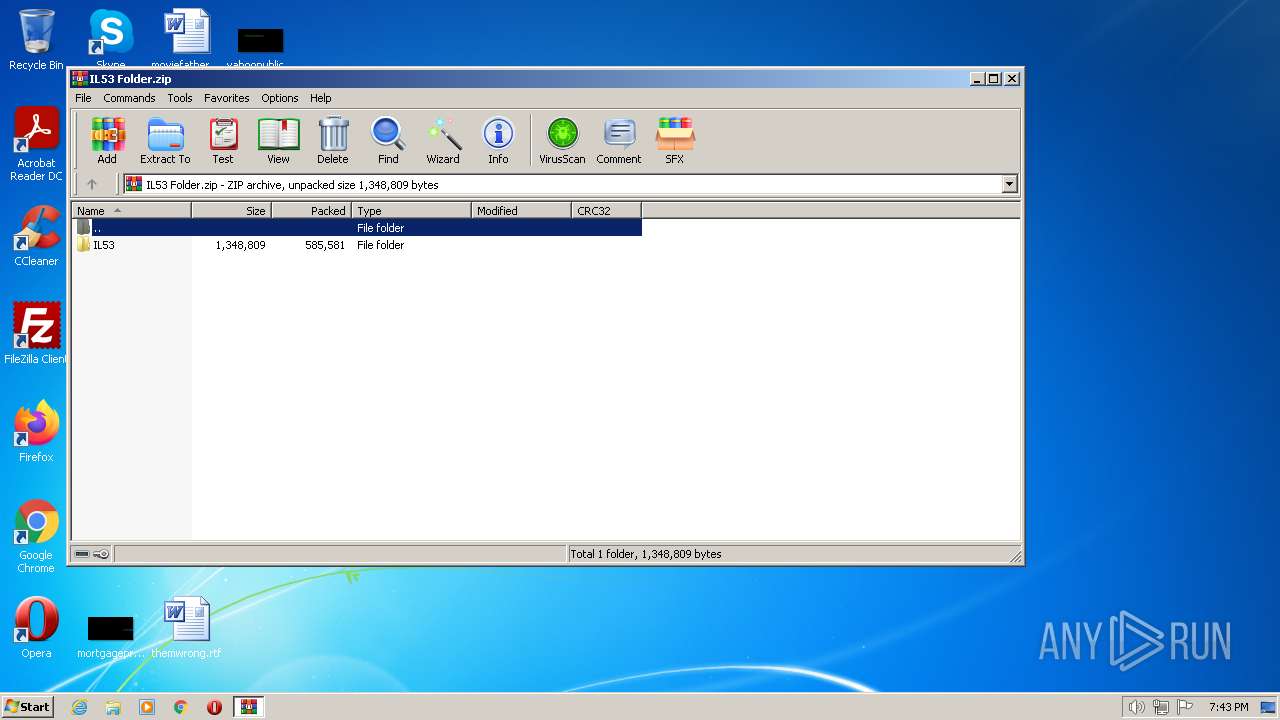
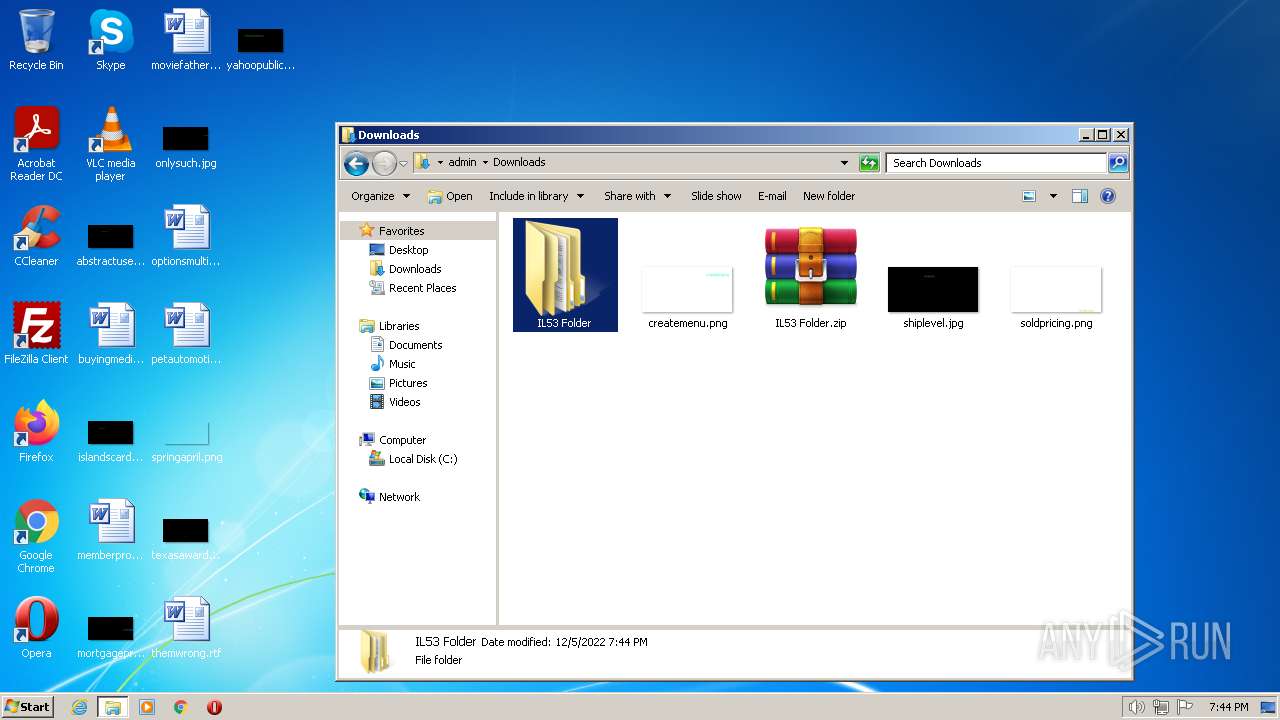
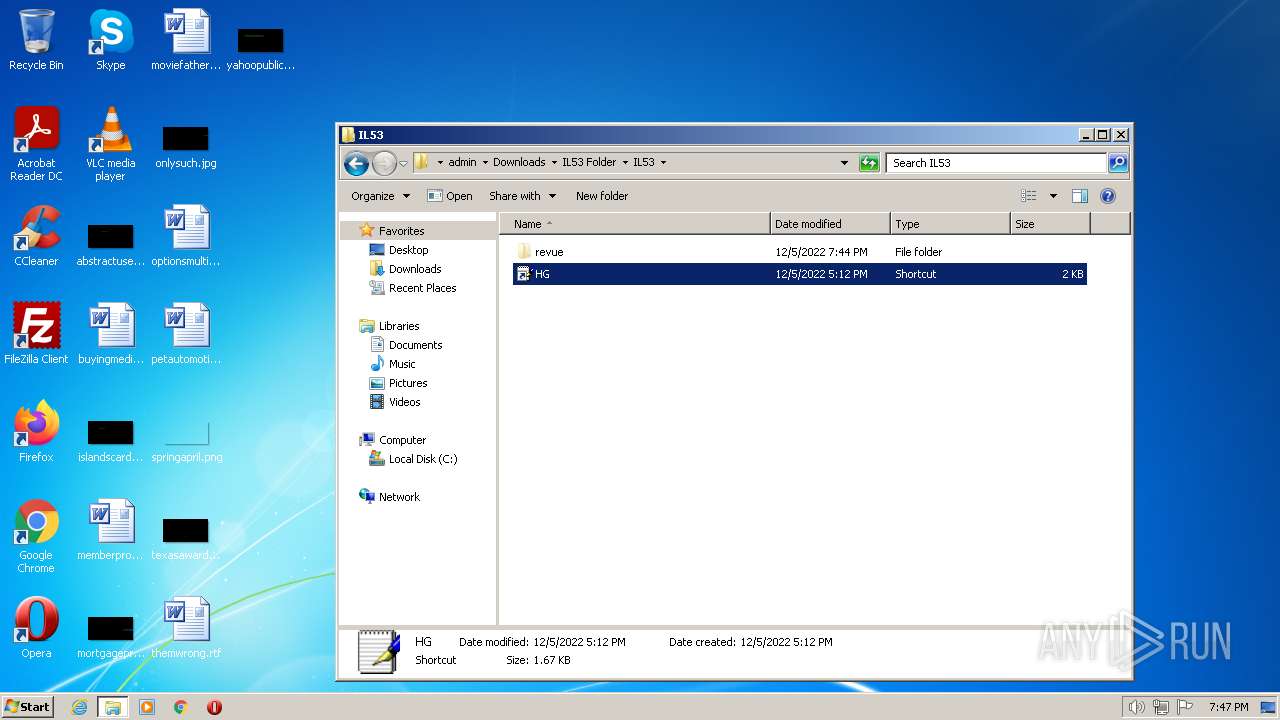
| File name: | IL53 Folder.zip |
| Full analysis: | https://app.any.run/tasks/7d708630-770e-415d-99af-d9dba5a717f5 |
| Verdict: | Malicious activity |
| Threats: | Qbot is a banking Trojan — a malware designed to collect banking information from victims. Qbot targets organizations mostly in the US. It is equipped with various sophisticated evasion and info-stealing functions and worm-like functionality, and a strong persistence mechanism. |
| Analysis date: | December 05, 2022, 19:43:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 015DA99C8A06BDCD1FC720812D632B8D |
| SHA1: | C2CE7A268932FC69EEC97F05B28E3ADF0459DFA2 |
| SHA256: | D15638B0454264677F94A41E3DB0479ABAB16DDC9894DC3F4AF9A6547B984B77 |
| SSDEEP: | 12288:zYI5fnAsHueQoyzbmOVm2HpmYY3Hjkgr9RimD6/u4QIW9futTBM//3:zYI91Byz5m2HpmYY3jTr9LD6/u4Qb9fp |
MALICIOUS
Loads dropped or rewritten executable
- rundll32.exe (PID: 2300)
QBOT detected by memory dumps
- wermgr.exe (PID: 708)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 1652)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Qbot
(PID) Process(708) wermgr.exe
BotnetBB09
Campaign1670238005
Version404.46
C2 (137)76.100.159.250:443
1.66.191.69:4611
1.1.186.64:17161
187.1.1.50:23289
1.187.1.1:28054
158.8.174.0:348
205.238.8.174:257
165.15.180.8:44545
41.44.19.36:995
1.78.17.157:1281
0.1.173.18:32259
187.1.1.75:25469
8.174.1.1:44122
138.8.174.1:283
45.237.8.174:257
68.227.219.1:47873
12.172.173.82:993
1.103.144.201:15880
1.1.12.172:44370
222.1.1.173:61278
1.187.1.1:23465
198.125.100.1:280
114.59.8.174:257
66.134.24.1:47873
93.164.248.234:443
1.24.64.114:15112
1.1.83.92:21853
187.1.1.78:17915
8.174.1.1:48774
61.1.187.0:258
47.198.8.174:257
223.248.31.1:47873
12.172.173.82:995
1.94.63.65:37377
1.1.80.13:45975
174.1.1.70:30948
8.35.1.1:55492
102.8.30.1:287
254.199.3.227:1
129.109.27.8:44545
69.119.123.159:2222
1.91.254.230:4609
0.1.64.121:41318
187.1.1.38:42738
8.39.0.1:3244
82.1.209.1:331
236.149.1.187:257
229.117.95.8:44545
74.92.243.113:50000
1.183.82.100:28168
1.1.75.98:39443
187.1.1.193:39626
1.187.0.1:31098
223.3.227.1:326
104.126.3.227:257
67.255.57.8:44545
213.91.235.146:443
1.37.14.229:56328
1.1.76.80:46234
227.1.1.62:8066
1.209.1.1:22899
99.1.187.1:258
12.243.1.187:1
152.152.46.1:47873
188.48.123.229:995
1.90.104.22:7176
1.1.201.210:27615
225.0.1.47:10650
1.187.1.1:12868
71.3.227.1:340
202.22.1.187:1
241.180.94.1:47873
92.189.214.236:2222
1.103.55.67:46081
1.1.90.89:24478
174.1.1.86:55802
8.174.1.1:18500
55.8.174.1:342
16.164.1.187:1
244.25.165.1:47873
65.30.139.145:995
1.73.161.176:55809
1.1.199.83:42473
187.1.1.98:37143
1.187.1.1:21539
14.3.227.1:280
114.59.13.61:257
68.204.71.1:47873
102.46.139.82:993
1.71.247.10:16131
1.1.149.126:40810
187.1.1.58:41695
1.187.1.1:55492
102.8.35.1:440
91.69.1.187:257
99.116.47.1:47873
81.131.210.167:443
1.103.141.50:29955
1.1.184.176:39507
227.1.1.92:53124
8.174.1.1:36513
232.8.174.1:432
207.63.1.187:257
153.132.82.1:47873
108.6.249.139:443
1.69.133.162:8961
1.1.76.20:10797
187.1.1.139:55460
1.187.1.1:6350
39.1.187.1:268
173.82.0.21:257
86.98.236.1:47873
50.68.204.71:993
1.88.126.94:1219
1.1.85.245:56663
30.0.1.190:52806
8.174.0.1:22493
110.8.174.1:339
54.186.1.187:257
223.91.46.1:47872
78.100.230.10:995
1.181.164.194:58369
1.1.174.101:28420
187.1.1.75:29454
1.187.0.1:22241
138.8.174.1:314
115.126.3.227:257
96.75.237.8:44544
105.103.56.28:2078
1.198.2.51:61955
1.1.174.104:47253
187.1.1.105:26424
3.222.0.1:6208
59.239.18.1:349
192.142.0.20:257
14.82.210.8:44544
90.116.219.167:2222
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
50
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | C:\Windows\system32\cmd.exe /K revue\upthrust.cmd system rundl | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 708 | C:\Windows\System32\wermgr.exe | C:\Windows\System32\wermgr.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7601.24521 (win7sp1_ldr_escrow.190909-1704) Modules
Qbot(PID) Process(708) wermgr.exe BotnetBB09 Campaign1670238005 Version404.46 C2 (137)76.100.159.250:443 1.66.191.69:4611 1.1.186.64:17161 187.1.1.50:23289 1.187.1.1:28054 158.8.174.0:348 205.238.8.174:257 165.15.180.8:44545 41.44.19.36:995 1.78.17.157:1281 0.1.173.18:32259 187.1.1.75:25469 8.174.1.1:44122 138.8.174.1:283 45.237.8.174:257 68.227.219.1:47873 12.172.173.82:993 1.103.144.201:15880 1.1.12.172:44370 222.1.1.173:61278 1.187.1.1:23465 198.125.100.1:280 114.59.8.174:257 66.134.24.1:47873 93.164.248.234:443 1.24.64.114:15112 1.1.83.92:21853 187.1.1.78:17915 8.174.1.1:48774 61.1.187.0:258 47.198.8.174:257 223.248.31.1:47873 12.172.173.82:995 1.94.63.65:37377 1.1.80.13:45975 174.1.1.70:30948 8.35.1.1:55492 102.8.30.1:287 254.199.3.227:1 129.109.27.8:44545 69.119.123.159:2222 1.91.254.230:4609 0.1.64.121:41318 187.1.1.38:42738 8.39.0.1:3244 82.1.209.1:331 236.149.1.187:257 229.117.95.8:44545 74.92.243.113:50000 1.183.82.100:28168 1.1.75.98:39443 187.1.1.193:39626 1.187.0.1:31098 223.3.227.1:326 104.126.3.227:257 67.255.57.8:44545 213.91.235.146:443 1.37.14.229:56328 1.1.76.80:46234 227.1.1.62:8066 1.209.1.1:22899 99.1.187.1:258 12.243.1.187:1 152.152.46.1:47873 188.48.123.229:995 1.90.104.22:7176 1.1.201.210:27615 225.0.1.47:10650 1.187.1.1:12868 71.3.227.1:340 202.22.1.187:1 241.180.94.1:47873 92.189.214.236:2222 1.103.55.67:46081 1.1.90.89:24478 174.1.1.86:55802 8.174.1.1:18500 55.8.174.1:342 16.164.1.187:1 244.25.165.1:47873 65.30.139.145:995 1.73.161.176:55809 1.1.199.83:42473 187.1.1.98:37143 1.187.1.1:21539 14.3.227.1:280 114.59.13.61:257 68.204.71.1:47873 102.46.139.82:993 1.71.247.10:16131 1.1.149.126:40810 187.1.1.58:41695 1.187.1.1:55492 102.8.35.1:440 91.69.1.187:257 99.116.47.1:47873 81.131.210.167:443 1.103.141.50:29955 1.1.184.176:39507 227.1.1.92:53124 8.174.1.1:36513 232.8.174.1:432 207.63.1.187:257 153.132.82.1:47873 108.6.249.139:443 1.69.133.162:8961 1.1.76.20:10797 187.1.1.139:55460 1.187.1.1:6350 39.1.187.1:268 173.82.0.21:257 86.98.236.1:47873 50.68.204.71:993 1.88.126.94:1219 1.1.85.245:56663 30.0.1.190:52806 8.174.0.1:22493 110.8.174.1:339 54.186.1.187:257 223.91.46.1:47872 78.100.230.10:995 1.181.164.194:58369 1.1.174.101:28420 187.1.1.75:29454 1.187.0.1:22241 138.8.174.1:314 115.126.3.227:257 96.75.237.8:44544 105.103.56.28:2078 1.198.2.51:61955 1.1.174.104:47253 187.1.1.105:26424 3.222.0.1:6208 59.239.18.1:349 192.142.0.20:257 14.82.210.8:44544 90.116.219.167:2222 | |||||||||||||||
| 1652 | "C:\Windows\System32\cmd.exe" /q /c revue\breweries.cmd | C:\Windows\System32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1772 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\IL53 Folder.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2276 | replace C:\Windows\\system32\\rundlr32.exe C:\Users\admin\AppData\Local\Temp /A | C:\Windows\system32\replace.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Replace File Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2300 | rundll32 revue\\nationwide.tmp,DrawThemeIcon | C:\Windows\system32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2848 | "C:\Windows\System32\cmd.exe" /q /c revue\breweries.cmd | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3588 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 228
Read events
1 189
Write events
39
Delete events
0
Modification events
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\IL53 Folder.zip | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1772) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
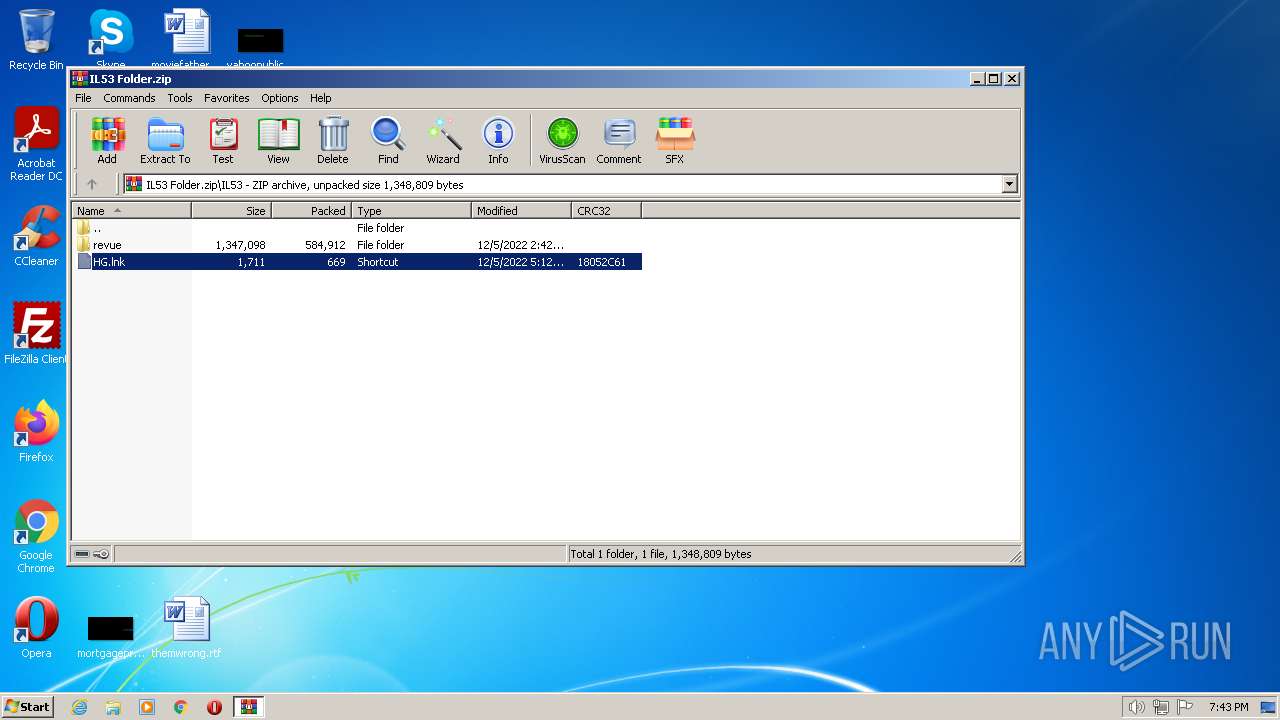
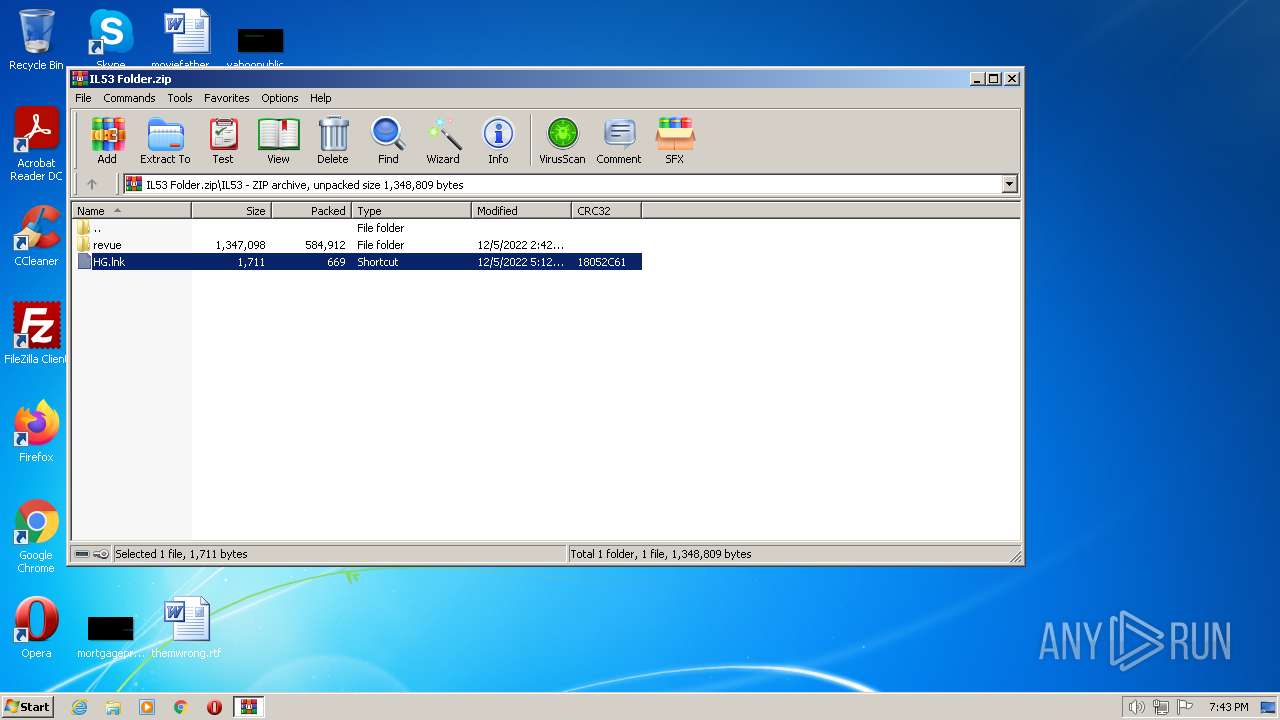
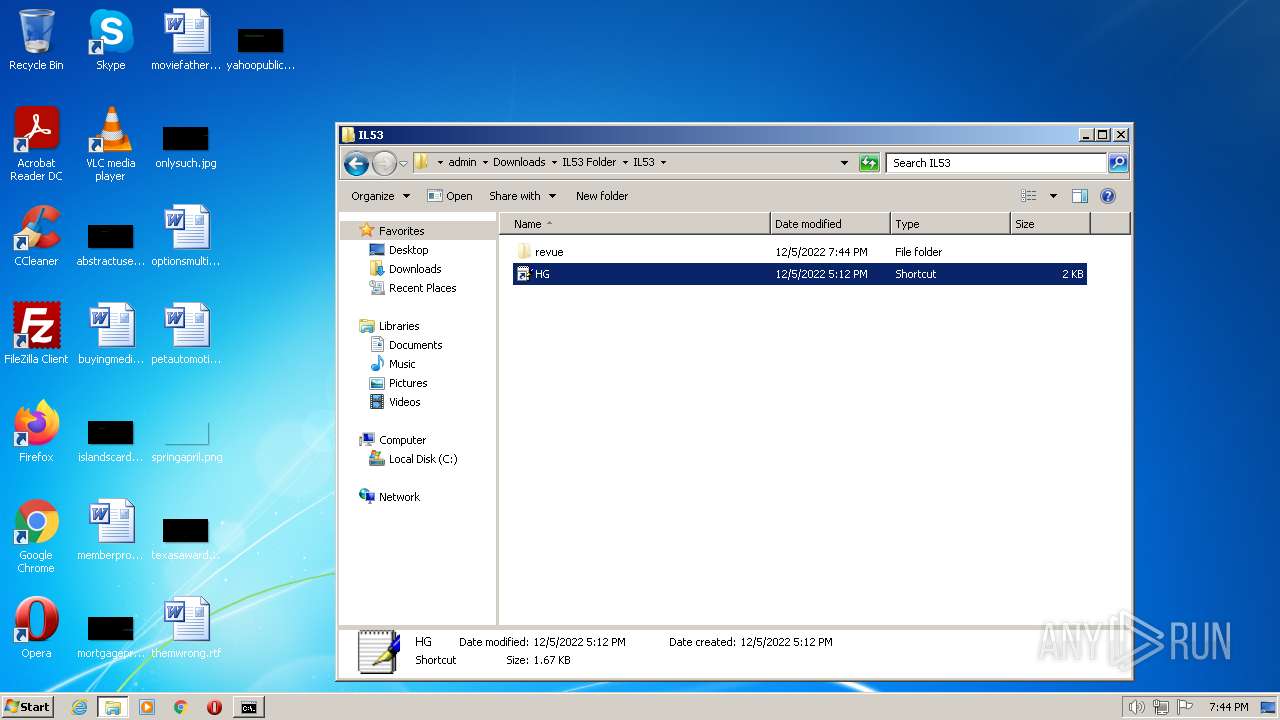
| 1772 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1772.41362\HG.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report