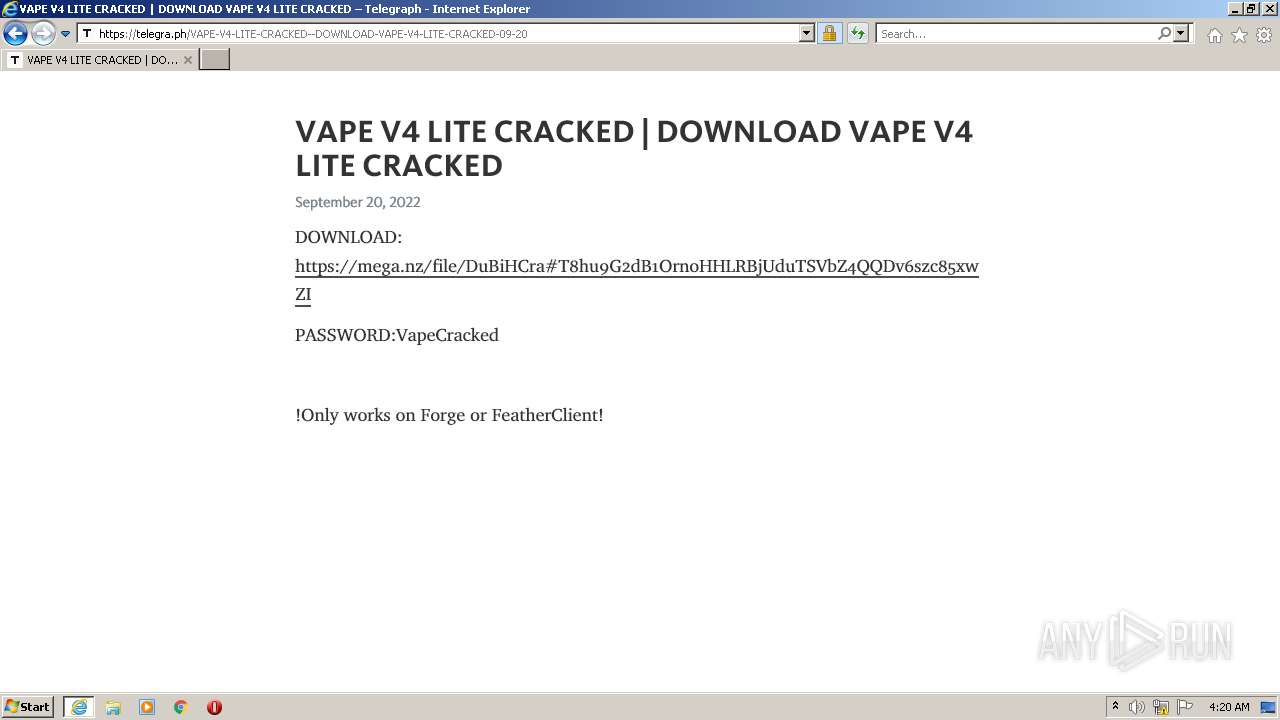
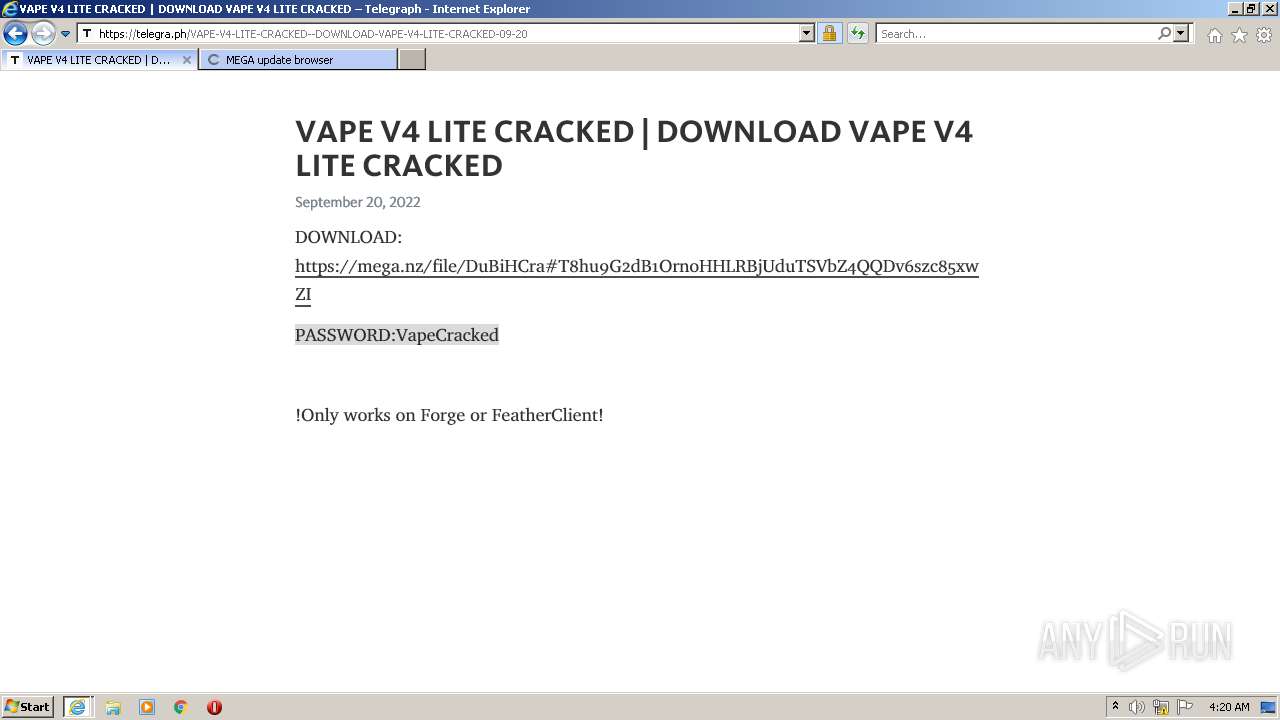
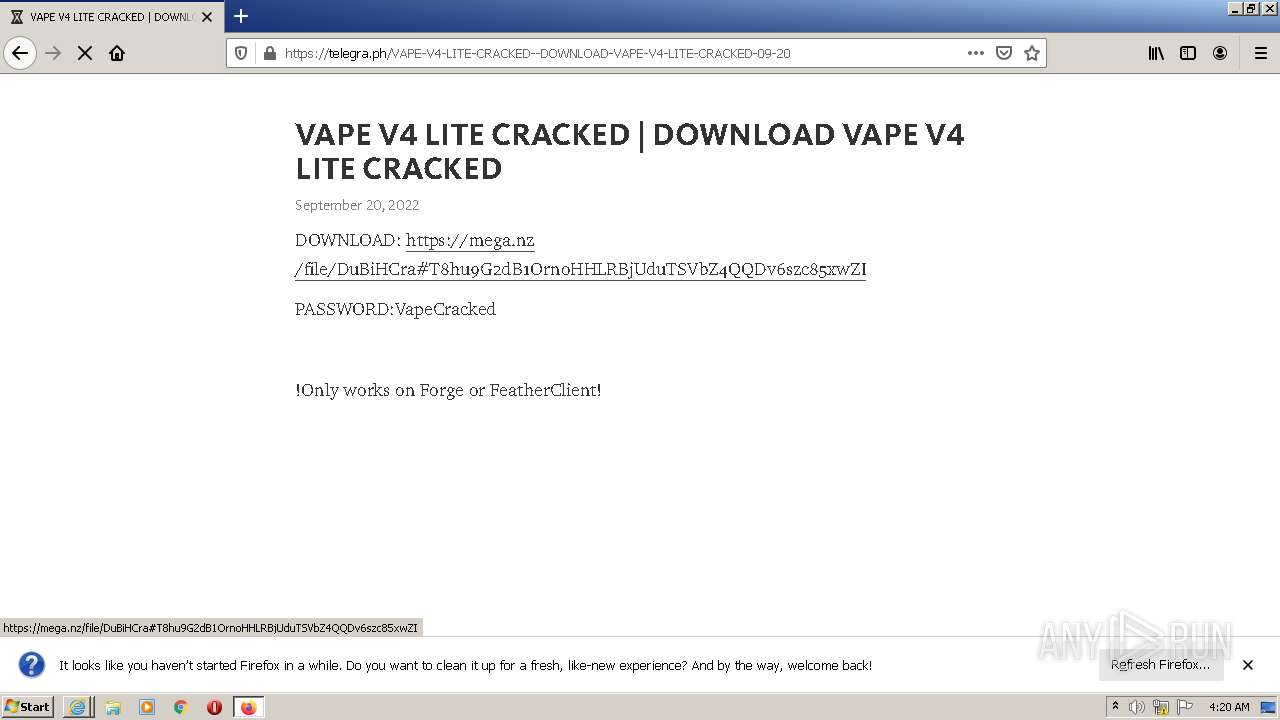
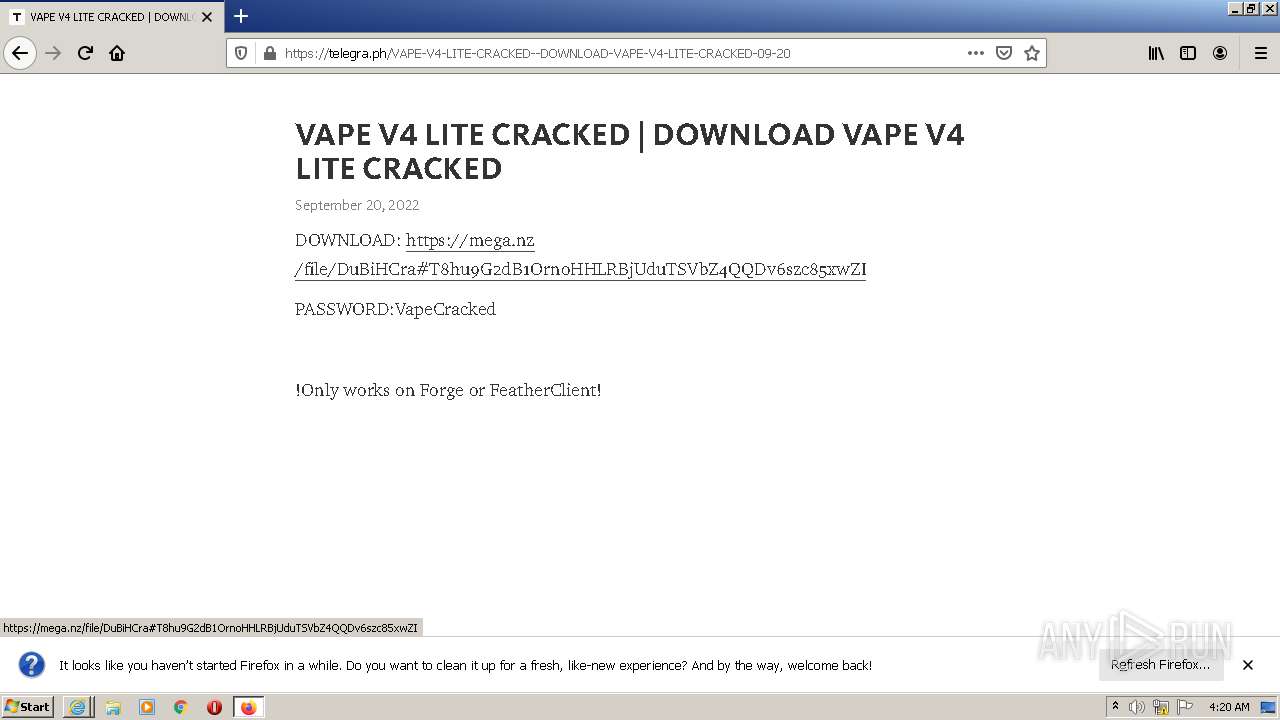
| URL: | https://www.youtube.com/redirect?event=video_description&redir_token=QUFFLUhqa3ZaNVlDXzVva2xxYncyeVpSaW5mNVEzUlNLd3xBQ3Jtc0ttTGZWbkF0cEd2b1VTcDBHY2hOSzFLSmhJMl81X2NScjFGWl9QVXlKR3NFaWk1NHdFaVZNV2dmN0RVejNLRXRsejM0WDJOZHJOVG4yRjdzY1NDdDJNOS13aU1seGF6elpMYWM4emdfMlVxVW5wYVJOZw&q=https%3A%2F%2Ftelegra.ph%2FVAPE-V4-LITE-CRACKED--DOWNLOAD-VAPE-V4-LITE-CRACKED-09-20&v=zqON_kTYE_0 |
| Full analysis: | https://app.any.run/tasks/58292fe8-40b7-4c69-842b-e3f661ad2177 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | October 05, 2022, 03:19:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9C9312299BE39F25C73D36024F2C087E |
| SHA1: | ECC14D36BD6669F303744FE52E4607253076602F |
| SHA256: | D172C4B9F5A70EEBACC6CD3E05A2BF570970DC77646550B5915019CBF2010A8E |
| SSDEEP: | 6:2OLUxGKmKLqZ3I0XU+V2bQZfjYtXpv9/Vtiv+Bu935hW2zT2q3z0Or1Duj2uO6:2jGRfLxZfU3pTYR5924BZDS7O6 |
MALICIOUS
Drops executable file immediately after starts
- firefox.exe (PID: 1188)
- WinRAR.exe (PID: 1408)
Application was dropped or rewritten from another process
- start.exe (PID: 2264)
- server.exe (PID: 4856)
Connects to CnC server
- AppLaunch.exe (PID: 101132)
Actions looks like stealing of personal data
- AppLaunch.exe (PID: 101132)
REDLINE was detected
- AppLaunch.exe (PID: 101132)
Steals credentials from Web Browsers
- AppLaunch.exe (PID: 101132)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1064)
- iexplore.exe (PID: 2844)
Reads the computer name
- WinRAR.exe (PID: 1408)
- cmd.exe (PID: 328)
- AppLaunch.exe (PID: 101132)
Executable content was dropped or overwritten
- firefox.exe (PID: 1188)
- WinRAR.exe (PID: 1408)
Checks supported languages
- WinRAR.exe (PID: 1408)
- start.exe (PID: 2264)
- cmd.exe (PID: 328)
- AppLaunch.exe (PID: 101132)
- server.exe (PID: 4856)
Drops a file with a compile date too recent
- firefox.exe (PID: 1188)
- WinRAR.exe (PID: 1408)
Starts CMD.EXE for commands execution
- start.exe (PID: 2264)
Reads Environment values
- AppLaunch.exe (PID: 101132)
Reads the cookies of Mozilla Firefox
- AppLaunch.exe (PID: 101132)
Reads the cookies of Google Chrome
- AppLaunch.exe (PID: 101132)
Searches for installed software
- AppLaunch.exe (PID: 101132)
INFO
Application launched itself
- iexplore.exe (PID: 2724)
- firefox.exe (PID: 2756)
- firefox.exe (PID: 1188)
Checks supported languages
- iexplore.exe (PID: 2724)
- iexplore.exe (PID: 1064)
- iexplore.exe (PID: 2844)
- firefox.exe (PID: 2756)
- firefox.exe (PID: 1188)
- firefox.exe (PID: 1176)
- firefox.exe (PID: 468)
- firefox.exe (PID: 628)
- firefox.exe (PID: 1404)
- firefox.exe (PID: 2704)
- firefox.exe (PID: 552)
- firefox.exe (PID: 2708)
Reads settings of System Certificates
- iexplore.exe (PID: 2724)
- iexplore.exe (PID: 1064)
- iexplore.exe (PID: 2844)
Reads the computer name
- iexplore.exe (PID: 1064)
- iexplore.exe (PID: 2724)
- iexplore.exe (PID: 2844)
- firefox.exe (PID: 1188)
- firefox.exe (PID: 468)
- firefox.exe (PID: 1176)
- firefox.exe (PID: 1404)
- firefox.exe (PID: 628)
- firefox.exe (PID: 2704)
- firefox.exe (PID: 552)
- firefox.exe (PID: 2708)
Checks Windows Trust Settings
- iexplore.exe (PID: 1064)
- iexplore.exe (PID: 2724)
- iexplore.exe (PID: 2844)
- firefox.exe (PID: 1188)
Reads internet explorer settings
- iexplore.exe (PID: 1064)
- iexplore.exe (PID: 2844)
Changes internet zones settings
- iexplore.exe (PID: 2724)
Creates files in the user directory
- iexplore.exe (PID: 1064)
- iexplore.exe (PID: 2724)
- firefox.exe (PID: 1188)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2724)
Manual execution by user
- firefox.exe (PID: 2756)
- WinRAR.exe (PID: 1408)
Changes settings of System certificates
- iexplore.exe (PID: 2724)
Reads CPU info
- firefox.exe (PID: 1188)
Creates files in the program directory
- firefox.exe (PID: 1188)
Reads the date of Windows installation
- firefox.exe (PID: 1188)
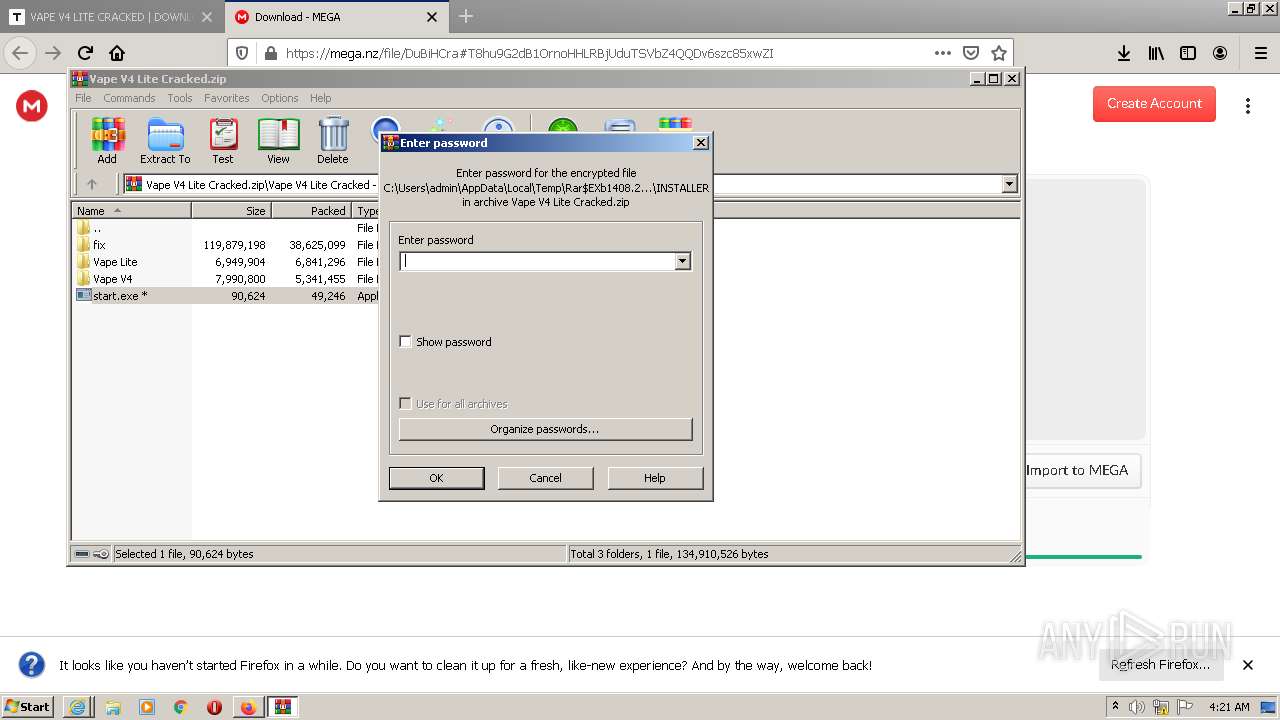
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 1408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
17
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Windows\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\AA21.tmp\AA22.tmp\AA23.bat "C:\Users\admin\AppData\Local\Temp\Rar$EXb1408.24510\Vape V4 Lite Cracked\start.exe"" | C:\Windows\system32\cmd.exe | — | start.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 468 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1188.13.449908484\327330269" -childID 2 -isForBrowser -prefsHandle 1916 -prefMapHandle 1932 -prefsLen 6644 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 1188 "\\.\pipe\gecko-crash-server-pipe.1188" 1852 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 552 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1188.34.832321356\336002037" -childID 5 -isForBrowser -prefsHandle 4004 -prefMapHandle 4000 -prefsLen 8250 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 1188 "\\.\pipe\gecko-crash-server-pipe.1188" 4016 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 628 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1188.20.1582419806\459684951" -childID 3 -isForBrowser -prefsHandle 1784 -prefMapHandle 1776 -prefsLen 7470 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 1188 "\\.\pipe\gecko-crash-server-pipe.1188" 3212 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1064 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2724 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1176 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1188.0.1832057186\379663438" -parentBuildID 20201112153044 -prefsHandle 1116 -prefMapHandle 1104 -prefsLen 1 -prefMapSize 238726 -appdir "C:\Program Files\Mozilla Firefox\browser" - 1188 "\\.\pipe\gecko-crash-server-pipe.1188" 1184 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1188 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1404 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1188.6.485286333\2130780721" -childID 1 -isForBrowser -prefsHandle 3012 -prefMapHandle 3008 -prefsLen 181 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 1188 "\\.\pipe\gecko-crash-server-pipe.1188" 3024 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
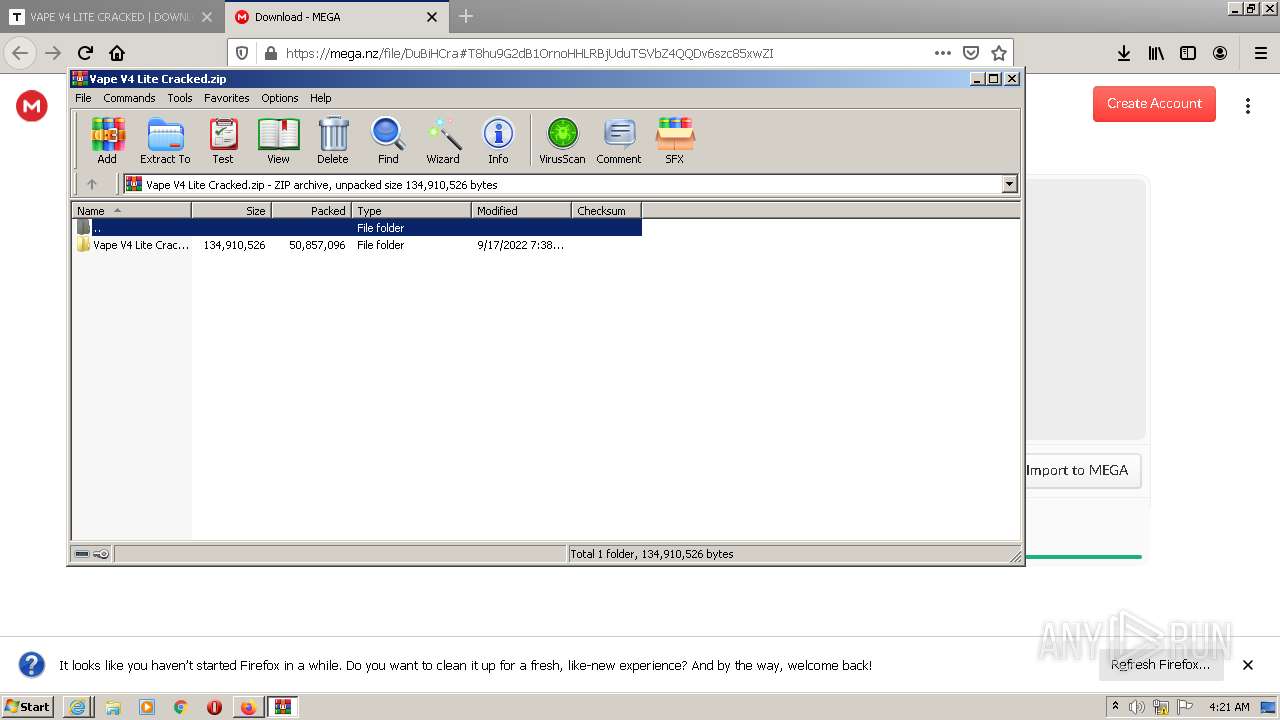
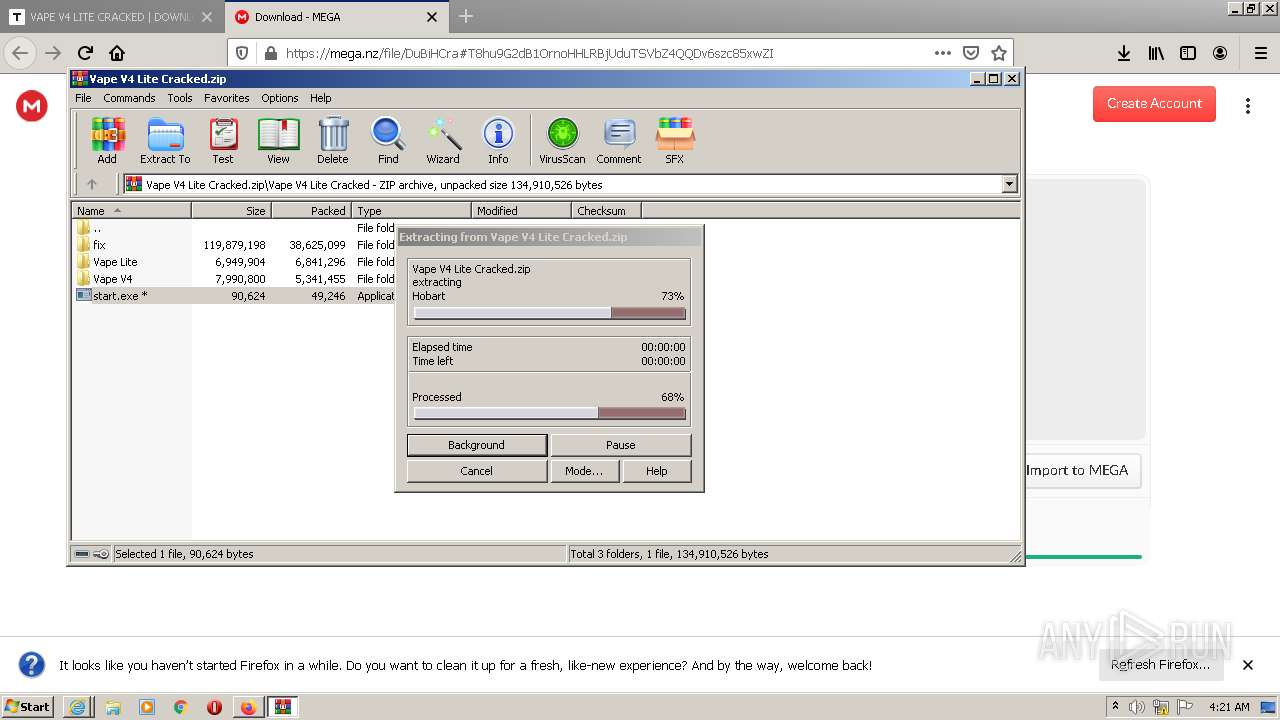
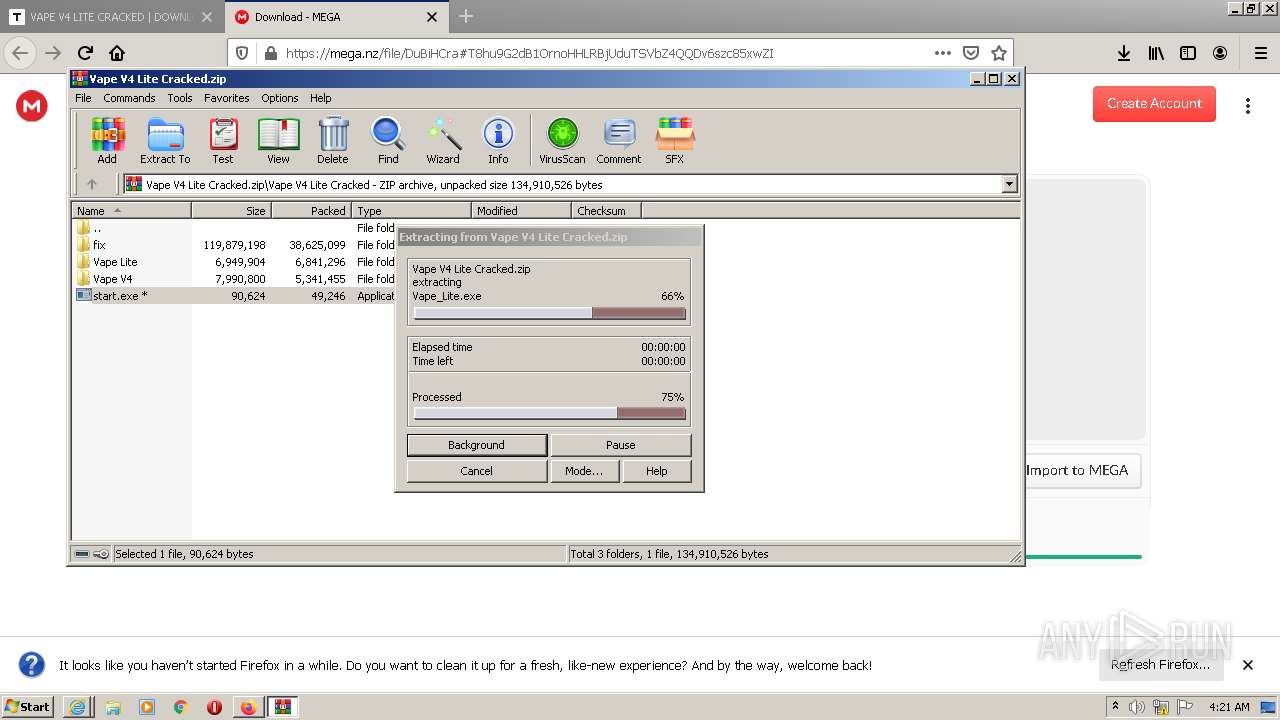
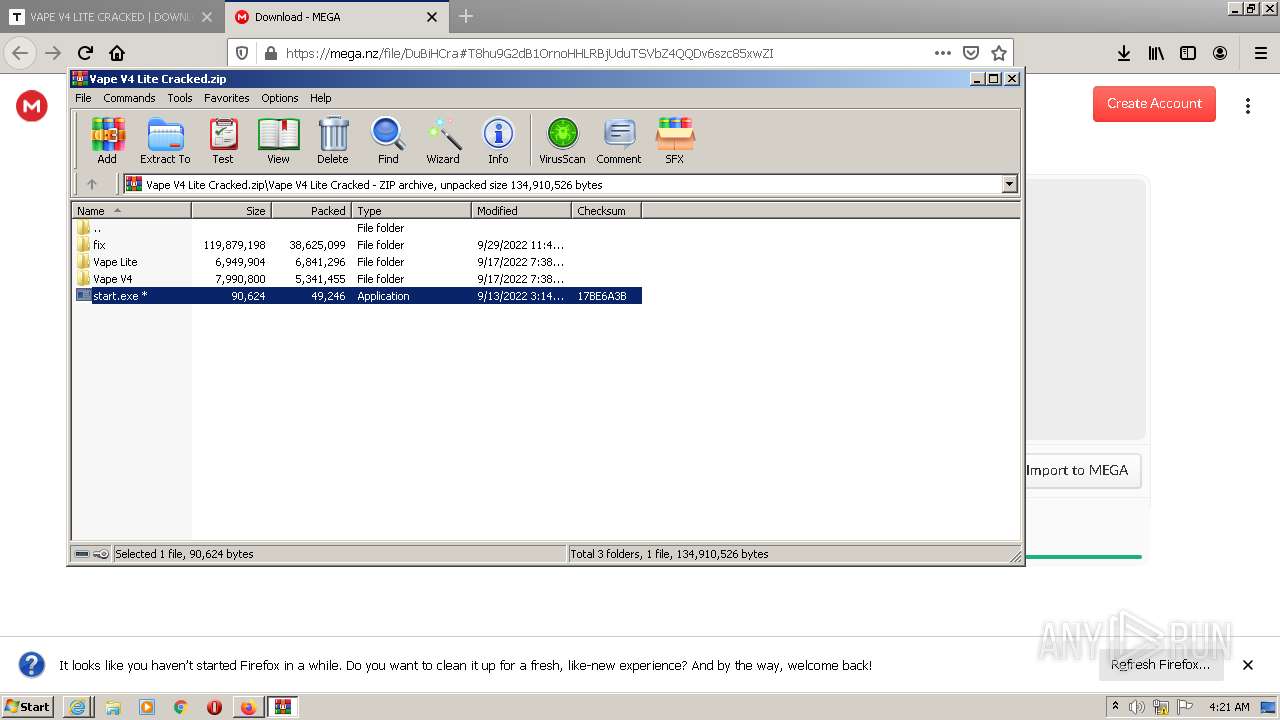
| 1408 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Vape V4 Lite Cracked.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
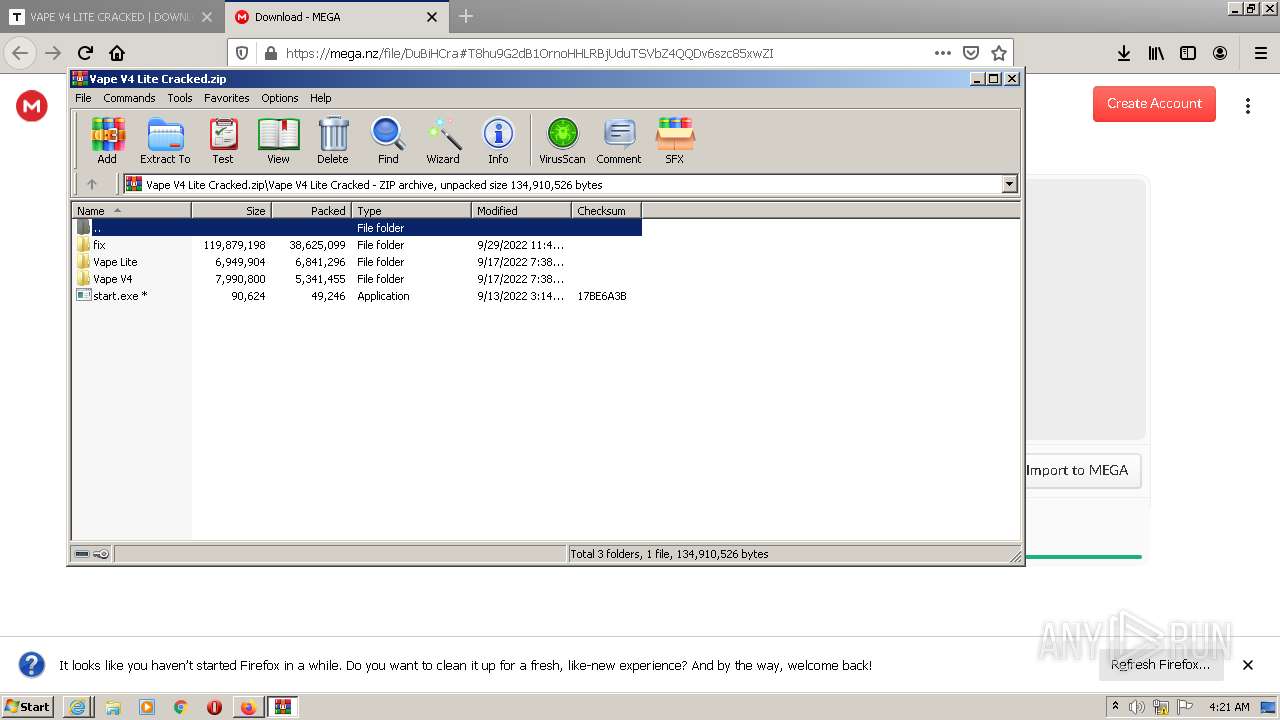
| 2264 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb1408.24510\Vape V4 Lite Cracked\start.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb1408.24510\Vape V4 Lite Cracked\start.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
34 683
Read events
34 462
Write events
217
Delete events
4
Modification events
| (PID) Process: | (2724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30988393 | |||
| (PID) Process: | (2724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30988393 | |||
| (PID) Process: | (2724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2724) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
107
Suspicious files
170
Text files
217
Unknown types
661
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2724 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_14F2E352CCFE495001982FFDAAC3BE84 | der | |
MD5:— | SHA256:— | |||
| 1064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
| 1064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | binary | |
MD5:— | SHA256:— | |||
| 1064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_1ACD2B4A039DF3260017F7BF28EE7323 | der | |
MD5:— | SHA256:— | |||
| 1064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 2724 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:— | SHA256:— | |||
| 1064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\265C0DEB29181DD1891051371C5F863A_1ACD2B4A039DF3260017F7BF28EE7323 | binary | |
MD5:— | SHA256:— | |||
| 1064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 1064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
118
DNS requests
165
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1064 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQDHwC6F%2BLNTXQ%3D%3D | US | der | 1.74 Kb | whitelisted |
1064 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
1064 | iexplore.exe | GET | 200 | 172.217.17.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECY%2B0YL3%2ByMOCtPdrqPffYg%3D | US | der | 471 b | whitelisted |
1064 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQC2T6rhHiP0ng%3D%3D | US | der | 1.74 Kb | whitelisted |
2844 | iexplore.exe | GET | 200 | 184.24.77.48:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQFdqD04q0ttS%2FOmrEk%2FigIvA%3D%3D | US | der | 503 b | shared |
2844 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 2.18 Kb | whitelisted |
2844 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQDqXkroZv5KiI1sJCfGNIam | US | der | 472 b | whitelisted |
1064 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
2724 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2844 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://crl.comodoca.com/AAACertificateServices.crl | US | der | 506 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1064 | iexplore.exe | 142.250.187.110:443 | www.youtube.com | GOOGLE | US | whitelisted |
— | — | 13.107.21.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2724 | iexplore.exe | 13.107.21.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2724 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1064 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
2724 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
1064 | iexplore.exe | 172.217.169.195:443 | www.gstatic.com | GOOGLE | US | whitelisted |
1064 | iexplore.exe | 172.217.17.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1064 | iexplore.exe | 149.154.164.13:443 | telegra.ph | Telegram Messenger Inc | GB | suspicious |
1064 | iexplore.exe | 192.124.249.41:80 | ocsp.godaddy.com | SUCURI-SEC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.youtube.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.gstatic.com |
| whitelisted |
telegra.ph |
| malicious |
ocsp.godaddy.com |
| whitelisted |
t.me |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1188 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1188 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1188 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
1188 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
9 ETPRO signatures available at the full report