| File name: | Nexol.zip |
| Full analysis: | https://app.any.run/tasks/cce3c0a0-b954-4786-b949-ab553e8f2047 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | December 14, 2024, 00:32:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
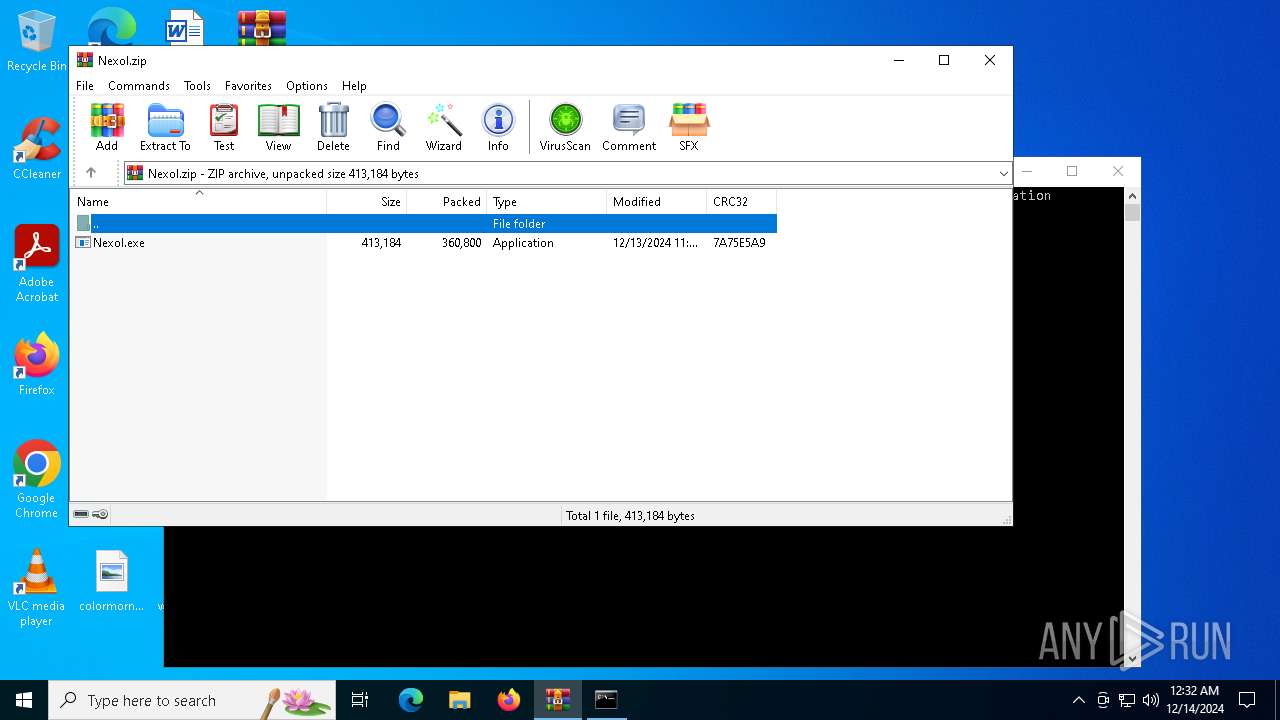
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 0BF42EAED1BF792ACA6430FAB77000E8 |
| SHA1: | 449A5986A4EDE250376287BAC6EECC7A70331E3A |
| SHA256: | D25CE2BCAD786CE1A3DE43271C168D943EAA40756255352CC22FC028324F76AB |
| SSDEEP: | 12288:66n/geVE07xzgdnxY1+YqR7xOGRHoUsJBa9yBXcAQ7y4jFXqJkxxojmQ:6MIwE07xzgdxY1+JRV1JsJ49yBXcy4j+ |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
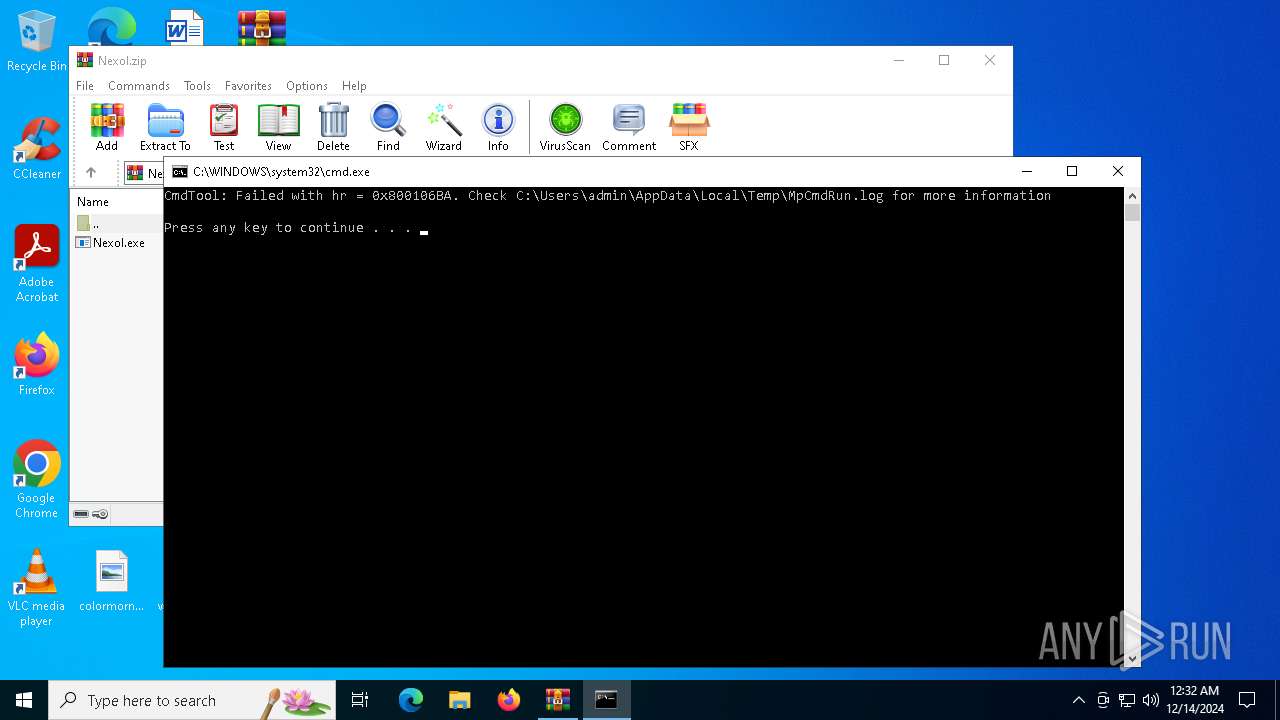
- MpCmdRun.exe (PID: 6844)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
- Nexol.exe (PID: 6972)
Connects to the CnC server
- svchost.exe (PID: 2192)
Actions looks like stealing of personal data
- Nexol.exe (PID: 6972)
LUMMA mutex has been found
- Nexol.exe (PID: 6972)
Steals credentials from Web Browsers
- Nexol.exe (PID: 6972)
LUMMA has been detected (YARA)
- Nexol.exe (PID: 6972)
SUSPICIOUS
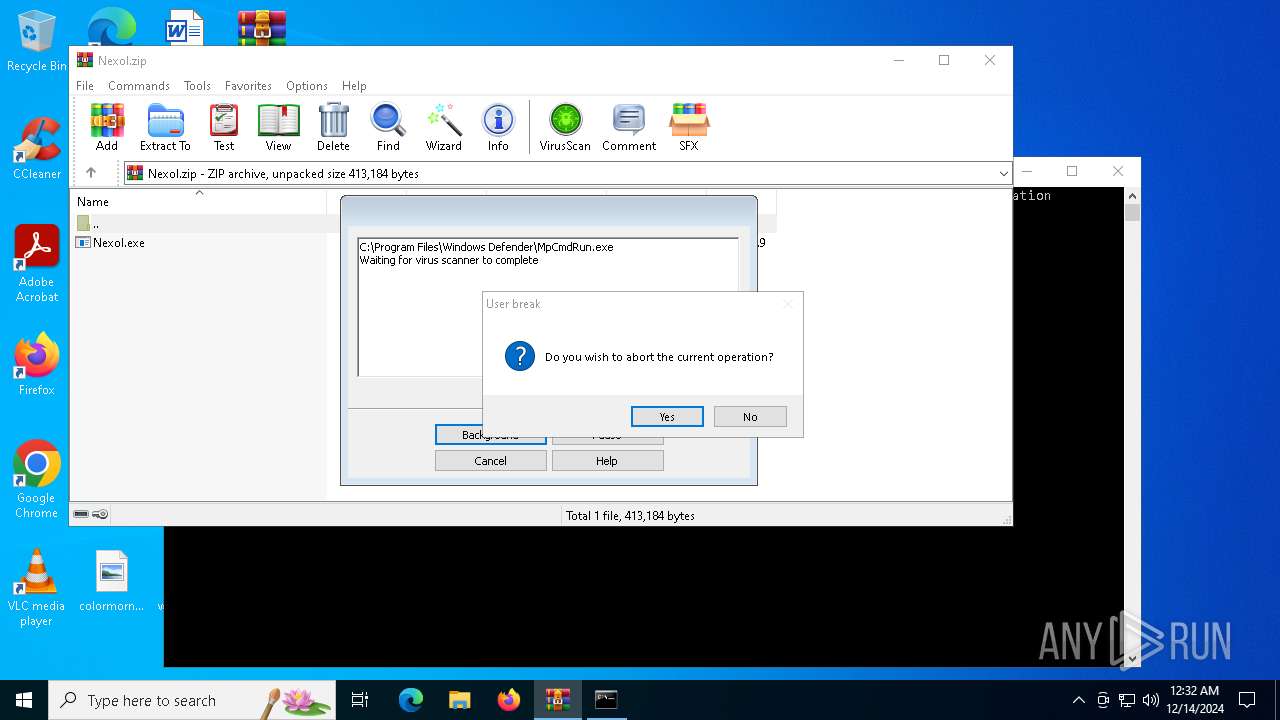
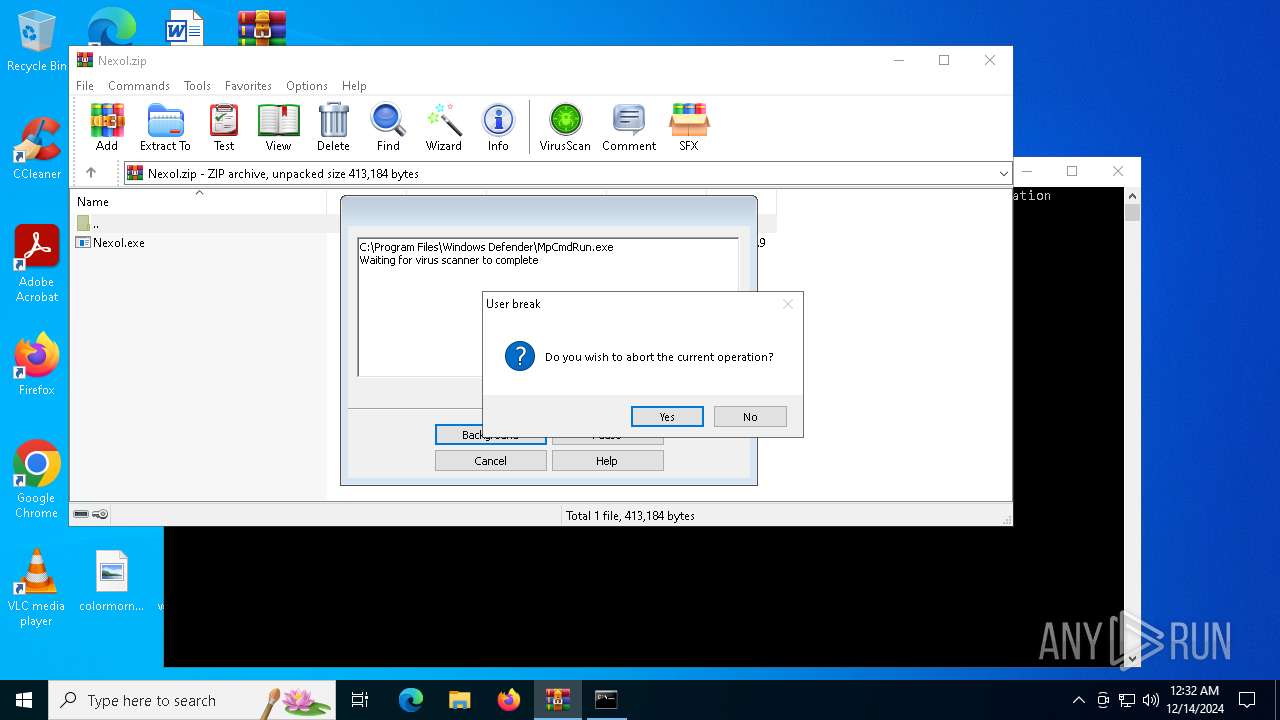
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6284)
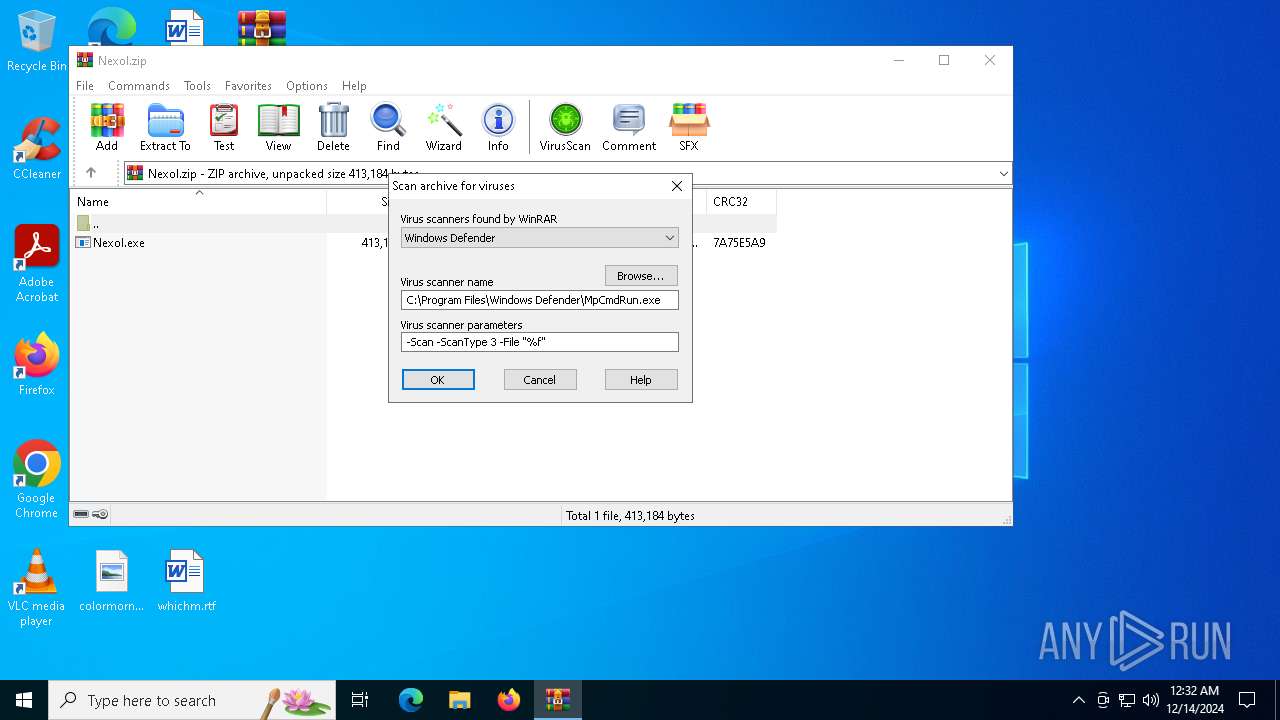
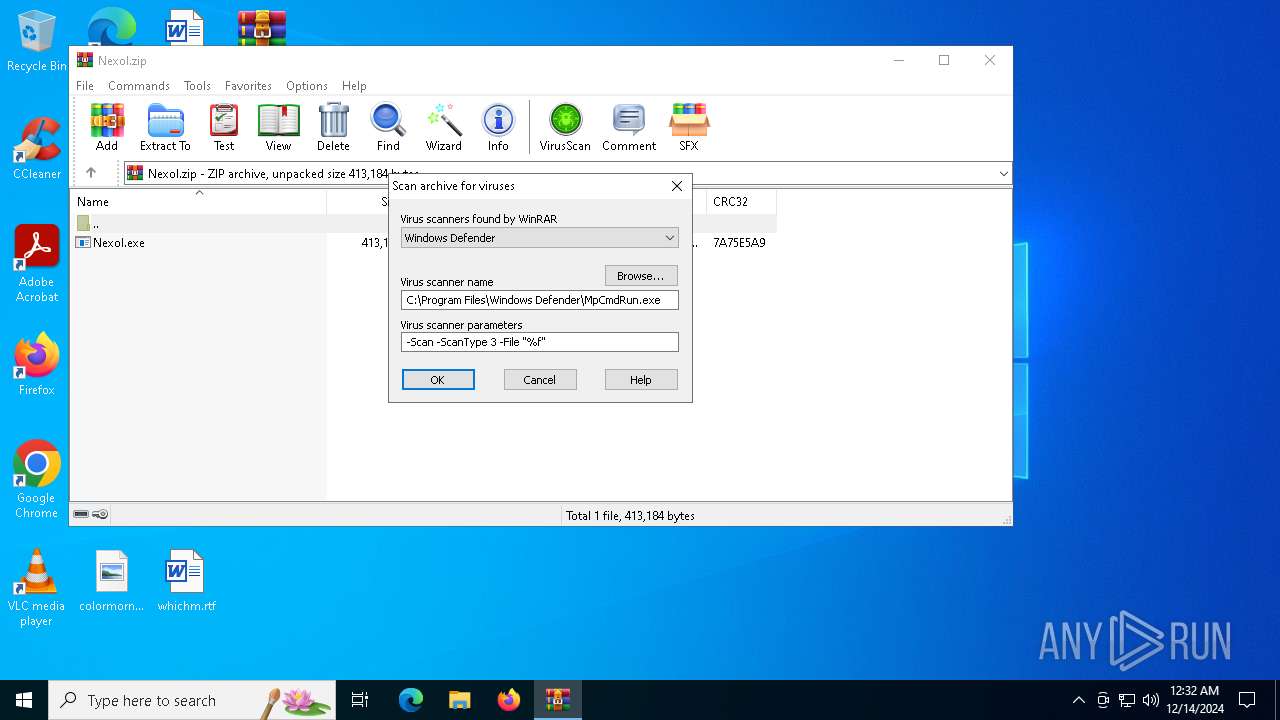
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6284)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6284)
Application launched itself
- Nexol.exe (PID: 6908)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2192)
- Nexol.exe (PID: 6972)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6284)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6284)
Checks supported languages
- MpCmdRun.exe (PID: 6844)
- Nexol.exe (PID: 6908)
- Nexol.exe (PID: 6972)
Reads the computer name
- MpCmdRun.exe (PID: 6844)
- Nexol.exe (PID: 6972)
Create files in a temporary directory
- MpCmdRun.exe (PID: 6844)
Manual execution by a user
- Nexol.exe (PID: 6908)
Reads the machine GUID from the registry
- Nexol.exe (PID: 6972)
Reads the software policy settings
- Nexol.exe (PID: 6972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:13 18:32:08 |
| ZipCRC: | 0x7a75e5a9 |
| ZipCompressedSize: | 360800 |
| ZipUncompressedSize: | 413184 |
| ZipFileName: | Nexol.exe |
Total processes
127
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6284 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Nexol.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6780 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6284.15890\Rar$Scan7475.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6788 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6844 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6284.15890" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6908 | "C:\Users\admin\Desktop\Nexol.exe" | C:\Users\admin\Desktop\Nexol.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6916 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Nexol.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6972 | "C:\Users\admin\Desktop\Nexol.exe" | C:\Users\admin\Desktop\Nexol.exe | Nexol.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
5 115
Read events
5 098
Write events
17
Delete events
0
Modification events
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Nexol.zip | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
| (PID) Process: | (6284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
Executable files
1
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6284.15890\Nexol.zip\Nexol.exe | executable | |
MD5:D4C48D03045F583445C43DCD5A7C654D | SHA256:E6BA1149605816935DBB7604A32459059FE28A0DAE1A2F4F1F04EE5D2A86AF96 | |||
| 6284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6284.15890\Rar$Scan7475.bat | text | |
MD5:F812D4341B07534B0EE929931687215C | SHA256:20DADC289060A2EF39ADE27130B16E202D83D79466B546534C48CC3B31CE06D8 | |||
| 6844 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:5F77F2C815101DC5500A3C32D670BEC4 | SHA256:D566EA45281DF388C1D18732F826F7E41EC0862B36D986D5F6F89271A06A94C3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
27
DNS requests
8
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2144 | RUXIMICS.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2356 | svchost.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2144 | RUXIMICS.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2356 | svchost.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 188.114.97.3:443 | https://bellflamre.click/api | unknown | text | 18.2 Kb | malicious |
— | — | POST | 200 | 188.114.96.3:443 | https://bellflamre.click/api | unknown | text | 2 b | malicious |
— | — | POST | 200 | 188.114.96.3:443 | https://bellflamre.click/api | unknown | text | 16 b | malicious |
— | — | POST | 200 | 188.114.97.3:443 | https://bellflamre.click/api | unknown | text | 48 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2356 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2144 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.80.27:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2356 | svchost.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2144 | RUXIMICS.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2356 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
bellflamre.click |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (bellflamre .click) |
6972 | Nexol.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (bellflamre .click in TLS SNI) |
6972 | Nexol.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (bellflamre .click in TLS SNI) |
6972 | Nexol.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (bellflamre .click in TLS SNI) |
6972 | Nexol.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (bellflamre .click in TLS SNI) |
6972 | Nexol.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (bellflamre .click in TLS SNI) |
6972 | Nexol.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (bellflamre .click in TLS SNI) |