| File name: | reflection_questions_on_the_four_agreements(97717).js |
| Full analysis: | https://app.any.run/tasks/41f92519-9850-49c6-8066-c95d225c1cf3 |
| Verdict: | Malicious activity |
| Threats: | GootLoader is an initial-access-as-a-service malware that operates by delivering the GootKit banking trojan and other malicious payloads. It utilizes techniques such as fileless execution and process injection to avoid detection. The malware is often distributed through SEO poisoning and compromised websites, deceiving users into downloading infected files. |
| Analysis date: | April 20, 2025, 19:23:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/javascript |
| File info: | JavaScript source, ASCII text |
| MD5: | DFB3DEAF1C98DDD0D67EC2548578B458 |
| SHA1: | 4759F324B5691A442C7CA14A5C697D2D5AE4CB9A |
| SHA256: | D253B9ABC09388C08C3AA790170DD331C6F397660DFD9DF5E82E0D4E55262797 |
| SSDEEP: | 49152:tQwFnjXKwrF9aJt/s+LfHQEQwFnjXKwrF9aJt/s+LfHQEQwFnjXKwrF9aJt/s+LH:tYYYYC |
MALICIOUS
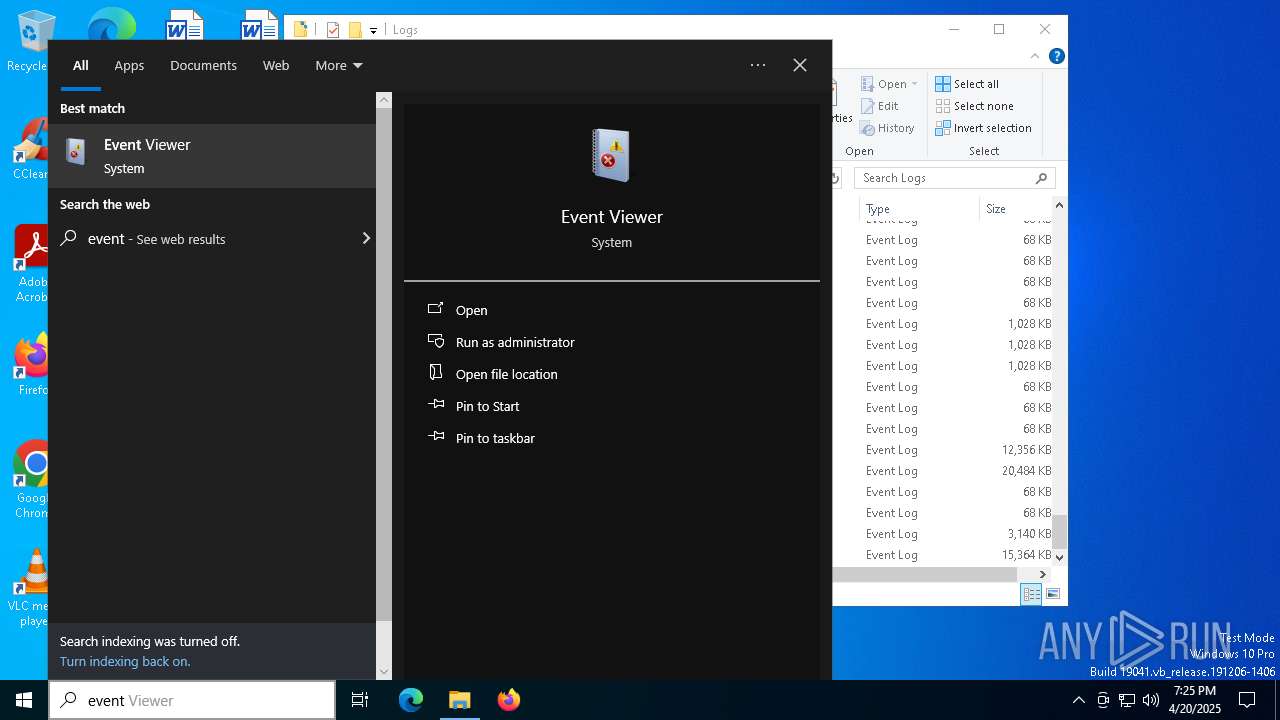
Gets %appdata% folder path (SCRIPT)
- wscript.exe (PID: 5204)
Opens a text file (SCRIPT)
- wscript.exe (PID: 5204)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 5204)
Access Task Scheduler's settings (SCRIPT)
- wscript.exe (PID: 5204)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- wscript.exe (PID: 5204)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 5204)
- wscript.exe (PID: 1616)
- cscript.exe (PID: 5308)
Creates a new scheduled task (SCRIPT)
- wscript.exe (PID: 5204)
Gets context to execute command-line operations (SCRIPT)
- wscript.exe (PID: 5204)
Gets or sets visibliity for the scheduled task (SCRIPT)
- wscript.exe (PID: 5204)
Gets username (SCRIPT)
- wscript.exe (PID: 5204)
SUSPICIOUS
Accesses Scheduled Task settings (SCRIPT)
- wscript.exe (PID: 5204)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 5204)
- cscript.exe (PID: 5308)
Gets context to manipulate triggers of a scheduled task (SCRIPT)
- wscript.exe (PID: 5204)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 5204)
Gets context to manipulate scheduled tasks (SCRIPT)
- wscript.exe (PID: 5204)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 5204)
Gets a folder of registered tasks (SCRIPT)
- wscript.exe (PID: 5204)
Gets scheduled task context (SCRIPT)
- wscript.exe (PID: 5204)
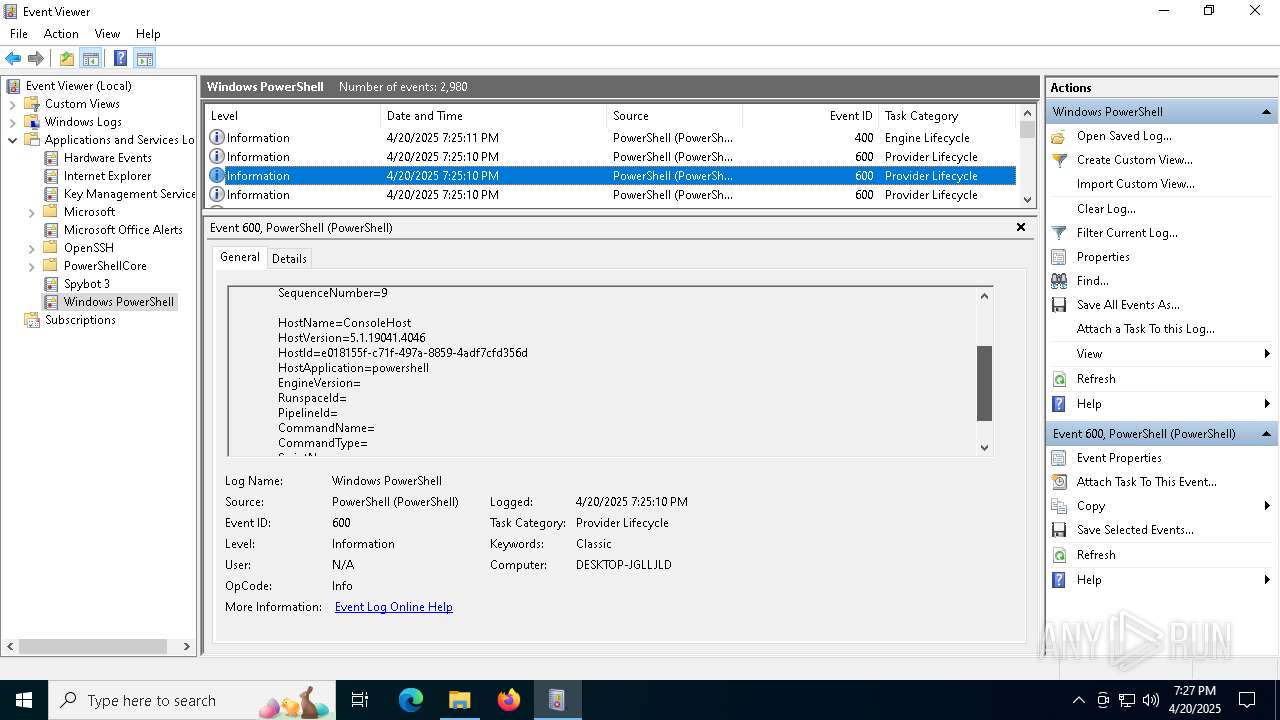
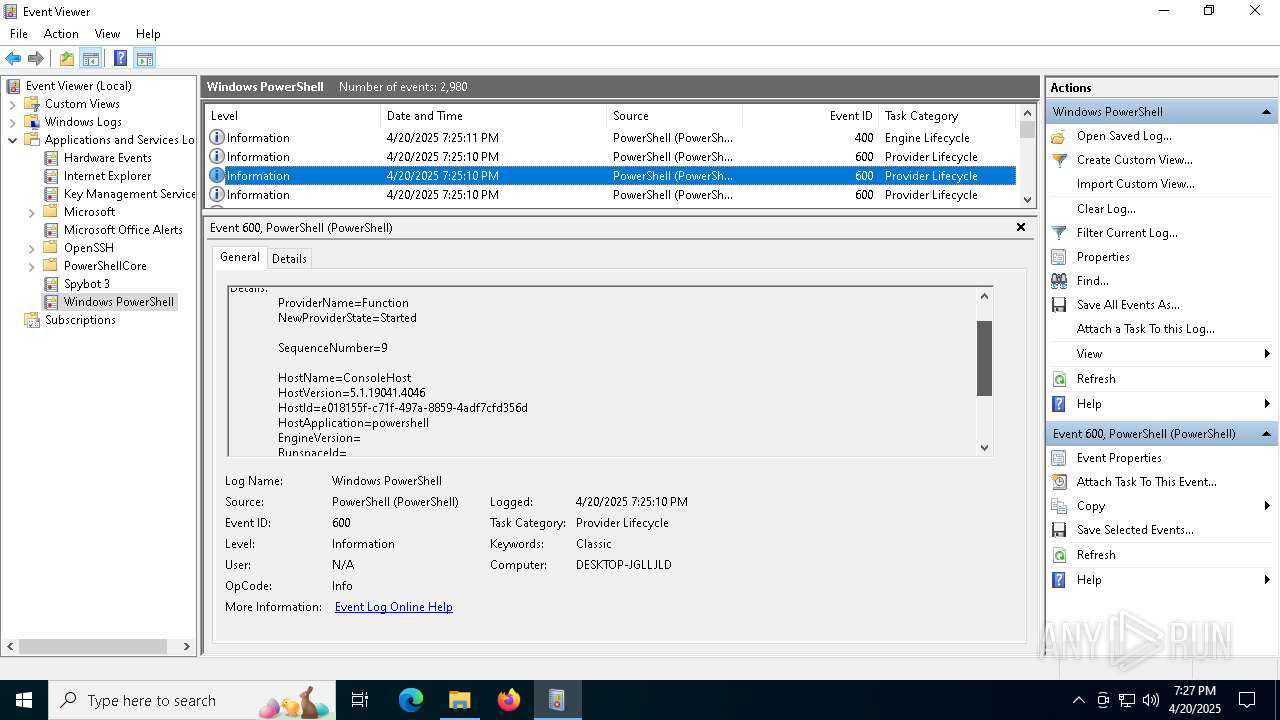
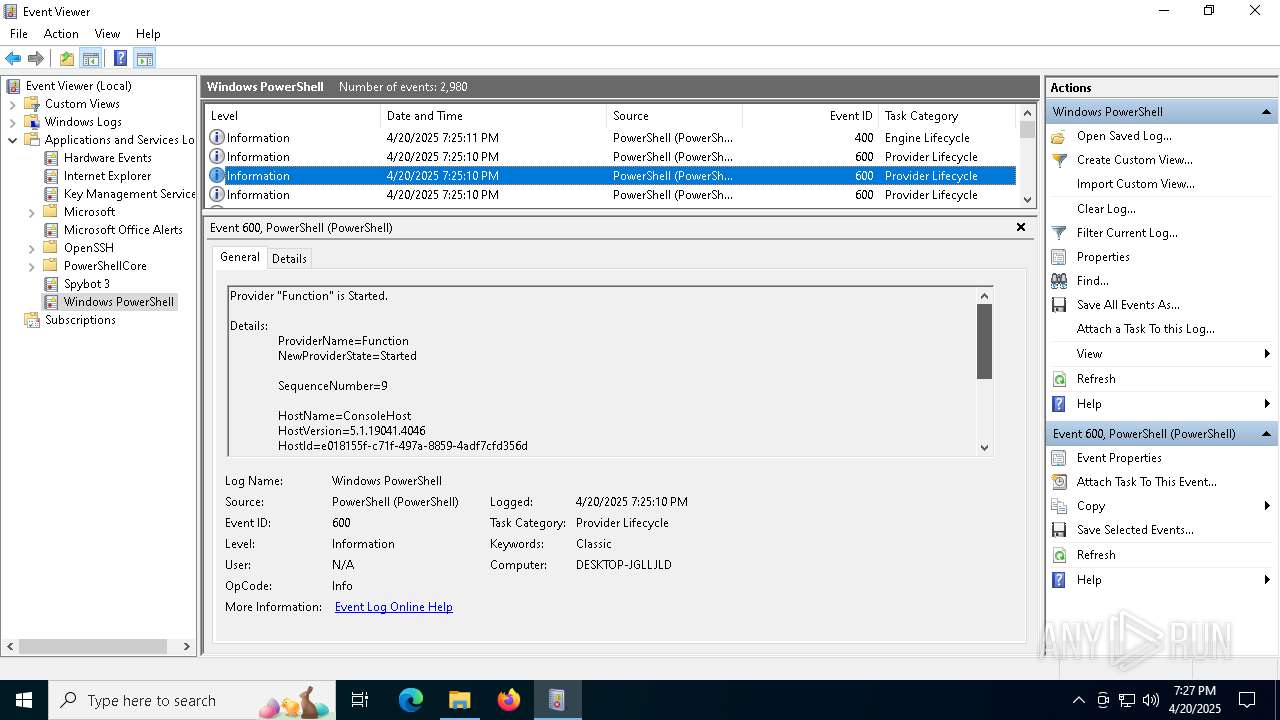
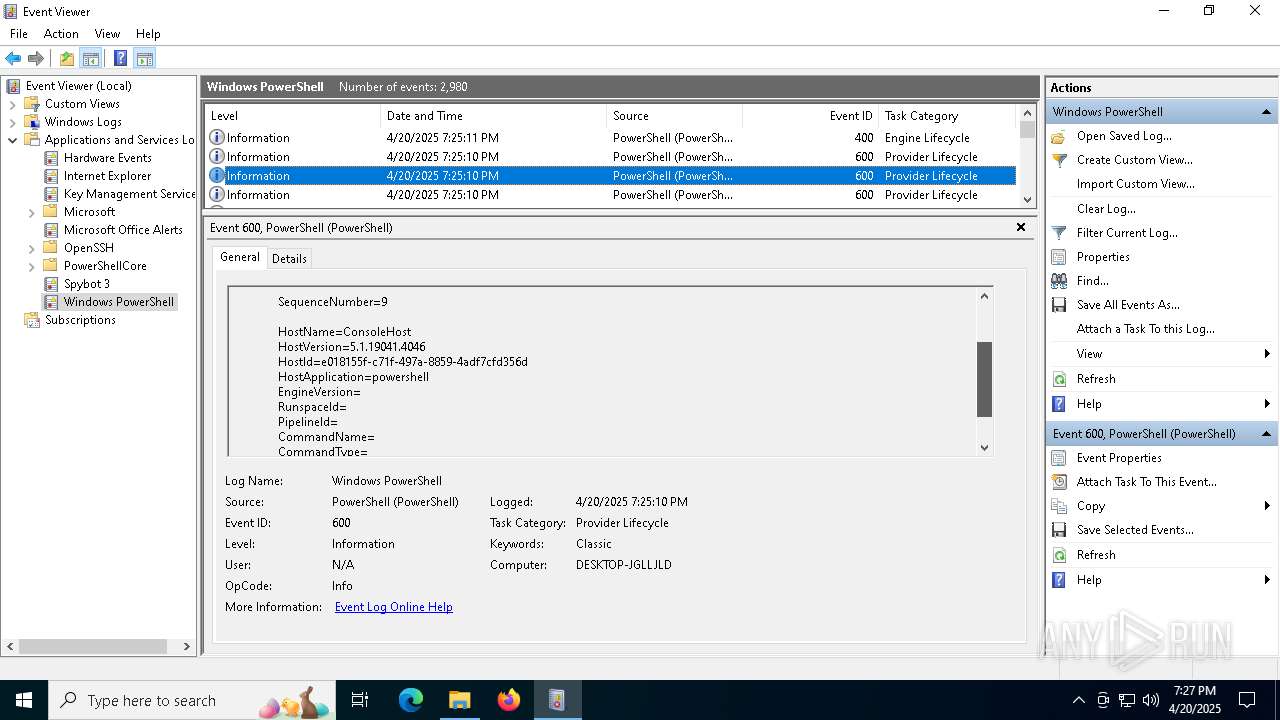
The process executes via Task Scheduler
- wscript.exe (PID: 1616)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 5204)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 1616)
The process executes JS scripts
- wscript.exe (PID: 1616)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1616)
- cscript.exe (PID: 5308)
Reads Internet Explorer settings
- mmc.exe (PID: 5324)
Starts POWERSHELL.EXE for commands execution
- cscript.exe (PID: 5308)
INFO
Self-termination (SCRIPT)
- wscript.exe (PID: 5204)
- wscript.exe (PID: 1616)
- cscript.exe (PID: 5308)
Reads the software policy settings
- slui.exe (PID: 2960)
- powershell.exe (PID: 6584)
- slui.exe (PID: 5008)
Reads security settings of Internet Explorer
- cscript.exe (PID: 5308)
- mmc.exe (PID: 5324)
- powershell.exe (PID: 6584)
Create files in a temporary directory
- powershell.exe (PID: 6584)
Manual execution by a user
- mmc.exe (PID: 5324)
- mmc.exe (PID: 6416)
Creates files in the program directory
- mmc.exe (PID: 5324)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 6584)
Creates files or folders in the user directory
- mmc.exe (PID: 5324)
Checks proxy server information
- slui.exe (PID: 5008)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .s | | | Digital Micrograph Script (100) |
|---|
Total processes
145
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1616 | "C:\WINDOWS\system32\wscript.EXE" CONCEP~1.JS | C:\Windows\System32\wscript.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2960 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5204 | "C:\Windows\System32\WScript.exe" C:\Users\admin\AppData\Local\Temp\reflection_questions_on_the_four_agreements(97717).js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5308 | "C:\Windows\System32\cscript.exe" "CONCEP~1.JS" | C:\Windows\System32\cscript.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
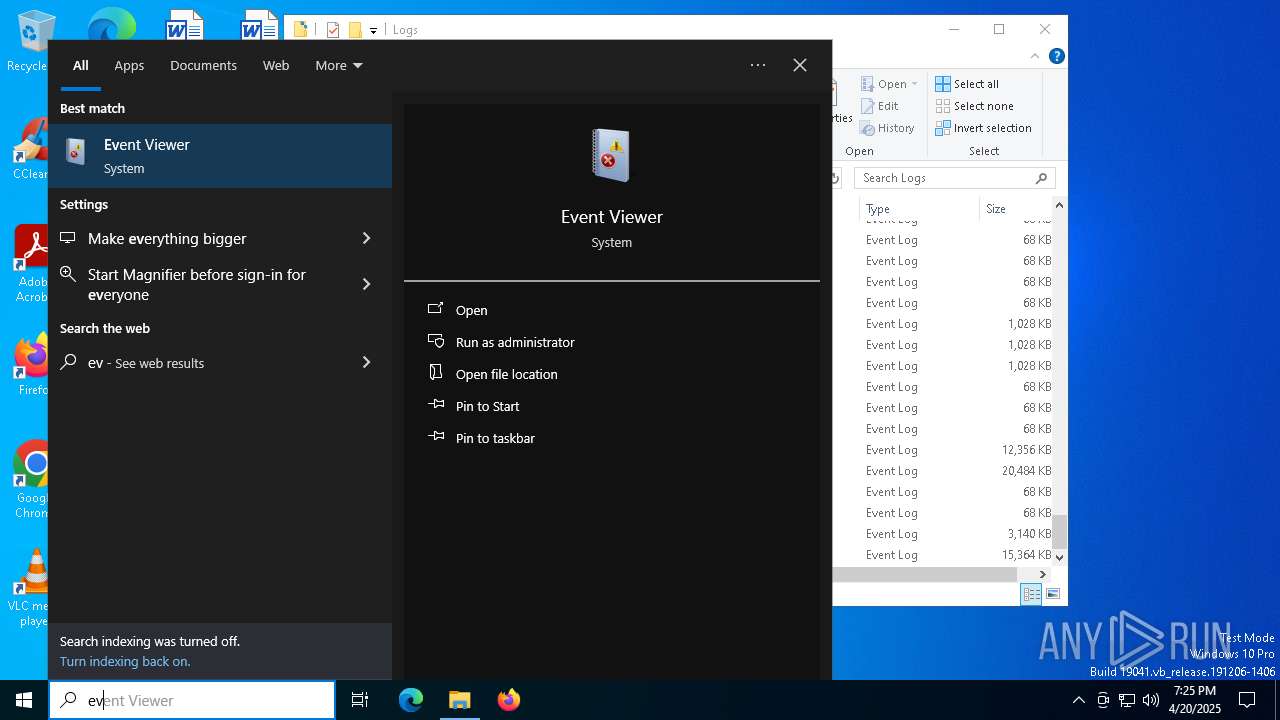
| 5324 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\eventvwr.msc" /s | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5772 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6416 | "C:\WINDOWS\system32\mmc.exe" "C:\WINDOWS\system32\eventvwr.msc" /s | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6584 | powershell | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6808 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 508
Read events
7 502
Write events
6
Delete events
0
Modification events
| (PID) Process: | (5204) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: B1DC110000000000 | |||
| (PID) Process: | (5308) cscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\cscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 6F4A120000000000 | |||
| (PID) Process: | (5324) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{b05566ad-fe9c-4363-be05-7a4cbb7cb510} |
| Operation: | write | Name: | HelpTopic |
Value: C:\WINDOWS\Help\eventviewer.chm | |||
| (PID) Process: | (5324) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{b05566ad-fe9c-4363-be05-7a4cbb7cb510} |
| Operation: | write | Name: | LinkedHelpTopics |
Value: C:\WINDOWS\Help\eventviewer.chm | |||
| (PID) Process: | (5324) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{b05566ae-fe9c-4363-be05-7a4cbb7cb510} |
| Operation: | write | Name: | HelpTopic |
Value: C:\WINDOWS\Help\eventviewer.chm | |||
| (PID) Process: | (5324) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{b05566ae-fe9c-4363-be05-7a4cbb7cb510} |
| Operation: | write | Name: | LinkedHelpTopics |
Value: C:\WINDOWS\Help\eventviewer.chm | |||
Executable files
0
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5204 | wscript.exe | C:\Users\admin\AppData\Roaming\Macromedia\Challenging Environment.dat | — | |
MD5:— | SHA256:— | |||
| 5204 | wscript.exe | C:\Users\admin\AppData\Roaming\Macromedia\Conceptual Planning.js | — | |
MD5:— | SHA256:— | |||
| 6584 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3oytzgkl.2yh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5324 | mmc.exe | C:\Users\admin\AppData\Local\Microsoft\Event Viewer\Settings.Xml | text | |
MD5:D8240AA7E9F240571A7A1D9037EC51DC | SHA256:2CBFEFDBF4D05F6C113C4D4CFC9E06F7217BDD02748D1DE69A6120A72060D99A | |||
| 6584 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x42j5wyz.yjy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
45
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.21.245.142:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.21.245.142:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.21.245.142:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.21.245.142:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.21.245.142:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.21.245.142:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.222.86.92:80 | www.microsoft.com | AKAMAI-AS | NZ | whitelisted |
2104 | svchost.exe | 23.222.86.92:80 | www.microsoft.com | AKAMAI-AS | NZ | whitelisted |
— | — | 23.222.86.92:80 | www.microsoft.com | AKAMAI-AS | NZ | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |