| File name: | Dogusign Reader 1.26g.msi |
| Full analysis: | https://app.any.run/tasks/a1531798-9771-4adb-ad8a-d2acd581a0a7 |
| Verdict: | Malicious activity |
| Threats: | HijackLoader is a modular malware acting as a vehicle for distributing different types of malicious software on compromised systems. It gained prominence during the summer of 2023 and has since been used in multiple attacks against organizations from various sectors, including hospitality businesses. |
| Analysis date: | January 10, 2025, 22:37:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
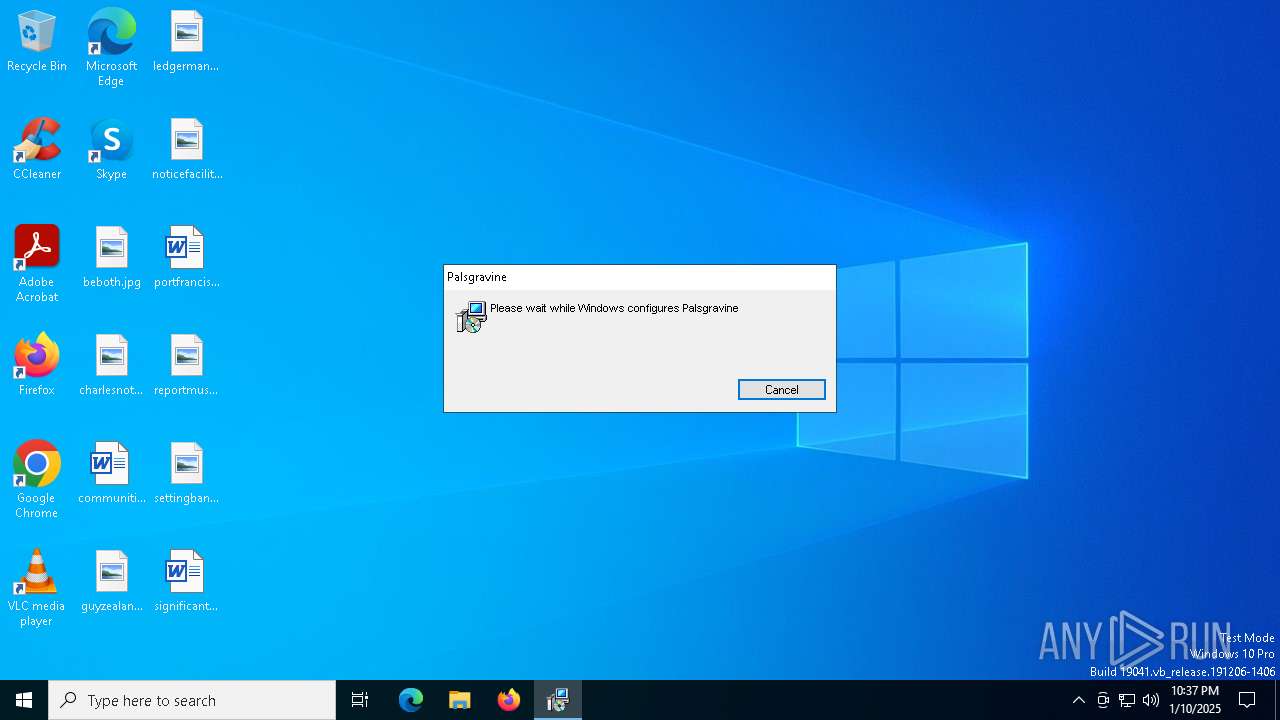
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Palsgravine, Author: Chaplainry Strudel, Keywords: Installer, Comments: This installer database contains the logic and data required to install Palsgravine., Template: Intel;1033, Revision Number: {823F9B91-5B1C-4363-89EB-5E534851E2CD}, Create Time/Date: Fri Jan 10 04:07:28 2025, Last Saved Time/Date: Fri Jan 10 04:07:28 2025, Number of Pages: 500, Number of Words: 10, Name of Creating Application: WiX Toolset (4.0.0.0), Security: 2 |
| MD5: | 35F774E65E57F419FFF8D8F74945EA51 |
| SHA1: | C3E1D2D50A9BBCA445576E0D71C6984CC1DC60BB |
| SHA256: | D00A3E22E53210ACBD5C3E39B85332E3D47C8EC001D2BBF7A13ABB07427BBBA2 |
| SSDEEP: | 98304:u6Q1TY/CdEG26wjPcEU9Z3eWXCiifD9sjT9abLW1WwqsZydr4oor437Ae5AKqSK3:UK/+bHYenoRPGg |
MALICIOUS
LUMMA mutex has been found
- explorer.exe (PID: 6732)
Connects to the CnC server
- explorer.exe (PID: 6764)
HIJACKLOADER has been detected (YARA)
- cmd.exe (PID: 4980)
Actions looks like stealing of personal data
- explorer.exe (PID: 6732)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6496)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6444)
Executable content was dropped or overwritten
- RttHlp.exe (PID: 2800)
- RttHlp.exe (PID: 3988)
Starts itself from another location
- RttHlp.exe (PID: 2800)
- RttHlp.exe (PID: 3988)
Connects to the server without a host name
- explorer.exe (PID: 6764)
Starts CMD.EXE for commands execution
- RttHlp.exe (PID: 3988)
- RttHlp.exe (PID: 1804)
Connects to unusual port
- explorer.exe (PID: 6764)
INFO
The sample compiled with english language support
- msiexec.exe (PID: 6248)
- msiexec.exe (PID: 6444)
- RttHlp.exe (PID: 3988)
- RttHlp.exe (PID: 2800)
Checks supported languages
- msiexec.exe (PID: 6444)
- RttHlp.exe (PID: 2800)
- RttHlp.exe (PID: 3988)
- RttHlp.exe (PID: 1804)
Reads the computer name
- msiexec.exe (PID: 6444)
- RttHlp.exe (PID: 2800)
- RttHlp.exe (PID: 3988)
- RttHlp.exe (PID: 1804)
Manages system restore points
- SrTasks.exe (PID: 7096)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6444)
Creates a software uninstall entry
- msiexec.exe (PID: 6444)
Creates files or folders in the user directory
- msiexec.exe (PID: 6444)
- RttHlp.exe (PID: 2800)
Reads the software policy settings
- explorer.exe (PID: 6732)
Application based on Golang
- explorer.exe (PID: 6764)
Create files in a temporary directory
- RttHlp.exe (PID: 3988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Palsgravine |
| Author: | Chaplainry Strudel |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Palsgravine. |
| Template: | Intel;1033 |
| RevisionNumber: | {823F9B91-5B1C-4363-89EB-5E534851E2CD} |
| CreateDate: | 2025:01:10 04:07:28 |
| ModifyDate: | 2025:01:10 04:07:28 |
| Pages: | 500 |
| Words: | 10 |
| Software: | WiX Toolset (4.0.0.0) |
| Security: | Read-only recommended |
Total processes
142
Monitored processes
14
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1804 | C:\Users\admin\AppData\Roaming\configRemote_PZ4\YEGPXJGHGKZZAQPHDPP\RttHlp.exe | C:\Users\admin\AppData\Roaming\configRemote_PZ4\YEGPXJGHGKZZAQPHDPP\RttHlp.exe | — | RttHlp.exe | |||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: IObit RttHlp Exit code: 1 Version: 11.0.0.0 Modules
| |||||||||||||||
| 2160 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | RttHlp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2800 | "C:\Users\admin\AppData\Local\Yarrow\RttHlp.exe" | C:\Users\admin\AppData\Local\Yarrow\RttHlp.exe | msiexec.exe | ||||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: IObit RttHlp Exit code: 0 Version: 11.0.0.0 Modules
| |||||||||||||||
| 3952 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3988 | C:\Users\admin\AppData\Roaming\configRemote_PZ4\RttHlp.exe | C:\Users\admin\AppData\Roaming\configRemote_PZ4\RttHlp.exe | RttHlp.exe | ||||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: IObit RttHlp Exit code: 1 Version: 11.0.0.0 Modules
| |||||||||||||||
| 4980 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | RttHlp.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Dogusign Reader 1.26g.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6444 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6496 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 495
Read events
3 230
Write events
247
Delete events
18
Modification events
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C16CC948B063DB016019000080190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C16CC948B063DB01601900007C190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C16CC948B063DB0160190000EC190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000C16CC948B063DB0160190000E8190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 48000000000000006733CE48B063DB01601900007C190000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
9
Suspicious files
19
Text files
0
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6444 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6444 | msiexec.exe | C:\Windows\Installer\13aaf9.msi | — | |
MD5:— | SHA256:— | |||
| 6444 | msiexec.exe | C:\Users\admin\AppData\Local\Yarrow\burro.ini | — | |
MD5:— | SHA256:— | |||
| 6444 | msiexec.exe | C:\Windows\Installer\13aafb.msi | — | |
MD5:— | SHA256:— | |||
| 6444 | msiexec.exe | C:\Windows\Temp\~DFBCE65A8167A33EBF.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6444 | msiexec.exe | C:\Users\admin\AppData\Local\Yarrow\magnesium.csv | binary | |
MD5:038C02B1CDCE1B2738C09D9D2B8BBD74 | SHA256:FF5F5110CA6CA5D57DB34EC4EA566D28D4B2535D71540331448711A25A89B3F4 | |||
| 6444 | msiexec.exe | C:\Users\admin\AppData\Local\Yarrow\RttHlp.exe | executable | |
MD5:A2D70FBAB5181A509369D96B682FC641 | SHA256:8AED681AD8D660257C10D2F0E85AE673184055A341901643F27AFC38E5EF8473 | |||
| 6444 | msiexec.exe | C:\Users\admin\AppData\Local\Yarrow\vcl120.bpl | binary | |
MD5:37C89F8997AF129D230837C87997B737 | SHA256:F3EA5D6457089B4C4AB207F0B96DD5F321CDC7B3360CA27CD6ED273EC25D807E | |||
| 6444 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{6b8f5f72-b941-4c8e-997f-1841560fb57f}_OnDiskSnapshotProp | binary | |
MD5:1C49B119A55D94CD000783EE5805DF95 | SHA256:C1343E6F4EFBA12696C49870501F7121B04842069E9B03BD1BA08170202FBC37 | |||
| 6444 | msiexec.exe | C:\Windows\Temp\~DF3E8581C79101625E.TMP | binary | |
MD5:2DDC7016E0E89CA33AE92FD6962E52BE | SHA256:93FF8A1CB0B00D92E8AF51099459BA71A317D5330891028FEB03962C8FBE3060 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
42
DNS requests
21
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3040 | svchost.exe | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3040 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4672 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4672 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3688 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6764 | explorer.exe | POST | 200 | 46.8.232.106:80 | http://46.8.232.106/ | unknown | — | — | malicious |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3040 | svchost.exe | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3040 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6764 | explorer.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
4 ETPRO signatures available at the full report