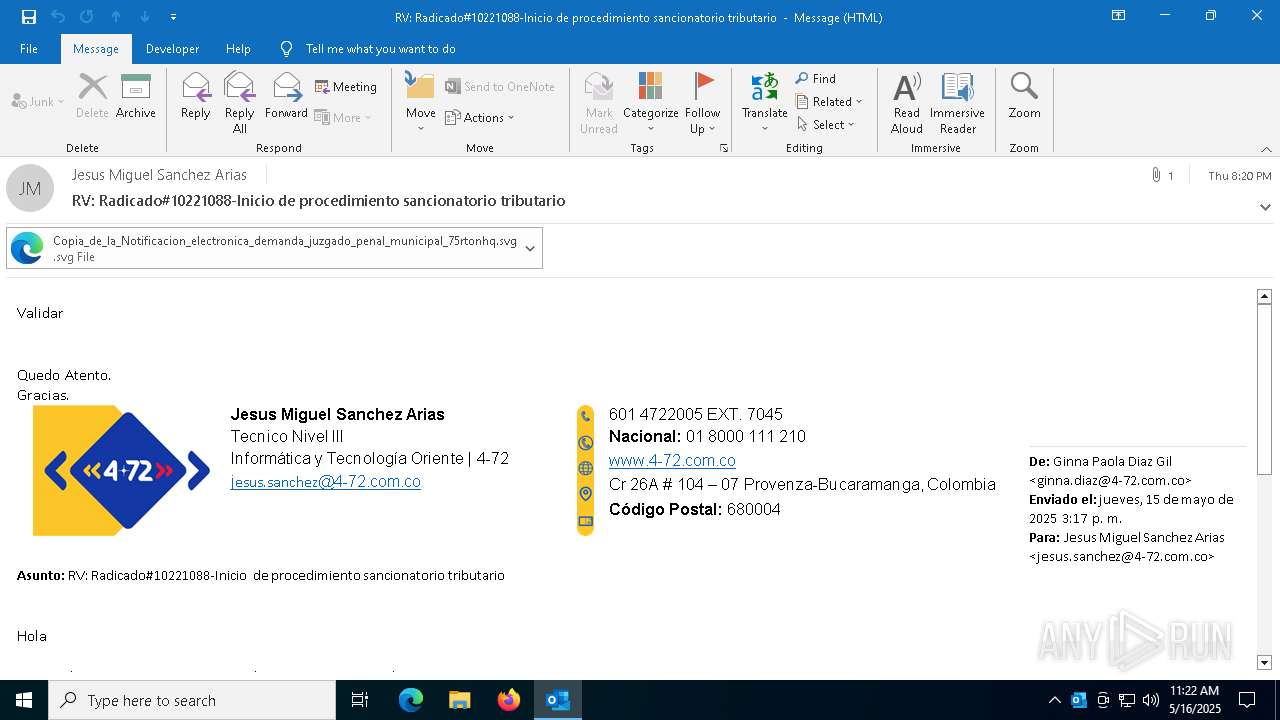
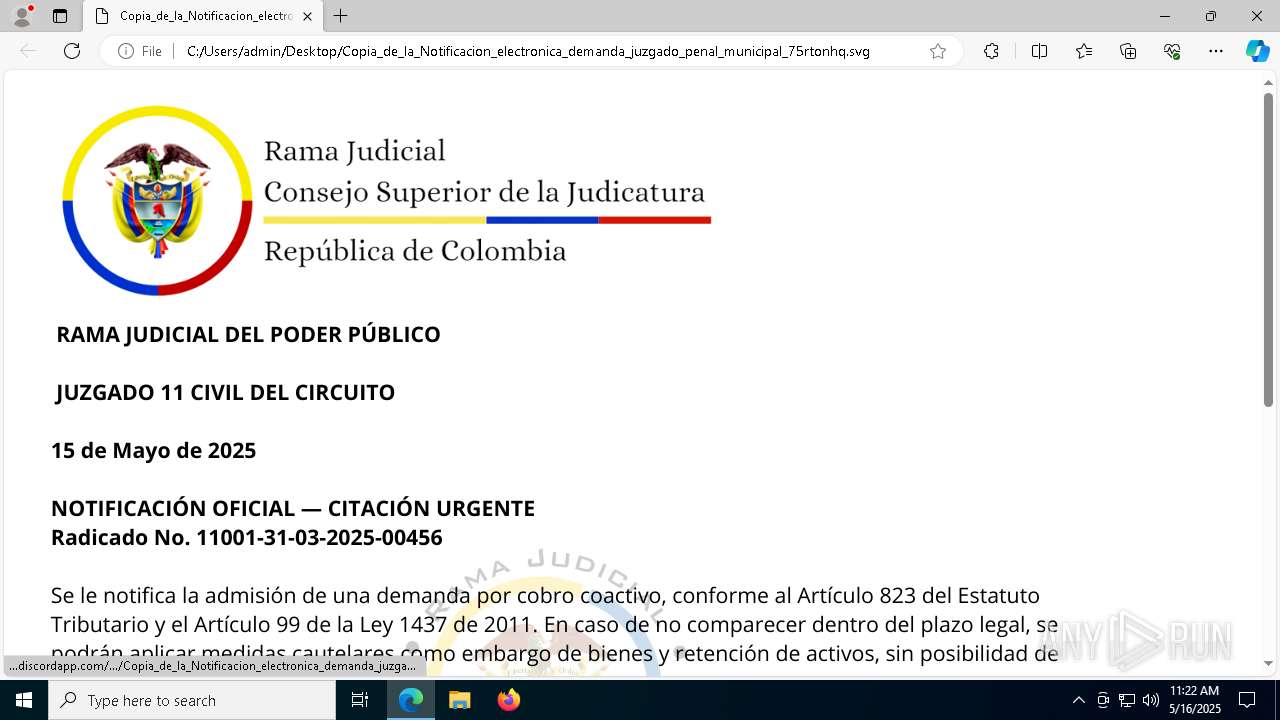
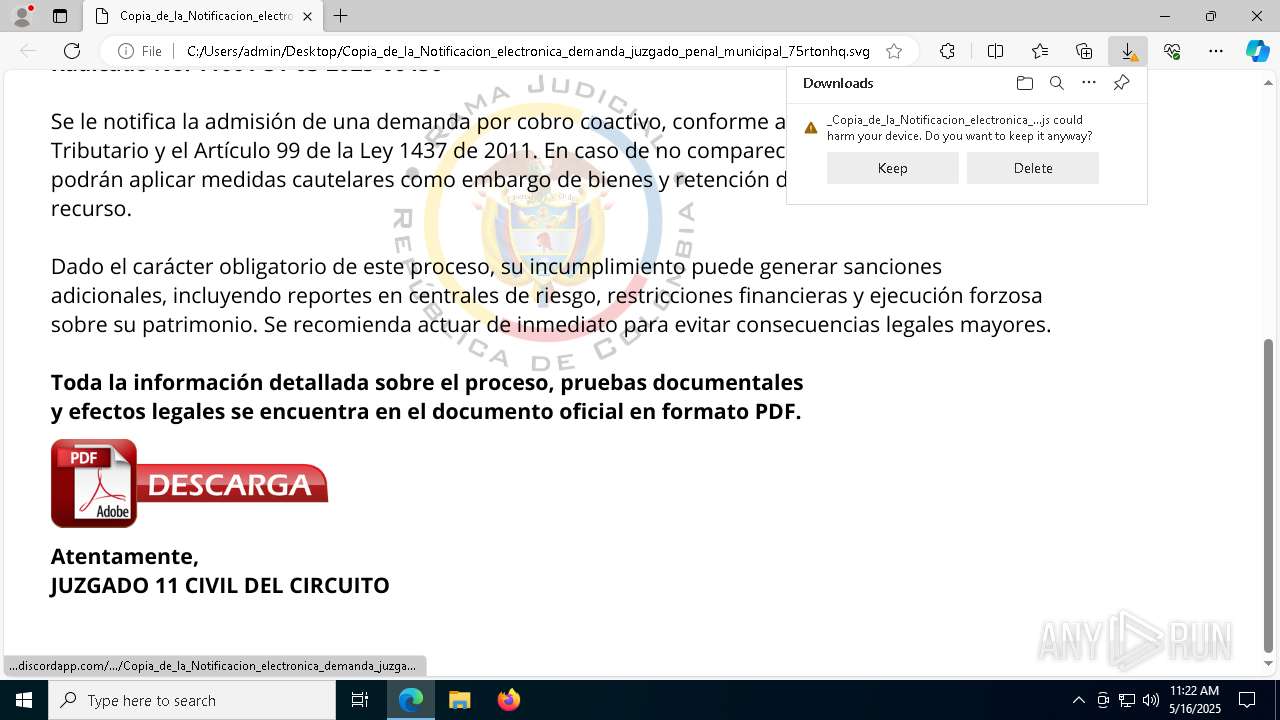
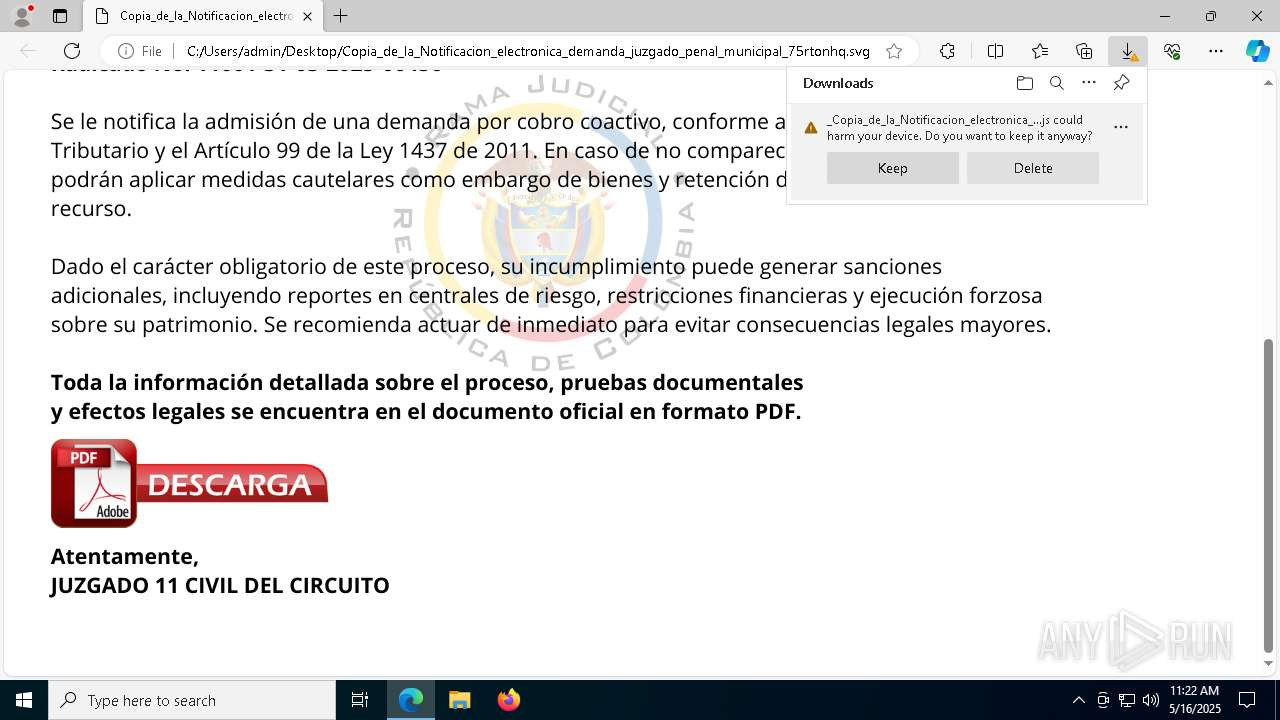
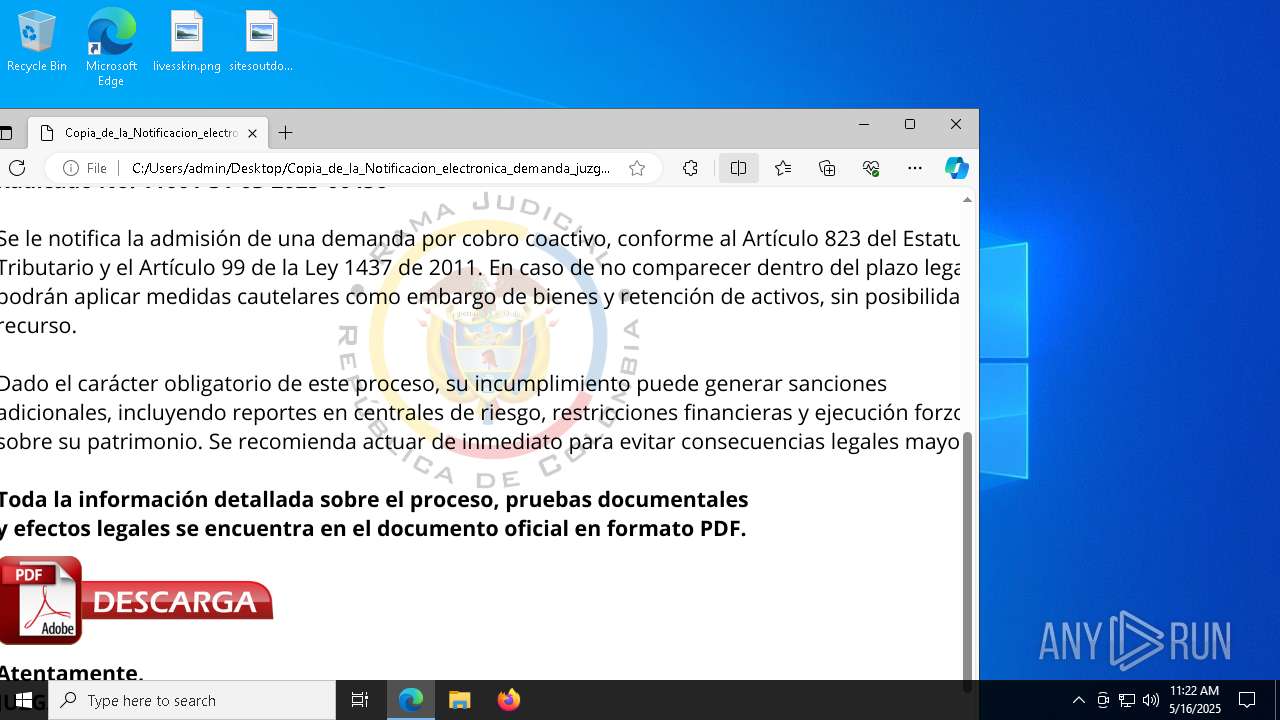
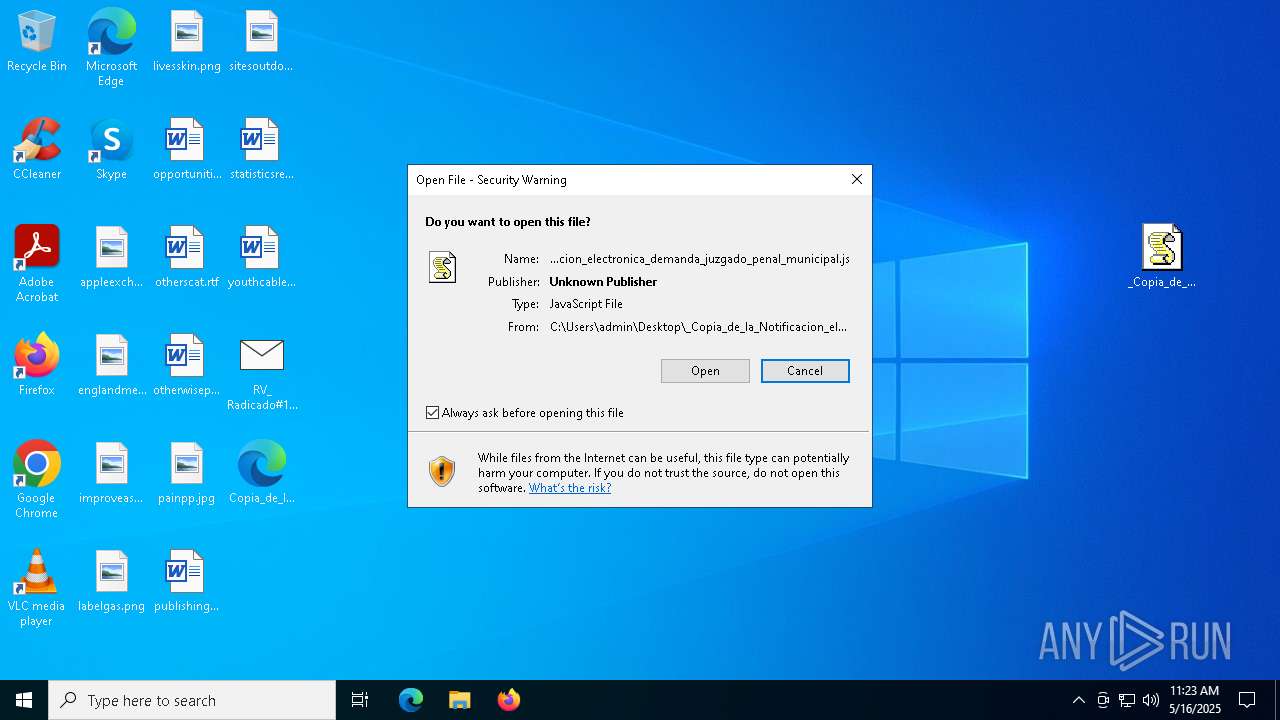
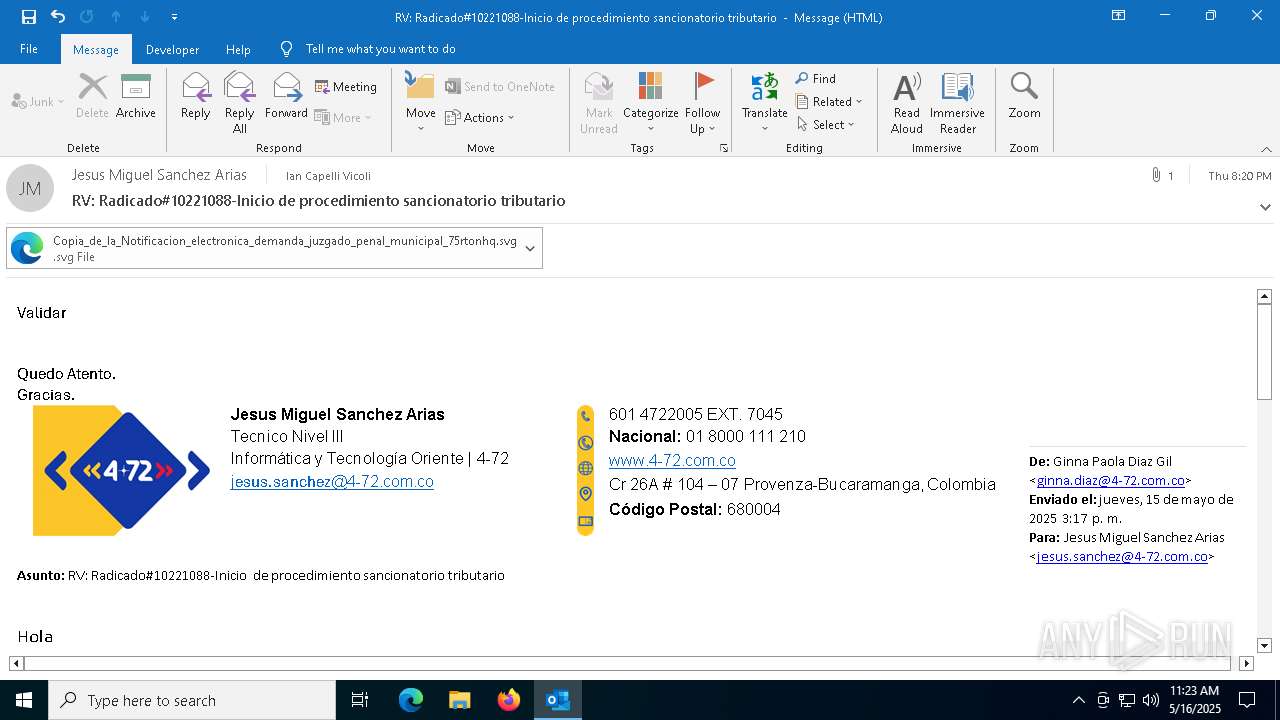
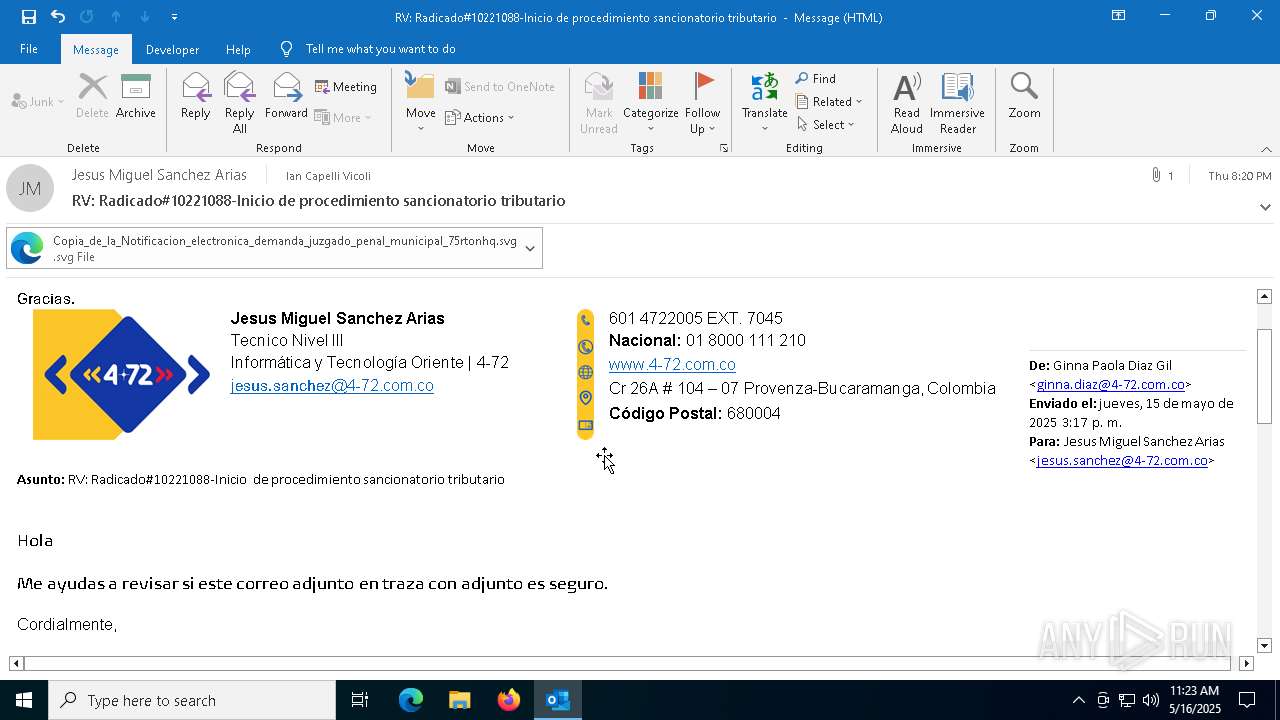
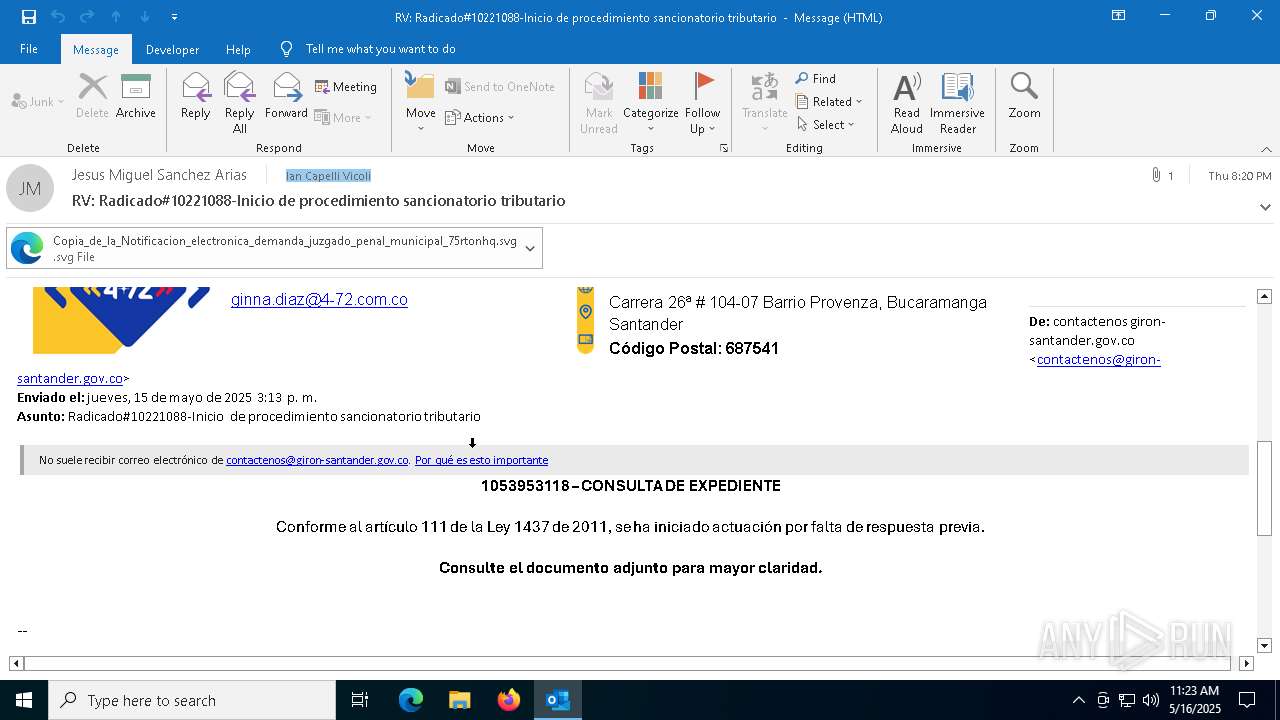
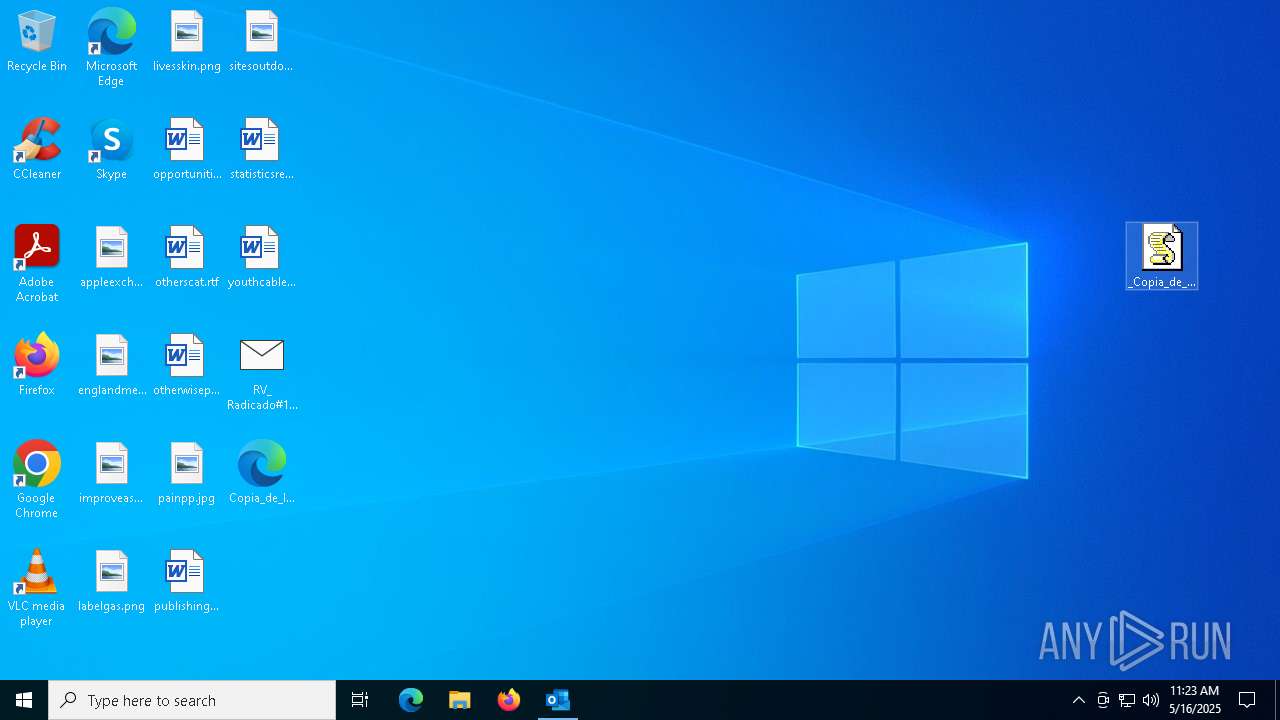
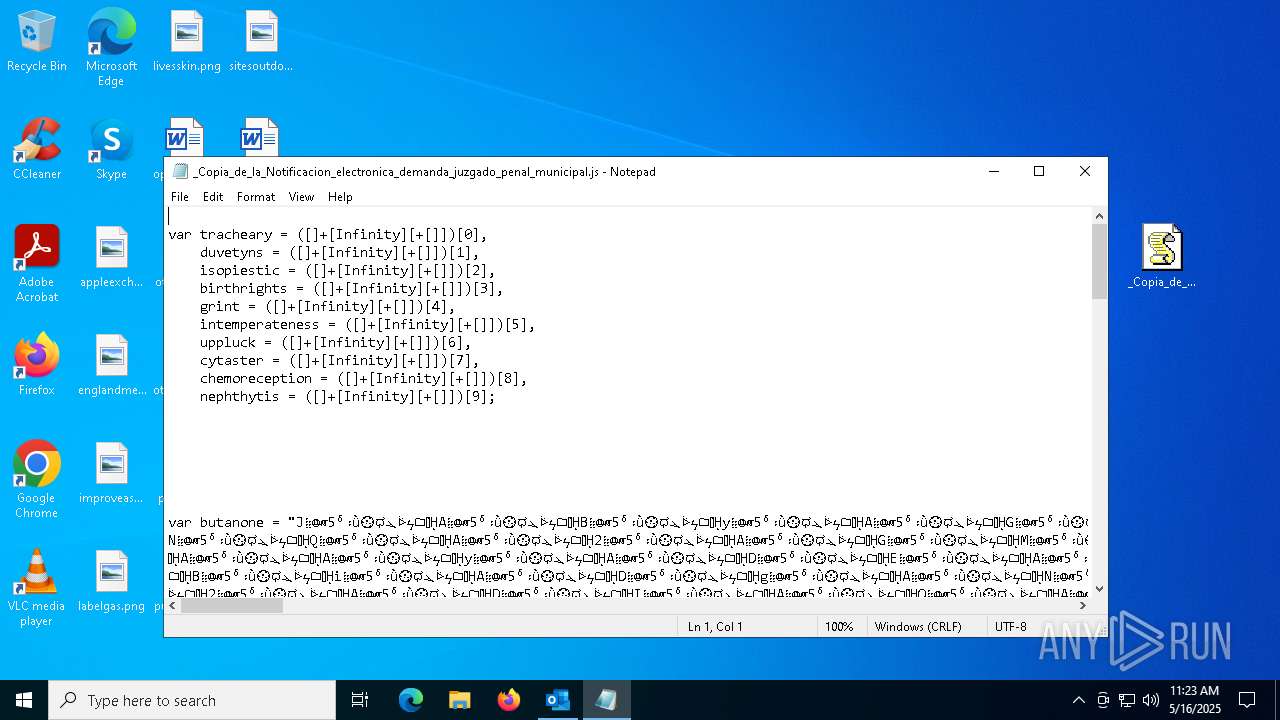
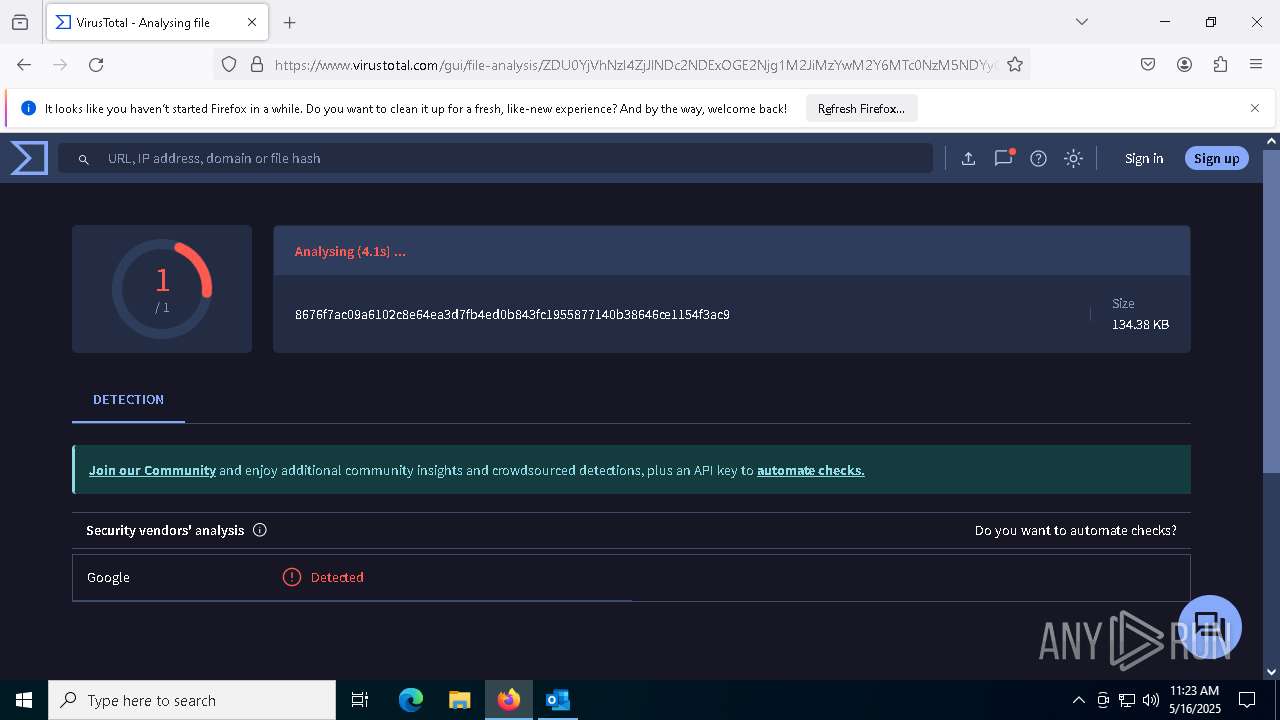
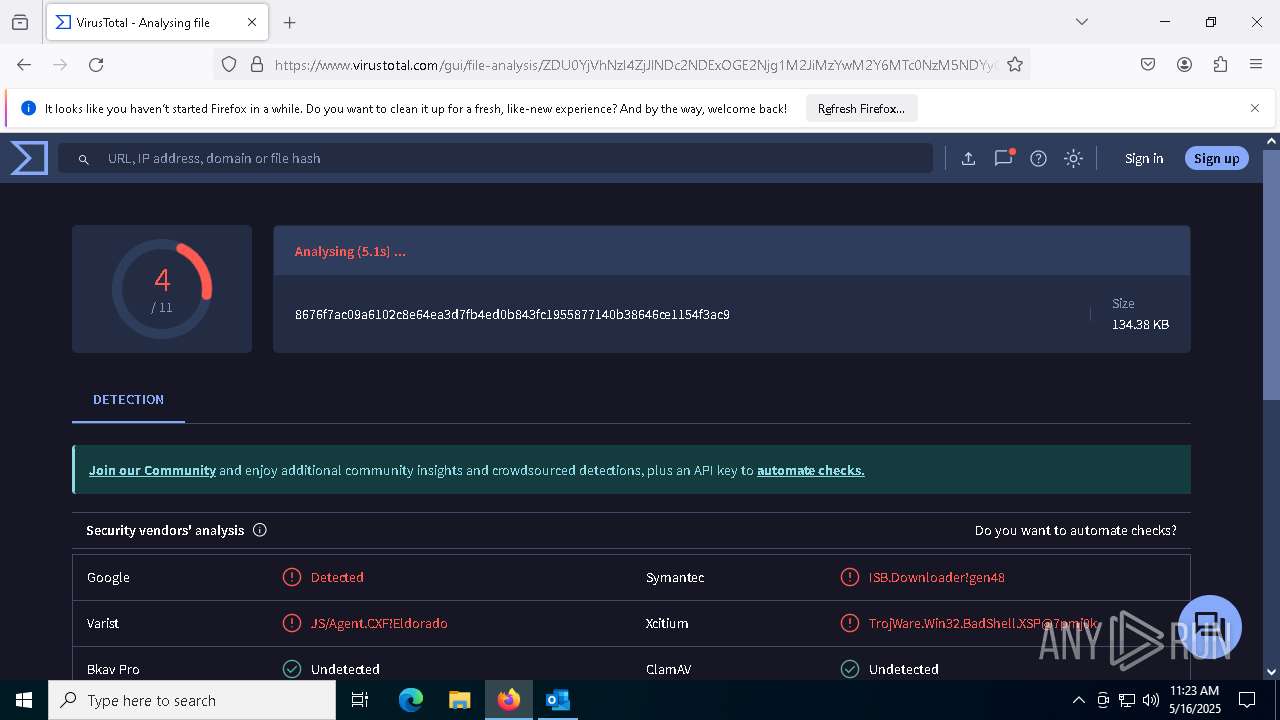
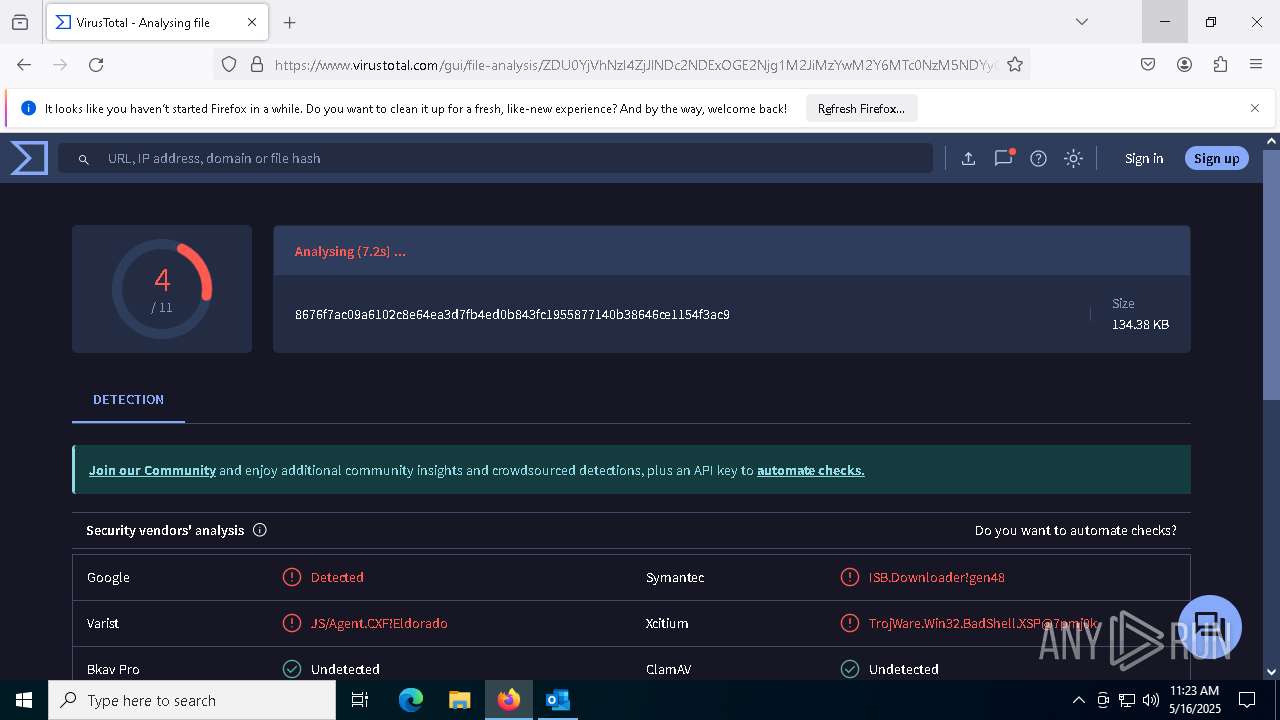
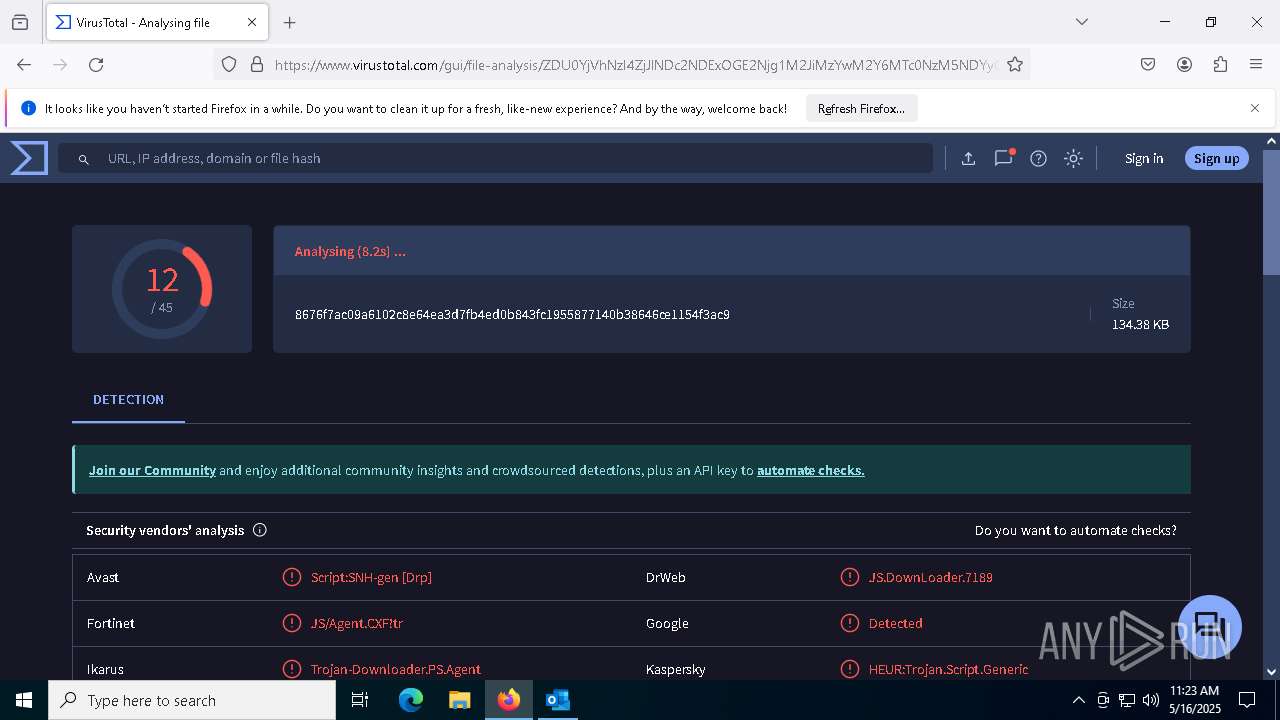
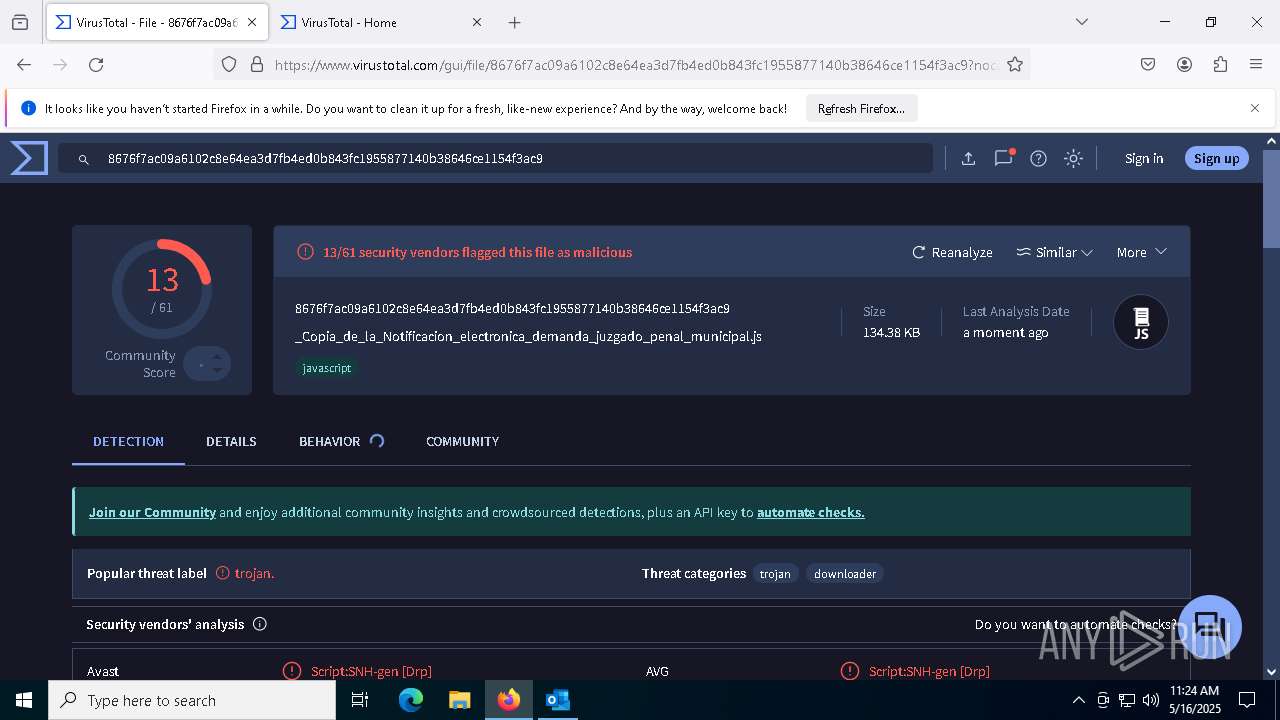
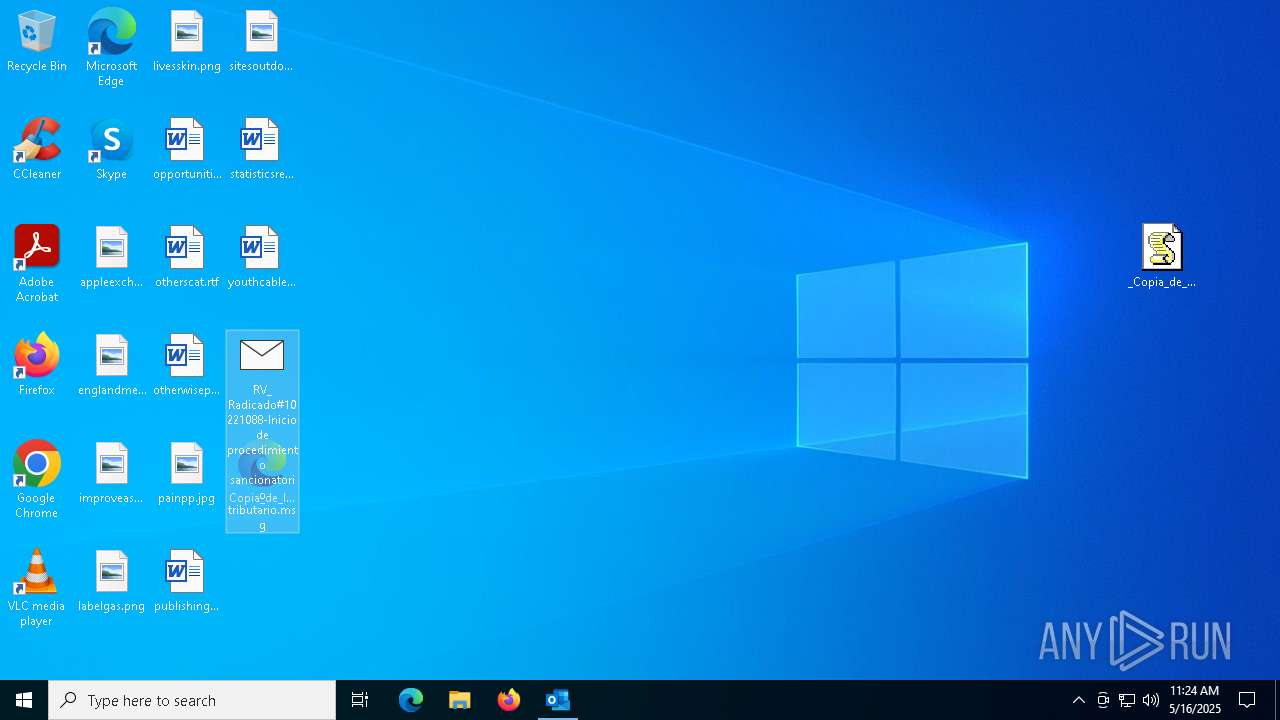
| File name: | RV_ Radicado#10221088-Inicio de procedimiento sancionatorio tributario.msg |
| Full analysis: | https://app.any.run/tasks/984b2ecc-73a2-455f-bcaa-56da448b087a |
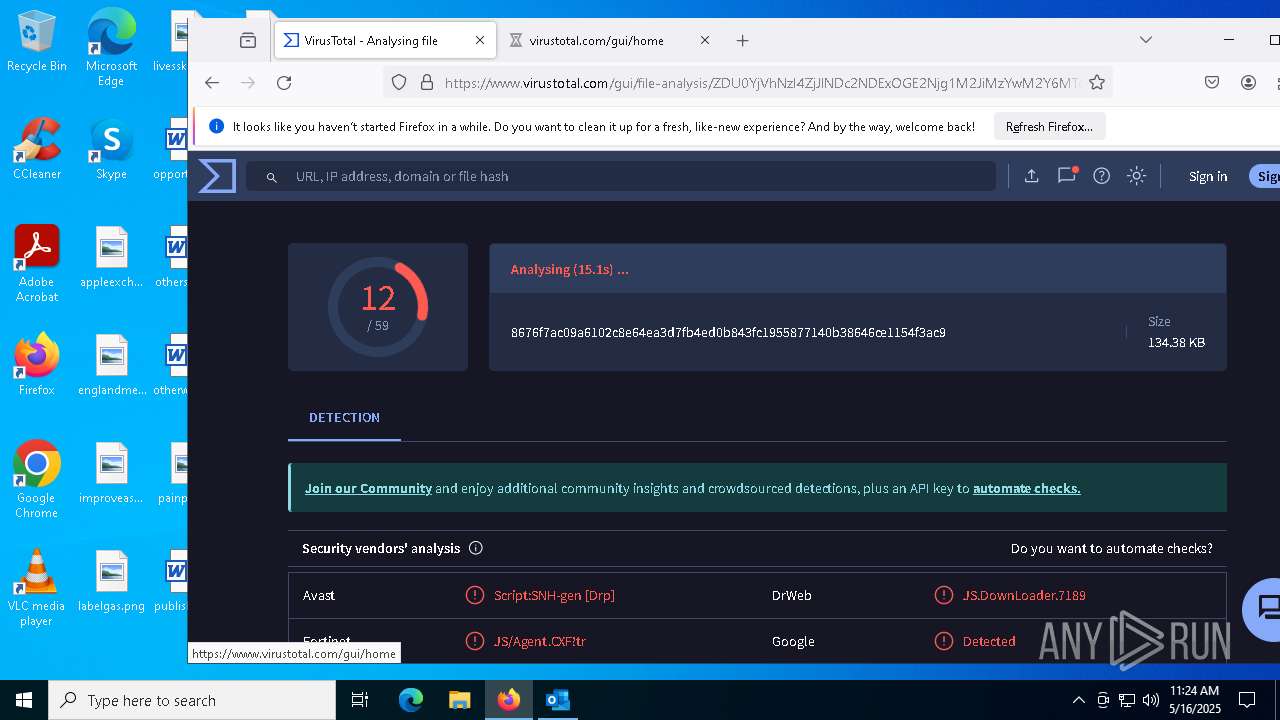
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 16, 2025, 11:21:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 796746A04818EF276A422198A8520924 |
| SHA1: | 294B10B2D7DC51A54A24BFCE14050ED1B7EE5625 |
| SHA256: | D584AB278CEC119F5A6D1E37B6C88A2306AE02FC8FB22F83C50151674D7F11FE |
| SSDEEP: | 24576:ynxwIf6DK3fIosLOnxwIf6DK3fIosLGK:YxUUxUGK |
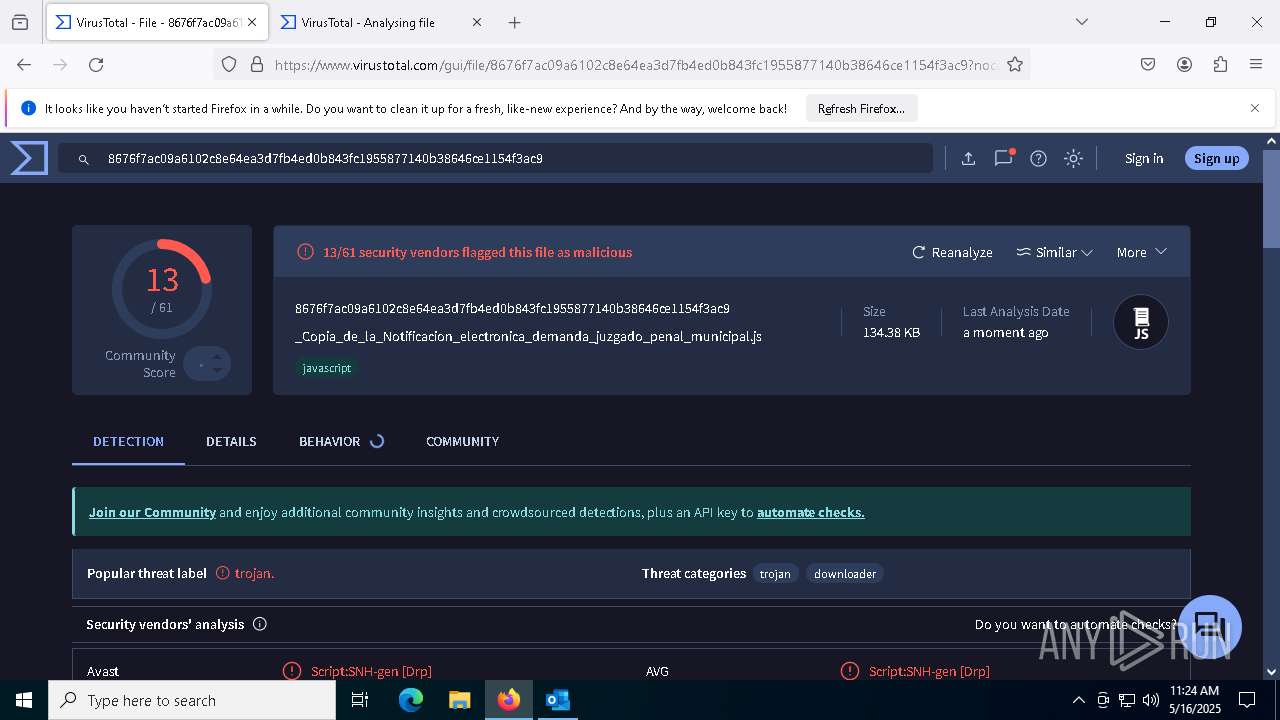
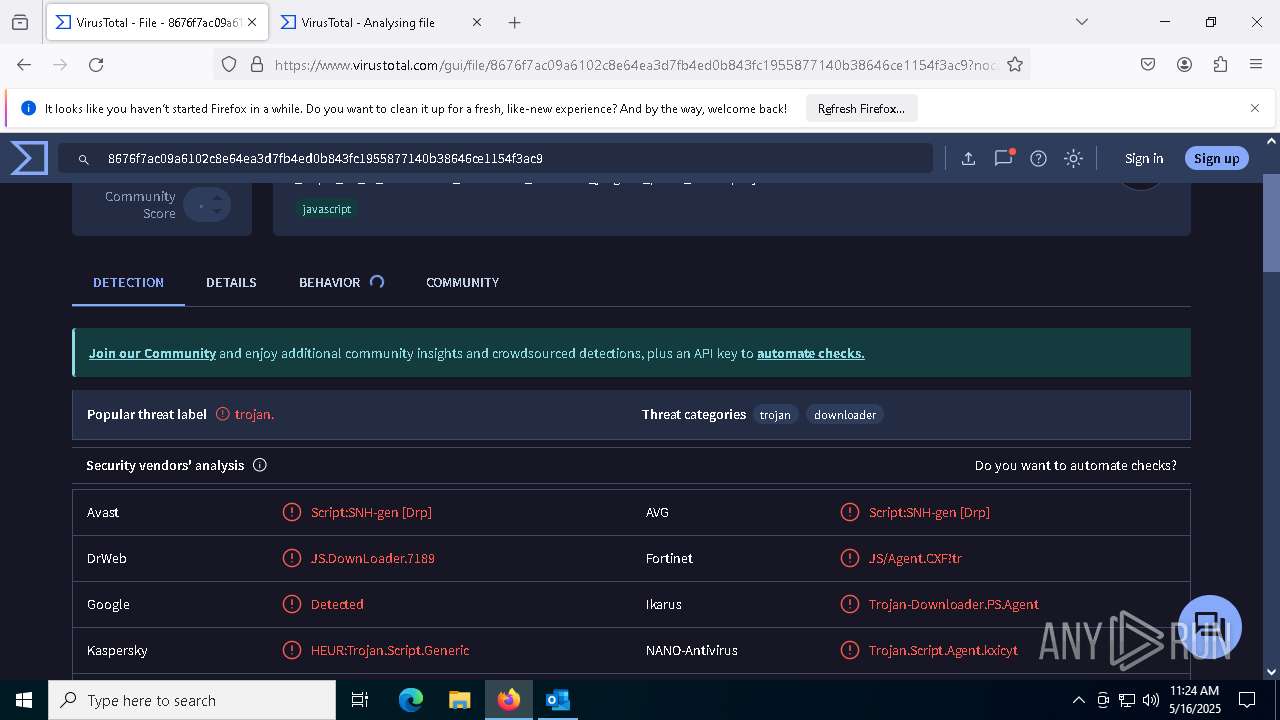
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 7376)
- powershell.exe (PID: 2268)
- powershell.exe (PID: 7540)
- powershell.exe (PID: 9080)
- powershell.exe (PID: 9024)
ASYNCRAT has been detected (YARA)
- MSBuild.exe (PID: 7848)
SUSPICIOUS
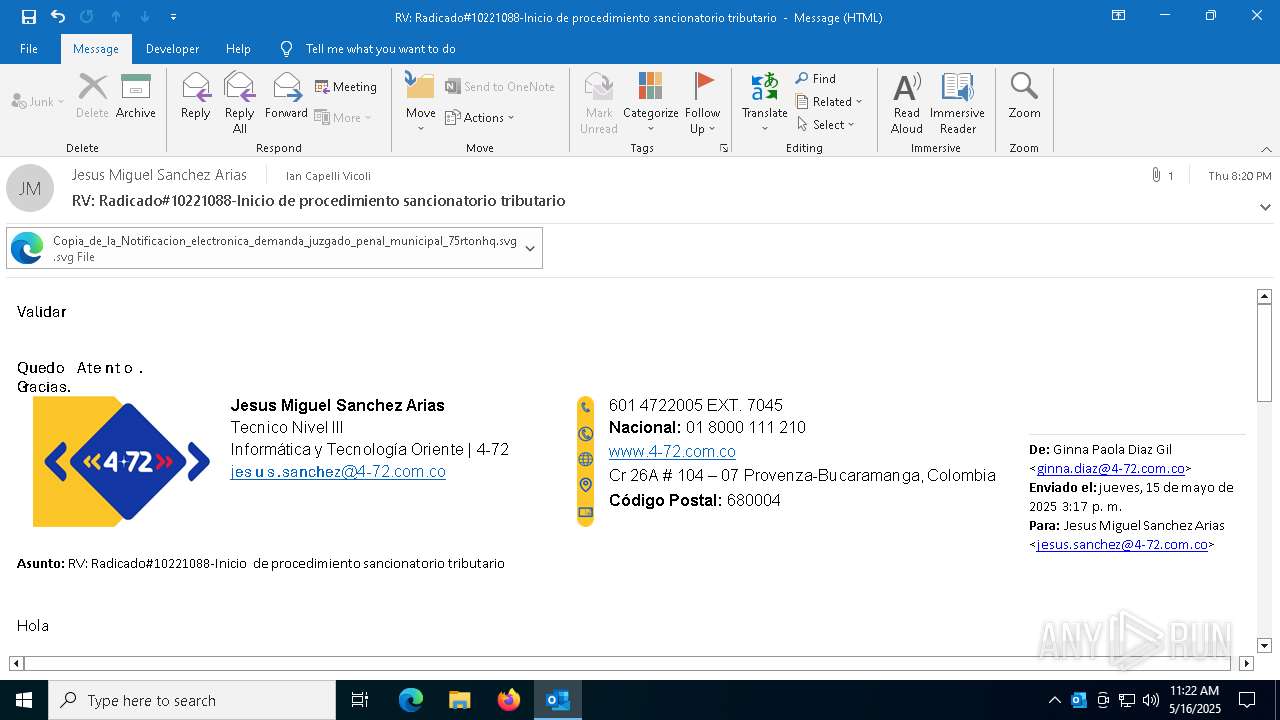
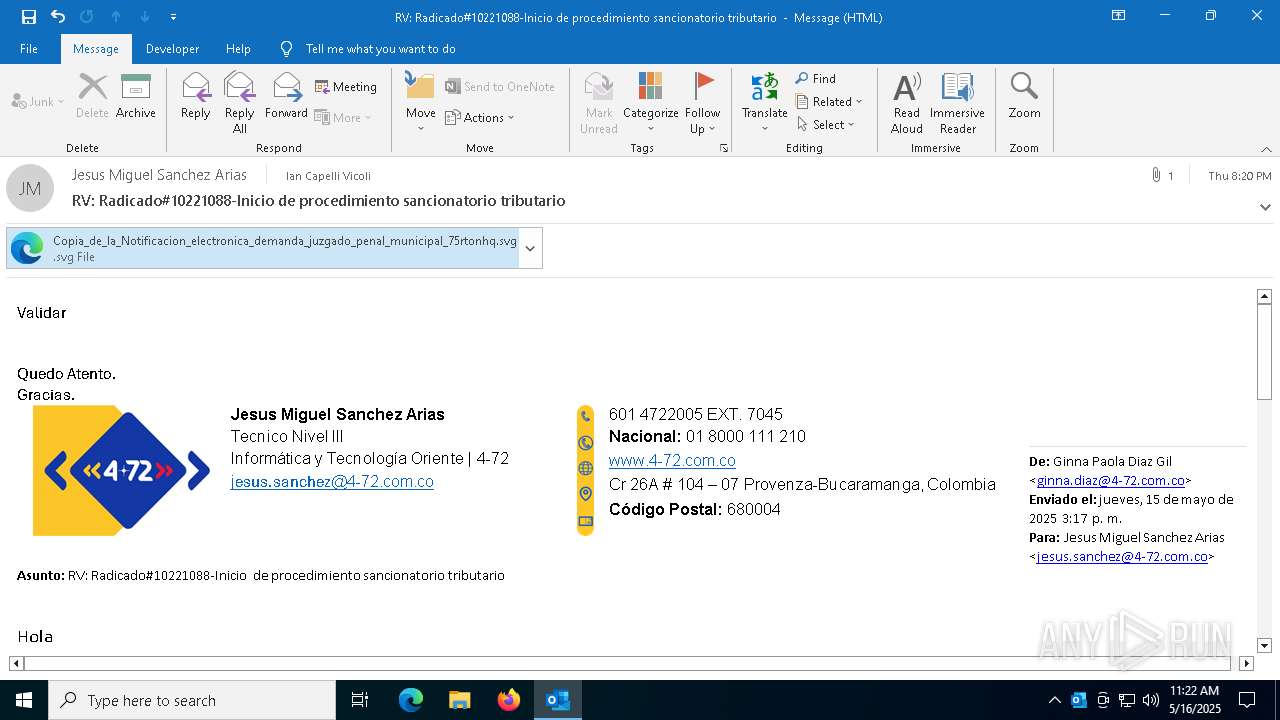
Email with suspicious attachment
- OUTLOOK.EXE (PID: 7412)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 8168)
- wscript.exe (PID: 9200)
- wscript.exe (PID: 7732)
- wscript.exe (PID: 8688)
- wscript.exe (PID: 8976)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 8168)
- wscript.exe (PID: 9200)
- wscript.exe (PID: 7732)
- wscript.exe (PID: 8976)
- wscript.exe (PID: 8688)
Executes script without checking the security policy
- powershell.exe (PID: 7376)
- powershell.exe (PID: 2268)
- powershell.exe (PID: 7540)
- powershell.exe (PID: 9024)
- powershell.exe (PID: 9080)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 8168)
- wscript.exe (PID: 9200)
- wscript.exe (PID: 7732)
- wscript.exe (PID: 8688)
- wscript.exe (PID: 8976)
Base64-obfuscated command line is found
- wscript.exe (PID: 8168)
- wscript.exe (PID: 9200)
- wscript.exe (PID: 7732)
- wscript.exe (PID: 8976)
- wscript.exe (PID: 8688)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 8168)
- wscript.exe (PID: 9200)
- wscript.exe (PID: 7732)
- wscript.exe (PID: 8688)
- wscript.exe (PID: 8976)
Connects to unusual port
- MSBuild.exe (PID: 7848)
INFO
Email with attachments
- OUTLOOK.EXE (PID: 7412)
Checks supported languages
- identity_helper.exe (PID: 6372)
Reads Environment values
- identity_helper.exe (PID: 6372)
Application launched itself
- msedge.exe (PID: 7084)
- msedge.exe (PID: 6480)
- firefox.exe (PID: 6488)
- firefox.exe (PID: 1852)
Reads the computer name
- identity_helper.exe (PID: 6372)
Attempting to use instant messaging service
- msedge.exe (PID: 7912)
- powershell.exe (PID: 7376)
- svchost.exe (PID: 2196)
- powershell.exe (PID: 2268)
- powershell.exe (PID: 7540)
- powershell.exe (PID: 9024)
Manual execution by a user
- wscript.exe (PID: 8168)
- OUTLOOK.EXE (PID: 4844)
- msedge.exe (PID: 7084)
- notepad.exe (PID: 6576)
- firefox.exe (PID: 6488)
- wscript.exe (PID: 9200)
- wscript.exe (PID: 7732)
- wscript.exe (PID: 8688)
- wscript.exe (PID: 8976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(7848) MSBuild.exe
C2 (1)envio14-05.duckdns.org
Ports (1)3000
Version| CRACKED BY https://t.me/xworm_v2
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAOQb7nA/hP/L1XXxqdDJNzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwNTI1MDUyMTIyWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIykAVxs0s6rZ/dwP6ujJtpnj6RSsCsZN6Cfj1InZxSIswX+zNiKJys8xyLlyexoya3ebLp5gOSz...
Server_SignatureZ2Z7R5o1WDTHZ1K32IZfF6UabgyxCS7ZsH3jnRBZzsDOjLFZ9DuZbsL19gHad5Ub4V603oqLA5N+Vw2VuewZfb6WG4JrnE8Pkhq7oulAq4rh2JGpDKpZJkelAvX5zzhT3Vi1Ie6zsbu+Rp5LBarfRp3lEO3At6gwLO3rUJjmFvNxky9rLb5txzHCQf9zThkSQQ/YKvaf6Us8u4J+3cGM6bYcWJtFfWI3Xso3ODIdg690tmCFw7CwmroGe4qIgmFtYGVMoIWke5Ygmp5L20NSrcle8mGiztgDvkWLIjG3r07E...
Keys
AES045bcebd731721e943577af0d62bb83cf9b7889f7e162d53d2b412fb00d0ec83
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
227
Monitored processes
91
Malicious processes
3
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6152 --field-trial-handle=2460,i,11170204957361145622,18261339218131978448,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 680 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=4440 --field-trial-handle=2460,i,11170204957361145622,18261339218131978448,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 856 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3488 --field-trial-handle=2460,i,11170204957361145622,18261339218131978448,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 896 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4324 --field-trial-handle=2460,i,11170204957361145622,18261339218131978448,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 924 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=4348 --field-trial-handle=2728,i,9164526482599959747,2999492404327267287,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1012 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5292 --field-trial-handle=2728,i,9164526482599959747,2999492404327267287,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1012 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1388 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2572 -childID 2 -isForBrowser -prefsHandle 4316 -prefMapHandle 4312 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1488 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {fb26dc07-004c-4799-a93c-e9eca41e22f8} 1852 "\\.\pipe\gecko-crash-server-pipe.1852" 1306ecb1690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1660 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5020 --field-trial-handle=2728,i,9164526482599959747,2999492404327267287,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1676 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3948 --field-trial-handle=2728,i,9164526482599959747,2999492404327267287,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
75 766
Read events
74 312
Write events
1 259
Delete events
195
Modification events
| (PID) Process: | (7412) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (7412) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\7412 |
| Operation: | write | Name: | 0 |
Value: 0B0E10393792897C08D14CB711CB5882D42D6A230046CEE0F2ABCCCAF1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511F439D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7412) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (7412) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (7412) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7412) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (7412) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (7412) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (7412) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (7412) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
7
Suspicious files
371
Text files
120
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7412 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7412 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:05D14B931F2F17C1E54212CC83A26B55 | SHA256:ED57696AE9783596C202A4873BAC4DEC144AFA6DE592323EBC04AFA840E8A1D4 | |||
| 7412 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:0EC0DE596CE0CF445EE32A9823E7B054 | SHA256:375F745FDE3F752A43645C20A39E56484D7F0207195155DB5D30FEBF1E8A7BDA | |||
| 7412 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\CloudFonts\Aptos\30153066857.ttf | binary | |
MD5:1250B2192733FA4D140AB32D9D31FBA1 | SHA256:95980114FCFD42F2F9C446DAE429B70582BF2F03097D68433EA9E7D85A49DA0B | |||
| 7412 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_A934FCCF4997374792AC7803906378AF.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 7412 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:132C05CC6DF7D9B00A89542FBF5F68E5 | SHA256:A8771DB566B4ABDB7D2C5F40B181B72466BA05CD8417248D8EA40DAB584697B4 | |||
| 7412 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\CatalogCacheMetaData.xml | xml | |
MD5:7357CECC31985ABD47D57FCEB8BD7EC9 | SHA256:96A958B115490C4E74A037B79E0BED7ECD91E779FFA32876E5DC52B9F9814DD1 | |||
| 7412 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:E62EFE7288ABCE3321A890EAAD8D8E9E | SHA256:A0F87CD29721837A844306B7CDB225C4BFFA893C090F4C6C9A94CFC4F783F0AF | |||
| 7412 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\E0E8CAE7.dat | image | |
MD5:6A42BAB266A74B0CE1E497F3BB832395 | SHA256:784BC9ED168F5BBB5B9F2D7C45A56691A61E71954E3D0193B30E35C7331BE0FC | |||
| 7412 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
69
TCP/UDP connections
197
DNS requests
213
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7412 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7412 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2108 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2108 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1852 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1852 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1852 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7412 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7412 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7412 | OUTLOOK.EXE | 23.212.222.21:443 | fs.microsoft.com | AKAMAI-AS | AU | whitelisted |
7412 | OUTLOOK.EXE | 52.109.28.47:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7912 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
7912 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
7376 | powershell.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |