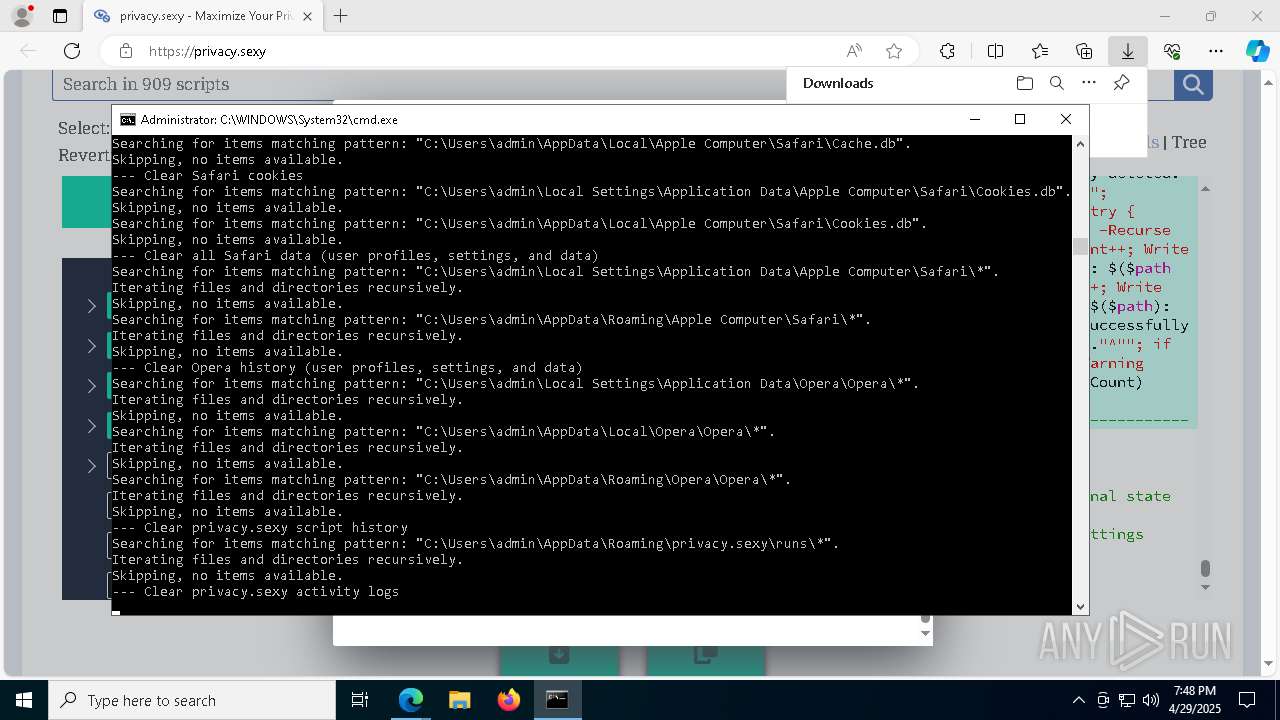
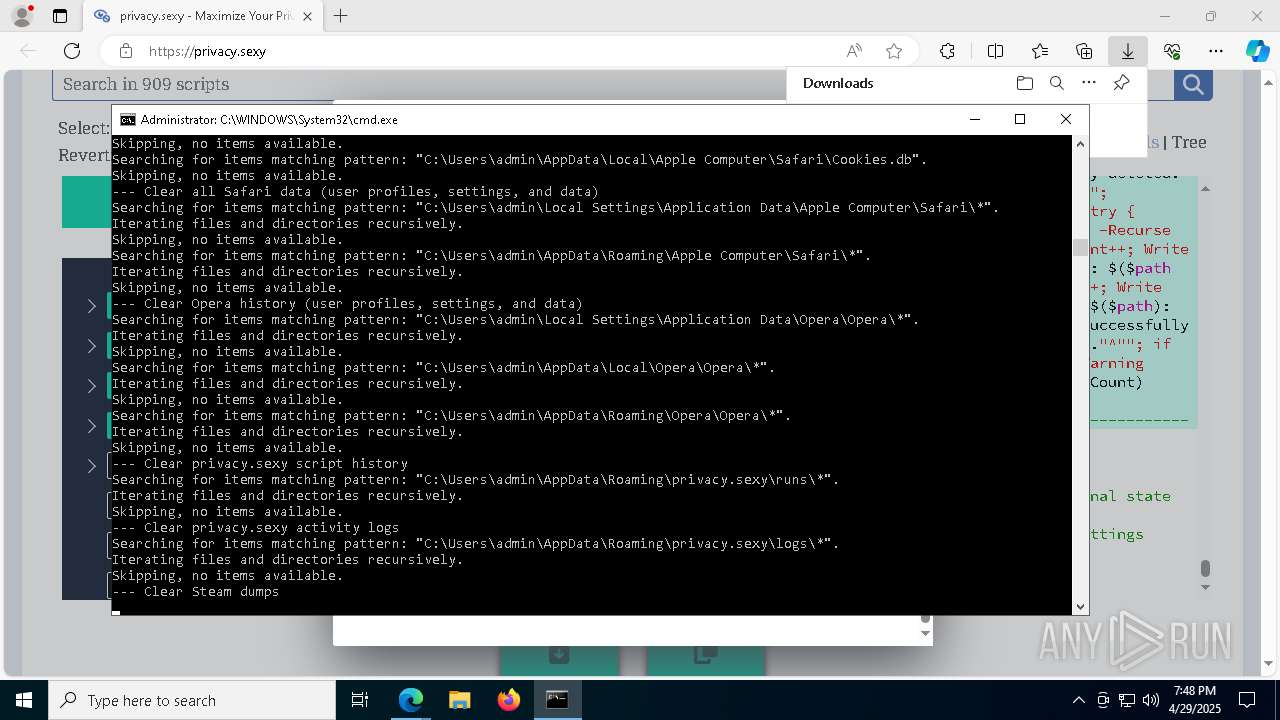
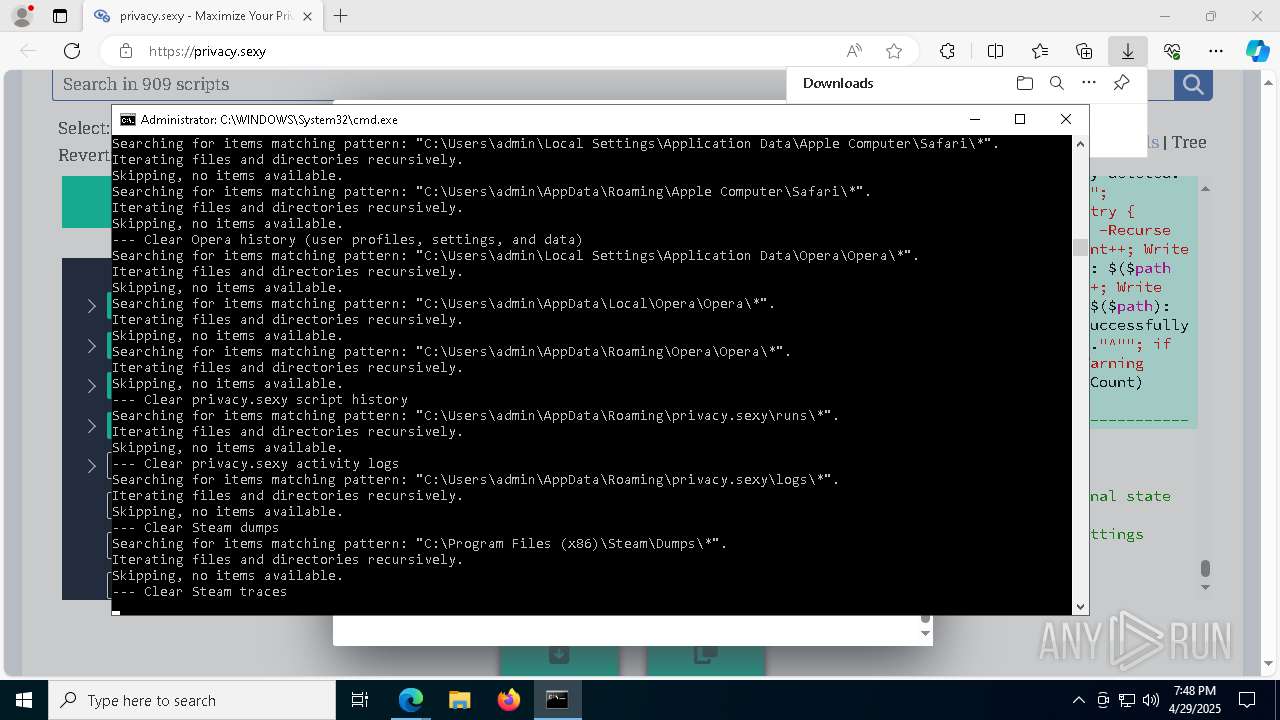
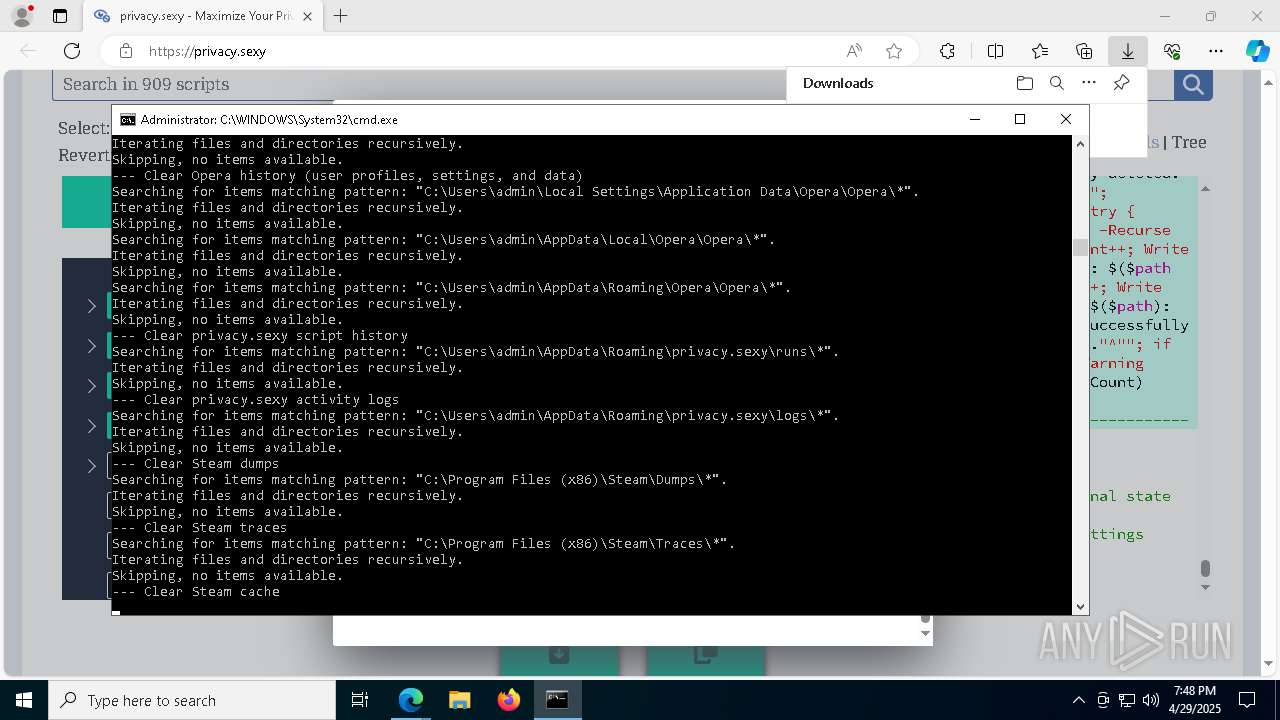
| URL: | https://privacy.sexy/ |
| Full analysis: | https://app.any.run/tasks/f25db8c9-3e8b-4800-a687-d1b7e03e48be |
| Verdict: | Malicious activity |
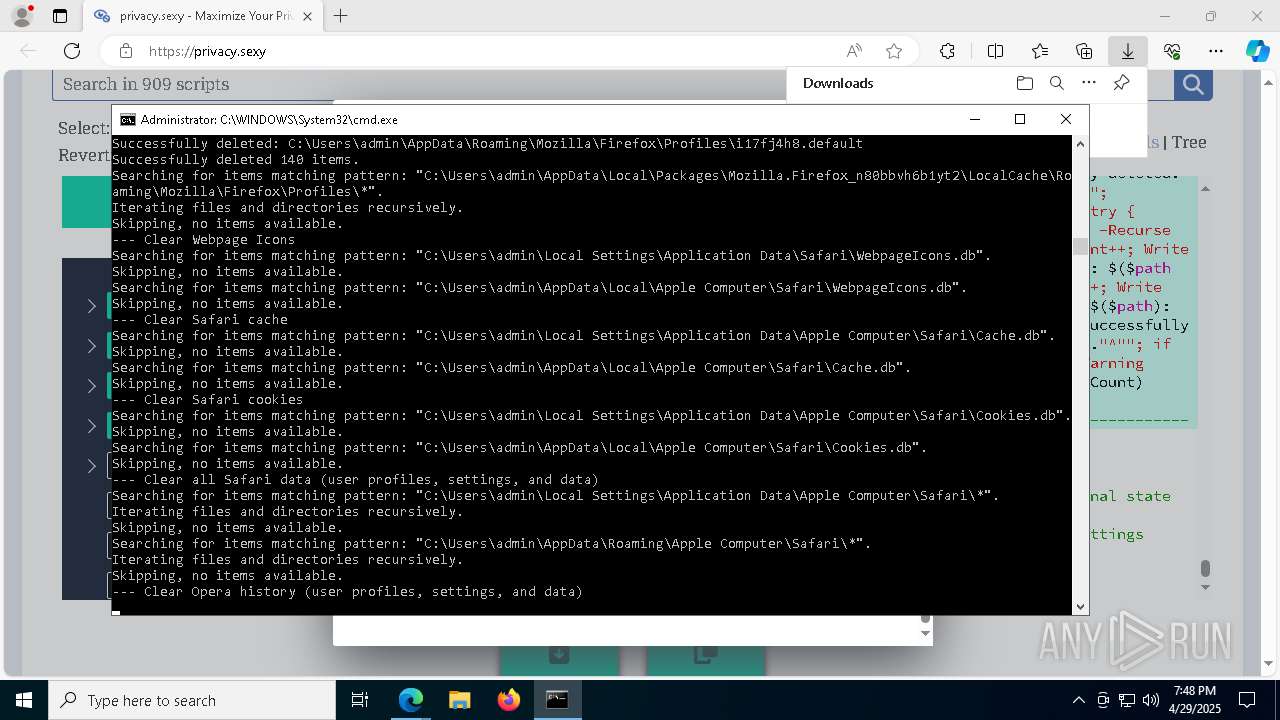
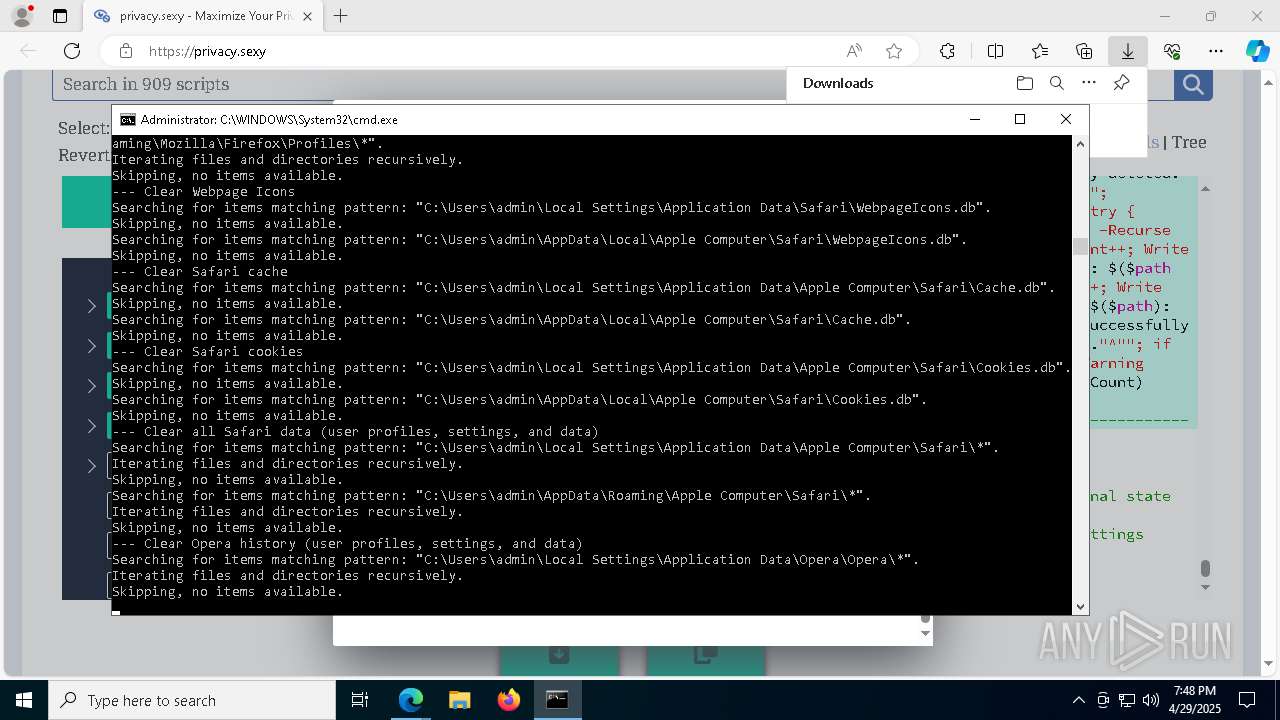
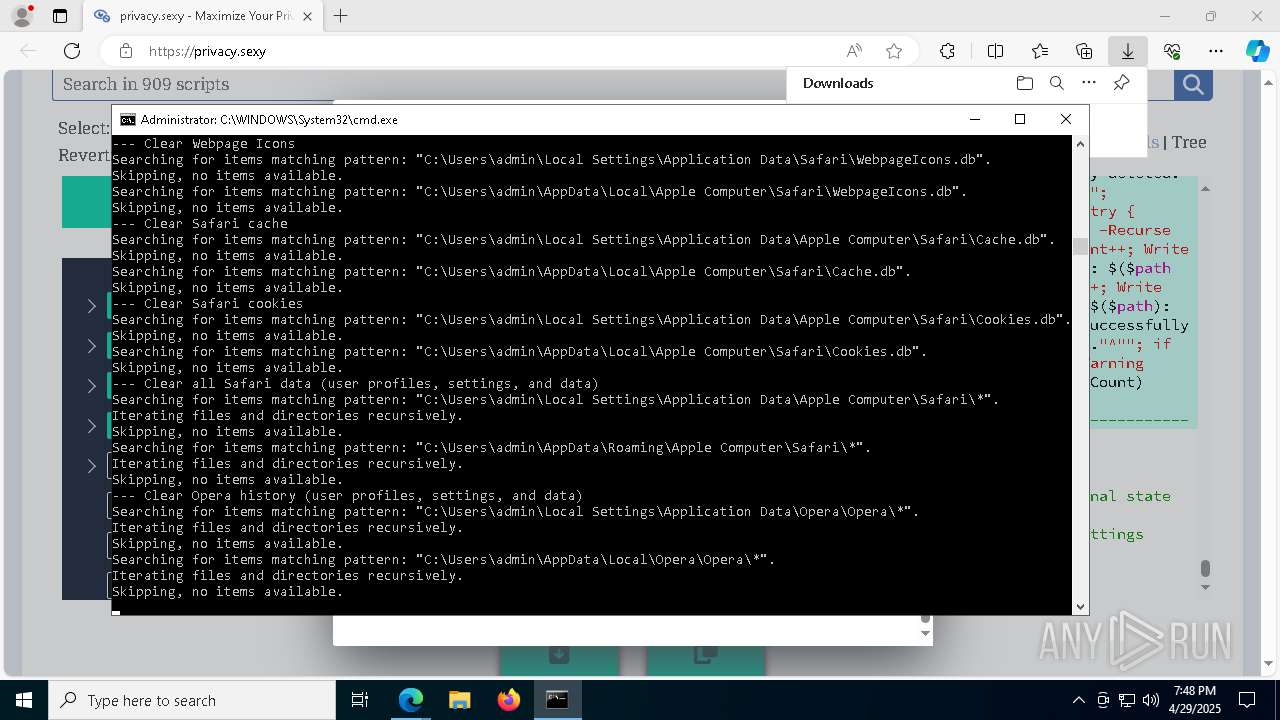
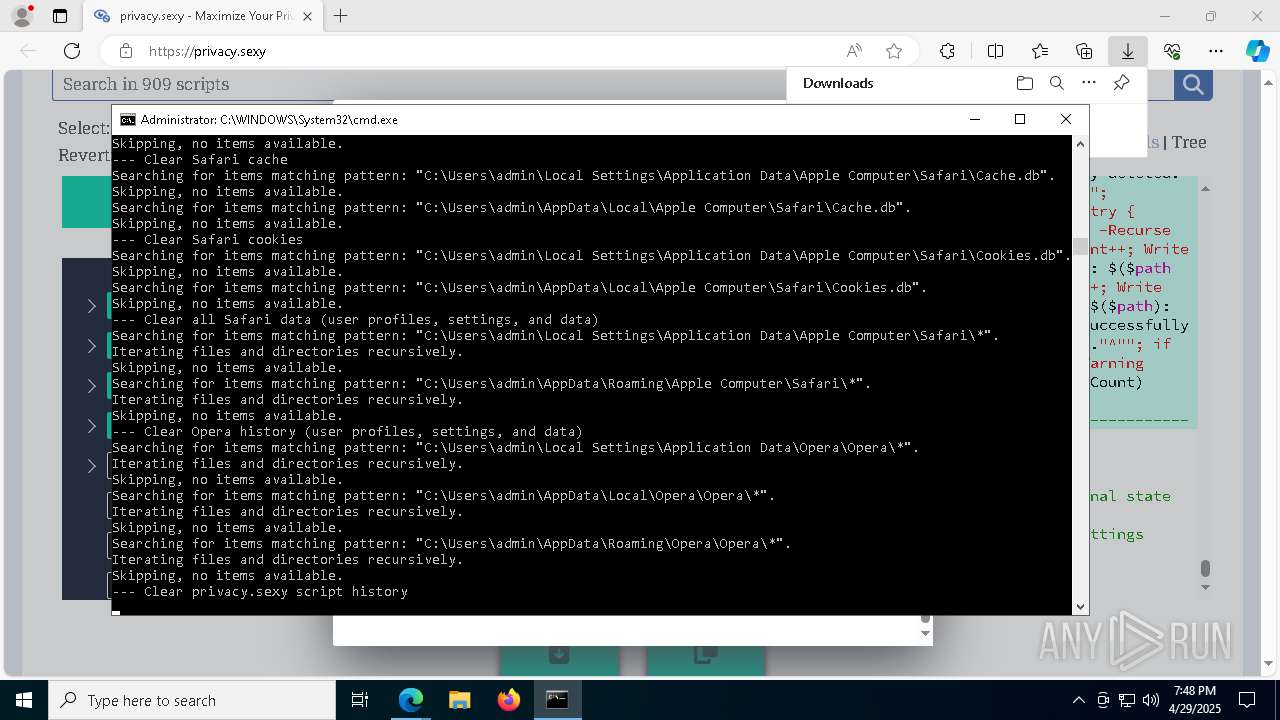
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | April 29, 2025, 19:44:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E129D0115610C3CE2696BB4DE42B3C3C |
| SHA1: | 7D62F73A086B69EFD4876F479E87EBB5F4A3B615 |
| SHA256: | D4F8B50CD8781C04B705C090D8510B1BEA7491C1D19FB3DA1C616F6F54A62E16 |
| SSDEEP: | 3:N8TMILis:2B |
MALICIOUS
GUMEN has been detected
- powershell.exe (PID: 3396)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 7432)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 6072)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7828)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 4896)
- powershell.exe (PID: 5328)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 4268)
- powershell.exe (PID: 472)
- powershell.exe (PID: 2344)
- powershell.exe (PID: 5172)
- powershell.exe (PID: 1748)
- powershell.exe (PID: 6900)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 3896)
- powershell.exe (PID: 7976)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 5512)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 5164)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 5892)
- powershell.exe (PID: 7412)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4180)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 2564)
- powershell.exe (PID: 7684)
- powershell.exe (PID: 5592)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 132)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 2596)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 6808)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 4728)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 632)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 7008)
- powershell.exe (PID: 5024)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 2332)
- powershell.exe (PID: 4304)
- powershell.exe (PID: 7548)
- powershell.exe (PID: 6036)
- powershell.exe (PID: 6456)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 7408)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 1748)
Detected an obfuscated command line used with Guloader
- powershell.exe (PID: 3396)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 7432)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 6072)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 7828)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 4896)
- powershell.exe (PID: 5328)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 4268)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4180)
- powershell.exe (PID: 7684)
- powershell.exe (PID: 5592)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 132)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 2596)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 6808)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 4728)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 7008)
- powershell.exe (PID: 632)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 5024)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 4304)
- powershell.exe (PID: 7548)
- powershell.exe (PID: 2332)
- powershell.exe (PID: 6036)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 6456)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 7408)
- powershell.exe (PID: 1748)
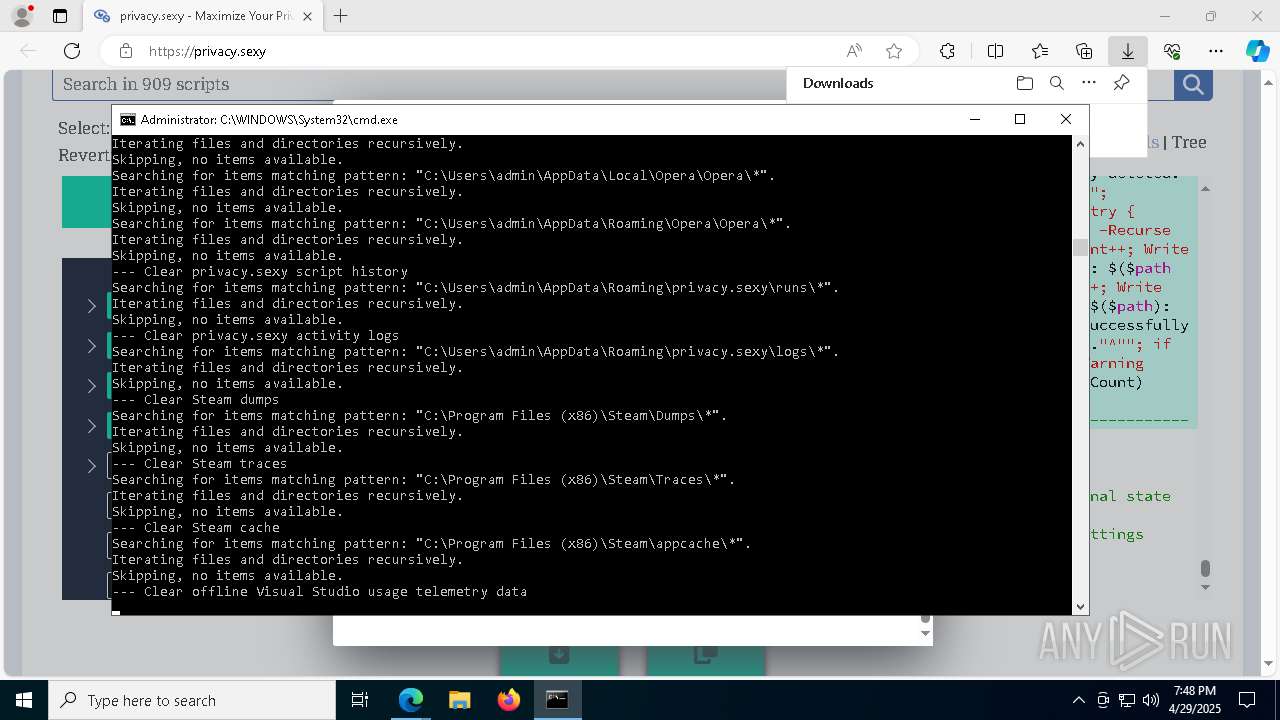
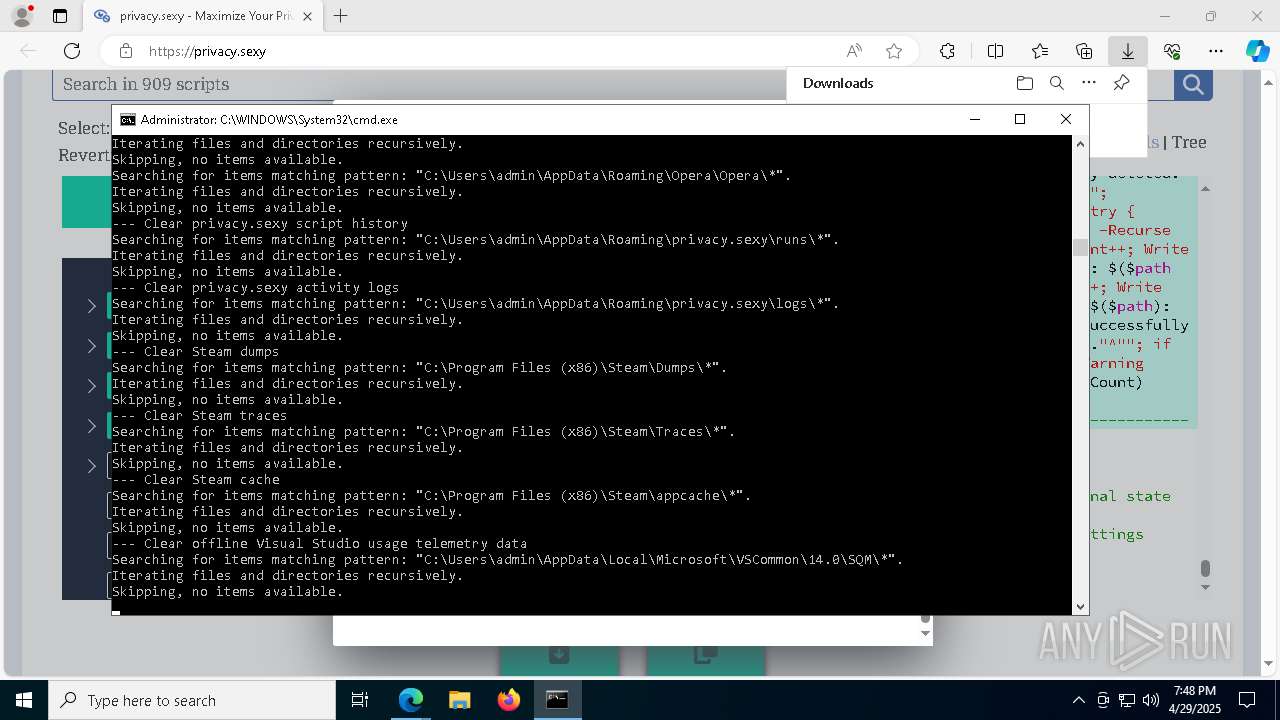
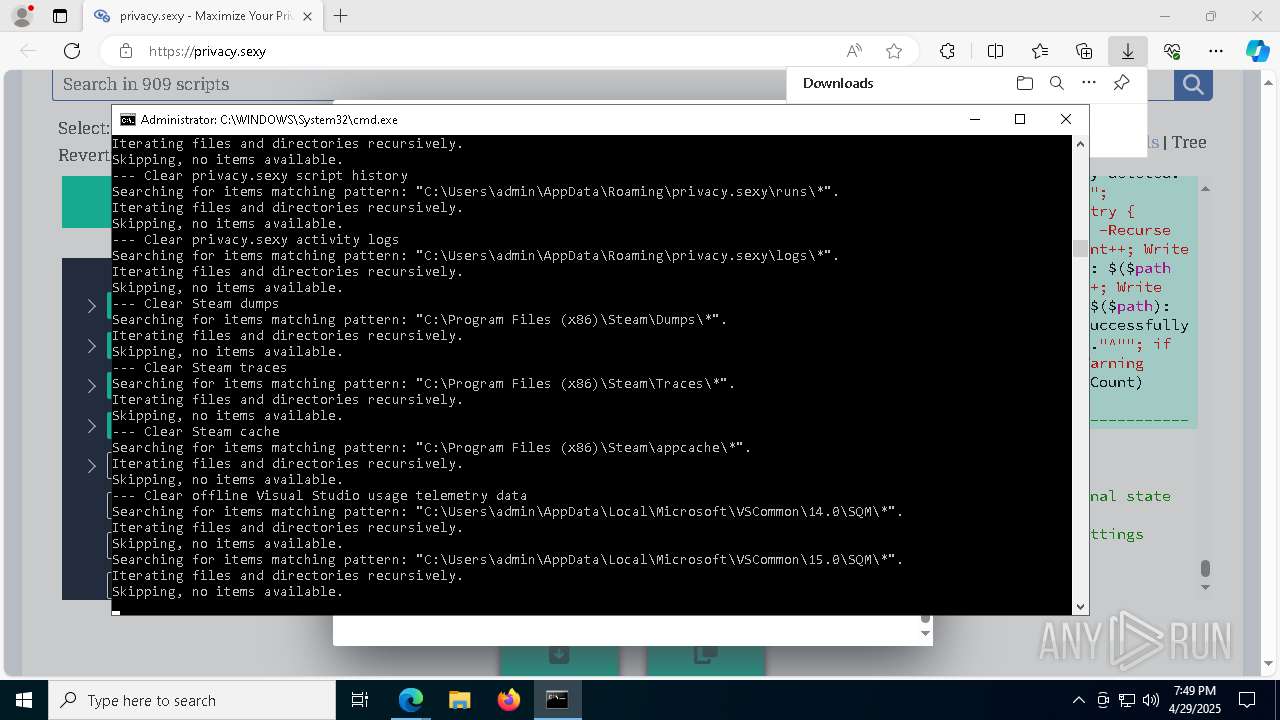
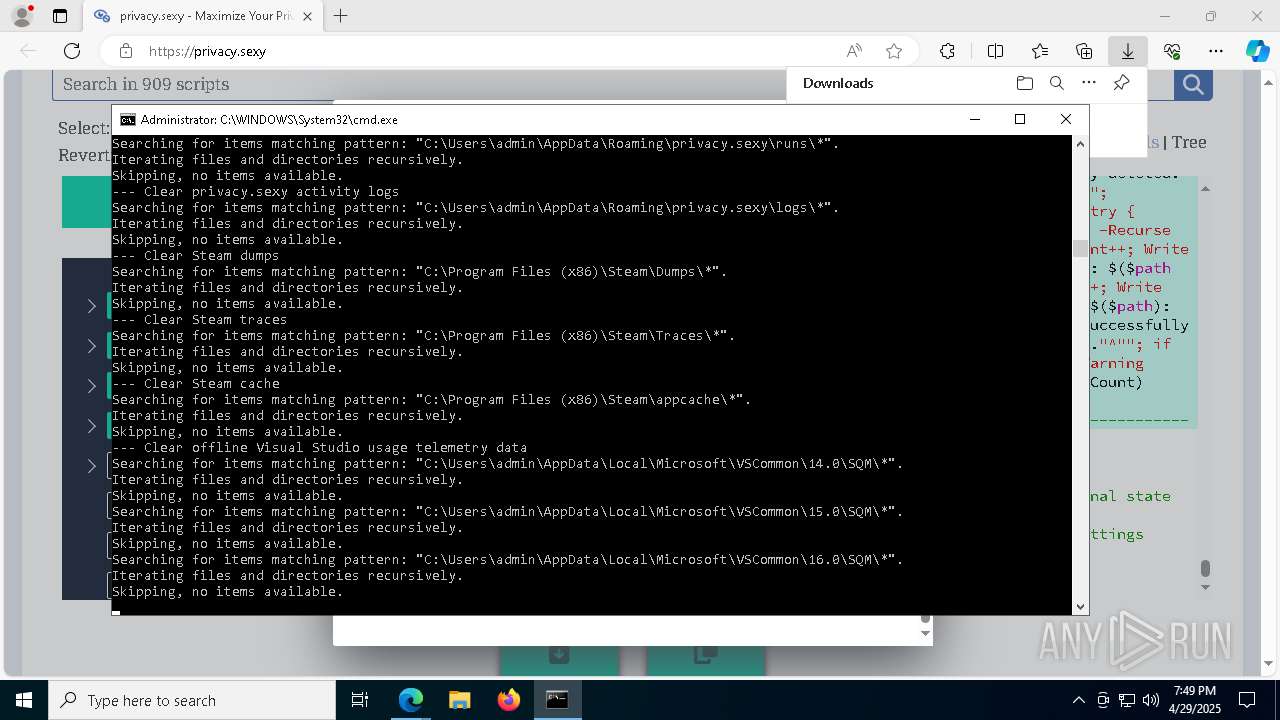
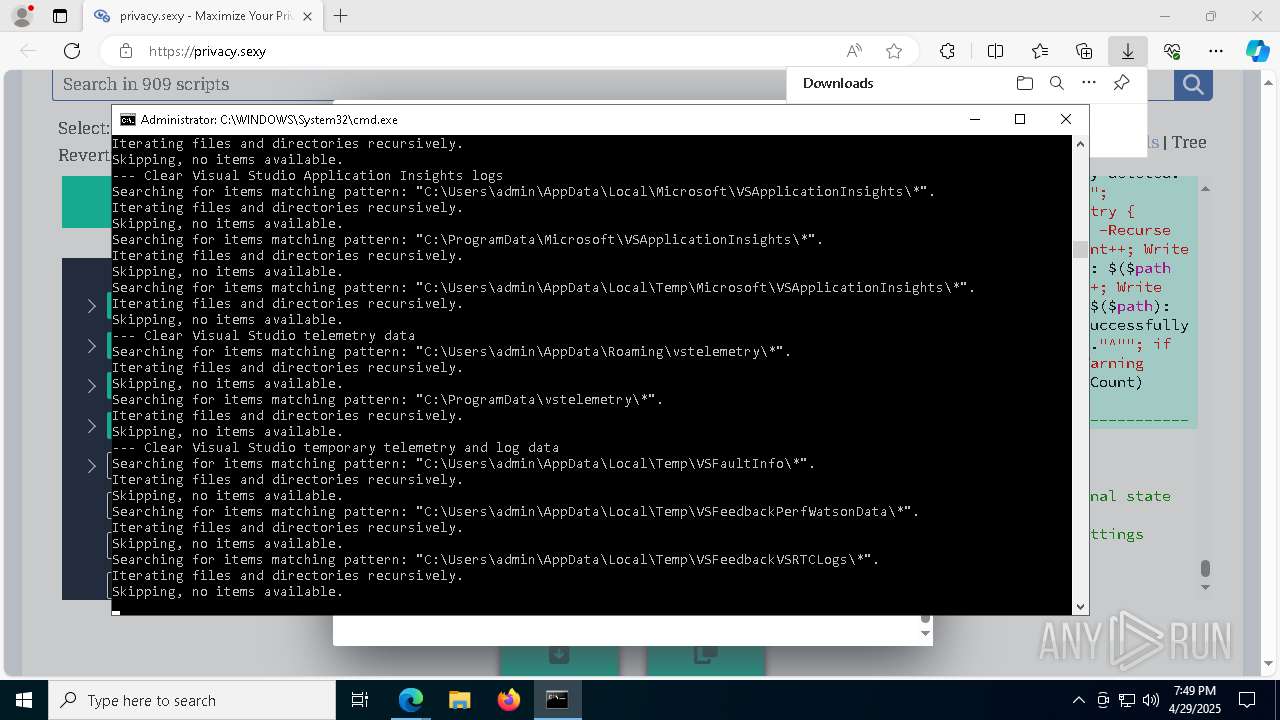
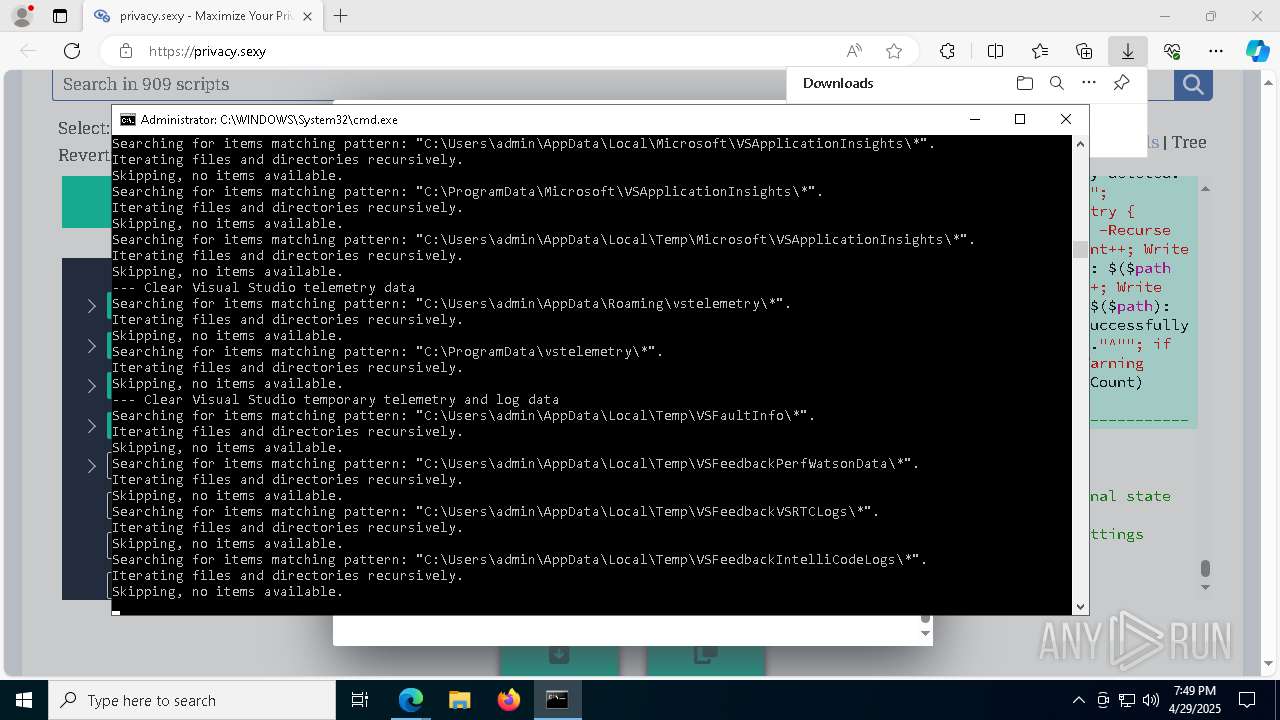
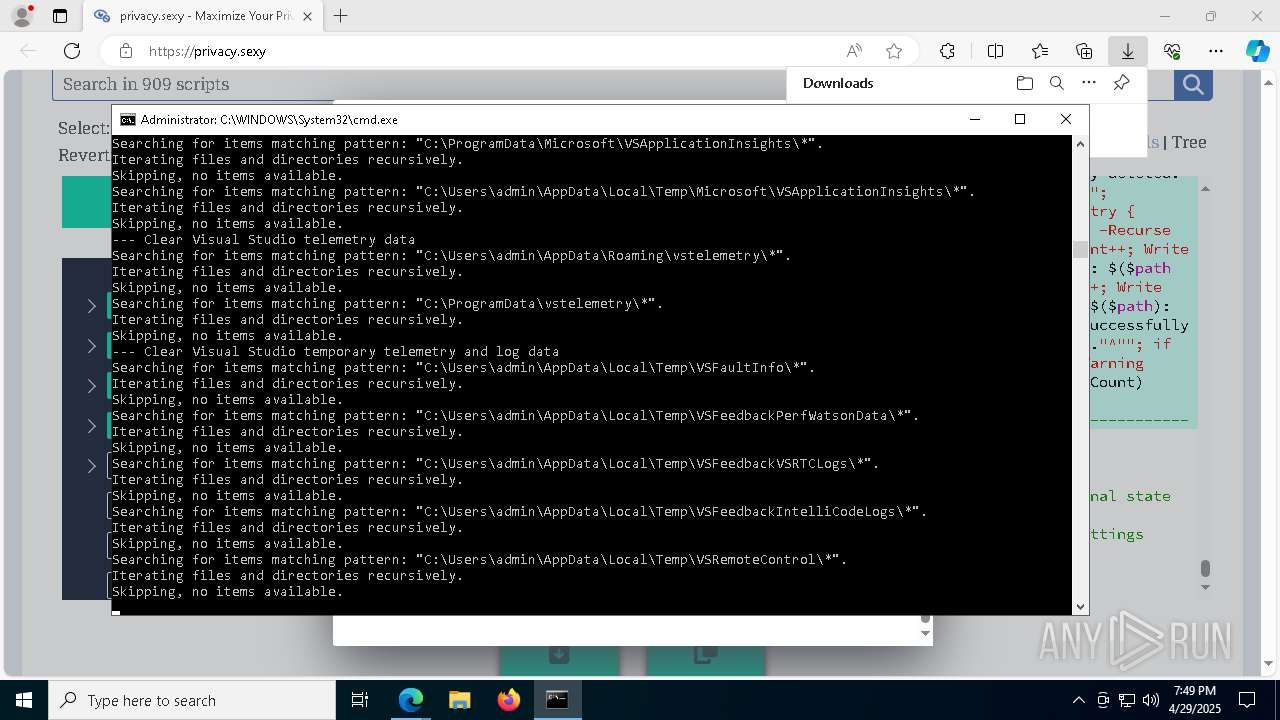
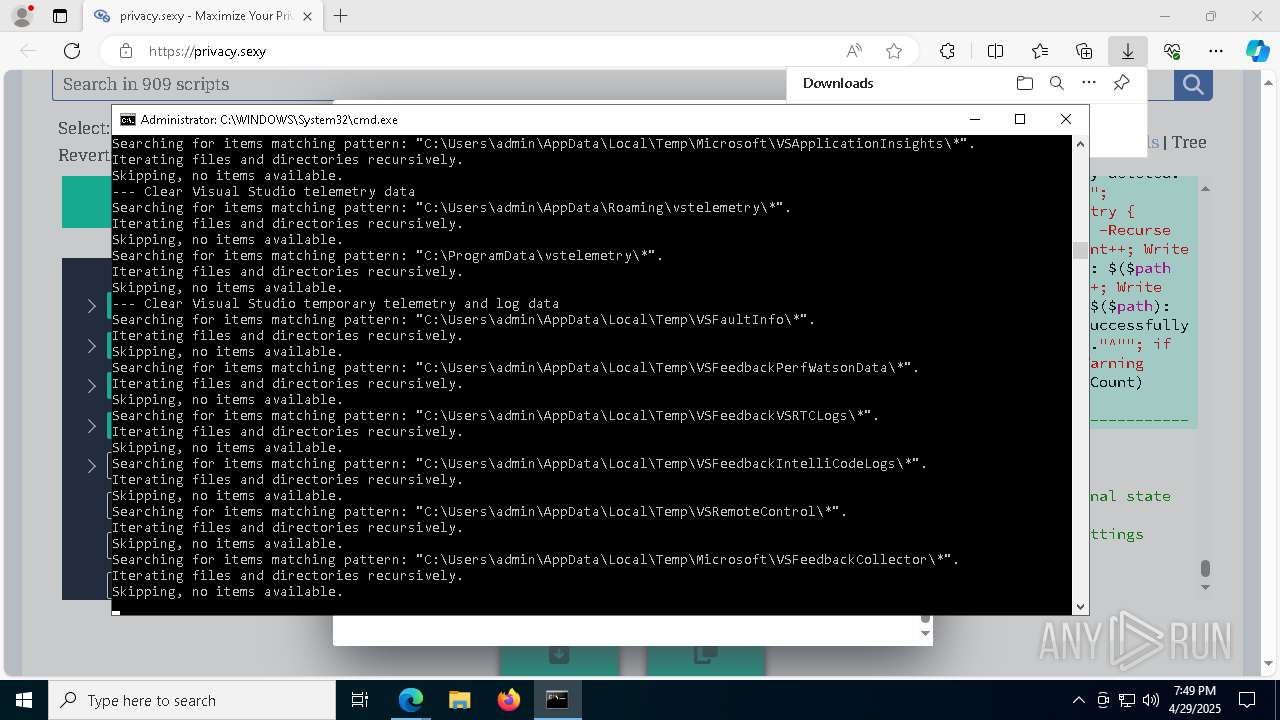
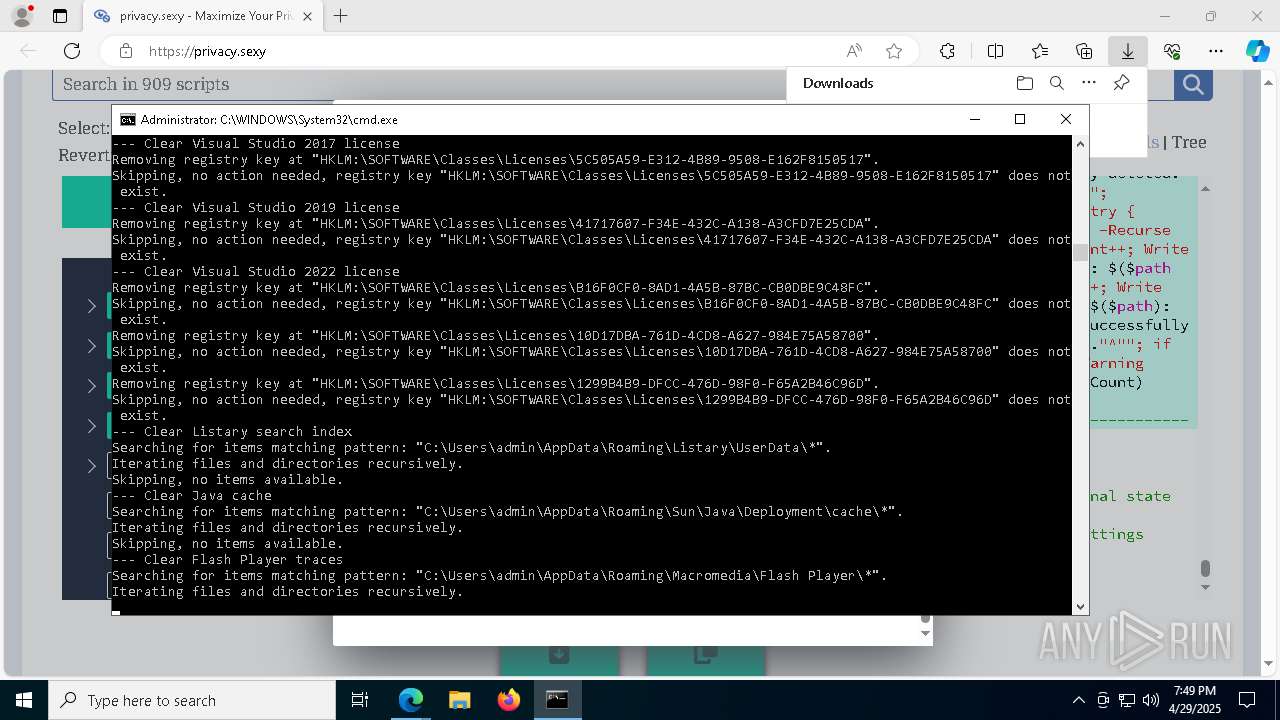
Changes powershell execution policy (Unrestricted)
- cmd.exe (PID: 7336)
Starts CMD.EXE for commands execution
- msedge.exe (PID: 7476)
SUSPICIOUS
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1020)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 7436)
Executing commands from a ".bat" file
- powershell.exe (PID: 1020)
- msedge.exe (PID: 7476)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 1764)
- powershell.exe (PID: 5044)
- powershell.exe (PID: 7432)
- powershell.exe (PID: 8032)
- powershell.exe (PID: 1676)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 1388)
- powershell.exe (PID: 6072)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7828)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 4896)
- powershell.exe (PID: 5328)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 4268)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 4180)
- powershell.exe (PID: 7684)
- powershell.exe (PID: 5592)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 132)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 2596)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 6808)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 4728)
- powershell.exe (PID: 632)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 7008)
- powershell.exe (PID: 5024)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 2332)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 4304)
- powershell.exe (PID: 6036)
- powershell.exe (PID: 7548)
- powershell.exe (PID: 6456)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 7408)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 1748)
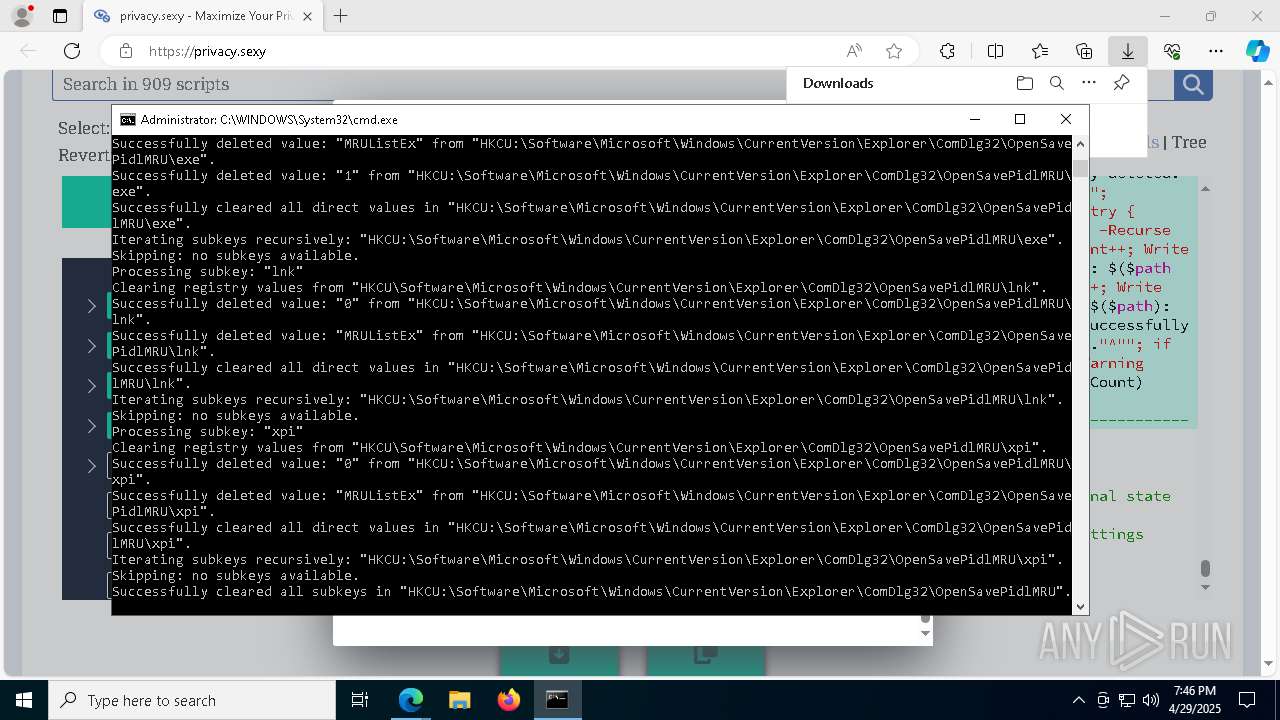
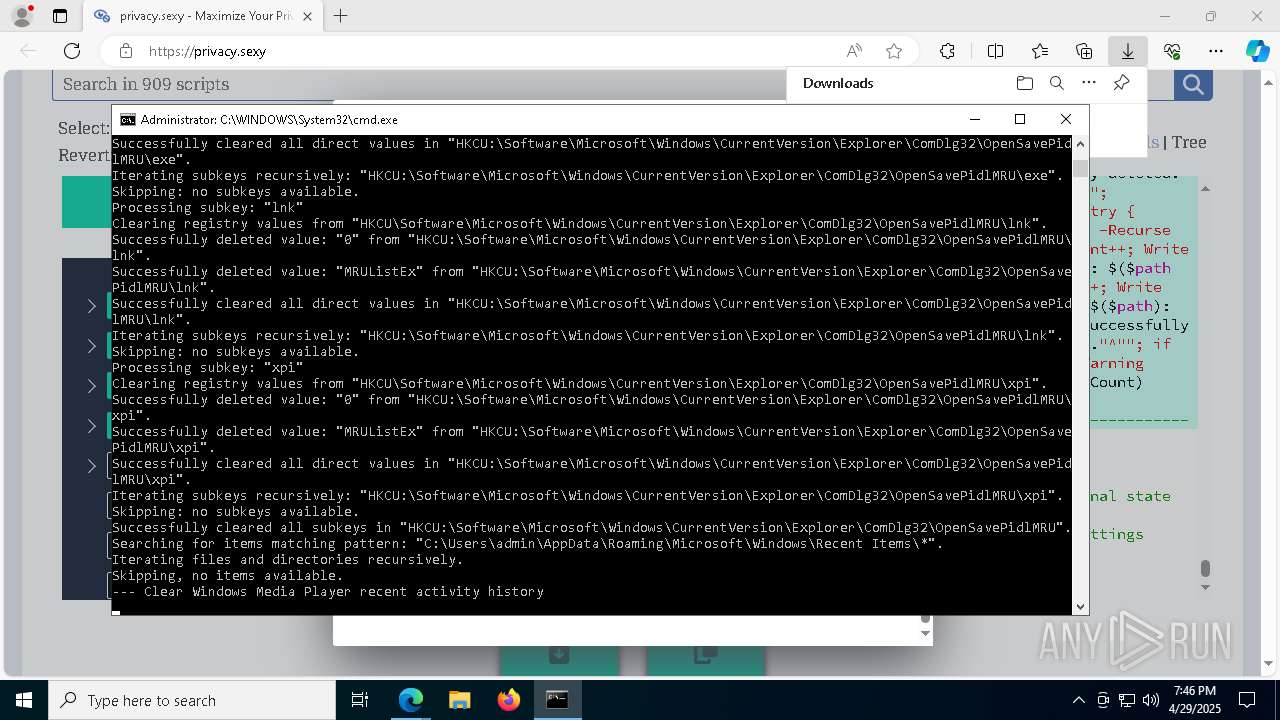
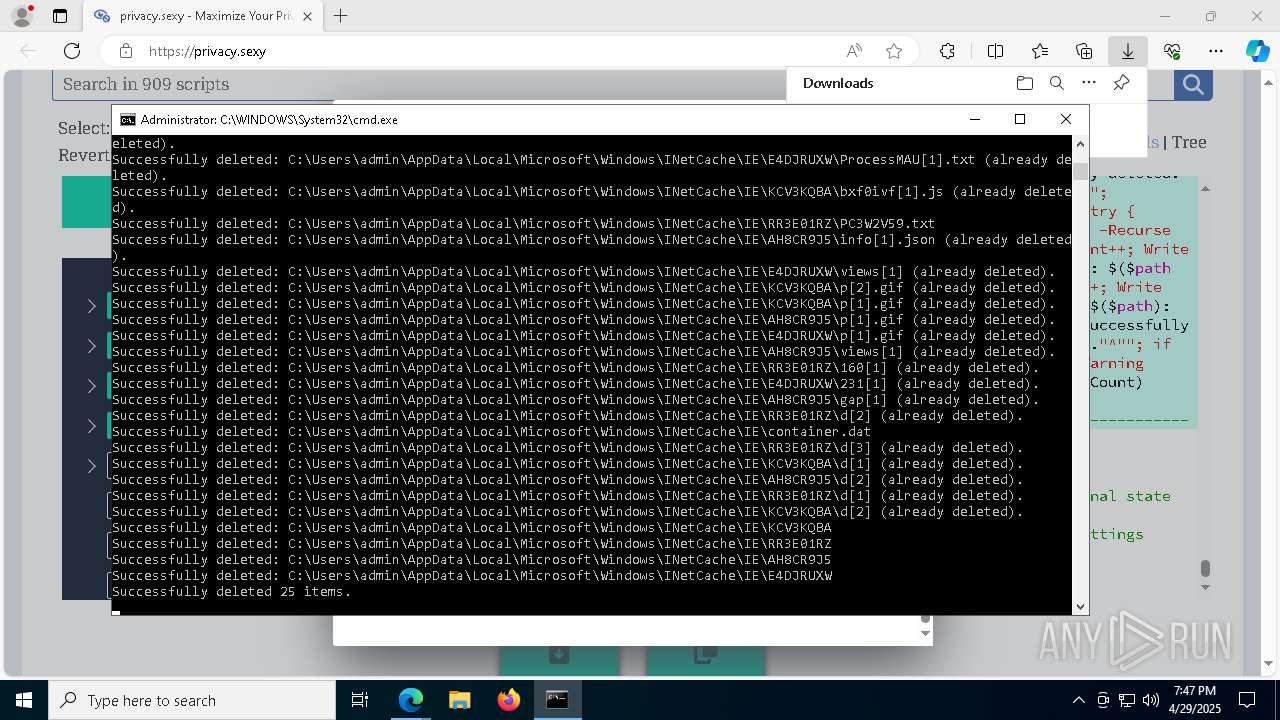
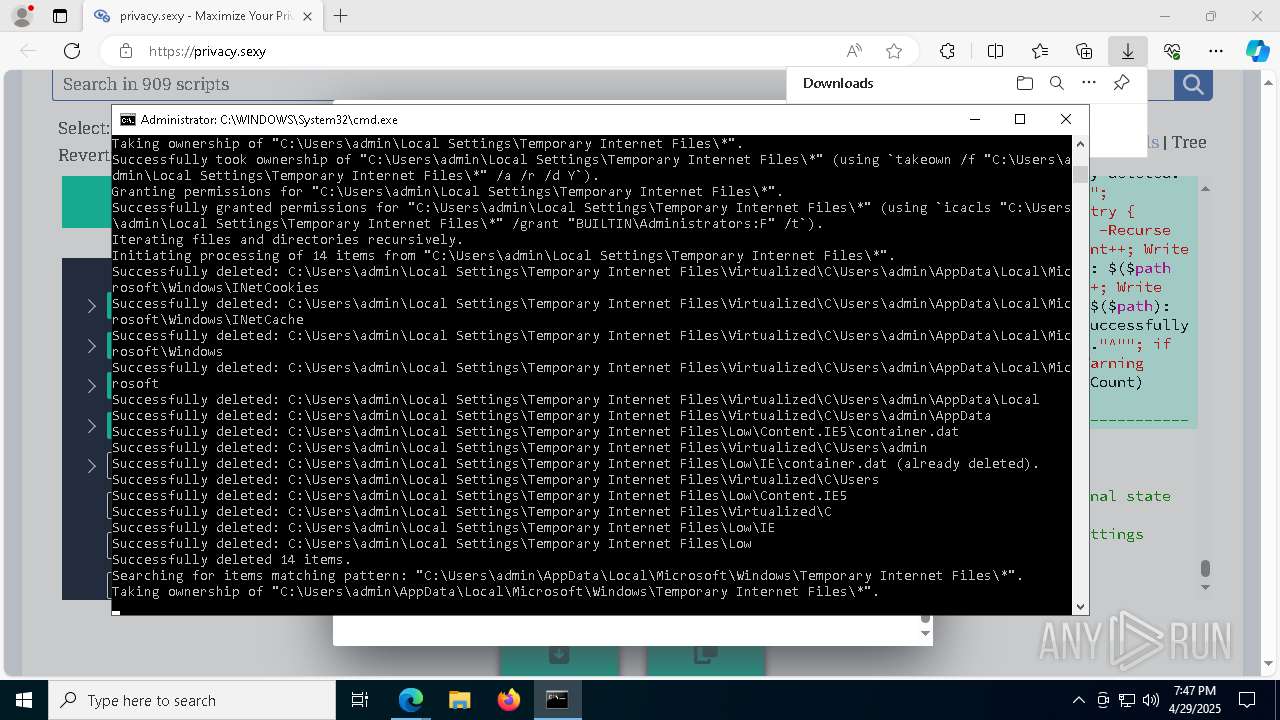
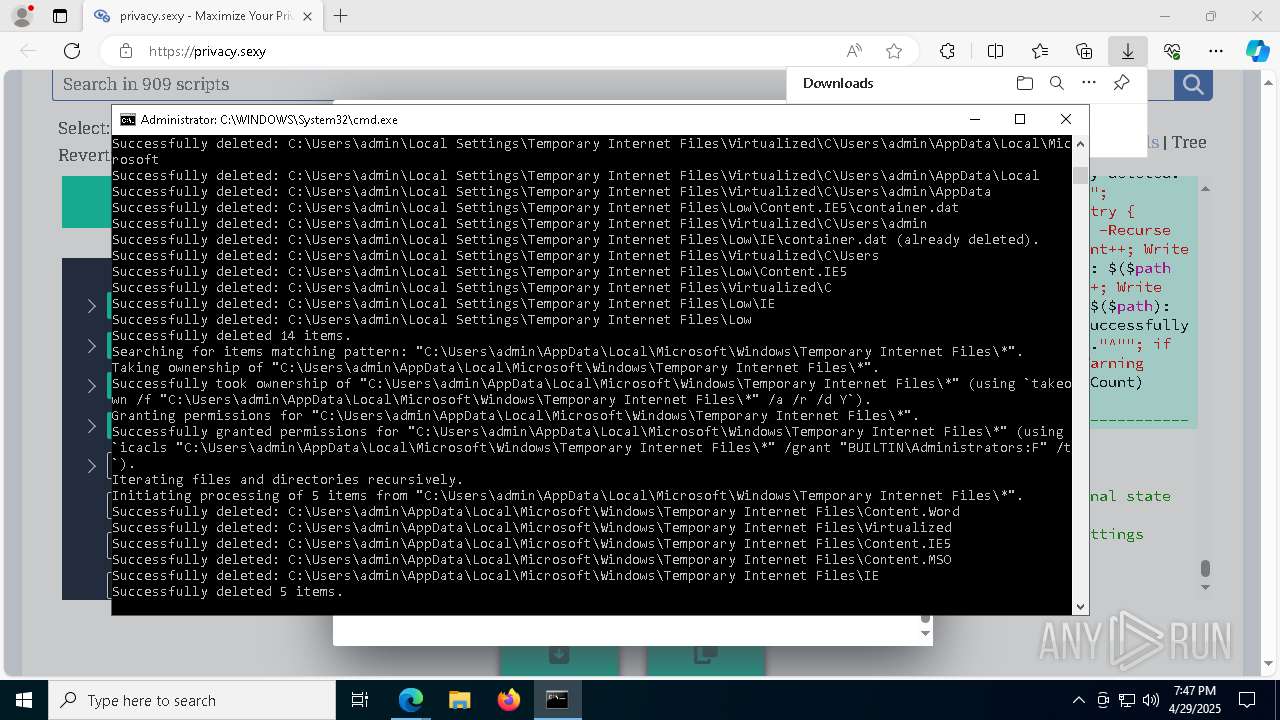
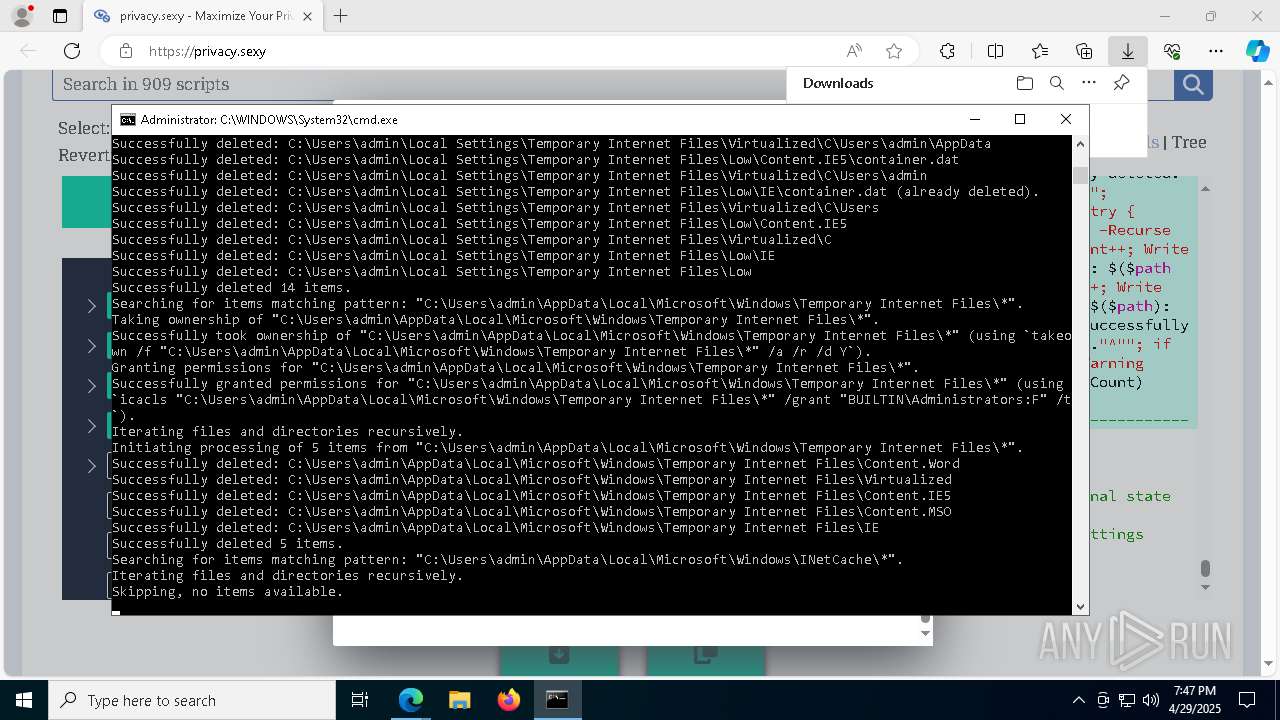
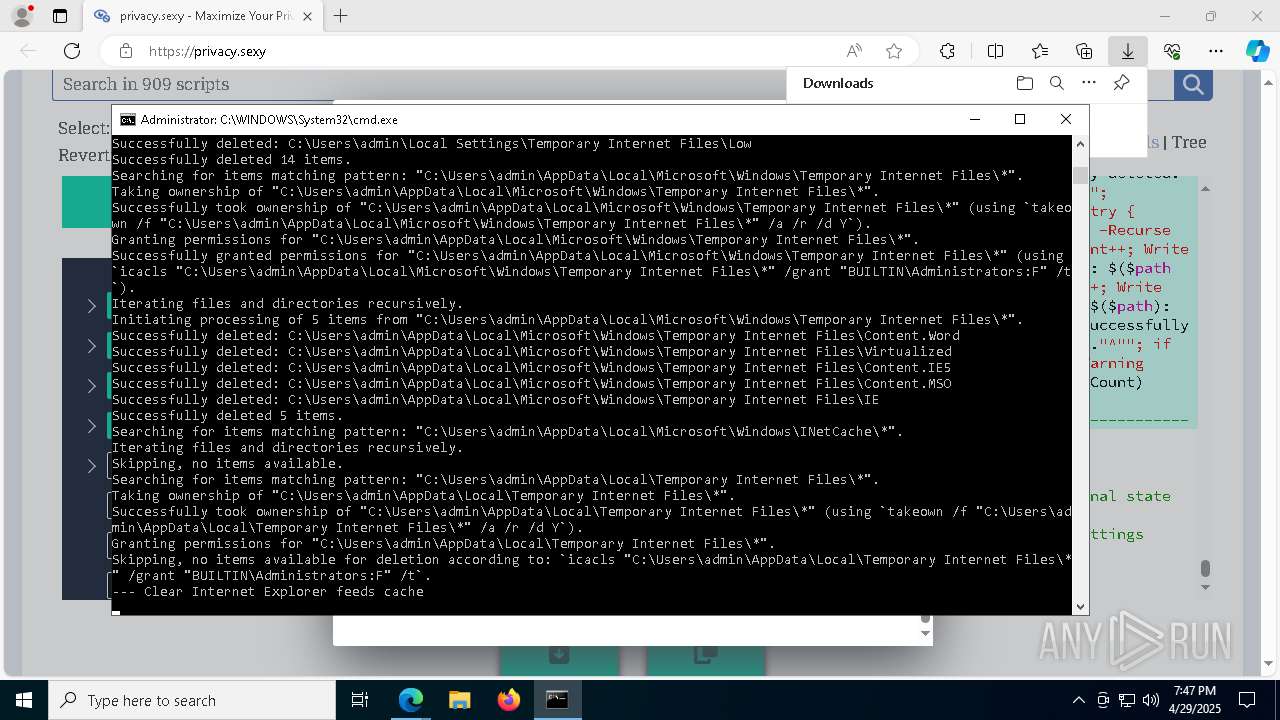
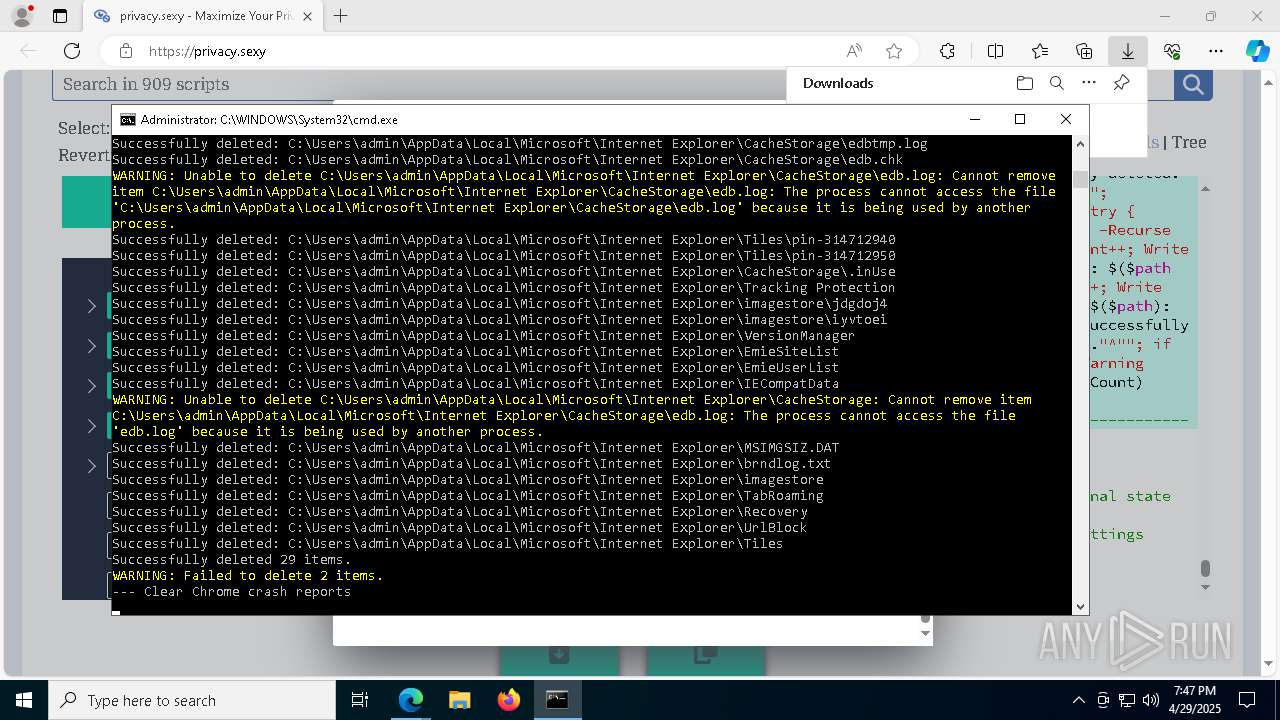
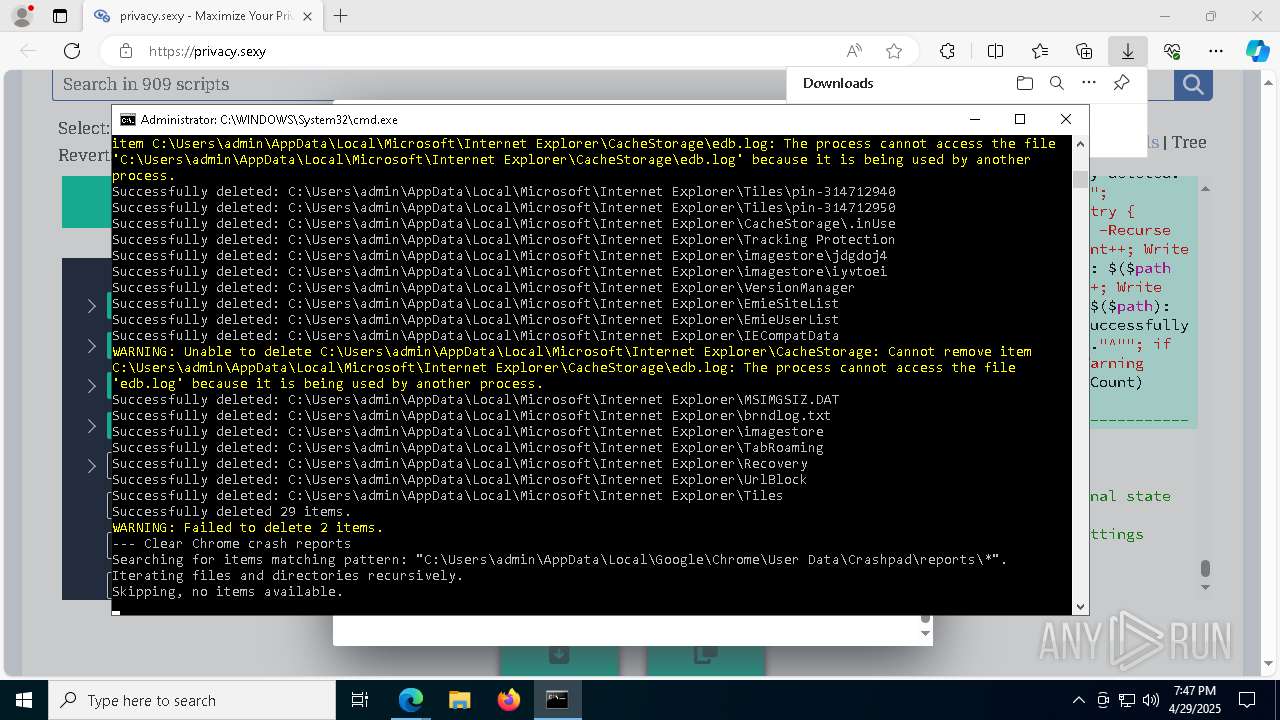
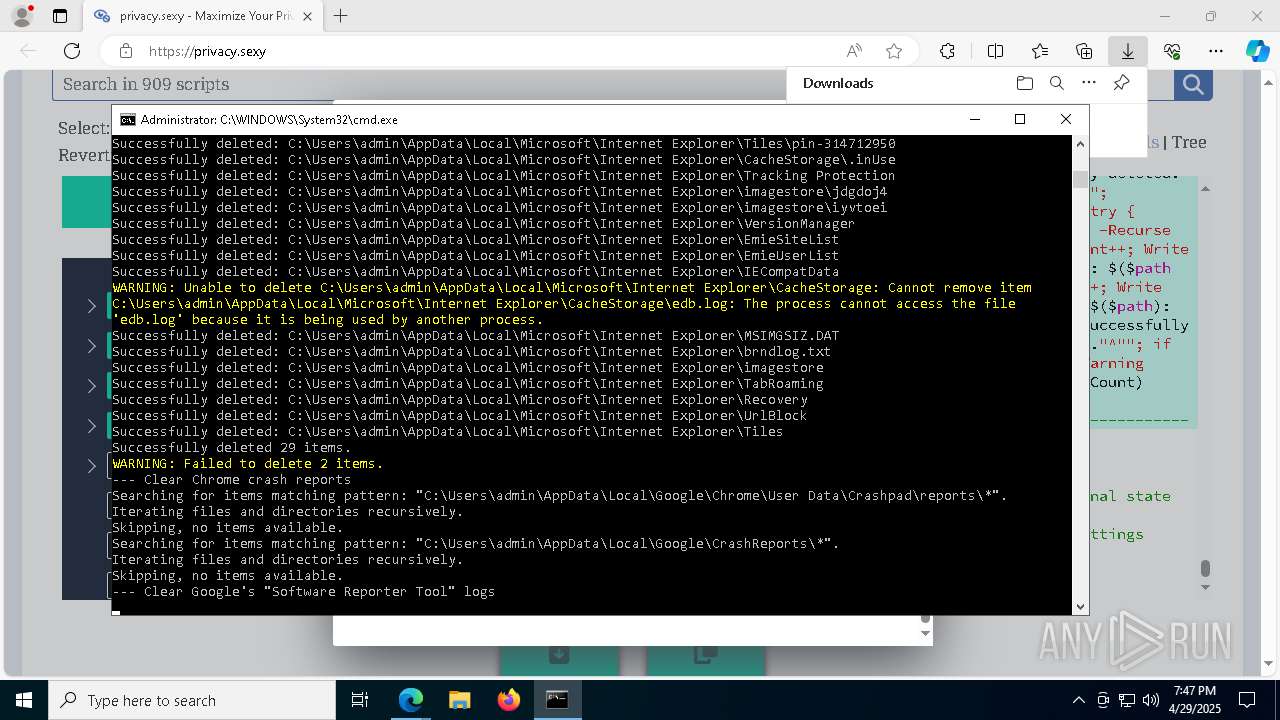
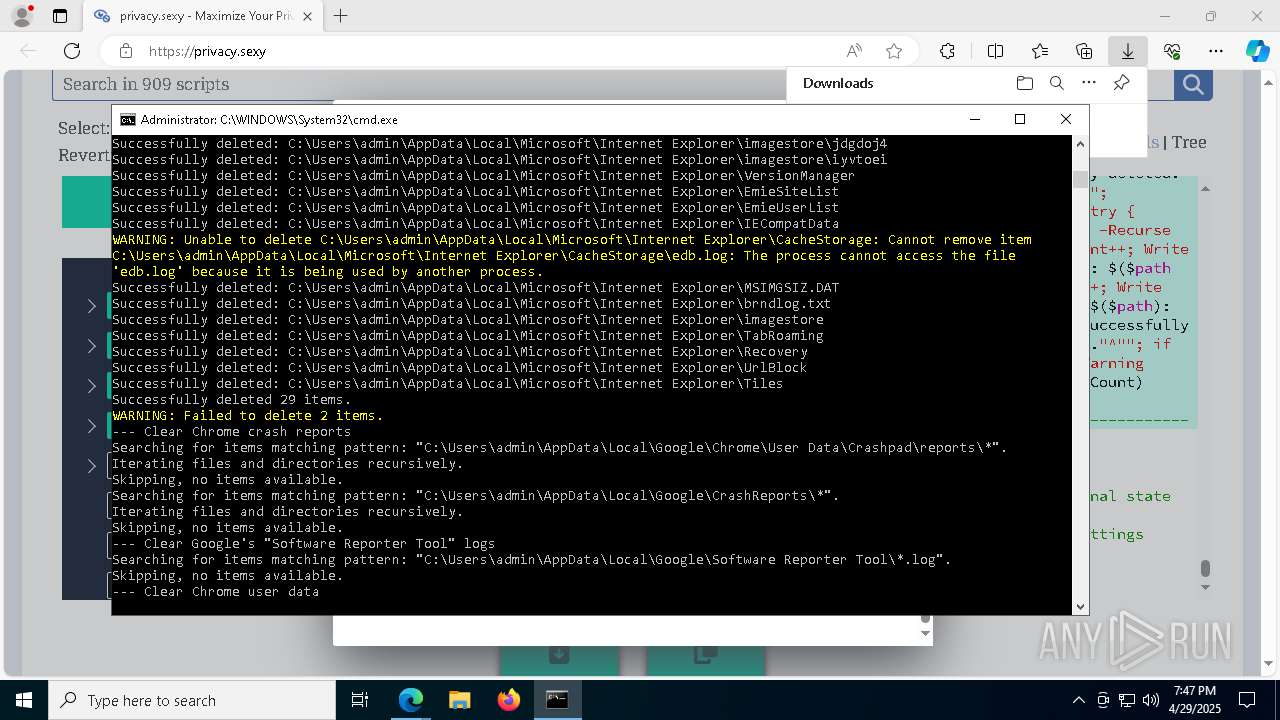
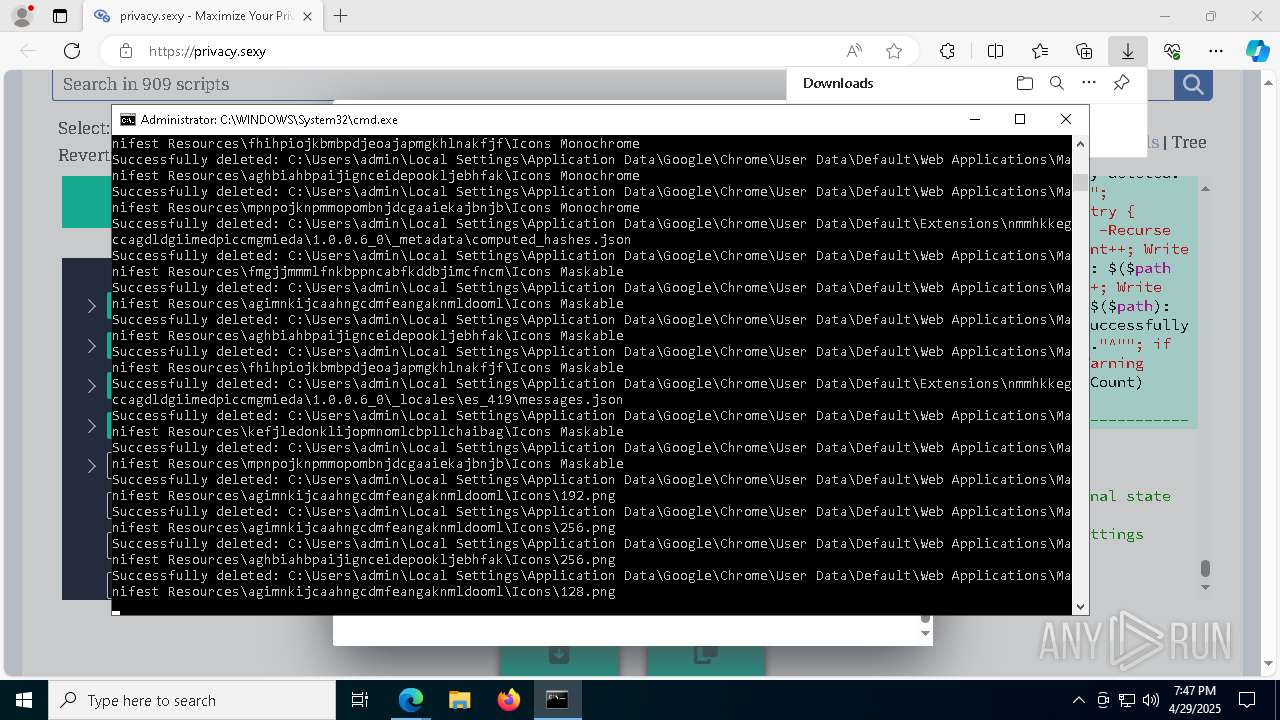
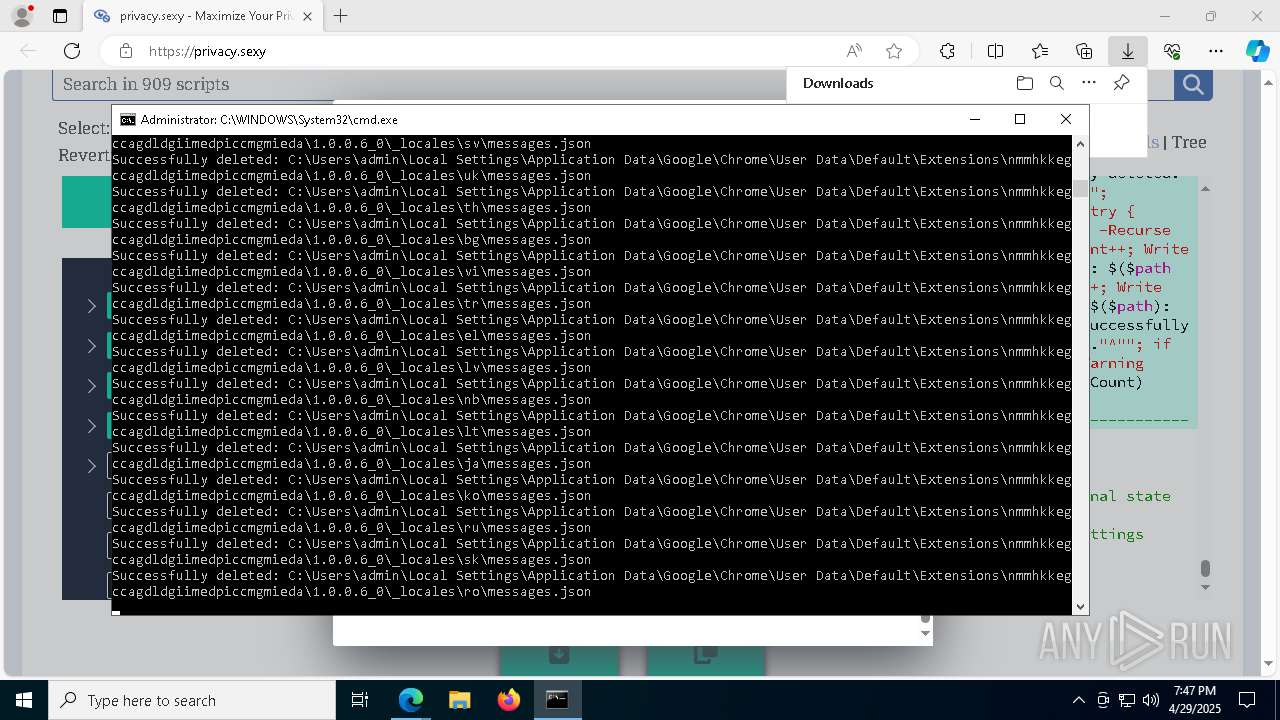
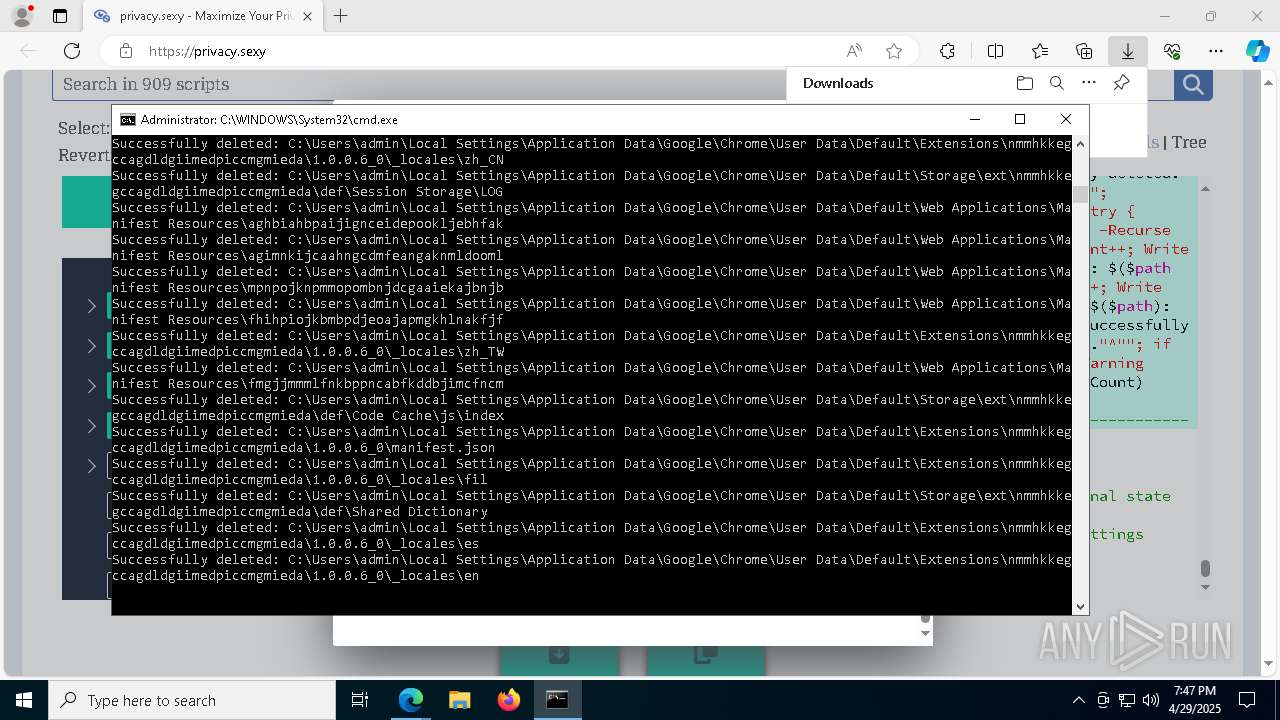
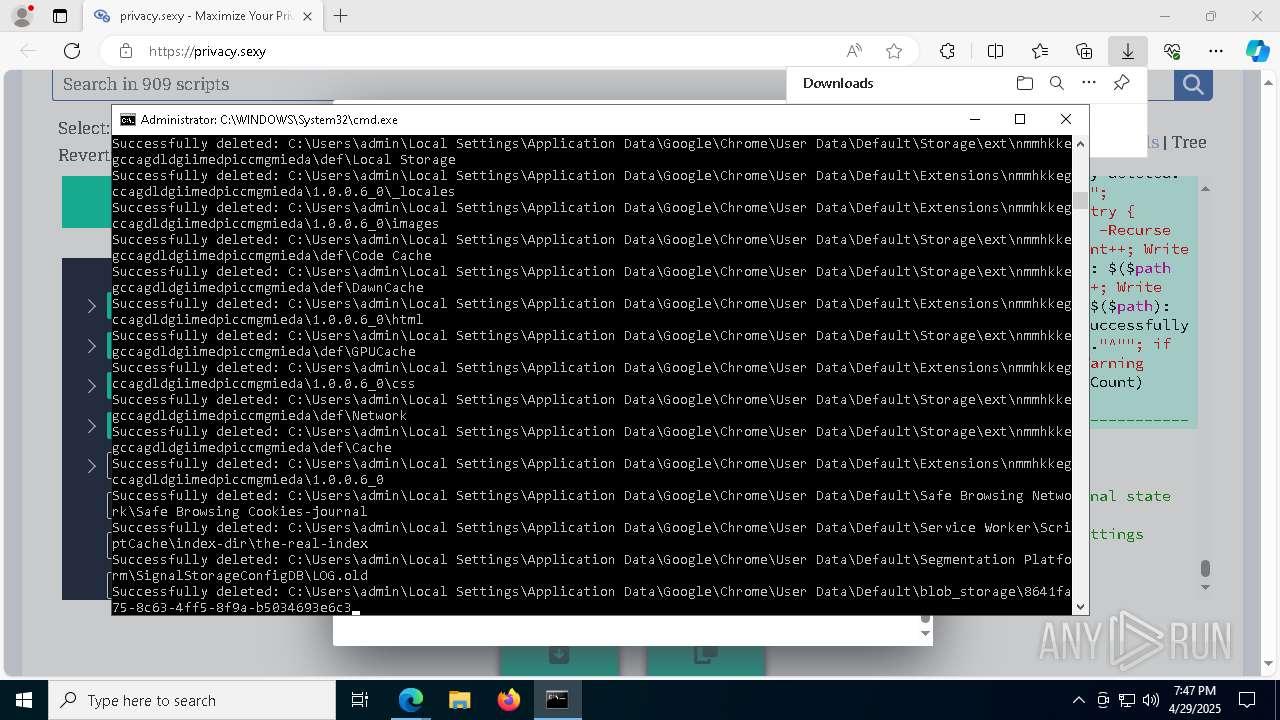
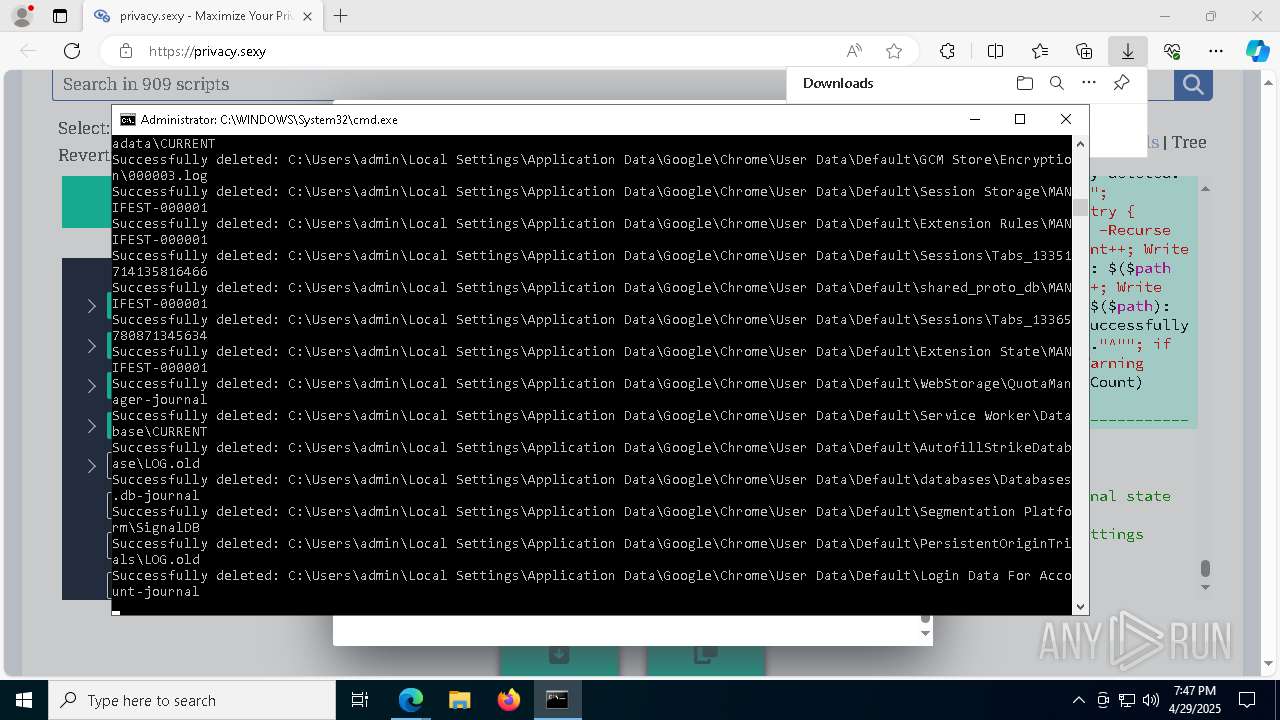
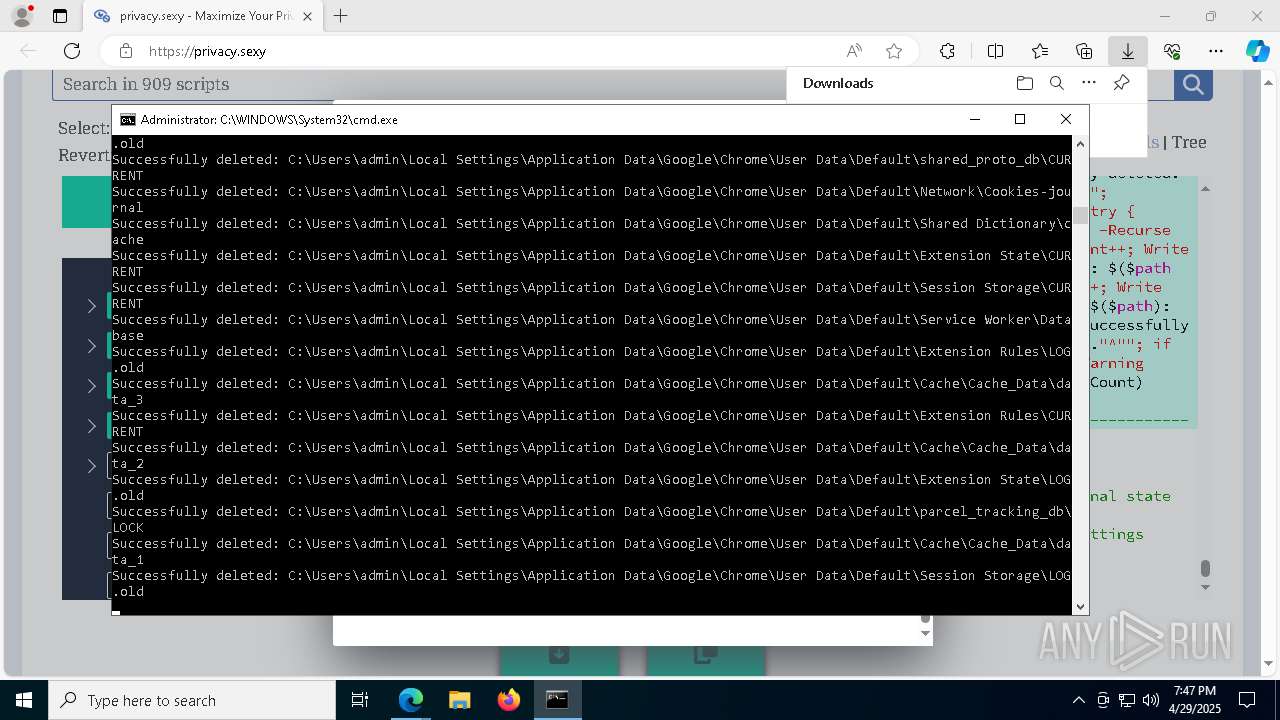
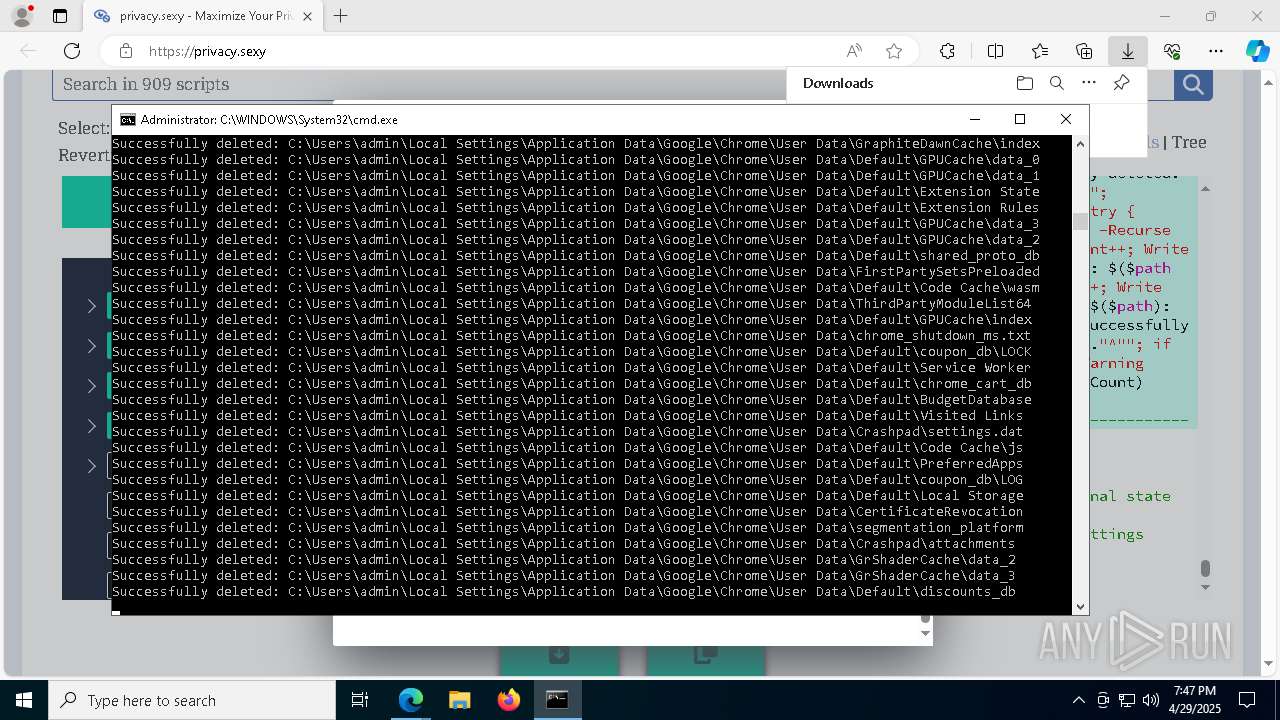
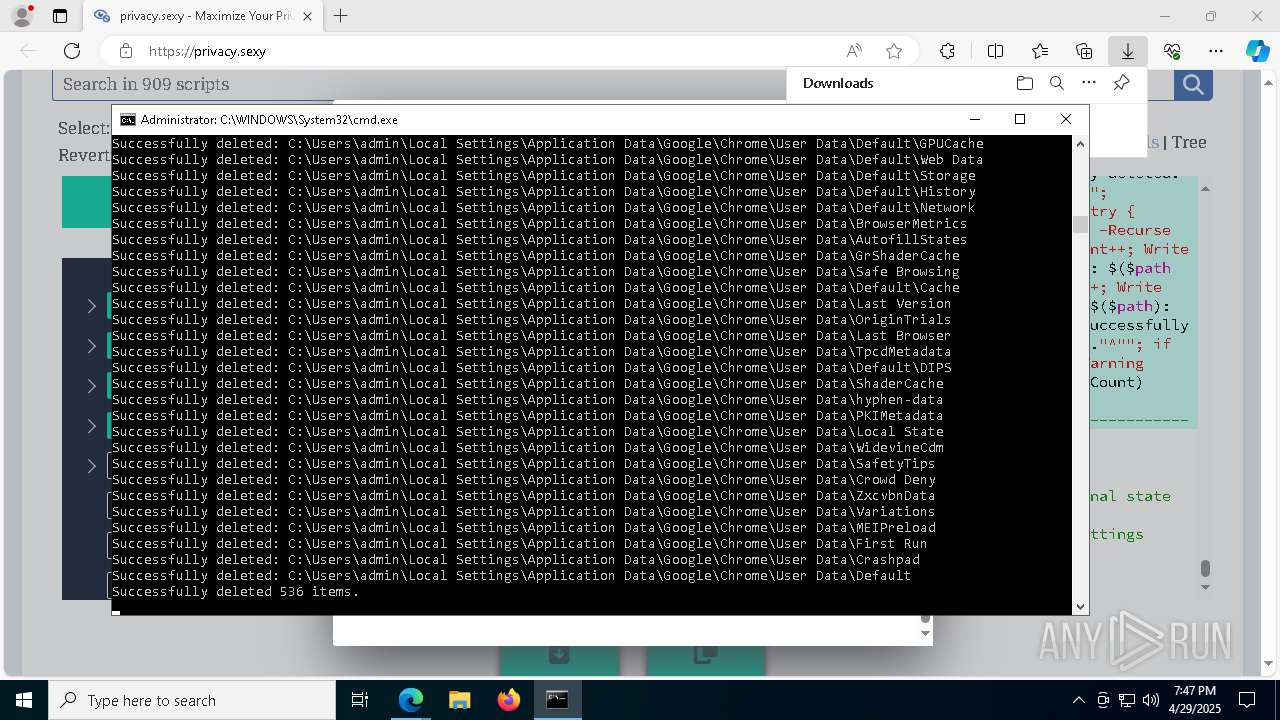
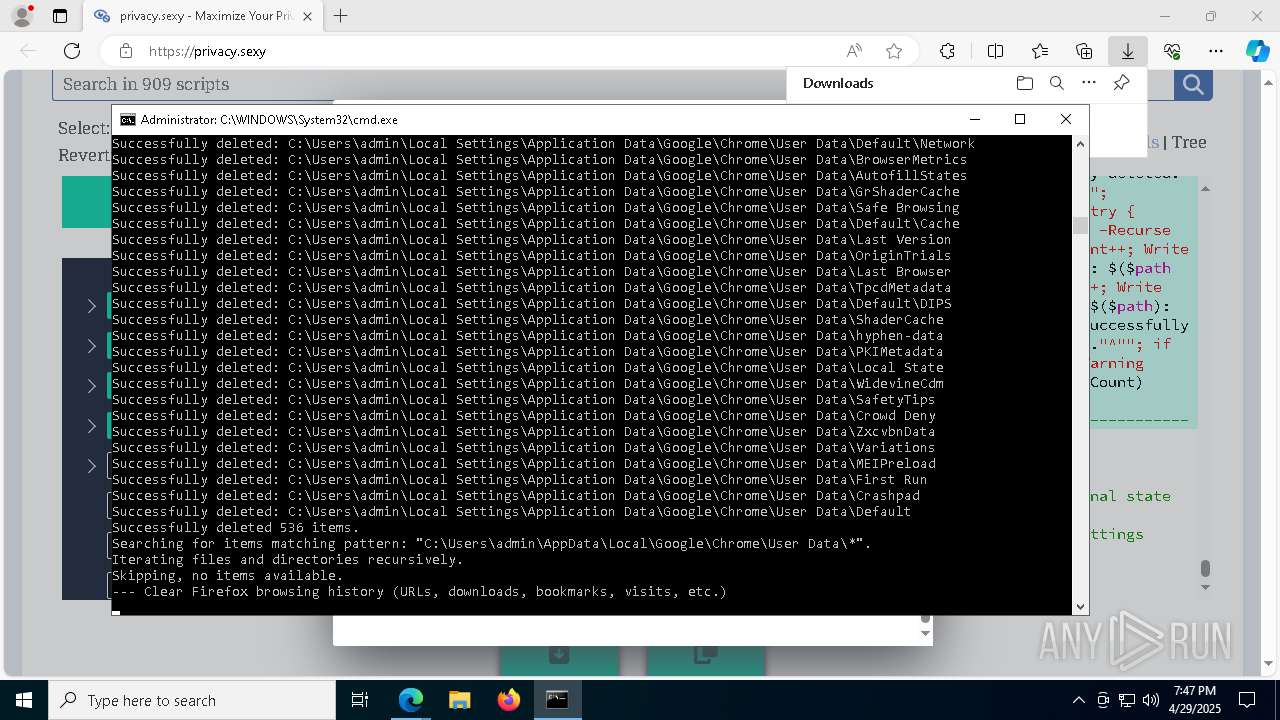
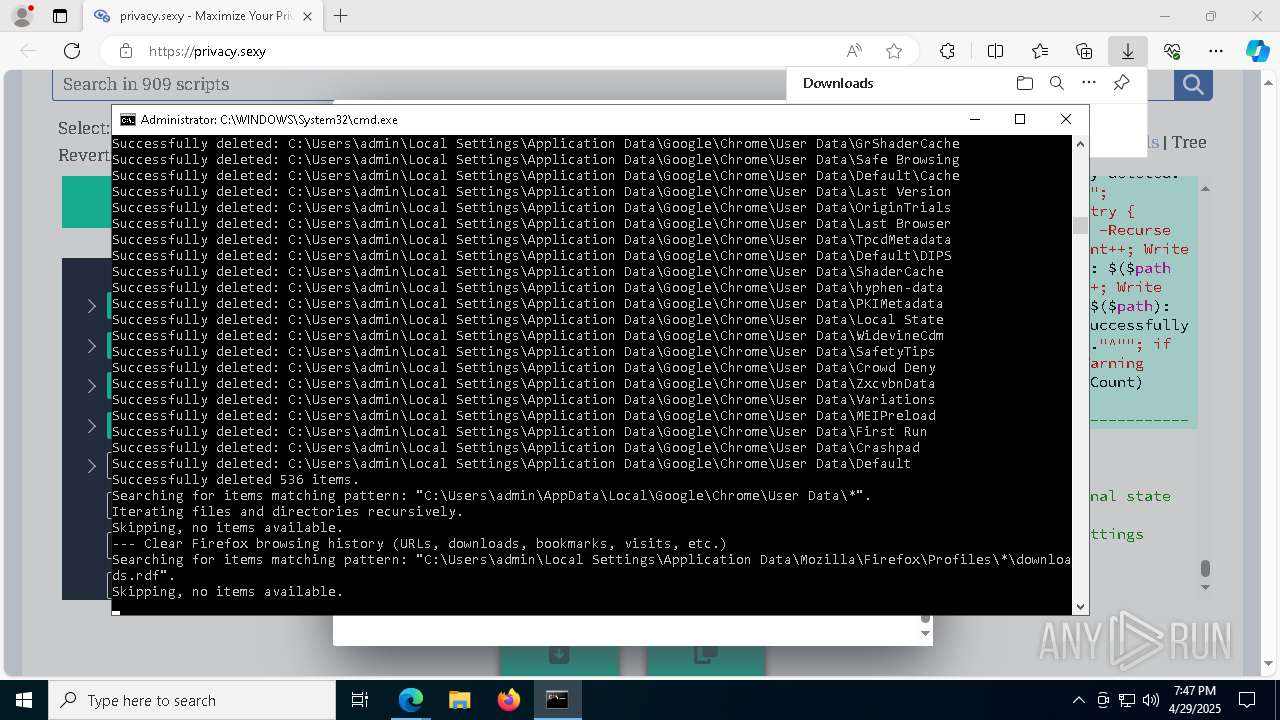
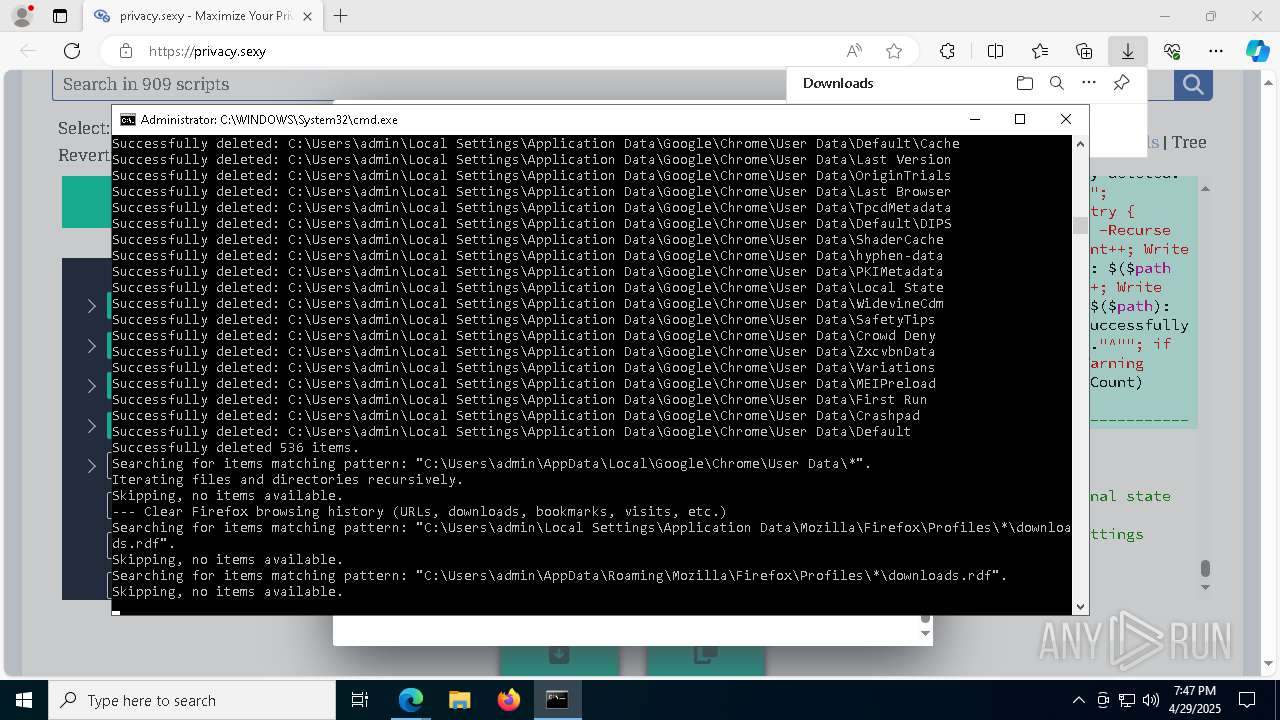
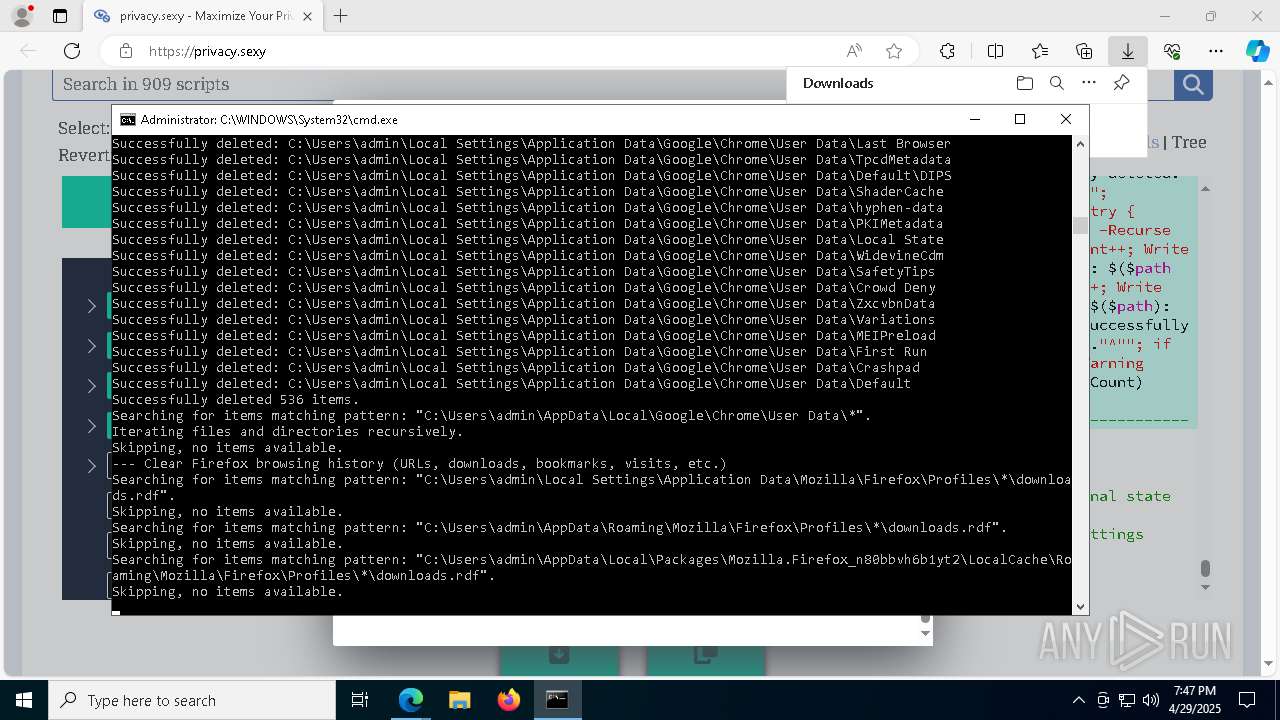
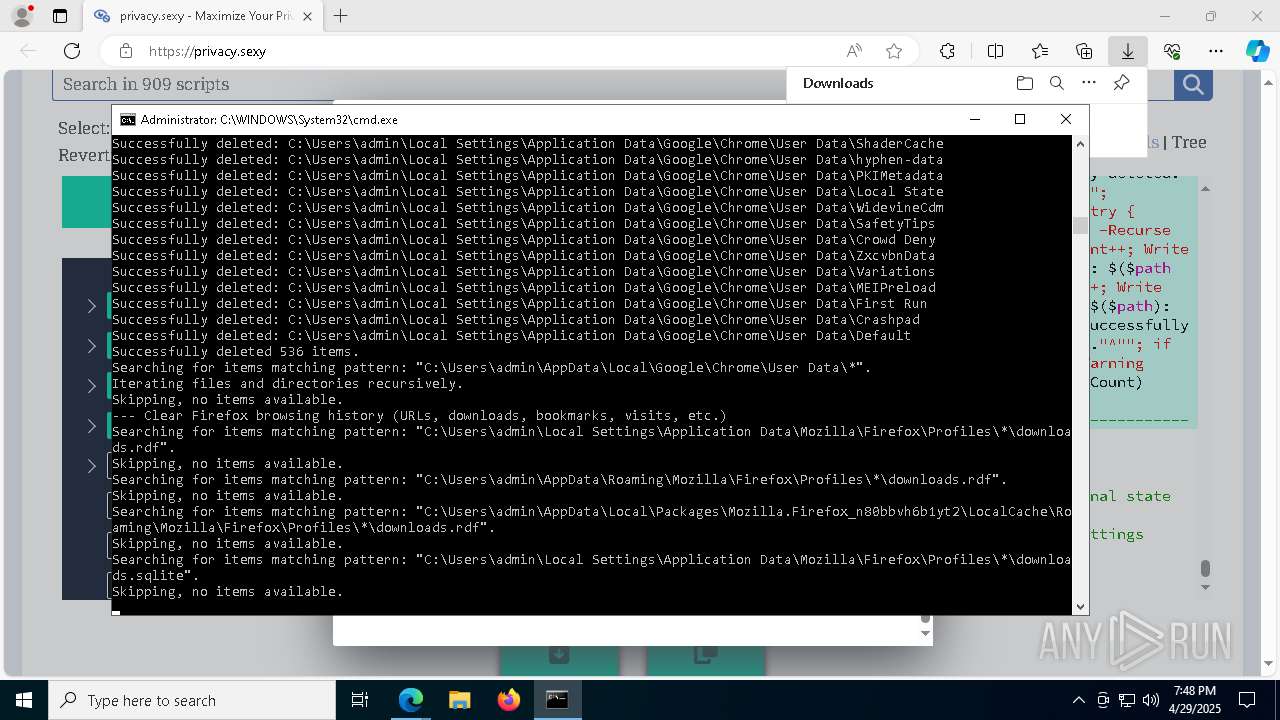
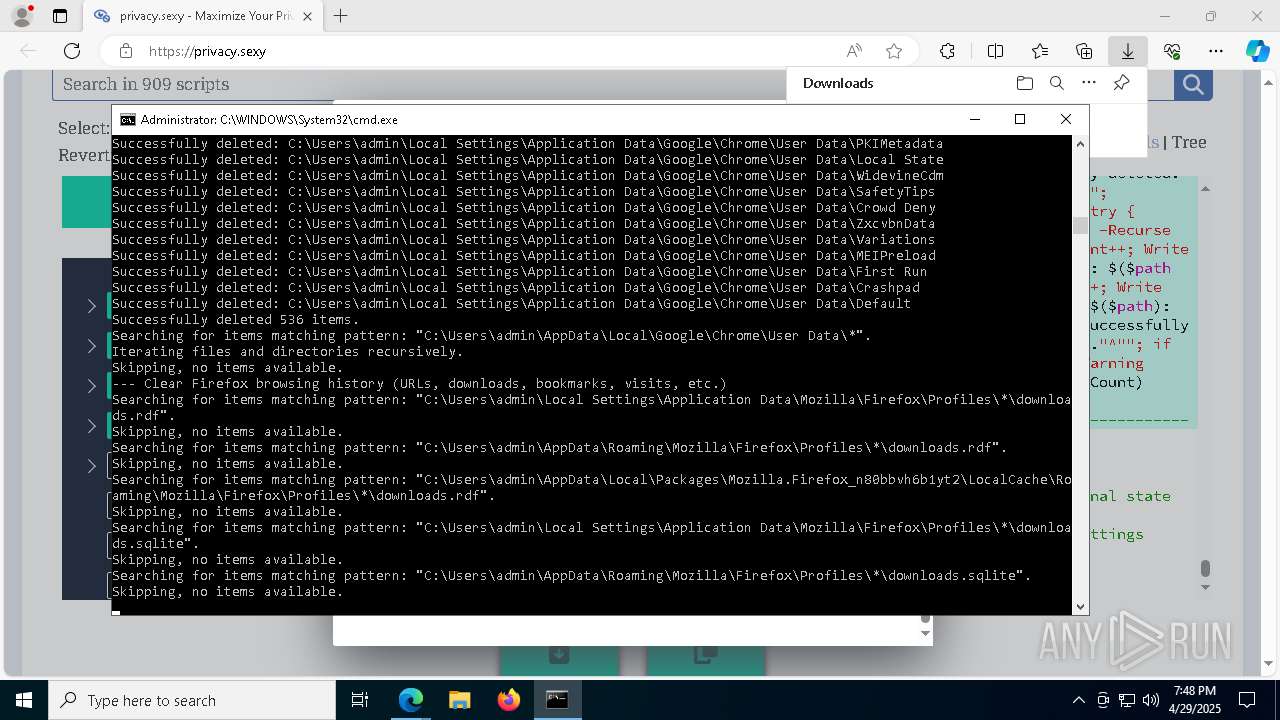
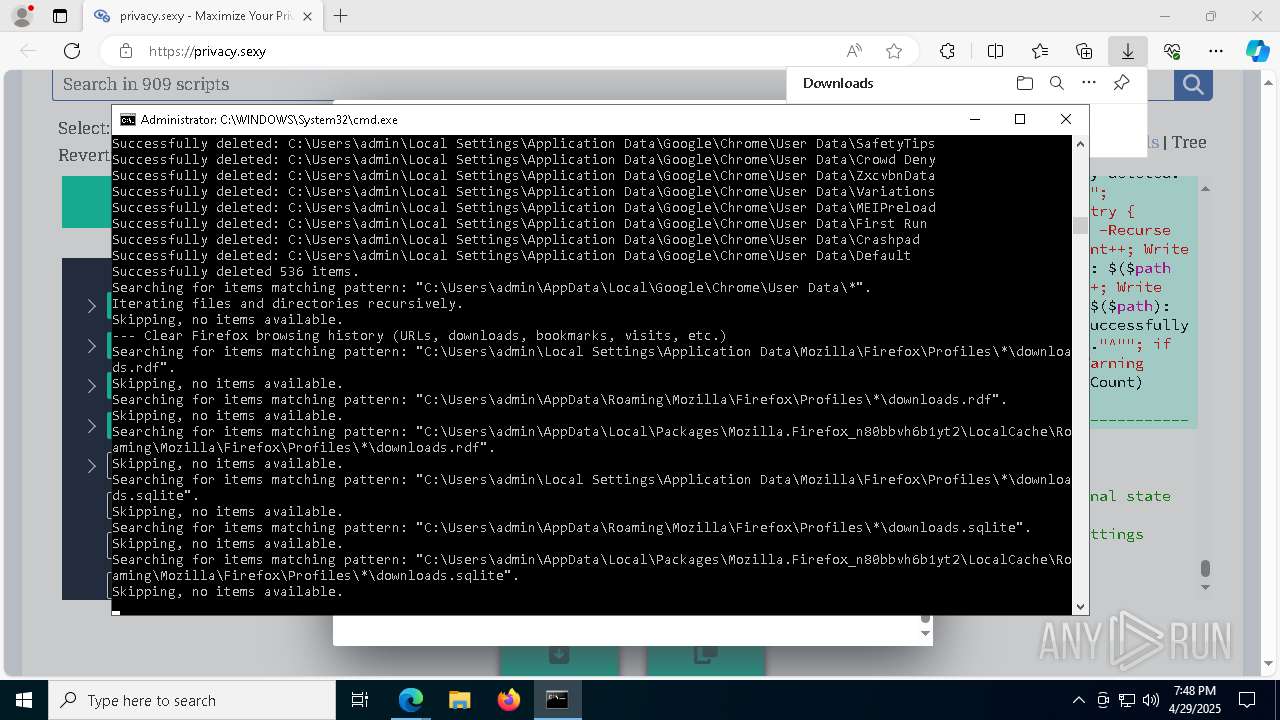
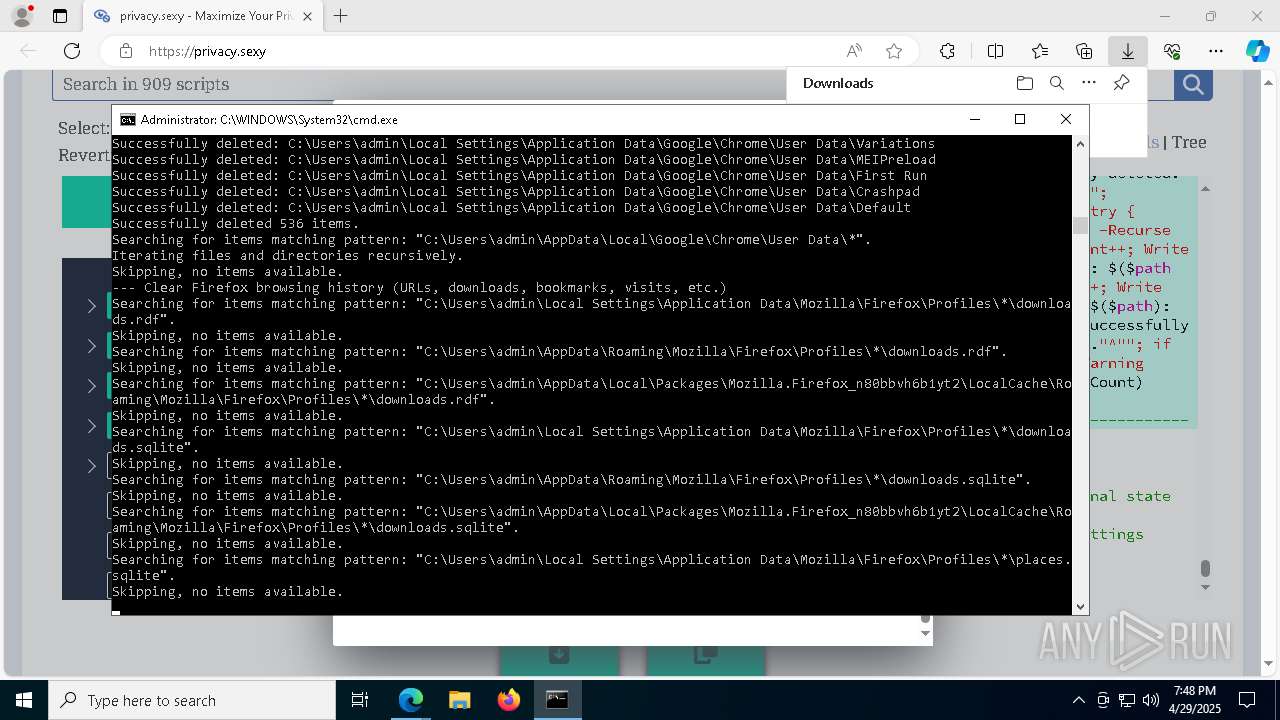
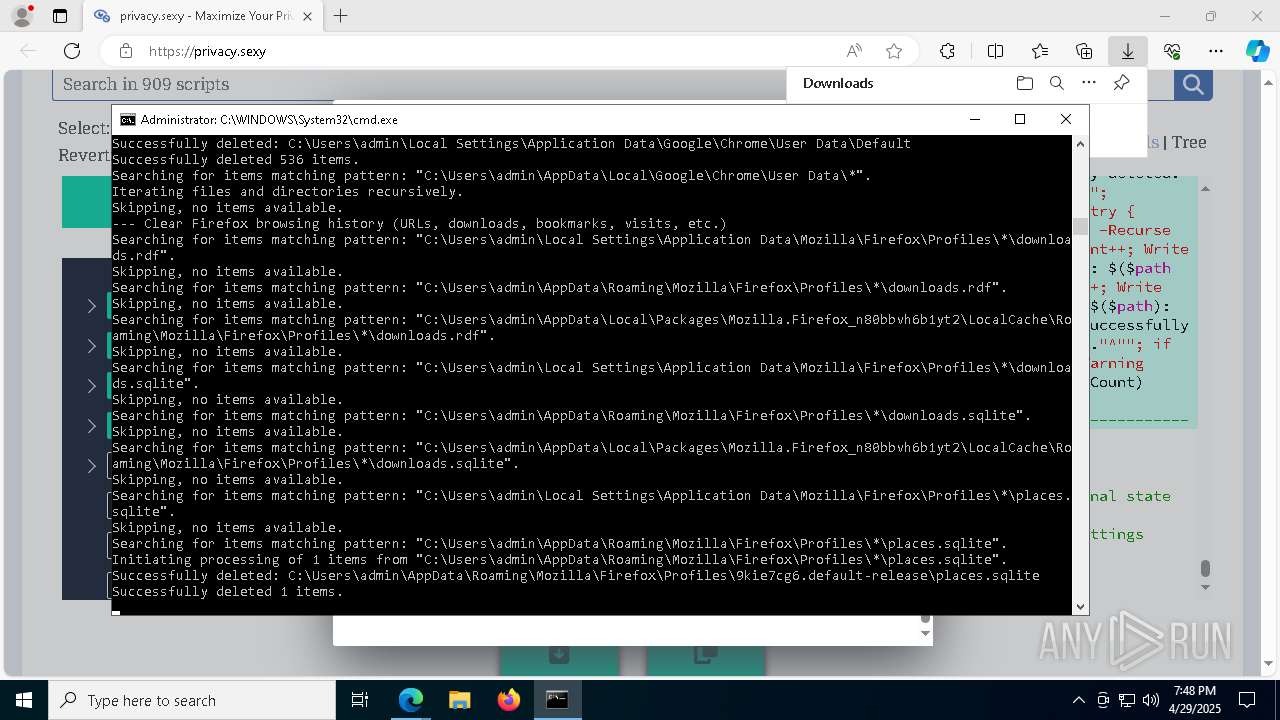
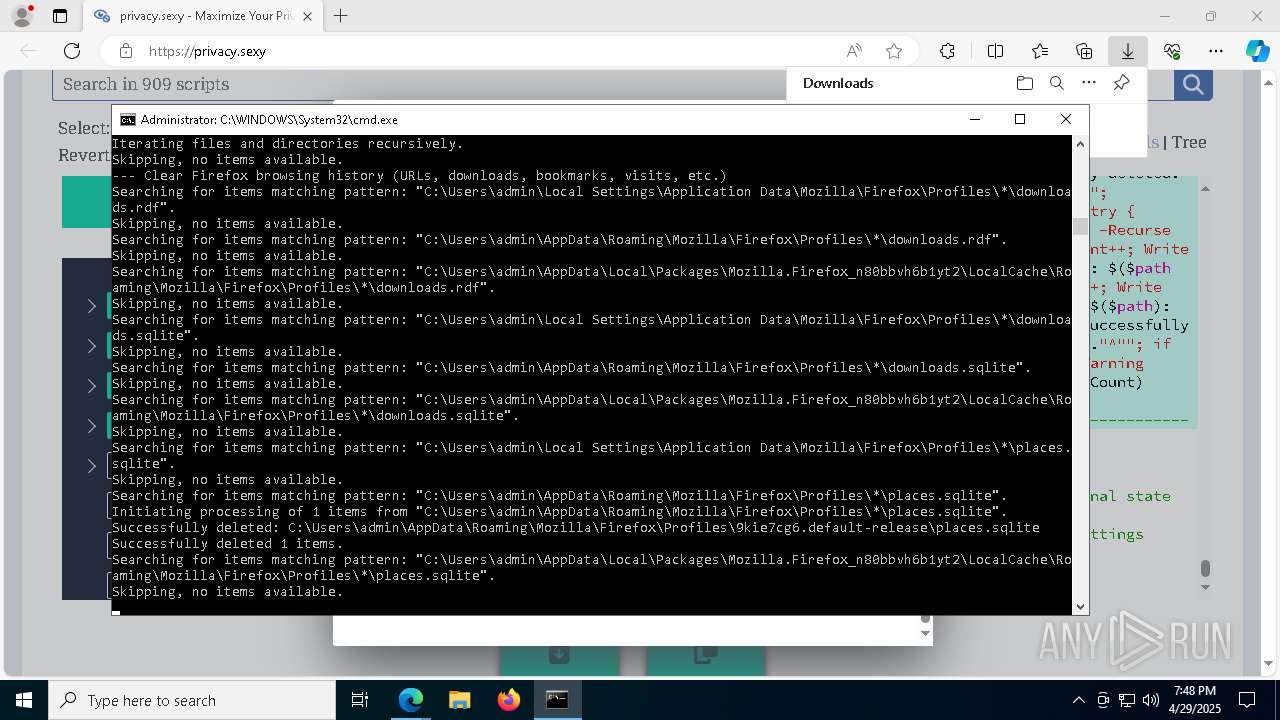
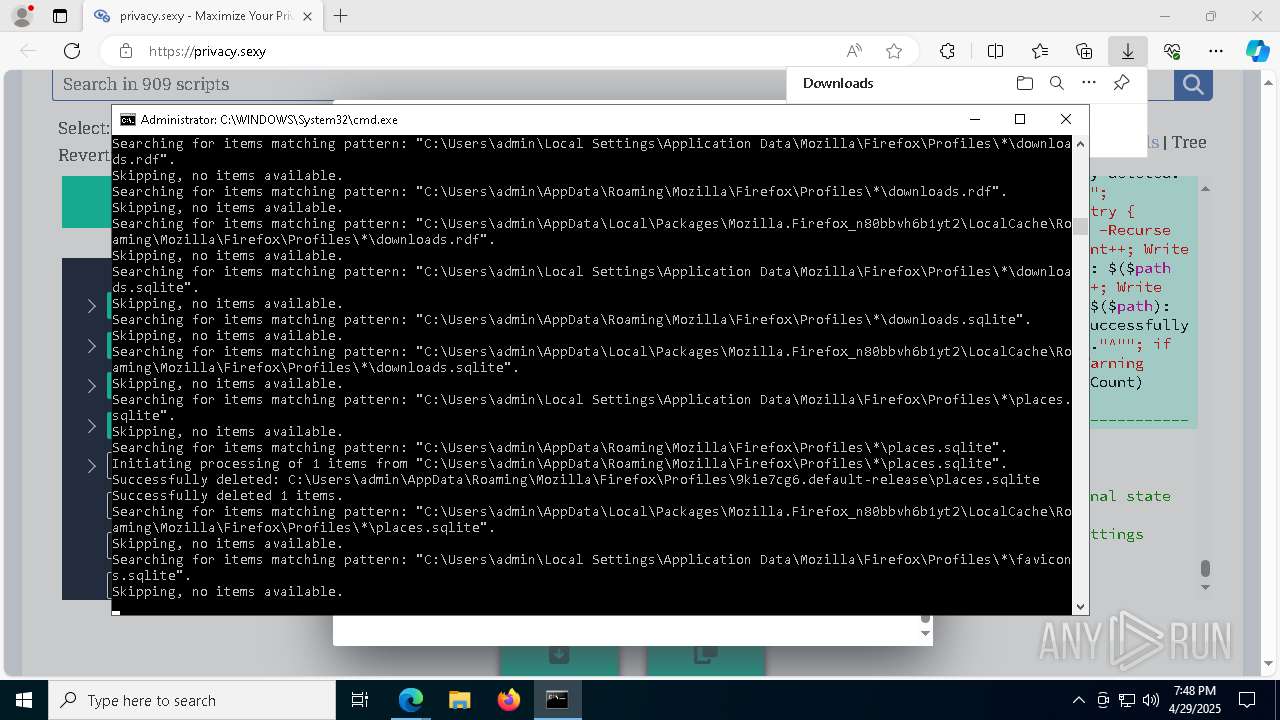
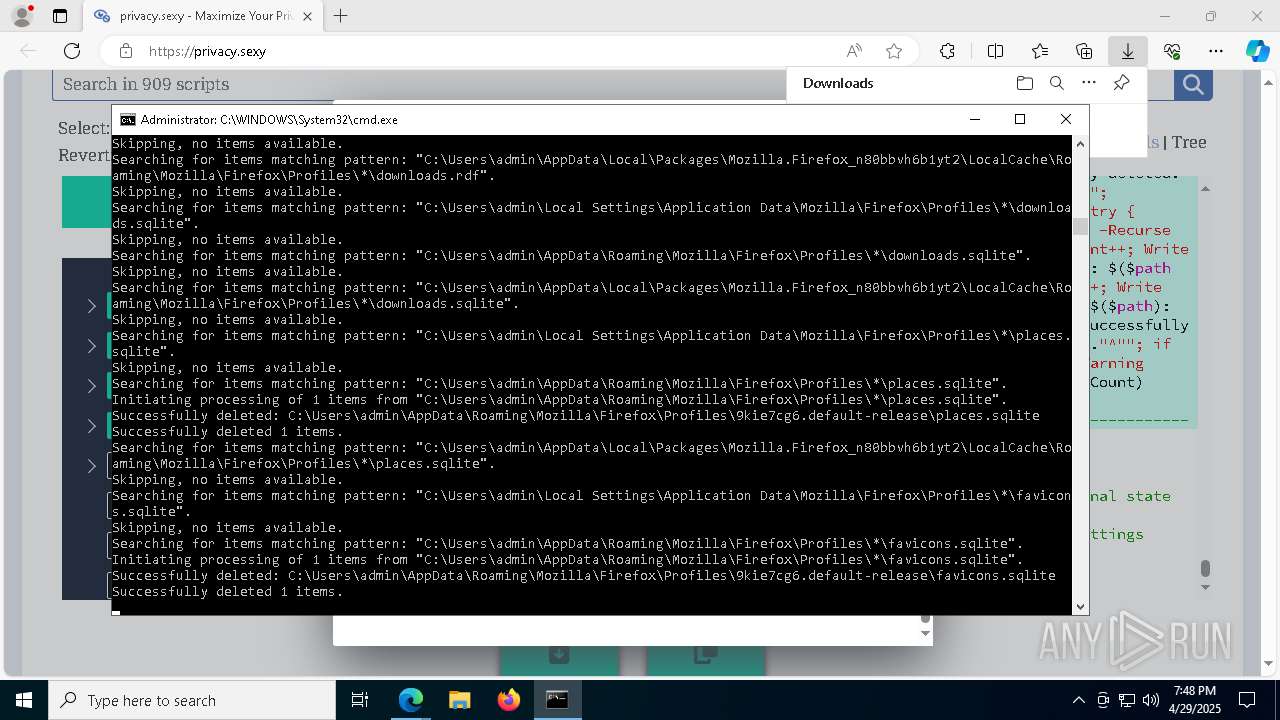
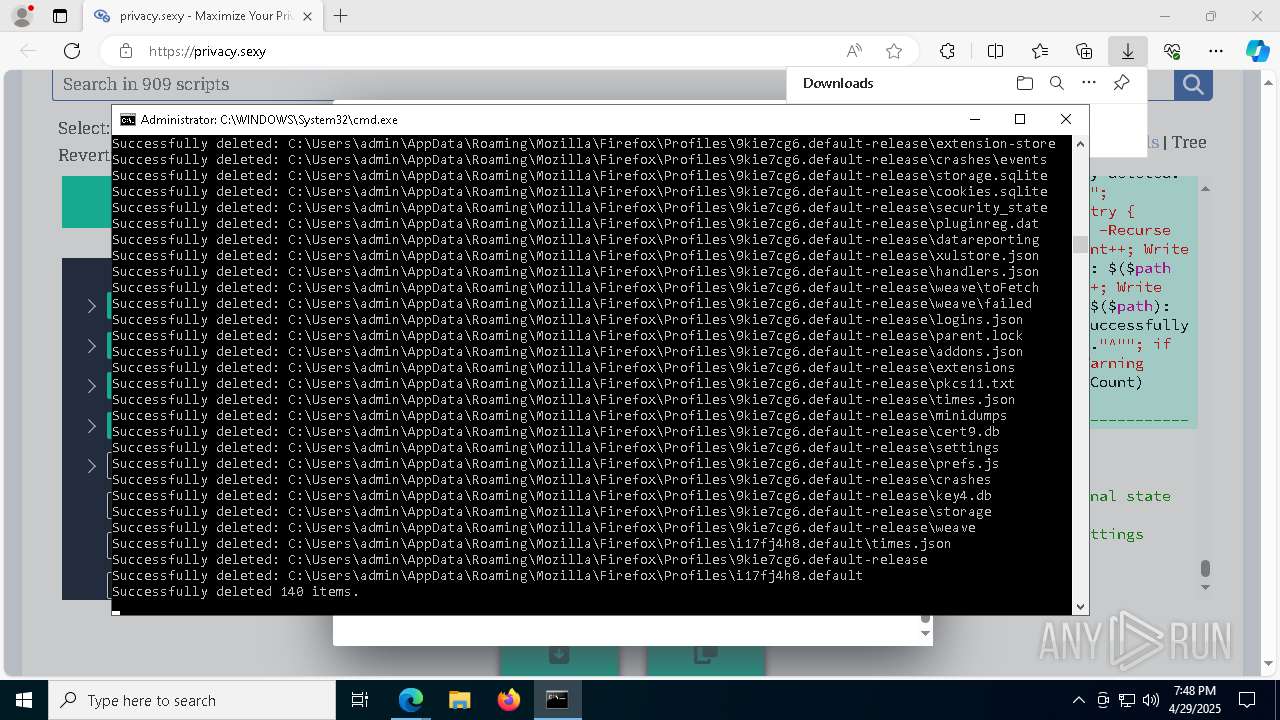
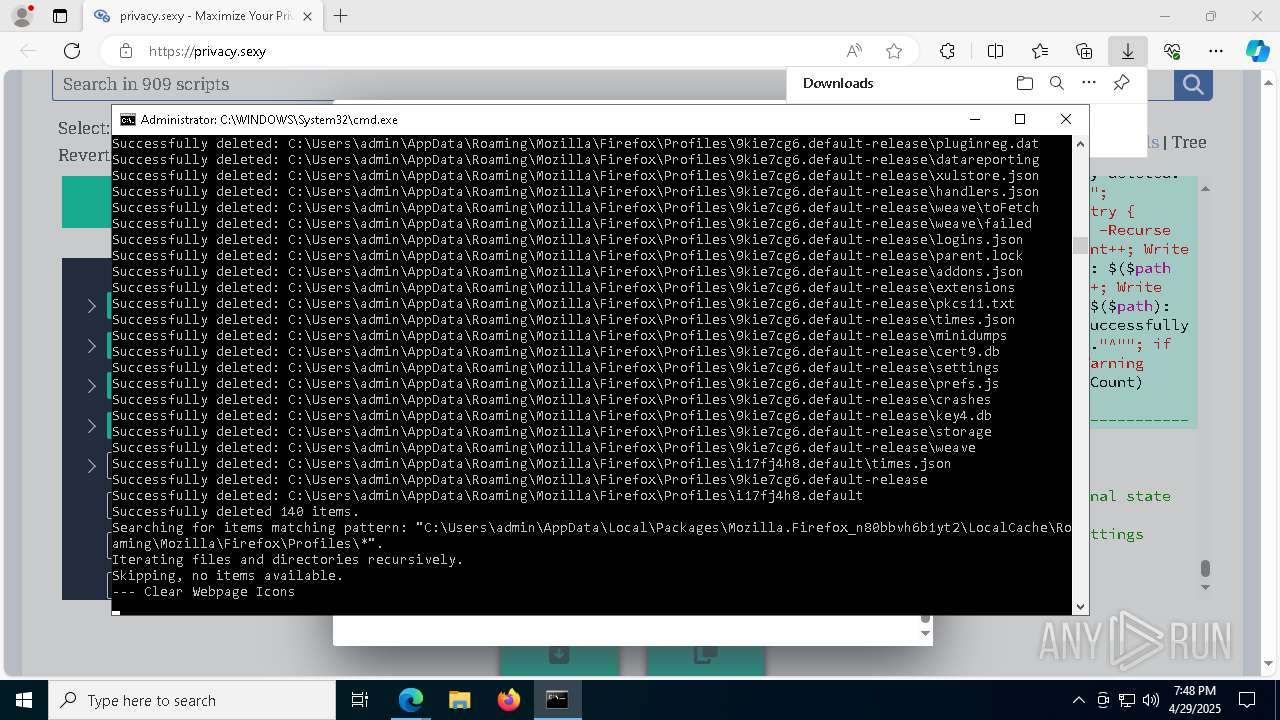
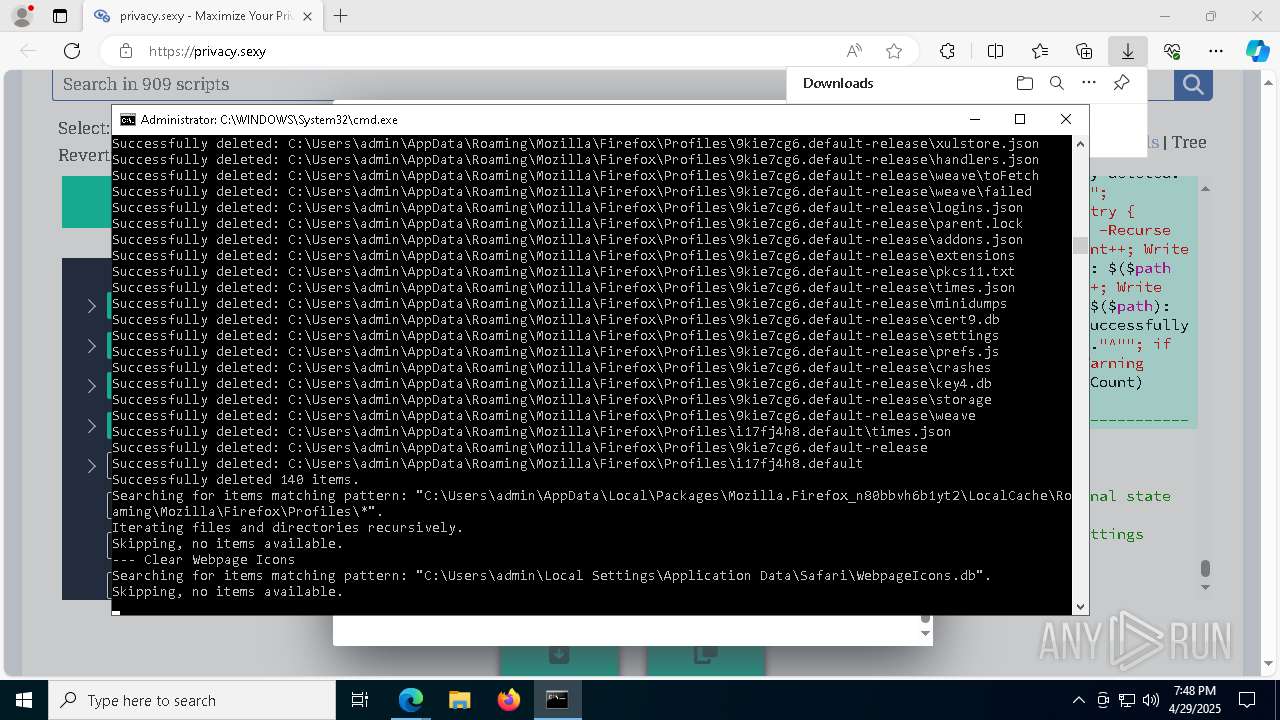
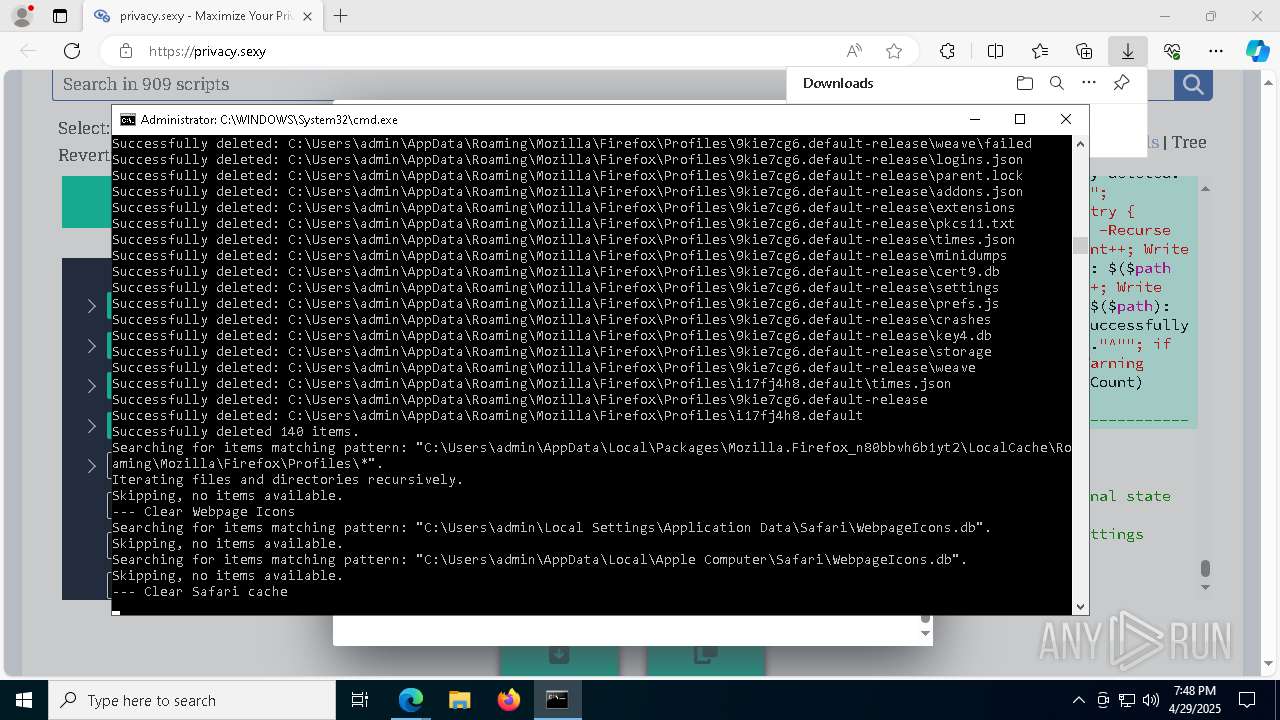
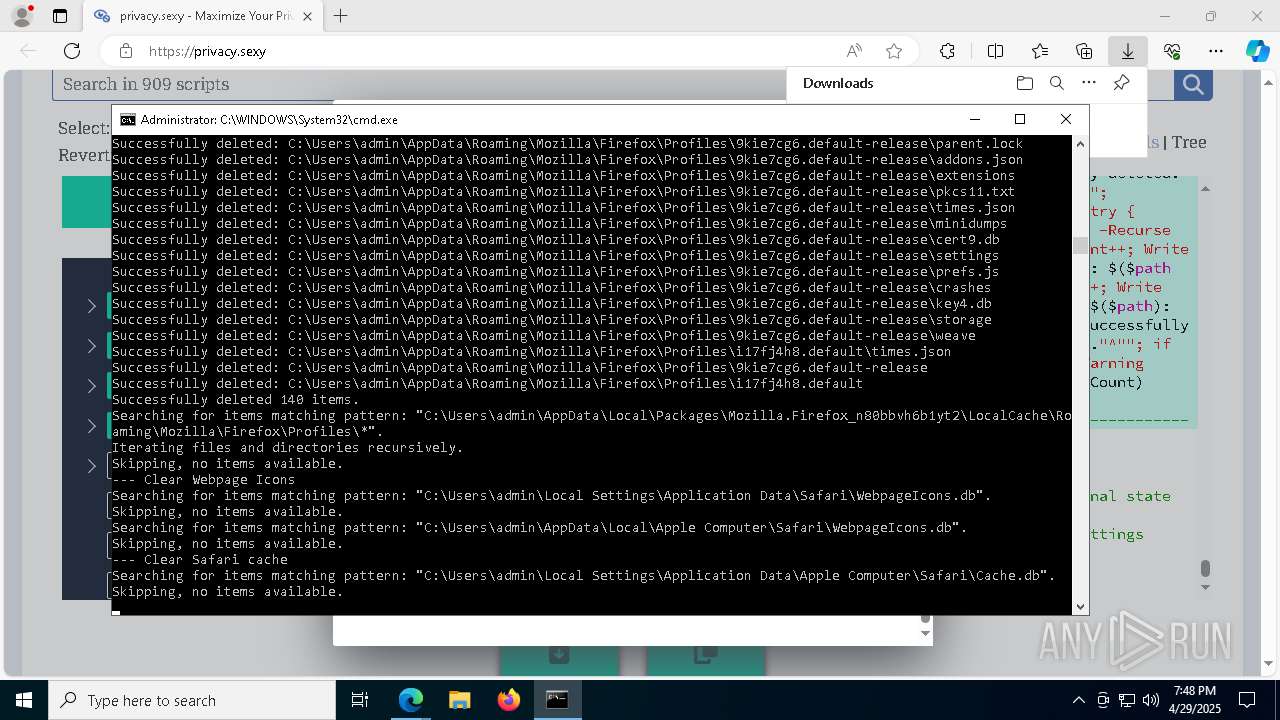
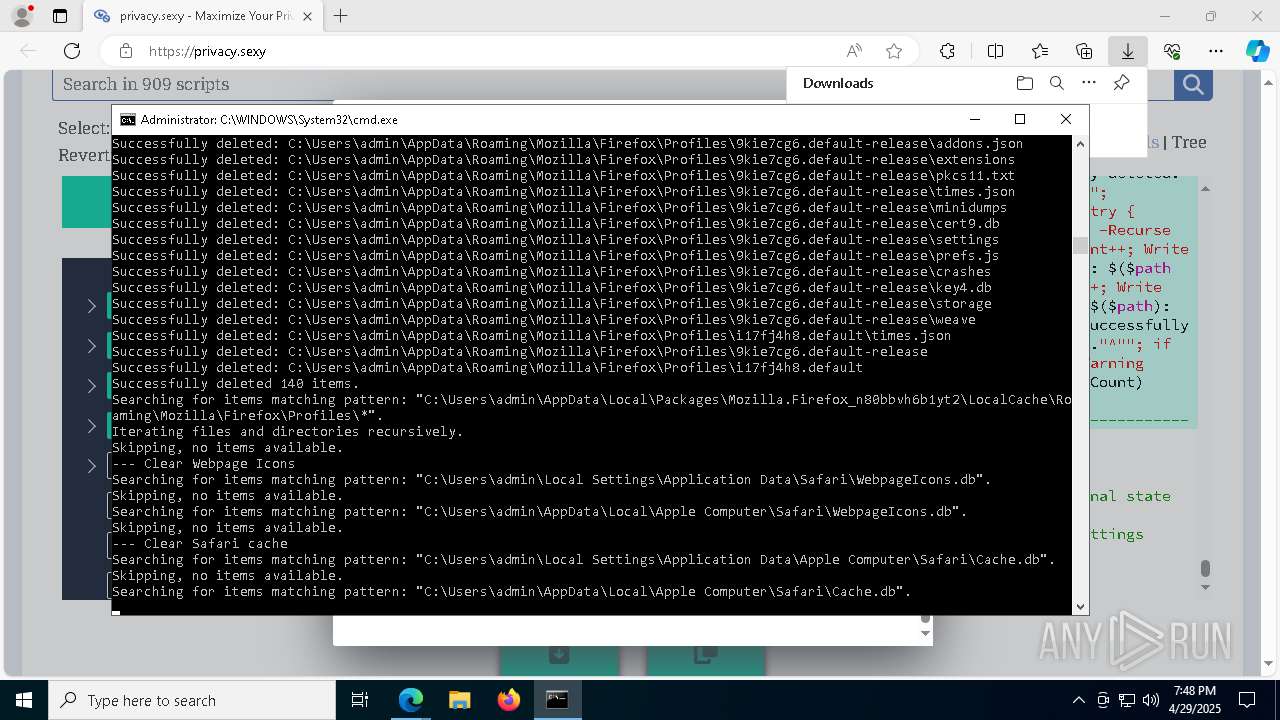
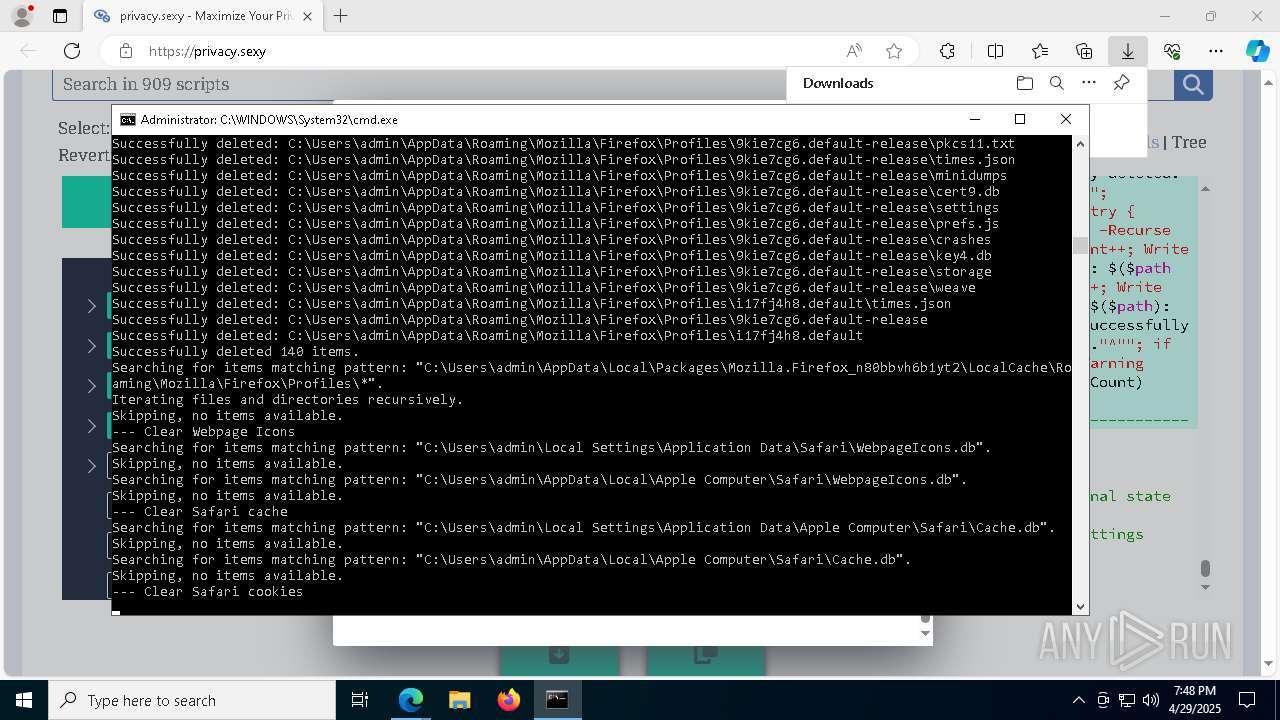
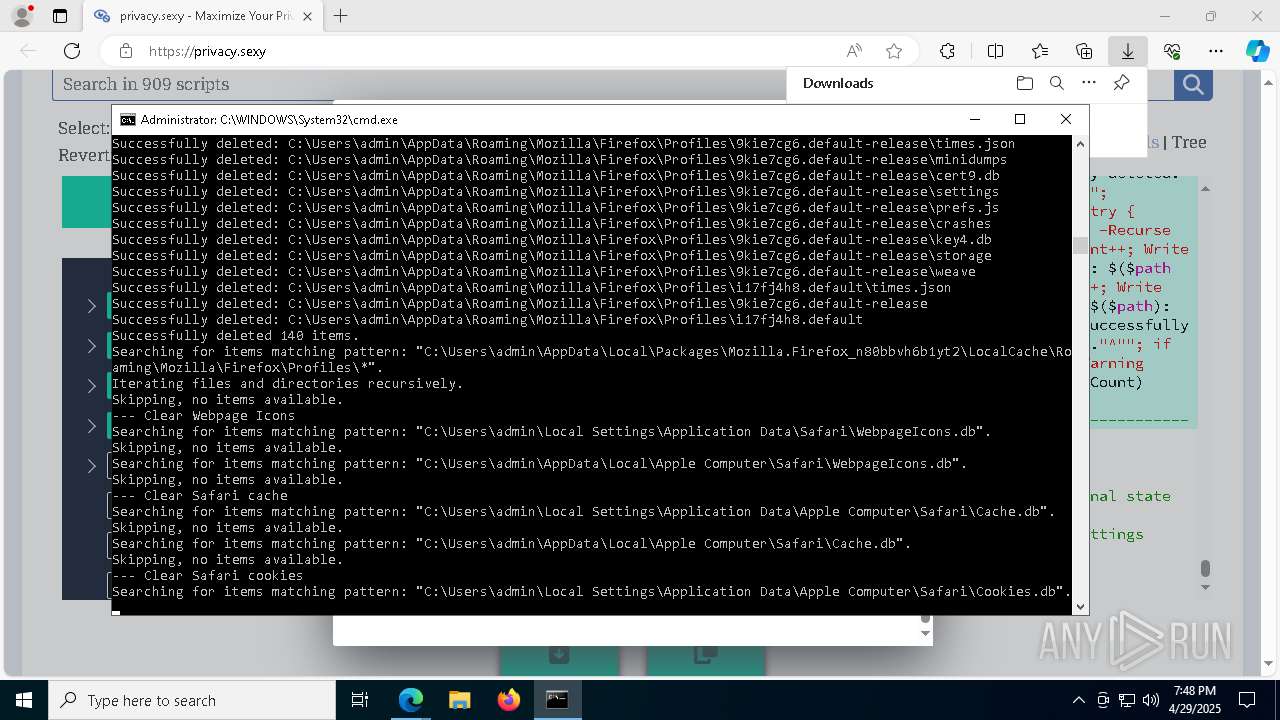
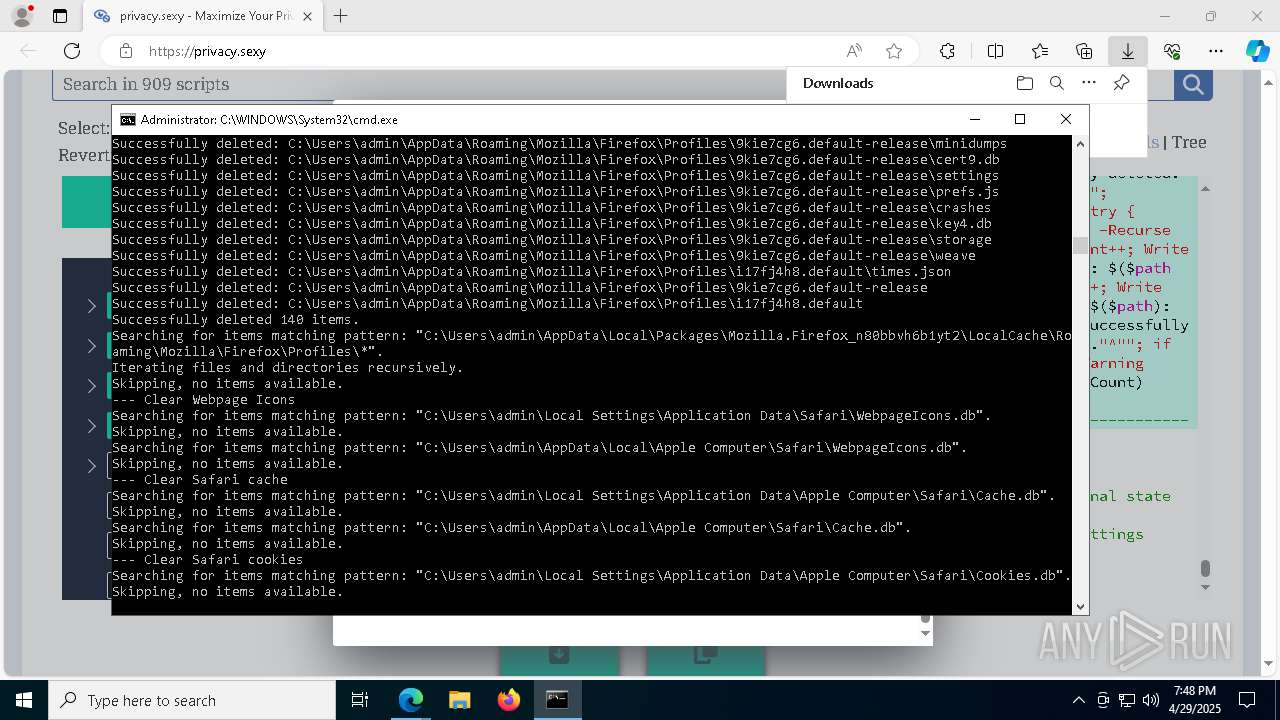
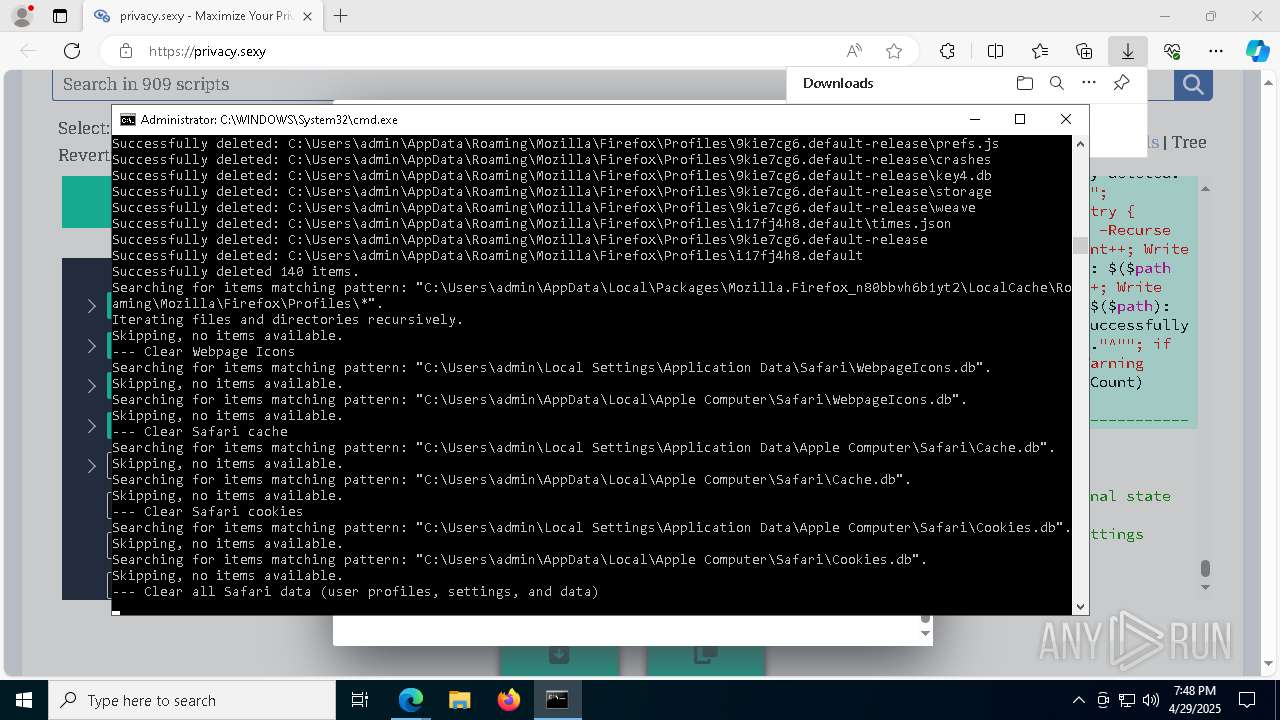
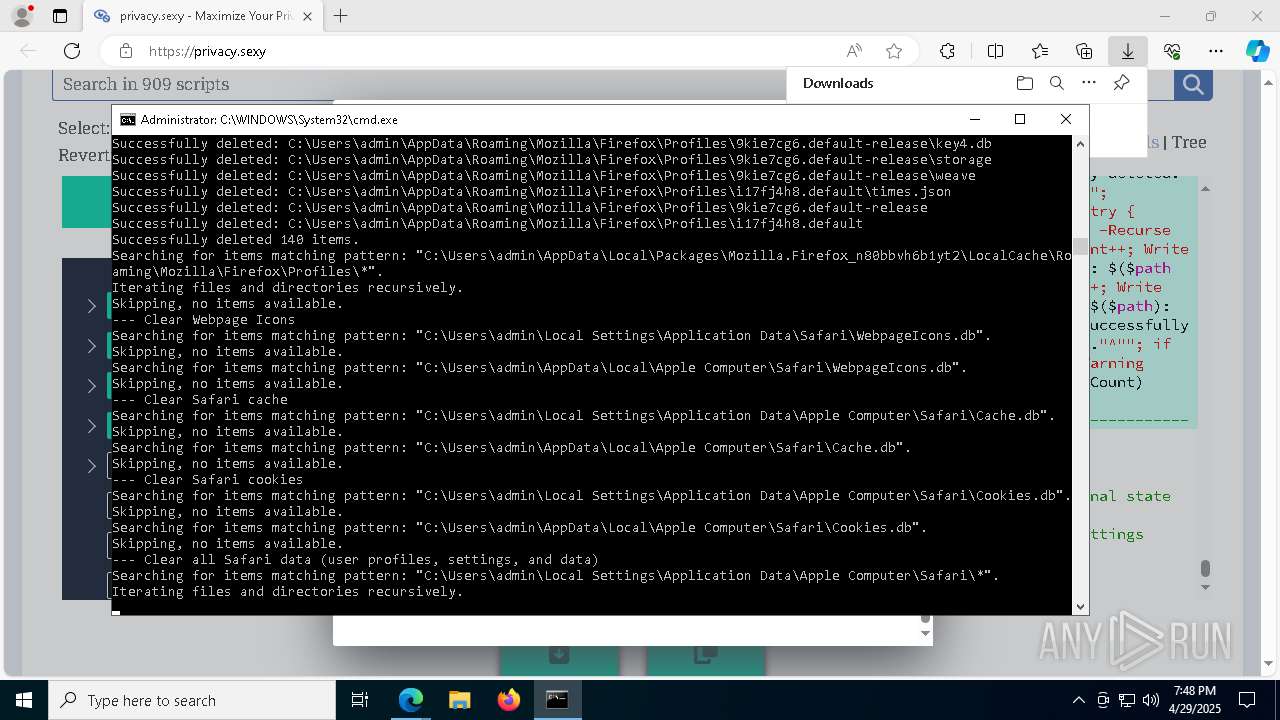
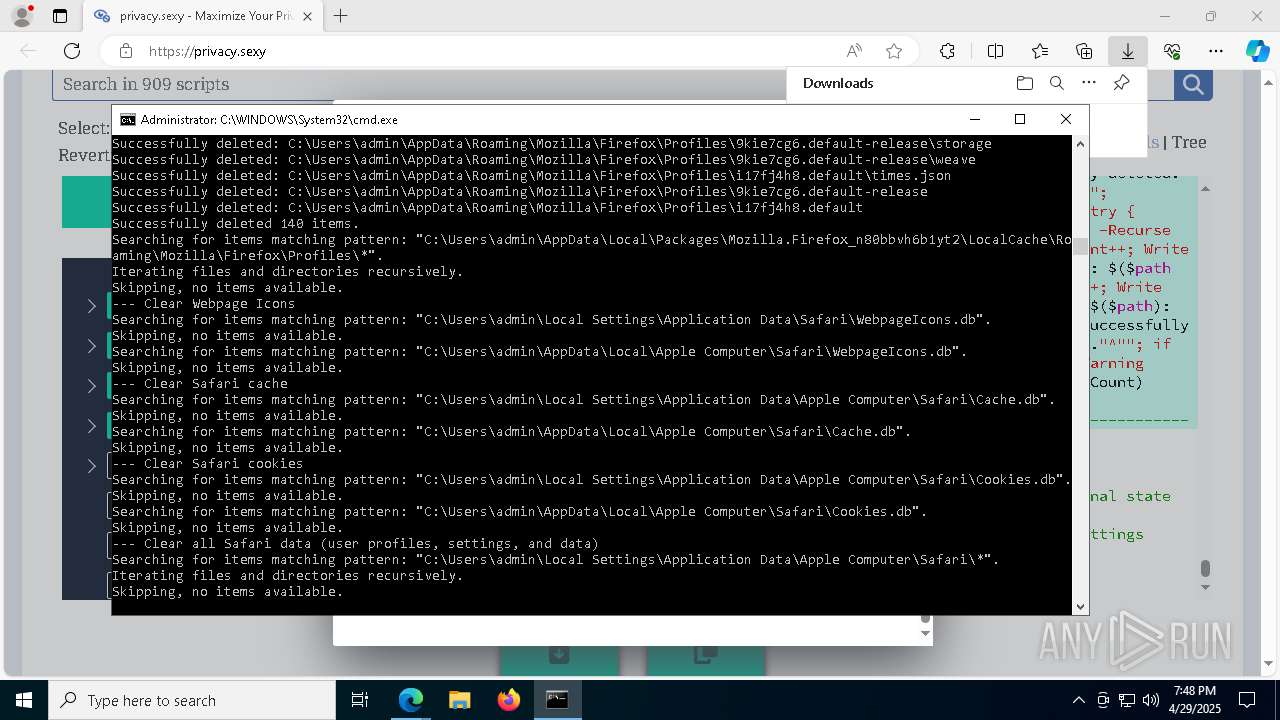
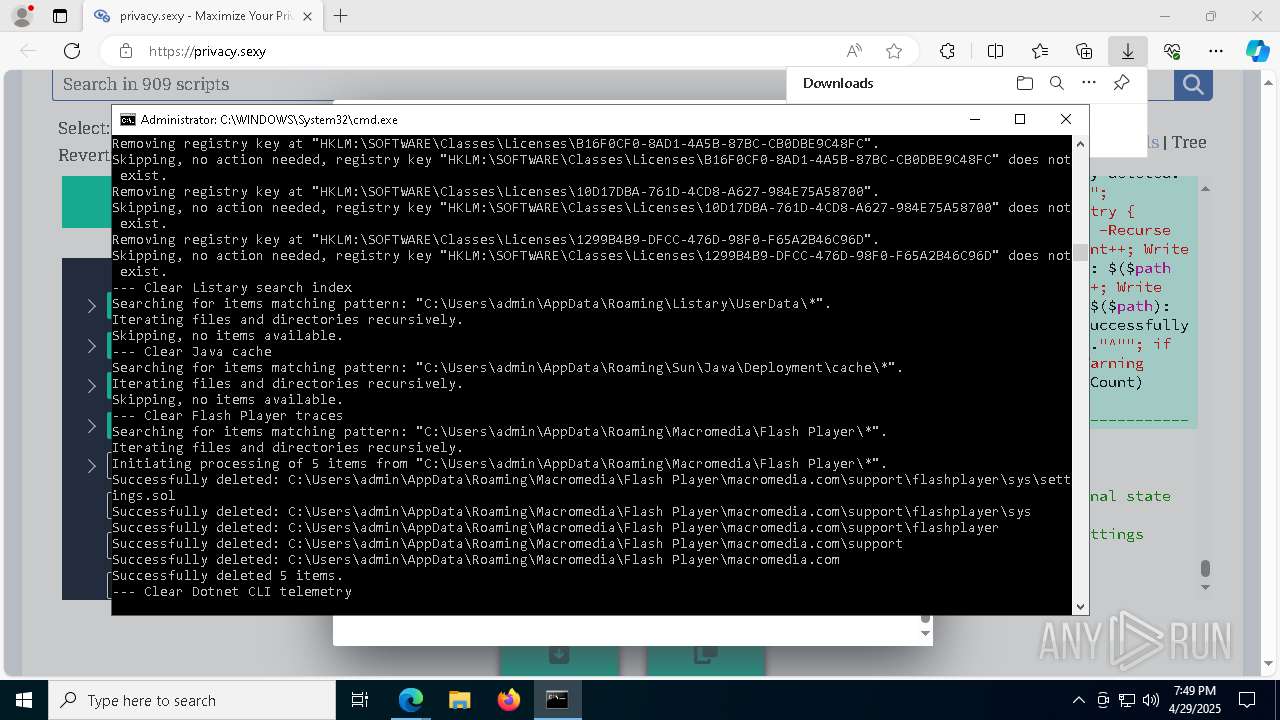
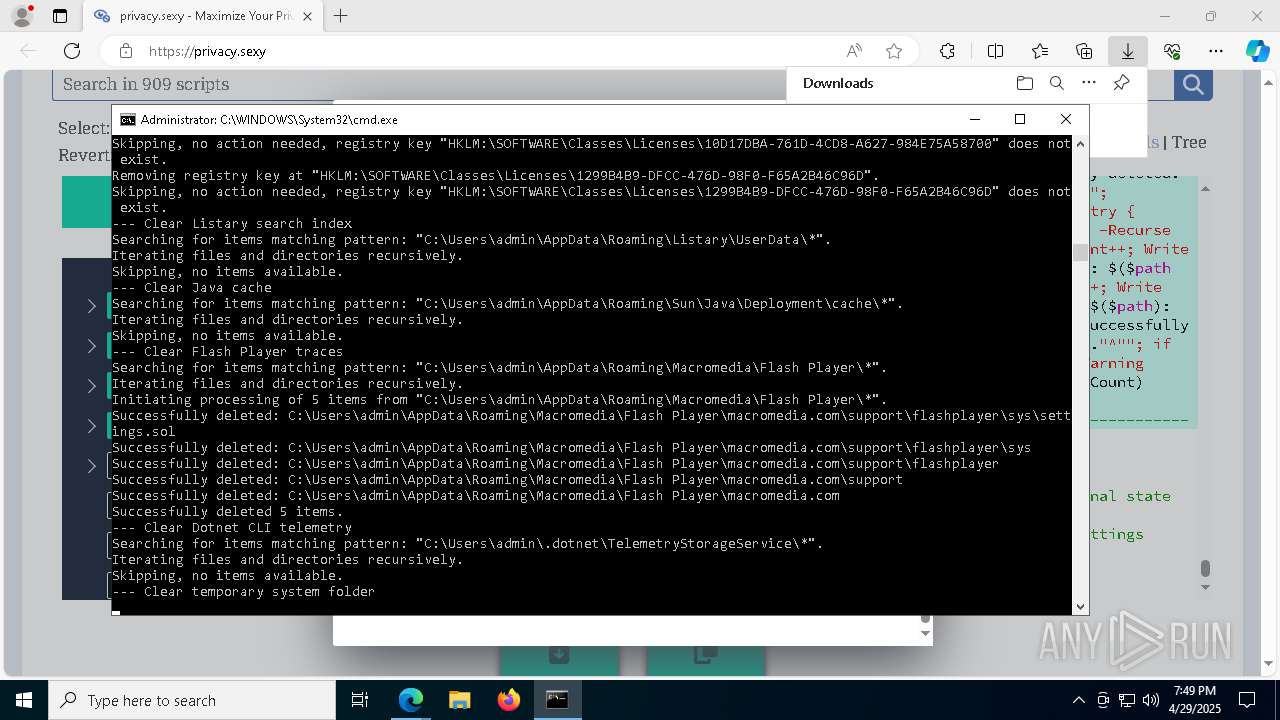
Removes files via Powershell
- powershell.exe (PID: 3396)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 5216)
- powershell.exe (PID: 7432)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 6072)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7828)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 4896)
- powershell.exe (PID: 5328)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 4268)
- powershell.exe (PID: 2344)
- powershell.exe (PID: 472)
- powershell.exe (PID: 5172)
- powershell.exe (PID: 1748)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 6900)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 7976)
- powershell.exe (PID: 3896)
- powershell.exe (PID: 5512)
- powershell.exe (PID: 5164)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 5892)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 7412)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 2564)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4180)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 7684)
- powershell.exe (PID: 5592)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 132)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 6808)
- powershell.exe (PID: 2596)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 4728)
- powershell.exe (PID: 7008)
- powershell.exe (PID: 632)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 5024)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 2332)
- powershell.exe (PID: 4304)
- powershell.exe (PID: 7548)
- powershell.exe (PID: 1012)
- powershell.exe (PID: 2776)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 448)
- powershell.exe (PID: 6036)
- powershell.exe (PID: 7100)
- powershell.exe (PID: 1868)
- powershell.exe (PID: 6456)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 7408)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 1748)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7336)
- cmd.exe (PID: 6480)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 7336)
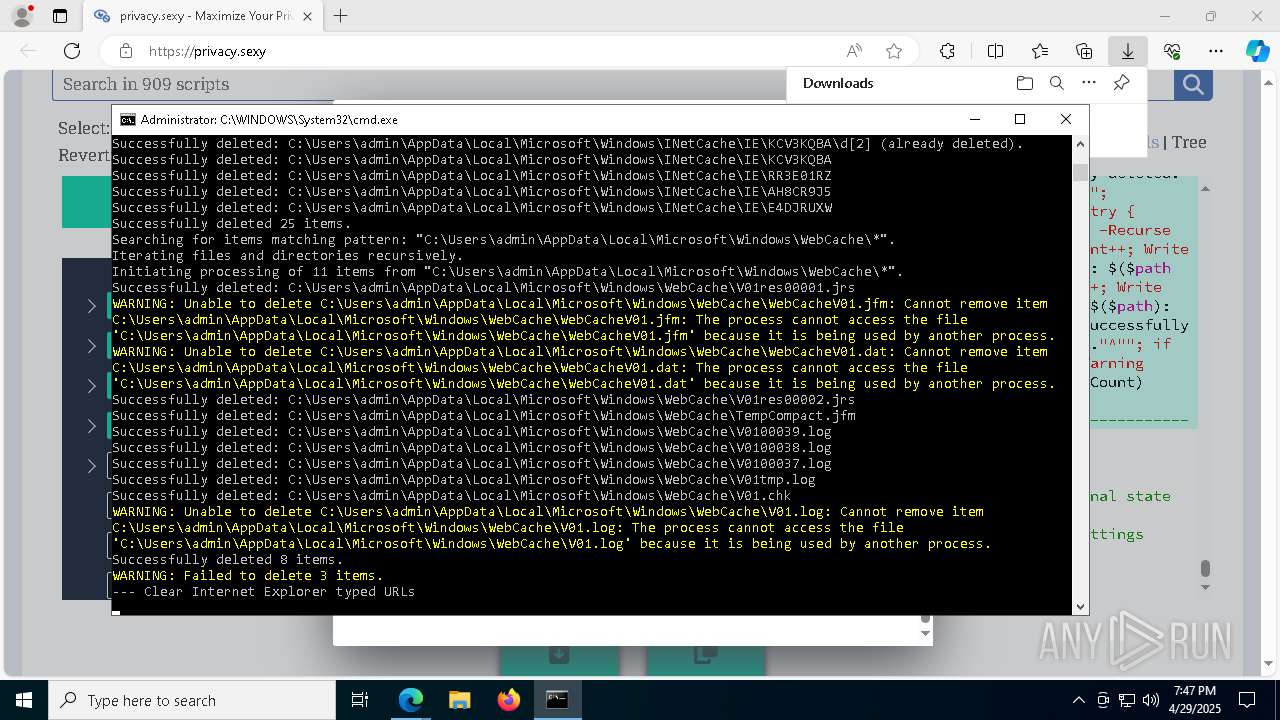
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 6700)
- cmd.exe (PID: 6480)
- cmd.exe (PID: 3968)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 7428)
- cmd.exe (PID: 4108)
- cmd.exe (PID: 6852)
INFO
Reads the computer name
- identity_helper.exe (PID: 7152)
Application launched itself
- msedge.exe (PID: 7476)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 7144)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 2560)
- powershell.exe (PID: 5216)
- powershell.exe (PID: 7432)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 6072)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 7828)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 4896)
- powershell.exe (PID: 5328)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 4268)
- powershell.exe (PID: 2344)
- powershell.exe (PID: 472)
- powershell.exe (PID: 5172)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 6900)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 7976)
- powershell.exe (PID: 3896)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 5512)
- powershell.exe (PID: 5164)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 7412)
- powershell.exe (PID: 5892)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 2564)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 1748)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4180)
- powershell.exe (PID: 5592)
- powershell.exe (PID: 7684)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 2596)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 132)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 6808)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 4728)
- powershell.exe (PID: 632)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 7008)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 5024)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 4304)
- powershell.exe (PID: 2332)
- powershell.exe (PID: 6036)
- powershell.exe (PID: 2776)
- powershell.exe (PID: 1012)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 448)
- powershell.exe (PID: 7100)
- powershell.exe (PID: 7548)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 1868)
- powershell.exe (PID: 2616)
- powershell.exe (PID: 6456)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 7408)
- powershell.exe (PID: 1748)
Returns all items recursively from all subfolders (POWERSHELL)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 7432)
- powershell.exe (PID: 5736)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 6072)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 7828)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 5328)
- powershell.exe (PID: 4896)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4268)
- powershell.exe (PID: 2344)
- powershell.exe (PID: 472)
- powershell.exe (PID: 4012)
- powershell.exe (PID: 5172)
- powershell.exe (PID: 1748)
- powershell.exe (PID: 4200)
- powershell.exe (PID: 6900)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 3896)
- powershell.exe (PID: 2780)
- powershell.exe (PID: 5512)
- powershell.exe (PID: 7976)
- powershell.exe (PID: 5164)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 1244)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 5892)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 7412)
- powershell.exe (PID: 2564)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 7240)
- powershell.exe (PID: 7368)
- powershell.exe (PID: 4180)
- powershell.exe (PID: 5116)
- powershell.exe (PID: 5416)
- powershell.exe (PID: 7684)
- powershell.exe (PID: 5592)
- powershell.exe (PID: 132)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 2596)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 6808)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 4728)
- powershell.exe (PID: 632)
- powershell.exe (PID: 4112)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 7008)
- powershell.exe (PID: 5024)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 2084)
- powershell.exe (PID: 4304)
- powershell.exe (PID: 2332)
- powershell.exe (PID: 7548)
- powershell.exe (PID: 6036)
- powershell.exe (PID: 6456)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 7408)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 2408)
- powershell.exe (PID: 1748)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3396)
- powershell.exe (PID: 4696)
- powershell.exe (PID: 2560)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2560)
Reads the software policy settings
- slui.exe (PID: 4424)
Reads Environment values
- identity_helper.exe (PID: 7152)
Checks supported languages
- identity_helper.exe (PID: 7152)
The sample compiled with english language support
- msedge.exe (PID: 4696)
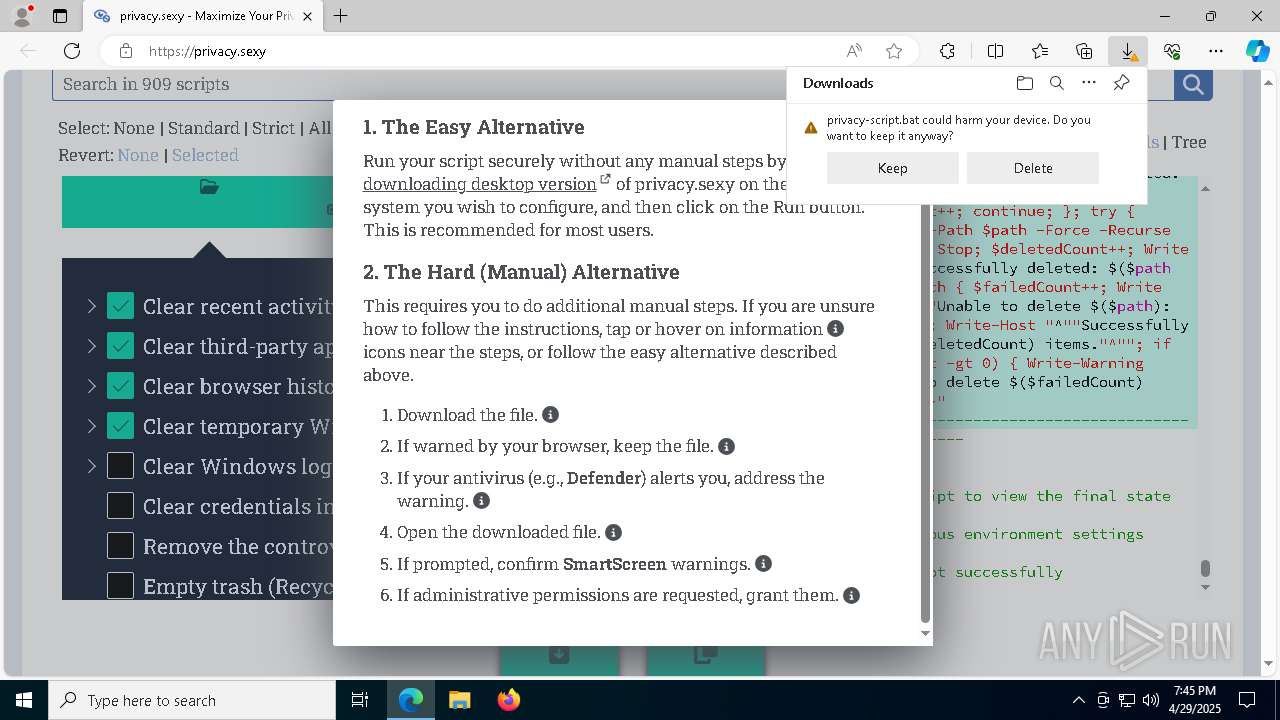
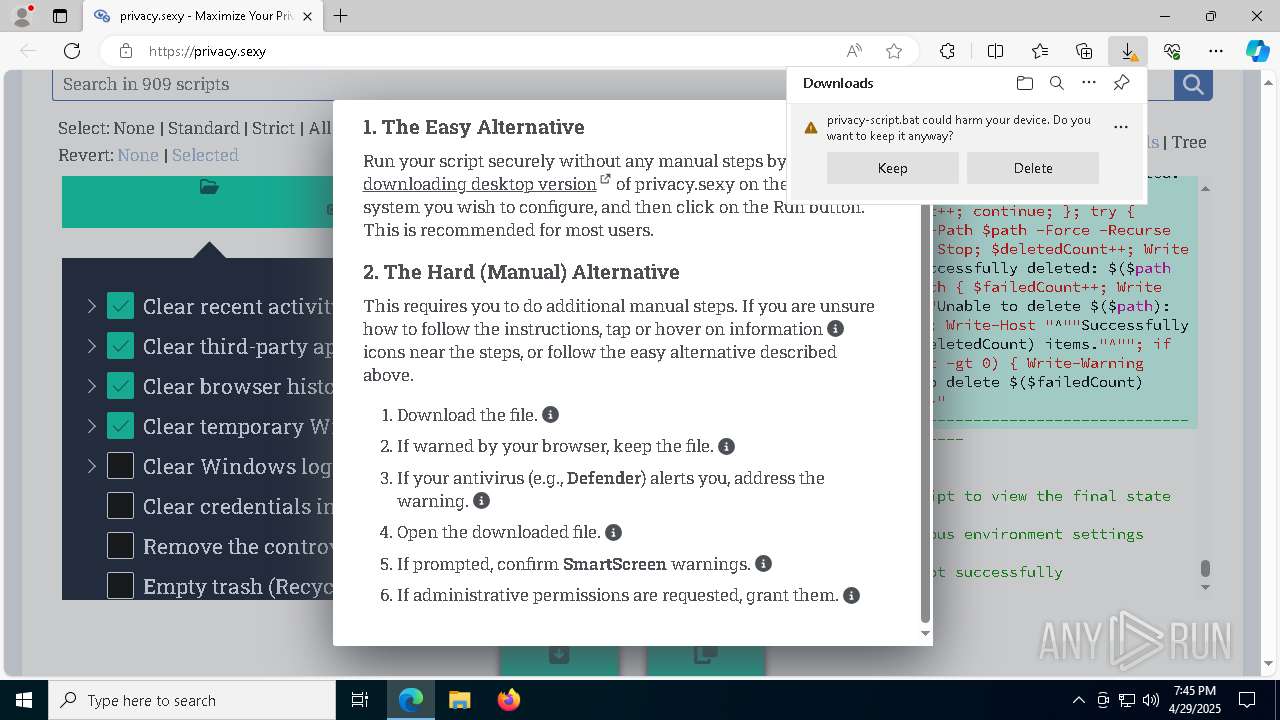
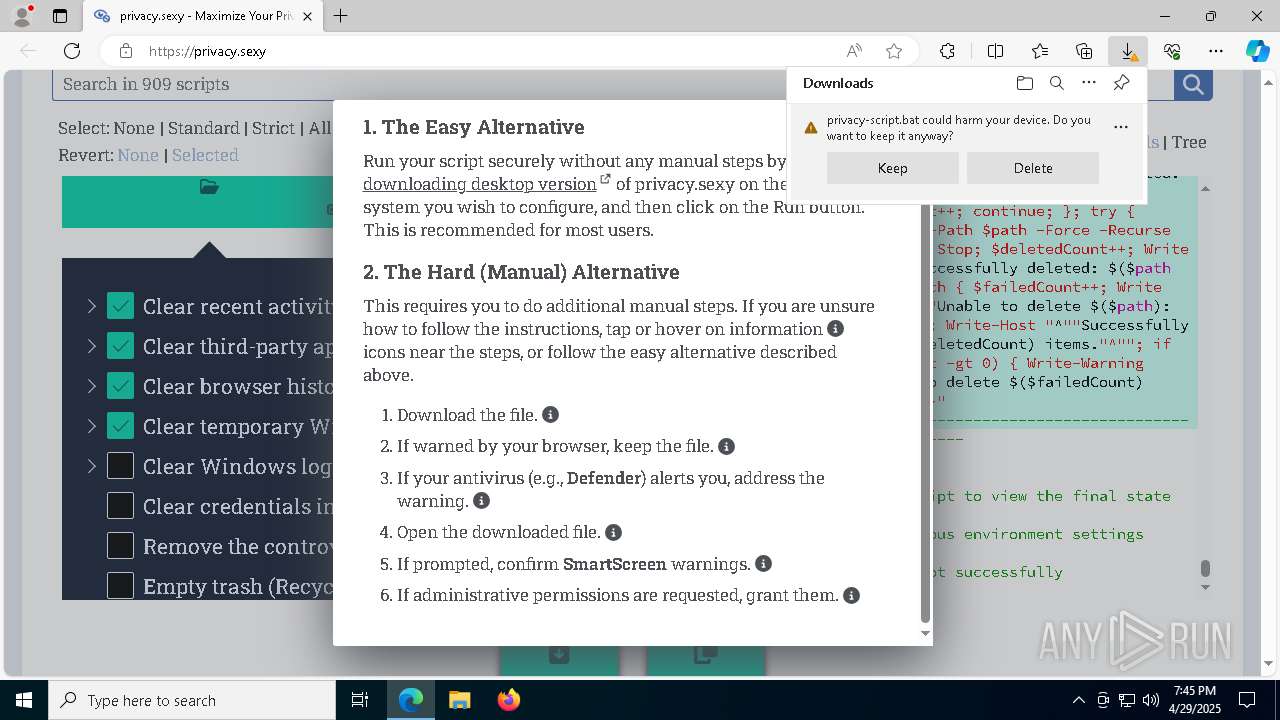
Executable content was dropped or overwritten
- msedge.exe (PID: 4696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
332
Monitored processes
196
Malicious processes
78
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
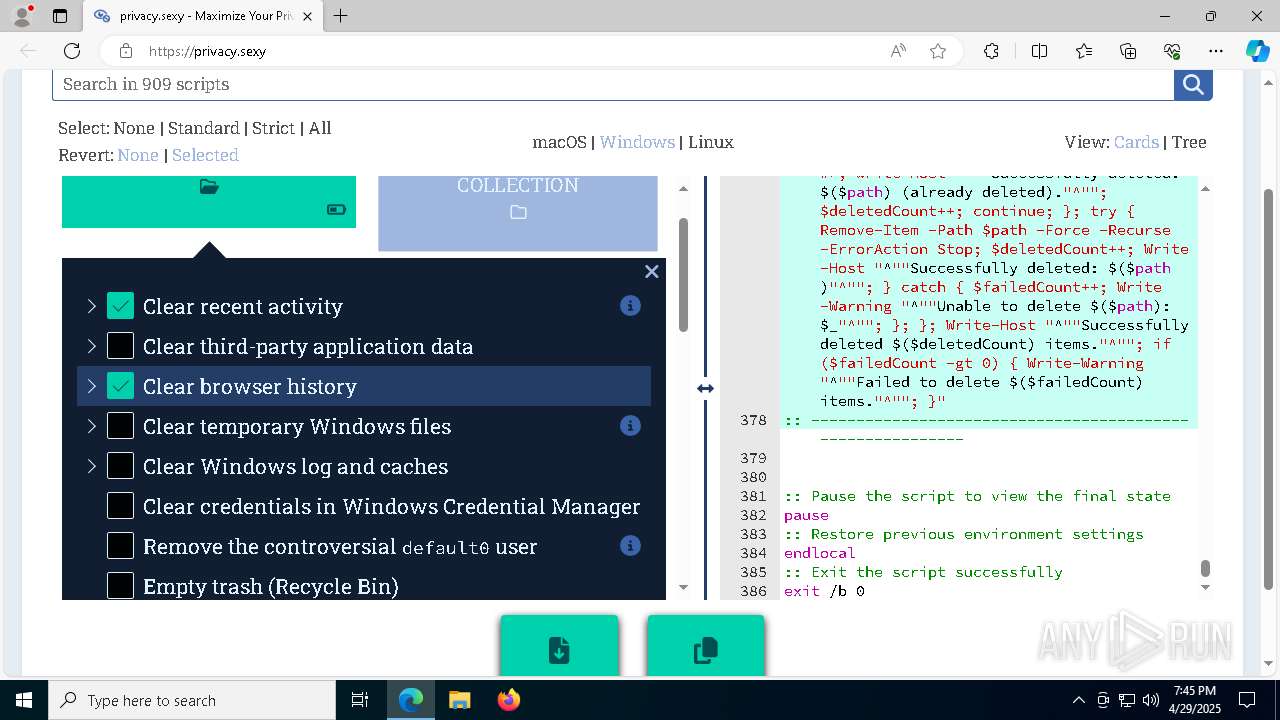
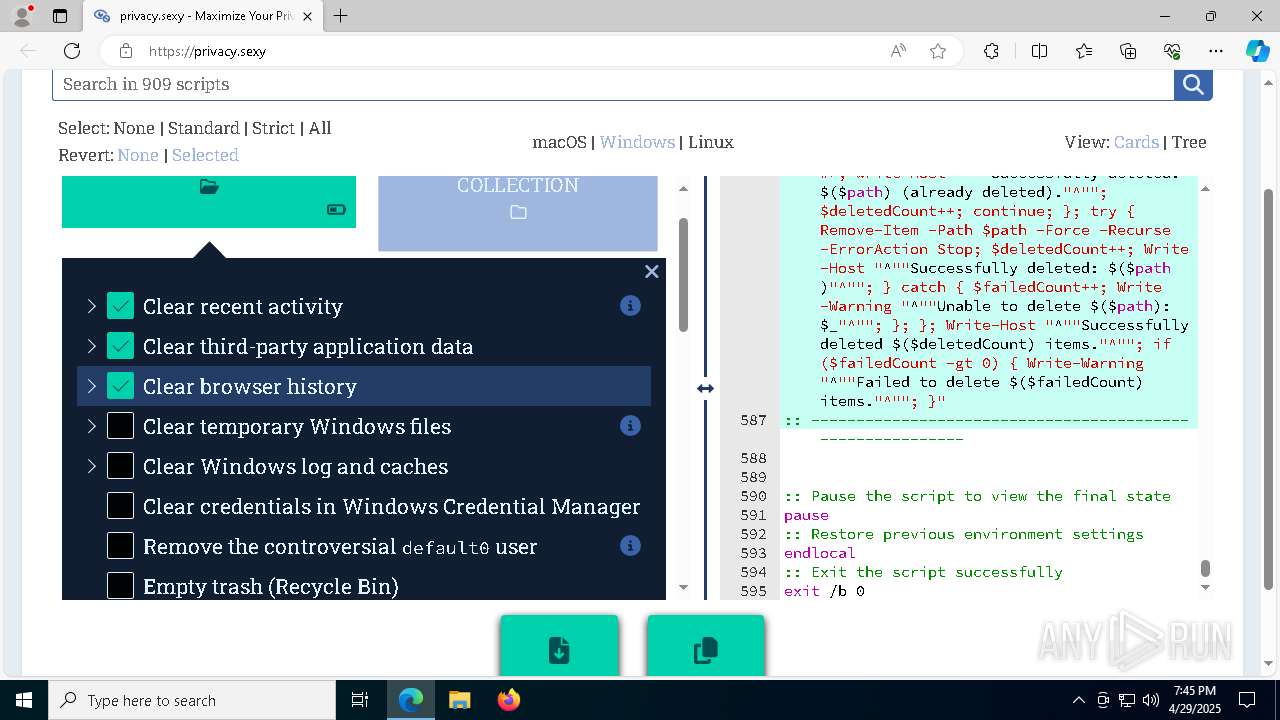
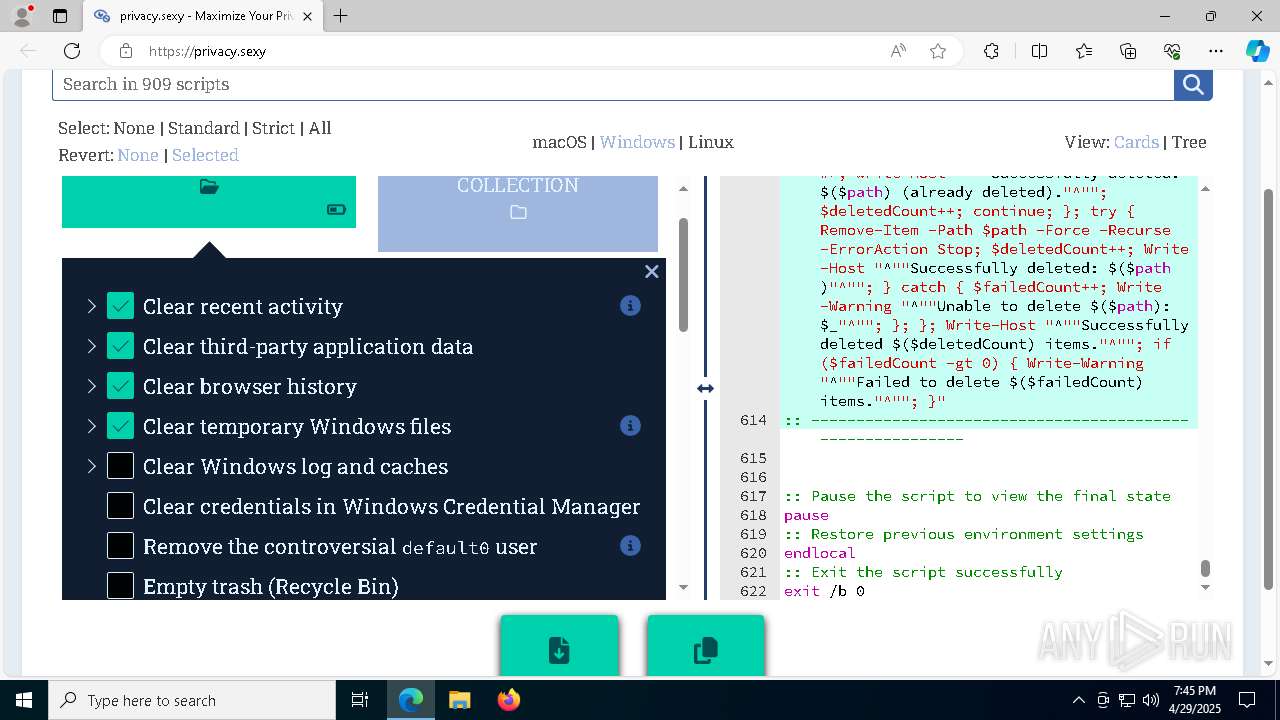
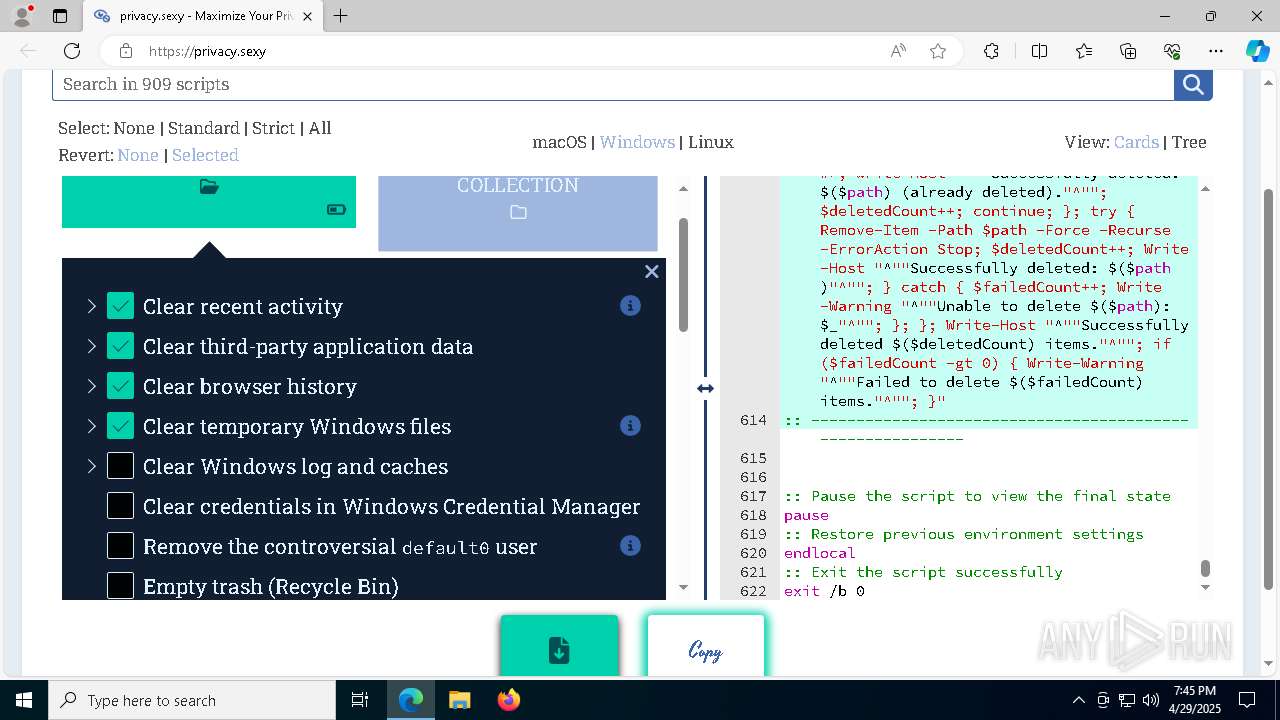
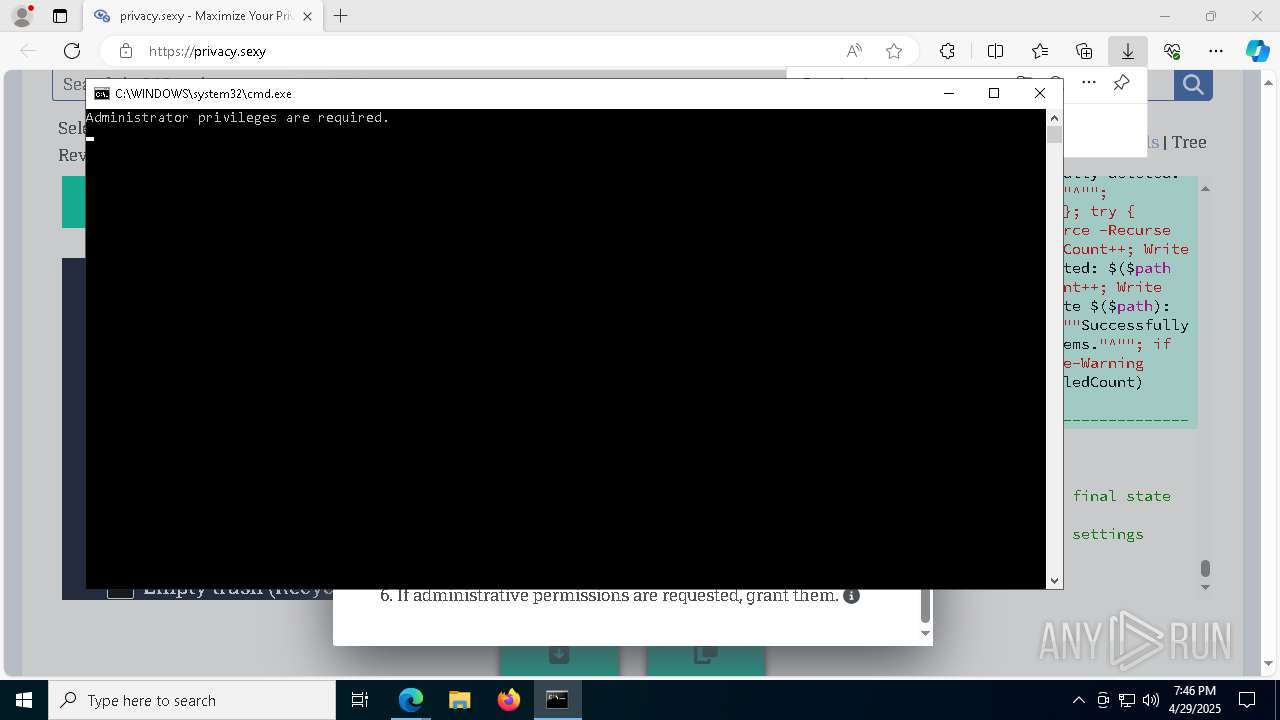
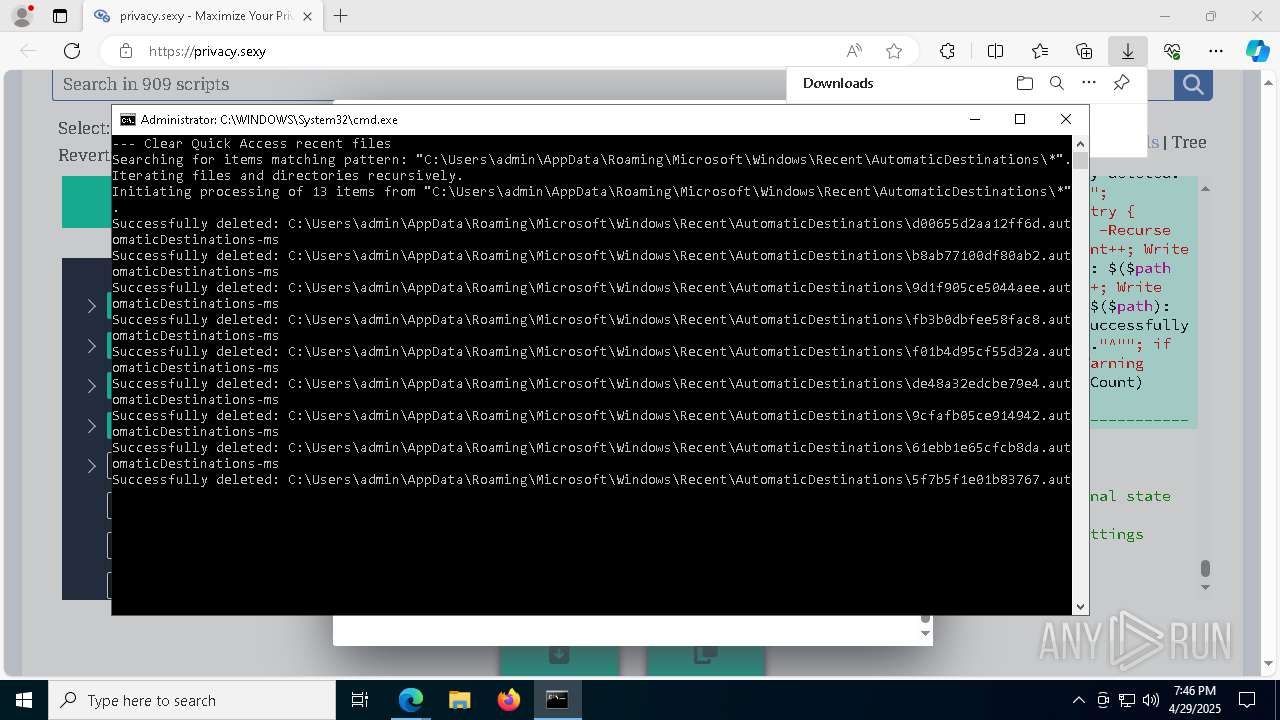
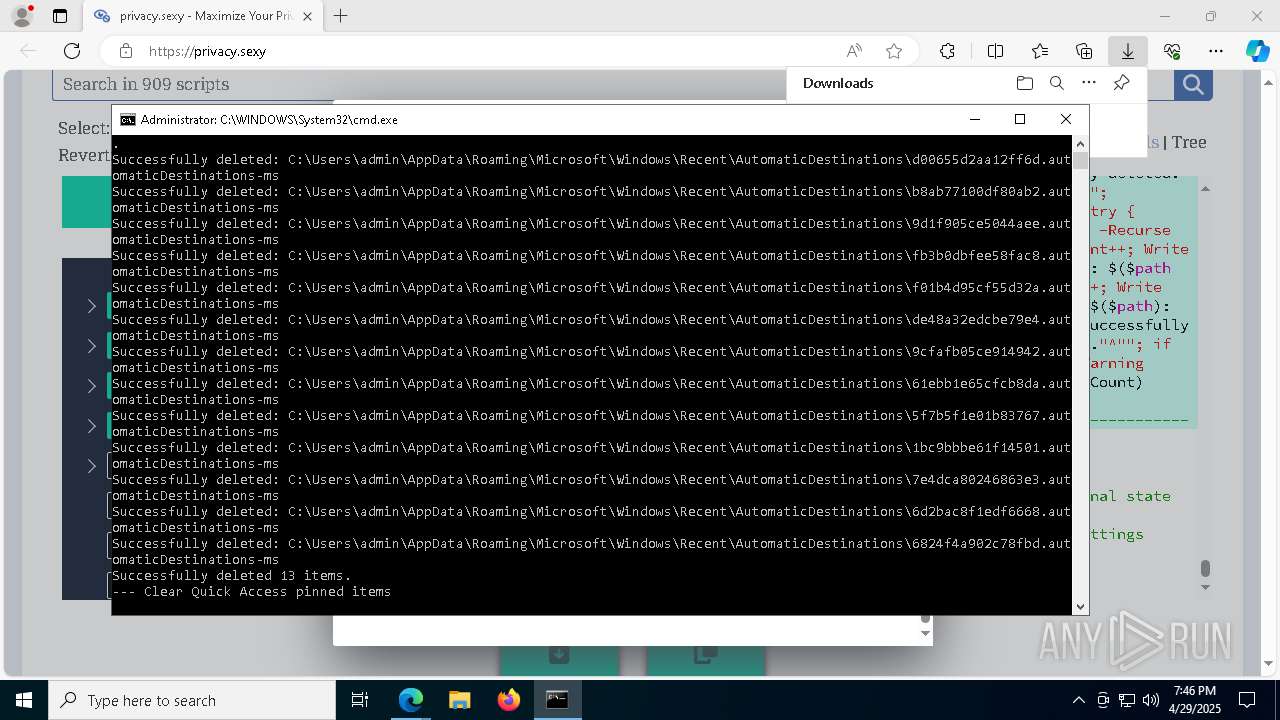
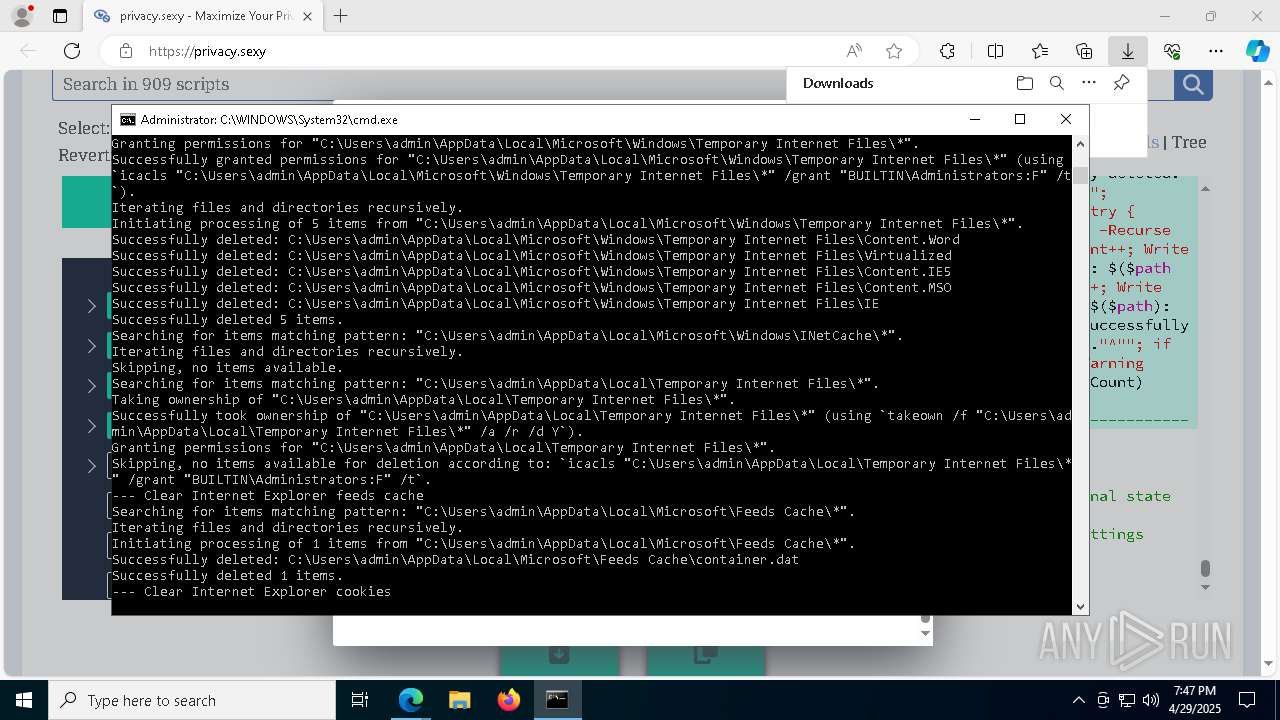
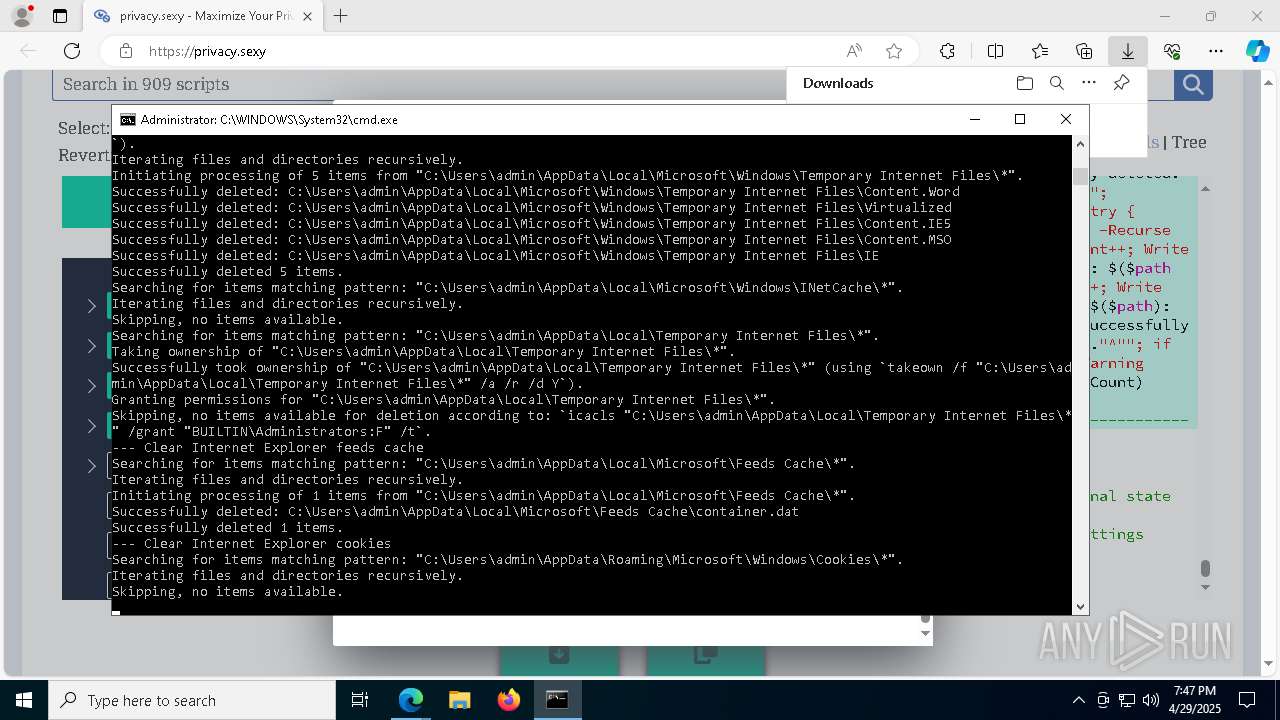
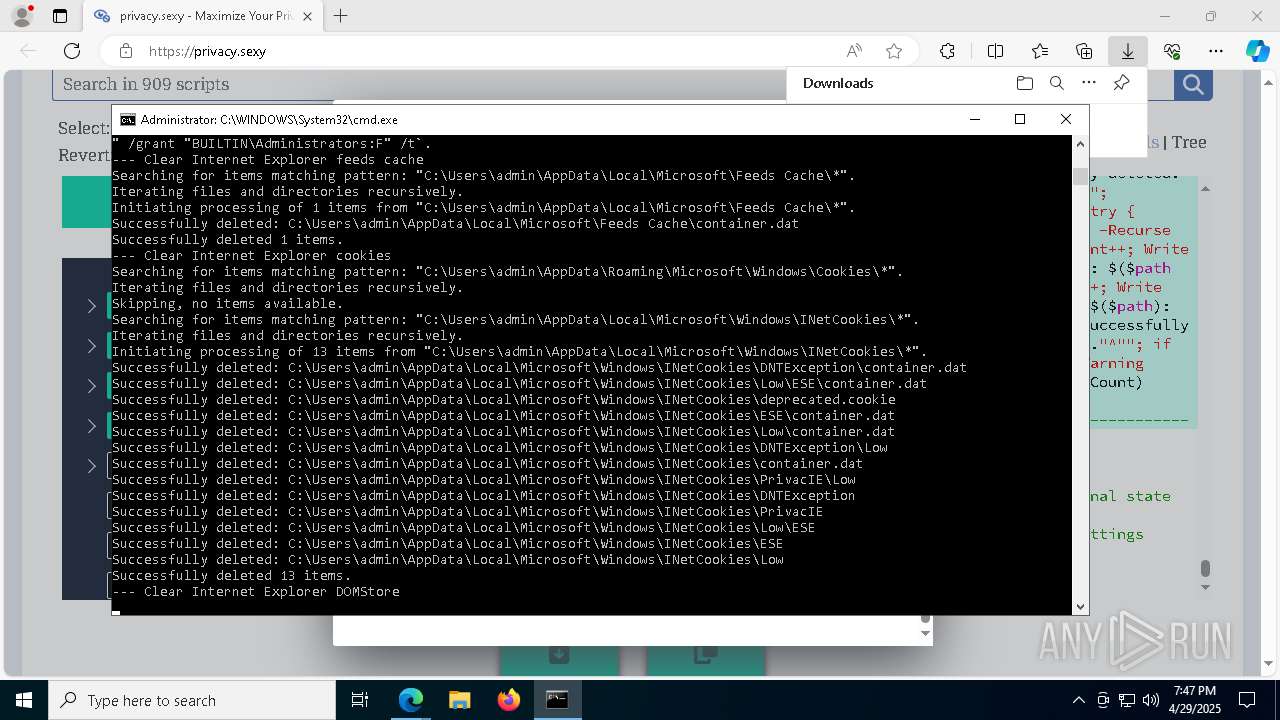
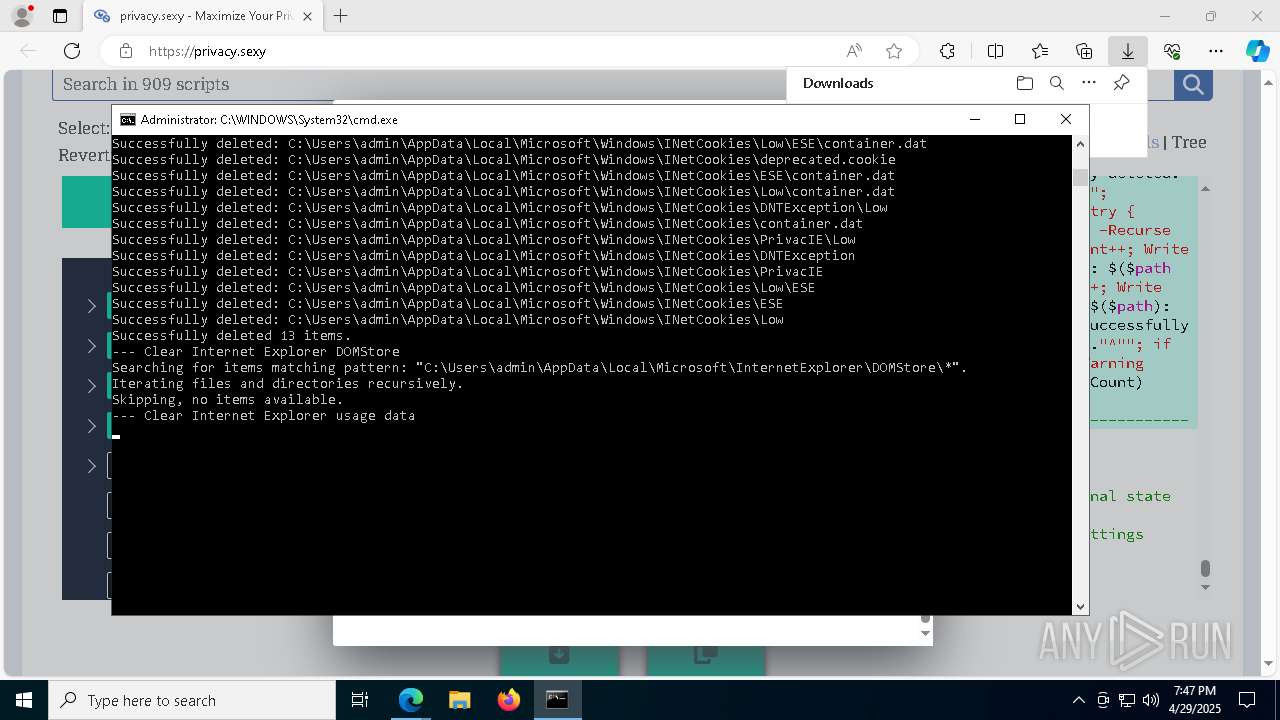
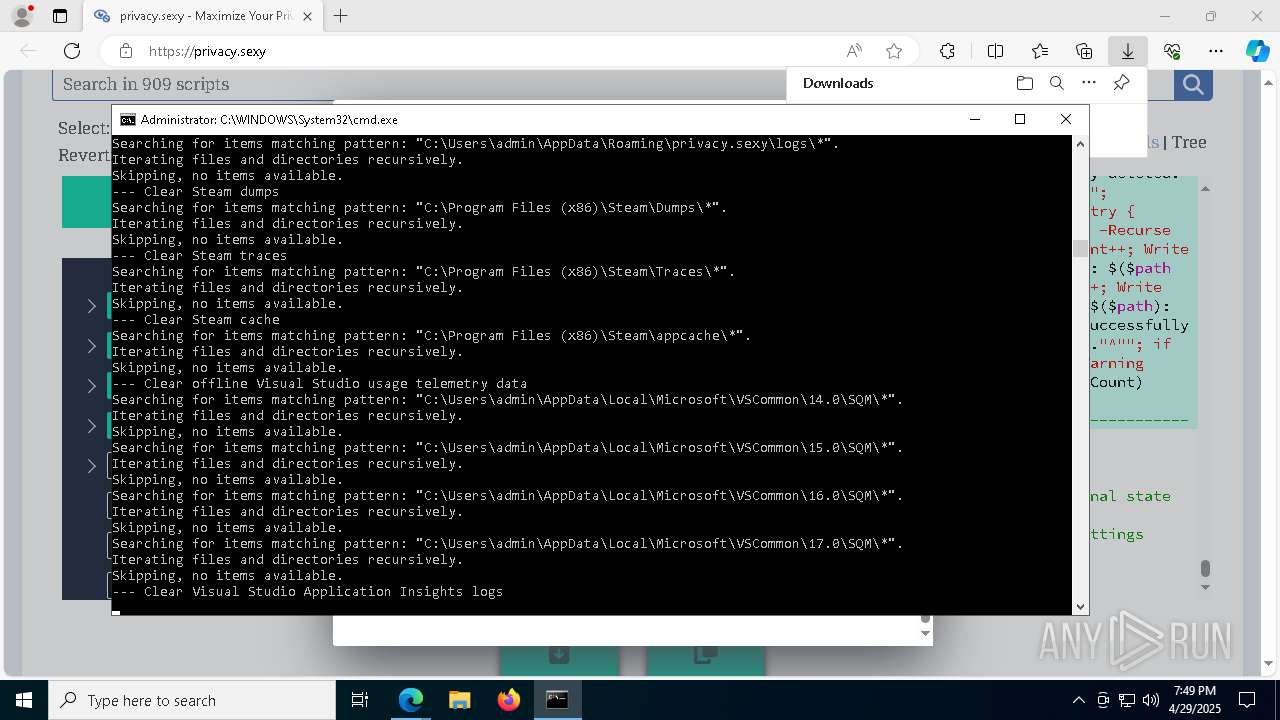
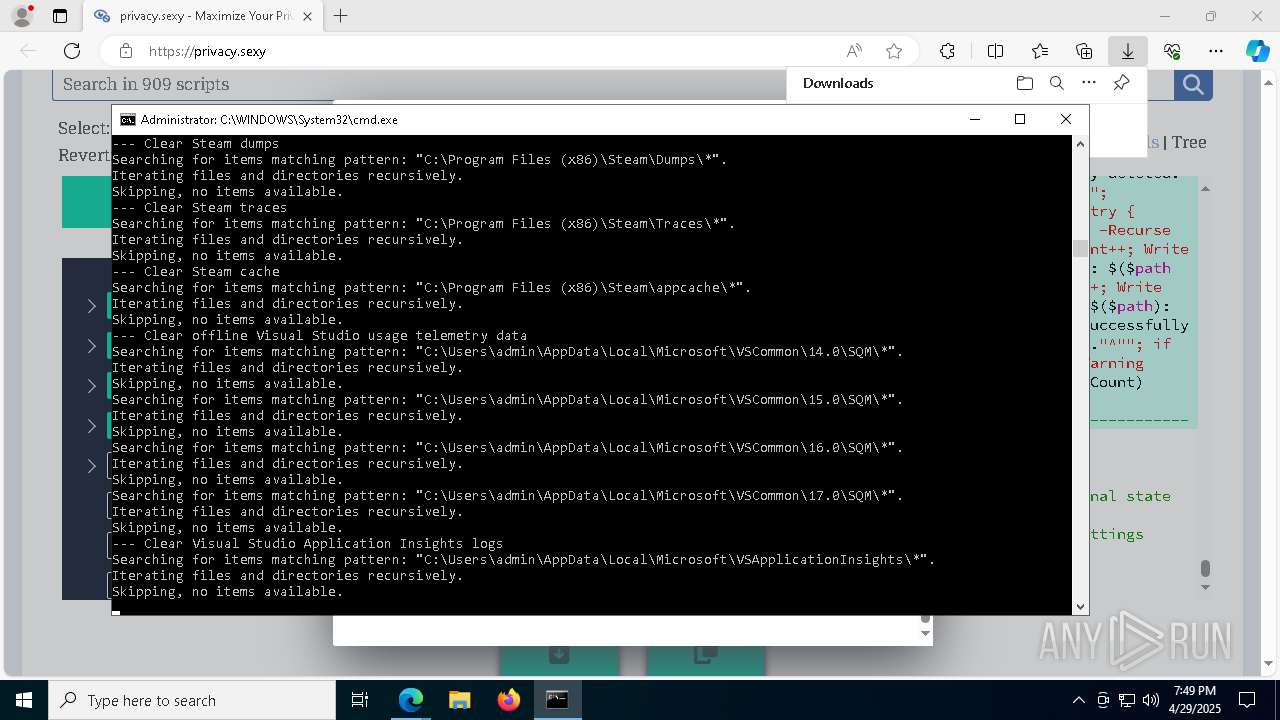
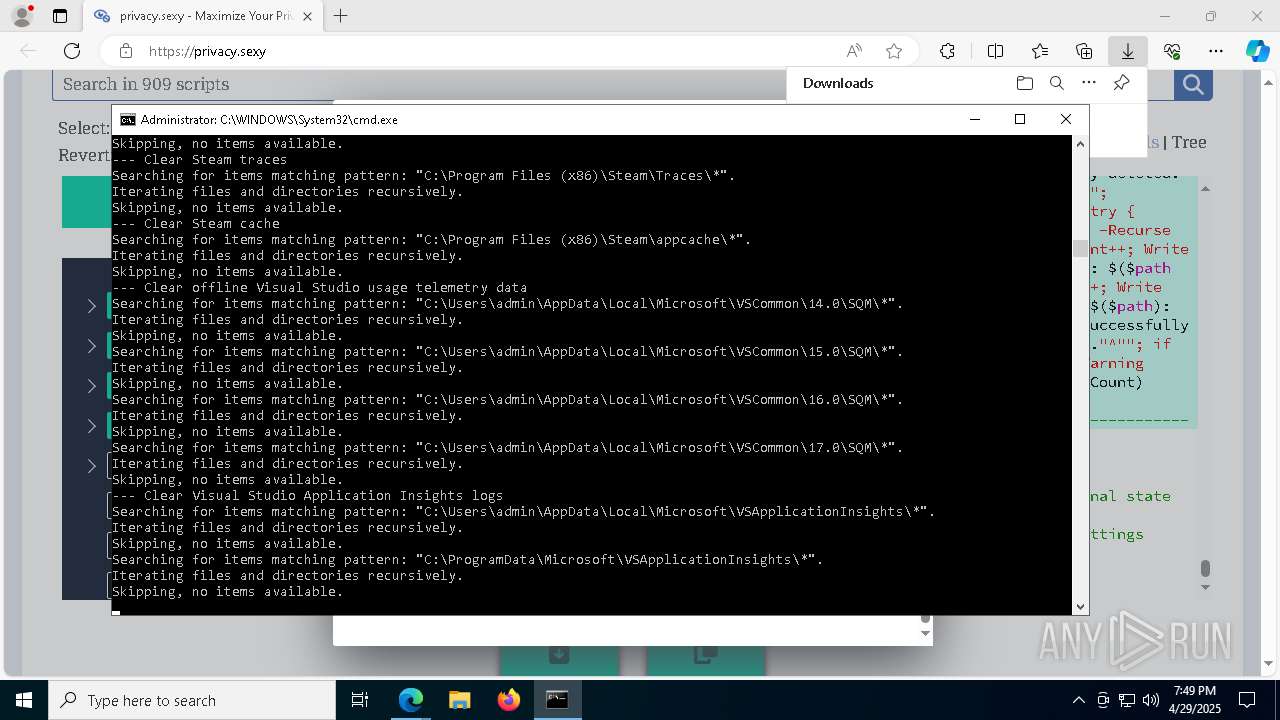
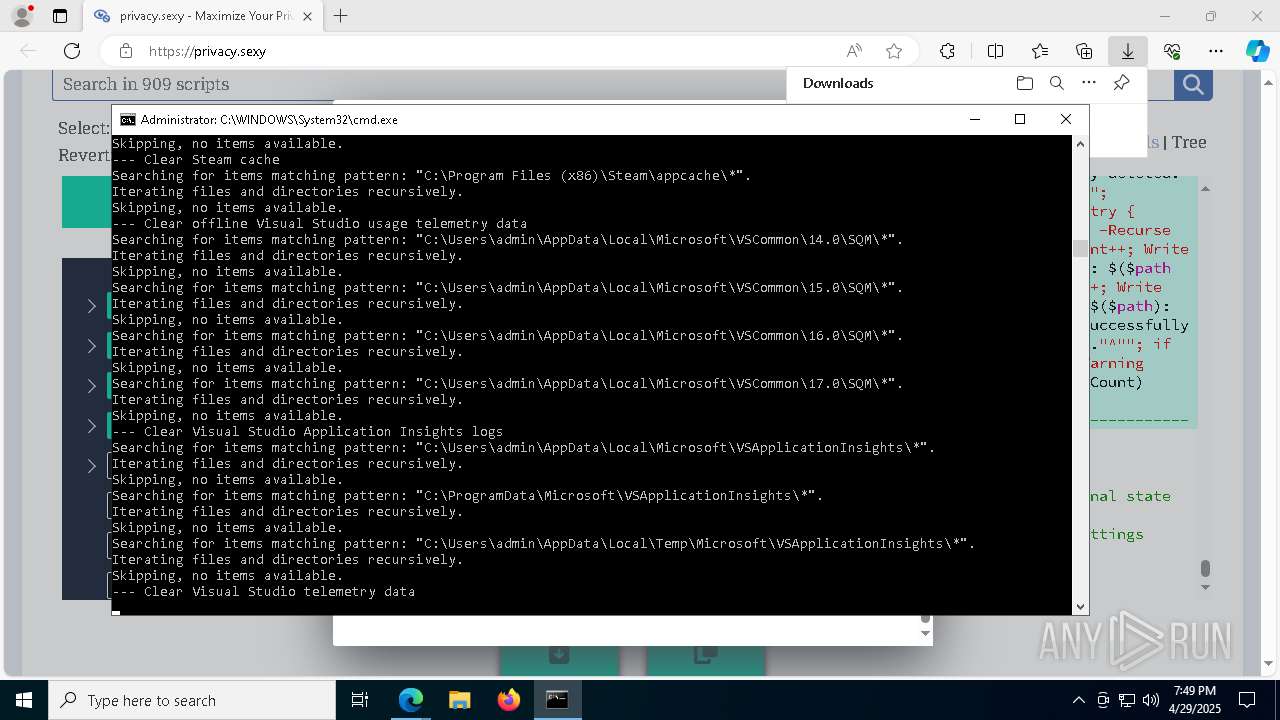
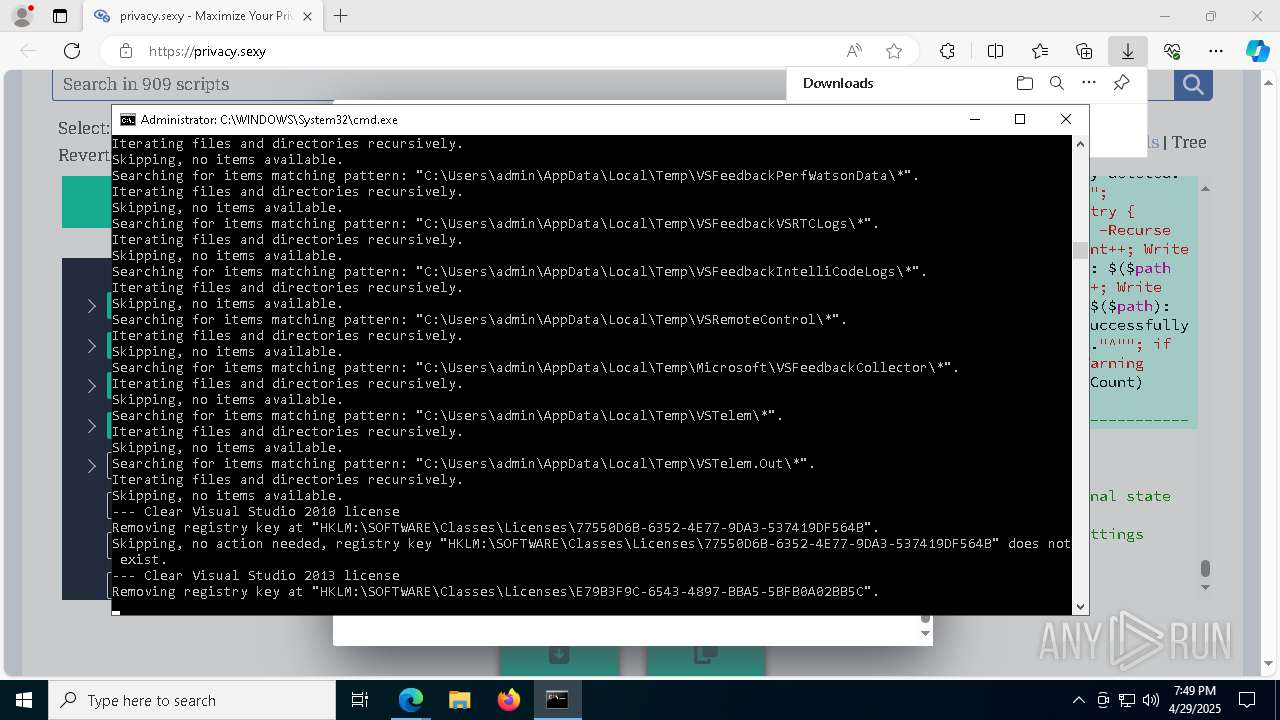
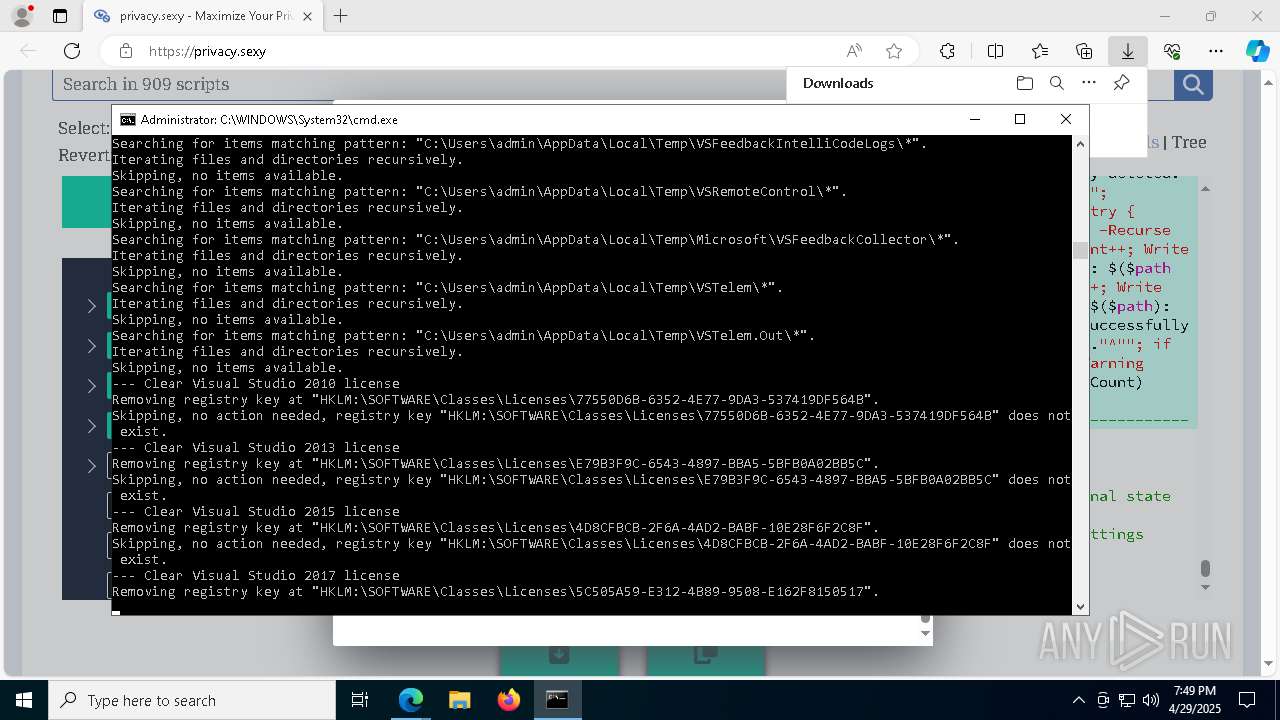
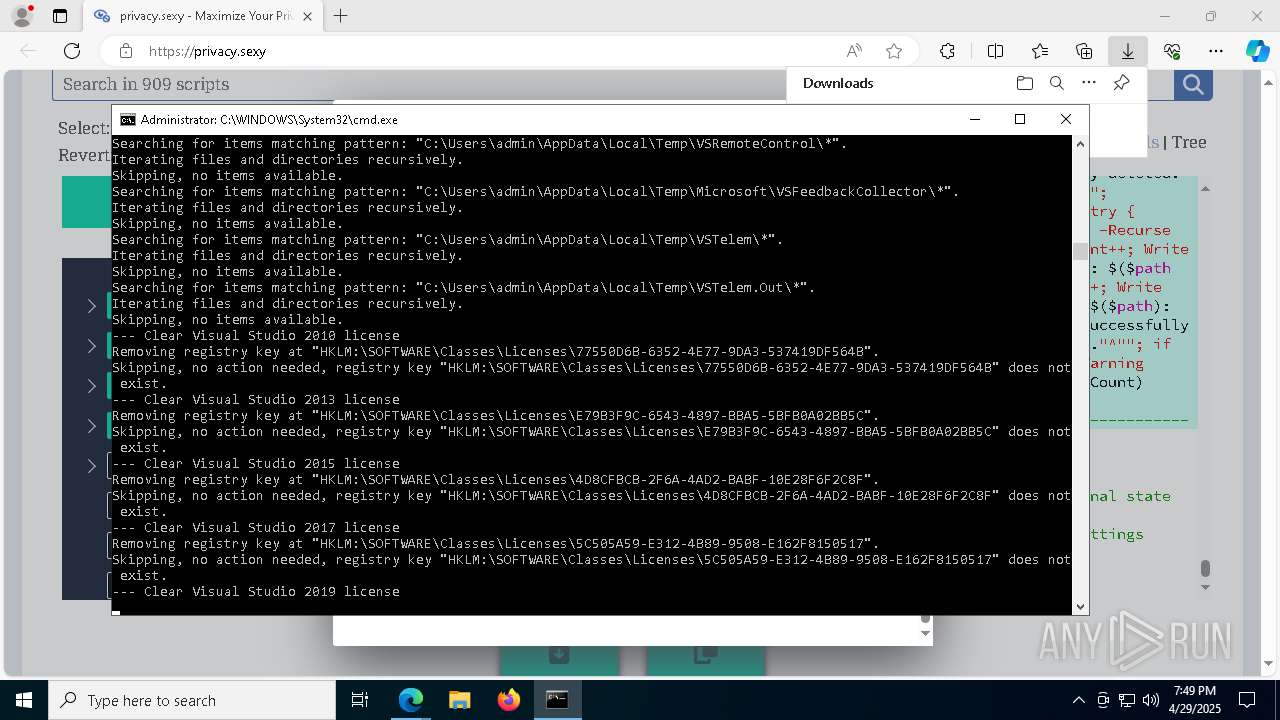
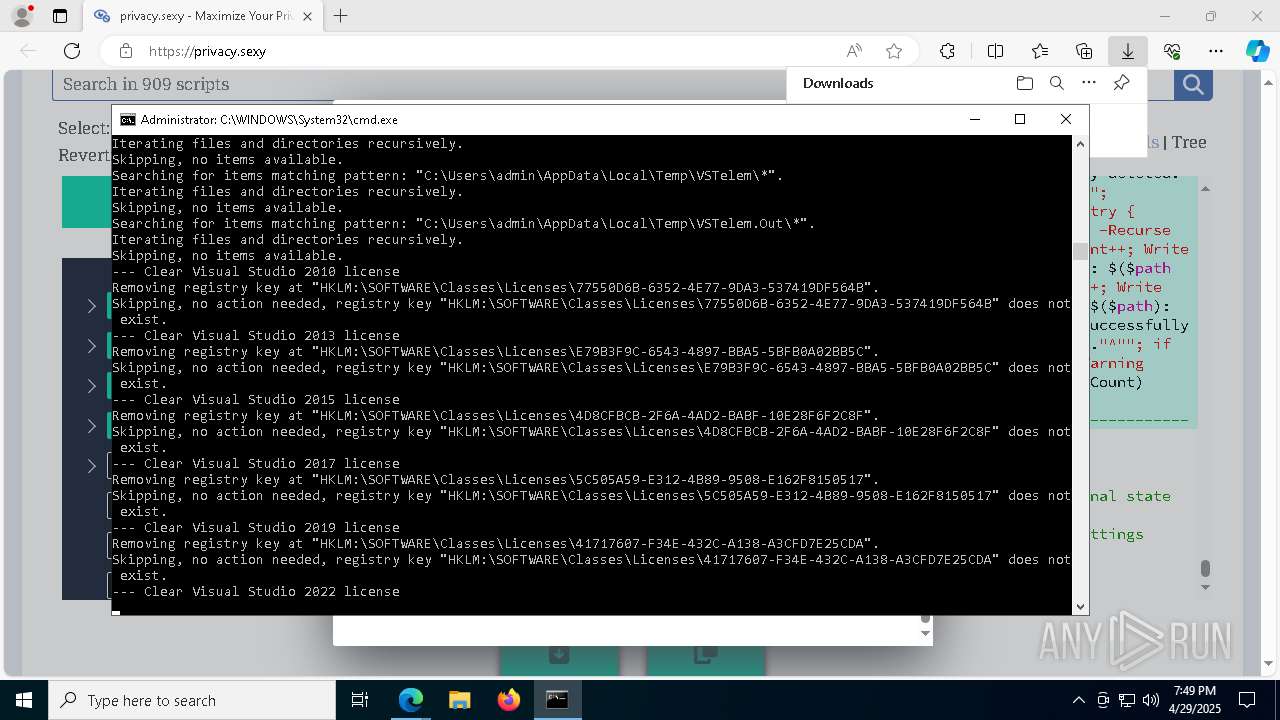
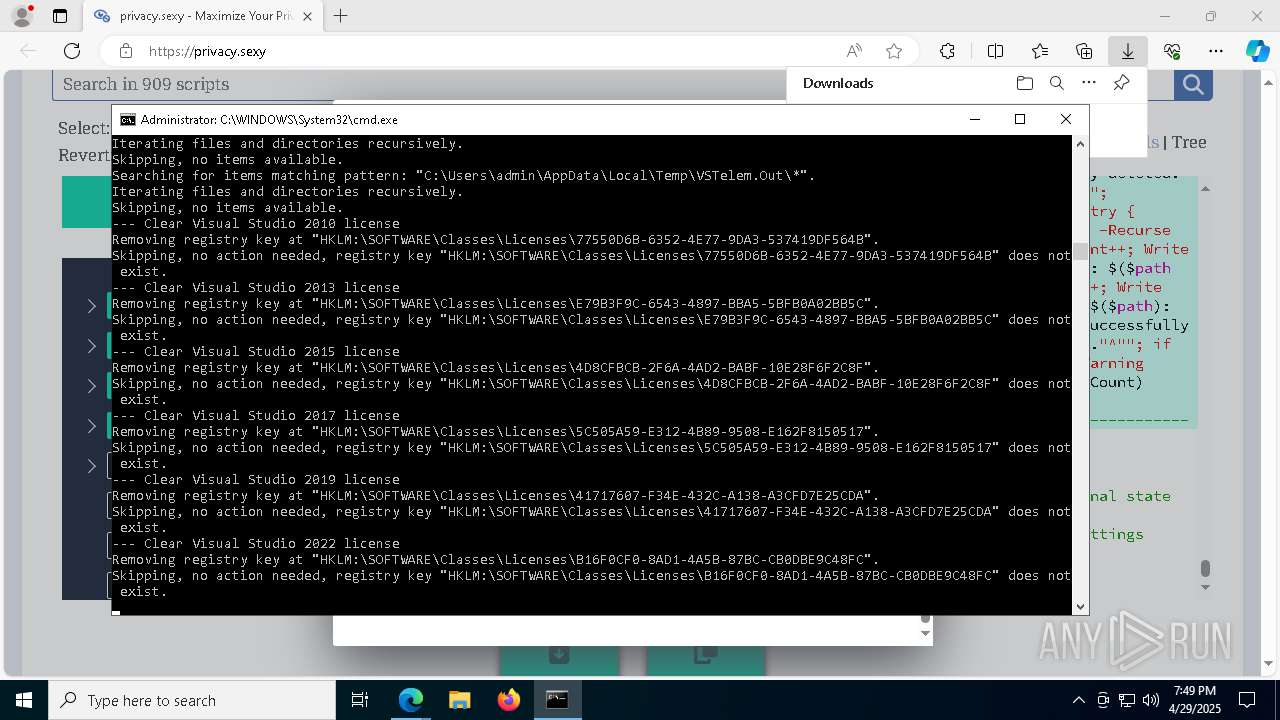
| 132 | PowerShell -ExecutionPolicy Unrestricted -Command "$pathGlobPattern = """$($directoryGlob = 'C:\Program Files (x86)\Steam\Traces'; if ($directoryGlob.EndsWith('\*')) { $directoryGlob } elseif ($directoryGlob.EndsWith('\')) { """$($directoryGlob)*""" } else { """$($directoryGlob)\*""" } )"""; $expandedPath = [System.Environment]::ExpandEnvironmentVariables($pathGlobPattern); Write-Host """Searching for items matching pattern: `"""$($expandedPath)`"""."""; $deletedCount = 0; $failedCount = 0; $foundAbsolutePaths = @(); Write-Host 'Iterating files and directories recursively.'; try { $foundAbsolutePaths += @(; Get-ChildItem -Path $expandedPath -Force -Recurse -ErrorAction Stop | Select-Object -ExpandProperty FullName; ); } catch [System.Management.Automation.ItemNotFoundException] { <# Swallow, do not run `Test-Path` before, it's unreliable for globs requiring extra permissions #>; }; try { $foundAbsolutePaths += @(; Get-Item -Path $expandedPath -ErrorAction Stop | Select-Object -ExpandProperty FullName; ); } catch [System.Management.Automation.ItemNotFoundException] { <# Swallow, do not run `Test-Path` before, it's unreliable for globs requiring extra permissions #>; }; $foundAbsolutePaths = $foundAbsolutePaths | Select-Object -Unique | Sort-Object -Property { $_.Length } -Descending; if (!$foundAbsolutePaths) { Write-Host 'Skipping, no items available.'; exit 0; }; Write-Host """Initiating processing of $($foundAbsolutePaths.Count) items from `"""$expandedPath`"""."""; foreach ($path in $foundAbsolutePaths) { if (-not (Test-Path $path)) { <# Re-check existence as prior deletions might remove subsequent items (e.g., subdirectories). #>; Write-Host """Successfully deleted: $($path) (already deleted)."""; $deletedCount++; continue; }; try { Remove-Item -Path $path -Force -Recurse -ErrorAction Stop; $deletedCount++; Write-Host """Successfully deleted: $($path)"""; } catch { $failedCount++; Write-Warning """Unable to delete $($path): $_"""; }; }; Write-Host """Successfully deleted $($deletedCount) items."""; if ($failedCount -gt 0) { Write-Warning """Failed to delete $($failedCount) items."""; }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | PowerShell -ExecutionPolicy Unrestricted -Command "$keyPath='HKLM\SOFTWARE\Classes\Licenses\41717607-F34E-432C-A138-A3CFD7E25CDA'; $registryHive = $keyPath.Split('\')[0]; $registryPath = """$($registryHive):$($keyPath.Substring($registryHive.Length))"""; Write-Host """Removing registry key at `"""$registryPath`"""."""; if (-not (Test-Path -LiteralPath $registryPath)) { Write-Host """Skipping, no action needed, registry key `"""$registryPath`""" does not exist."""; exit 0; }; try { Remove-Item -LiteralPath $registryPath -Force -ErrorAction Stop | Out-Null; Write-Host """Successfully removed the registry key at path `"""$registryPath`"""."""; } catch { Write-Error """Failed to remove the registry key at path `"""$registryPath`""": $($_.Exception.Message)"""; }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
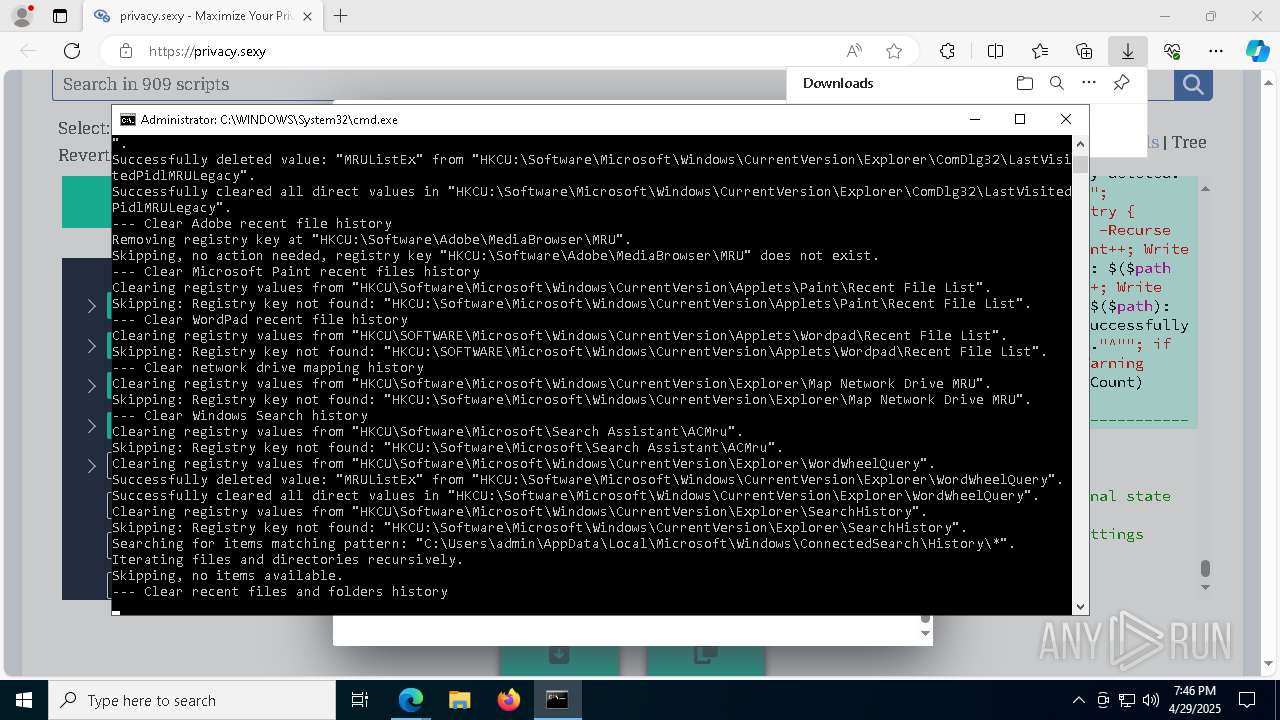
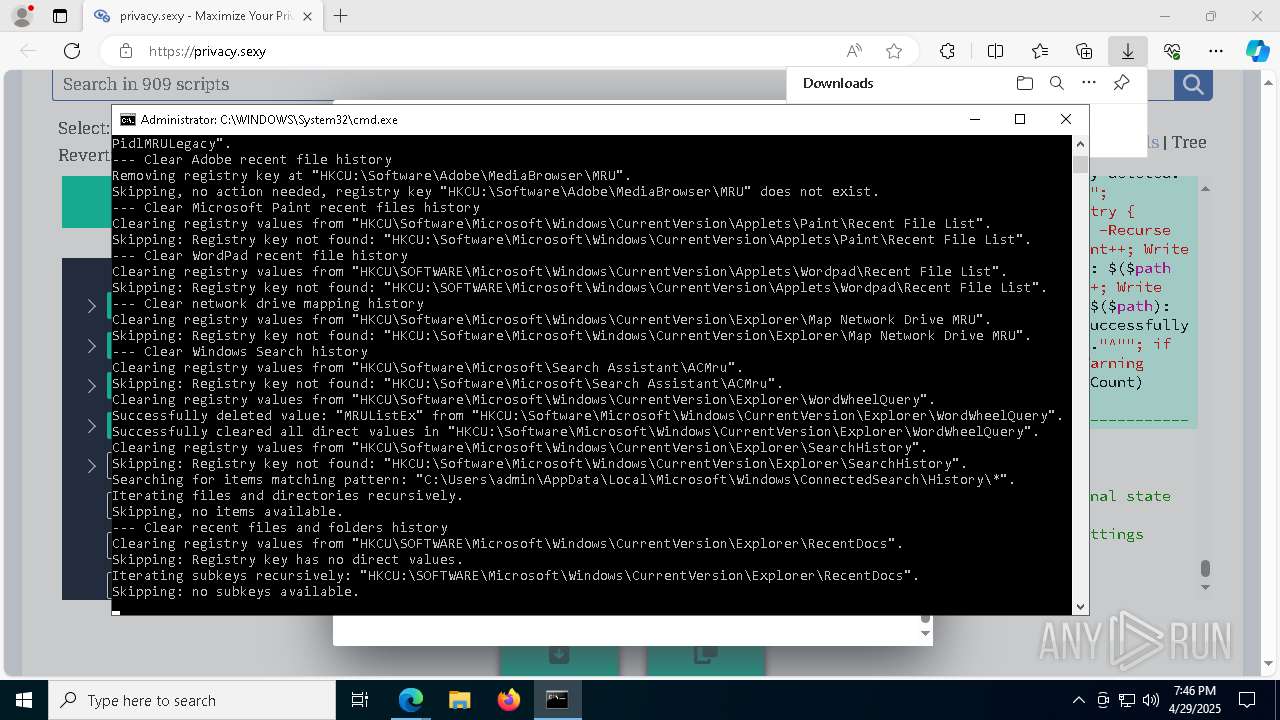
| 472 | PowerShell -ExecutionPolicy Unrestricted -Command "$pathGlobPattern = """C:\Users\admin\AppData\Local\Google\Software Reporter Tool\*.log"""; $expandedPath = [System.Environment]::ExpandEnvironmentVariables($pathGlobPattern); Write-Host """Searching for items matching pattern: `"""$($expandedPath)`"""."""; $deletedCount = 0; $failedCount = 0; $skippedCount = 0; $foundAbsolutePaths = @(); try { $foundAbsolutePaths += @(; Get-Item -Path $expandedPath -ErrorAction Stop | Select-Object -ExpandProperty FullName; ); } catch [System.Management.Automation.ItemNotFoundException] { <# Swallow, do not run `Test-Path` before, it's unreliable for globs requiring extra permissions #>; }; $foundAbsolutePaths = $foundAbsolutePaths | Select-Object -Unique | Sort-Object -Property { $_.Length } -Descending; if (!$foundAbsolutePaths) { Write-Host 'Skipping, no items available.'; exit 0; }; Write-Host """Initiating processing of $($foundAbsolutePaths.Count) items from `"""$expandedPath`"""."""; foreach ($path in $foundAbsolutePaths) { if (Test-Path -Path $path -PathType Container) { Write-Host """Skipping, the path is not a file but a folder: $($path)."""; $skippedCount++; continue; }; if (-not (Test-Path $path)) { <# Re-check existence as prior deletions might remove subsequent items (e.g., subdirectories). #>; Write-Host """Successfully deleted: $($path) (already deleted)."""; $deletedCount++; continue; }; try { Remove-Item -Path $path -Force -Recurse -ErrorAction Stop; $deletedCount++; Write-Host """Successfully deleted: $($path)"""; } catch { $failedCount++; Write-Warning """Unable to delete $($path): $_"""; }; }; if ($skippedCount -gt 0) { Write-Host """Skipped $($skippedCount) items."""; }; Write-Host """Successfully deleted $($deletedCount) items."""; if ($failedCount -gt 0) { Write-Warning """Failed to delete $($failedCount) items."""; }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | icacls "C:\Users\admin\Local Settings\Temporary Internet Files\*" /grant "BUILTIN\Administrators:F" /t | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | PowerShell -ExecutionPolicy Unrestricted -Command "$pathGlobPattern = """$($directoryGlob = 'C:\Users\admin\AppData\Roaming\vstelemetry'; if ($directoryGlob.EndsWith('\*')) { $directoryGlob } elseif ($directoryGlob.EndsWith('\')) { """$($directoryGlob)*""" } else { """$($directoryGlob)\*""" } )"""; $expandedPath = [System.Environment]::ExpandEnvironmentVariables($pathGlobPattern); Write-Host """Searching for items matching pattern: `"""$($expandedPath)`"""."""; $deletedCount = 0; $failedCount = 0; $foundAbsolutePaths = @(); Write-Host 'Iterating files and directories recursively.'; try { $foundAbsolutePaths += @(; Get-ChildItem -Path $expandedPath -Force -Recurse -ErrorAction Stop | Select-Object -ExpandProperty FullName; ); } catch [System.Management.Automation.ItemNotFoundException] { <# Swallow, do not run `Test-Path` before, it's unreliable for globs requiring extra permissions #>; }; try { $foundAbsolutePaths += @(; Get-Item -Path $expandedPath -ErrorAction Stop | Select-Object -ExpandProperty FullName; ); } catch [System.Management.Automation.ItemNotFoundException] { <# Swallow, do not run `Test-Path` before, it's unreliable for globs requiring extra permissions #>; }; $foundAbsolutePaths = $foundAbsolutePaths | Select-Object -Unique | Sort-Object -Property { $_.Length } -Descending; if (!$foundAbsolutePaths) { Write-Host 'Skipping, no items available.'; exit 0; }; Write-Host """Initiating processing of $($foundAbsolutePaths.Count) items from `"""$expandedPath`"""."""; foreach ($path in $foundAbsolutePaths) { if (-not (Test-Path $path)) { <# Re-check existence as prior deletions might remove subsequent items (e.g., subdirectories). #>; Write-Host """Successfully deleted: $($path) (already deleted)."""; $deletedCount++; continue; }; try { Remove-Item -Path $path -Force -Recurse -ErrorAction Stop; $deletedCount++; Write-Host """Successfully deleted: $($path)"""; } catch { $failedCount++; Write-Warning """Unable to delete $($path): $_"""; }; }; Write-Host """Successfully deleted $($deletedCount) items."""; if ($failedCount -gt 0) { Write-Warning """Failed to delete $($failedCount) items."""; }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
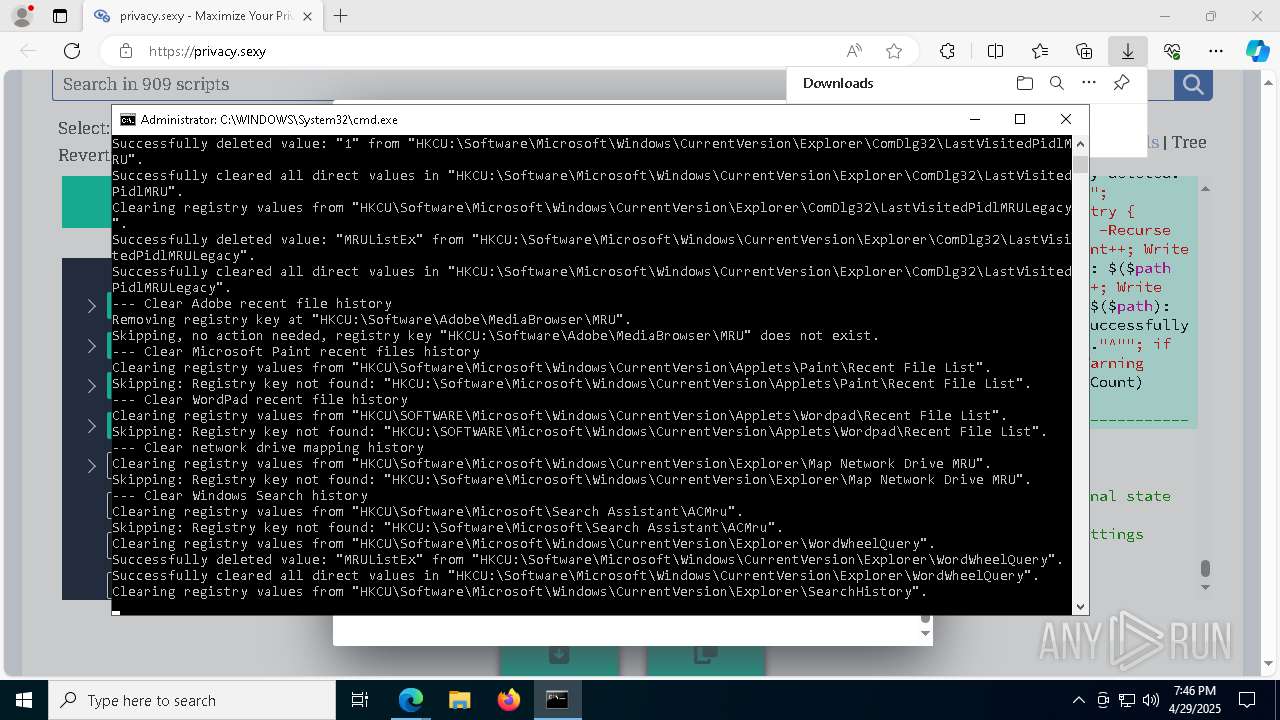
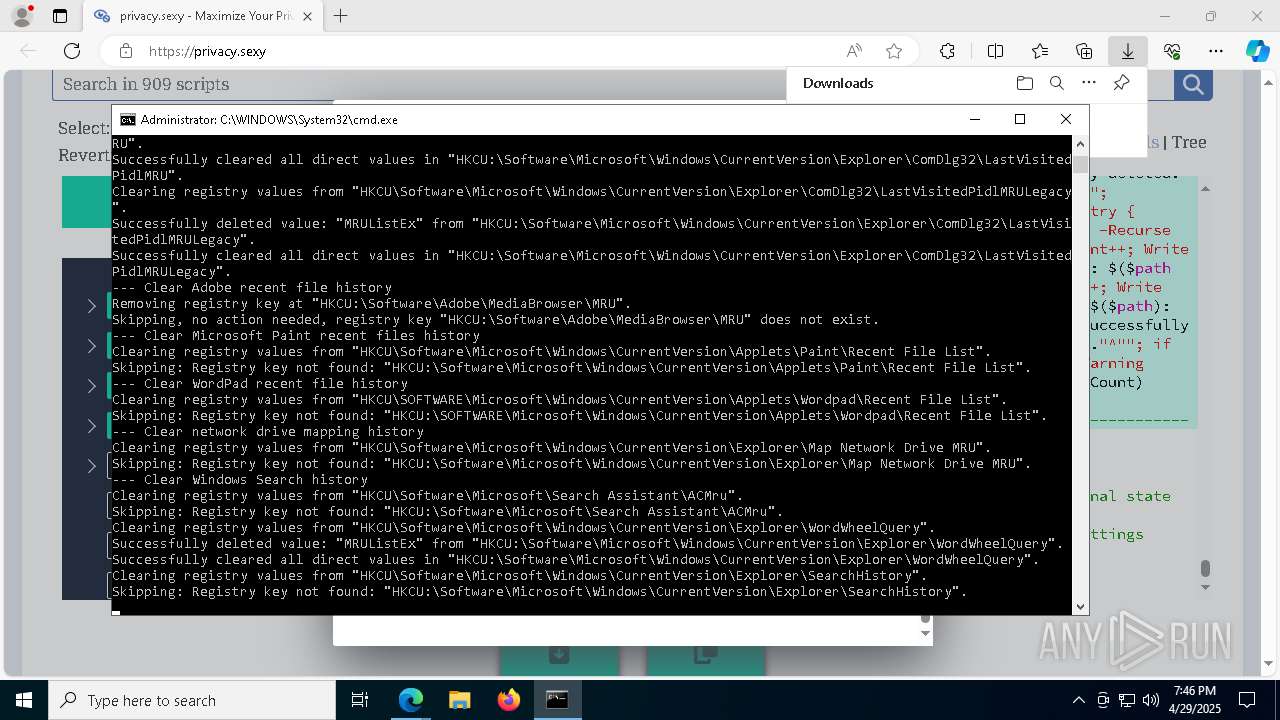
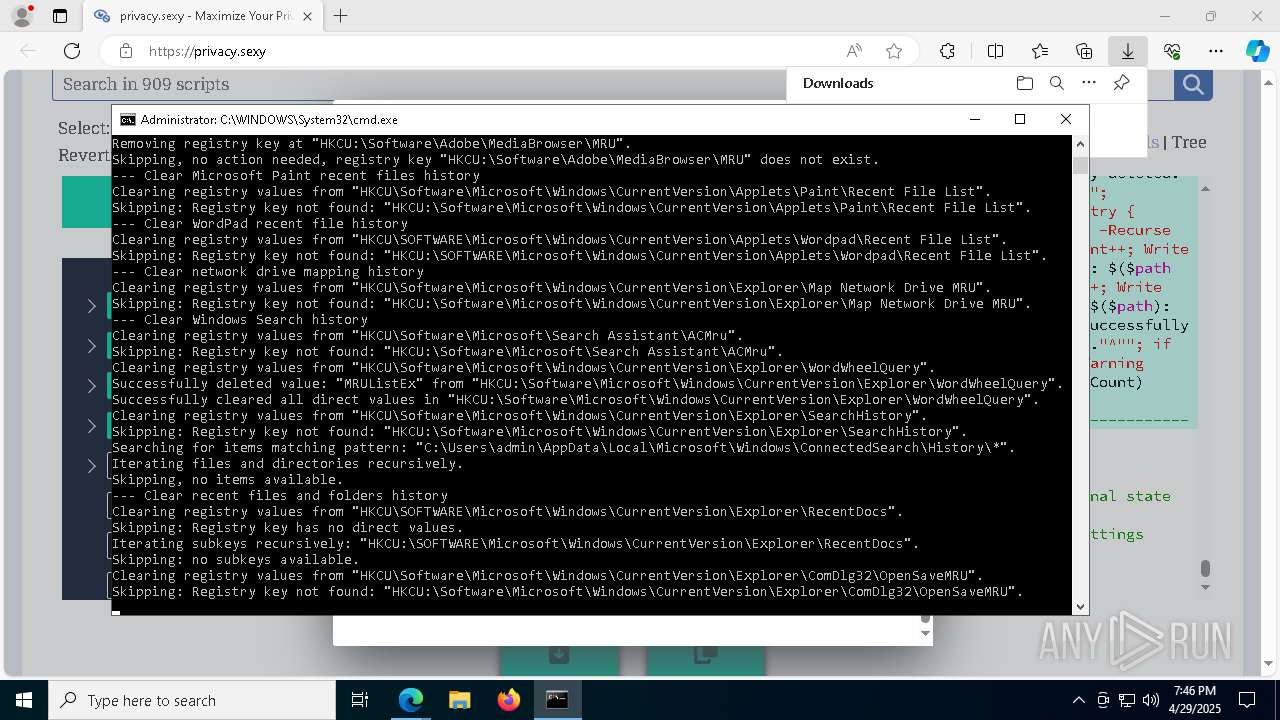
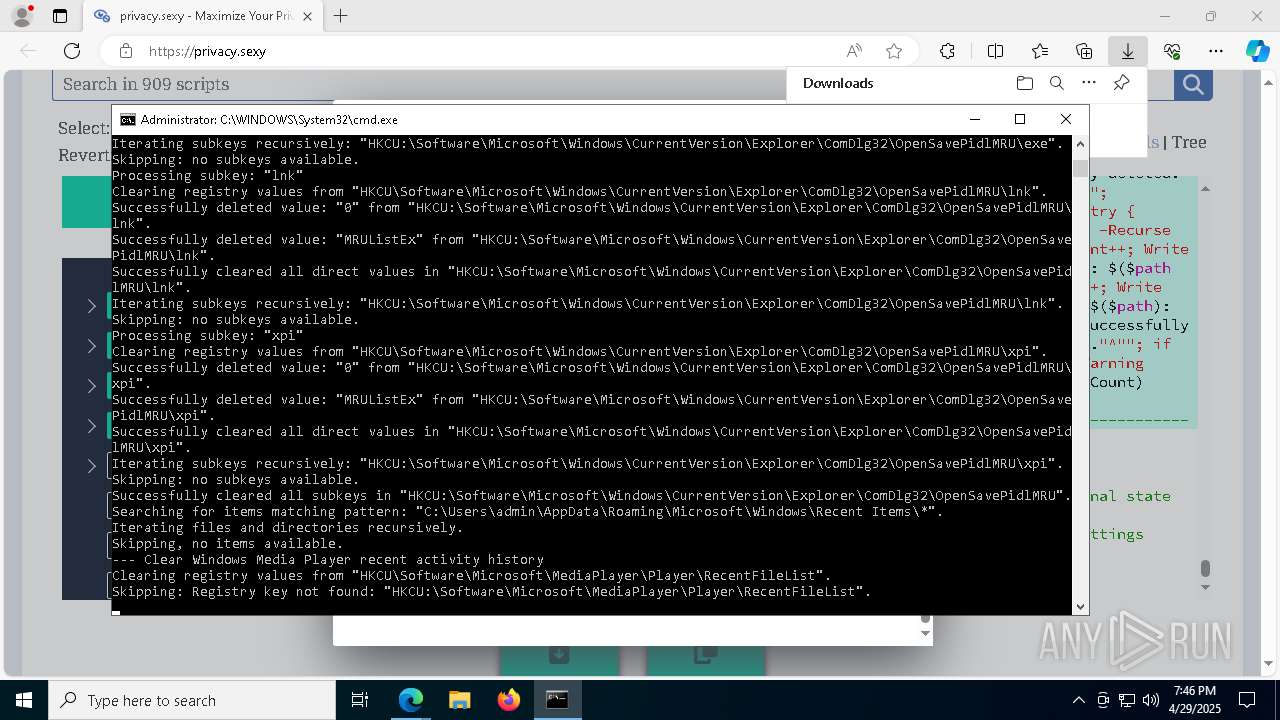
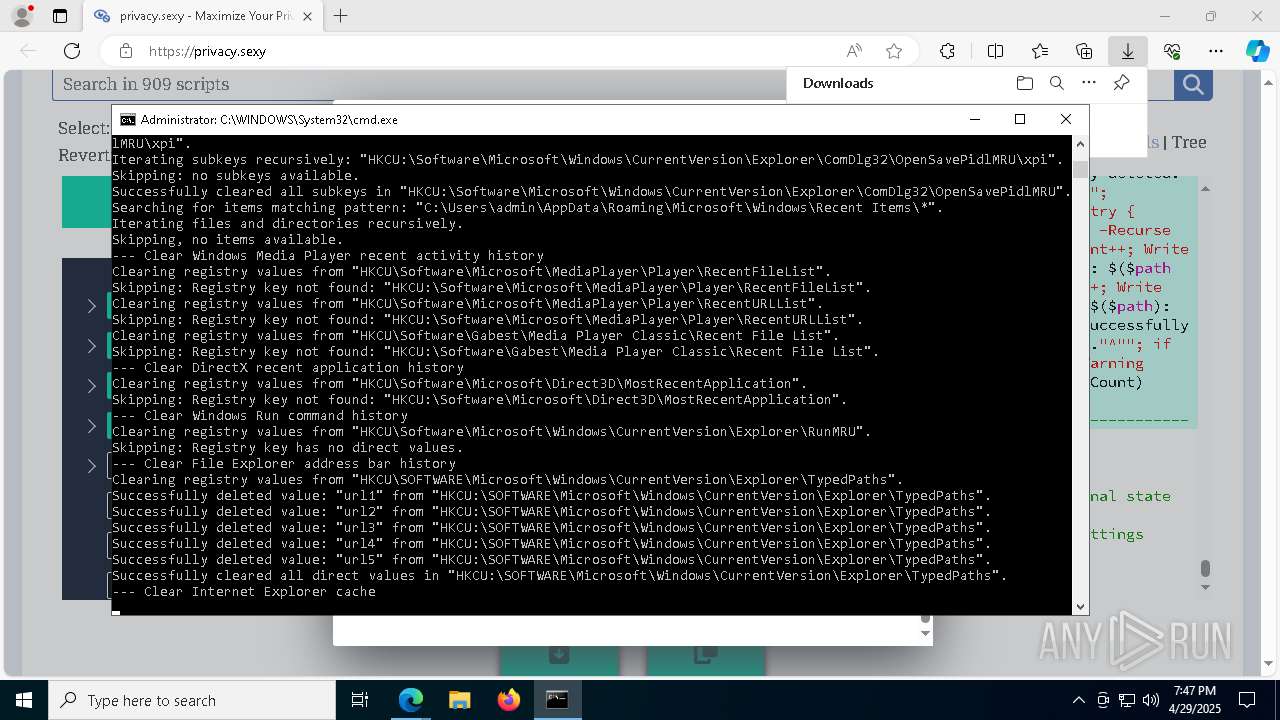
| 668 | PowerShell -ExecutionPolicy Unrestricted -Command "$rootRegistryKeyPath = 'HKCU\Software\Microsoft\MediaPlayer\Player\RecentFileList'; function Clear-RegistryKeyValues { try { $currentRegistryKeyPath = $args[0]; Write-Output """Clearing registry values from `"""$currentRegistryKeyPath`"""."""; $formattedRegistryKeyPath = $currentRegistryKeyPath -replace '^([^\\]+)', '$1:'; if (-Not (Test-Path -LiteralPath $formattedRegistryKeyPath)) { Write-Output """Skipping: Registry key not found: `"""$formattedRegistryKeyPath`"""."""; return; }; $directValueNames=(Get-Item -LiteralPath $formattedRegistryKeyPath -ErrorAction Stop | Select-Object -ExpandProperty Property); if (-Not $directValueNames) { Write-Output 'Skipping: Registry key has no direct values.'; } else { foreach ($valueName in $directValueNames) { Remove-ItemProperty -LiteralPath $formattedRegistryKeyPath -Name $valueName -ErrorAction Stop; Write-Output """Successfully deleted value: `"""$valueName`""" from `"""$formattedRegistryKeyPath`"""."""; }; Write-Output """Successfully cleared all direct values in `"""$formattedRegistryKeyPath`"""."""; }; } catch { Write-Error """Failed to clear registry values in `"""$formattedRegistryKeyPath`""". Error: $_"""; Exit 1; }; }; Clear-RegistryKeyValues $rootRegistryKeyPath" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | takeown /f "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\*" /a /r /d Y | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | PowerShell -ExecutionPolicy Unrestricted -Command "$rootRegistryKeyPath = 'HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Map Network Drive MRU'; function Clear-RegistryKeyValues { try { $currentRegistryKeyPath = $args[0]; Write-Output """Clearing registry values from `"""$currentRegistryKeyPath`"""."""; $formattedRegistryKeyPath = $currentRegistryKeyPath -replace '^([^\\]+)', '$1:'; if (-Not (Test-Path -LiteralPath $formattedRegistryKeyPath)) { Write-Output """Skipping: Registry key not found: `"""$formattedRegistryKeyPath`"""."""; return; }; $directValueNames=(Get-Item -LiteralPath $formattedRegistryKeyPath -ErrorAction Stop | Select-Object -ExpandProperty Property); if (-Not $directValueNames) { Write-Output 'Skipping: Registry key has no direct values.'; } else { foreach ($valueName in $directValueNames) { Remove-ItemProperty -LiteralPath $formattedRegistryKeyPath -Name $valueName -ErrorAction Stop; Write-Output """Successfully deleted value: `"""$valueName`""" from `"""$formattedRegistryKeyPath`"""."""; }; Write-Output """Successfully cleared all direct values in `"""$formattedRegistryKeyPath`"""."""; }; } catch { Write-Error """Failed to clear registry values in `"""$formattedRegistryKeyPath`""". Error: $_"""; Exit 1; }; }; Clear-RegistryKeyValues $rootRegistryKeyPath" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
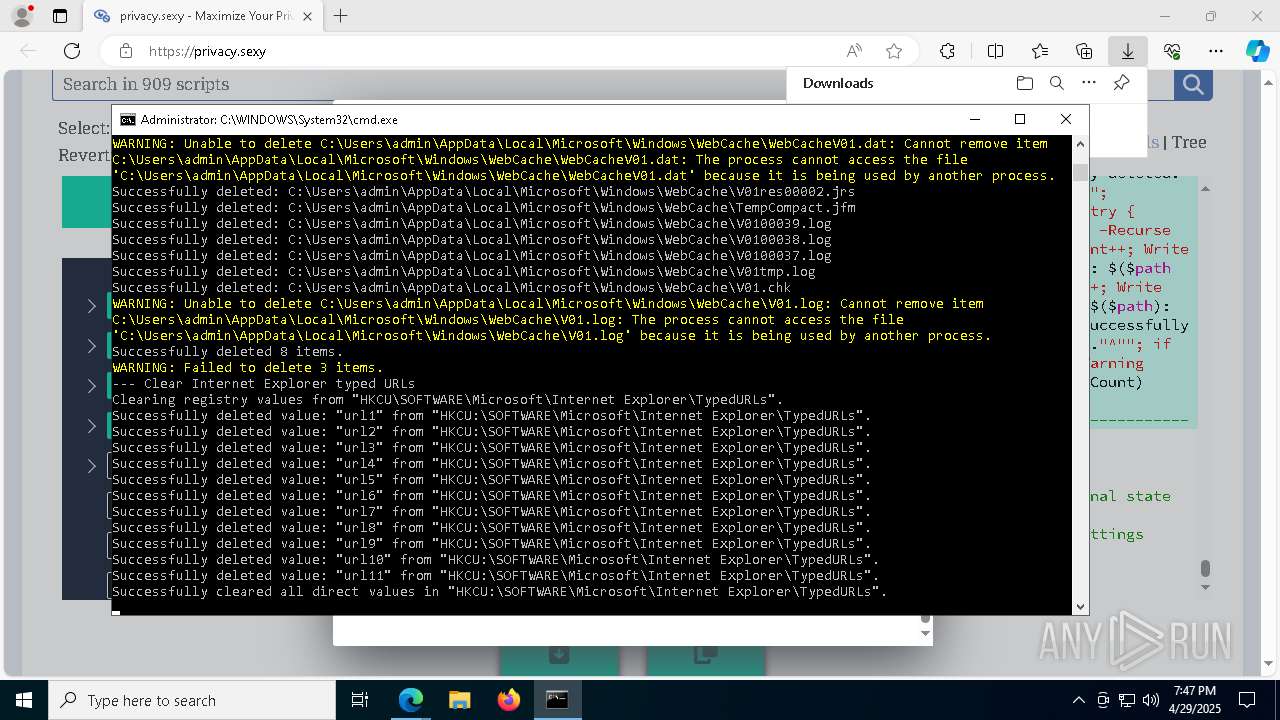
| 1004 | PowerShell -ExecutionPolicy Unrestricted -Command "$rootRegistryKeyPath = 'HKCU\SOFTWARE\Microsoft\Internet Explorer\TypedURLs'; function Clear-RegistryKeyValues { try { $currentRegistryKeyPath = $args[0]; Write-Output """Clearing registry values from `"""$currentRegistryKeyPath`"""."""; $formattedRegistryKeyPath = $currentRegistryKeyPath -replace '^([^\\]+)', '$1:'; if (-Not (Test-Path -LiteralPath $formattedRegistryKeyPath)) { Write-Output """Skipping: Registry key not found: `"""$formattedRegistryKeyPath`"""."""; return; }; $directValueNames=(Get-Item -LiteralPath $formattedRegistryKeyPath -ErrorAction Stop | Select-Object -ExpandProperty Property); if (-Not $directValueNames) { Write-Output 'Skipping: Registry key has no direct values.'; } else { foreach ($valueName in $directValueNames) { Remove-ItemProperty -LiteralPath $formattedRegistryKeyPath -Name $valueName -ErrorAction Stop; Write-Output """Successfully deleted value: `"""$valueName`""" from `"""$formattedRegistryKeyPath`"""."""; }; Write-Output """Successfully cleared all direct values in `"""$formattedRegistryKeyPath`"""."""; }; } catch { Write-Error """Failed to clear registry values in `"""$formattedRegistryKeyPath`""". Error: $_"""; Exit 1; }; }; Clear-RegistryKeyValues $rootRegistryKeyPath" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
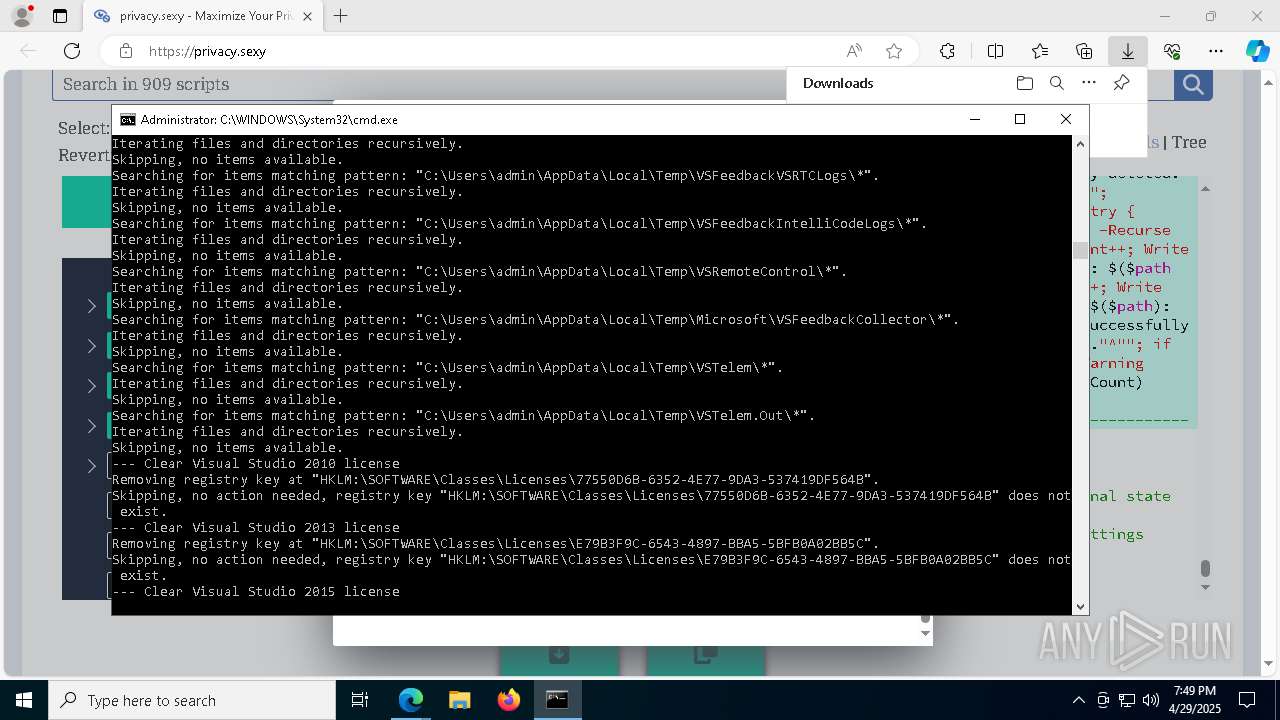
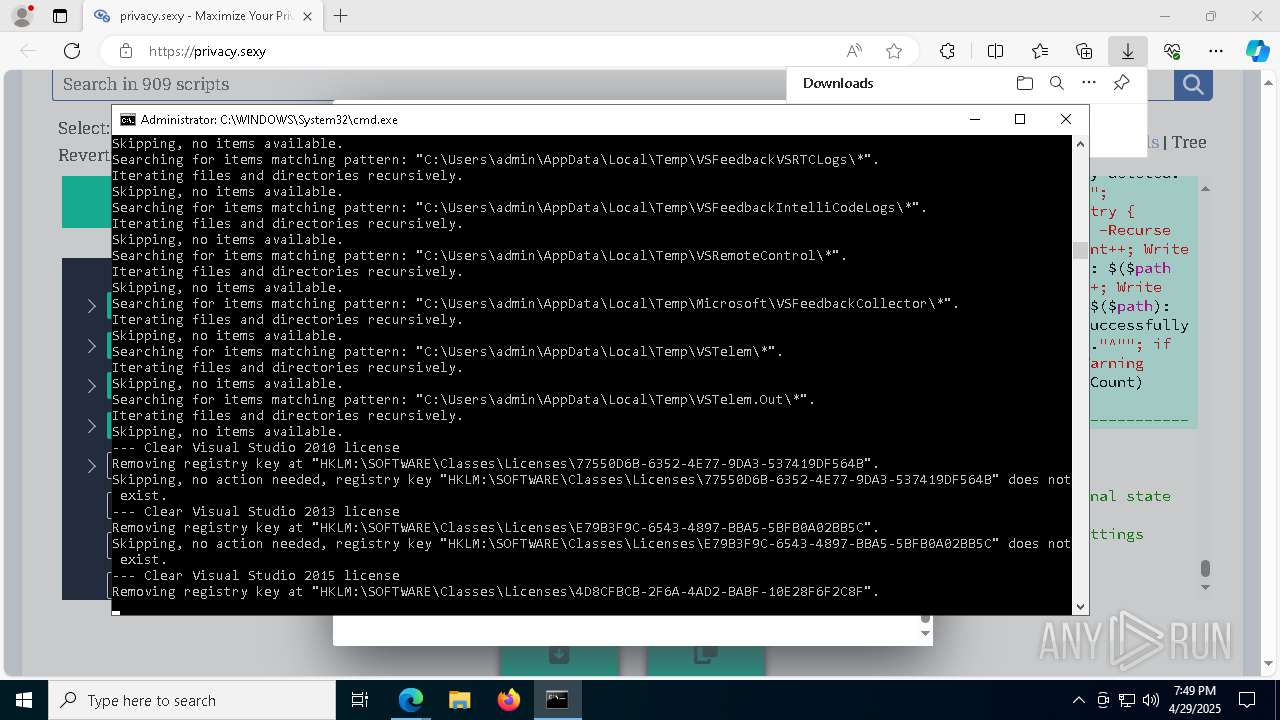
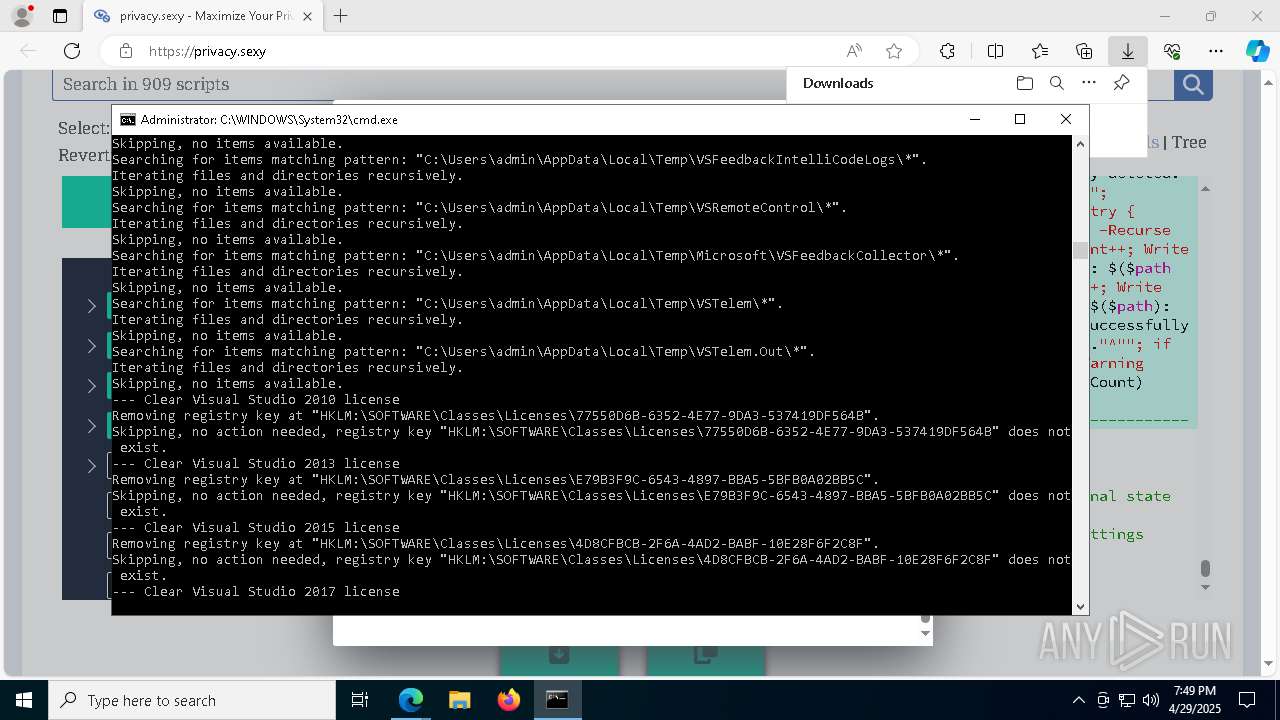
| 1012 | PowerShell -ExecutionPolicy Unrestricted -Command "$keyPath='HKLM\SOFTWARE\Classes\Licenses\77550D6B-6352-4E77-9DA3-537419DF564B'; $registryHive = $keyPath.Split('\')[0]; $registryPath = """$($registryHive):$($keyPath.Substring($registryHive.Length))"""; Write-Host """Removing registry key at `"""$registryPath`"""."""; if (-not (Test-Path -LiteralPath $registryPath)) { Write-Host """Skipping, no action needed, registry key `"""$registryPath`""" does not exist."""; exit 0; }; try { Remove-Item -LiteralPath $registryPath -Force -ErrorAction Stop | Out-Null; Write-Host """Successfully removed the registry key at path `"""$registryPath`"""."""; } catch { Write-Error """Failed to remove the registry key at path `"""$registryPath`""": $($_.Exception.Message)"""; }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
489 143
Read events
489 087
Write events
19
Delete events
37
Modification events
| (PID) Process: | (7476) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7476) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7476) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7476) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7476) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 166DA25186922F00 | |||
| (PID) Process: | (7476) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 78C5AA5186922F00 | |||
| (PID) Process: | (7476) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328396 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {4C06E0F1-E27F-423D-A082-0FFE3A80CDA9} | |||
| (PID) Process: | (7476) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328396 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {7BBAF30B-2A4D-42E4-B006-0C7D325326A9} | |||
| (PID) Process: | (7476) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328396 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C01337C7-C835-4B01-B5EA-53A2168C4417} | |||
| (PID) Process: | (7476) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
Executable files
16
Suspicious files
557
Text files
317
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7476 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10bdf3.TMP | — | |
MD5:— | SHA256:— | |||
| 7476 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10bdf3.TMP | — | |
MD5:— | SHA256:— | |||
| 7476 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7476 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7476 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10bdf3.TMP | — | |
MD5:— | SHA256:— | |||
| 7476 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7476 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10be02.TMP | — | |
MD5:— | SHA256:— | |||
| 7476 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7476 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10be02.TMP | — | |
MD5:— | SHA256:— | |||
| 7476 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
51
TCP/UDP connections
58
DNS requests
67
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4448 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4448 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7312 | svchost.exe | HEAD | 200 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cf34b06a-2f53-4bd0-9d11-b58cf2e820a4?P1=1746407448&P2=404&P3=2&P4=CkOznexsPGEnqSHhxbs3uaA1eZJTzyU4DLyCMTOB3VF23UJ6w%2b%2fiqoLUM2zUdiXg%2bJuXVMWZdPNmWPekIOYFWw%3d%3d | unknown | — | — | whitelisted |
7312 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cf34b06a-2f53-4bd0-9d11-b58cf2e820a4?P1=1746407448&P2=404&P3=2&P4=CkOznexsPGEnqSHhxbs3uaA1eZJTzyU4DLyCMTOB3VF23UJ6w%2b%2fiqoLUM2zUdiXg%2bJuXVMWZdPNmWPekIOYFWw%3d%3d | unknown | — | — | whitelisted |
7312 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cf34b06a-2f53-4bd0-9d11-b58cf2e820a4?P1=1746407448&P2=404&P3=2&P4=CkOznexsPGEnqSHhxbs3uaA1eZJTzyU4DLyCMTOB3VF23UJ6w%2b%2fiqoLUM2zUdiXg%2bJuXVMWZdPNmWPekIOYFWw%3d%3d | unknown | — | — | whitelisted |
7312 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cf34b06a-2f53-4bd0-9d11-b58cf2e820a4?P1=1746407448&P2=404&P3=2&P4=CkOznexsPGEnqSHhxbs3uaA1eZJTzyU4DLyCMTOB3VF23UJ6w%2b%2fiqoLUM2zUdiXg%2bJuXVMWZdPNmWPekIOYFWw%3d%3d | unknown | — | — | whitelisted |
7312 | svchost.exe | GET | 206 | 208.89.74.29:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cf34b06a-2f53-4bd0-9d11-b58cf2e820a4?P1=1746407448&P2=404&P3=2&P4=CkOznexsPGEnqSHhxbs3uaA1eZJTzyU4DLyCMTOB3VF23UJ6w%2b%2fiqoLUM2zUdiXg%2bJuXVMWZdPNmWPekIOYFWw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7764 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7476 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7764 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
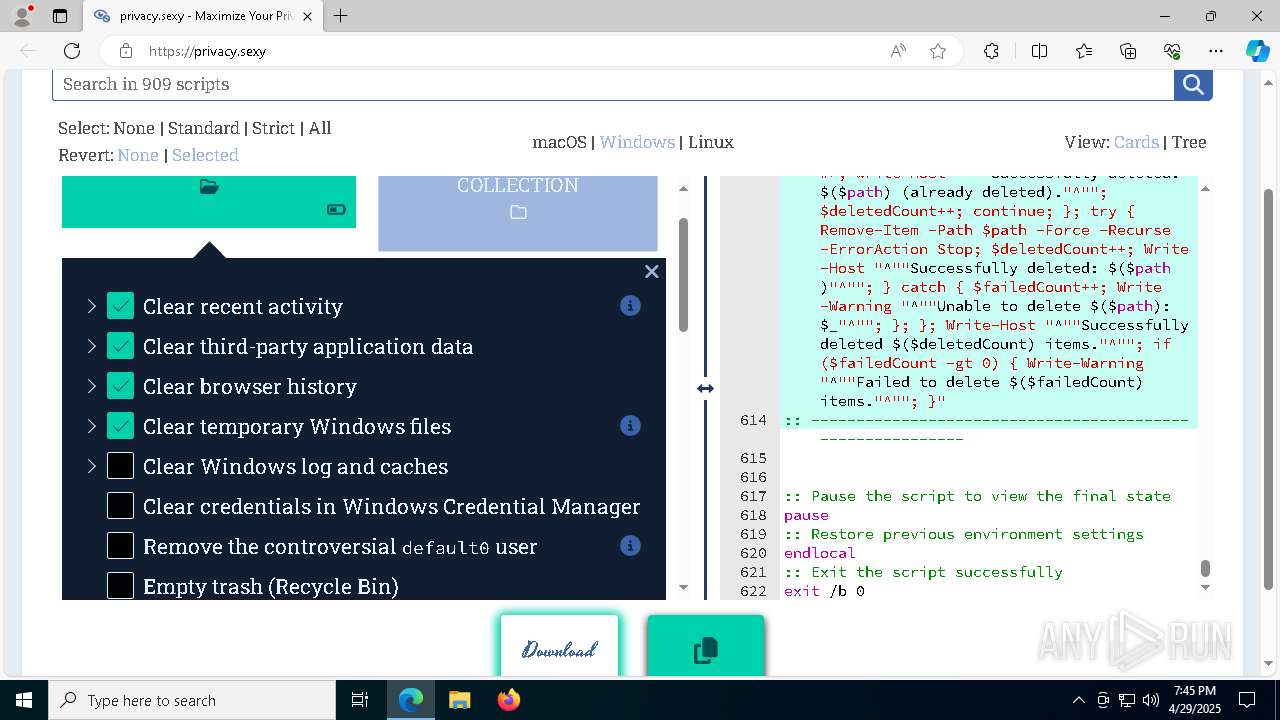
7764 | msedge.exe | 18.66.102.91:443 | privacy.sexy | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
privacy.sexy |
| malicious |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
www.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |