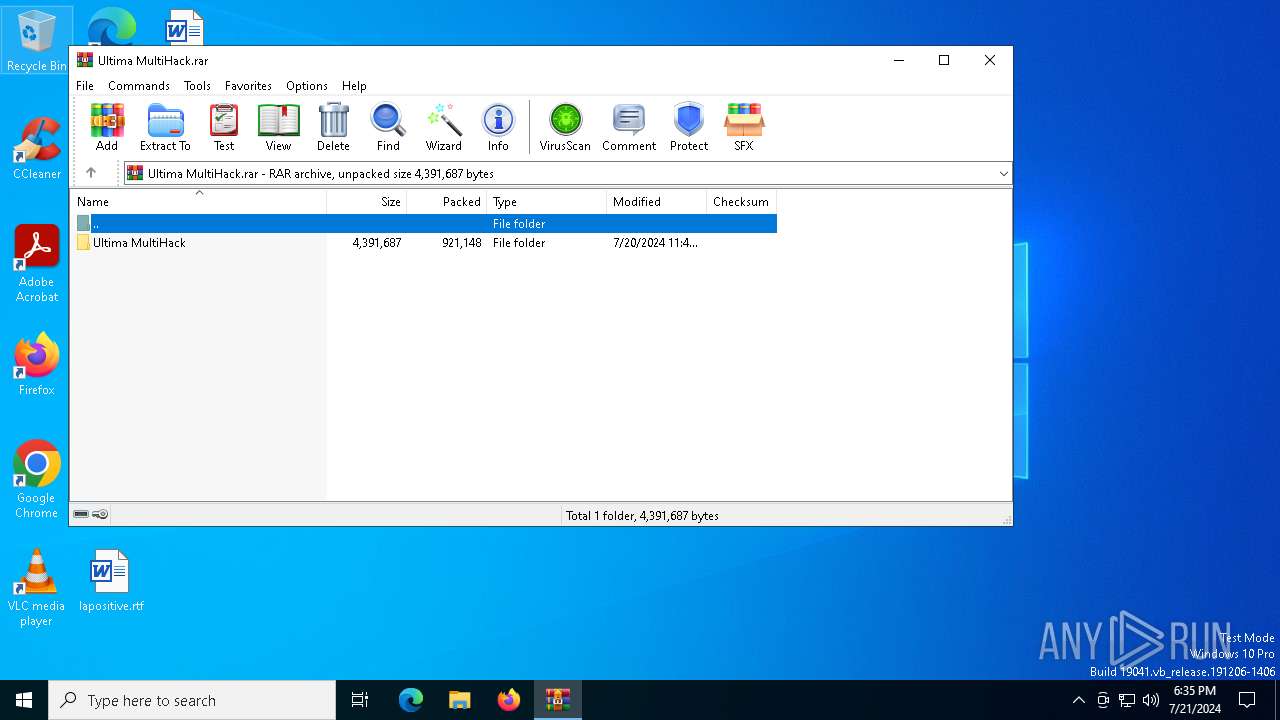
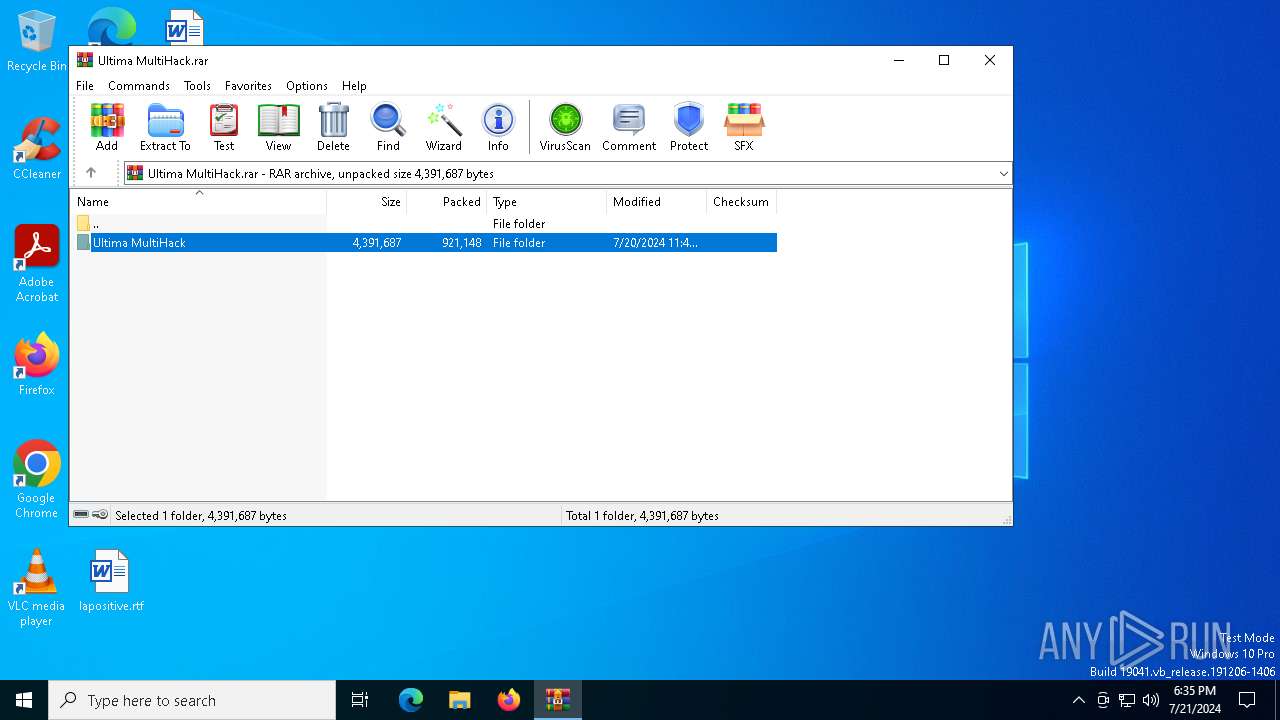
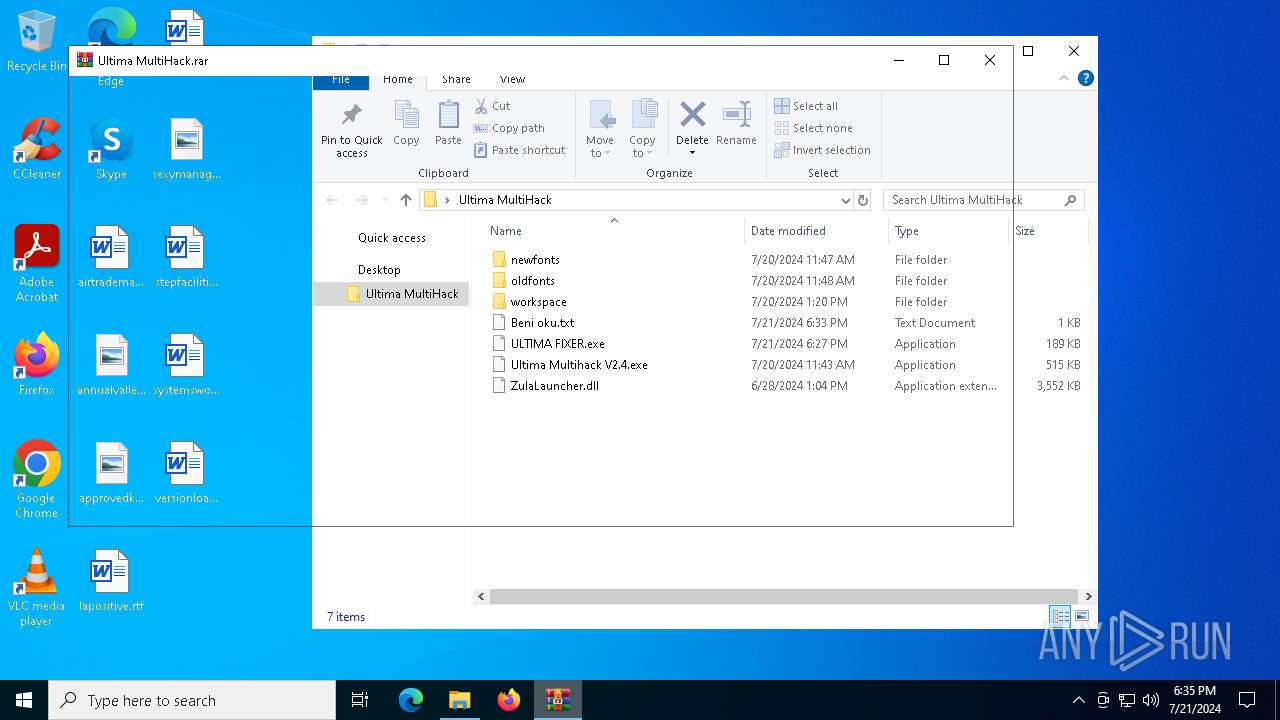
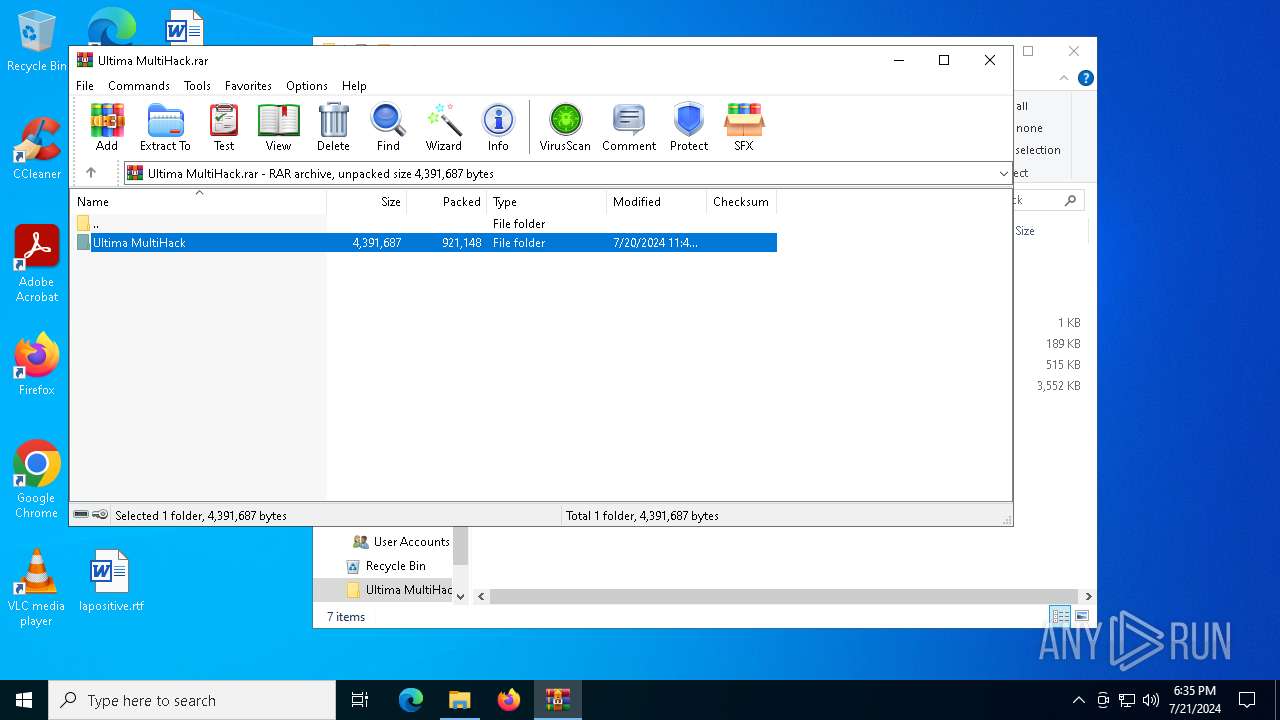
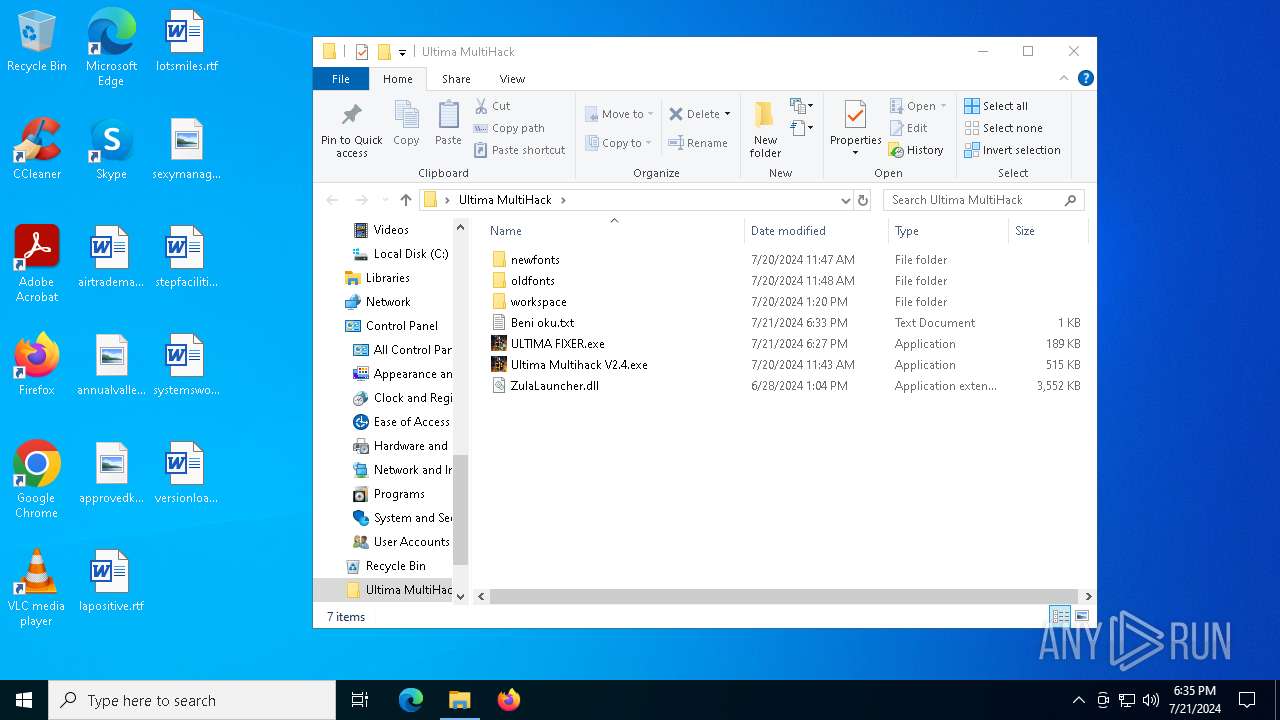
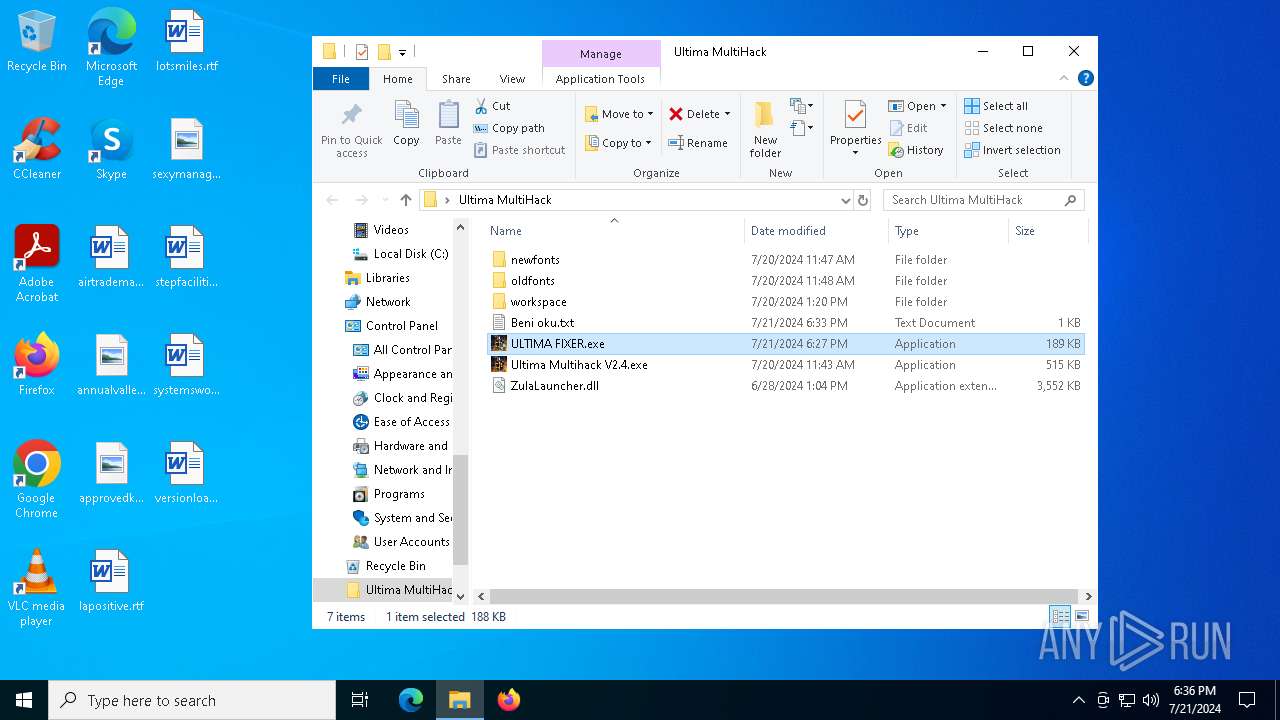
| File name: | Ultima MultiHack.rar |
| Full analysis: | https://app.any.run/tasks/6a7f975b-a4a8-4b08-8723-b8fec1852914 |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | July 21, 2024, 18:34:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A09A8CABB50E56464134342B7F592BC9 |
| SHA1: | B27265D1AD48A2FA0755EF858D448A0CE1D7A79F |
| SHA256: | D024F9D679126FDDB8ACB96726F0B1745FC5DFBD56319B9B8197D59A24FDA952 |
| SSDEEP: | 49152:ugYEFbCNYC1j+43tBBmQ9BabS3bCOouM2jPvgpW2+uc71bOM1Giw9QO/1WW1C9PF:dsx1j+ouQ9obyeOXg02hc7ltKr/1N1Cr |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6800)
- ULTICHEATS.EXE (PID: 7792)
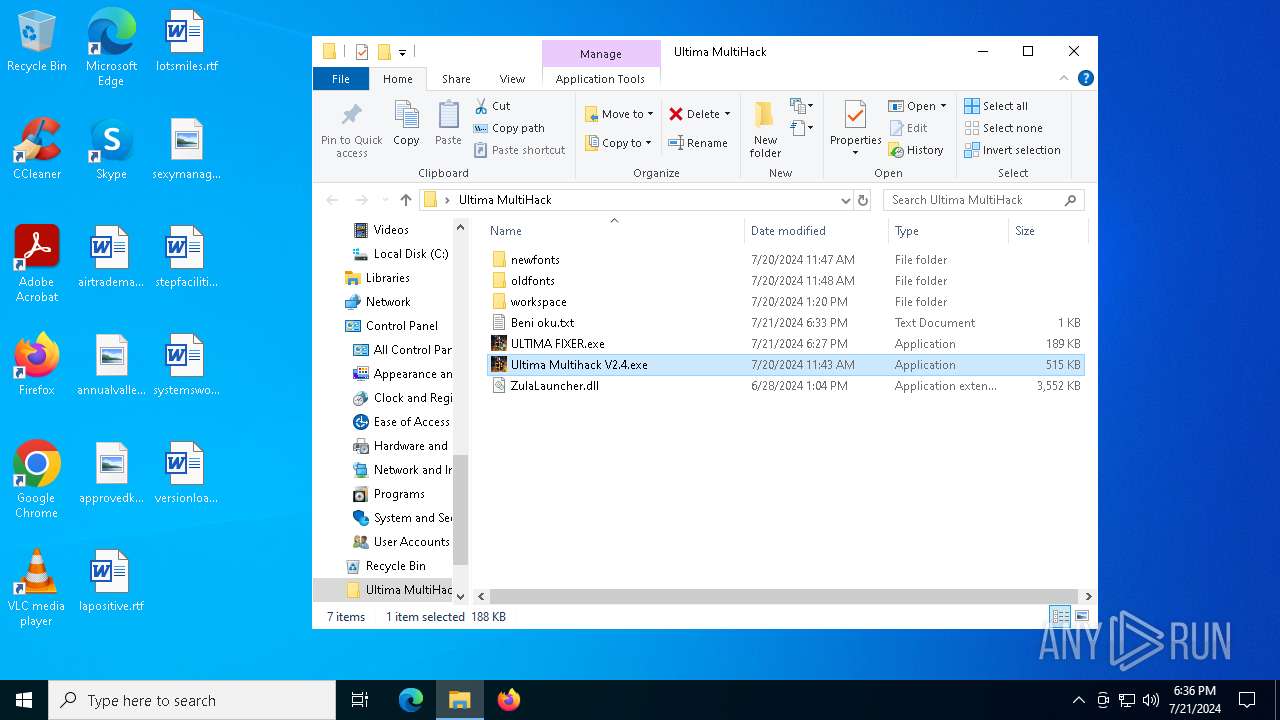
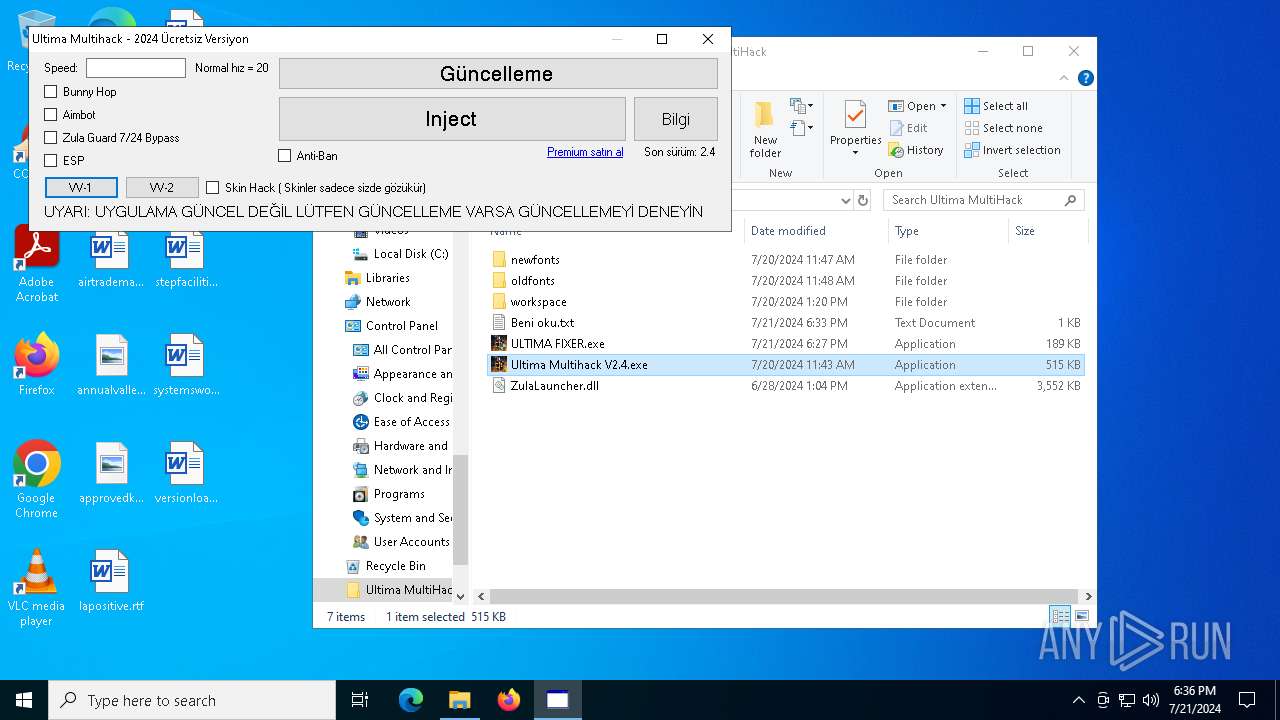
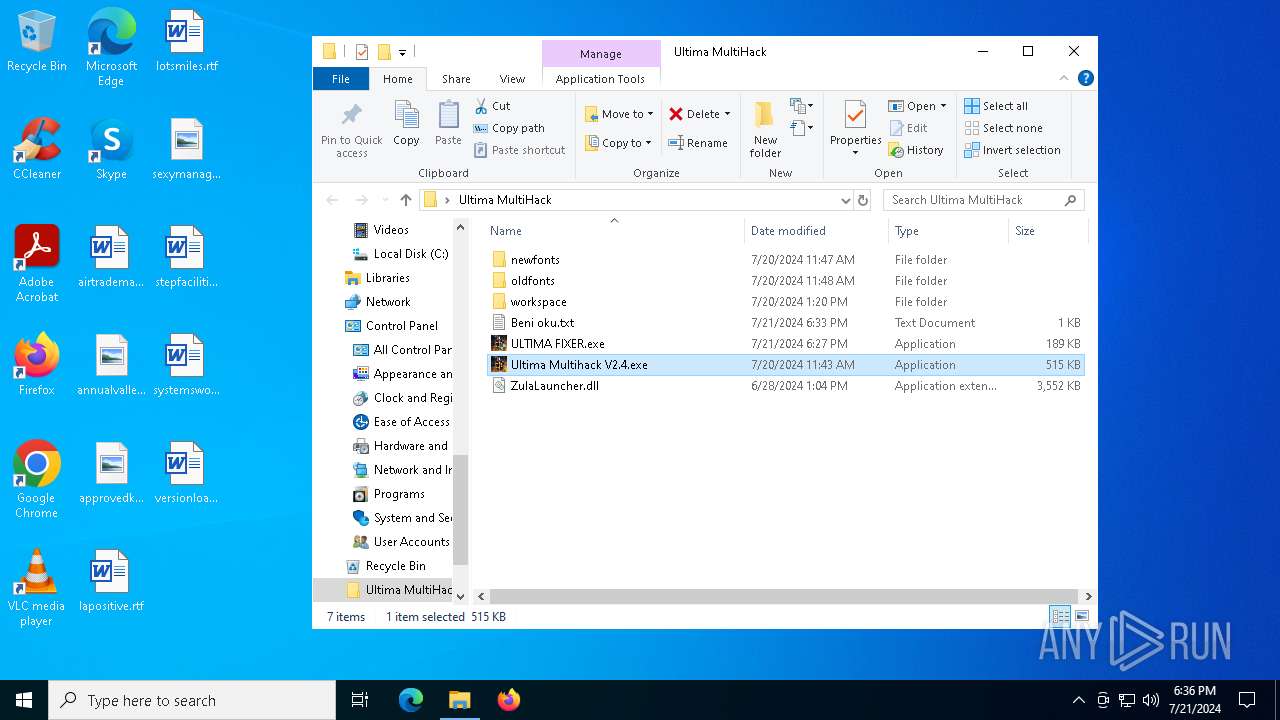
- Ultima Multihack V2.4.exe (PID: 6112)
- ULTINJ.EXE (PID: 6032)
- csrss.exe (PID: 7588)
Disables Windows Defender
- reg.exe (PID: 7132)
- reg.exe (PID: 5784)
- reg.exe (PID: 6036)
- reg.exe (PID: 7212)
Starts SC.EXE for service management
- cmd.exe (PID: 6396)
- cmd.exe (PID: 5228)
Changes the login/logoff helper path in the registry
- ULTICHEATS.EXE (PID: 7792)
Changes the autorun value in the registry
- ULTICHEATS.EXE (PID: 7792)
- csrss.exe (PID: 6288)
- csrss.exe (PID: 7588)
NjRAT is detected
- ULTINJ.EXE (PID: 6032)
- csrss.exe (PID: 7588)
Create files in the Startup directory
- csrss.exe (PID: 7588)
NJRAT has been detected (YARA)
- csrss.exe (PID: 7588)
Connects to the CnC server
- csrss.exe (PID: 7588)
NJRAT has been detected (SURICATA)
- csrss.exe (PID: 7588)
SUSPICIOUS
Reads security settings of Internet Explorer
- ULTIMA FIXER.exe (PID: 7300)
- SecHealthUI.exe (PID: 6872)
- Ultima Multihack V2.4.exe (PID: 6112)
- ULTICHEATS.EXE (PID: 7792)
- ULTINJ.EXE (PID: 6032)
- ULTIMA FIXER.exe (PID: 7476)
Reads the date of Windows installation
- ULTIMA FIXER.exe (PID: 7300)
- ULTICHEATS.EXE (PID: 7792)
- Ultima Multihack V2.4.exe (PID: 6112)
- ULTINJ.EXE (PID: 6032)
- ULTIMA FIXER.exe (PID: 7476)
Starts CMD.EXE for commands execution
- ULTIMA FIXER.exe (PID: 7300)
- ULTICHEATS.EXE (PID: 7792)
- ULTIMA FIXER.exe (PID: 7476)
Executing commands from a ".bat" file
- ULTIMA FIXER.exe (PID: 7300)
- ULTIMA FIXER.exe (PID: 7476)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 6396)
- cmd.exe (PID: 5228)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6396)
- cmd.exe (PID: 5228)
Starts SC.EXE for service management
- cmd.exe (PID: 6396)
- cmd.exe (PID: 5228)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6396)
- cmd.exe (PID: 5228)
Downloads file from URI
- powershell.exe (PID: 7936)
- powershell.exe (PID: 8028)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 6396)
- cmd.exe (PID: 5228)
The process creates files with name similar to system file names
- ULTICHEATS.EXE (PID: 7792)
- ULTINJ.EXE (PID: 6032)
Executable content was dropped or overwritten
- ULTICHEATS.EXE (PID: 7792)
- Ultima Multihack V2.4.exe (PID: 6112)
- ULTINJ.EXE (PID: 6032)
- csrss.exe (PID: 7588)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6104)
- cmd.exe (PID: 4508)
Starts itself from another location
- ULTICHEATS.EXE (PID: 7792)
- ULTINJ.EXE (PID: 6032)
Reads Internet Explorer settings
- ULTIMAMULTI2024.EXE (PID: 6280)
Connects to unusual port
- csrss.exe (PID: 6288)
- csrss.exe (PID: 7588)
Start notepad (likely ransomware note)
- csrss.exe (PID: 6288)
Uses NETSH.EXE to add a firewall rule or allowed programs
- csrss.exe (PID: 7588)
Contacting a server suspected of hosting an CnC
- csrss.exe (PID: 7588)
INFO
Manual execution by a user
- ULTIMA FIXER.exe (PID: 7300)
- ULTIMA FIXER.exe (PID: 2328)
- Ultima Multihack V2.4.exe (PID: 6112)
- ULTIMA FIXER.exe (PID: 7476)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6800)
Checks supported languages
- ULTIMA FIXER.exe (PID: 7300)
- SecHealthUI.exe (PID: 6872)
- Ultima Multihack V2.4.exe (PID: 6112)
- ULTIMAMULTI2024.EXE (PID: 6280)
- ULTICHEATS.EXE (PID: 7792)
- ULTINJ.EXE (PID: 6032)
- csrss.exe (PID: 6288)
- csrss.exe (PID: 7588)
- ULTIMA FIXER.exe (PID: 7476)
Create files in a temporary directory
- ULTIMA FIXER.exe (PID: 7300)
- Ultima Multihack V2.4.exe (PID: 6112)
- ULTIMA FIXER.exe (PID: 7476)
Reads the computer name
- ULTIMA FIXER.exe (PID: 7300)
- SecHealthUI.exe (PID: 6872)
- Ultima Multihack V2.4.exe (PID: 6112)
- ULTICHEATS.EXE (PID: 7792)
- ULTIMAMULTI2024.EXE (PID: 6280)
- ULTINJ.EXE (PID: 6032)
- csrss.exe (PID: 6288)
- csrss.exe (PID: 7588)
- ULTIMA FIXER.exe (PID: 7476)
Process checks computer location settings
- ULTIMA FIXER.exe (PID: 7300)
- Ultima Multihack V2.4.exe (PID: 6112)
- ULTICHEATS.EXE (PID: 7792)
- ULTINJ.EXE (PID: 6032)
- ULTIMA FIXER.exe (PID: 7476)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7936)
- powershell.exe (PID: 8028)
Checks proxy server information
- powershell.exe (PID: 7936)
- powershell.exe (PID: 8028)
UPX packer has been detected
- ULTIMA FIXER.exe (PID: 7300)
Disables trace logs
- powershell.exe (PID: 7936)
- powershell.exe (PID: 8028)
Creates files or folders in the user directory
- ULTINJ.EXE (PID: 6032)
- csrss.exe (PID: 7588)
Reads the machine GUID from the registry
- ULTIMAMULTI2024.EXE (PID: 6280)
- csrss.exe (PID: 7588)
Reads Environment values
- csrss.exe (PID: 7588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
NjRat
(PID) Process(7588) csrss.exe
C2jvjv2044duck33.duckdns.org
Ports5552
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\0ce256616b847d6ba32935097dcc5537
Splitter|'|'|
Versionim523
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
196
Monitored processes
51
Malicious processes
8
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v DisableRegistryTools /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2072 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2328 | "C:\Users\admin\Desktop\Ultima MultiHack\ULTIMA FIXER.exe" | C:\Users\admin\Desktop\Ultima MultiHack\ULTIMA FIXER.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2360 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v DisableTaskMgr /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2408 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Roaming\csrss.exe" "csrss.exe" ENABLE | C:\Windows\SysWOW64\netsh.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3152 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3400 | C:\Windows\System32\SecurityHealthHost.exe {E041C90B-68BA-42C9-991E-477B73A75C90} -Embedding | C:\Windows\System32\SecurityHealthHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Security Health Host Exit code: 0 Version: 4.18.1907.16384 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4024 | notepad | C:\Windows\SysWOW64\notepad.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | C:\Windows\System32\SecurityHealthHost.exe {E041C90B-68BA-42C9-991E-477B73A75C90} -Embedding | C:\Windows\System32\SecurityHealthHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Security Health Host Exit code: 0 Version: 4.18.1907.16384 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 278
Read events
32 967
Write events
311
Delete events
0
Modification events
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ultima MultiHack.rar | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C00000000000000010000000083FFFF0083FFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
10
Suspicious files
1
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.21682\Ultima MultiHack\Ultima Multihack V2.4.exe | executable | |
MD5:77AF29D119090535B678909637B50A7B | SHA256:6F0B668F7F2BB2D08AEB7ED32AF70496064EBBF527F4A8EDDB94E1B47F4833C7 | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.21682\Ultima MultiHack\ULTIMA FIXER.exe | executable | |
MD5:A1B9891034AC4D37A7B1CC50E89DA311 | SHA256:C96021DBC189AC871841CD06C7CB78FEEEDED68729EEFBFAFF18AD5425F7DB97 | |||
| 7936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_glmlfiqv.4vr.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jkenzwwa.jst.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.21682\Ultima MultiHack\Beni oku.txt | text | |
MD5:57FEE35BC4DDB35BD3F7478B98524DCA | SHA256:AC52417BB488D8A2E01C5F5EF8E1023DFEABFA059A1DA718778AB617FFEE5E2C | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.21682\Ultima MultiHack\ZulaLauncher.dll | executable | |
MD5:CADD865A049BFD30D61BCD2533194E88 | SHA256:3A0A0B13FD474E805CCB5DD07A39A2F82326EBC36D911114C2346153D5E727C9 | |||
| 8028 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i2p0zl2m.zra.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6800 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6800.21682\Ultima MultiHack\oldfonts\ultiInject.exe | executable | |
MD5:0A1C8BDEC0475A012049AE3EB0E7A0EF | SHA256:B58E20B5E2888CC7B0716BB858BE28FF328D35E487F5C64DADC73CF6C3DD5DF8 | |||
| 7476 | ULTIMA FIXER.exe | C:\Users\admin\AppData\Local\Temp\D79D.tmp\D79E.tmp\D79F.bat | text | |
MD5:F08DA42187B78D04D21C8498CB0CDA50 | SHA256:1633D8B4E65CF51C127FC2222A96EA08E7BBFD0D028F7E712C4E3E7291E1A211 | |||
| 7588 | csrss.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\0ce256616b847d6ba32935097dcc5537.exe | executable | |
MD5:FDBDBBDD177068BE5407B463333646BC | SHA256:9D276C5382BD697BF7AE23831ADE6AA6DB48874472865DB34DCFF66BC1108004 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
51
DNS requests
26
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5628 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7856 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4716 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5620 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3656 | backgroundTaskHost.exe | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2760 | svchost.exe | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
download1323.mediafire.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
www.mediafire.com |
| shared |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2168 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2168 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2168 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2168 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2168 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2168 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2168 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
7588 | csrss.exe | Malware Command and Control Activity Detected | ET MALWARE Generic njRAT/Bladabindi CnC Activity (ll) |
2168 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
6 ETPRO signatures available at the full report