| File name: | 26508958.docx |
| Full analysis: | https://app.any.run/tasks/99e042b2-7abb-4cd6-81f3-07e1fd56b75e |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | November 14, 2018, 12:39:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 0ADC9FD56F00E4CC7AE5D66CA6B709C0 |
| SHA1: | CC4A2E352459568F4CB420A9FFF00E2191B8264A |
| SHA256: | CF5FBDA88A21986886E93382FE2B338DD4EFE31B758D563CB66F45733690F9C1 |
| SSDEEP: | 192:9VSaw7yMtWNDP0mqQTnhr5OJQT1Q6P55pzUbFTB8GoA6aZkWj6Pq4Pa:9VSaw7yMtiDBLOJQT1Q6DpzSdlxR4Pa |
MALICIOUS
Writes to a start menu file
- notpadd.exe (PID: 2488)
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 3584)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3584)
Application was dropped or rewritten from another process
- 1.cmd (PID: 3576)
- notpadd.exe (PID: 2488)
- notpadd.exe (PID: 328)
LOKIBOT was detected
- notpadd.exe (PID: 328)
Detected artifacts of LokiBot
- notpadd.exe (PID: 328)
Connects to CnC server
- notpadd.exe (PID: 328)
Actions looks like stealing of personal data
- notpadd.exe (PID: 328)
SUSPICIOUS
Creates files in the user directory
- notpadd.exe (PID: 2488)
- EQNEDT32.EXE (PID: 3584)
- notpadd.exe (PID: 328)
- 1.cmd (PID: 3576)
Suspicious files were dropped or overwritten
- EQNEDT32.EXE (PID: 3584)
Starts application with an unusual extension
- EQNEDT32.EXE (PID: 3584)
Executable content was dropped or overwritten
- notpadd.exe (PID: 328)
- 1.cmd (PID: 3576)
- EQNEDT32.EXE (PID: 3584)
Application launched itself
- notpadd.exe (PID: 2488)
Starts itself from another location
- 1.cmd (PID: 3576)
Loads DLL from Mozilla Firefox
- notpadd.exe (PID: 328)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 584)
- WINWORD.EXE (PID: 640)
Creates files in the user directory
- WINWORD.EXE (PID: 584)
- WINWORD.EXE (PID: 640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:10:07 14:11:06 |
| ZipCRC: | 0x82872409 |
| ZipCompressedSize: | 358 |
| ZipUncompressedSize: | 1422 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | dotm.dotm |
|---|---|
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | 1 |
| Characters: | 7 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | SPecialiST RePack |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 7 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 14 |
| LastModifiedBy: | Microsoft |
| RevisionNumber: | 1 |
| CreateDate: | 2017:09:24 17:26:00Z |
| ModifyDate: | 2017:09:24 17:27:00Z |
XMP
| Creator: | Microsoft |
|---|
Total processes
38
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Users\admin\AppData\Roaming\ghdet\notpadd.exe" | C:\Users\admin\AppData\Roaming\ghdet\notpadd.exe | notpadd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 584 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\26508958.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 640 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\26508958.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2488 | "C:\Users\admin\AppData\Roaming\ghdet\notpadd.exe" | C:\Users\admin\AppData\Roaming\ghdet\notpadd.exe | 1.cmd | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3576 | C:\Users\admin\AppData\Local\Temp\1.cmd | C:\Users\admin\AppData\Local\Temp\1.cmd | EQNEDT32.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3584 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
Total events
1 576
Read events
1 142
Write events
413
Delete events
21
Modification events
| (PID) Process: | (584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | kue |
Value: 6B75650048020000010000000000000000000000 | |||
| (PID) Process: | (584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (584) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1299054608 | |||
| (PID) Process: | (584) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299054720 | |||
| (PID) Process: | (584) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299054721 | |||
| (PID) Process: | (584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 4802000072D2F61E177CD40100000000 | |||
| (PID) Process: | (584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 8xe |
Value: 387865004802000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 8xe |
Value: 387865004802000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
4
Suspicious files
25
Text files
11
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA16B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{864E21E8-399E-4477-86AA-7CF1DAF40537} | — | |
MD5:— | SHA256:— | |||
| 584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{C9E3E1E8-113D-431D-8E6D-1658295D1BC4} | — | |
MD5:— | SHA256:— | |||
| 584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{00D52117-DC18-45F7-985B-C36E3EFFBD1D}.tmp | — | |
MD5:— | SHA256:— | |||
| 584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{35D1D8E9-F3AB-448C-9639-747DA36267B5}.tmp | — | |
MD5:— | SHA256:— | |||
| 584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{0D92C514-96E2-4F1B-B2E0-1DFC8DB577C1}.tmp | — | |
MD5:— | SHA256:— | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9BD9.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\783EEB81.doc | — | |
MD5:— | SHA256:— | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\197D3A37.doc | — | |
MD5:— | SHA256:— | |||
| 584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-{0EED76CE-12AC-4BB7-AA27-243B0491D4C0}.FSD | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
13
DNS requests
3
Threats
39
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
328 | notpadd.exe | POST | — | 199.192.27.109:80 | http://uip.igg.biz/and/cat.php | US | — | — | malicious |
3584 | EQNEDT32.EXE | GET | 301 | 67.199.248.10:80 | http://bit.ly/2FkIbcW | US | html | 116 b | shared |
328 | notpadd.exe | POST | — | 199.192.27.109:80 | http://uip.igg.biz/and/cat.php | US | — | — | malicious |
328 | notpadd.exe | POST | — | 199.192.27.109:80 | http://uip.igg.biz/and/cat.php | US | — | — | malicious |
328 | notpadd.exe | POST | — | 199.192.27.109:80 | http://uip.igg.biz/and/cat.php | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
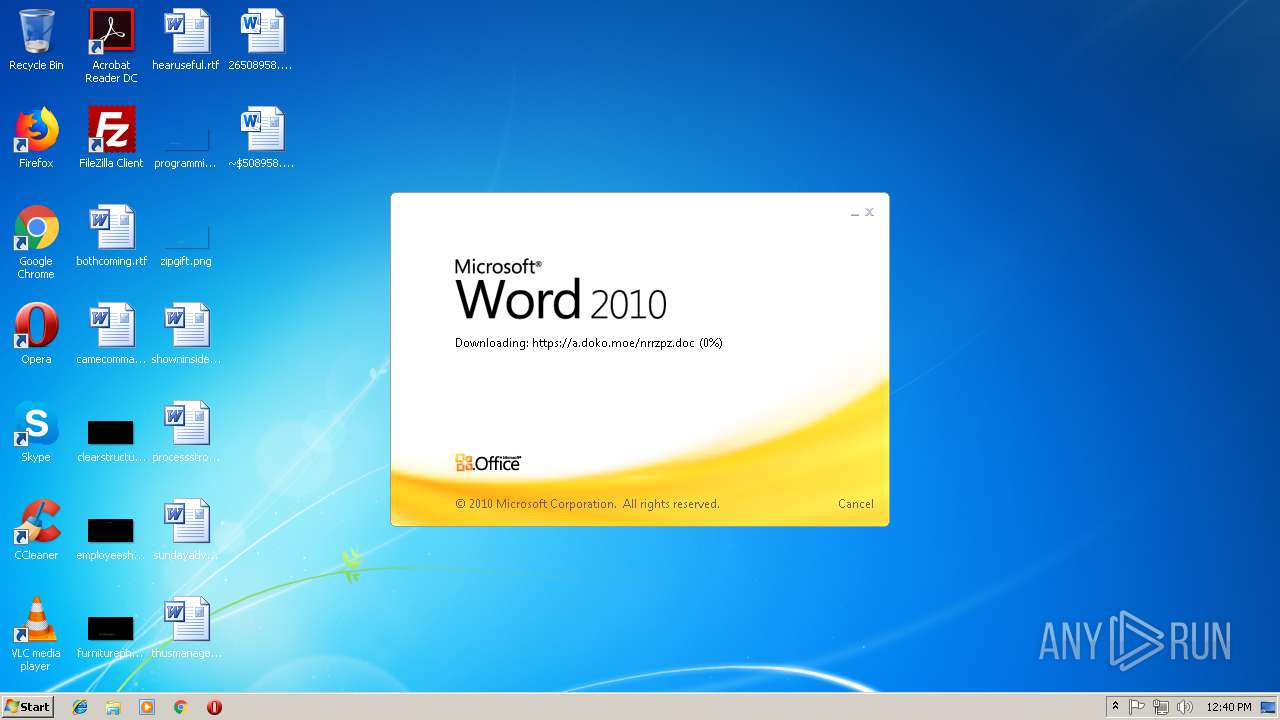
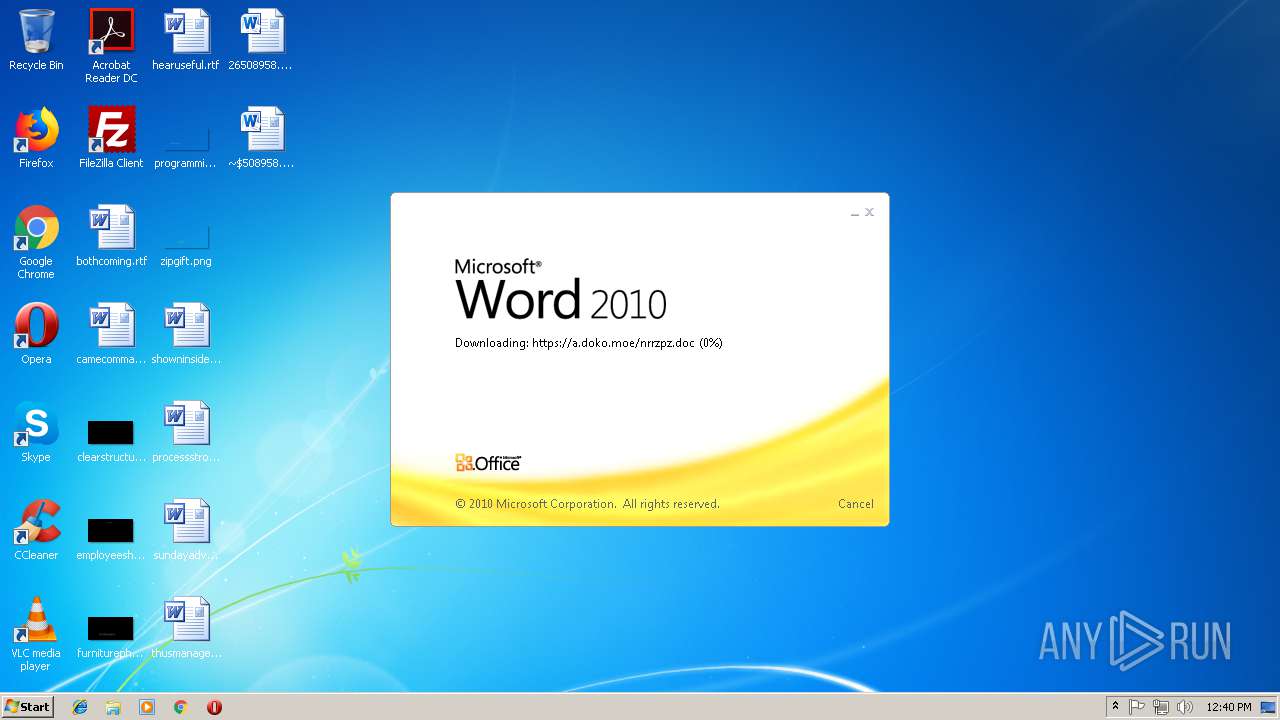
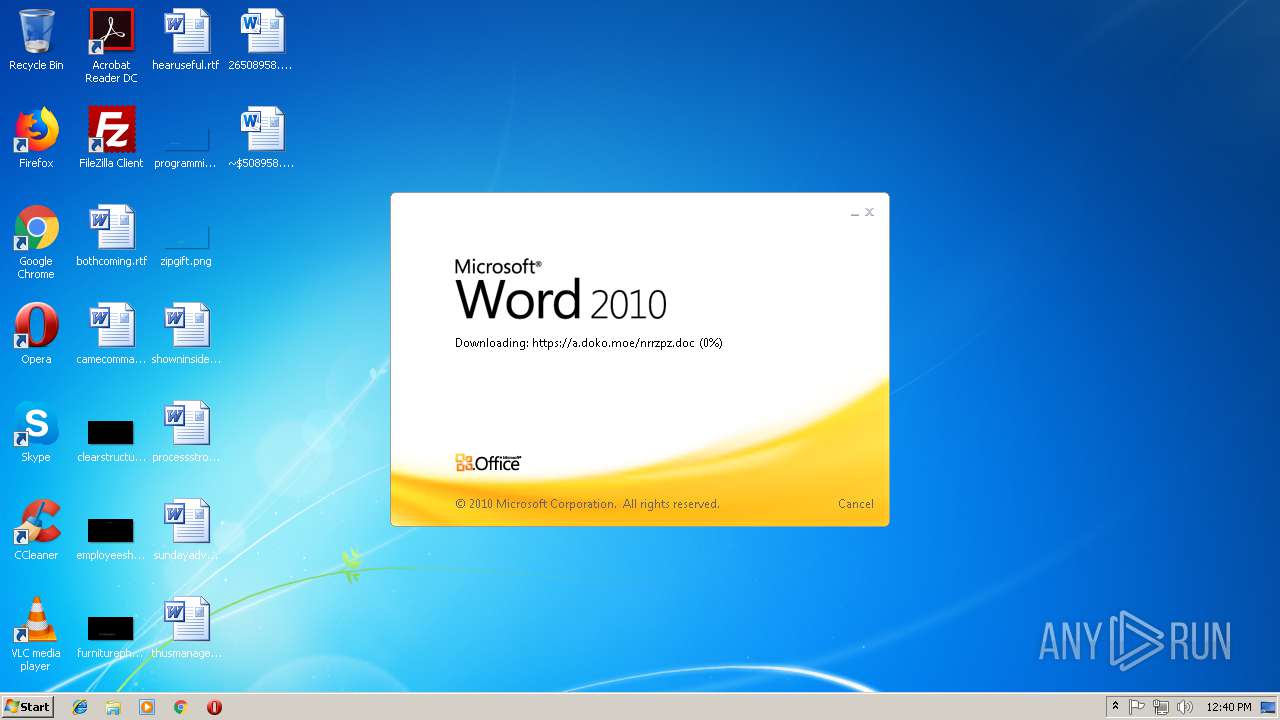
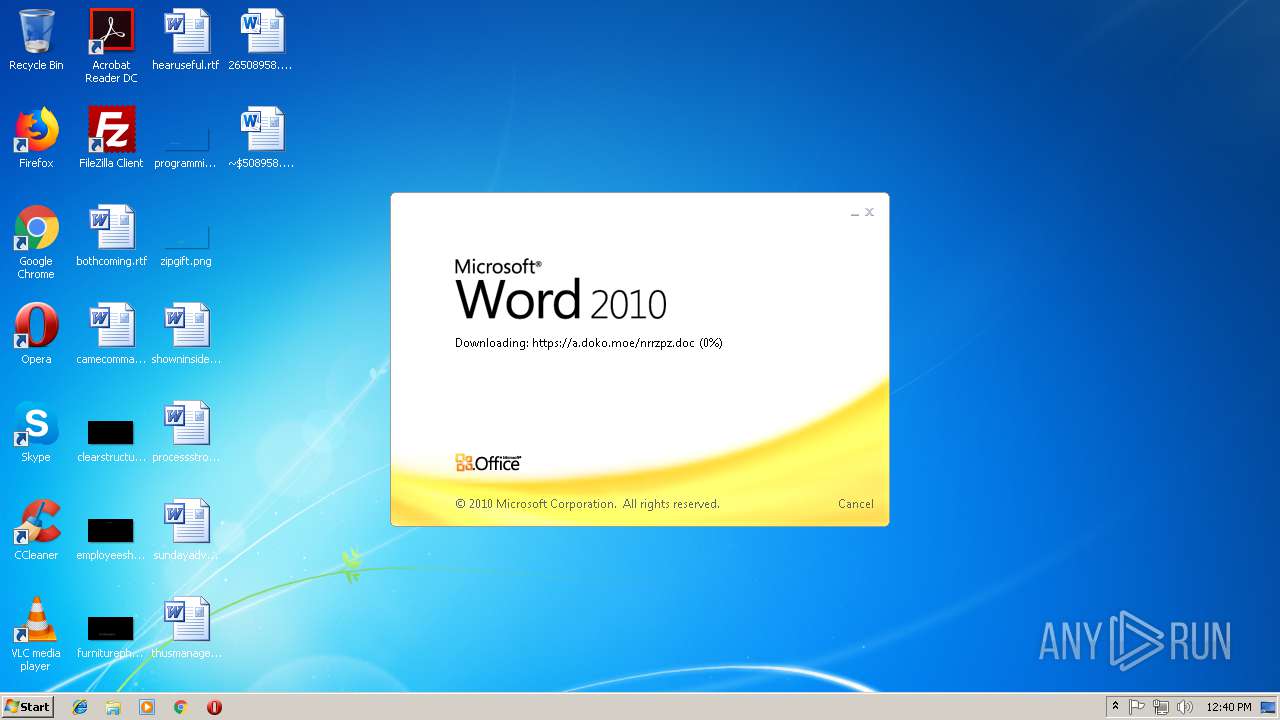
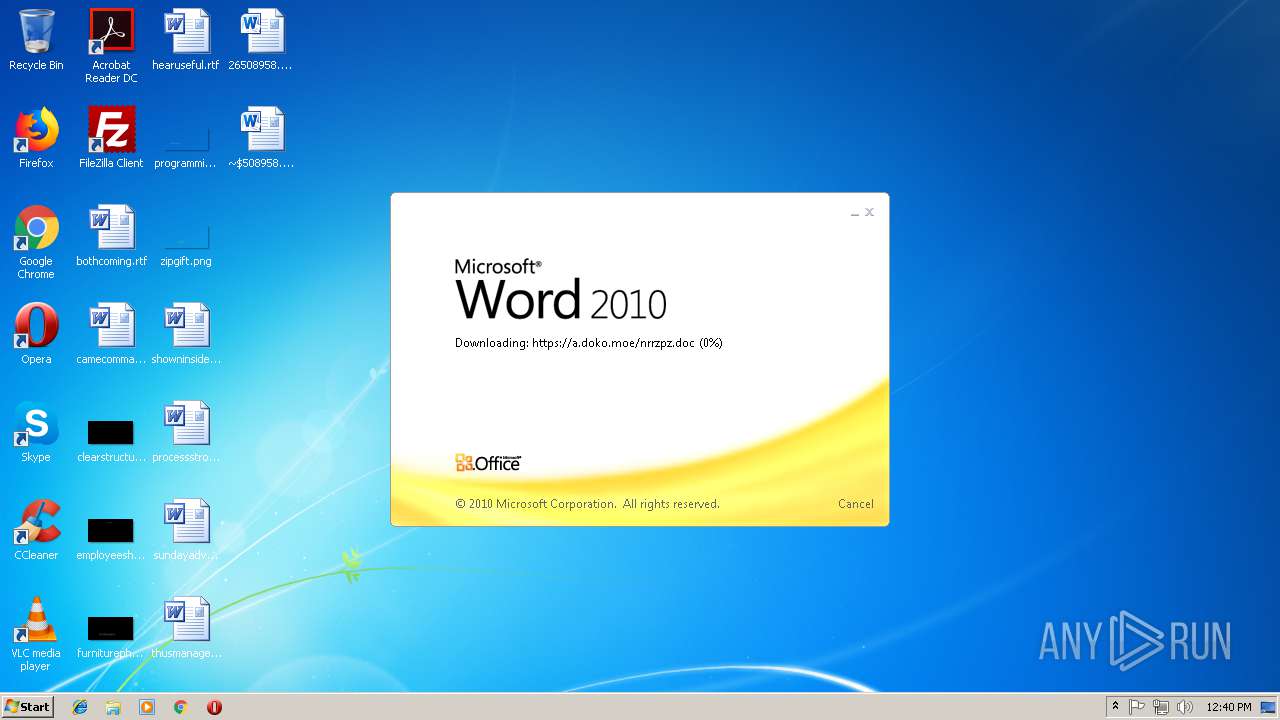
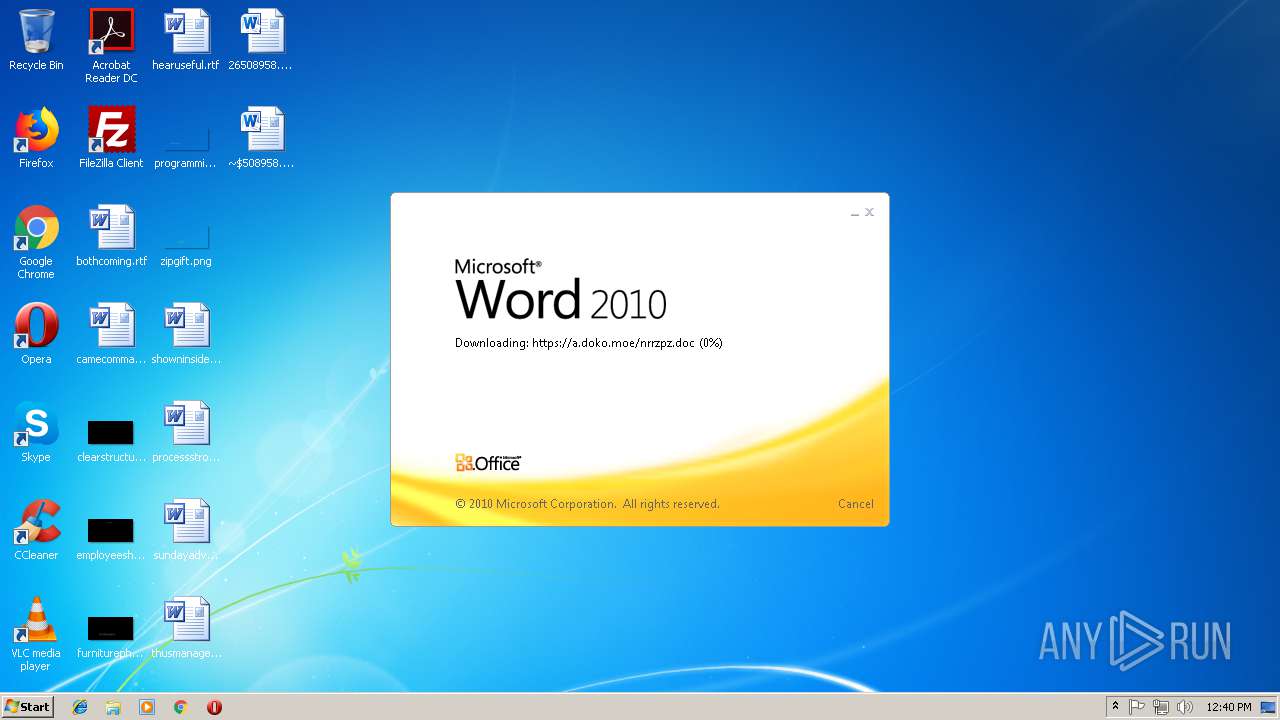
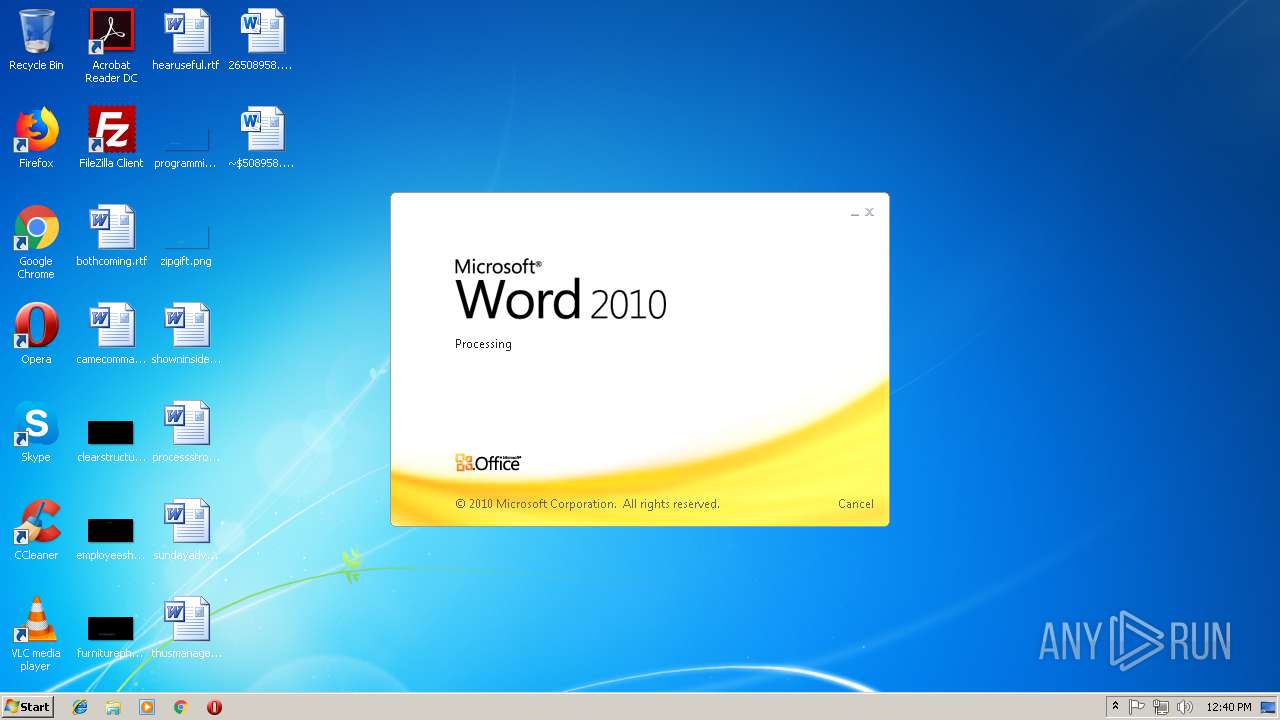
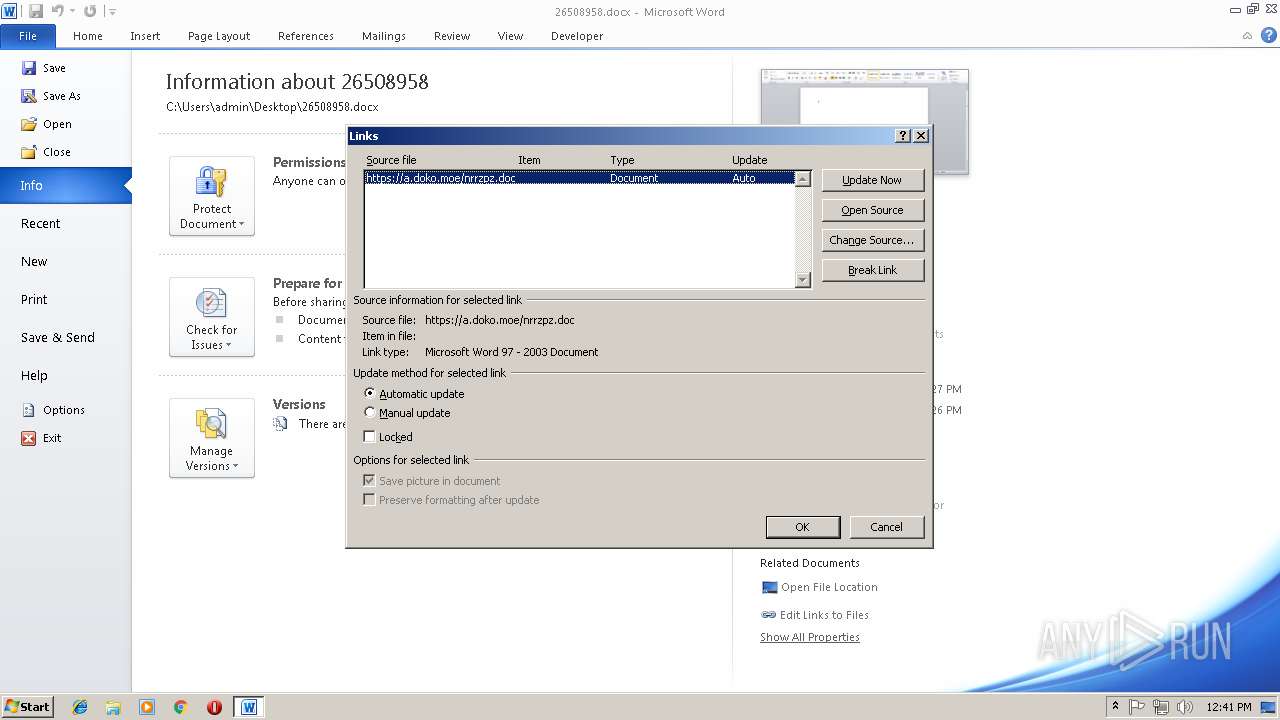
584 | WINWORD.EXE | 185.83.214.16:443 | a.doko.moe | — | PT | suspicious |
640 | WINWORD.EXE | 185.83.214.16:443 | a.doko.moe | — | PT | suspicious |
980 | svchost.exe | 185.83.214.16:443 | a.doko.moe | — | PT | suspicious |
3584 | EQNEDT32.EXE | 67.199.248.10:80 | bit.ly | Bitly Inc | US | shared |
3584 | EQNEDT32.EXE | 185.83.214.16:443 | a.doko.moe | — | PT | suspicious |
328 | notpadd.exe | 199.192.27.109:80 | uip.igg.biz | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
a.doko.moe |
| unknown |
bit.ly |
| shared |
uip.igg.biz |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
328 | notpadd.exe | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
328 | notpadd.exe | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
328 | notpadd.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
328 | notpadd.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
328 | notpadd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
328 | notpadd.exe | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
328 | notpadd.exe | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
328 | notpadd.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
328 | notpadd.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
328 | notpadd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
13 ETPRO signatures available at the full report