| File name: | 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry |
| Full analysis: | https://app.any.run/tasks/352bc9f8-6f91-4946-9ca2-290dedb1190f |
| Verdict: | Malicious activity |
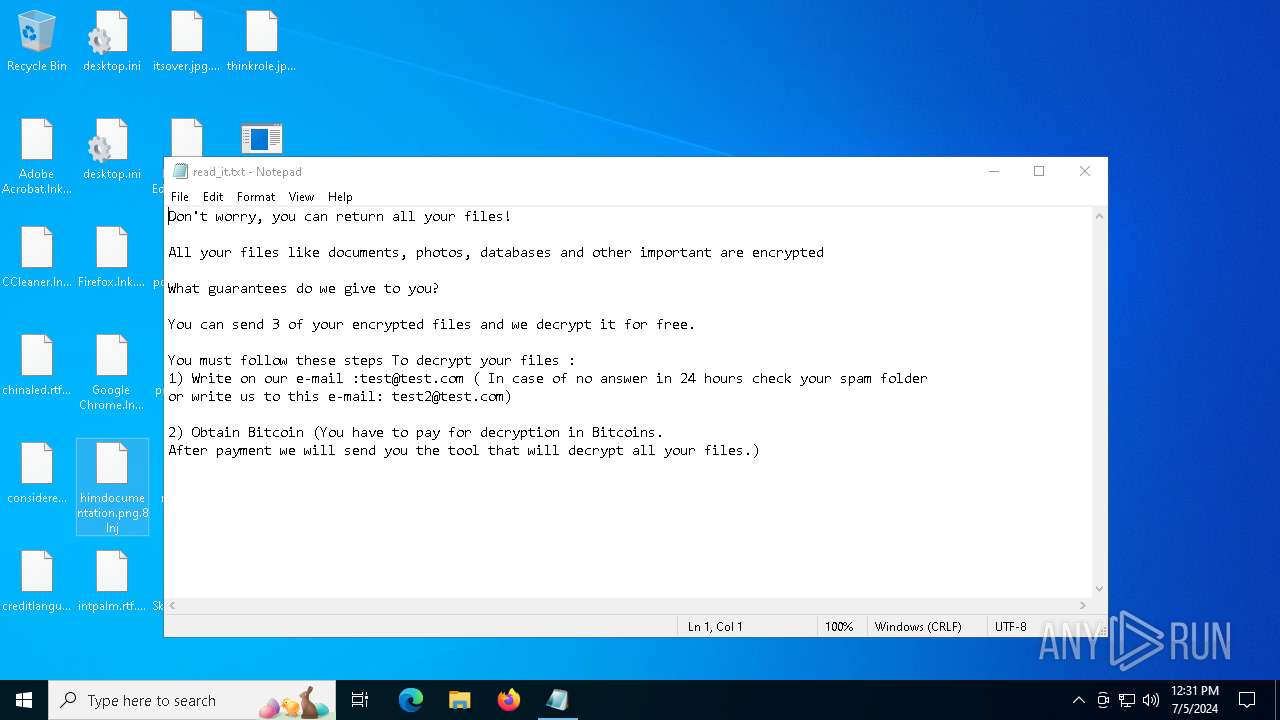
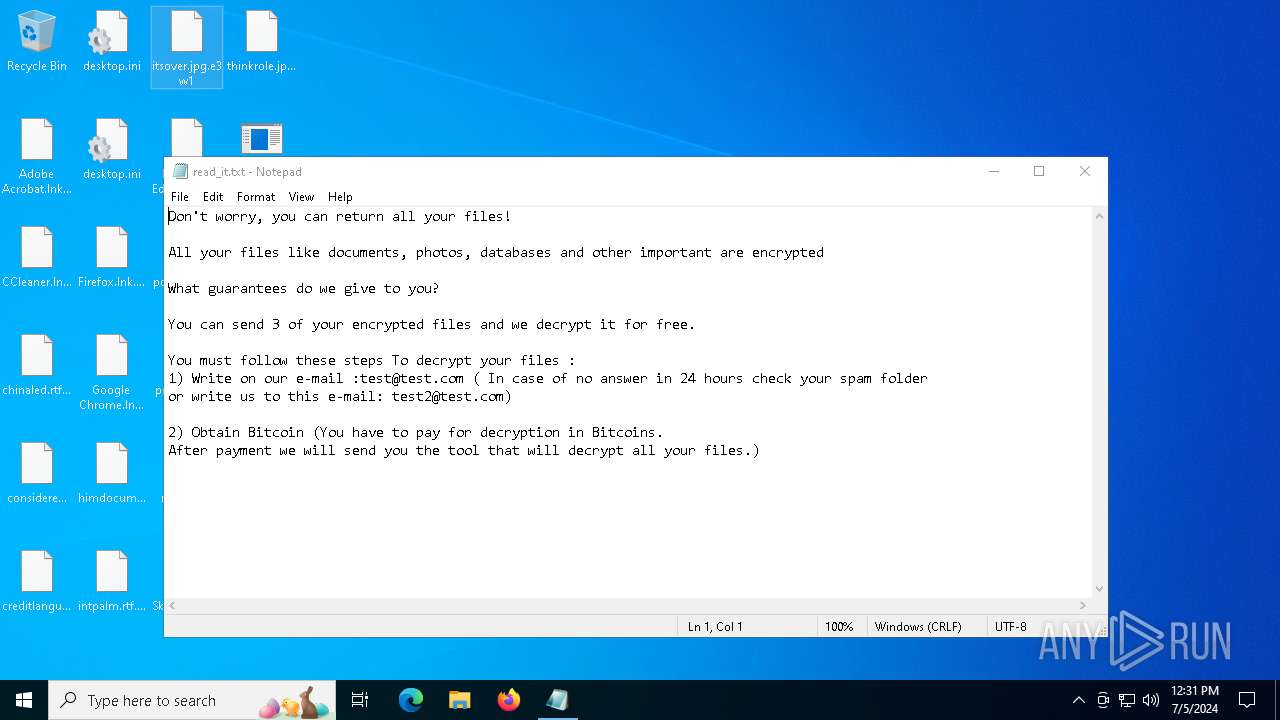
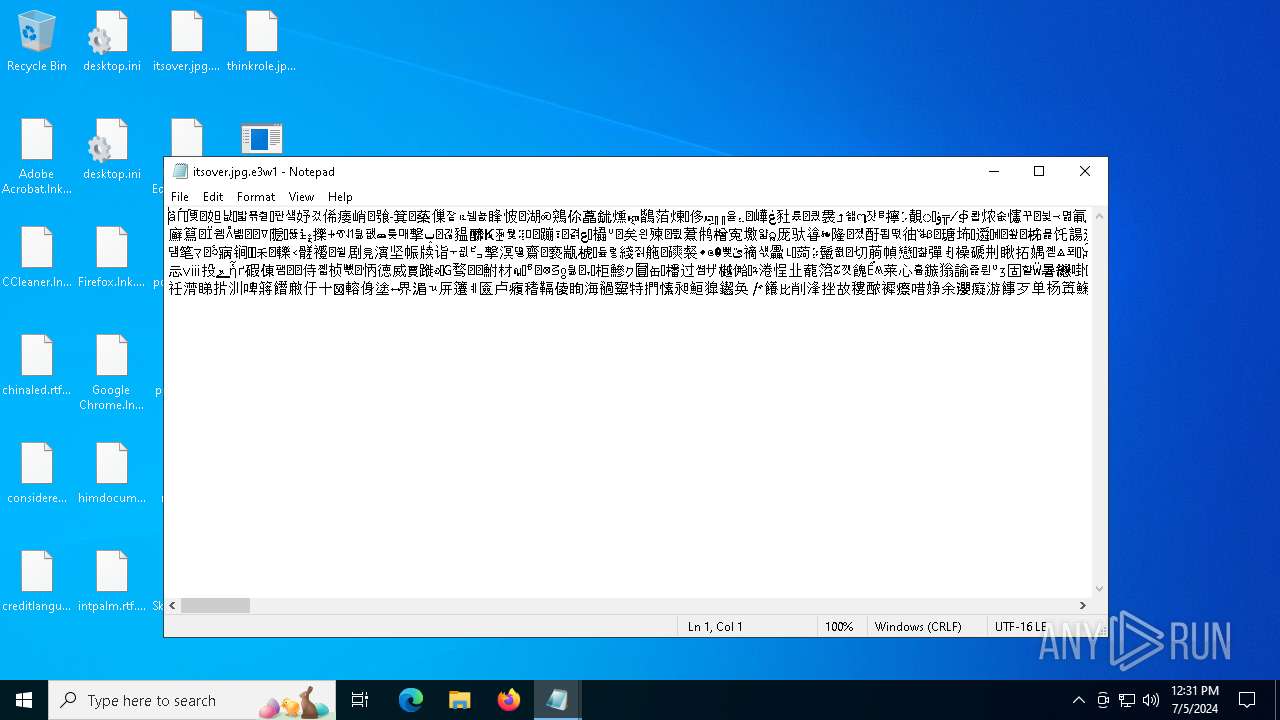
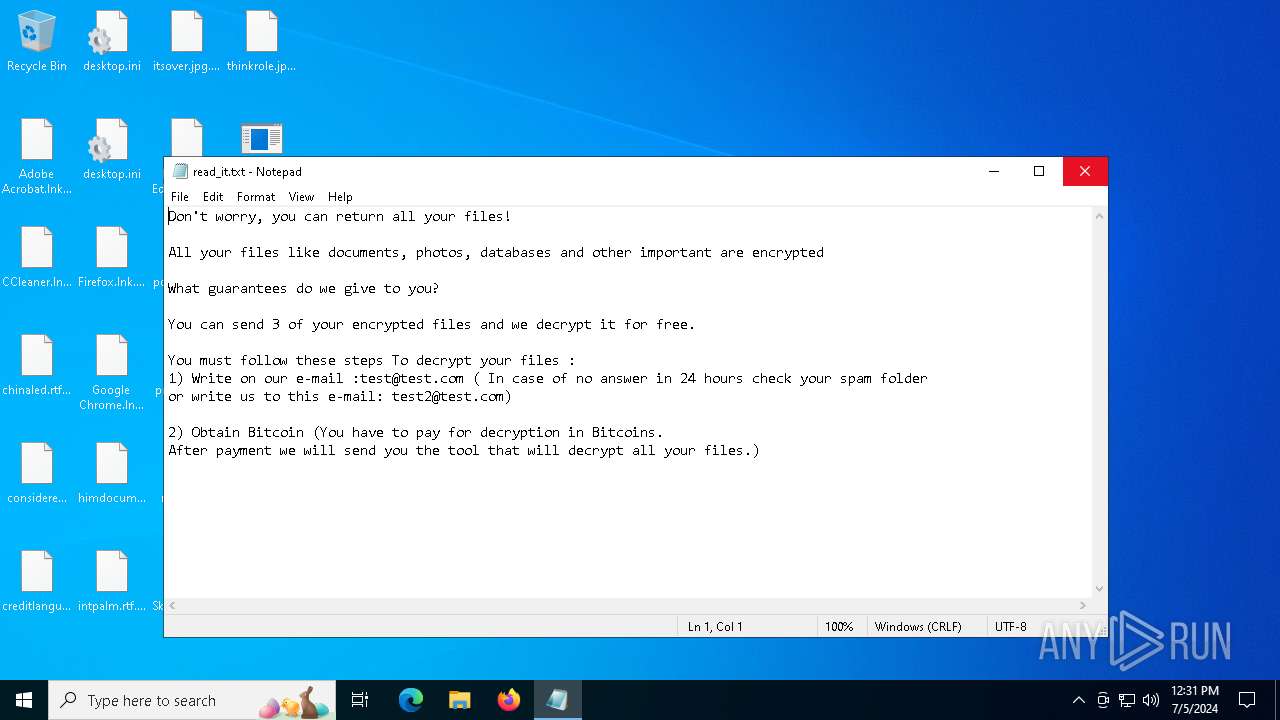
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | July 05, 2024, 12:29:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | F6171E8867374374BF04E1AE0BD5E24C |
| SHA1: | 593CE46F24067CBA4096228C199AD2CC2BB2B50E |
| SHA256: | D214F322652F890ECEE73ED143BE316B4EDD8D6BC13805106C7ECBA0C04AC35E |
| SSDEEP: | 384:/nixKotc/2fhl6VbyKdRkEH5sufPrQUB12lVOy5o91G4k1M3PNB322jp:/WLa2fhRKd/5sufPcUB4ho9s4k1M/DR |
MALICIOUS
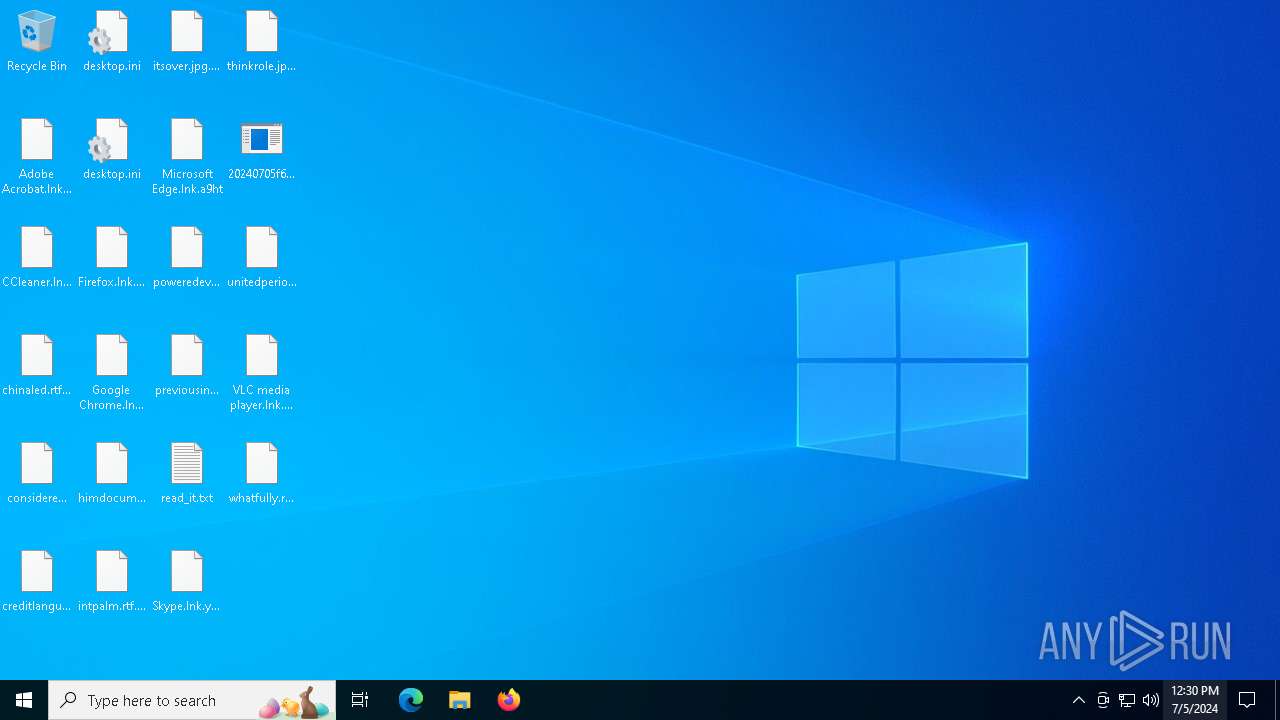
Drops the executable file immediately after the start
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
Changes the autorun value in the registry
- svchost.exe (PID: 5872)
Deletes shadow copies
- cmd.exe (PID: 4600)
- cmd.exe (PID: 2476)
Modifies files in the Chrome extension folder
- svchost.exe (PID: 5872)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 2404)
CHAOS has been detected (YARA)
- svchost.exe (PID: 5872)
Steals credentials from Web Browsers
- svchost.exe (PID: 5872)
Create files in the Startup directory
- svchost.exe (PID: 5872)
Actions looks like stealing of personal data
- svchost.exe (PID: 5872)
SUSPICIOUS
Reads security settings of Internet Explorer
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
- svchost.exe (PID: 5872)
Reads the date of Windows installation
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
- svchost.exe (PID: 5872)
The process creates files with name similar to system file names
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
Executable content was dropped or overwritten
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
Starts itself from another location
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 5872)
Executes as Windows Service
- vds.exe (PID: 2268)
- wbengine.exe (PID: 4048)
- VSSVC.exe (PID: 2784)
Found regular expressions for crypto-addresses (YARA)
- svchost.exe (PID: 5872)
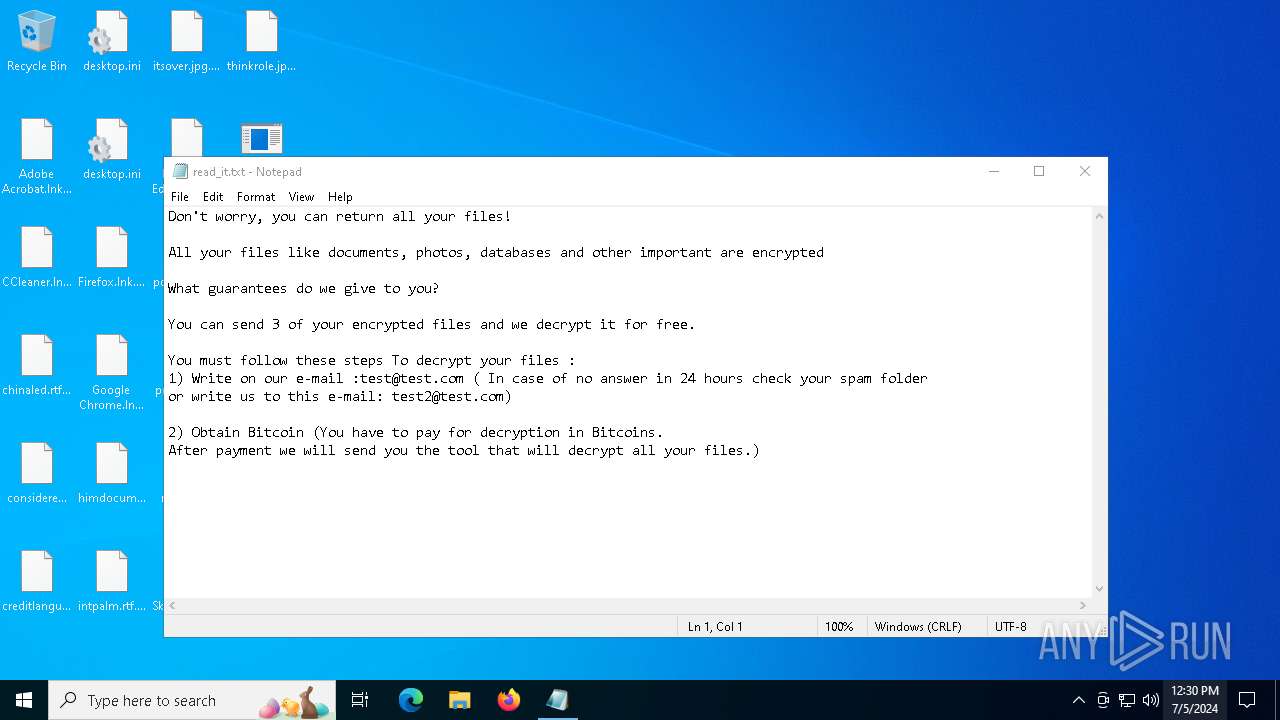
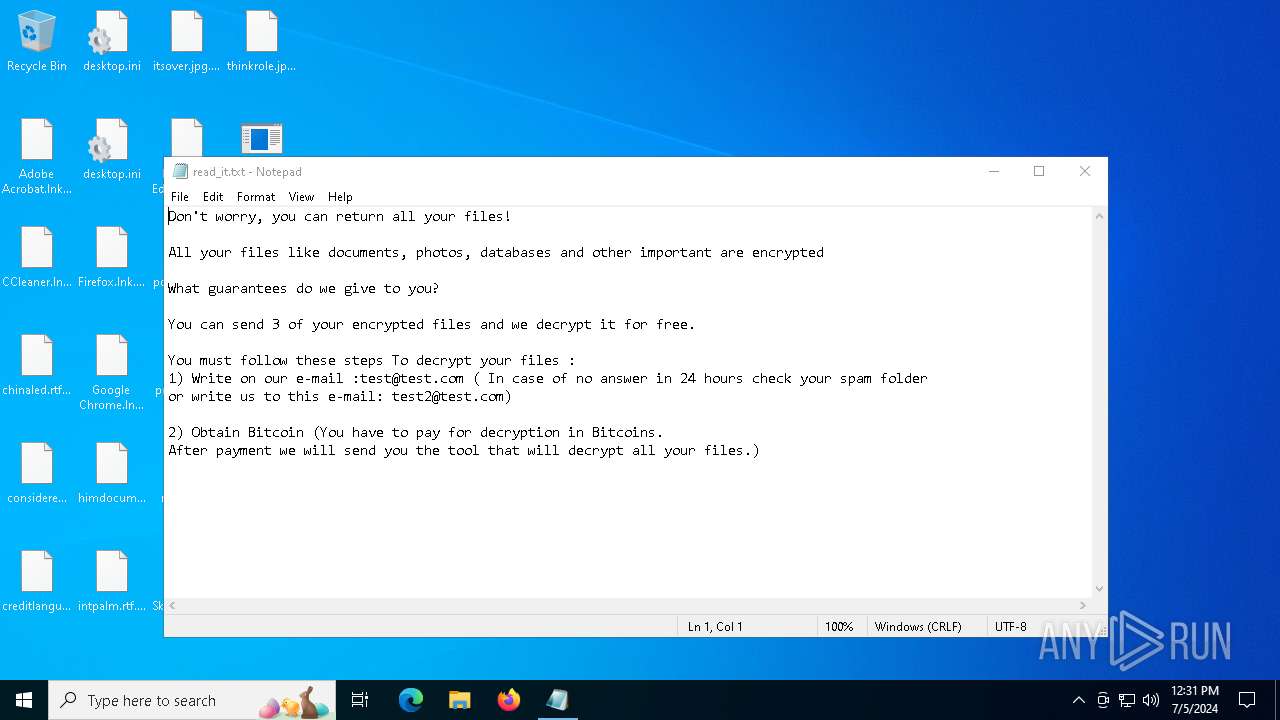
Start notepad (likely ransomware note)
- svchost.exe (PID: 5872)
INFO
Checks supported languages
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
- svchost.exe (PID: 5872)
Reads the computer name
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
- svchost.exe (PID: 5872)
Reads the machine GUID from the registry
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
- svchost.exe (PID: 5872)
Creates files or folders in the user directory
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
- svchost.exe (PID: 5872)
Process checks computer location settings
- 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe (PID: 3224)
- svchost.exe (PID: 5872)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 240)
- OpenWith.exe (PID: 2716)
- notepad.exe (PID: 4544)
- notepad.exe (PID: 2360)
Creates files in the program directory
- svchost.exe (PID: 5872)
Reads Microsoft Office registry keys
- svchost.exe (PID: 5872)
- OpenWith.exe (PID: 2716)
Create files in a temporary directory
- svchost.exe (PID: 5872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:04 13:47:16+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 25600 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x82ee |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | yhtg.exe |
| LegalCopyright: | |
| OriginalFileName: | yhtg.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
144
Monitored processes
20
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | wmic shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 428 | C:\WINDOWS\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1192 | bcdedit /set {default} recoveryenabled no | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2120 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | C:\WINDOWS\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2360 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\itsover.jpg.e3w1 | C:\Windows\System32\notepad.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2404 | "C:\Windows\System32\cmd.exe" /C bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2476 | "C:\Windows\System32\cmd.exe" /C wbadmin delete catalog -quiet | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 923
Read events
13 830
Write events
73
Delete events
20
Modification events
| (PID) Process: | (3224) 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3224) 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3224) 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3224) 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5872) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UpdateTask |
Value: C:\Users\admin\AppData\Roaming\svchost.exe | |||
| (PID) Process: | (5872) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5872) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5872) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5872) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2888) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
554
Text files
865
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3224 | 20240705f6171e8867374374bf04e1ae0bd5e24cdestroyerwannacry.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:F6171E8867374374BF04E1AE0BD5E24C | SHA256:D214F322652F890ECEE73ED143BE316B4EDD8D6BC13805106C7ECBA0C04AC35E | |||
| 5872 | svchost.exe | C:\$WinREAgent\RollbackInfo.ini.ofmt | binary | |
MD5:5B75861F4EF910ED22BF6A178794EA41 | SHA256:F40E0EB9E6E77988301181CF4A3421351D9449B380C7217E2F2E6F11F61CDE62 | |||
| 5872 | svchost.exe | C:\$WinREAgent\Backup\location.txt | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
| 5872 | svchost.exe | C:\$WinREAgent\Backup\ReAgent.xml.i6gp | binary | |
MD5:9F503135CE00A01BADF3771584CF481F | SHA256:8D0ABDBCC2AFB5799E3A9DEC723865F681334892BA657EA60E051AE691830656 | |||
| 5872 | svchost.exe | C:\$WinREAgent\Backup\location.txt.n0tx | binary | |
MD5:2E74241E7C5703343D4C37AE4981DF65 | SHA256:277867B4DD2D416488455E94F56BDA341E6BBDAF1DF510E4DF197DE40DD3D0F4 | |||
| 5872 | svchost.exe | C:\Recovery\ReAgentOld.xml | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
| 5872 | svchost.exe | C:\Recovery\ReAgentOld.xml.d5gk | binary | |
MD5:88343FD13458F35EF88DF18B94D60585 | SHA256:77F40DD58467973969FCE86982D3BBBC78267099DD18672B40D32C2718790027 | |||
| 5872 | svchost.exe | C:\found.000\dir0001.chk\WmiApRpl.ini.v0oo | binary | |
MD5:640D227E5DDC8A280B5874456E562B74 | SHA256:27573300C220A855E6401BBA2CCDB3918D8D269CFF0C1CE056907CF7ED1A9A23 | |||
| 5872 | svchost.exe | C:\$WinREAgent\RollbackInfo.ini | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
| 5872 | svchost.exe | C:\found.000\dir0001.chk\WmiApRpl.ini | binary | |
MD5:D1457B72C3FB323A2671125AEF3EAB5D | SHA256:8A8DE823D5ED3E12746A62EF169BCF372BE0CA44F0A1236ABC35DF05D96928E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
27
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2336 | RUXIMICS.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2336 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 104.126.37.153:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=regedi&setlang=en-US&cc=US&nohs=1&qfm=1&cp=6&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=46856f19730442d7bfc8a588e4a577aa | unknown | binary | 3.97 Kb | unknown |
— | — | GET | 200 | 104.126.37.147:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=regedit&setlang=en-US&cc=US&nohs=1&qfm=1&cp=7&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=0c07db2ed43b472383863f523ee03420 | unknown | binary | 4.78 Kb | unknown |
— | — | GET | 200 | 104.126.37.153:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=rege&setlang=en-US&cc=US&nohs=1&qfm=1&cp=4&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=9e5ca3b8609c45288674b78f53cdefa2 | unknown | binary | 5.06 Kb | unknown |
— | — | GET | 200 | 104.126.37.153:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=re&setlang=en-US&cc=US&nohs=1&qfm=1&cp=2&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=886f7dfaf8a943d7ac515843550c84b9 | unknown | binary | 6.56 Kb | unknown |
— | — | GET | 200 | 104.126.37.152:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | s | 21.3 Kb | unknown |
— | — | GET | 200 | 104.126.37.130:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=reged&setlang=en-US&cc=US&nohs=1&qfm=1&cp=5&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=d9fc350f72484720963919f484813311 | unknown | binary | 4.71 Kb | unknown |
— | — | GET | 200 | 104.126.37.131:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=r&setlang=en-US&cc=US&nohs=1&qfm=1&cp=1&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=8217ecd434a24e319c68e41132cd851d | unknown | binary | 15.4 Kb | unknown |
— | — | GET | 200 | 104.126.37.137:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Suggestions?qry=reg&setlang=en-US&cc=US&nohs=1&qfm=1&cp=3&cvid=917f2af1fe65416cbd620a4b992edbf0&ig=65838b980f4f409493f636a698a90235 | unknown | binary | 5.10 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4448 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2336 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4452 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4448 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | RUXIMICS.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2336 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4452 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
wbadmin.exe | Invalid parameter passed to C runtime function.
|