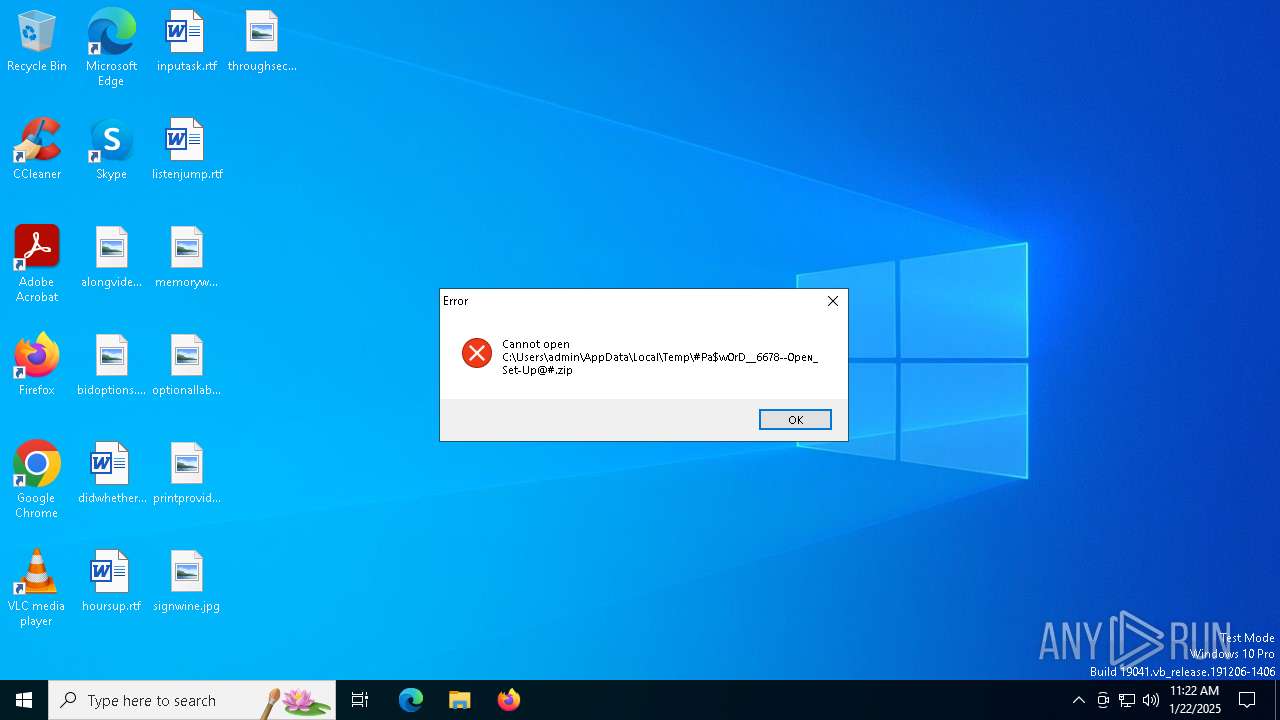
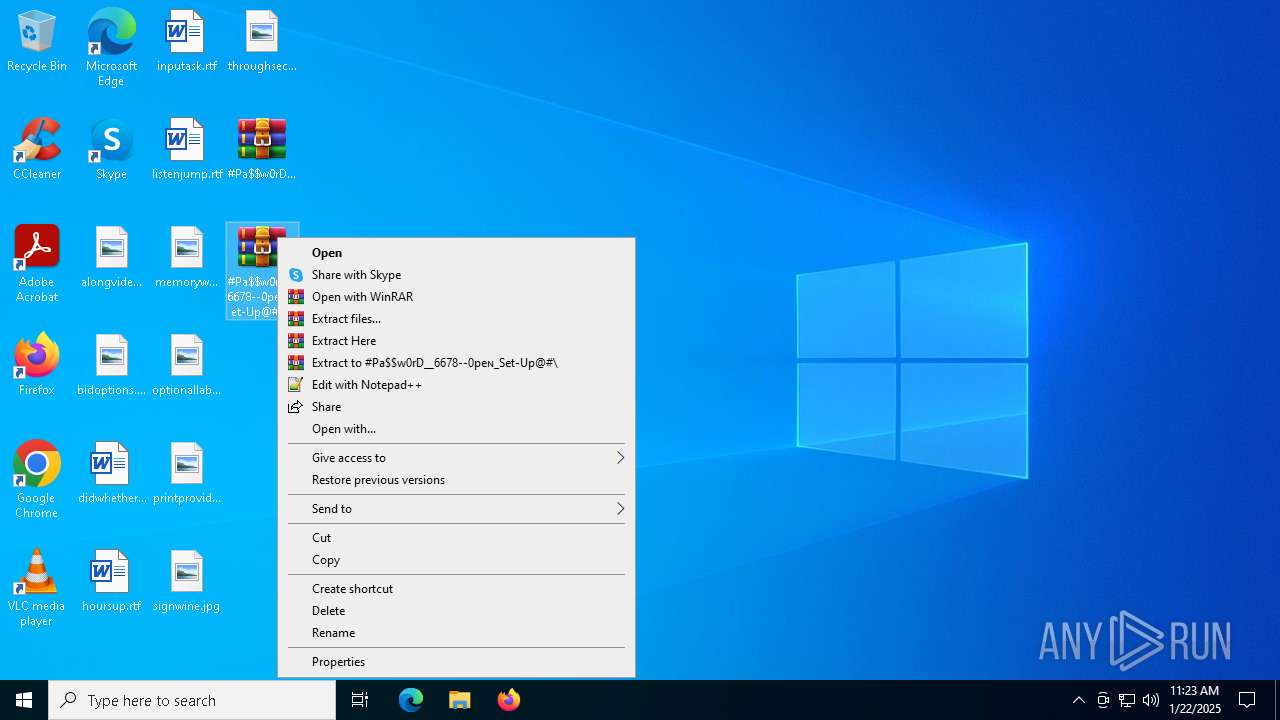
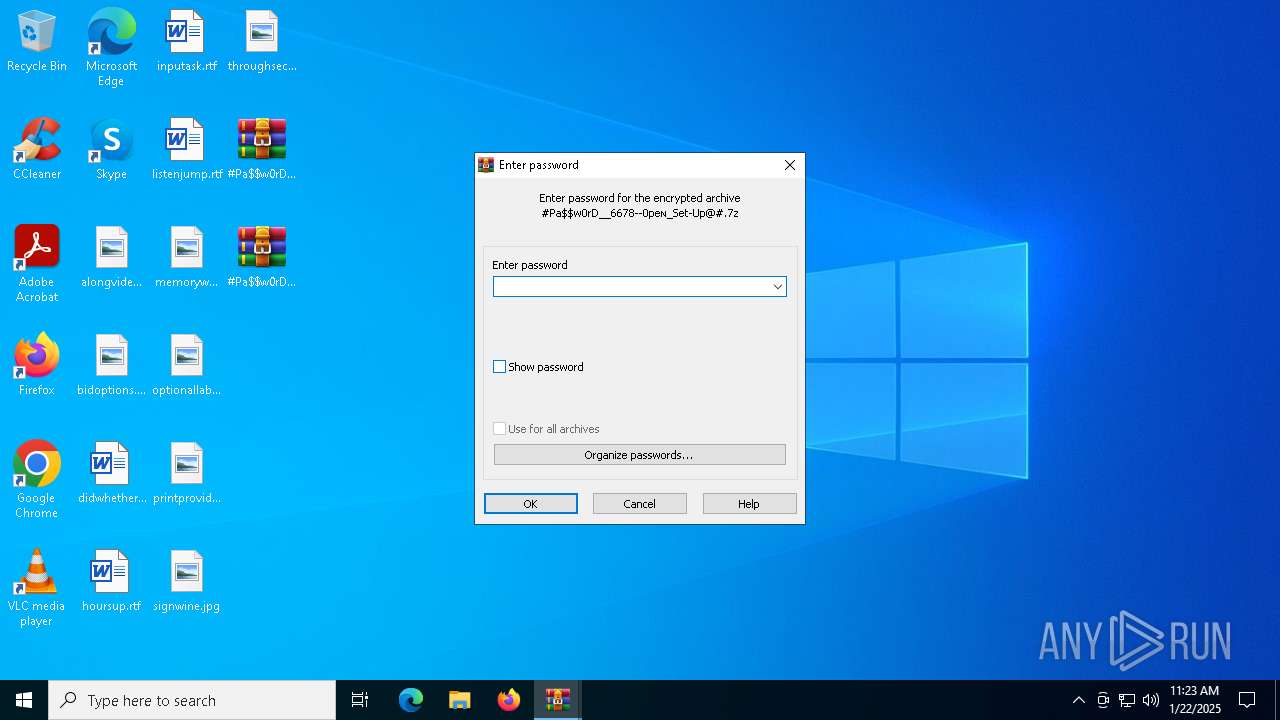
| File name: | #Pa$w0rD__6678--0peɴ_Set-Up@#.zip |
| Full analysis: | https://app.any.run/tasks/f71c54a2-1428-4e27-ae96-e7c4fd3b1cd1 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 22, 2025, 11:22:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 74C158F1C600626EA4FE571F48C1C0FA |
| SHA1: | F2159D9115B0D732C816CC7324F9F2453560FAF1 |
| SHA256: | D4350AC5372EC3F0297D624C868A9F4D8E2C197CAF020A6F8850487B4CDAF091 |
| SSDEEP: | 98304:nE8CKc/Q6ApPUrh6mHy0LxU75TSO4quC+dk7yonfJ7ZhnsEvSu3A7JpWFdqHeEzd:j09pxZU2qpc95sQk8IuTjiG |
MALICIOUS
Executing a file with an untrusted certificate
- Setup.exe (PID: 3732)
- Setup.exe (PID: 6360)
LUMMA has been detected (SURICATA)
- Setup.exe (PID: 3732)
- Setup.exe (PID: 6360)
Steals credentials from Web Browsers
- Setup.exe (PID: 3732)
- Setup.exe (PID: 6360)
Actions looks like stealing of personal data
- Setup.exe (PID: 3732)
- Setup.exe (PID: 6360)
LUMMA has been detected (YARA)
- Setup.exe (PID: 6360)
LUMMA mutex has been found
- Setup.exe (PID: 6360)
- Setup.exe (PID: 3732)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 5236)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 5236)
Searches for installed software
- Setup.exe (PID: 3732)
- Setup.exe (PID: 6360)
INFO
Manual execution by a user
- WinRAR.exe (PID: 3692)
- WinRAR.exe (PID: 5236)
- Setup.exe (PID: 3732)
- Setup.exe (PID: 6360)
The process uses the downloaded file
- WinRAR.exe (PID: 3692)
- WinRAR.exe (PID: 5236)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5236)
The sample compiled with english language support
- WinRAR.exe (PID: 5236)
Checks supported languages
- Setup.exe (PID: 3732)
- Setup.exe (PID: 6360)
Compiled with Borland Delphi (YARA)
- Setup.exe (PID: 3732)
- Setup.exe (PID: 6360)
Reads the software policy settings
- Setup.exe (PID: 6360)
- Setup.exe (PID: 3732)
Reads the computer name
- Setup.exe (PID: 6360)
- Setup.exe (PID: 3732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:22 13:06:46 |
| ZipCRC: | 0x0a216adc |
| ZipCompressedSize: | 11863650 |
| ZipUncompressedSize: | 11863650 |
| ZipFileName: | #Pa$w0rD__6678--0peɴ_Set-Up@#.7z |
Total processes
134
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3692 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\#Pa$w0rD__6678--0peɴ_Set-Up@#.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3732 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Lamantine Software a.s. Integrity Level: MEDIUM Description: Portable Sticky Password run tool Exit code: 0 Version: 8.8.5.1743 Modules
| |||||||||||||||
| 5236 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\#Pa$w0rD__6678--0peɴ_Set-Up@#.7z" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5720 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6172 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6678--0peɴ_Set-Up@#.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
| 6360 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Lamantine Software a.s. Integrity Level: MEDIUM Description: Portable Sticky Password run tool Exit code: 0 Version: 8.8.5.1743 Modules
| |||||||||||||||
Total events
2 835
Read events
2 819
Write events
16
Delete events
0
Modification events
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F00000000000000000000000000000000000000000005803050000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F00000000000000000000000000000000000000000000C0304000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (6172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F0000000000000000000000000000000000000000000E00105000000000000000000180000006400000000000000000000000000000003000000 | |||
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
21
Suspicious files
26
Text files
109
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3692 | WinRAR.exe | C:\Users\admin\Desktop\#Pa$w0rD__6678--0peɴ_Set-Up@#.7z | — | |
MD5:— | SHA256:— | |||
| 5236 | WinRAR.exe | C:\Users\admin\Desktop\Resources\Config\Data\bug78034.phpt | text | |
MD5:D27A19FDE988CAEDEDC179608A95CB3A | SHA256:74152939BDB9BEA0AD72904B64E69E1A3F62C6FF19F2AB9EF976D3FB83F007C3 | |||
| 5236 | WinRAR.exe | C:\Users\admin\Desktop\Resources\Config\change.txt | text | |
MD5:9878038DE35CAA429DE9005518B2E275 | SHA256:CB9552335747A6544211FFE4B4DC98CD7817DCB3D2DB034E390AC11309BA42BF | |||
| 5236 | WinRAR.exe | C:\Users\admin\Desktop\Resources\Config\Data\bcmod.phpt | text | |
MD5:378758E56D88DF69F590980F5C2A4640 | SHA256:165B115F38BD513DB6F8843D2485FB499E4025A725AF780556E472341DEAF6CC | |||
| 5236 | WinRAR.exe | C:\Users\admin\Desktop\Resources\Config\code2.txt | text | |
MD5:131BD577A5612FDC1B83518795549C3D | SHA256:C90AB4DBCF5807B8CE9D34F22B3A5F0F8F38B008371222C7FC83A63B7B57DB75 | |||
| 5236 | WinRAR.exe | C:\Users\admin\Desktop\Resources\Config\Data\bz2_filter_compress.phpt | text | |
MD5:45D6763603D0CADA98764197A22453D3 | SHA256:ED7BBBF583C3962DF9A98829689C6F799A264694F2F52391C7FB33C485BC4177 | |||
| 5236 | WinRAR.exe | C:\Users\admin\Desktop\Resources\Config\Data\const.h | text | |
MD5:5871E169454966ED873DA45E88CA836F | SHA256:6EB43E8A05D0F9F935D2A092FF6CD283868A89A186CA8BEB966062E2472F3996 | |||
| 5236 | WinRAR.exe | C:\Users\admin\Desktop\Resources\Config\Data\DisplayLanguageNames.en_CA.txt | text | |
MD5:C6762A82D75C68A93D7F0C15CF1C23E3 | SHA256:6B7884673A6381EF470660585CB406595D8D898F6EE6B5E92AA180BAB92B521A | |||
| 5236 | WinRAR.exe | C:\Users\admin\Desktop\Resources\Config\Data\bug46064.phpt | text | |
MD5:CF40380DBA6768A0601B9C9B4B3FE413 | SHA256:E74BE1F99C26ADAB2C1F29B7471F32EF0690554098957DF546F20F0D06C1D072 | |||
| 5236 | WinRAR.exe | C:\Users\admin\Desktop\Resources\Config\Data\gh16777_1.phpt | text | |
MD5:15383B745898A3F6FAED824BE93AA9F4 | SHA256:30C020C18272DFEFCFE9162C4F98989171CC2E9BF7A84BAA4B9763D41659C8E2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
41
DNS requests
16
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7112 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6772 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7112 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 2.16.164.114:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4164 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
624 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | — | AKAMAI-AS | DE | unknown |
1076 | svchost.exe | 2.23.242.9:443 | go.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3732 | Setup.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
6360 | Setup.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |