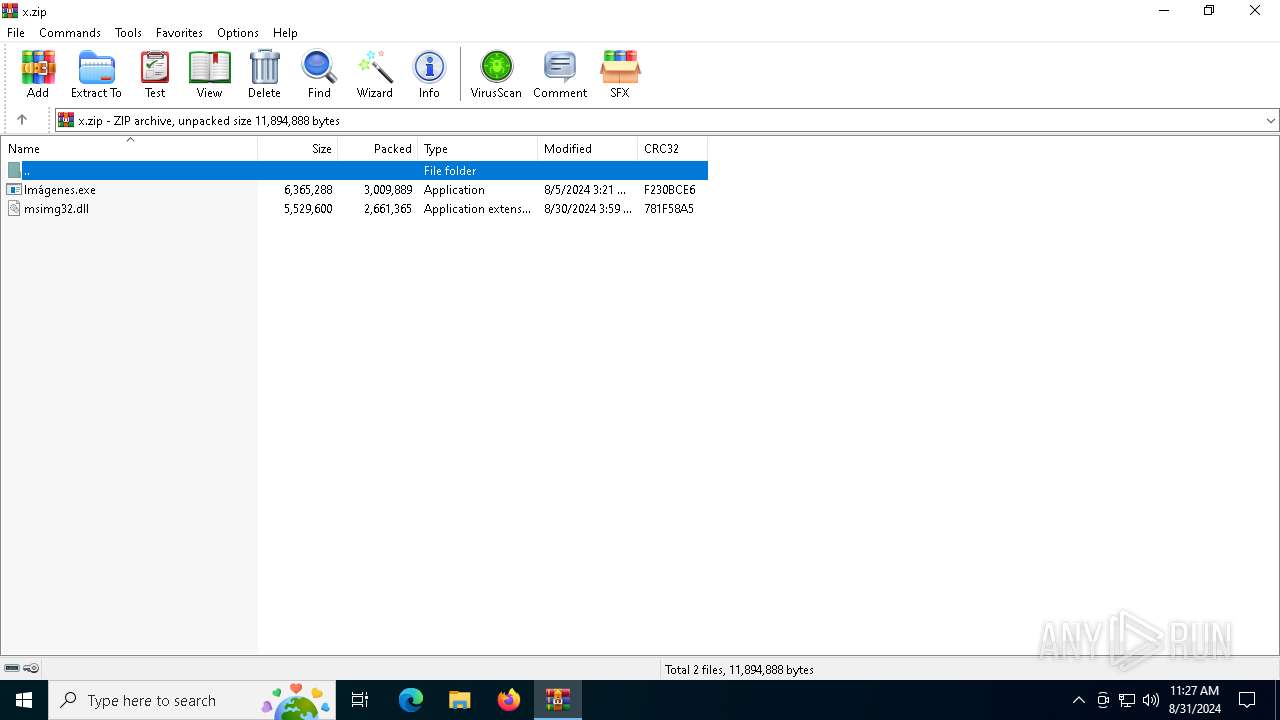
| File name: | x.zip |
| Full analysis: | https://app.any.run/tasks/4afccaba-3bf4-4323-958a-25230f2dc599 |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | August 31, 2024, 11:27:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 3B17A4181797E46530E068103FDAEF3B |
| SHA1: | 87652B1F8A70270CEBEB8A4BF757906DF2FD2700 |
| SHA256: | D49A5648DF0AA95EC47EE1C090C9E4A0D7ECF9D7E2A9EF11C5E62CA33EE40BEB |
| SSDEEP: | 98304:BDlcZrDEh0c1Ynbv5/zWJBIASKN0+wkgv+yCTmWugkU1faMttPzD5DWec1Lll5Xt:iY5SPL3 |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 6604)
RHADAMANTHYS has been detected (SURICATA)
- OpenWith.exe (PID: 3660)
- OOBE-Maintenance.exe (PID: 3272)
Actions looks like stealing of personal data
- OOBE-Maintenance.exe (PID: 3272)
Stealers network behavior
- OOBE-Maintenance.exe (PID: 3272)
SUSPICIOUS
Executes application which crashes
- Imágenes.exe (PID: 6168)
Application launched itself
- Imágenes.exe (PID: 5128)
Connects to unusual port
- OpenWith.exe (PID: 3660)
- OOBE-Maintenance.exe (PID: 3272)
The process checks if it is being run in the virtual environment
- OpenWith.exe (PID: 3660)
Starts CMD.EXE for commands execution
- Imágenes.exe (PID: 5128)
Searches for installed software
- OOBE-Maintenance.exe (PID: 3272)
Contacting a server suspected of hosting an CnC
- OpenWith.exe (PID: 3660)
- OOBE-Maintenance.exe (PID: 3272)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4080)
Loads DLL from Mozilla Firefox
- OOBE-Maintenance.exe (PID: 3272)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2456)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2456)
Manual execution by a user
- OpenWith.exe (PID: 3660)
- OOBE-Maintenance.exe (PID: 3272)
- Imágenes.exe (PID: 5128)
Checks supported languages
- wmpshare.exe (PID: 2768)
- Imágenes.exe (PID: 5128)
- Imágenes.exe (PID: 6168)
Reads the machine GUID from the registry
- wmpshare.exe (PID: 2768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:05 05:21:10 |
| ZipCRC: | 0xf230bce6 |
| ZipCompressedSize: | 3009889 |
| ZipUncompressedSize: | 6365288 |
| ZipFileName: | Im?genes.exe |
Total processes
140
Monitored processes
14
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 488 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 788 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6168 -s 556 | C:\Windows\SysWOW64\WerFault.exe | — | Imágenes.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
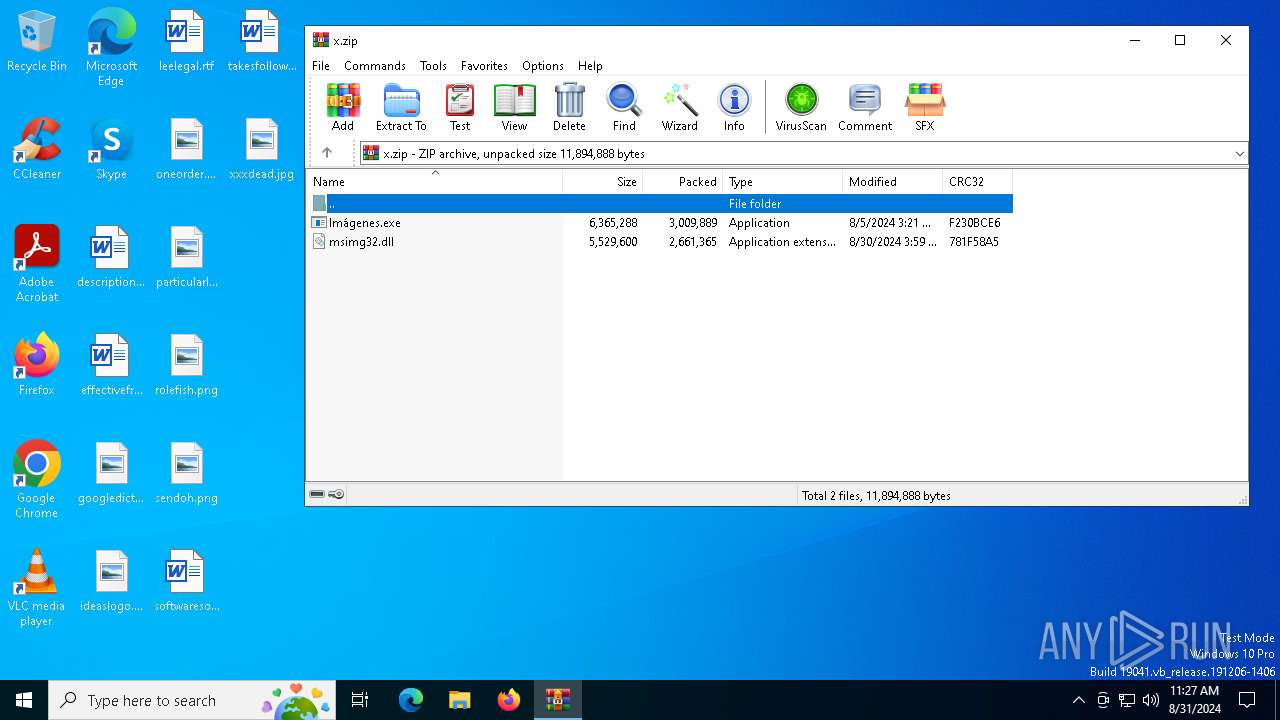
| 2456 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\x.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2768 | "C:\Program Files\Windows Media Player\wmpshare.exe" | C:\Program Files\Windows Media Player\wmpshare.exe | — | OOBE-Maintenance.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Folder Sharing Executable Version: 12.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3272 | "C:\WINDOWS\system32\OOBE-Maintenance.exe" | C:\Windows\System32\OOBE-Maintenance.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: OOBE-Maintenance Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3660 | "C:\WINDOWS\system32\openwith.exe" | C:\Windows\SysWOW64\OpenWith.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3708 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6168 -s 536 | C:\Windows\SysWOW64\WerFault.exe | — | Imágenes.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4080 | cmd.exe /C reg add "HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "*UpdaterCisco" /t REG_SZ /d "rundll32.exe C:\Users\admin\Documents\CiscoUpdater000_PARTIAL.dll",EntryPoint /f & exit | C:\Windows\SysWOW64\cmd.exe | — | Imágenes.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5128 | "C:\Users\admin\Desktop\Imágenes.exe" | C:\Users\admin\Desktop\Imágenes.exe | — | explorer.exe | |||||||||||
User: admin Company: Haihaisoft Limited Integrity Level: MEDIUM Description: Haihaisoft PDF Reader Exit code: 0 Version: 1.5.7.0 Modules
| |||||||||||||||
Total events
7 334
Read events
7 313
Write events
21
Delete events
0
Modification events
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\x.zip | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF2901000019000000E904000002020000 | |||
| (PID) Process: | (2456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5128 | Imágenes.exe | C:\Users\admin\Documents\CiscoUpdater000_PARTIAL.dll | — | |
MD5:— | SHA256:— | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2456.46455\Imágenes.exe | executable | |
MD5:4864A55CFF27F686023456A22371E790 | SHA256:08C7FB6067ACC8AC207D28AB616C9EA5BC0D394956455D6A3EECB73F8010F7A2 | |||
| 2456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2456.46455\msimg32.dll | executable | |
MD5:F13E41D83906E954BB4133AEA4A88806 | SHA256:DFBE1C30C331FFFE8C6FA40765CBD92245F7AD465E4B6038D05308829DF0DB9D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
31
DNS requests
14
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6120 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3292 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3292 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6224 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6288 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6224 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6120 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6120 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3292 | SIHClient.exe | 40.127.169.103:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3272 | OOBE-Maintenance.exe | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
3272 | OOBE-Maintenance.exe | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
6 ETPRO signatures available at the full report