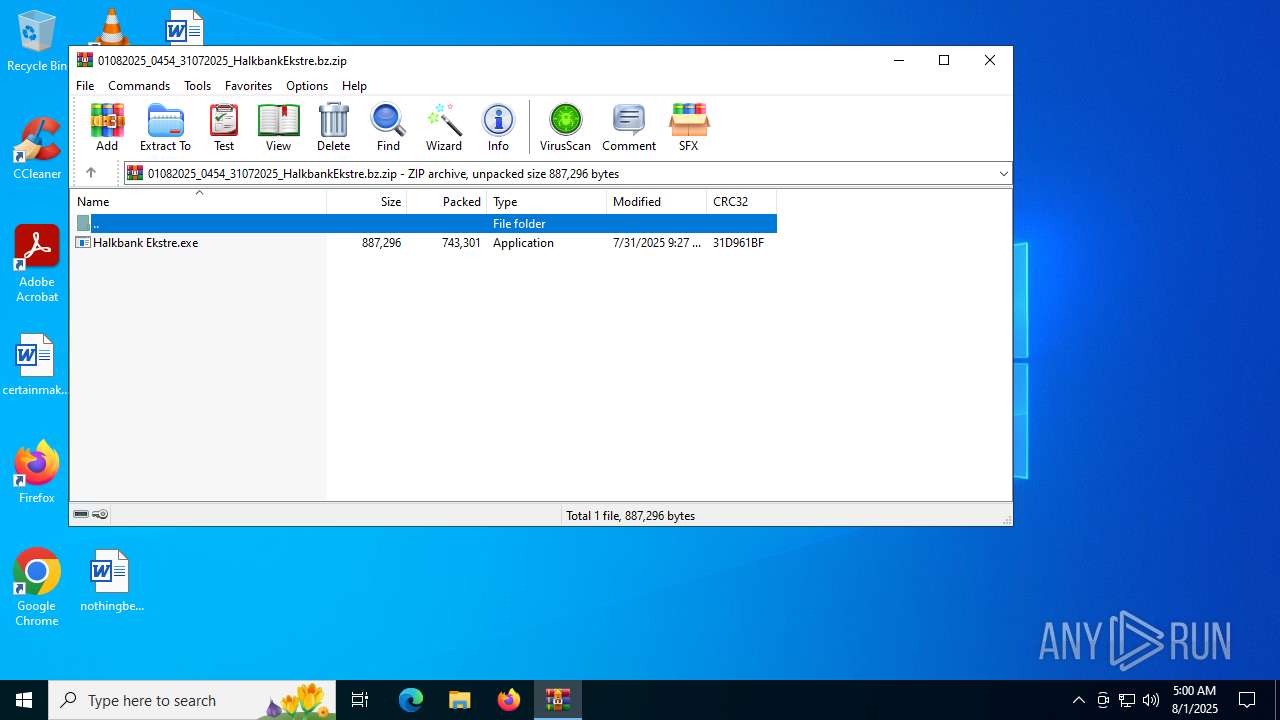
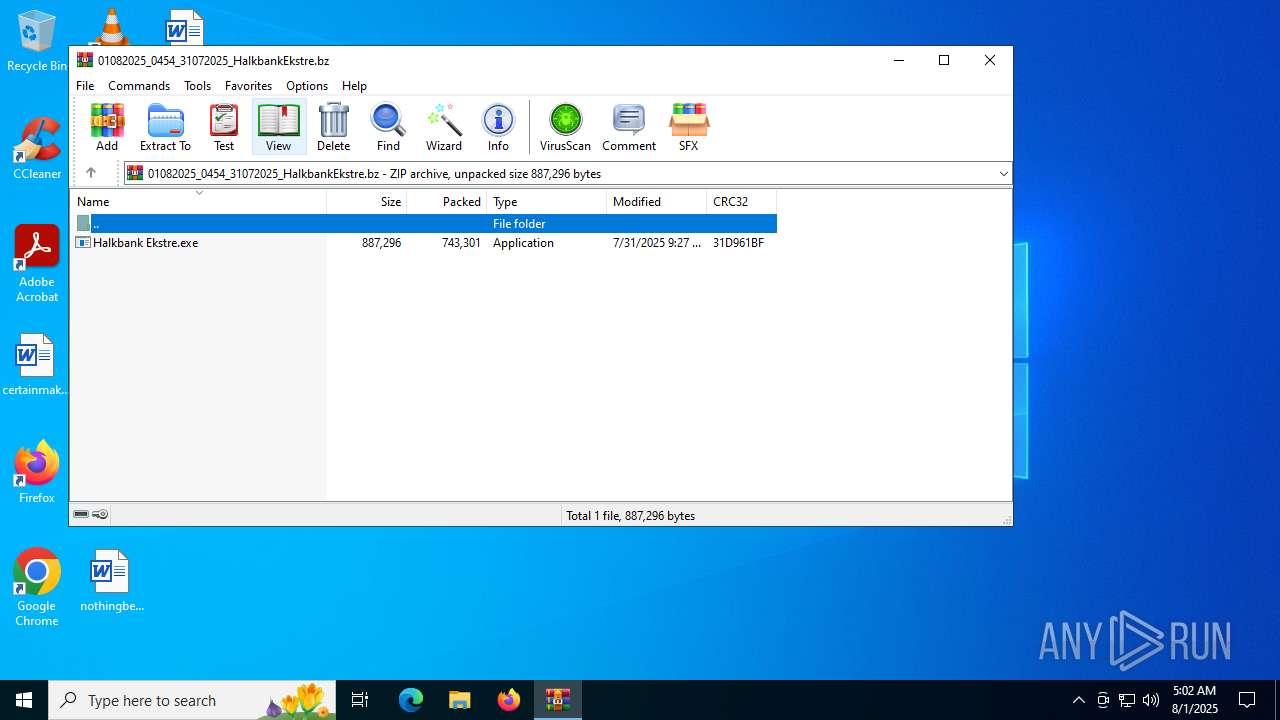
| File name: | 01082025_0454_31072025_HalkbankEkstre.bz |
| Full analysis: | https://app.any.run/tasks/a81c44cf-c08e-4292-a365-b51b57842089 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | August 01, 2025, 05:00:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F4FF9A6A4609221D343E5DCFBE0CED08 |
| SHA1: | 53B4F0A3D5A9AC647C58DACEB6E1F70B25058406 |
| SHA256: | D518E1B17C5B3E0B00A0373E5668E8A613C417CDC7DB11D3F47DF4300FE500A3 |
| SSDEEP: | 24576:IpjQ+d2MJB+FBLVvTv+tzIw9Xc3enelsEkLmRYCi9LAH/QE/7OHvmelNaYe2PCK4:Ipk+d2MJB+FBLVLv+tzIw9XmenelFkLw |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4748)
Uses Task Scheduler to run other applications
- Halkbank Ekstre.exe (PID: 6412)
- gPxubmX.exe (PID: 1216)
Actions looks like stealing of personal data
- Halkbank Ekstre.exe (PID: 6012)
- gPxubmX.exe (PID: 424)
Steals credentials from Web Browsers
- Halkbank Ekstre.exe (PID: 6012)
- gPxubmX.exe (PID: 424)
AGENTTESLA has been detected (YARA)
- Halkbank Ekstre.exe (PID: 6012)
- gPxubmX.exe (PID: 424)
SUSPICIOUS
Application launched itself
- Halkbank Ekstre.exe (PID: 6412)
- gPxubmX.exe (PID: 1216)
Connects to SMTP port
- Halkbank Ekstre.exe (PID: 6012)
- gPxubmX.exe (PID: 424)
Reads security settings of Internet Explorer
- Halkbank Ekstre.exe (PID: 6412)
- WinRAR.exe (PID: 4748)
- gPxubmX.exe (PID: 1216)
Executable content was dropped or overwritten
- Halkbank Ekstre.exe (PID: 6412)
INFO
Manual execution by a user
- Halkbank Ekstre.exe (PID: 6412)
- gPxubmX.exe (PID: 1216)
Reads the computer name
- Halkbank Ekstre.exe (PID: 6412)
- Halkbank Ekstre.exe (PID: 6012)
- gPxubmX.exe (PID: 1216)
- gPxubmX.exe (PID: 424)
Reads the machine GUID from the registry
- Halkbank Ekstre.exe (PID: 6412)
- Halkbank Ekstre.exe (PID: 6012)
- gPxubmX.exe (PID: 1216)
- gPxubmX.exe (PID: 424)
Checks supported languages
- Halkbank Ekstre.exe (PID: 6012)
- gPxubmX.exe (PID: 1216)
- gPxubmX.exe (PID: 424)
- Halkbank Ekstre.exe (PID: 6412)
Process checks computer location settings
- Halkbank Ekstre.exe (PID: 6412)
- gPxubmX.exe (PID: 1216)
ULTRAVNC has been detected
- Halkbank Ekstre.exe (PID: 6012)
- gPxubmX.exe (PID: 424)
Create files in a temporary directory
- gPxubmX.exe (PID: 1216)
- Halkbank Ekstre.exe (PID: 6412)
Checks proxy server information
- slui.exe (PID: 5348)
Reads the software policy settings
- slui.exe (PID: 5348)
Creates files or folders in the user directory
- Halkbank Ekstre.exe (PID: 6412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(6012) Halkbank Ekstre.exe
Protocolsmtp
Hostmail.blade.com.tr
Port587
Usernameinfo@blade.com.tr
PasswordePsiTp=DT4
(PID) Process(424) gPxubmX.exe
Protocolsmtp
Hostmail.blade.com.tr
Port587
Usernameinfo@blade.com.tr
PasswordePsiTp=DT4
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:31 02:27:20 |
| ZipCRC: | 0x31d961bf |
| ZipCompressedSize: | 743301 |
| ZipUncompressedSize: | 887296 |
| ZipFileName: | Halkbank Ekstre.exe |
Total processes
143
Monitored processes
10
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 424 | "C:\Users\admin\AppData\Roaming\gPxubmX.exe" | C:\Users\admin\AppData\Roaming\gPxubmX.exe | gPxubmX.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Analyze Graphics Version: 4.0.0.0 Modules
AgentTesla(PID) Process(424) gPxubmX.exe Protocolsmtp Hostmail.blade.com.tr Port587 Usernameinfo@blade.com.tr PasswordePsiTp=DT4 | |||||||||||||||
| 1216 | "C:\Users\admin\AppData\Roaming\gPxubmX.exe" | C:\Users\admin\AppData\Roaming\gPxubmX.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Analyze Graphics Exit code: 0 Version: 4.0.0.0 Modules
| |||||||||||||||
| 1612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4708 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\gPxubmX" /XML "C:\Users\admin\AppData\Local\Temp\tmp87A5.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | gPxubmX.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4748 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\01082025_0454_31072025_HalkbankEkstre.bz.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5348 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6012 | "C:\Users\admin\Desktop\Halkbank Ekstre.exe" | C:\Users\admin\Desktop\Halkbank Ekstre.exe | Halkbank Ekstre.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Analyze Graphics Version: 4.0.0.0 Modules
AgentTesla(PID) Process(6012) Halkbank Ekstre.exe Protocolsmtp Hostmail.blade.com.tr Port587 Usernameinfo@blade.com.tr PasswordePsiTp=DT4 | |||||||||||||||
| 6412 | "C:\Users\admin\Desktop\Halkbank Ekstre.exe" | C:\Users\admin\Desktop\Halkbank Ekstre.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Analyze Graphics Exit code: 0 Version: 4.0.0.0 Modules
| |||||||||||||||
| 7152 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\gPxubmX" /XML "C:\Users\admin\AppData\Local\Temp\tmp2E0B.tmp" | C:\Windows\SysWOW64\schtasks.exe | — | Halkbank Ekstre.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 565
Read events
7 541
Write events
24
Delete events
0
Modification events
| (PID) Process: | (4748) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4748) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4748) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4748) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\01082025_0454_31072025_HalkbankEkstre.bz.zip | |||
| (PID) Process: | (4748) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4748) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4748) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4748) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4748) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (4748) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
1
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1216 | gPxubmX.exe | C:\Users\admin\AppData\Local\Temp\tmp87A5.tmp | xml | |
MD5:2474E167FF1E2903A7901C788A90CB64 | SHA256:44996D764810128DEEE910E38BEE84FA86248AEC6DF88A46B8A53129E6CF83EE | |||
| 6412 | Halkbank Ekstre.exe | C:\Users\admin\AppData\Local\Temp\tmp2E0B.tmp | xml | |
MD5:2474E167FF1E2903A7901C788A90CB64 | SHA256:44996D764810128DEEE910E38BEE84FA86248AEC6DF88A46B8A53129E6CF83EE | |||
| 6412 | Halkbank Ekstre.exe | C:\Users\admin\AppData\Roaming\gPxubmX.exe | executable | |
MD5:55F55A99154FC12F2EAF55CD2D6A1961 | SHA256:C2F7724DB607D9C550E1F5BE3EE7FBB199DE5EBB97029F0EEE7832803F756959 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
42
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4024 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4024 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.129:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.160.65:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.32.72:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4024 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4024 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4024 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
mail.blade.com.tr |
| unknown |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |