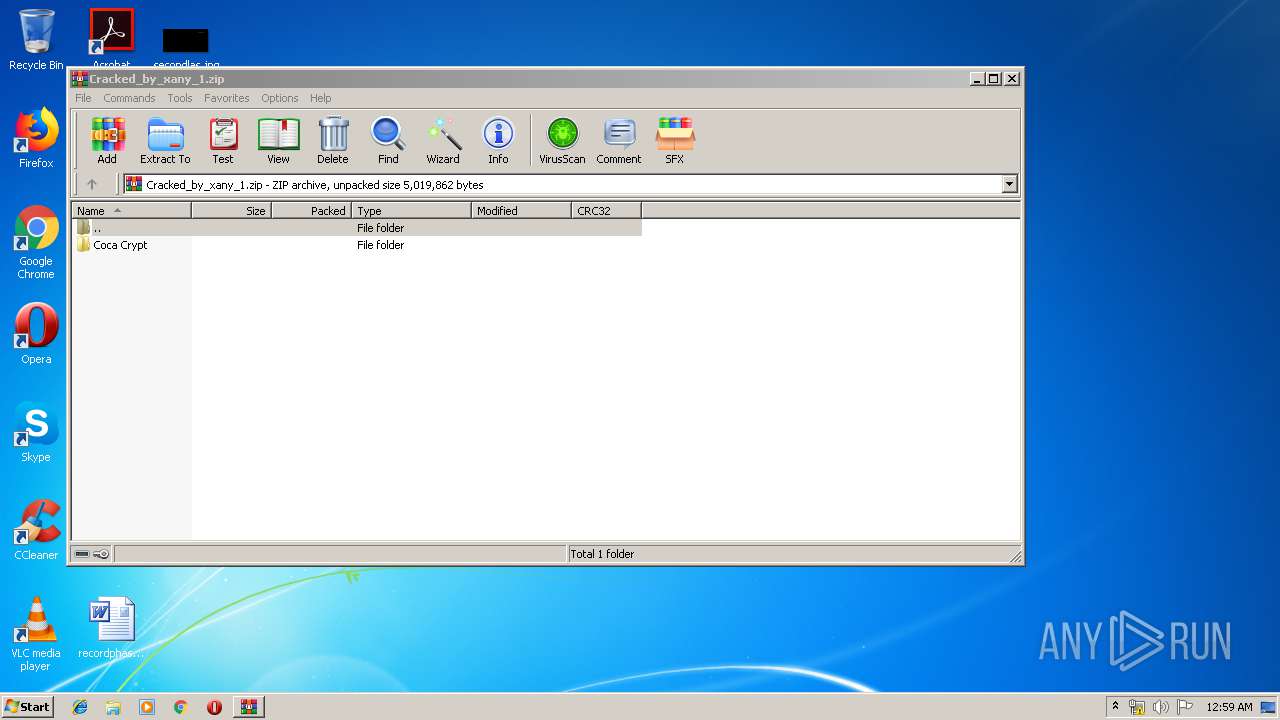
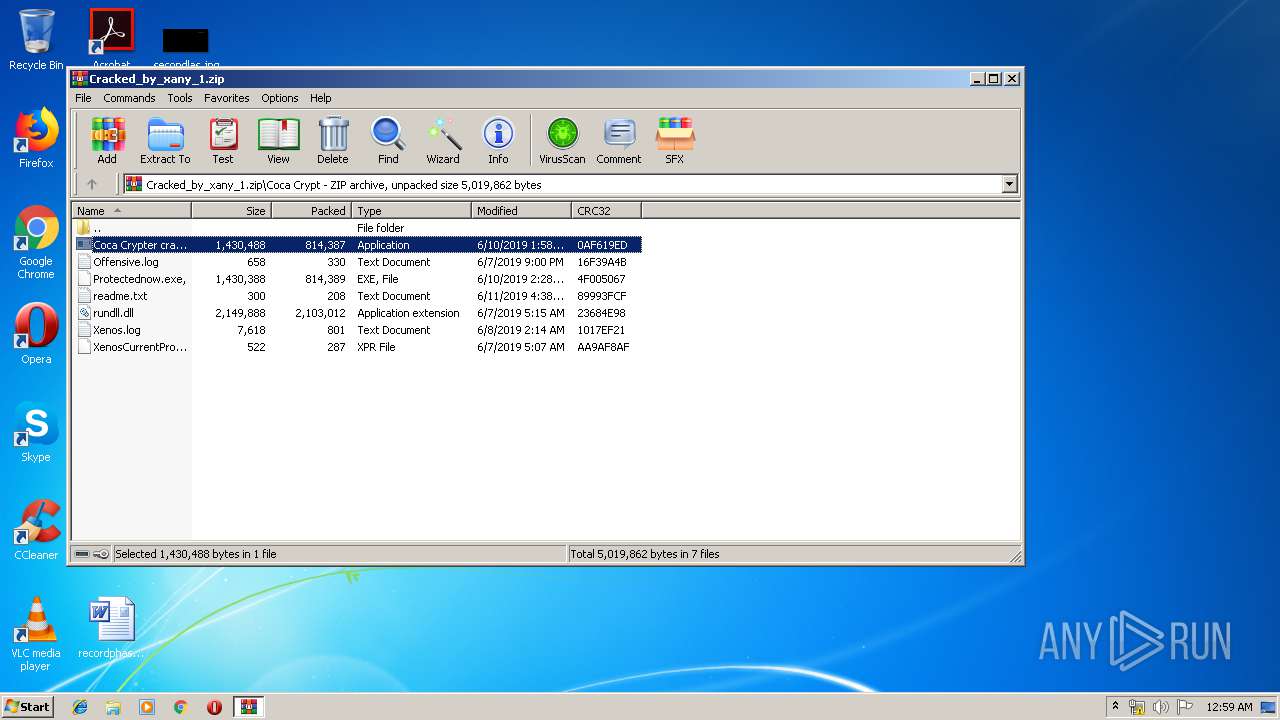
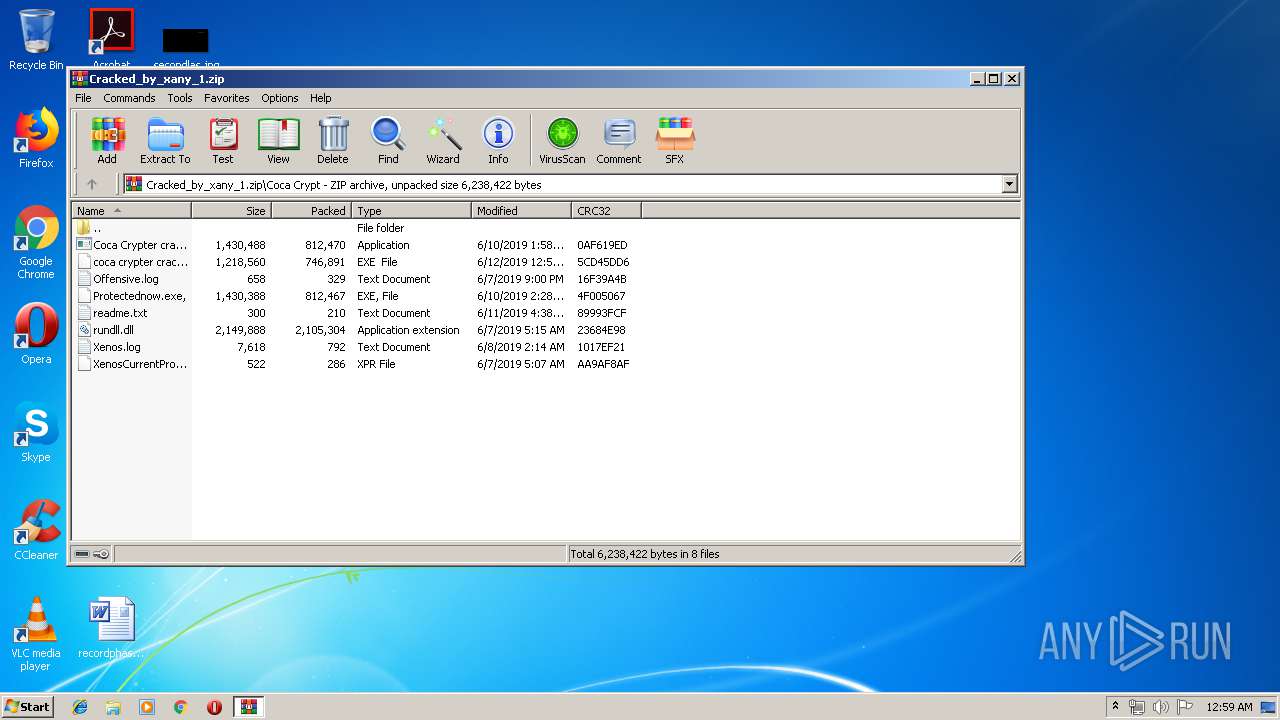
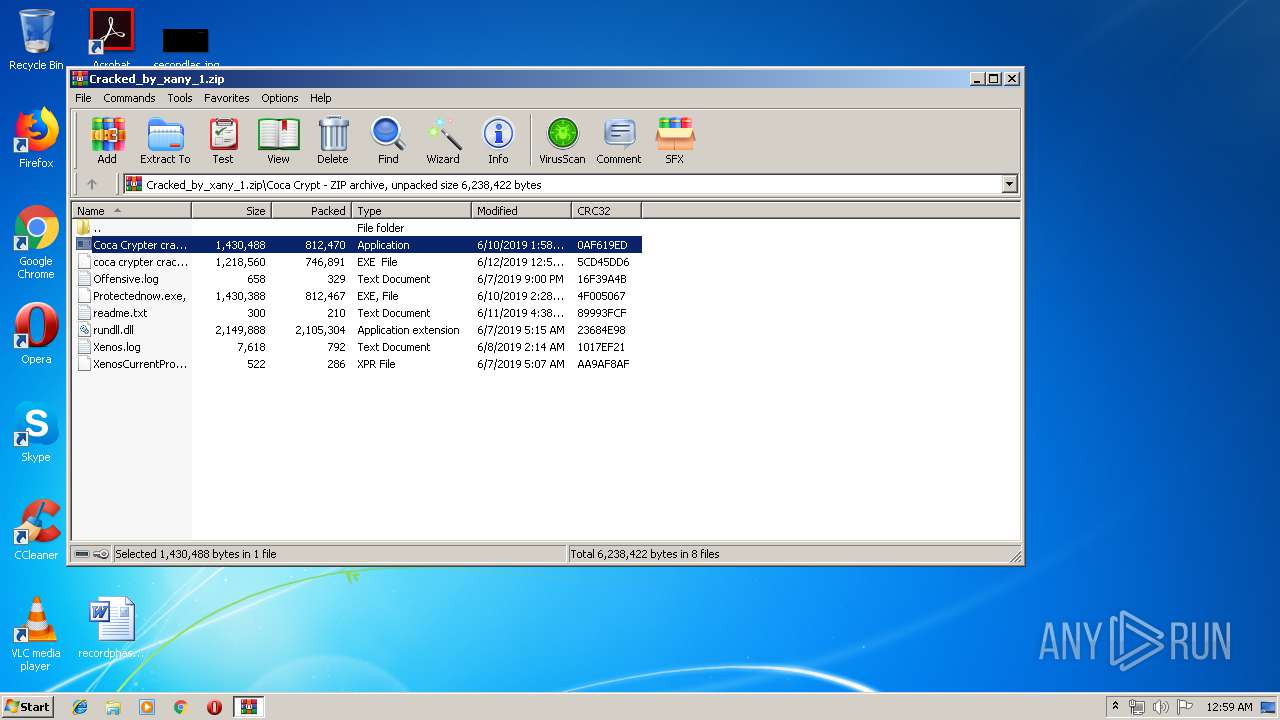
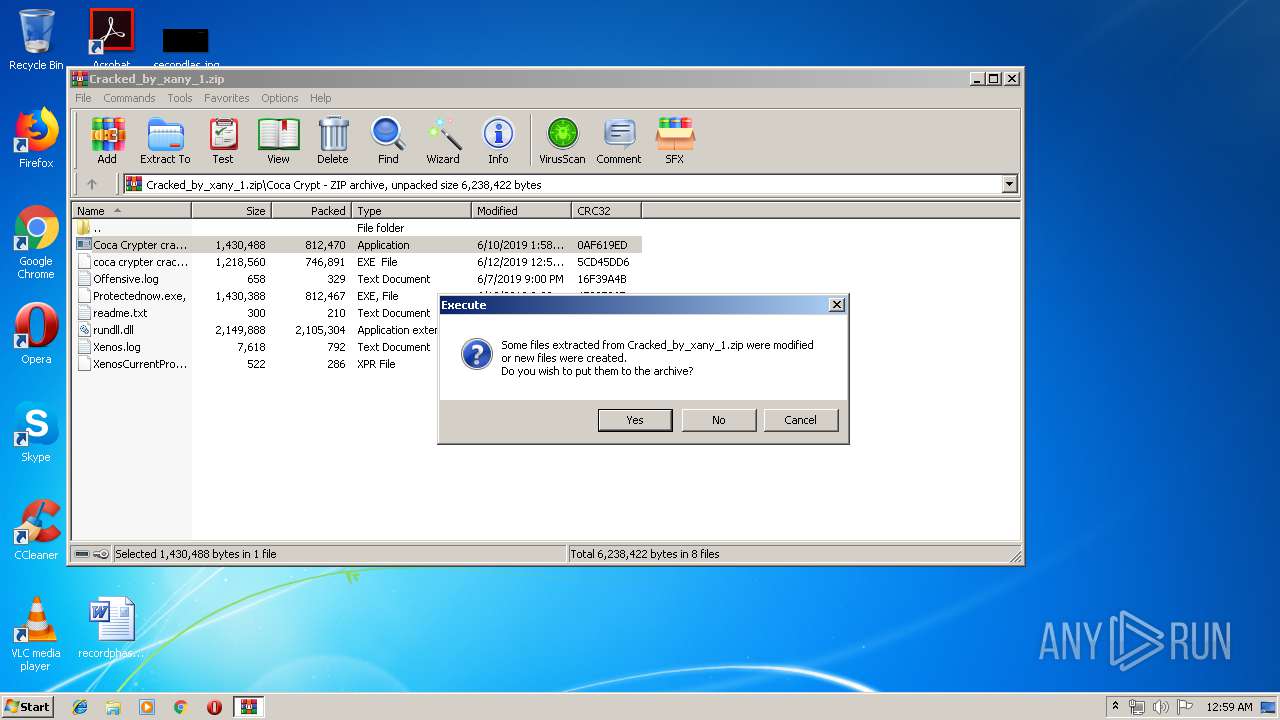
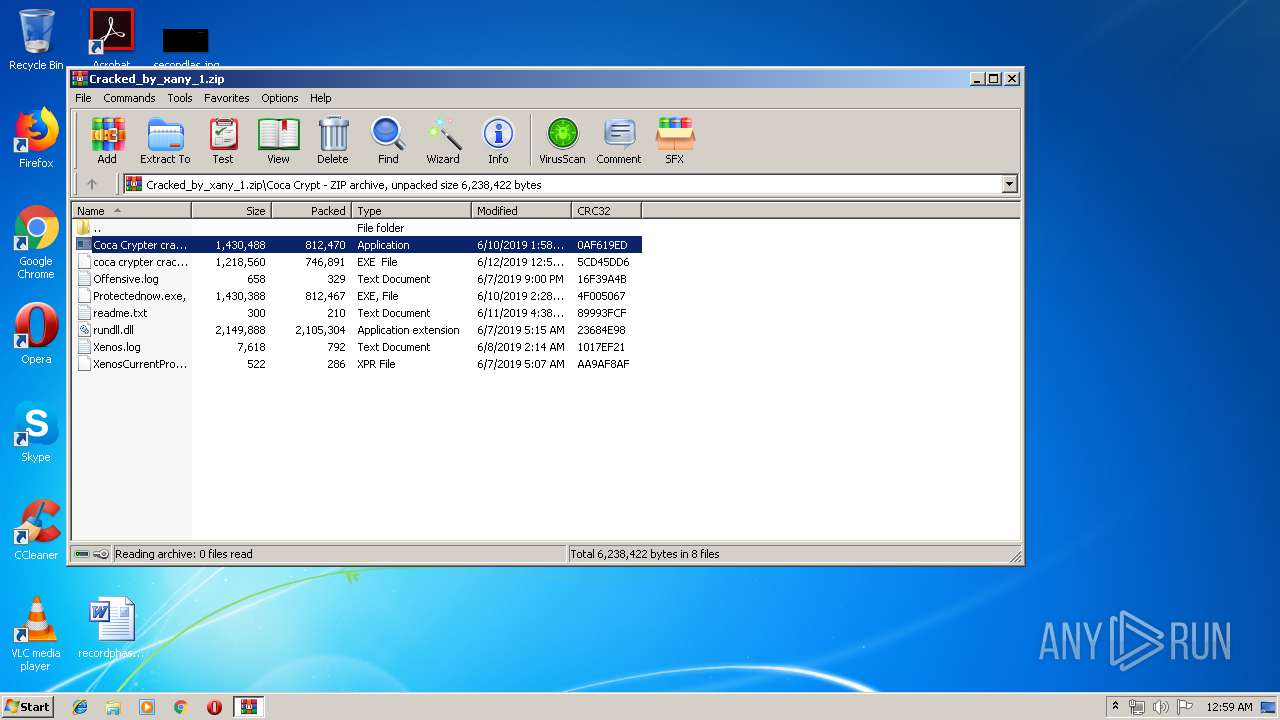
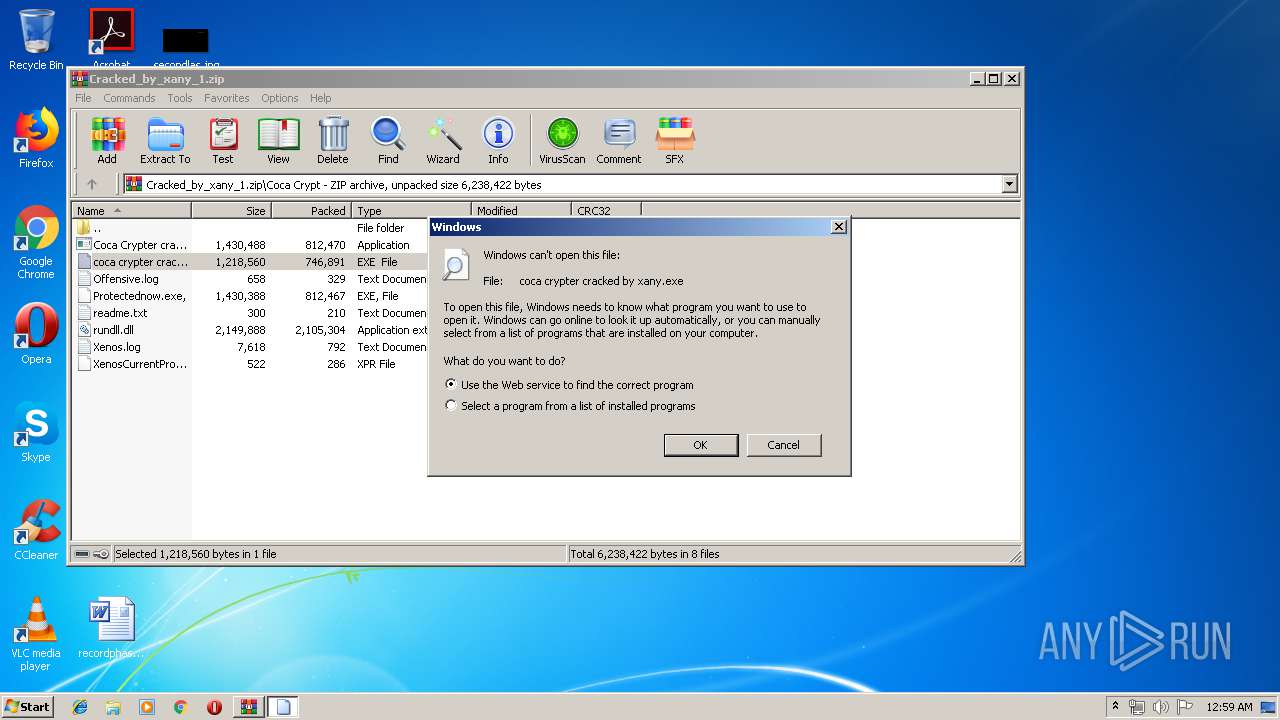
| download: | Cracked_by_xany_1.zip |
| Full analysis: | https://app.any.run/tasks/f3ddaa75-9c16-43f4-8f5e-f6b0aa70fc16 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | June 11, 2019, 23:58:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 1D172FF502F0801053A05BD5AC134963 |
| SHA1: | 0595C3662A2F4566647DC6C3782195037C5A9E04 |
| SHA256: | D2F90B648F96F5D993CA89DFE81E92DEB650A8A7FFB435A75B8E179A36880A0D |
| SSDEEP: | 98304:CG8wRhKKugYD/fKKu8ADUS+fFyinaUDUPQlLNSqgyJJ:1/vuFfvuD4S+psgYHaJ |
MALICIOUS
Application was dropped or rewritten from another process
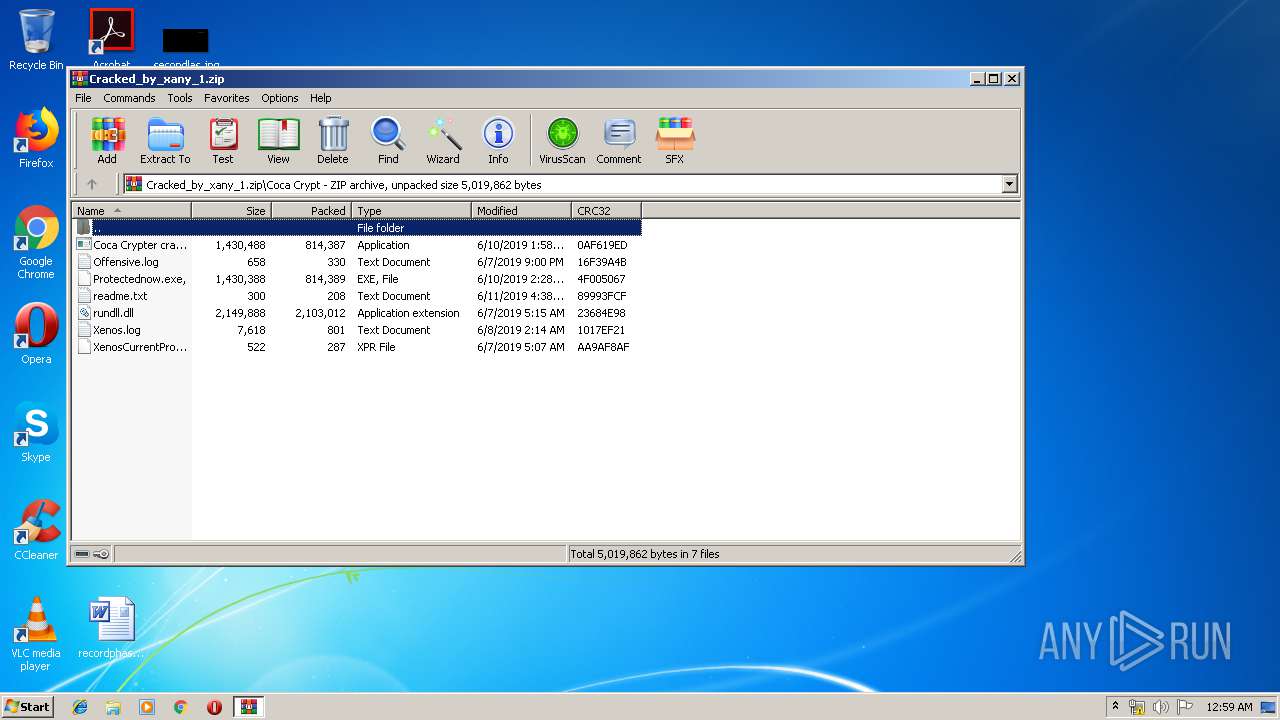
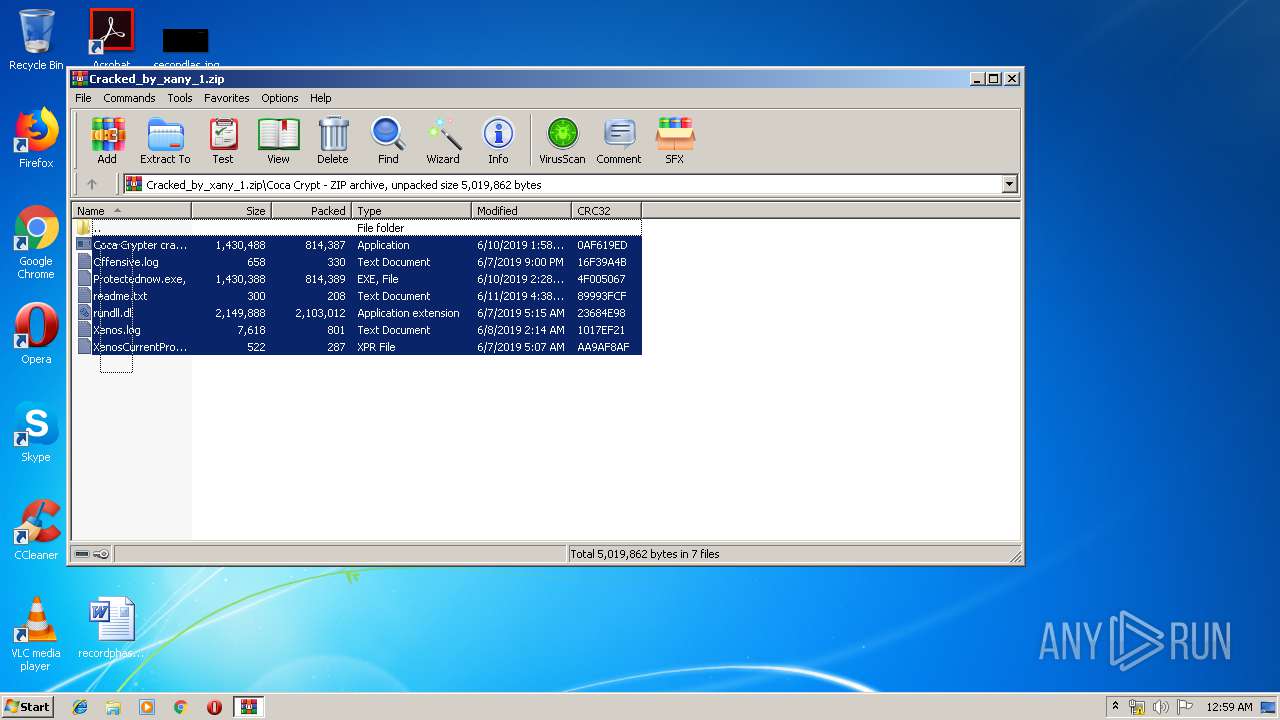
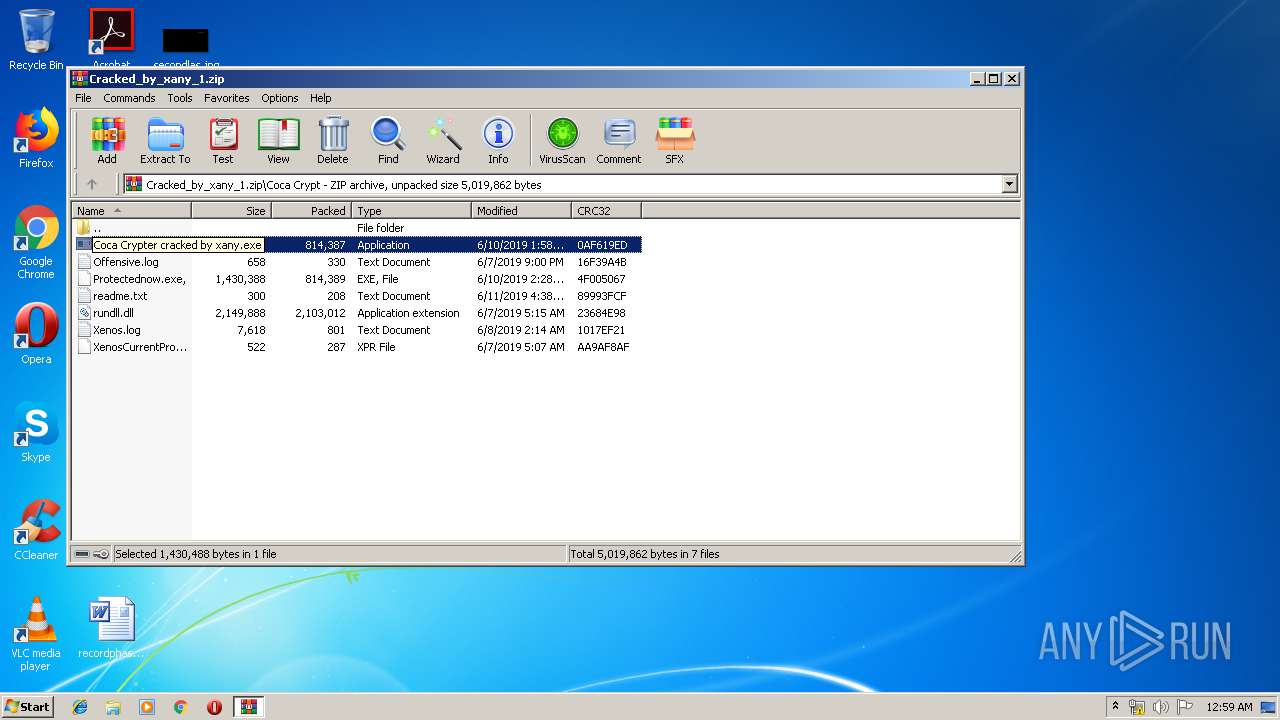
- Coca Crypter cracked by xany.exe (PID: 2416)
- icsys.icn.exe (PID: 2140)
- coca crypter cracked by xany.exe (PID: 2512)
- Coca Crypter cracked by xany.exe (PID: 2672)
- coca crypter cracked by xany.exe (PID: 2380)
- icsys.icn.exe (PID: 3280)
Changes the autorun value in the registry
- coca crypter cracked by xany.exe (PID: 2512)
QUASAR was detected
- RegAsm.exe (PID: 3584)
SUSPICIOUS
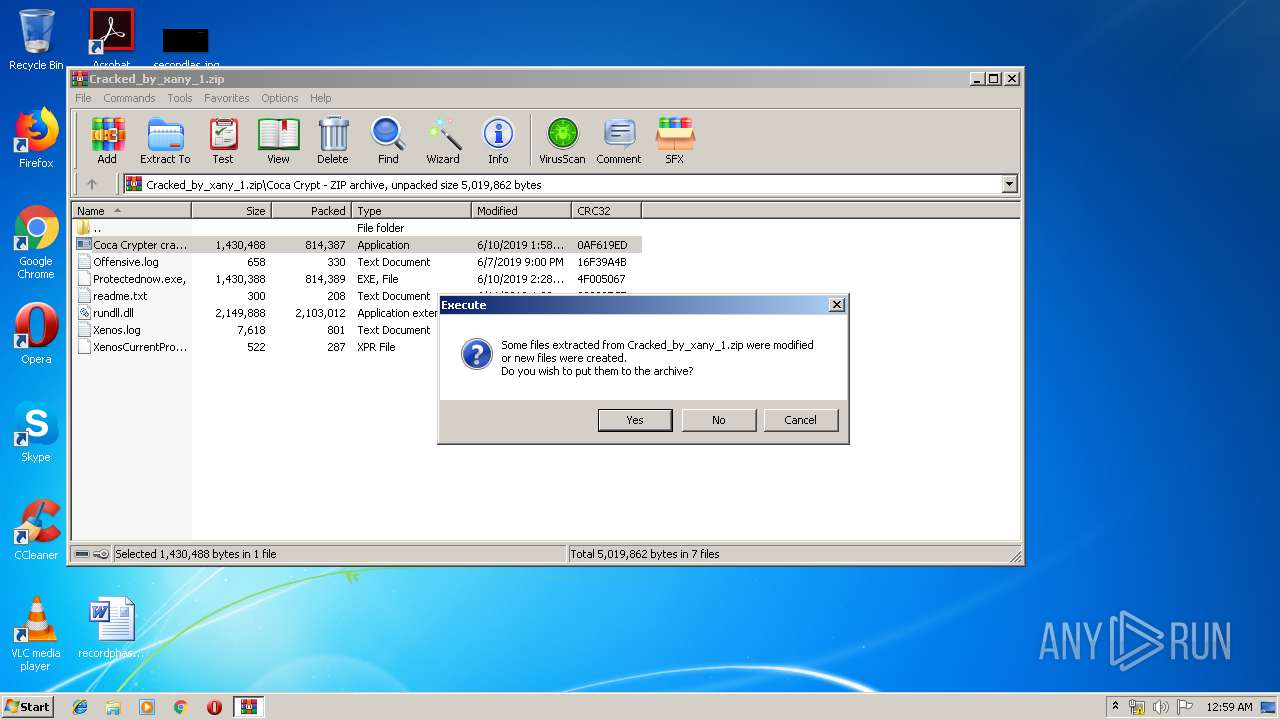
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3296)
- Coca Crypter cracked by xany.exe (PID: 2416)
- coca crypter cracked by xany.exe (PID: 2512)
- Coca Crypter cracked by xany.exe (PID: 2672)
Starts application with an unusual extension
- Coca Crypter cracked by xany.exe (PID: 2416)
- Coca Crypter cracked by xany.exe (PID: 2672)
Starts itself from another location
- Coca Crypter cracked by xany.exe (PID: 2416)
- Coca Crypter cracked by xany.exe (PID: 2672)
Creates files in the user directory
- coca crypter cracked by xany.exe (PID: 2512)
Checks for external IP
- RegAsm.exe (PID: 3584)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 3296)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:06:10 13:58:25 |
| ZipCRC: | 0x0af619ed |
| ZipCompressedSize: | 814387 |
| ZipUncompressedSize: | 1430488 |
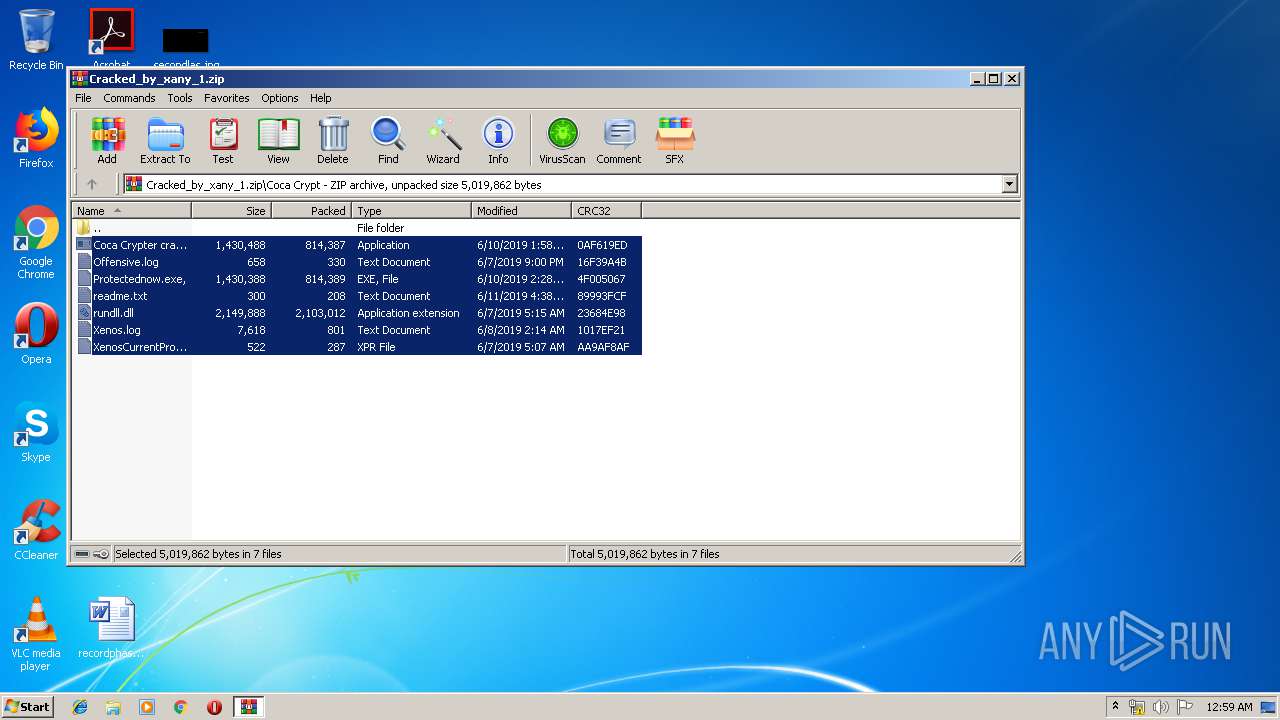
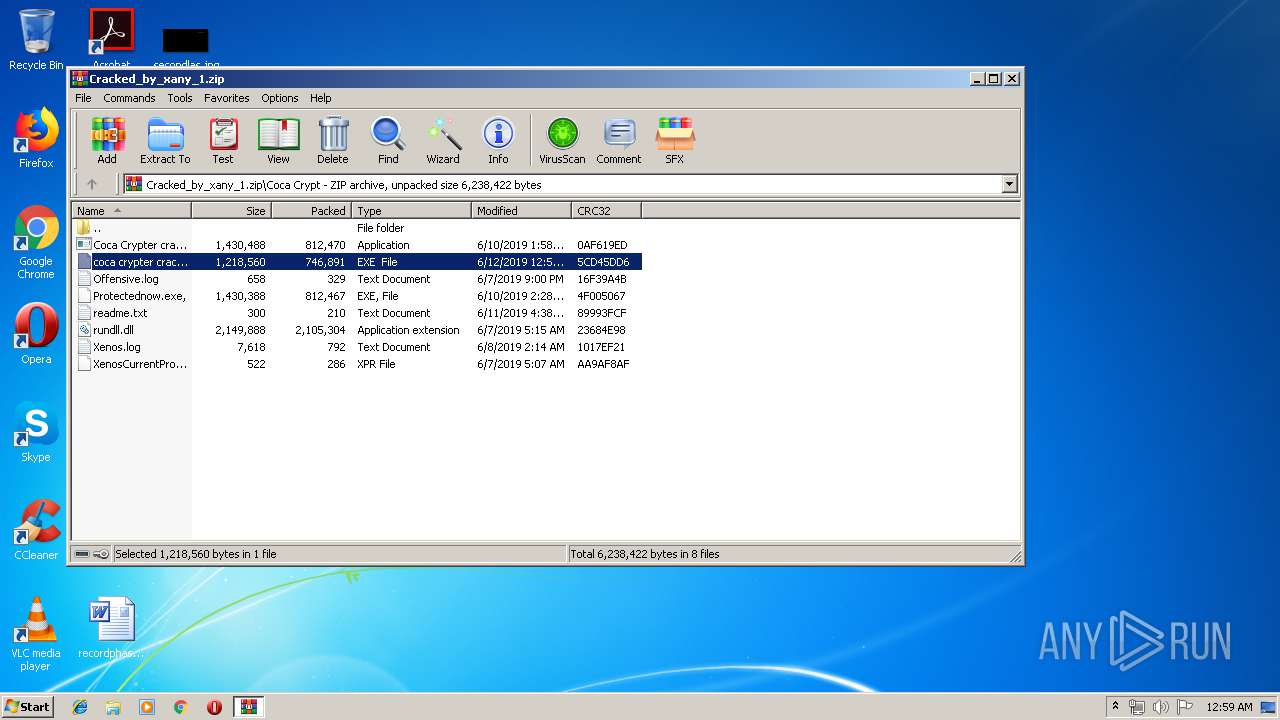
| ZipFileName: | Coca Crypt/Coca Crypter cracked by xany.exe |
Total processes
45
Monitored processes
14
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | coca crypter cracked by xany.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 2140 | C:\Users\admin\AppData\Local\icsys.icn.exe | C:\Users\admin\AppData\Local\icsys.icn.exe | — | Coca Crypter cracked by xany.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2380 | "c:\users\admin\appdata\local\temp\rar$exa3296.8585\coca crypt\coca crypter cracked by xany.exe " | c:\users\admin\appdata\local\temp\rar$exa3296.8585\coca crypt\coca crypter cracked by xany.exe | — | Coca Crypter cracked by xany.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2416 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.6696\Coca Crypt\Coca Crypter cracked by xany.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.6696\Coca Crypt\Coca Crypter cracked by xany.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2512 | "c:\users\admin\appdata\local\temp\rar$exa3296.6696\coca crypt\coca crypter cracked by xany.exe " | c:\users\admin\appdata\local\temp\rar$exa3296.6696\coca crypt\coca crypter cracked by xany.exe | Coca Crypter cracked by xany.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2652 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | coca crypter cracked by xany.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.8585\Coca Crypt\Coca Crypter cracked by xany.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.8585\Coca Crypt\Coca Crypter cracked by xany.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3116 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | coca crypter cracked by xany.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 3152 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | coca crypter cracked by xany.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 3280 | C:\Users\admin\AppData\Local\icsys.icn.exe | C:\Users\admin\AppData\Local\icsys.icn.exe | — | Coca Crypter cracked by xany.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
821
Read events
771
Write events
50
Delete events
0
Modification events
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Cracked_by_xany_1.zip | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Cracked_by_xany_1 | |||
Executable files
16
Suspicious files
2
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2416 | Coca Crypter cracked by xany.exe | C:\Users\admin\AppData\Local\Temp\~DF7AE0C9B00C4D4D7A.TMP | — | |
MD5:— | SHA256:— | |||
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rzi_3296.7419 | — | |
MD5:— | SHA256:— | |||
| 2140 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DF37B205F8B025EA94.TMP | — | |
MD5:— | SHA256:— | |||
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cracked_by_xany_1\Protectednow.exe, | executable | |
MD5:— | SHA256:— | |||
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cracked_by_xany_1\rundll.dll | executable | |
MD5:— | SHA256:— | |||
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cracked_by_xany_1\readme.txt | text | |
MD5:— | SHA256:— | |||
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.6696\Coca Crypt\Coca Crypter cracked by xany.exe | executable | |
MD5:— | SHA256:— | |||
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cracked_by_xany_1\XenosCurrentProfile.xpr | text | |
MD5:— | SHA256:— | |||
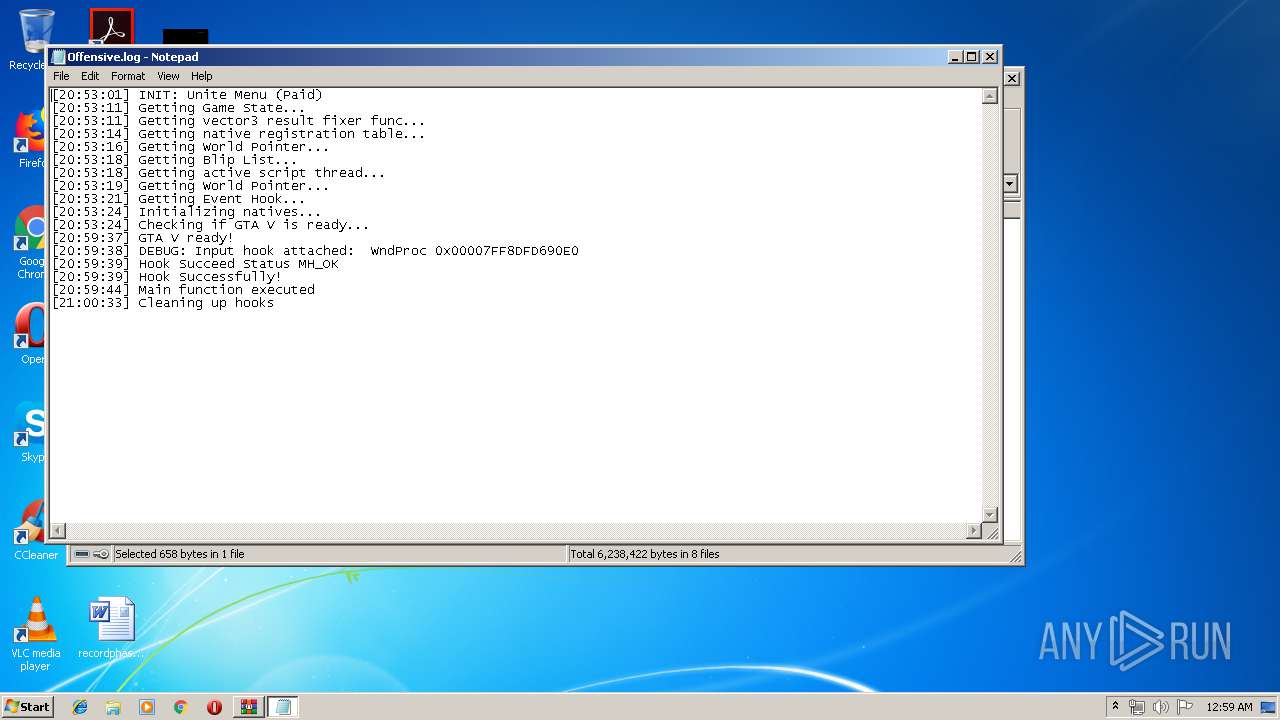
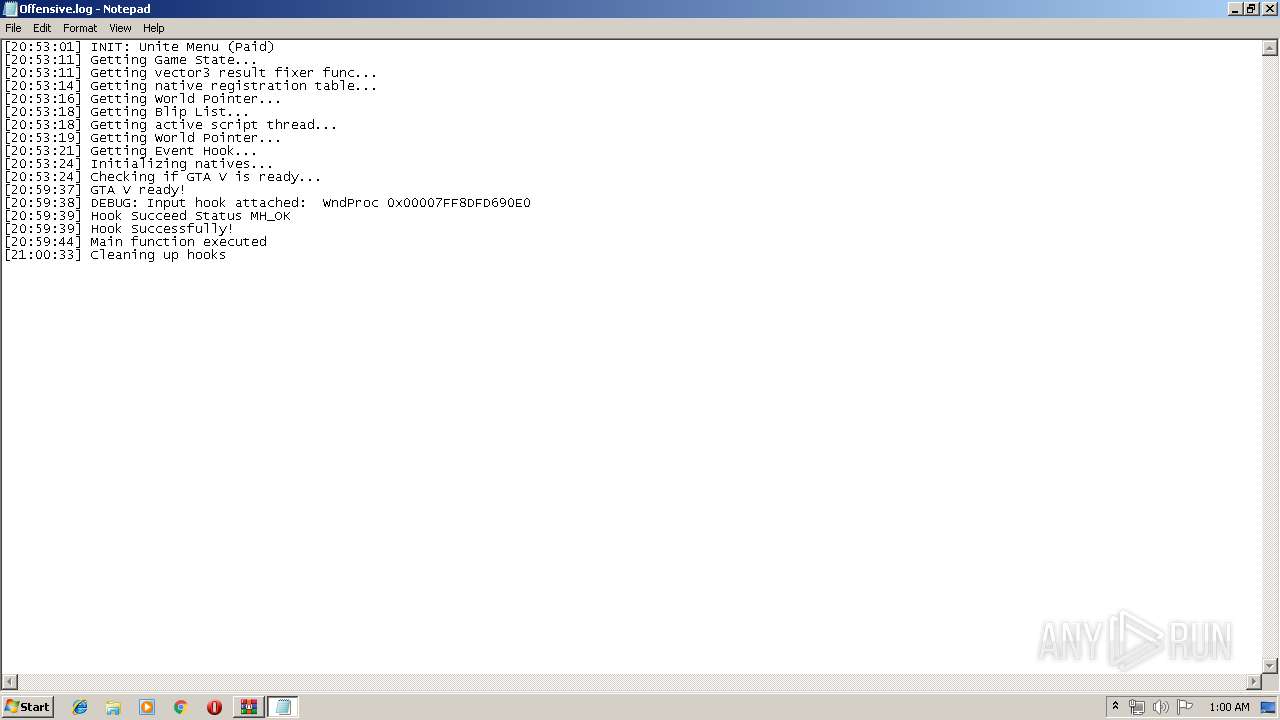
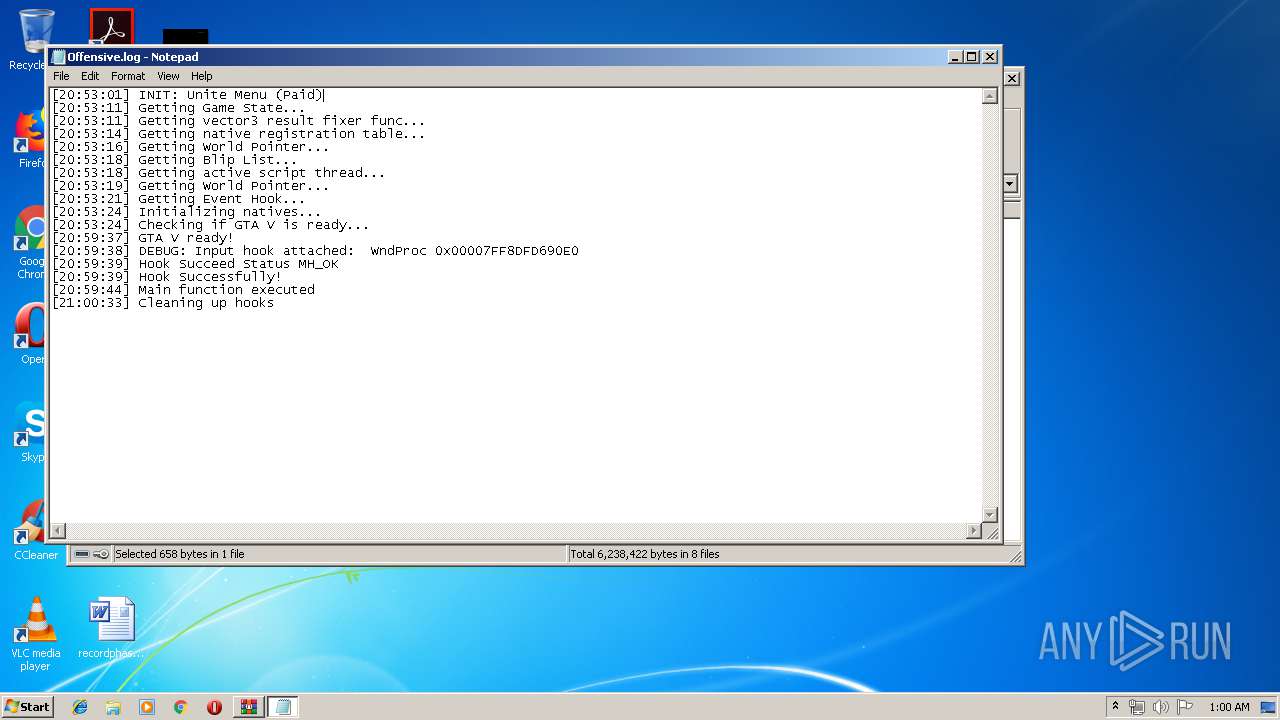
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.6696\Coca Crypt\Offensive.log | text | |
MD5:— | SHA256:— | |||
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Cracked_by_xany_1\Coca Crypter cracked by xany.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
1
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3584 | RegAsm.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/json/ | DE | text | 321 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3584 | RegAsm.exe | 185.194.141.58:80 | ip-api.com | netcup GmbH | DE | unknown |
3584 | RegAsm.exe | 104.248.42.215:4782 | — | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3584 | RegAsm.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
3584 | RegAsm.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
3584 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Quasar 1.3 RAT IP Lookup ip-api.com (HTTP headeer) |
3584 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Quasar RAT |
1 ETPRO signatures available at the full report