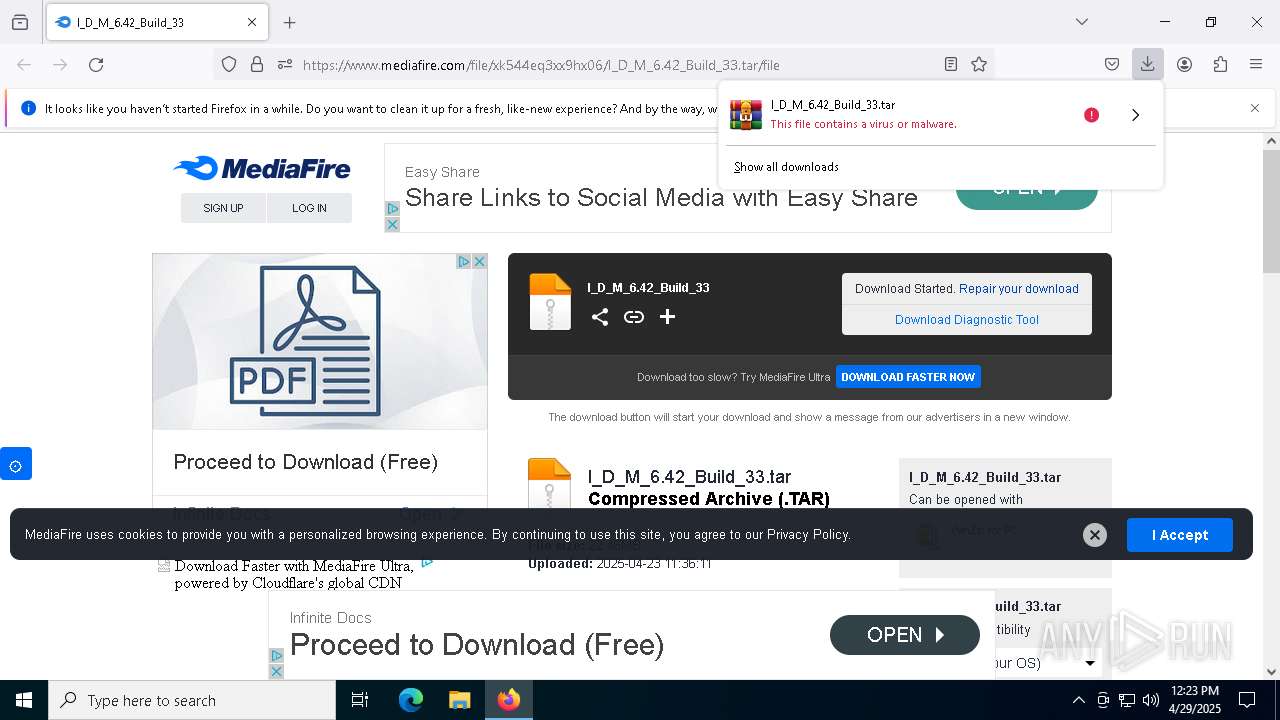
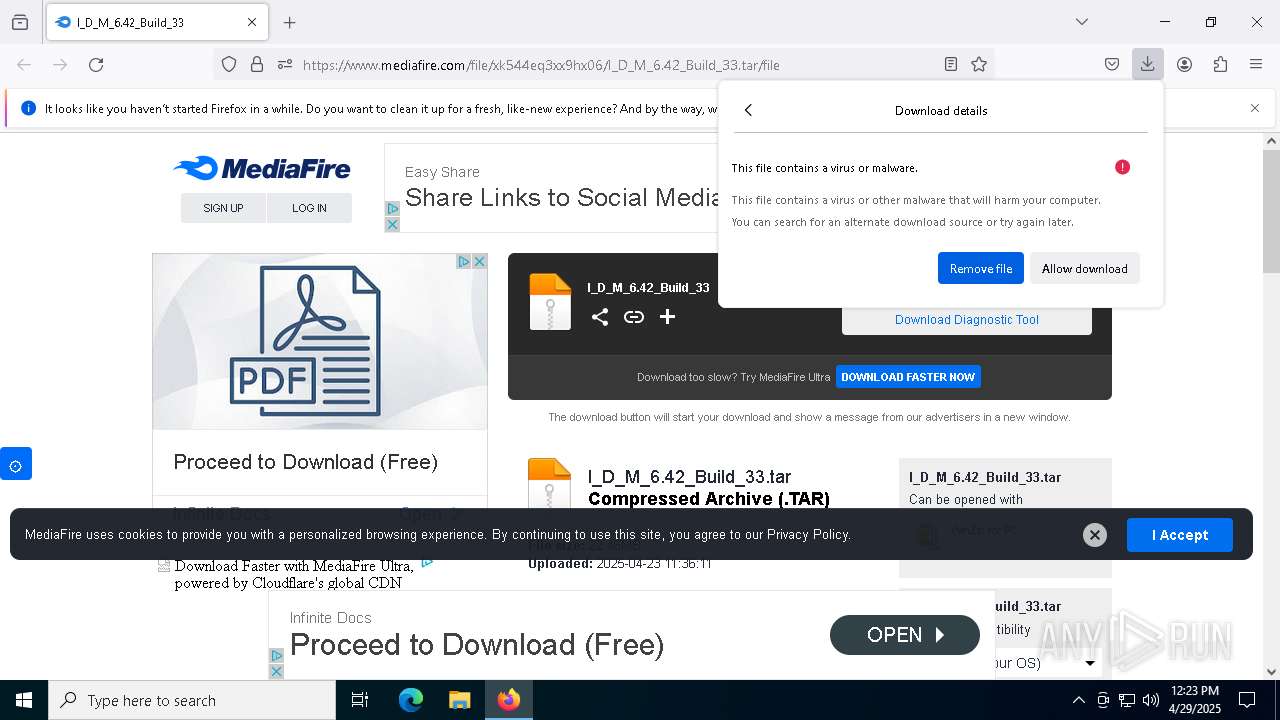
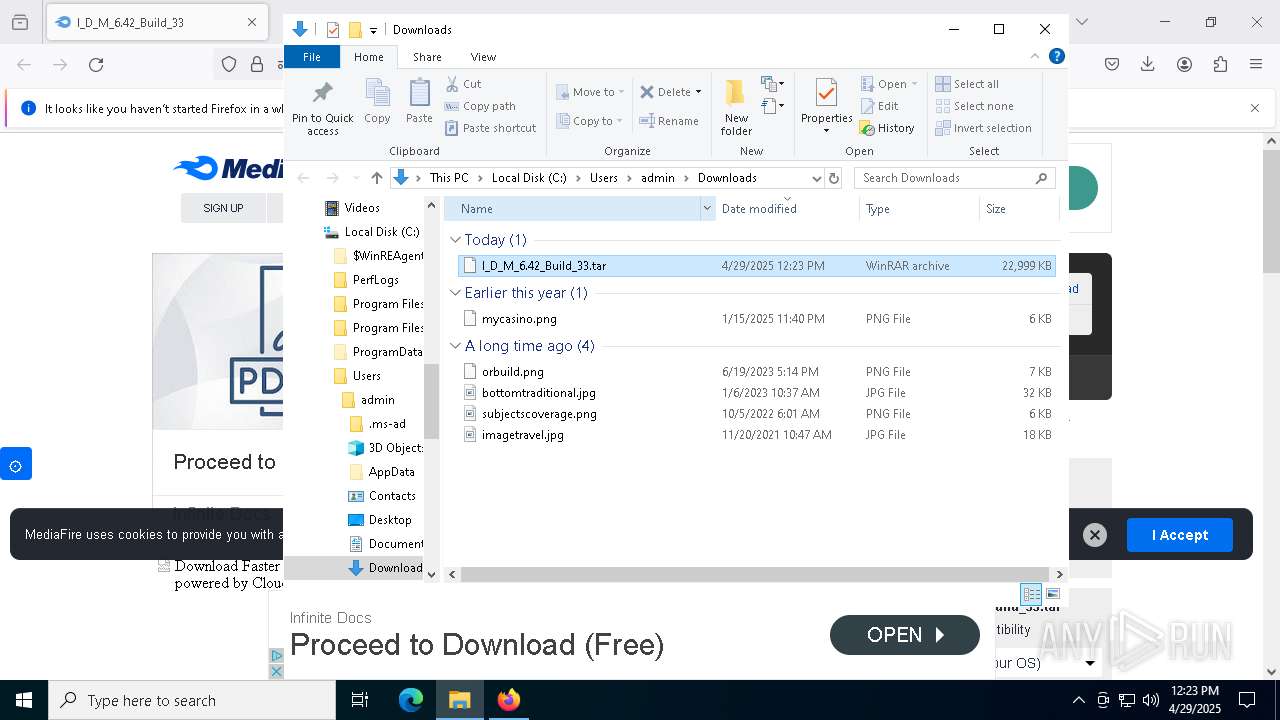
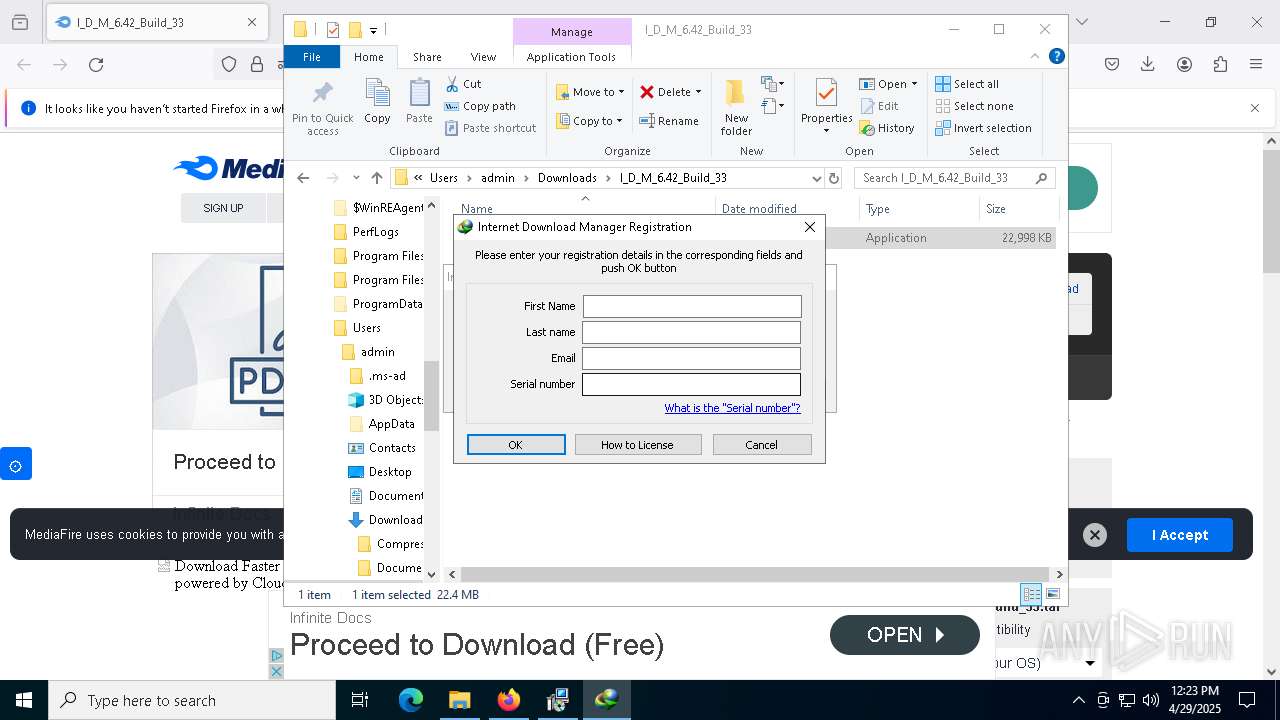
| URL: | https://www.mediafire.com/file/xk544eq3xx9hx06/I_D_M_6.42_Build_33.tar/file |
| Full analysis: | https://app.any.run/tasks/cc28d7ef-e607-4a52-81de-21c45ef65e06 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 29, 2025, 12:22:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9E3D6B8F641E2F72D4E6E306F41ECD2A |
| SHA1: | 892F168F5F9FC1A96C7D7D50E381D8A88877C976 |
| SHA256: | D22C686864CB284482032453D9668FC16E3B301809D5FD5348F2FC04B0E9BD30 |
| SSDEEP: | 3:N8DSLw3eGUoR3AlSuh6nxqQIcREXKDIA:2OLw3eGFNXIgEPA |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- IDM1.tmp (PID: 7332)
- IDMan.exe (PID: 5172)
- Uninstall.exe (PID: 7752)
Starts NET.EXE for service management
- net.exe (PID: 8236)
- Uninstall.exe (PID: 7752)
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 8432)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
Bypass execution policy to execute commands
- powershell.exe (PID: 8288)
- powershell.exe (PID: 8468)
- powershell.exe (PID: 7820)
- powershell.exe (PID: 8536)
- powershell.exe (PID: 9132)
- powershell.exe (PID: 8256)
Run PowerShell with an invisible window
- powershell.exe (PID: 8288)
- powershell.exe (PID: 8536)
- powershell.exe (PID: 7820)
- powershell.exe (PID: 9132)
- powershell.exe (PID: 8256)
PURECRYPTER has been detected (SURICATA)
- RegAsm.exe (PID: 1912)
- MSBuild.exe (PID: 8276)
LUMMA has been detected (SURICATA)
- chrome.exe (PID: 7208)
SUSPICIOUS
Executable content was dropped or overwritten
- Internet Download Manager 6.42 Build 33.exe (PID: 6540)
- IDMan.exe (PID: 5172)
- rundll32.exe (PID: 1128)
- drvinst.exe (PID: 3124)
- VC_redist.x64.exe (PID: 8732)
- powershell.exe (PID: 8468)
- dotNetFx46_Full_setup.exe (PID: 2104)
- Value.exe (PID: 8748)
- VC_redist.x86.exe (PID: 9204)
- RegAsm.exe (PID: 1912)
- gkonkh.exe (PID: 8980)
- CanReuseTransform.exe (PID: 8912)
Process drops legitimate windows executable
- Internet Download Manager 6.42 Build 33.exe (PID: 6540)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6940)
- cmd.exe (PID: 7732)
Starts CMD.EXE for commands execution
- Internet Download Manager 6.42 Build 33.exe (PID: 6540)
- cmd.exe (PID: 8792)
- cmd.exe (PID: 8840)
Starts application with an unusual extension
- S.exe (PID: 7084)
Executing commands from a ".bat" file
- Internet Download Manager 6.42 Build 33.exe (PID: 6540)
- cmd.exe (PID: 8792)
- cmd.exe (PID: 8840)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 7752)
There is functionality for taking screenshot (YARA)
- Internet Download Manager 6.42 Build 33.exe (PID: 6540)
- VC_redist.x64.exe (PID: 8732)
Detects AdvancedInstaller (YARA)
- Internet Download Manager 6.42 Build 33.exe (PID: 6540)
- msiexec.exe (PID: 7516)
- msiexec.exe (PID: 7560)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 1128)
- drvinst.exe (PID: 3124)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 8432)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 8432)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 8792)
- cmd.exe (PID: 8840)
Application launched itself
- cmd.exe (PID: 8792)
- cmd.exe (PID: 8840)
The process executes via Task Scheduler
- powershell.exe (PID: 8288)
- powershell.exe (PID: 7820)
- Value.exe (PID: 8748)
- powershell.exe (PID: 8536)
- CanReuseTransform.exe (PID: 8912)
- Value.exe (PID: 4812)
- powershell.exe (PID: 9132)
- powershell.exe (PID: 8256)
- CanReuseTransform.exe (PID: 6980)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 8432)
The process executes Powershell scripts
- msiexec.exe (PID: 8432)
Connects to unusual port
- RegAsm.exe (PID: 1912)
- MSBuild.exe (PID: 8276)
Contacting a server suspected of hosting an CnC
- RegAsm.exe (PID: 1912)
- MSBuild.exe (PID: 8276)
- chrome.exe (PID: 7208)
INFO
Manual execution by a user
- Internet Download Manager 6.42 Build 33.exe (PID: 6404)
- WinRAR.exe (PID: 5176)
- Internet Download Manager 6.42 Build 33.exe (PID: 6540)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5176)
- msiexec.exe (PID: 7516)
Application launched itself
- firefox.exe (PID: 300)
- firefox.exe (PID: 2140)
- chrome.exe (PID: 7288)
The sample compiled with english language support
- WinRAR.exe (PID: 5176)
- Internet Download Manager 6.42 Build 33.exe (PID: 6540)
- msiexec.exe (PID: 7516)
- IDMan.exe (PID: 5172)
- rundll32.exe (PID: 1128)
- drvinst.exe (PID: 3124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
295
Monitored processes
156
Malicious processes
11
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://www.mediafire.com/file/xk544eq3xx9hx06/I_D_M_6.42_Build_33.tar/file" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --use-angle=swiftshader-webgl --use-gl=angle --mute-audio --user-data-dir="C:\WINDOWS\system32\config\systemprofile\AppData\Local\Google\Chrome\dpjek" --no-appcompat-clear --mojo-platform-channel-handle=5008 --field-trial-handle=2132,i,1066321931116406911,14265469585694630929,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --use-angle=swiftshader-webgl --use-gl=angle --mute-audio --user-data-dir="C:\WINDOWS\system32\config\systemprofile\AppData\Local\Google\Chrome\dpjek" --no-appcompat-clear --mojo-platform-channel-handle=6248 --field-trial-handle=2132,i,1066321931116406911,14265469585694630929,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 840 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --use-angle=swiftshader-webgl --use-gl=angle --mute-audio --user-data-dir="C:\WINDOWS\system32\config\systemprofile\AppData\Local\Google\Chrome\dpjek" --no-appcompat-clear --mojo-platform-channel-handle=4568 --field-trial-handle=2132,i,1066321931116406911,14265469585694630929,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 976 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\IDMShellExt64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | IDMan.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\WINDOWS\Sysnative\RUNDLL32.EXE" SETUPAPI.DLL,InstallHinfSection DefaultInstall 128 C:\Program Files (x86)\Internet Download Manager\idmwfp.inf | C:\Windows\System32\rundll32.exe | Uninstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --user-data-dir="C:\WINDOWS\system32\config\systemprofile\AppData\Local\Google\Chrome\dpjek" --no-appcompat-clear --autoplay-policy=no-user-gesture-required --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=5864 --field-trial-handle=2132,i,1066321931116406911,14265469585694630929,262144 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1912 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\RegAsm.exe | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\RegAsm.exe | Value.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft .NET Assembly Registration Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6256 -childID 10 -isForBrowser -prefsHandle 6316 -prefMapHandle 6312 -prefsLen 31324 -prefMapSize 244583 -jsInitHandle 1400 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {66009f9a-cf61-4bc3-8d07-a7be4b62b60a} 2140 "\\.\pipe\gecko-crash-server-pipe.2140" 2458da8e4d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
86 325
Read events
85 547
Write events
606
Delete events
172
Modification events
| (PID) Process: | (2140) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (5176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (5176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (5176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
| (PID) Process: | (5176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 11 |
Value: | |||
| (PID) Process: | (5176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 10 |
Value: | |||
| (PID) Process: | (5176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 9 |
Value: | |||
| (PID) Process: | (5176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 8 |
Value: | |||
| (PID) Process: | (5176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 7 |
Value: | |||
Executable files
51
Suspicious files
740
Text files
214
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\protections.sqlite-journal | binary | |
MD5:515D00D279A9FD5445EB73CCB9FC904A | SHA256:4BBB64C349872AB5CC62BC6B4A7237FD5977F23585F45483A220BECDA4EBCA27 | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db-journal | binary | |
MD5:6688FF171F94CD3F88AE7D6B5583C364 | SHA256:758DA8A64B7C8229D7B1C7533D0F65B3F51DFDACF84C5183E1C3D3D1B98F7A64 | |||
| 2140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db | binary | |
MD5:9023A722C98FB1109266C0D4A475D7A6 | SHA256:7F95DA92213C0B6856460A8E728BECB91A17F9491CCC5FF7676DDC4A62AE3DEC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
82
TCP/UDP connections
331
DNS requests
387
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2140 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2140 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2140 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2140 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
2140 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
2140 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
2140 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://o.pki.goog/s/we1/sY8 | unknown | — | — | whitelisted |
2140 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2140 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
2140 | firefox.exe | 104.17.151.117:443 | www.mediafire.com | CLOUDFLARENET | — | whitelisted |
2140 | firefox.exe | 142.250.186.106:443 | safebrowsing.googleapis.com | — | — | whitelisted |
2140 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
www.mediafire.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
prod.content-signature-chains.prod.webservices.mozgcp.net |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2196 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2196 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2196 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
8468 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.crabdance .com Domain |
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\WINDOWS\system32\config\systemprofile\AppData\Local directory exists )
|