| File name: | DogusignReader1.26g.msi |
| Full analysis: | https://app.any.run/tasks/4bf36241-2e39-4e28-85cf-730aa73a87db |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 10, 2025, 18:08:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
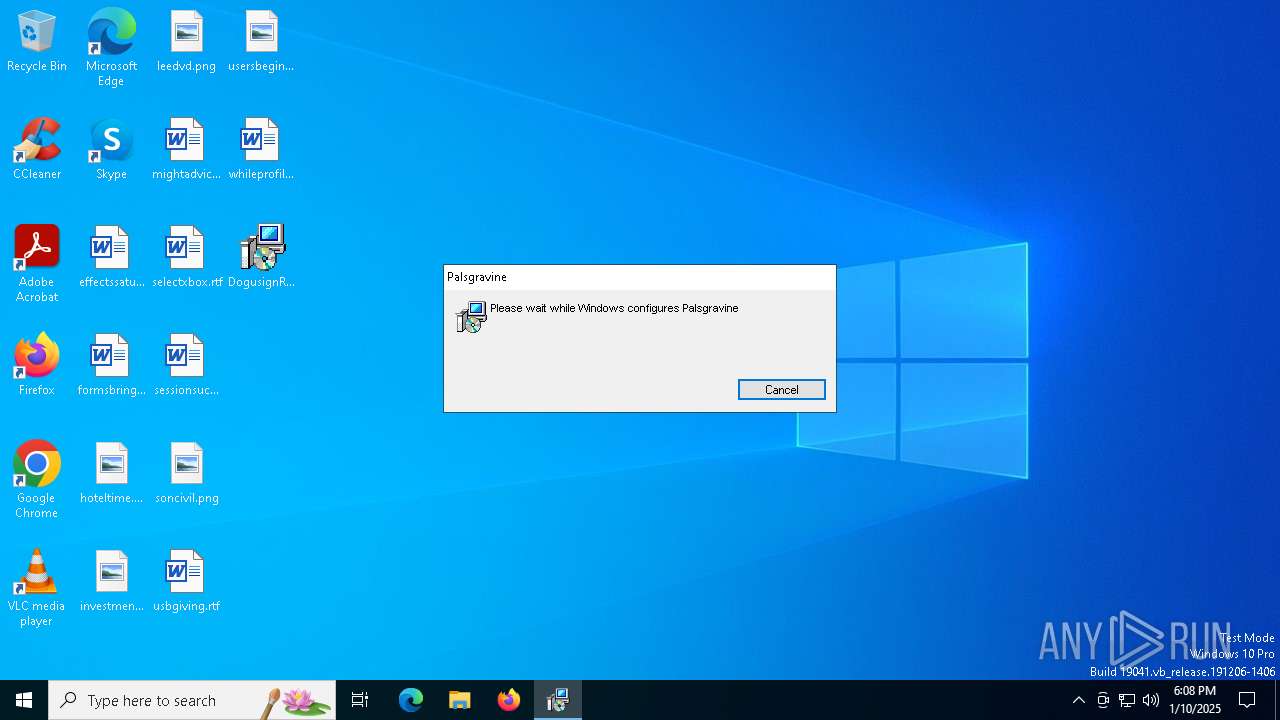
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Palsgravine, Author: Chaplainry Strudel, Keywords: Installer, Comments: This installer database contains the logic and data required to install Palsgravine., Template: Intel;1033, Revision Number: {823F9B91-5B1C-4363-89EB-5E534851E2CD}, Create Time/Date: Fri Jan 10 04:07:28 2025, Last Saved Time/Date: Fri Jan 10 04:07:28 2025, Number of Pages: 500, Number of Words: 10, Name of Creating Application: WiX Toolset (4.0.0.0), Security: 2 |
| MD5: | 35F774E65E57F419FFF8D8F74945EA51 |
| SHA1: | C3E1D2D50A9BBCA445576E0D71C6984CC1DC60BB |
| SHA256: | D00A3E22E53210ACBD5C3E39B85332E3D47C8EC001D2BBF7A13ABB07427BBBA2 |
| SSDEEP: | 98304:u6Q1TY/CdEG26wjPcEU9Z3eWXCiifD9sjT9abLW1WwqsZydr4oor437Ae5AKqSK3:UK/+bHYenoRPGg |
MALICIOUS
LUMMA mutex has been found
- explorer.exe (PID: 3988)
Connects to the CnC server
- explorer.exe (PID: 3836)
SUSPICIOUS
Executable content was dropped or overwritten
- RttHlp.exe (PID: 5472)
- RttHlp.exe (PID: 5036)
Executes as Windows Service
- VSSVC.exe (PID: 1544)
Starts itself from another location
- RttHlp.exe (PID: 5472)
- RttHlp.exe (PID: 5036)
Starts CMD.EXE for commands execution
- RttHlp.exe (PID: 3172)
- RttHlp.exe (PID: 5036)
Connects to the server without a host name
- explorer.exe (PID: 3836)
Connects to unusual port
- explorer.exe (PID: 3836)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3092)
INFO
Reads the computer name
- msiexec.exe (PID: 3092)
- RttHlp.exe (PID: 5472)
- RttHlp.exe (PID: 3172)
The sample compiled with english language support
- RttHlp.exe (PID: 5036)
- RttHlp.exe (PID: 5472)
- msiexec.exe (PID: 3092)
- msiexec.exe (PID: 556)
Manages system restore points
- SrTasks.exe (PID: 776)
Checks supported languages
- RttHlp.exe (PID: 3172)
- RttHlp.exe (PID: 5036)
- msiexec.exe (PID: 3092)
Reads the software policy settings
- explorer.exe (PID: 3988)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3092)
Creates a software uninstall entry
- msiexec.exe (PID: 3092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Palsgravine |
| Author: | Chaplainry Strudel |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Palsgravine. |
| Template: | Intel;1033 |
| RevisionNumber: | {823F9B91-5B1C-4363-89EB-5E534851E2CD} |
| CreateDate: | 2025:01:10 04:07:28 |
| ModifyDate: | 2025:01:10 04:07:28 |
| Pages: | 500 |
| Words: | 10 |
| Software: | WiX Toolset (4.0.0.0) |
| Security: | Read-only recommended |
Total processes
133
Monitored processes
14
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\DogusignReader1.26g.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2744 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | RttHlp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3092 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3172 | C:\Users\admin\AppData\Roaming\configRemote_PZ4\YEGPXJGHGKZZAQPHDPP\RttHlp.exe | C:\Users\admin\AppData\Roaming\configRemote_PZ4\YEGPXJGHGKZZAQPHDPP\RttHlp.exe | — | RttHlp.exe | |||||||||||
User: admin Company: IObit Integrity Level: MEDIUM Description: IObit RttHlp Exit code: 1 Version: 11.0.0.0 Modules
| |||||||||||||||
| 3836 | C:\WINDOWS\SysWOW64\explorer.exe | C:\Windows\SysWOW64\explorer.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3988 | C:\WINDOWS\SysWOW64\explorer.exe | C:\Windows\SysWOW64\explorer.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4308 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | RttHlp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 377
Read events
6 112
Write events
247
Delete events
18
Modification events
| (PID) Process: | (3092) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000428DFA9F8A63DB01140C000074130000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3092) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000428DFA9F8A63DB01140C000074130000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3092) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000008A1DB2A08A63DB01140C000074130000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3092) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000008A1DB2A08A63DB01140C000074130000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3092) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000044E5B6A08A63DB01140C000074130000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3092) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000002C48B9A08A63DB01140C000074130000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3092) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (3092) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000005D6729A18A63DB01140C000074130000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3092) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000024B82BA18A63DB01140C0000A8080000E80300000100000000000000000000003D41435EC885BB408E77AFC355C3748D00000000000000000000000000000000 | |||
| (PID) Process: | (1544) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000964735A18A63DB010806000034080000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
9
Suspicious files
27
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3092 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3092 | msiexec.exe | C:\Windows\Installer\13ba5a.msi | — | |
MD5:— | SHA256:— | |||
| 3092 | msiexec.exe | C:\Users\admin\AppData\Local\Yarrow\burro.ini | — | |
MD5:— | SHA256:— | |||
| 3092 | msiexec.exe | C:\Windows\Installer\13ba5c.msi | — | |
MD5:— | SHA256:— | |||
| 3092 | msiexec.exe | C:\Windows\Temp\~DF66E81F55B3DB1D1E.TMP | binary | |
MD5:468616117F5C0E2F42826FC414CB5F79 | SHA256:FD0D8BEA93F309F3E52BE034926FC396D7C02CA1814652DD3DB7C2121EF5FBD8 | |||
| 3092 | msiexec.exe | C:\Users\admin\AppData\Local\Yarrow\magnesium.csv | binary | |
MD5:038C02B1CDCE1B2738C09D9D2B8BBD74 | SHA256:FF5F5110CA6CA5D57DB34EC4EA566D28D4B2535D71540331448711A25A89B3F4 | |||
| 3092 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:468616117F5C0E2F42826FC414CB5F79 | SHA256:FD0D8BEA93F309F3E52BE034926FC396D7C02CA1814652DD3DB7C2121EF5FBD8 | |||
| 3092 | msiexec.exe | C:\Users\admin\AppData\Local\Yarrow\RttHlp.exe | executable | |
MD5:A2D70FBAB5181A509369D96B682FC641 | SHA256:8AED681AD8D660257C10D2F0E85AE673184055A341901643F27AFC38E5EF8473 | |||
| 3092 | msiexec.exe | C:\Users\admin\AppData\Local\Yarrow\vcl120.bpl | binary | |
MD5:37C89F8997AF129D230837C87997B737 | SHA256:F3EA5D6457089B4C4AB207F0B96DD5F321CDC7B3360CA27CD6ED273EC25D807E | |||
| 3092 | msiexec.exe | C:\Users\admin\AppData\Local\Yarrow\Register.dll | executable | |
MD5:40B9628354EF4E6EF3C87934575545F4 | SHA256:372B14FCE2EB35B264F6D4AEEF7987DA56D951D3A09EF866CF55ED72763CAA12 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
29
DNS requests
8
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4128 | svchost.exe | GET | 200 | 23.48.23.158:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4128 | svchost.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3836 | explorer.exe | POST | 200 | 46.8.232.106:80 | http://46.8.232.106/ | unknown | — | — | malicious |
— | — | POST | 200 | 104.21.48.1:443 | https://relaxanimanjk.rent/api | unknown | text | 18.3 Kb | unknown |
— | — | POST | 200 | 104.21.112.1:443 | https://relaxanimanjk.rent/api | unknown | — | — | unknown |
— | — | POST | 200 | 104.21.64.1:443 | https://relaxanimanjk.rent/api | unknown | text | 13.6 Kb | unknown |
— | — | POST | 200 | 104.21.96.1:443 | https://relaxanimanjk.rent/api | unknown | text | 17 b | unknown |
— | — | POST | 200 | 104.21.48.1:443 | https://relaxanimanjk.rent/api | unknown | text | 2 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.16.204.152:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4128 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4128 | svchost.exe | 23.48.23.158:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.158:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4128 | svchost.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
relaxanimanjk.rent |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3836 | explorer.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
4 ETPRO signatures available at the full report