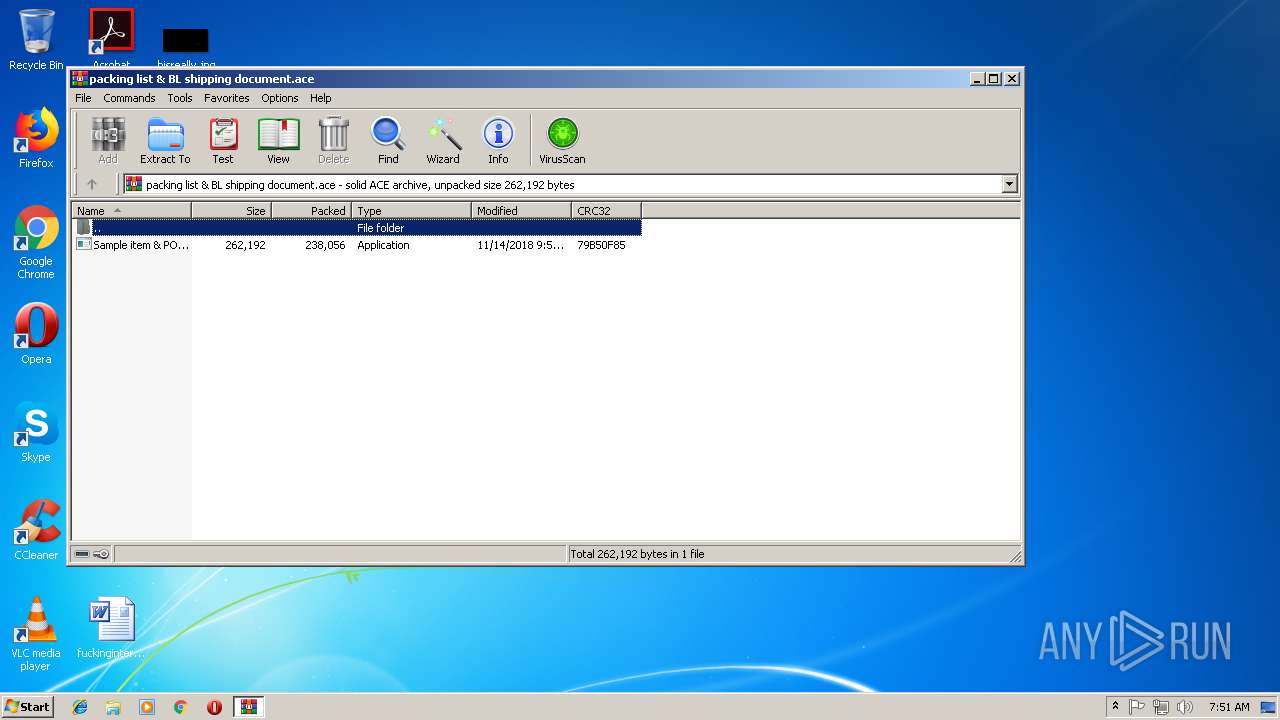
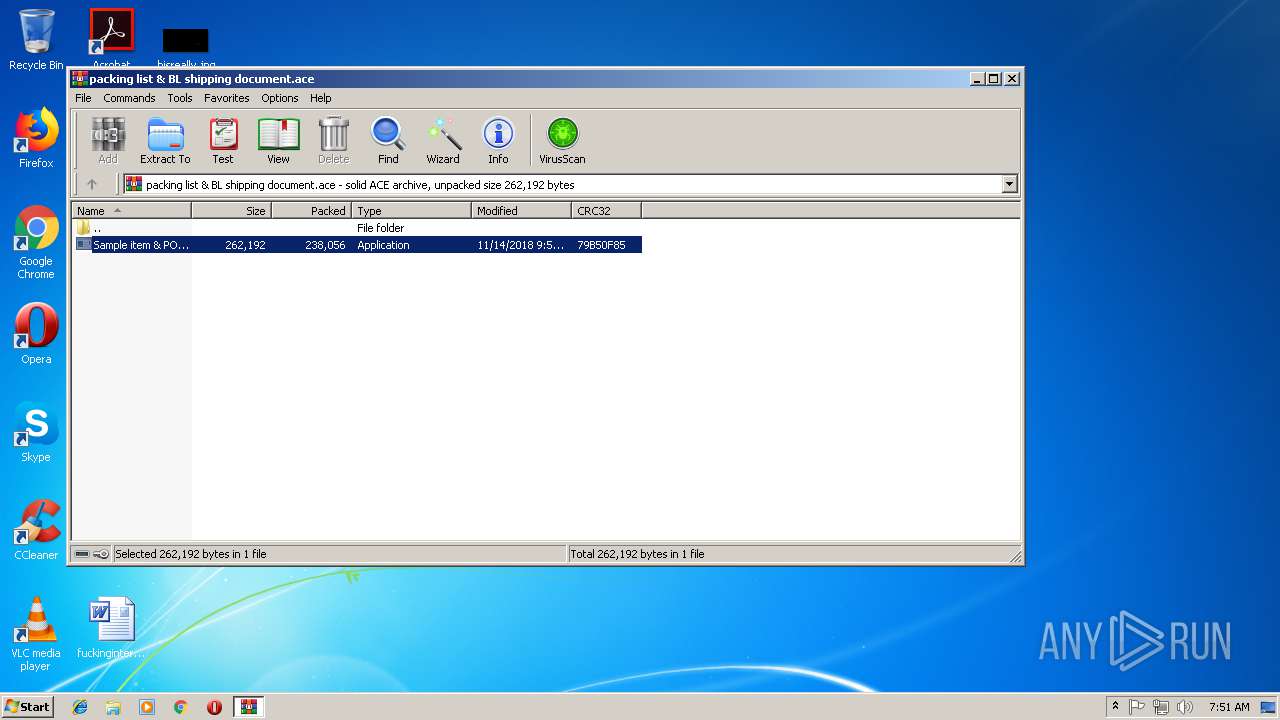
| File name: | packing list & BL shipping document.ace |
| Full analysis: | https://app.any.run/tasks/d5265df0-c4cc-428e-a2c0-3023b58e6940 |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | November 15, 2018, 07:51:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | ACE archive data version 20, from Win/32, version 20 to extract, solid |
| MD5: | 97606C54C896F88C7CCD2A21AA531418 |
| SHA1: | B8C9A9002C9DAD071BC09BE842F36D1935CE6CD2 |
| SHA256: | D42AA3AC80F9C88BC2ED8E211EDFDB1FF58BB60EA5AF9C147126E50F7E7DB92F |
| SSDEEP: | 6144:x7PINEP//B0Gp8CQQTeWAGWgmUjYLaJLfr:x7P7P/ugQaeWxWgFYL6r |
MALICIOUS
Application was dropped or rewritten from another process
- Sample item & PO4829831796 design.exe (PID: 2524)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3272)
- Sample item & PO4829831796 design.exe (PID: 2524)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ace | | | ACE compressed archive (100) |
|---|
Total processes
33
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2524 | "C:\Users\admin\Desktop\Sample item & PO4829831796 design.exe" | C:\Users\admin\Desktop\Sample item & PO4829831796 design.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3272 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\packing list & BL shipping document.ace" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
464
Read events
434
Write events
30
Delete events
0
Modification events
| (PID) Process: | (3272) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3272) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3272) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3272) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\packing list & BL shipping document.ace | |||
| (PID) Process: | (3272) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3272) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3272) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3272) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3272) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\ACE Compression Software\ActiveAce\2.0 |
| Operation: | write | Name: | Count |
Value: 0 | |||
| (PID) Process: | (3272) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\ACE Compression Software\ActiveAce\2.0 |
| Operation: | write | Name: | Name |
Value: 542D4B42647265644B76737A7E794B566767537663764B5B7874767B4B43727A674B6776747C7E7970377B7E6463373137555B37647F7E67677E797037737874627A727963397674721717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171717171700 | |||
Executable files
3
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3272 | WinRAR.exe | C:\Users\admin\Desktop\Sample item & PO4829831796 design.exe | executable | |
MD5:— | SHA256:— | |||
| 2524 | Sample item & PO4829831796 design.exe | C:\Users\admin\AppData\Local\Temp\Subabbot | binary | |
MD5:— | SHA256:— | |||
| 2524 | Sample item & PO4829831796 design.exe | C:\Users\admin\AppData\Local\Temp\beeeaters.dll | executable | |
MD5:— | SHA256:— | |||
| 2524 | Sample item & PO4829831796 design.exe | C:\Users\admin\AppData\Local\Temp\made.rtf | text | |
MD5:8274425DE767B30B2FFF1124AB54ABB5 | SHA256:0D6AFB7E939F0936F40AFDC759B5A354EA5427EC250A47E7B904AB1EA800A01D | |||
| 2524 | Sample item & PO4829831796 design.exe | C:\Users\admin\AppData\Local\Temp\nsbFCBB.tmp\System.dll | executable | |
MD5:75ED96254FBF894E42058062B4B4F0D1 | SHA256:A632D74332B3F08F834C732A103DAFEB09A540823A2217CA7F49159755E8F1D7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
1
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 404 | 188.225.24.241:80 | http://mamujeeproduct.com/nk/encode.php | RU | text | 15 b | malicious |
— | — | POST | 404 | 188.225.24.241:80 | http://mamujeeproduct.com/nk/encode.php | RU | text | 15 b | malicious |
— | — | POST | 404 | 188.225.24.241:80 | http://mamujeeproduct.com/nk/encode.php | RU | binary | 23 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 188.225.24.241:80 | mamujeeproduct.com | TimeWeb Ltd. | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mamujeeproduct.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
— | — | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
— | — | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
— | — | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |