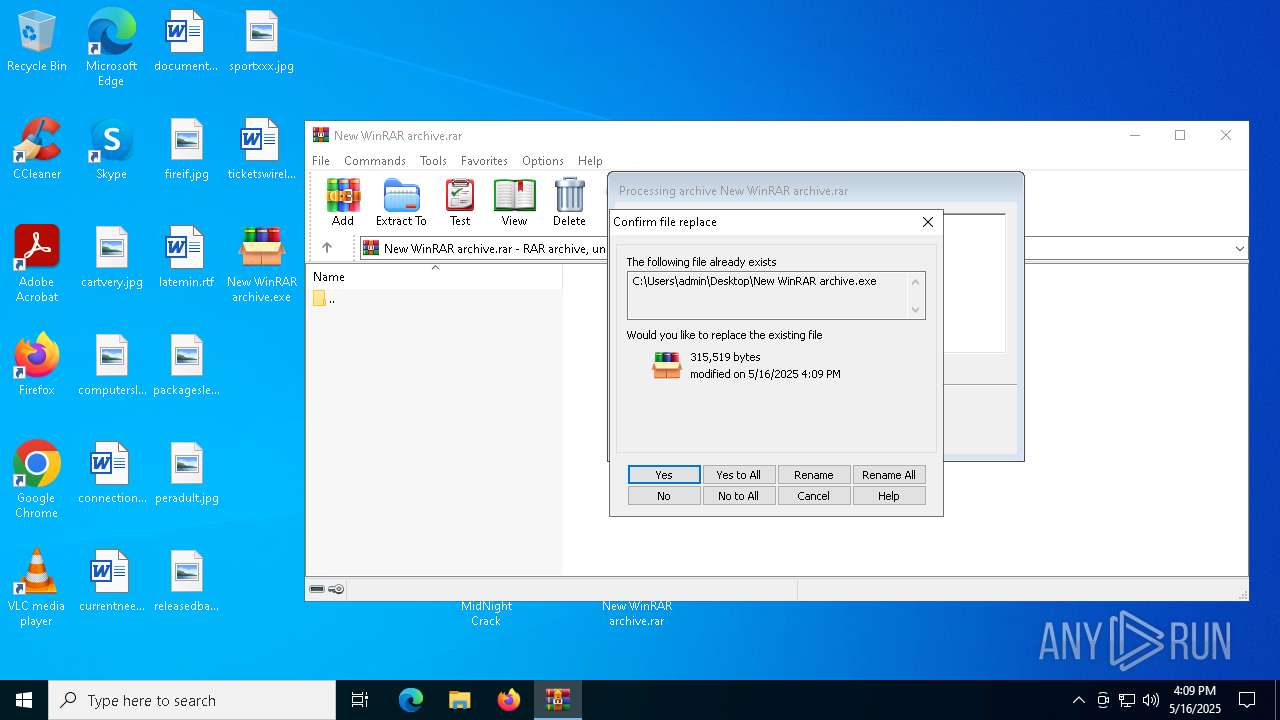
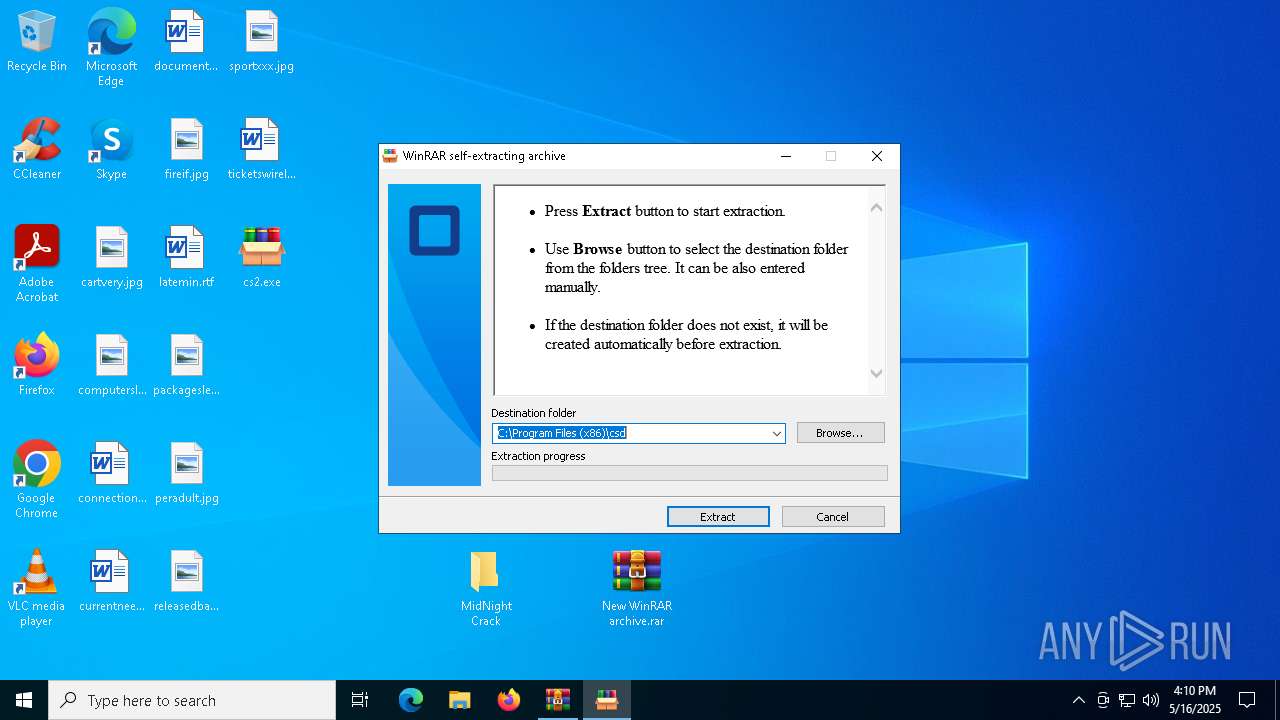
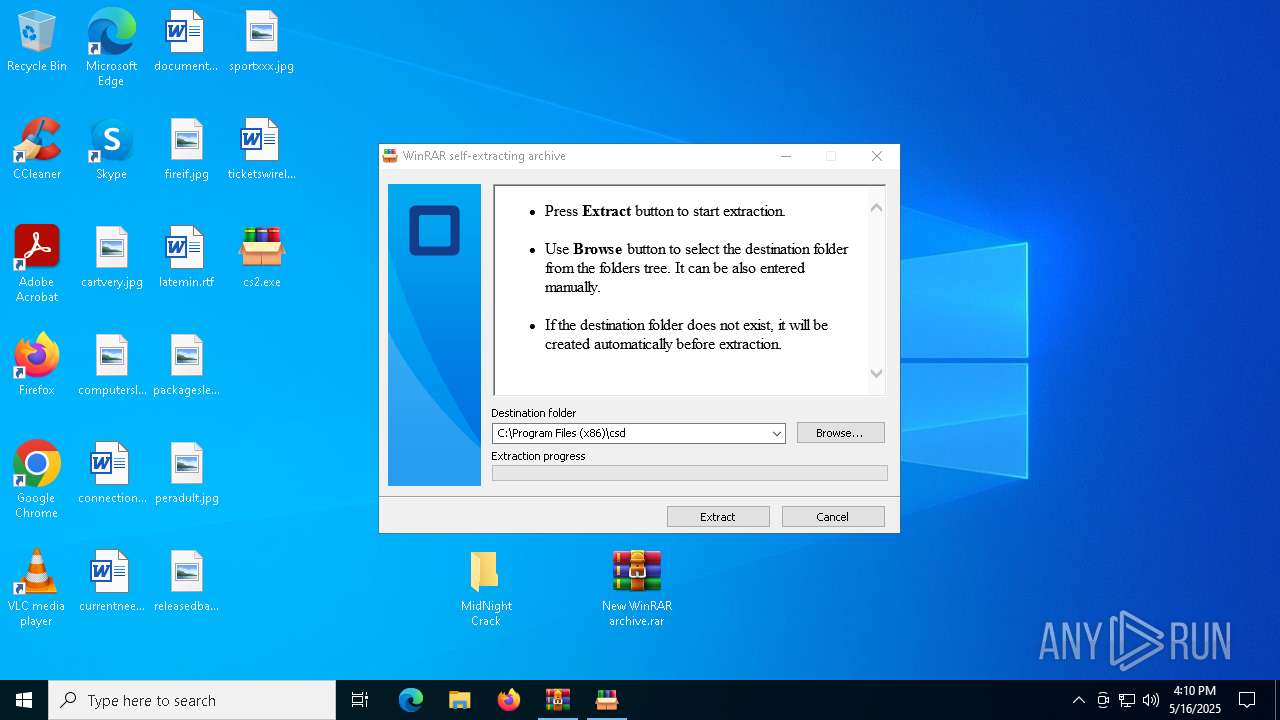
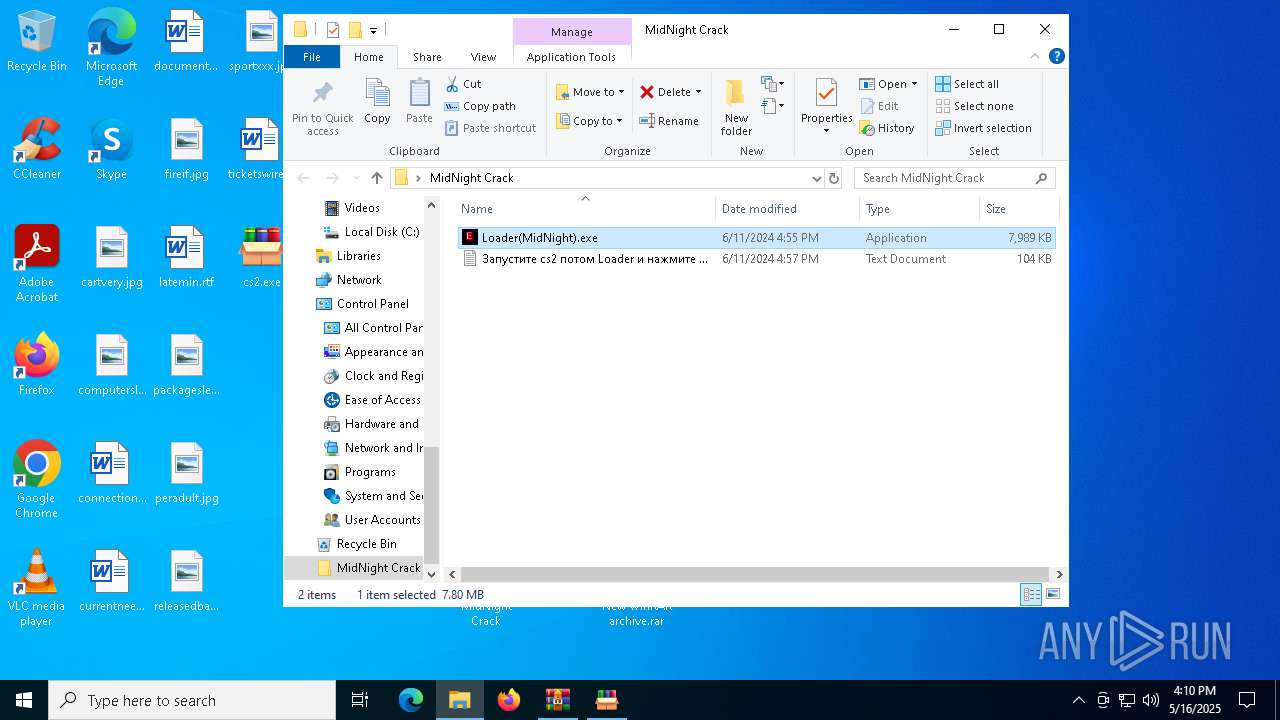
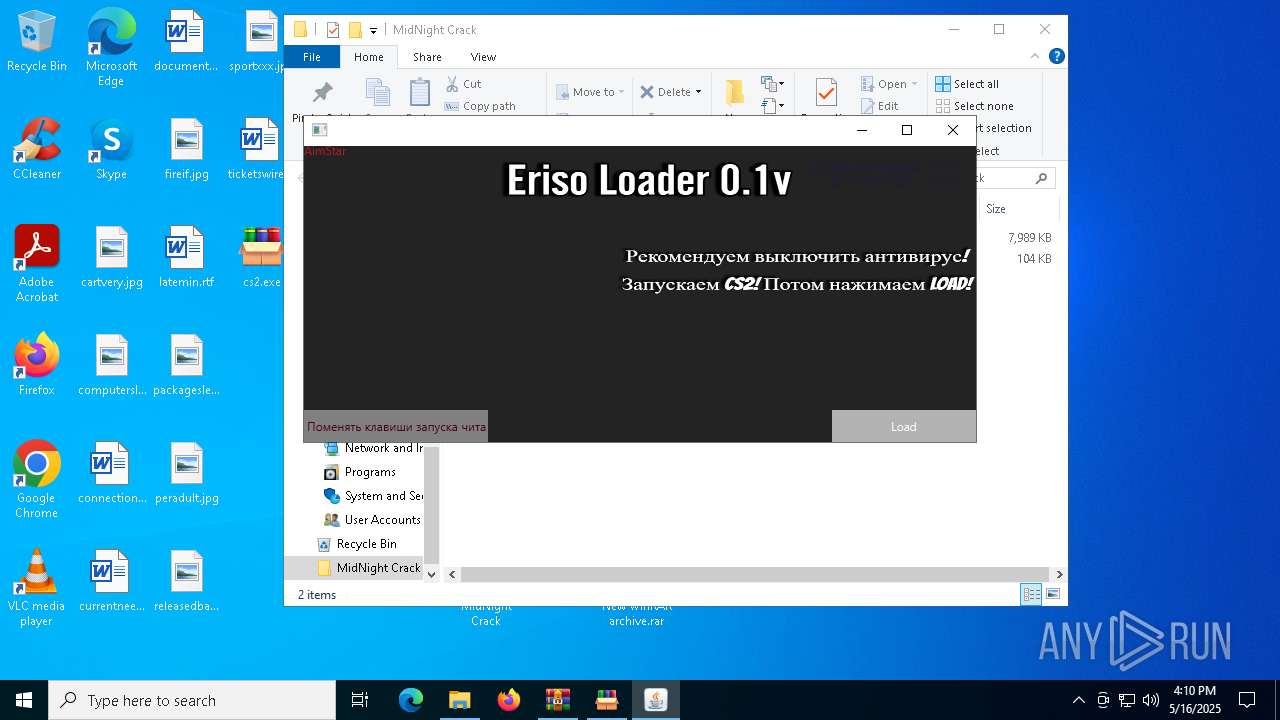
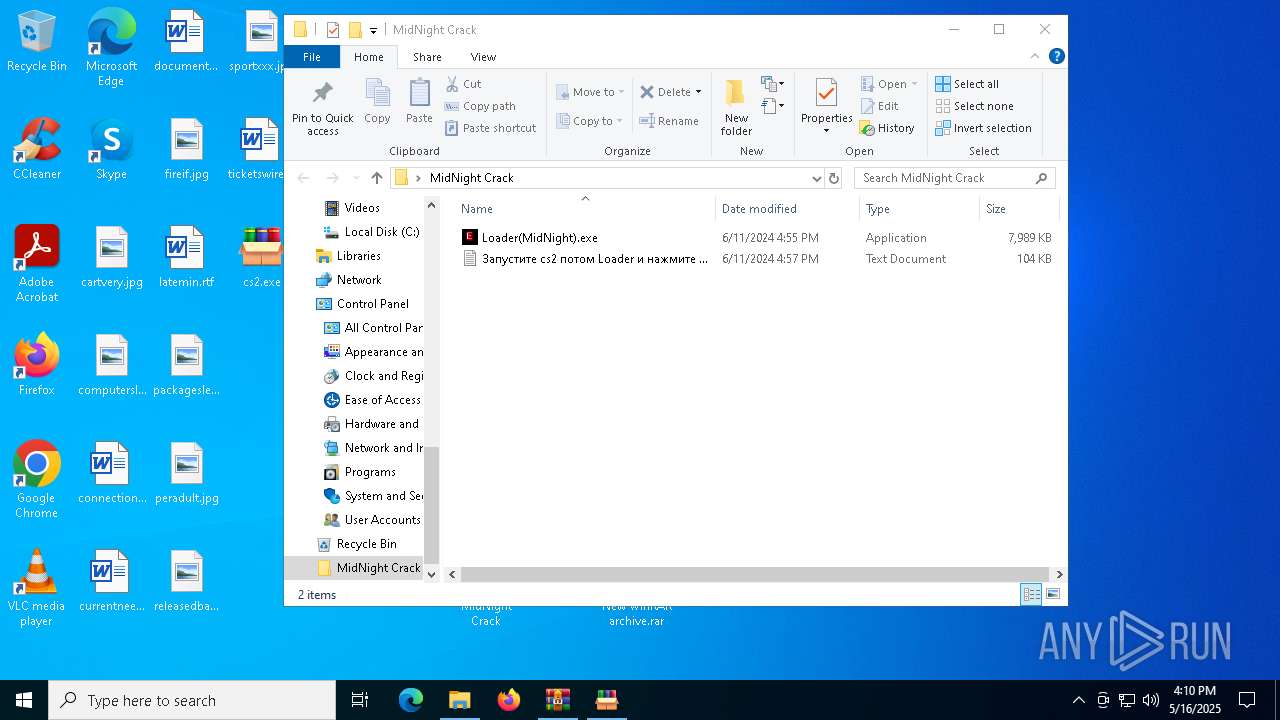
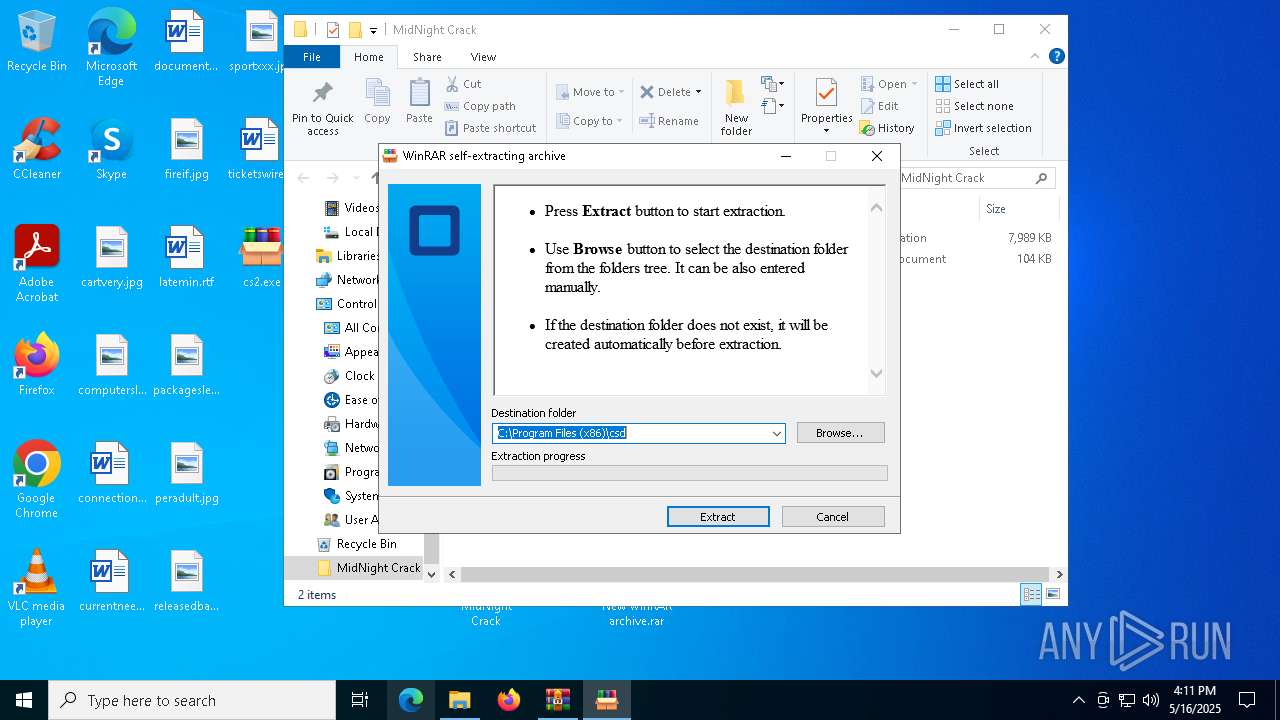
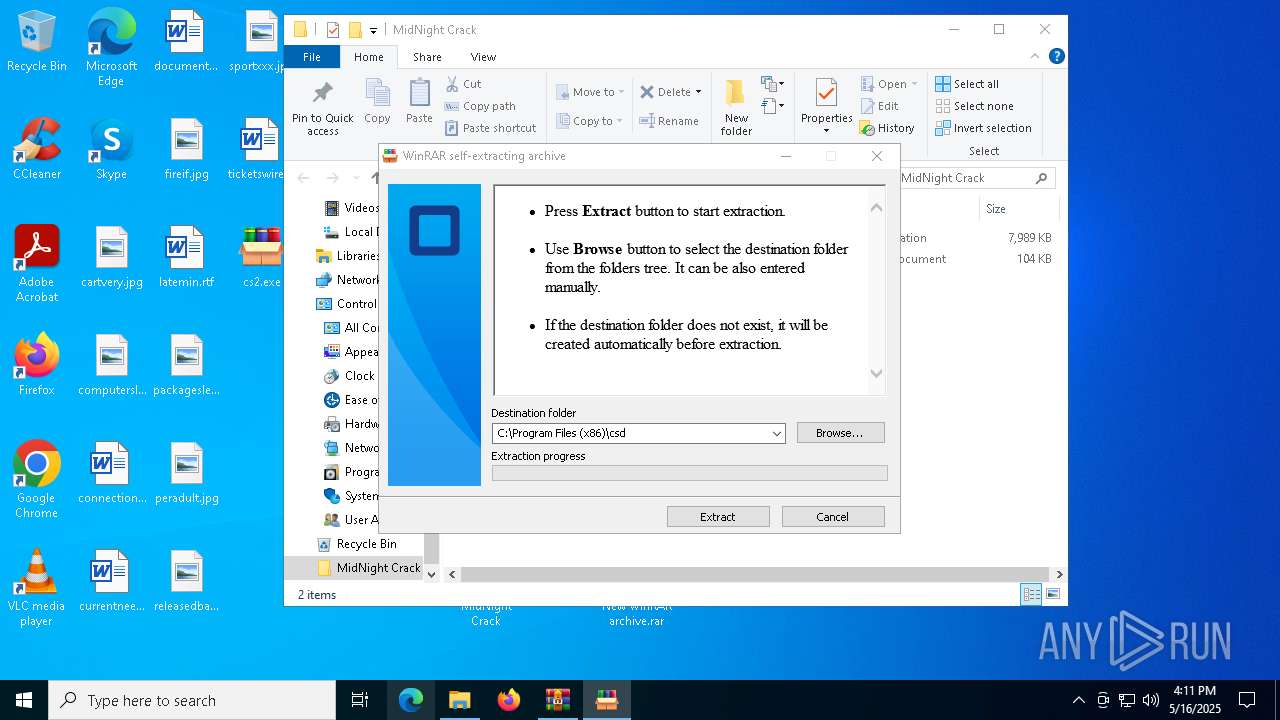
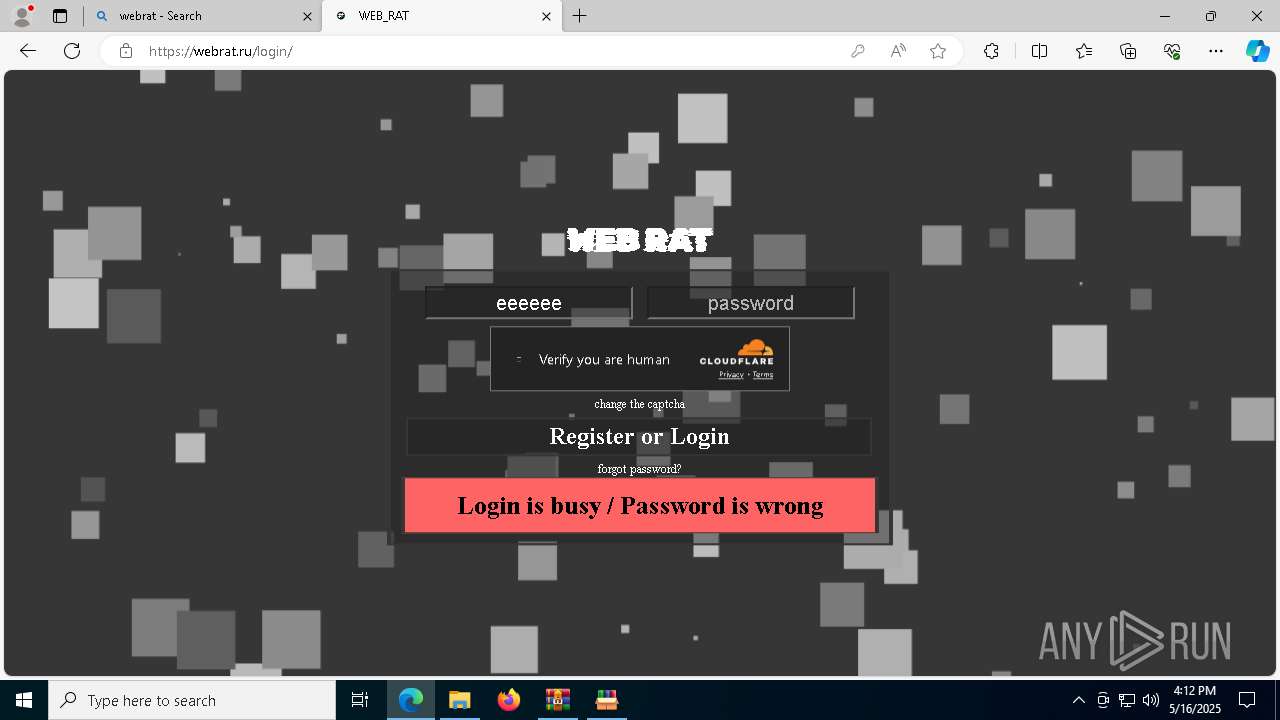
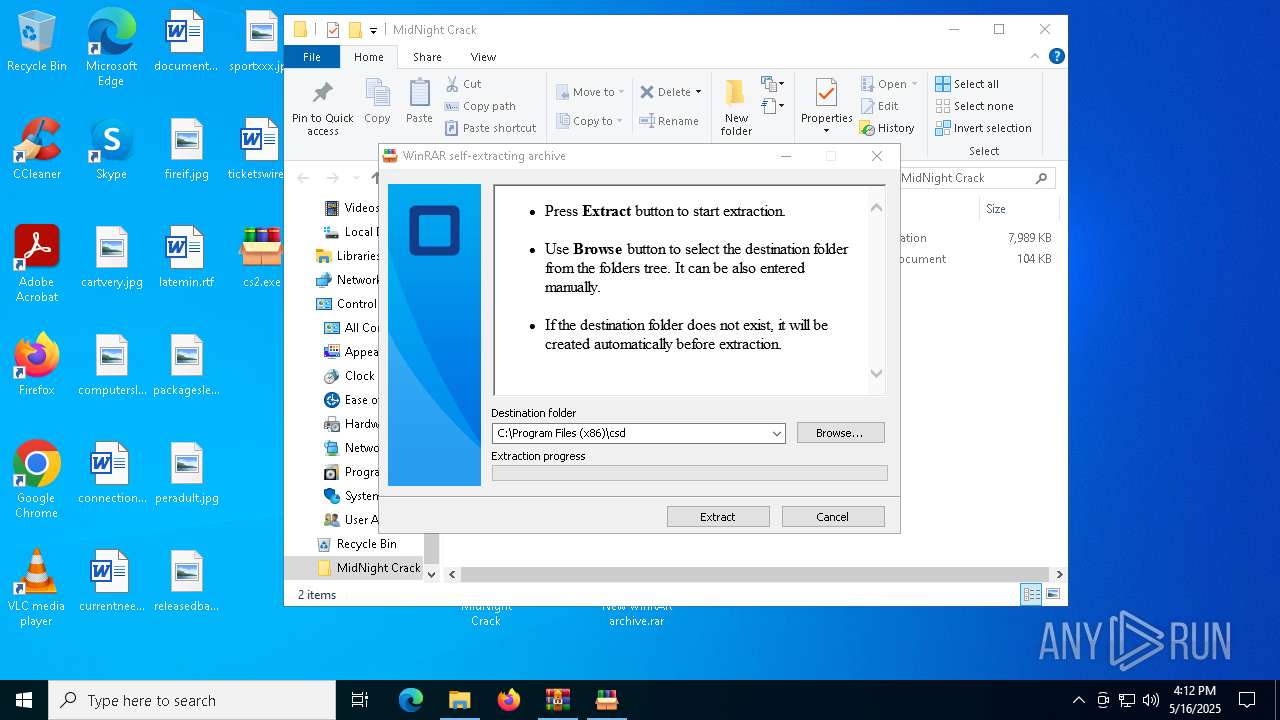
| File name: | MidNight Crack.zip |
| Full analysis: | https://app.any.run/tasks/8606f93d-a294-40fb-8521-c06f99855004 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | May 16, 2025, 16:08:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | E280C10725E88B213F3E217A40040568 |
| SHA1: | 1BCA05A4A9E18621FF9FC613CE8F435F42BB29DE |
| SHA256: | D1B1ACD787F64FA36A13CF04E7EA78C3D2D63734E0E782B95064AC5B47812240 |
| SSDEEP: | 98304:Cp9lM+MJzXwX1ckTilXtzXgfr3rLIZVAld+i+XVL7mhQpytiM0dVA/PQGfI2hcZ6:bYNrC1oMy6PxTA |
MALICIOUS
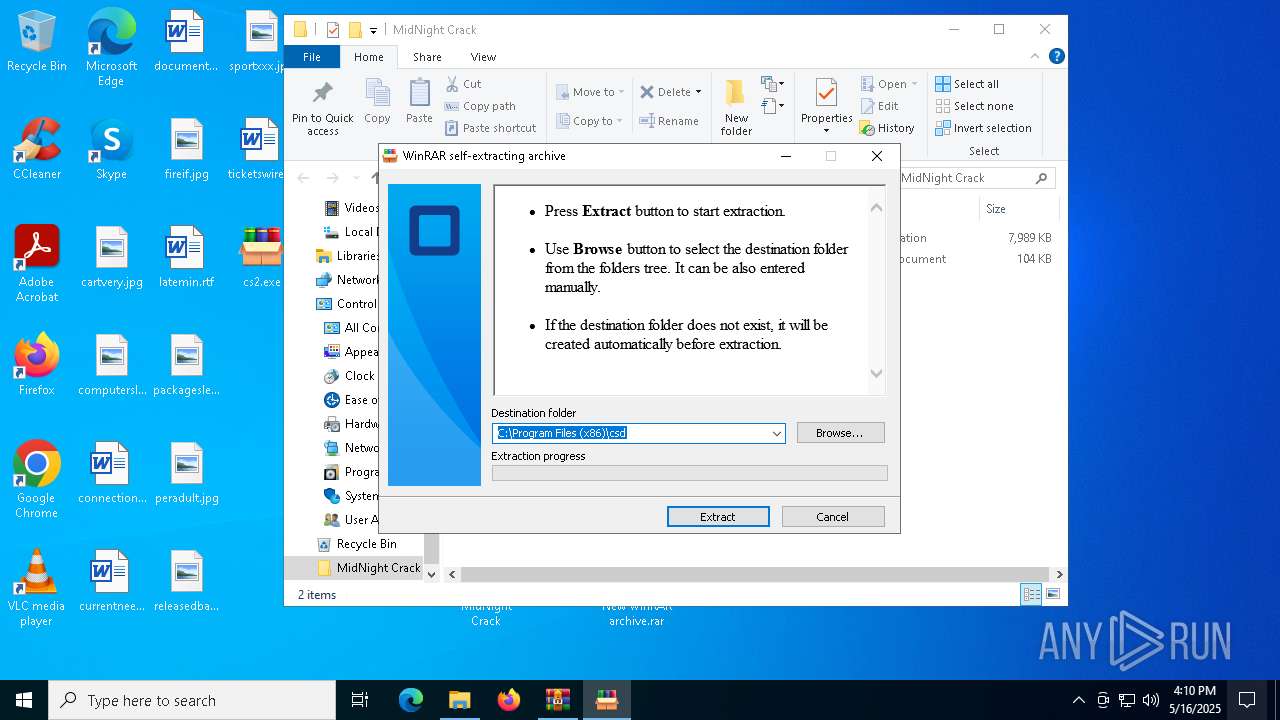
Generic archive extractor
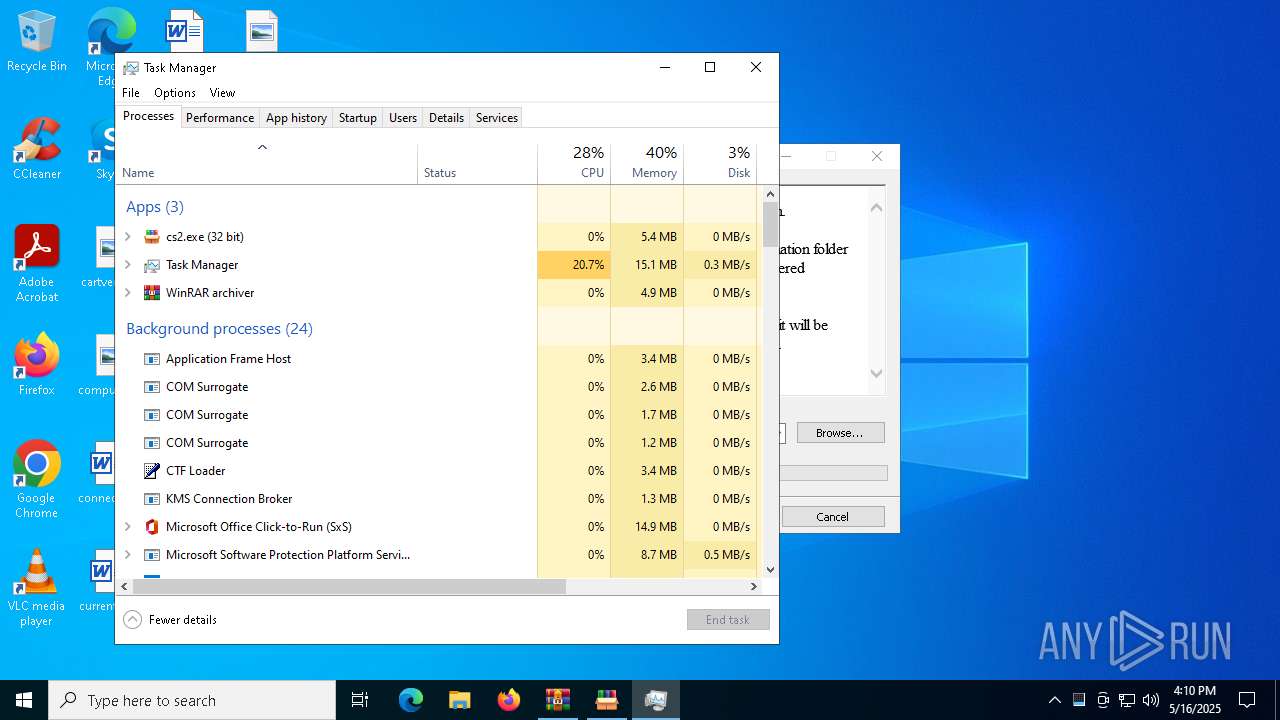
- WinRAR.exe (PID: 7012)
Changes the autorun value in the registry
- Svhost.exe (PID: 5728)
- Services.exe (PID: 7152)
Vulnerable driver has been detected
- Svhost.exe (PID: 5728)
Connects to the CnC server
- explorer.exe (PID: 7964)
MINER has been detected (SURICATA)
- explorer.exe (PID: 7964)
SUSPICIOUS
The process creates files with name similar to system file names
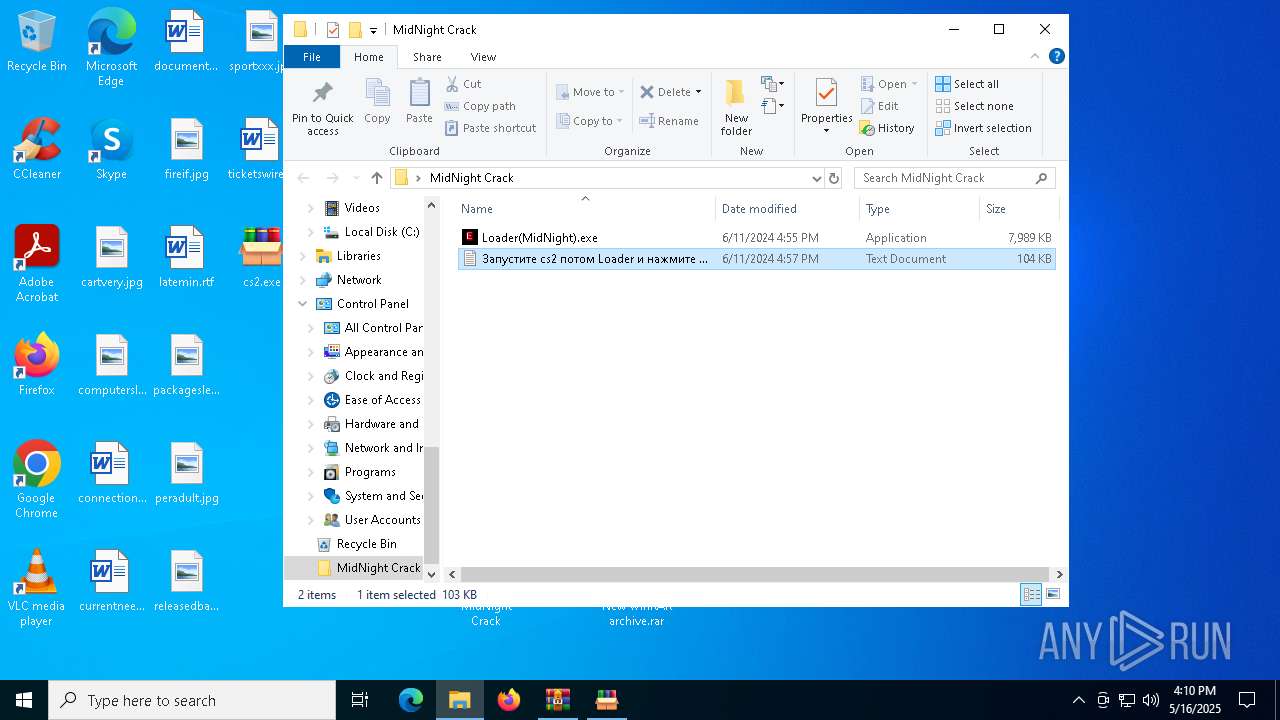
- Loader(MidNight).exe (PID: 1228)
- Svhost.exe (PID: 5728)
Reads Internet Explorer settings
- cs2.exe (PID: 8112)
Reads security settings of Internet Explorer
- cs2.exe (PID: 8112)
- System32.exe (PID: 5008)
- Loader(MidNight).exe (PID: 1228)
- Svhost.exe (PID: 5728)
Reads Microsoft Outlook installation path
- cs2.exe (PID: 8112)
There is functionality for taking screenshot (YARA)
- cs2.exe (PID: 8112)
Executable content was dropped or overwritten
- System32.exe (PID: 5008)
- Svhost.exe (PID: 5728)
- Loader(MidNight).exe (PID: 1228)
- Hyperprovidersaves.exe (PID: 2284)
- TextInputHost.exe (PID: 4728)
Checks for Java to be installed
- AimStar.exe (PID: 3240)
Starts itself from another location
- Svhost.exe (PID: 5728)
Reads the date of Windows installation
- Svhost.exe (PID: 5728)
Drops a system driver (possible attempt to evade defenses)
- Svhost.exe (PID: 5728)
Executing commands from a ".bat" file
- wscript.exe (PID: 4688)
- Hyperprovidersaves.exe (PID: 2284)
Potential Corporate Privacy Violation
- explorer.exe (PID: 7964)
Starts application with an unusual extension
- cmd.exe (PID: 5400)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5400)
Connects to unusual port
- explorer.exe (PID: 7964)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4688)
- Hyperprovidersaves.exe (PID: 2284)
INFO
Reads the computer name
- cs2.exe (PID: 8112)
- Loader(MidNight).exe (PID: 1228)
- System32.exe (PID: 5008)
- Svhost.exe (PID: 5728)
- javaw.exe (PID: 6564)
- sihost64.exe (PID: 6480)
- Services.exe (PID: 7152)
Checks supported languages
- cs2.exe (PID: 8112)
- System32.exe (PID: 5008)
- Loader(MidNight).exe (PID: 1228)
- AimStar.exe (PID: 3240)
- Svhost.exe (PID: 5728)
- javaw.exe (PID: 6564)
- sihost64.exe (PID: 6480)
- Services.exe (PID: 7152)
Checks proxy server information
- cs2.exe (PID: 8112)
Reads the software policy settings
- slui.exe (PID: 7212)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7012)
- WinRAR.exe (PID: 7740)
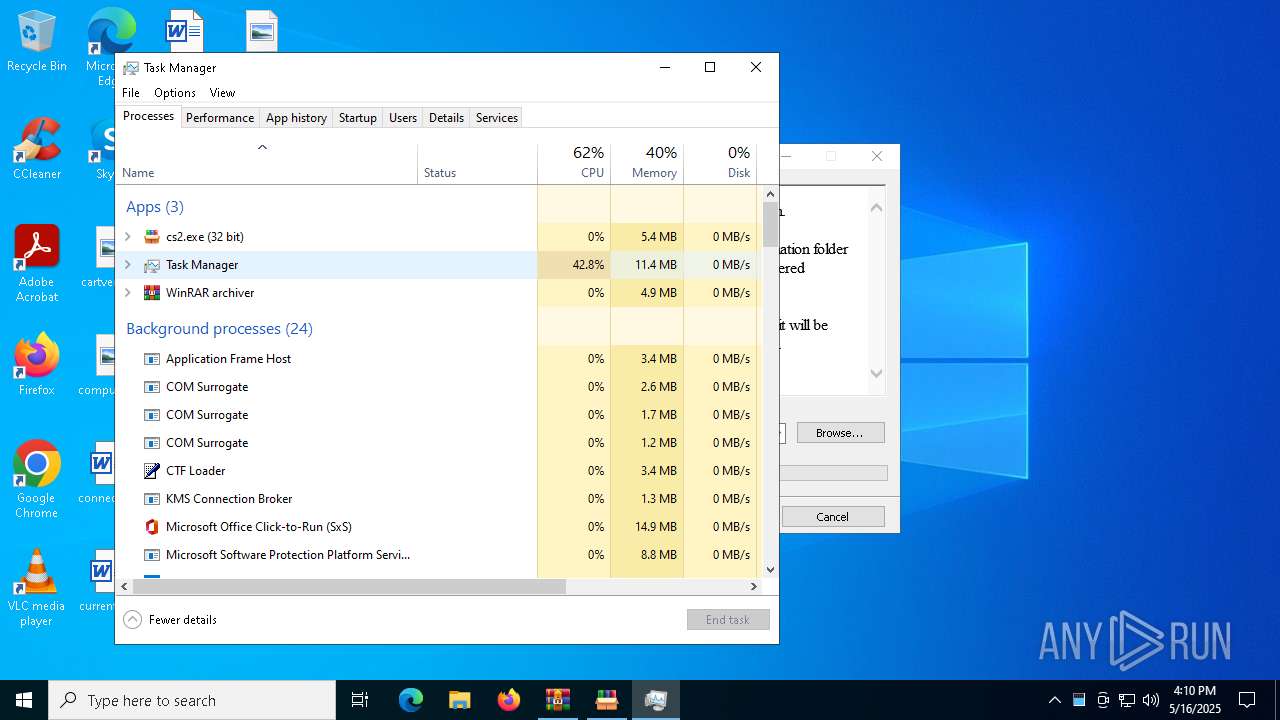
Manual execution by a user
- WinRAR.exe (PID: 7740)
- Taskmgr.exe (PID: 5588)
- cs2.exe (PID: 8112)
- Taskmgr.exe (PID: 2616)
- Loader(MidNight).exe (PID: 1228)
- msedge.exe (PID: 924)
Create files in a temporary directory
- Loader(MidNight).exe (PID: 1228)
- javaw.exe (PID: 6564)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 5588)
Drops encrypted VBS script (Microsoft Script Encoder)
- System32.exe (PID: 5008)
Process checks computer location settings
- System32.exe (PID: 5008)
- Loader(MidNight).exe (PID: 1228)
- Svhost.exe (PID: 5728)
Reads the machine GUID from the registry
- Svhost.exe (PID: 5728)
- javaw.exe (PID: 6564)
- sihost64.exe (PID: 6480)
- Services.exe (PID: 7152)
Creates files in the program directory
- javaw.exe (PID: 6564)
Creates files or folders in the user directory
- Svhost.exe (PID: 5728)
- javaw.exe (PID: 6564)
The sample compiled with japanese language support
- Svhost.exe (PID: 5728)
Changes the display of characters in the console
- cmd.exe (PID: 5400)
Application launched itself
- msedge.exe (PID: 924)
- msedge.exe (PID: 5084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:06:11 20:01:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | MidNight Crack/ |
Total processes
225
Monitored processes
89
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2744 --field-trial-handle=2256,i,14470447527025182798,1099860695088755475,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 744 | "C:\Users\admin\AppData\Roaming\Microsoft\Libs\sihost64.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Libs\sihost64.exe | — | Services.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Shell Infrastructure Host Version: 10.0.19041.746 Modules
| |||||||||||||||
| 812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2248 --field-trial-handle=2256,i,14470447527025182798,1099860695088755475,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 924 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1012 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6120 --field-trial-handle=2284,i,9453220711996672754,827770478247215286,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\Desktop\MidNight Crack\Loader(MidNight).exe" | C:\Users\admin\Desktop\MidNight Crack\Loader(MidNight).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1240 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=5848 --field-trial-handle=2284,i,9453220711996672754,827770478247215286,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2096 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6656 --field-trial-handle=2284,i,9453220711996672754,827770478247215286,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2108 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4004 --field-trial-handle=2284,i,9453220711996672754,827770478247215286,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
25 366
Read events
25 230
Write events
117
Delete events
19
Modification events
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MidNight Crack.zip | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7012) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
54
Suspicious files
484
Text files
90
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7740 | WinRAR.exe | C:\Users\admin\Desktop\New WinRAR archive.exe | executable | |
MD5:D0BDC1A40612F5212562A16ADD3E59B8 | SHA256:32A8C46536557033AA2F27113DED2CD1AD0A41712EC17ED3ACEC5FB4EE047D96 | |||
| 7012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7012.3268\MidNight Crack\Loader(MidNight).exe | executable | |
MD5:15B001FEF4488733A9BF87C69B7207DF | SHA256:F3F5566609126FCE08427113A2D0700335CC7016A7D099C8FD8FCE85C198C682 | |||
| 7012 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7012.3268\MidNight Crack\Запустите cs2 потом Loader и нажмите ins!.txt | text | |
MD5:B576F5AD11F191F0532E8DB8E01F522A | SHA256:46FB17CCD1E60D5BB1A3CF4ACC0B75A1669F7673C2E153F9077BBEF97E6EB975 | |||
| 7740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$CM7740.9408 | binary | |
MD5:0B708DDC493D3891E1F91E727B2EB614 | SHA256:B34EF2EC9FBBA8E2821734C777D3DFA340DAB86D20BF2F723959CB84B37EE521 | |||
| 5588 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 5728 | Svhost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Libs\WR64.sys | executable | |
MD5:0C0195C48B6B8582FA6F6373032118DA | SHA256:11BD2C9F9E2397C9A16E0990E4ED2CF0679498FE0FD418A3DFDAC60B5C160EE5 | |||
| 5008 | System32.exe | C:\msChainHostSvc\Y7mP1Qm5Rzc.bat | text | |
MD5:FD1F21DEDCD979CBDA65C2B71905BEB1 | SHA256:24820DCA97985317C11F2A75892FF737FA3CF5F0D1663AB52AE6D25A8FB01030 | |||
| 1228 | Loader(MidNight).exe | C:\Users\admin\AppData\Local\Temp\System32.exe | executable | |
MD5:4643C8D0BF811034A8CAD26124483DBE | SHA256:1ABBB73619234BDBFF1954212F317CA7F22173B9E56C37C50C47BD0C8EC95542 | |||
| 7740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$CM7740.7010 | binary | |
MD5:37A7B4117100971E414A5DA7B39EB2E7 | SHA256:4DF355BBE810787ADACF9ACF78F9FE3EF78BA0417A2F98422A6FA8E8800B0256 | |||
| 7740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$CM7740.9616 | binary | |
MD5:0B708DDC493D3891E1F91E727B2EB614 | SHA256:B34EF2EC9FBBA8E2821734C777D3DFA340DAB86D20BF2F723959CB84B37EE521 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
129
DNS requests
137
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.7:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7852 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7852 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7408 | svchost.exe | HEAD | 200 | 23.50.131.74:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1747693644&P2=404&P3=2&P4=UtpAbIvCQ11Oedorgs7x4rT%2bRhfWMA9PupC9TyNybZBanRYuR1b19AMySNsDbPGaexMo1WI8YjmoMql2ikxhTw%3d%3d | unknown | — | — | whitelisted |
4728 | TextInputHost.exe | POST | 404 | 46.41.16.168:80 | http://759931cm.n9shteam1.top/ToLinuxflower.php | unknown | — | — | malicious |
7408 | svchost.exe | GET | 206 | 23.50.131.74:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1747693644&P2=404&P3=2&P4=UtpAbIvCQ11Oedorgs7x4rT%2bRhfWMA9PupC9TyNybZBanRYuR1b19AMySNsDbPGaexMo1WI8YjmoMql2ikxhTw%3d%3d | unknown | — | — | whitelisted |
7408 | svchost.exe | GET | 206 | 23.50.131.74:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1747693644&P2=404&P3=2&P4=UtpAbIvCQ11Oedorgs7x4rT%2bRhfWMA9PupC9TyNybZBanRYuR1b19AMySNsDbPGaexMo1WI8YjmoMql2ikxhTw%3d%3d | unknown | — | — | whitelisted |
7408 | svchost.exe | GET | 206 | 23.50.131.74:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1747693644&P2=404&P3=2&P4=UtpAbIvCQ11Oedorgs7x4rT%2bRhfWMA9PupC9TyNybZBanRYuR1b19AMySNsDbPGaexMo1WI8YjmoMql2ikxhTw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.7:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
7964 | explorer.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7964 | explorer.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
4728 | TextInputHost.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
5796 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
5796 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
5796 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
5796 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |