| File name: | powershell-script-obfuscated.ps1 |
| Full analysis: | https://app.any.run/tasks/f72d8d40-c190-49fb-a022-56ae26374c98 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | October 02, 2024, 10:36:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (65536), with no line terminators |
| MD5: | 28CCF59CC18145D043EFD83EA4D136B6 |
| SHA1: | DD172FA854B431E255E6EC7D4631BBCA4EBC7439 |
| SHA256: | D05704C7B30D7CEAC99988D9AC35A8ABB32BBEBE7C90F742968D2F7F6319C0AB |
| SSDEEP: | 6144:O59f1mdzrqK9QxMRSLEt0MphWGvwwppr2rCo2HeRqC0q0npNP81gMkE4IUx7JKp3:SK7WGvjO0eRqS1nkESxFKZ |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 3580)
ASYNCRAT has been detected (SURICATA)
- powershell.exe (PID: 3580)
SUSPICIOUS
CSC.EXE is used to compile C# code
- csc.exe (PID: 6200)
Executable content was dropped or overwritten
- csc.exe (PID: 6200)
Contacting a server suspected of hosting an CnC
- powershell.exe (PID: 3580)
Checks for external IP
- svchost.exe (PID: 2256)
- powershell.exe (PID: 3580)
Connects to unusual port
- powershell.exe (PID: 3580)
Uses NETSH.EXE to add a firewall rule or allowed programs
- powershell.exe (PID: 3580)
INFO
Application launched itself
- chrome.exe (PID: 1220)
- chrome.exe (PID: 1124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
152
Monitored processes
22
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --headless --use-angle=swiftshader-webgl --headless --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --mojo-platform-channel-handle=1456 --field-trial-handle=1464,i,13856406382312125261,16875837814412588582,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --headless --remote-debugging-port=9222 --allow-pre-commit-input --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2696 --field-trial-handle=1464,i,13856406382312125261,16875837814412588582,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --remote-debugging-port=9222 --user-data-dir="C:\Users\admin\AppData\Local\Microsoft\Edge\Backup Data" --profile-directory="Default" --headless --window-position=-10000,-10000 https://www.google.com | C:\Program Files\Google\Chrome\Application\chrome.exe | powershell.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 4294967295 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --remote-debugging-port=9222 --user-data-dir="C:\Users\admin\AppData\Local\Google\Chrome\Backup Data" --profile-directory="Default" --headless --window-position=-10000,-10000 https://www.google.com | C:\Program Files\Google\Chrome\Application\chrome.exe | powershell.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 4294967295 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1280 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\Backup Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\Backup Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x220,0x224,0x228,0x1e0,0x22c,0x7fffd15edc40,0x7fffd15edc4c,0x7fffd15edc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --headless --use-angle=swiftshader-webgl --headless --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --mojo-platform-channel-handle=1452 --field-trial-handle=1456,i,11632543939902642120,4859848307339430251,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2132 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
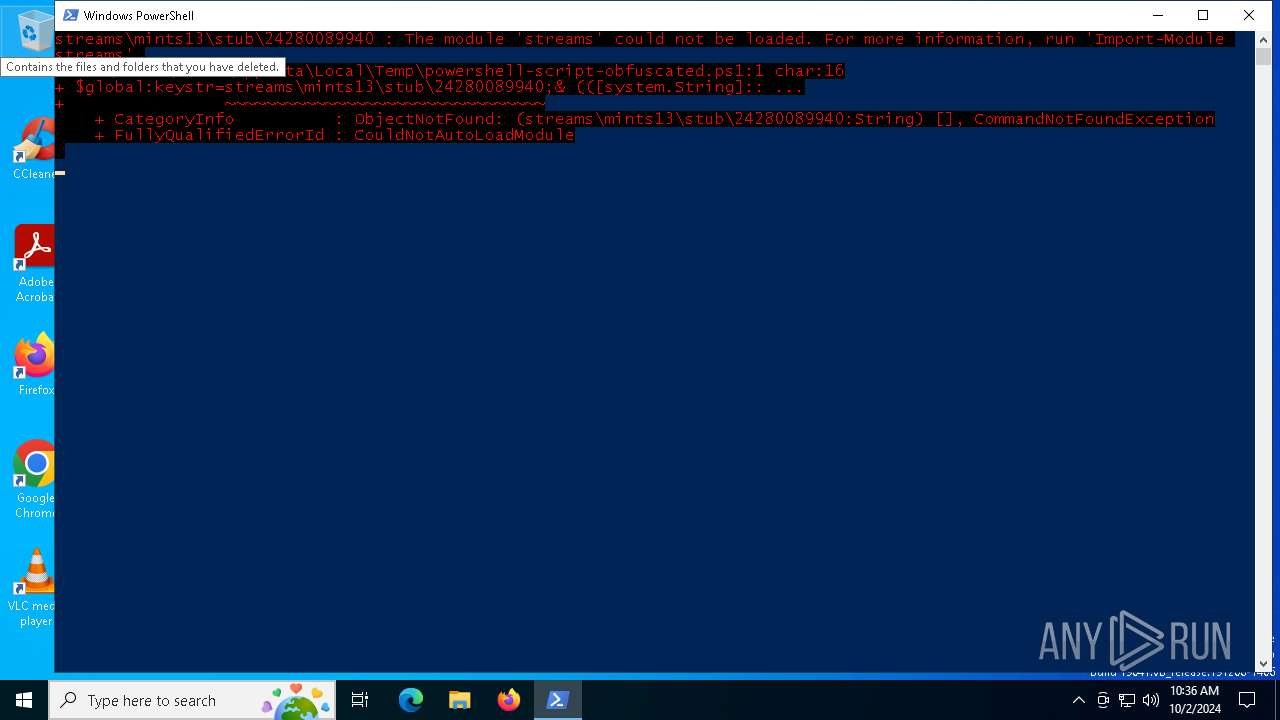
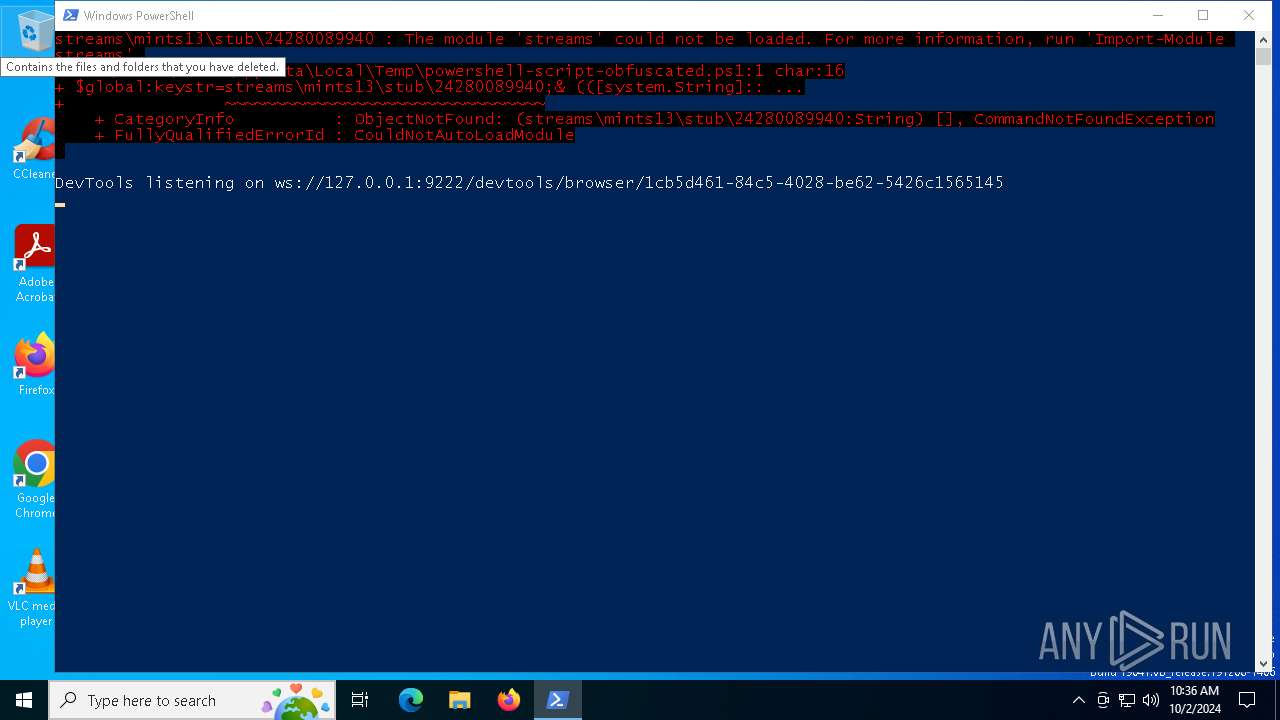
| 3580 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\AppData\Local\Temp\powershell-script-obfuscated.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 151
Read events
22 145
Write events
6
Delete events
0
Modification events
| (PID) Process: | (1220) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1220) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1220) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1124) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1124) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1124) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
Executable files
1
Suspicious files
82
Text files
39
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6200 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC77A745FCA1E546ECBEE441E70BE8D14.TMP | binary | |
MD5:55AE13108E3EC86119BE746E82E20189 | SHA256:C61D01F81B92C5858B6DC4933BCA2EA5075A3D43B233FC61CCB2B904DB116F55 | |||
| 6200 | csc.exe | C:\Users\admin\AppData\Local\Temp\nrjagt0z.dll | executable | |
MD5:A1812871D20415010B35473F5A303A48 | SHA256:590529E27AADF6D0B03697227B387A963C6CD02682B44504A13A3AEB21C404DA | |||
| 3580 | powershell.exe | C:\Users\admin\AppData\Local\Temp\nrjagt0z.cmdline | text | |
MD5:30DBED96EA8E580D1CD3BE34E354DE54 | SHA256:87DBE038478A664D081526DB898D50B6D86F2EB0786FE3F6C2D2987EEC3BBB44 | |||
| 6200 | csc.exe | C:\Users\admin\AppData\Local\Temp\nrjagt0z.out | text | |
MD5:612375792EE5E7C2D797BCBC82666E75 | SHA256:DDF20BC33A965A0BCF5864154BAD0C03FF668976A099858E35261B2D6B2C41CB | |||
| 1220 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\Backup Data\DevToolsActivePort | text | |
MD5:07669690476A74D0FE95D2F73E164F00 | SHA256:48CB31AE3CB64104C7D3E0680E7AF72B27725D66BC9D31A03FB56DC4EAFA6EDB | |||
| 3580 | powershell.exe | C:\Users\admin\AppData\Local\Google\Chrome\Backup Data\Default\Network\Cookies | sqlite | |
MD5:06AD9E737639FDC745B3B65312857109 | SHA256:C8925892CA8E213746633033AE95ACFB8DD9531BC376B82066E686AC6F40A404 | |||
| 1220 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\Backup Data\Crashpad\settings.dat | binary | |
MD5:6FB51541948BB9FB8306A72198BCF29A | SHA256:360683F7D230C617E05C9118CE149900E854FD4BDF2B569B3DB7DF4D244FF002 | |||
| 3580 | powershell.exe | C:\Users\admin\AppData\Local\Google\Chrome\Backup Data\Local State | binary | |
MD5:414B7F9E82EE13FB08D39D366B2FBEC8 | SHA256:6F9AD831D38FF839C0EE3593CC5452D7BE31D9725EE81D3E7AD20E4D91736971 | |||
| 1220 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\Backup Data\Default\Code Cache\wasm\index | binary | |
MD5:54CB446F628B2EA4A5BCE5769910512E | SHA256:FBCFE23A2ECB82B7100C50811691DDE0A33AA3DA8D176BE9882A9DB485DC0F2D | |||
| 1220 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\Backup Data\Default\Local Storage\leveldb\000001.dbtmp | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
73
DNS requests
29
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6664 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7080 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4308 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2708 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2708 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6028 | wermgr.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3580 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/138.199.36.199/country | unknown | — | — | shared |
3580 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/138.199.36.199/city | unknown | — | — | shared |
3580 | powershell.exe | GET | 200 | 193.122.130.0:80 | http://checkip.dyndns.org/ | unknown | — | — | malicious |
3580 | powershell.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/138.199.36.199/region | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7108 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6664 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7108 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7080 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7080 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
r3m13l24o2npkbx.top |
| unknown |
api.ipify.org |
| shared |
go.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3580 | powershell.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3580 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
2256 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
3580 | powershell.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
3580 | powershell.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
3580 | powershell.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup - checkip.dyndns.org |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
3580 | powershell.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
3580 | powershell.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ipinfo.io |
7 ETPRO signatures available at the full report
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\Backup Data directory exists )
|
chrome.exe | [1002/103653.030:ERROR:interface_endpoint_client.cc(707)] Message 0 rejected by interface blink.mojom.WidgetHost
|
chrome.exe | [1002/103653.149:INFO:CONSOLE(88)] "Autofocus processing was blocked because a document already has a focused element.", source: https://www.google.com/ (88)
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Microsoft\Edge\Backup Data directory exists )
|
chrome.exe | [1002/103700.263:INFO:CONSOLE(88)] "Autofocus processing was blocked because a document already has a focused element.", source: https://www.google.com/ (88)
|