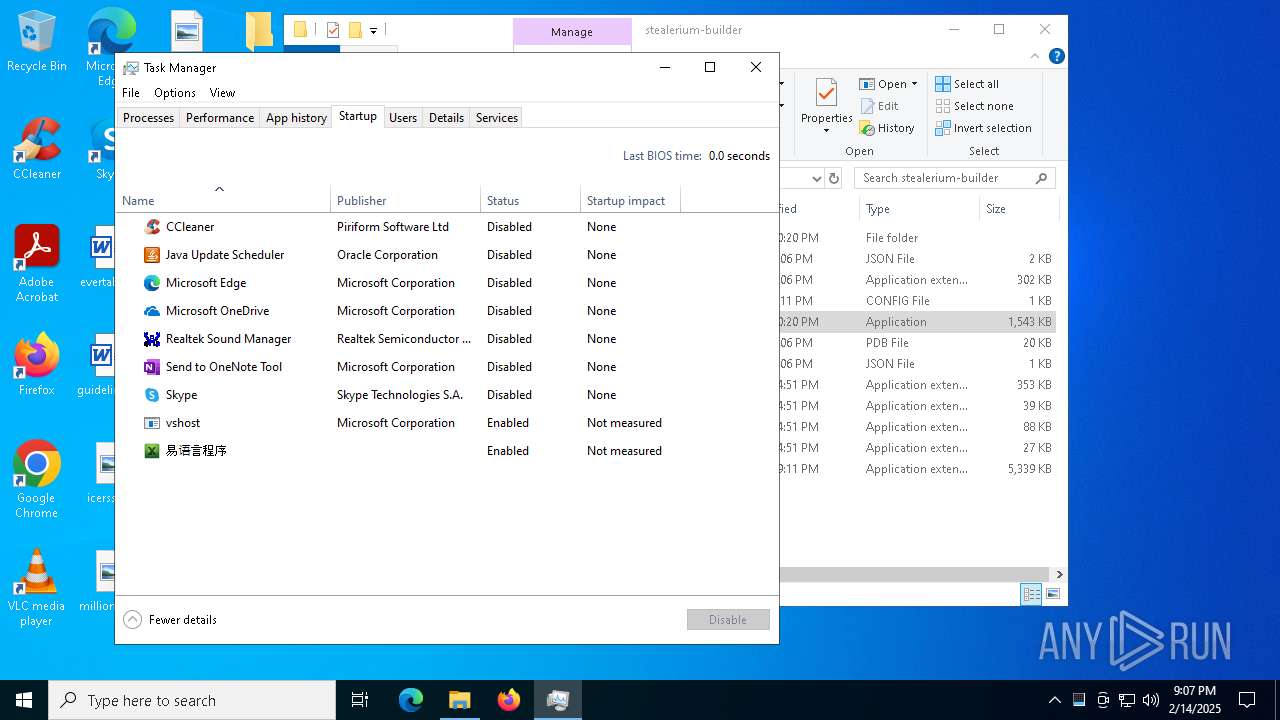
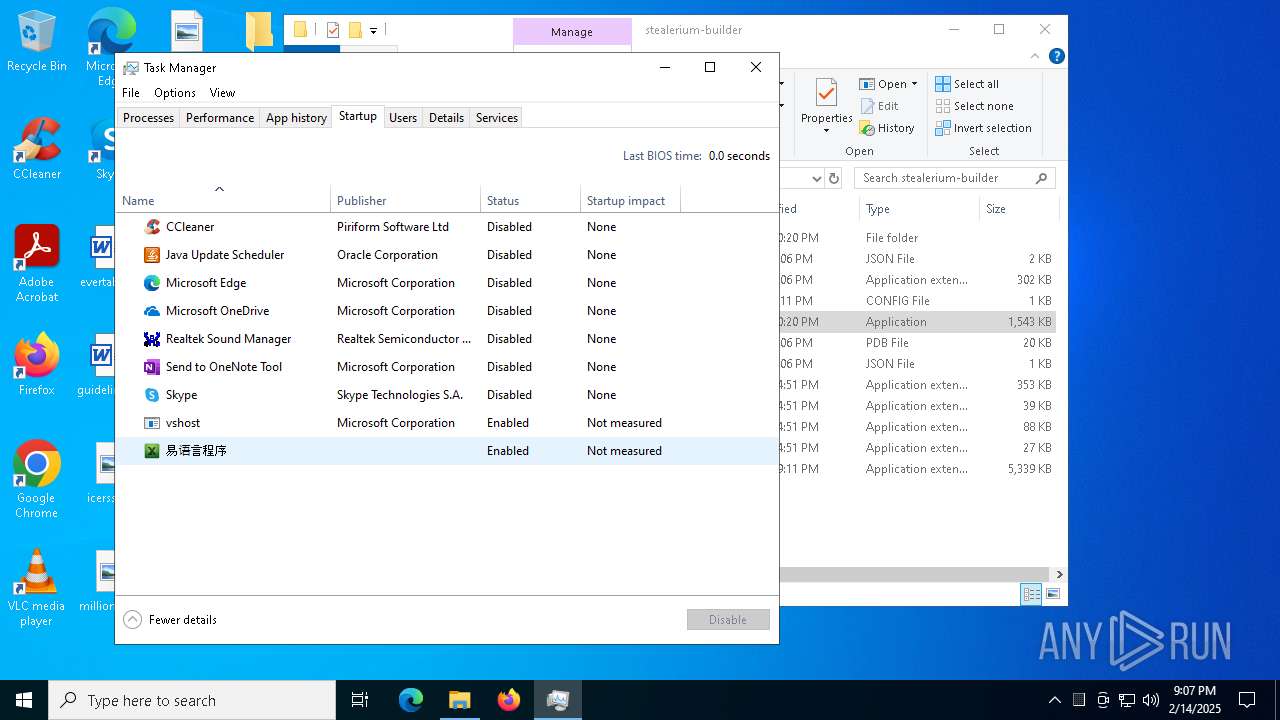
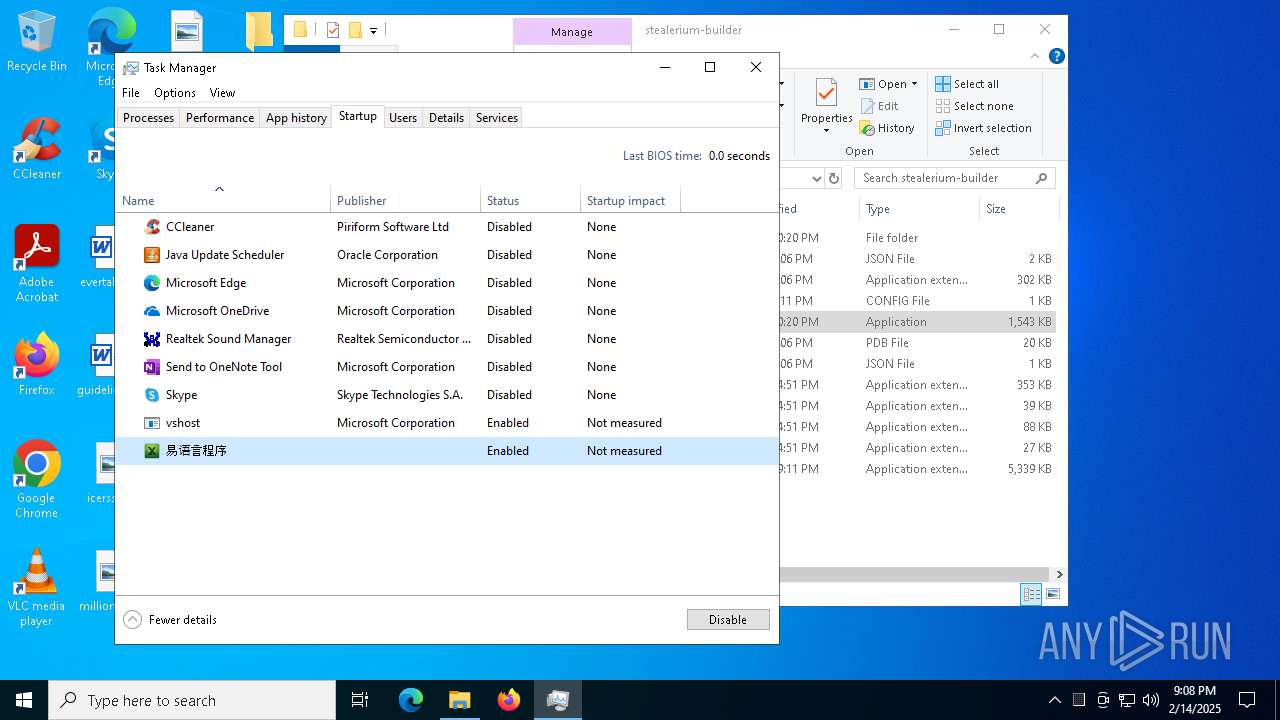
The sample compiled with chinese language support
- WinRAR.exe (PID: 6324)
- Builder.exe (PID: 2136)
- ._cache_Builder.exe (PID: 2676)
Manual execution by a user
- Builder.exe (PID: 2136)
- Taskmgr.exe (PID: 2800)
- Taskmgr.exe (PID: 7116)
- Builder.exe (PID: 7072)
- firefox.exe (PID: 3080)
- Taskmgr.exe (PID: 2940)
- Taskmgr.exe (PID: 5872)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6324)
Checks supported languages
- Builder.exe (PID: 2136)
- ._cache_Builder.exe (PID: 2676)
- Hyxcsgl.exe (PID: 4740)
- Caiyusdgkujgte.exe (PID: 5252)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- tmpA7F6.exe (PID: 6632)
- Synaptics.exe (PID: 6660)
- vshost.exe (PID: 5340)
- tmpD262.exe (PID: 6188)
- Builder.exe (PID: 7072)
- ._cache_Builder.exe (PID: 5892)
- Hyxcsgl.exe (PID: 1080)
- Caiyusdgkujgte.exe (PID: 6220)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
- tmp5EF2.exe (PID: 3584)
Process checks computer location settings
- Builder.exe (PID: 2136)
- ._cache_Builder.exe (PID: 2676)
- Caiyusdgkujgte.exe (PID: 5252)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- vshost.exe (PID: 5340)
- Builder.exe (PID: 7072)
- ._cache_Builder.exe (PID: 5892)
- Caiyusdgkujgte.exe (PID: 6220)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
Reads the computer name
- Builder.exe (PID: 2136)
- ._cache_Builder.exe (PID: 2676)
- Hyxcsgl.exe (PID: 4740)
- Caiyusdgkujgte.exe (PID: 5252)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- Synaptics.exe (PID: 6660)
- vshost.exe (PID: 5340)
- Builder.exe (PID: 7072)
- ._cache_Builder.exe (PID: 5892)
- Hyxcsgl.exe (PID: 1080)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
- Caiyusdgkujgte.exe (PID: 6220)
Creates files in the program directory
- Builder.exe (PID: 2136)
- Synaptics.exe (PID: 6660)
Reads the machine GUID from the registry
- ._cache_Builder.exe (PID: 2676)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- vshost.exe (PID: 5340)
- ._cache_Builder.exe (PID: 5892)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
- Synaptics.exe (PID: 6660)
Create files in a temporary directory
- ._cache_Builder.exe (PID: 2676)
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- vshost.exe (PID: 5340)
- ._cache_Builder.exe (PID: 5892)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
- Synaptics.exe (PID: 6660)
Reads Environment values
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- vshost.exe (PID: 5340)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
Creates files or folders in the user directory
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- WerFault.exe (PID: 6656)
- WerFault.exe (PID: 1544)
- WerFault.exe (PID: 3824)
- Synaptics.exe (PID: 6660)
The sample compiled with english language support
- ._cache_Caiyusdgkujgte.exe (PID: 5236)
- vshost.exe (PID: 5340)
- ._cache_Caiyusdgkujgte.exe (PID: 4864)
Checks proxy server information
- WerFault.exe (PID: 6656)
- Synaptics.exe (PID: 6660)
- WerFault.exe (PID: 1544)
- WerFault.exe (PID: 3824)
Reads the software policy settings
- WerFault.exe (PID: 6656)
- WerFault.exe (PID: 1544)
- WerFault.exe (PID: 3824)
- Synaptics.exe (PID: 6660)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 7116)
- Taskmgr.exe (PID: 5872)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- vshost.exe (PID: 5340)
Potential library load (Base64 Encoded 'LoadLibrary')
- vshost.exe (PID: 5340)
Compiled with Borland Delphi (YARA)
- Synaptics.exe (PID: 6660)
- vshost.exe (PID: 5340)
- Taskmgr.exe (PID: 5872)
Application launched itself
- firefox.exe (PID: 3080)
- firefox.exe (PID: 4144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(5340) vshost.exe
C2 (2)127.0.0.1
149.143.81.189
Ports (2)4449
5555
VersionVenom Pwn3rzs' Edtition v6.0.1
Options
AutoRuntrue
Mutexbrsgtvswueo
InstallFolder%AppData%
Certificates
Cert1MIICOTCCAaKgAwIBAgIVALsa7CumGCIOWaYkKMDUXTUNivajMA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTI0MDQyNDE2MTM0MVoXDTM1MDIwMTE2MTM0MVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureUrAl8DoJSZAztuV5XcPtK8WhoM6M1yleIYReExh4KPoWjkFTF5yF2JHn90lfUXmGehYNPEYz1pdQLrlVwCC4fmNzC8S3OCvfovPF7VtIqWXQalPzCVMSleRWZr40dtaCu6esxz2/PwmTCP20ywjg2msef+ymfGopECA2GOwjPQ4=
Keys
AES4c1d98719cc053dbd54ada166f659e5d2507888879d77ac6ee4d22a834a6268b
SaltVenomRATByVenom
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:02:03 16:06:08 |
| ZipCRC: | 0xe7265856 |
| ZipCompressedSize: | 588 |
| ZipUncompressedSize: | 1974 |
| ZipFileName: | Builder.deps.json |
Total processes
176
Monitored processes
41
Malicious processes
21
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 776 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2864 -childID 8 -isForBrowser -prefsHandle 6008 -prefMapHandle 5664 -prefsLen 32088 -prefMapSize 244583 -jsInitHandle 1508 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {23b1df1c-5fad-416b-805f-1f9e6d75f7f6} 4144 "\\.\pipe\gecko-crash-server-pipe.4144" 17826137d90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1080 | "C:\Users\admin\AppData\Local\Temp\Hyxcsgl.exe" | C:\Users\admin\AppData\Local\Temp\Hyxcsgl.exe | ._cache_Builder.exe | ||||||||||||
User: admin Company: Builder Integrity Level: MEDIUM Description: Builder Exit code: 2147516570 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1544 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6188 -s 468 | C:\Windows\SysWOW64\WerFault.exe | tmpD262.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\Desktop\stealerium-builder\Builder.exe" | C:\Users\admin\Desktop\stealerium-builder\Builder.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: 易语言程序 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2548 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2676 | "C:\Users\admin\Desktop\stealerium-builder\._cache_Builder.exe" | C:\Users\admin\Desktop\stealerium-builder\._cache_Builder.exe | Builder.exe | ||||||||||||
User: admin Company: Microsoft® Windows® Operating System Integrity Level: MEDIUM Description: Microsoft® Windows® Operating System Exit code: 0 Version: 10.0.19041.4355 Modules
| |||||||||||||||
| 2800 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2940 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2992 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4752 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4656 -prefMapHandle 4828 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {eb725104-f95f-410a-ba4b-eec829c357d5} 4144 "\\.\pipe\gecko-crash-server-pipe.4144" 178287f1110 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
35 844
Read events
35 756
Write events
73
Delete events
15
Modification events
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\stealerium-builder.zip | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
22
Suspicious files
203
Text files
41
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6324 | WinRAR.exe | C:\Users\admin\Desktop\stealerium-builder\Builder.dll | executable | |
MD5:F961FDD3422688D8E4A862FDE1C2FEF6 | SHA256:D09AD0884F643E23A66CF359717F127C40770E94BA4867E01573D6F9854CC158 | |||
| 6324 | WinRAR.exe | C:\Users\admin\Desktop\stealerium-builder\Builder.deps.json | binary | |
MD5:503C7248E00282D9A70A331DA0129E95 | SHA256:A86C83CCCF639E2C3121C6A86A0CE14CEF77914261F6B8EAF6717165EAE805A5 | |||
| 6324 | WinRAR.exe | C:\Users\admin\Desktop\stealerium-builder\Stub\stub.exe | executable | |
MD5:F60C20FF835271FF3B420C816248D464 | SHA256:E6F5C02E1B407AC410FF25EFEE7F5D1B1E159FF17FB648B3C07475168653F06C | |||
| 6324 | WinRAR.exe | C:\Users\admin\Desktop\stealerium-builder\Stub\stub.pdb | binary | |
MD5:394AC086B777365F76C4B6BBBDAC15C7 | SHA256:E202201DFEC95E4282E9B55BC4C5456AB8A46E2A7990330827E9BF477B341B9F | |||
| 6324 | WinRAR.exe | C:\Users\admin\Desktop\stealerium-builder\Stub\stub.exe.config | xml | |
MD5:F7C0C29C927C06059383BCBB937DB342 | SHA256:402E225960E22721A21FFC56FF77D9C2C7B4BFFDB2CEF8B93AFA2617DA6C798E | |||
| 6324 | WinRAR.exe | C:\Users\admin\Desktop\stealerium-builder\Stub\runtimes\win-x86\native\e_sqlite3.dll | executable | |
MD5:6FC560F5084A8B7FB99840A6FD356170 | SHA256:F80D5F5DE3F7A82E684229028B946F6EFA1682D27EC960EF18518542FD12A407 | |||
| 2136 | Builder.exe | C:\Users\admin\Desktop\stealerium-builder\._cache_Builder.exe | executable | |
MD5:AA1DD66856048E8ECB72081F74785B94 | SHA256:8D5DB05019906DAC967634E516144595E0A432DC5E0B0030ACE9701E1D7003B2 | |||
| 6324 | WinRAR.exe | C:\Users\admin\Desktop\stealerium-builder\Mono.Cecil.Mdb.dll | executable | |
MD5:7287A874E5384C339299B7F3A7588141 | SHA256:28CB367972BDC1CD43E4006306AF2FD96D37F4ED4B239EE90E1DC7237A93AF7F | |||
| 2136 | Builder.exe | C:\ProgramData\Synaptics\Synaptics.exe | executable | |
MD5:2FA36582E9ED3FB6943A2E8EDB281288 | SHA256:0C802B5DD7BC80485FDE905279745BA5957D2D413A7BF51862FEAAB7C25BBD0E | |||
| 2136 | Builder.exe | C:\ProgramData\Synaptics\RCX9BB2.tmp | executable | |
MD5:91A76B1FB0EB34B7B02D662FD88F5ACE | SHA256:CBD3BE81101AE7D2D0E11A736B86887982C56799EA58C7FDEE6E78CD5975AD1D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
167
DNS requests
178
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6156 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6156 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6852 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6656 | WerFault.exe | GET | 200 | 23.48.23.170:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6660 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
6656 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2380 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.168:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to Abused Domain *.mooo.com |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
Process | Message |
|---|---|
Hyxcsgl.exe | The application to execute does not exist: 'C:\Users\admin\AppData\Local\Temp\Builder.dll'. |
Hyxcsgl.exe | The application to execute does not exist: 'C:\Users\admin\AppData\Local\Temp\Builder.dll'. |