| File name: | HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.7z |
| Full analysis: | https://app.any.run/tasks/f4de983c-d2d5-4cc6-bf15-c6147dadef7d |
| Verdict: | Malicious activity |
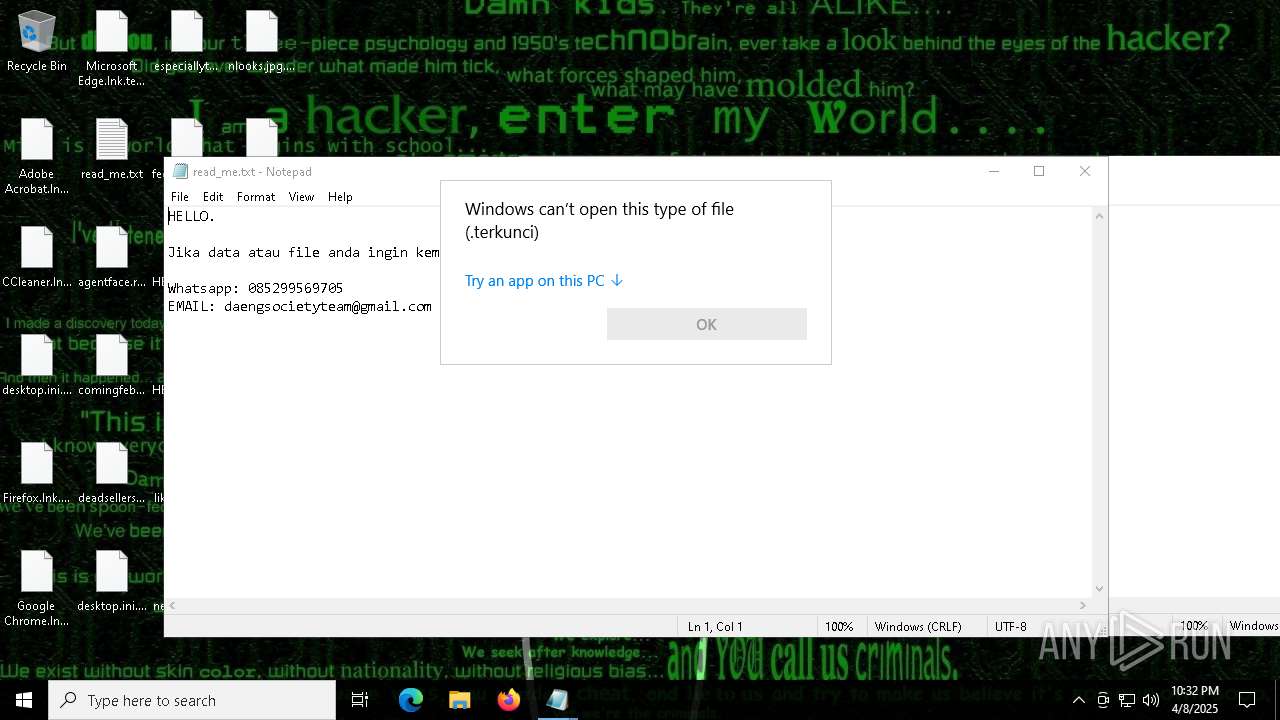
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | April 08, 2025, 22:31:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | EF33D374465DB0FAD8946B46AF6EB3DB |
| SHA1: | 558720FE70CA9F42FFBF74750A1B0E48D50172B7 |
| SHA256: | CF1E44A5541F085692256D31D028B18BAD7A3ED5AE096E887BBFA1D6EA6DA011 |
| SSDEEP: | 24576:l+AdZim/wtUwtKZ/hOmsJnGUWXc81mdOmaUKItbnZ1FozYpA/ZndtJlhPQhXHlJw:l+AdZim/wtUwtKRhOmsJnGUWM81mdOmc |
MALICIOUS
Create files in the Startup directory
- getbinomo.exe (PID: 7960)
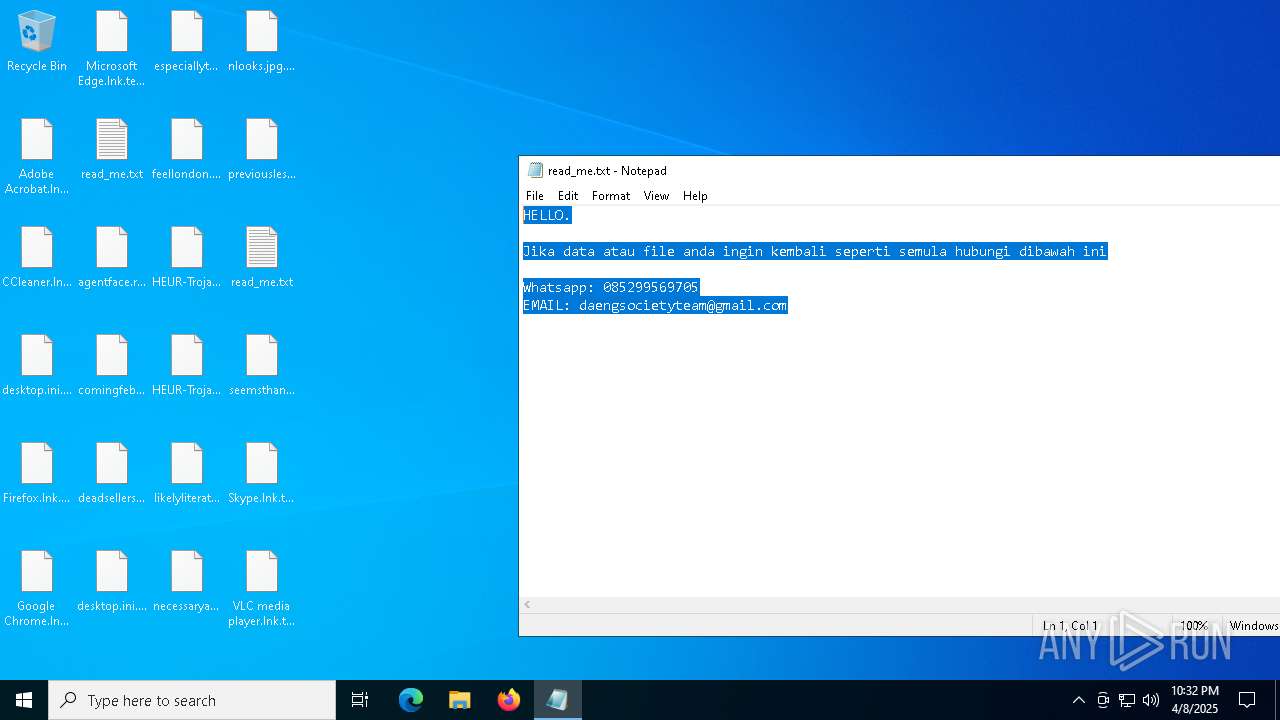
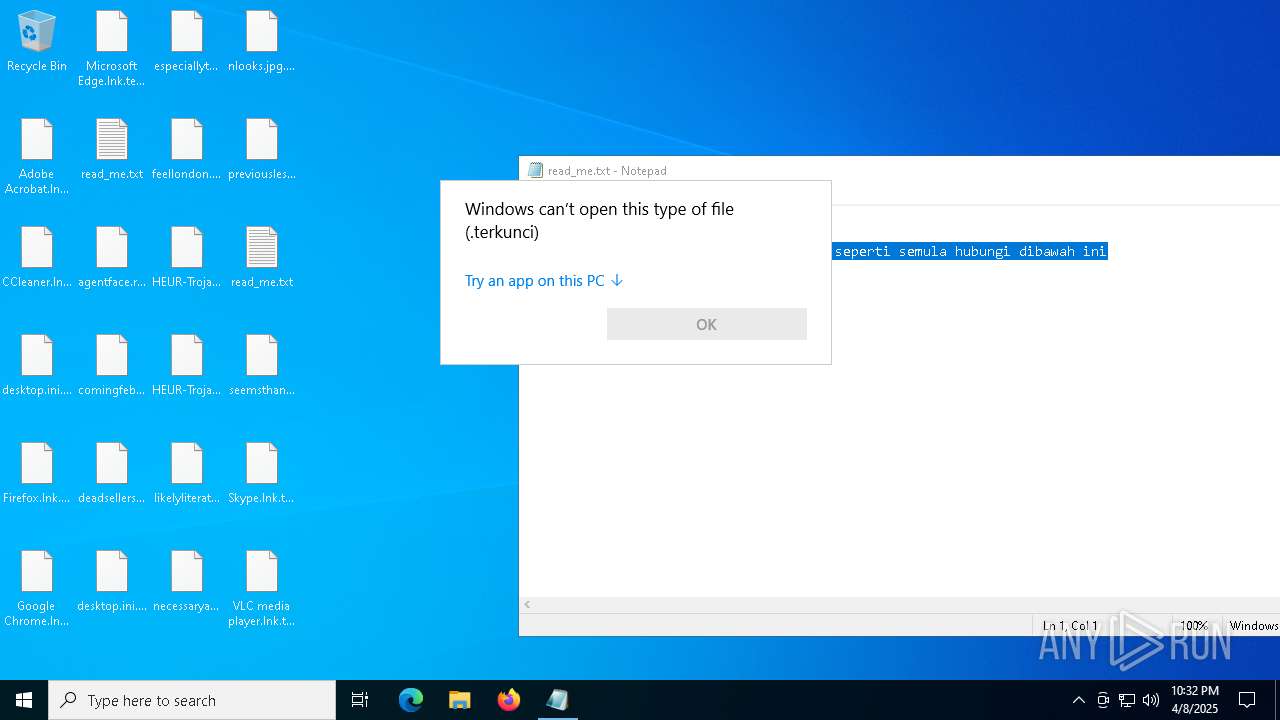
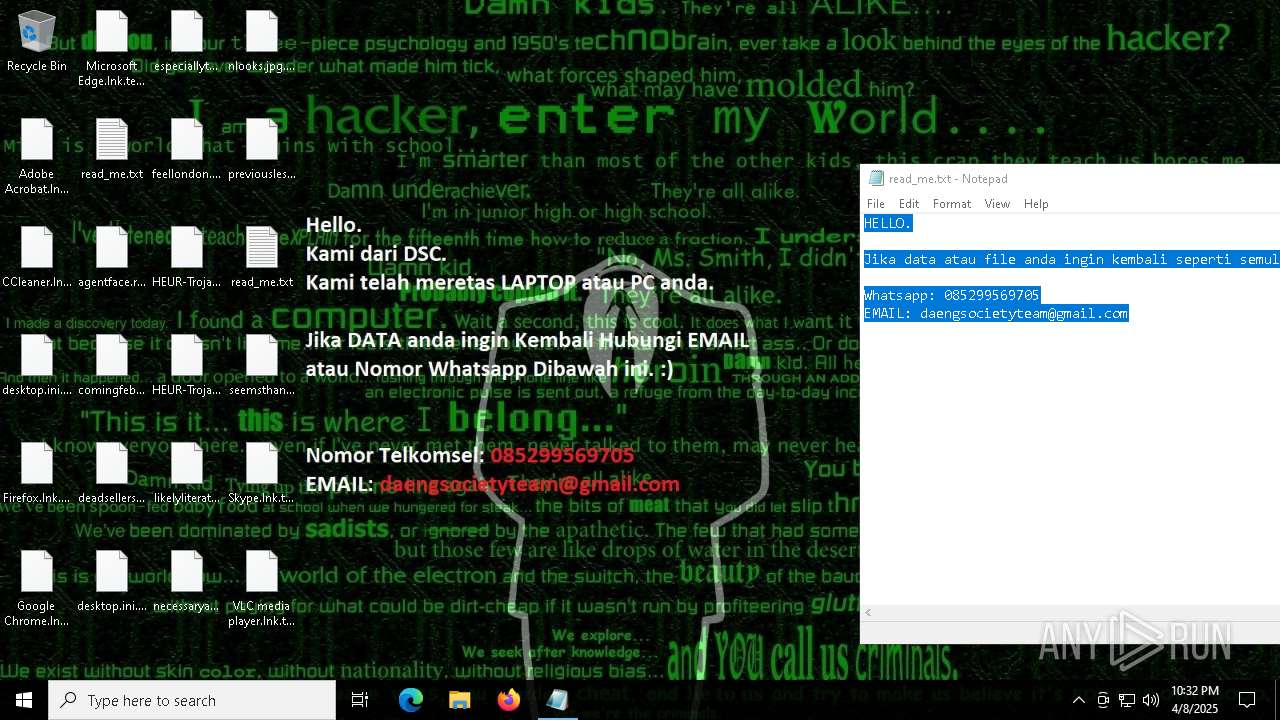
Renames files like ransomware
- getbinomo.exe (PID: 7960)
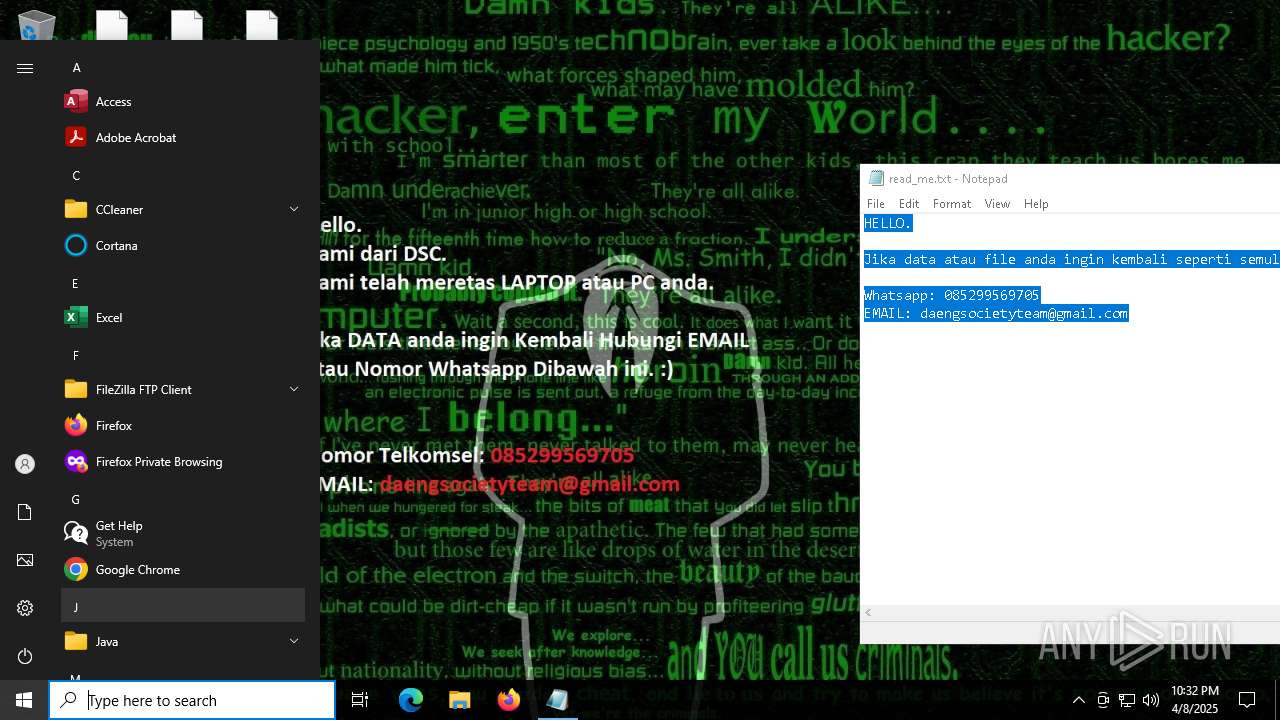
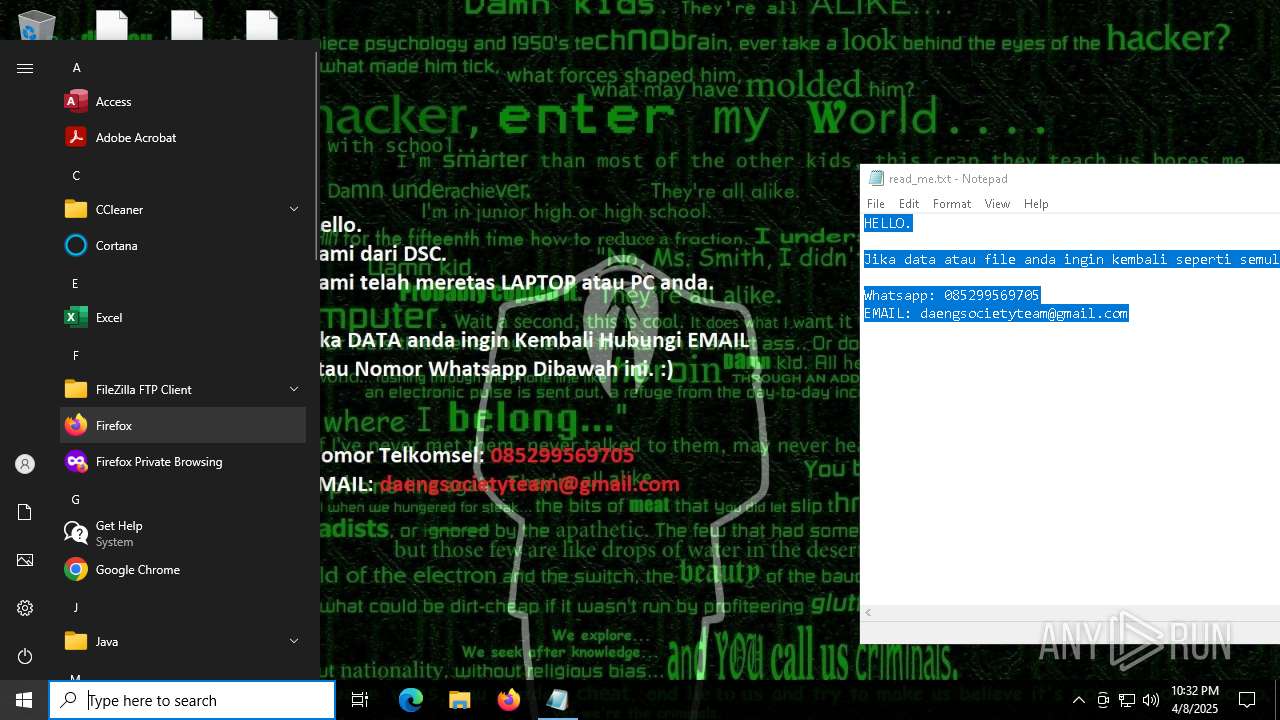
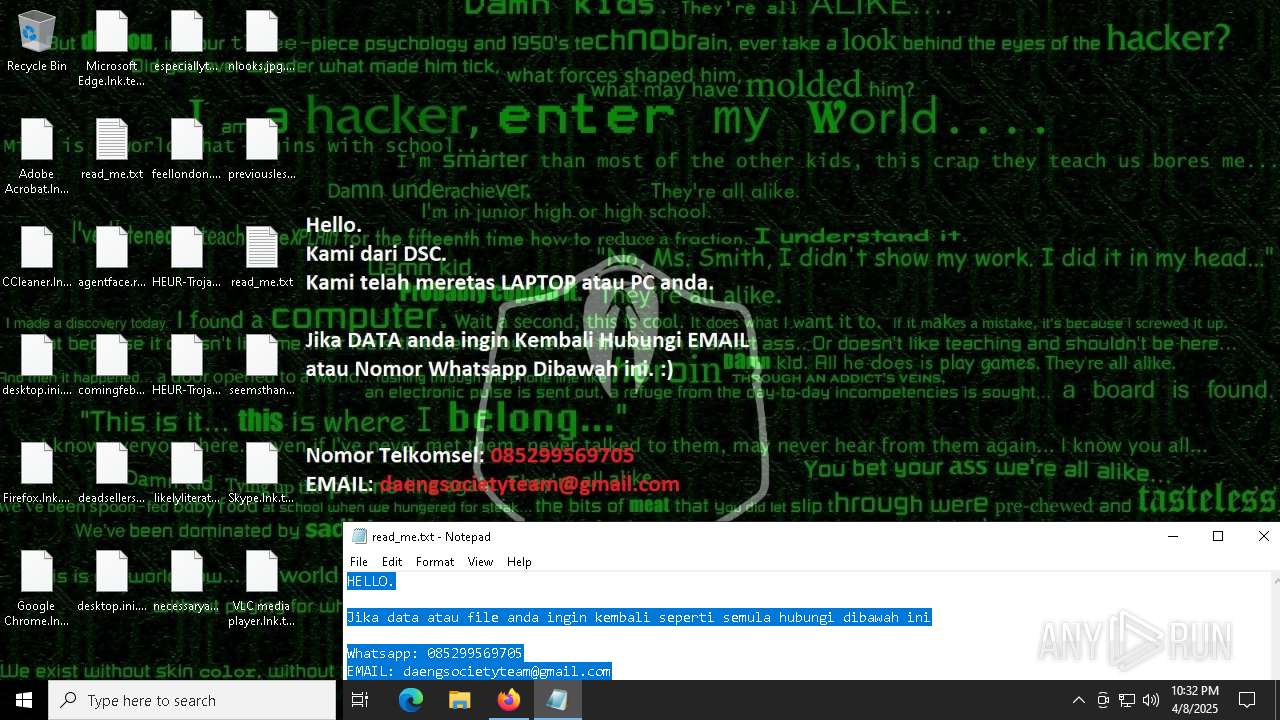
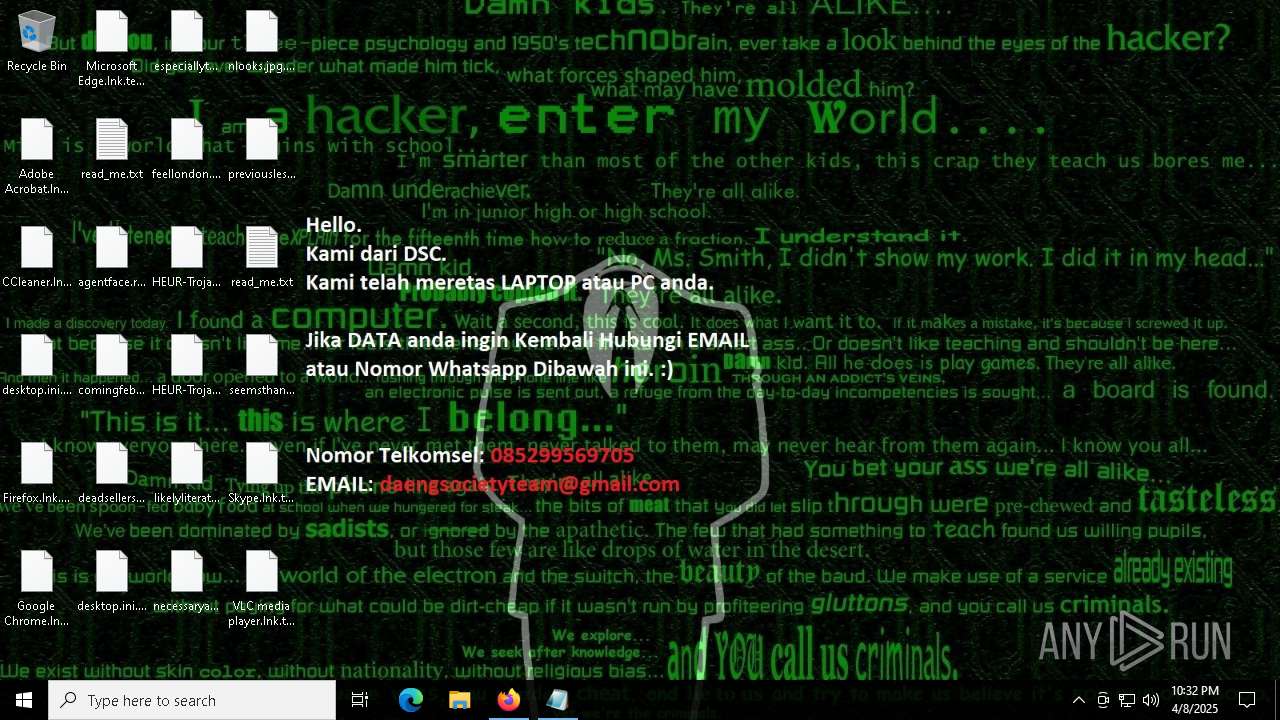
RANSOMWARE has been detected
- getbinomo.exe (PID: 7960)
CHAOS has been detected (YARA)
- getbinomo.exe (PID: 7960)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 7316)
Deletes shadow copies
- cmd.exe (PID: 1020)
- cmd.exe (PID: 4180)
Actions looks like stealing of personal data
- getbinomo.exe (PID: 7960)
SUSPICIOUS
Executable content was dropped or overwritten
- HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe (PID: 7852)
Reads security settings of Internet Explorer
- HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe (PID: 7852)
- getbinomo.exe (PID: 7960)
Reads the date of Windows installation
- HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe (PID: 7852)
- getbinomo.exe (PID: 7960)
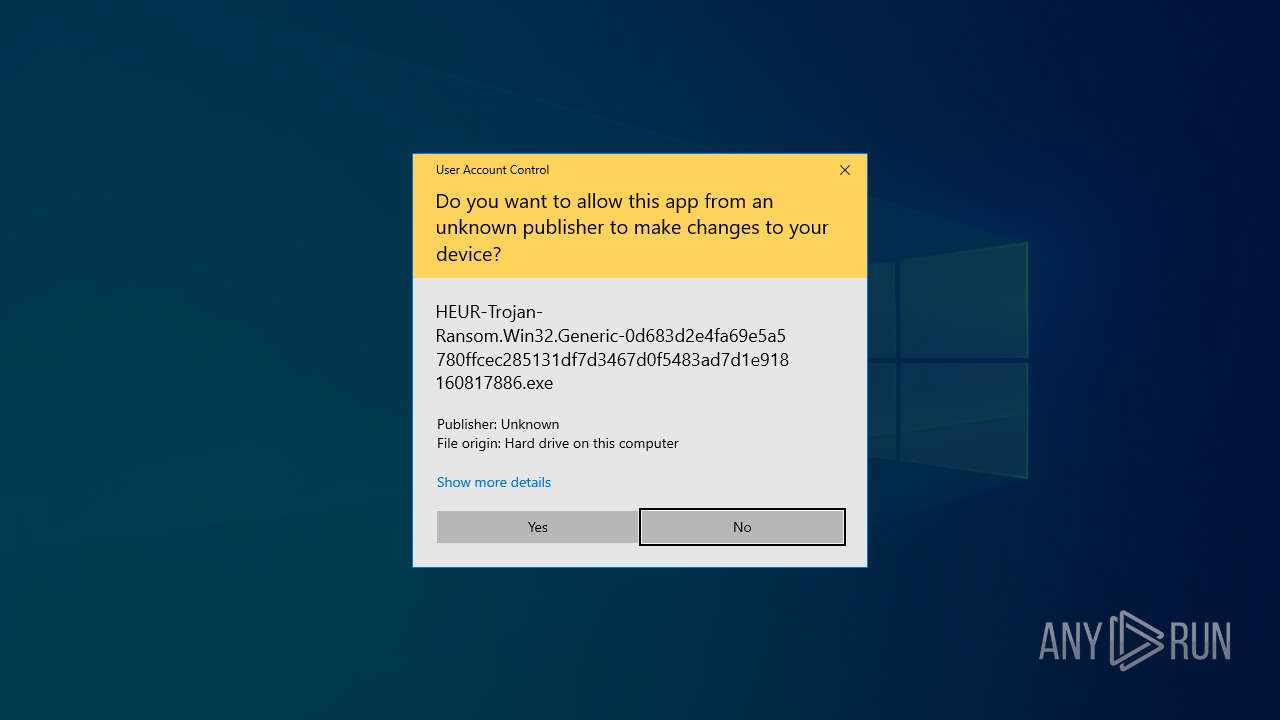
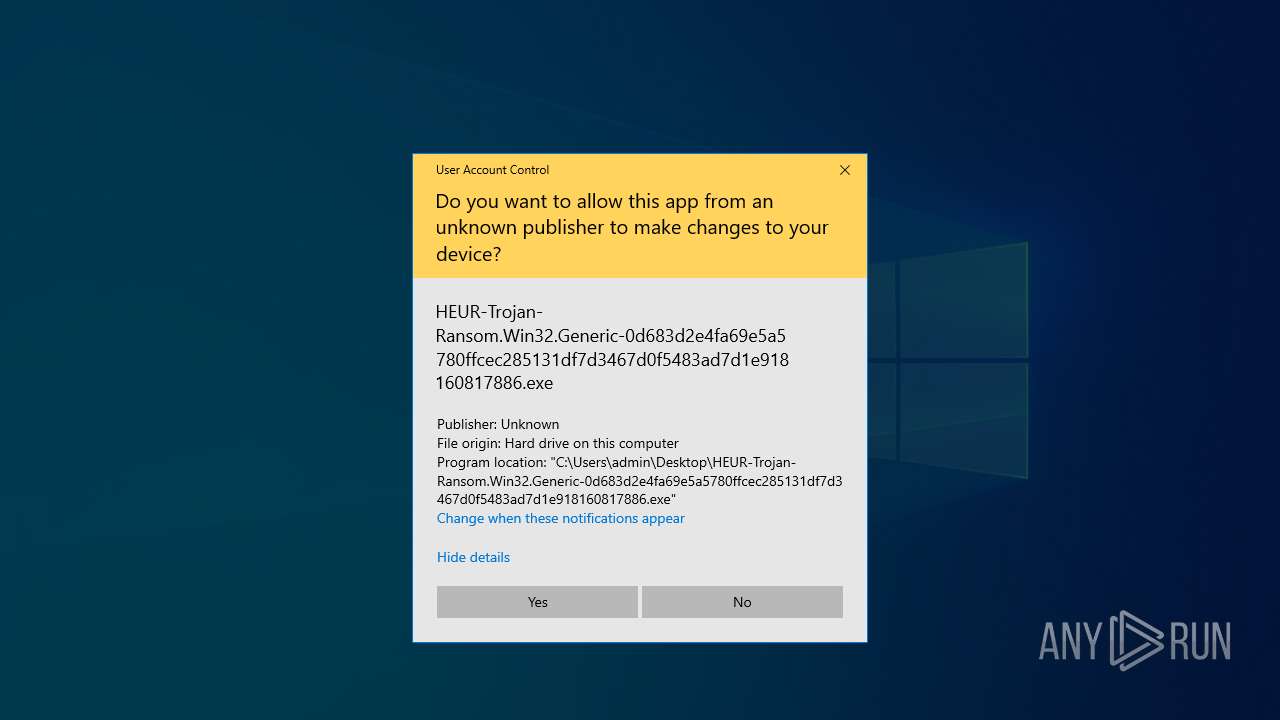
Starts itself from another location
- HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe (PID: 7852)
Write to the desktop.ini file (may be used to cloak folders)
- getbinomo.exe (PID: 7960)
Found regular expressions for crypto-addresses (YARA)
- getbinomo.exe (PID: 7960)
Executes as Windows Service
- VSSVC.exe (PID: 516)
- wbengine.exe (PID: 1764)
- vds.exe (PID: 7696)
Starts CMD.EXE for commands execution
- getbinomo.exe (PID: 7960)
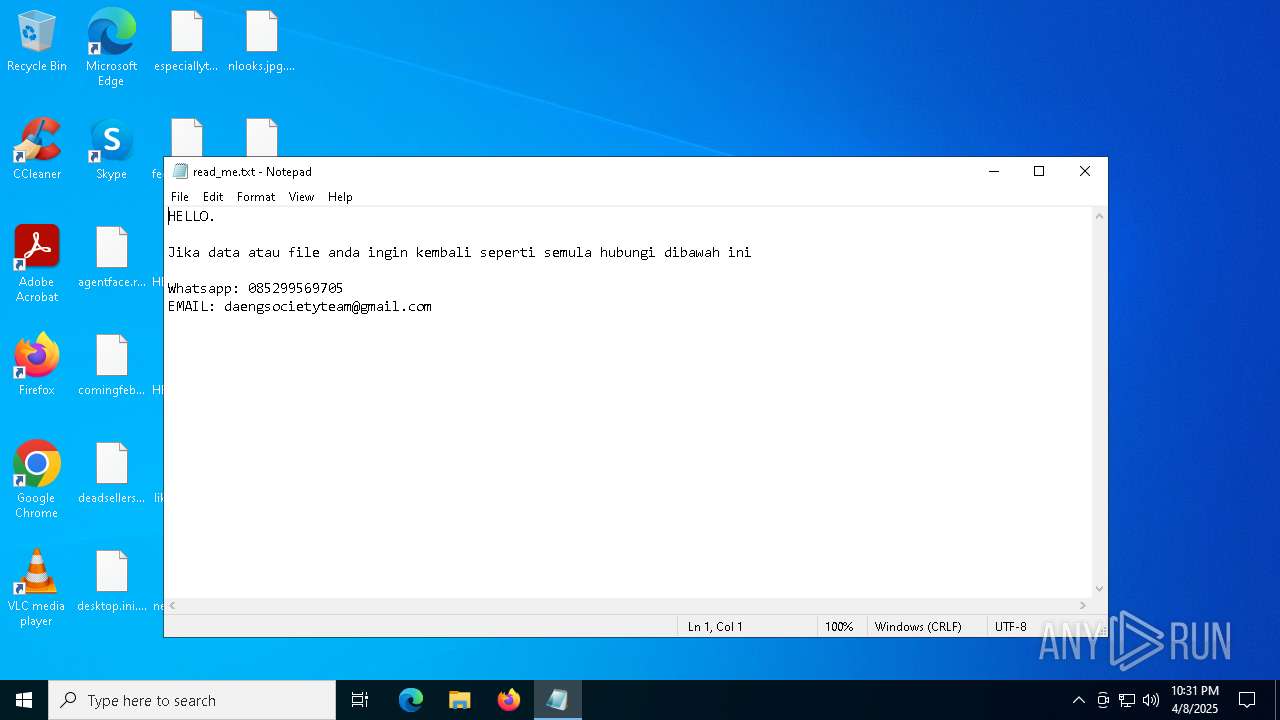
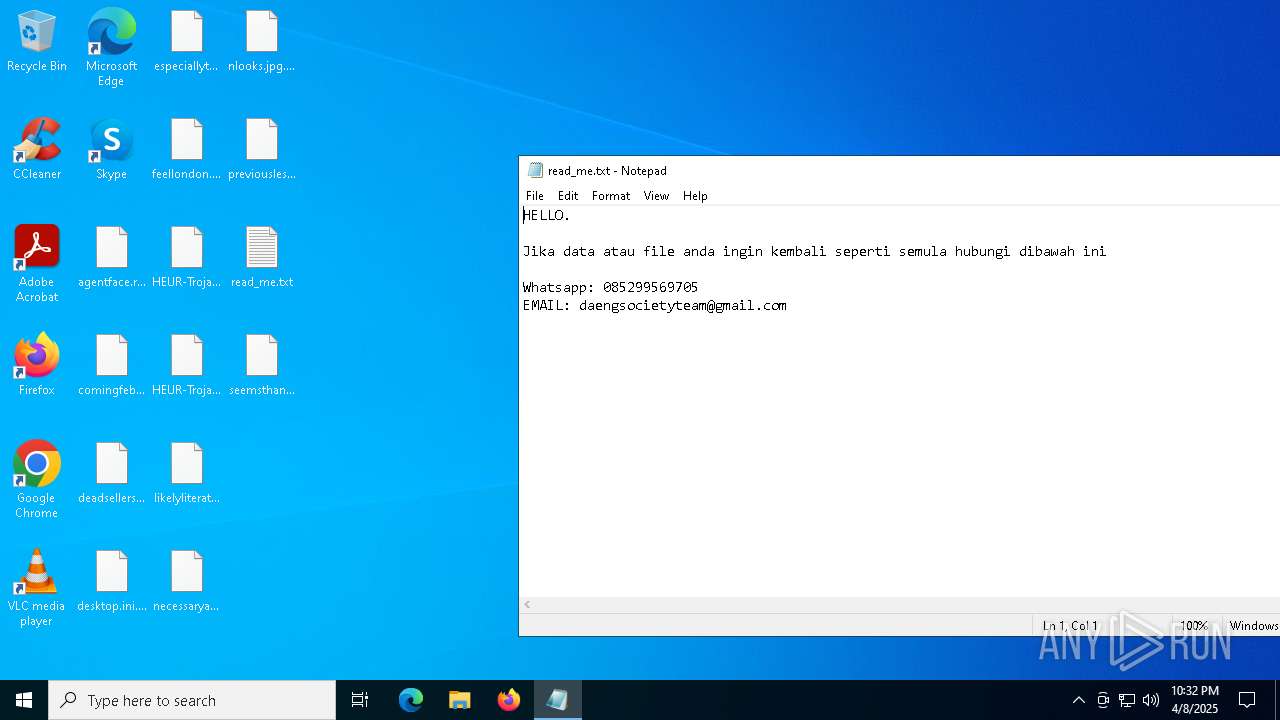
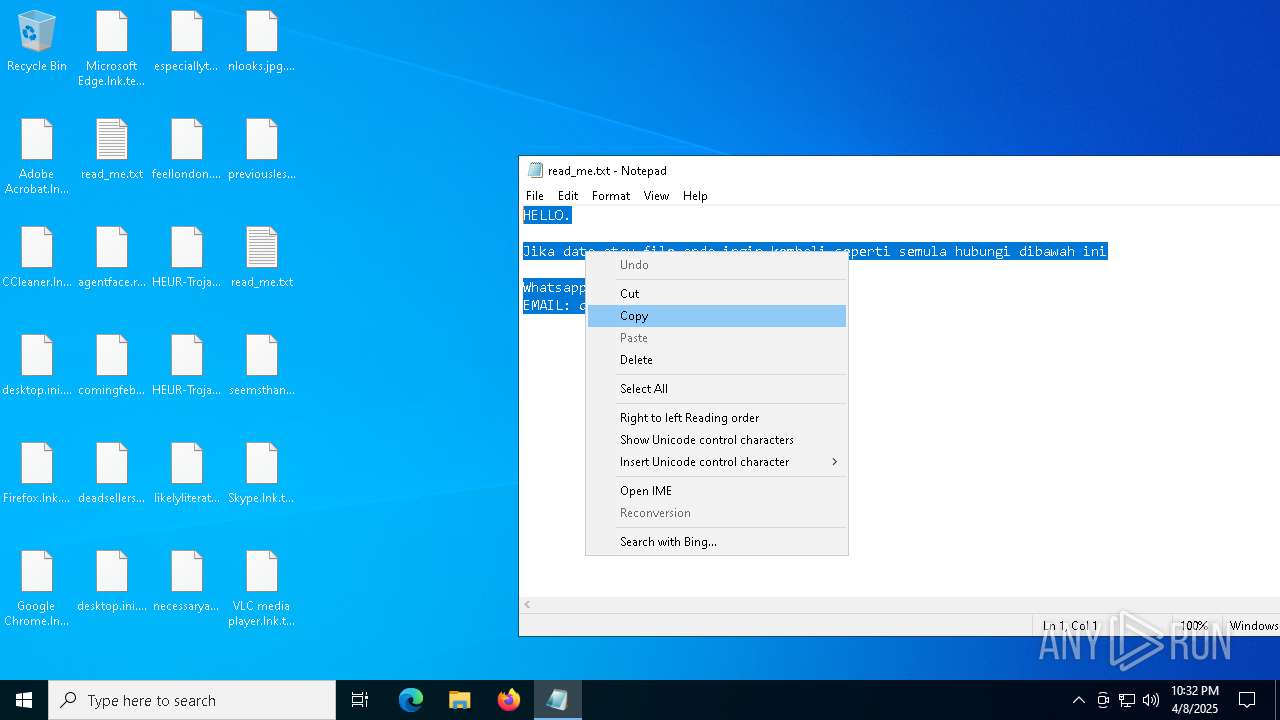
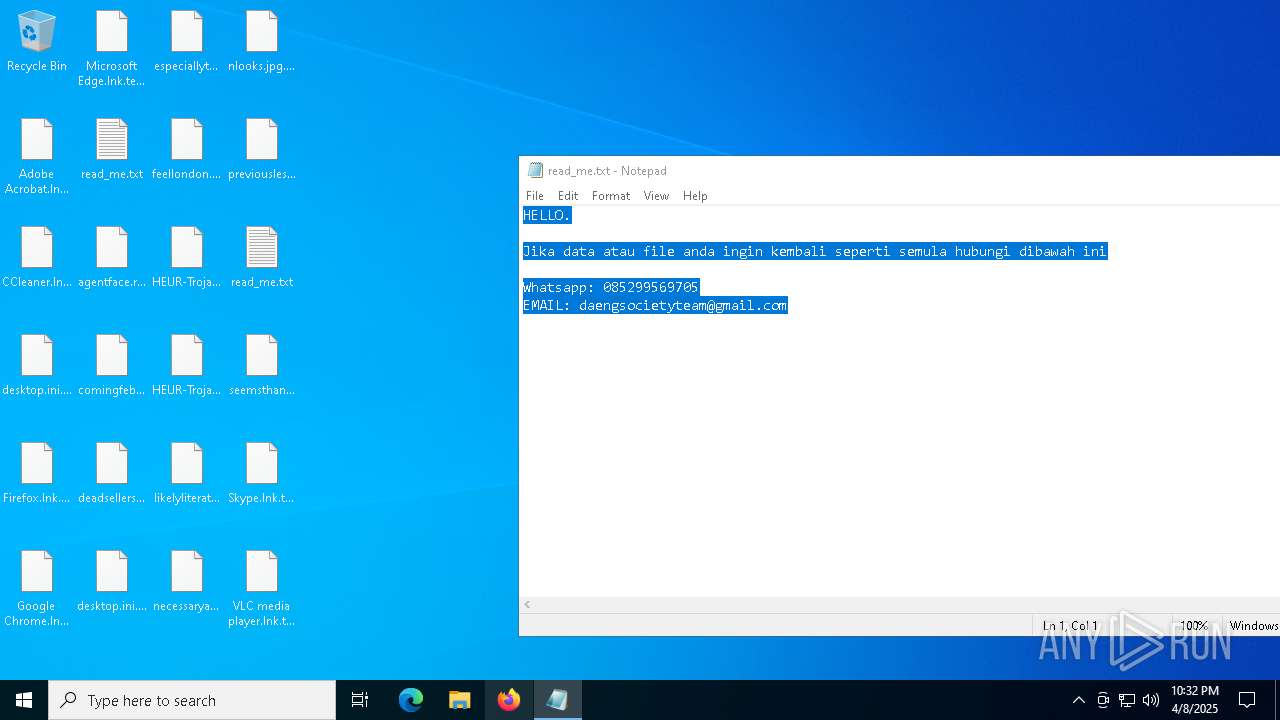
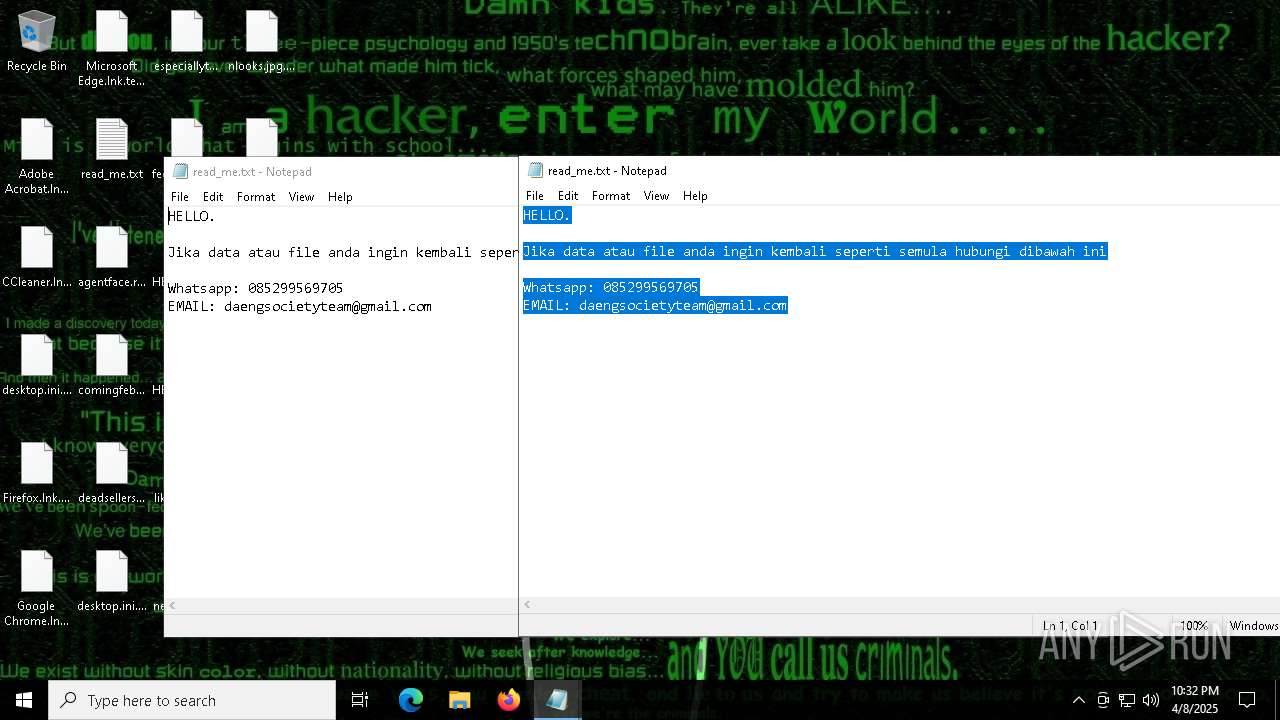
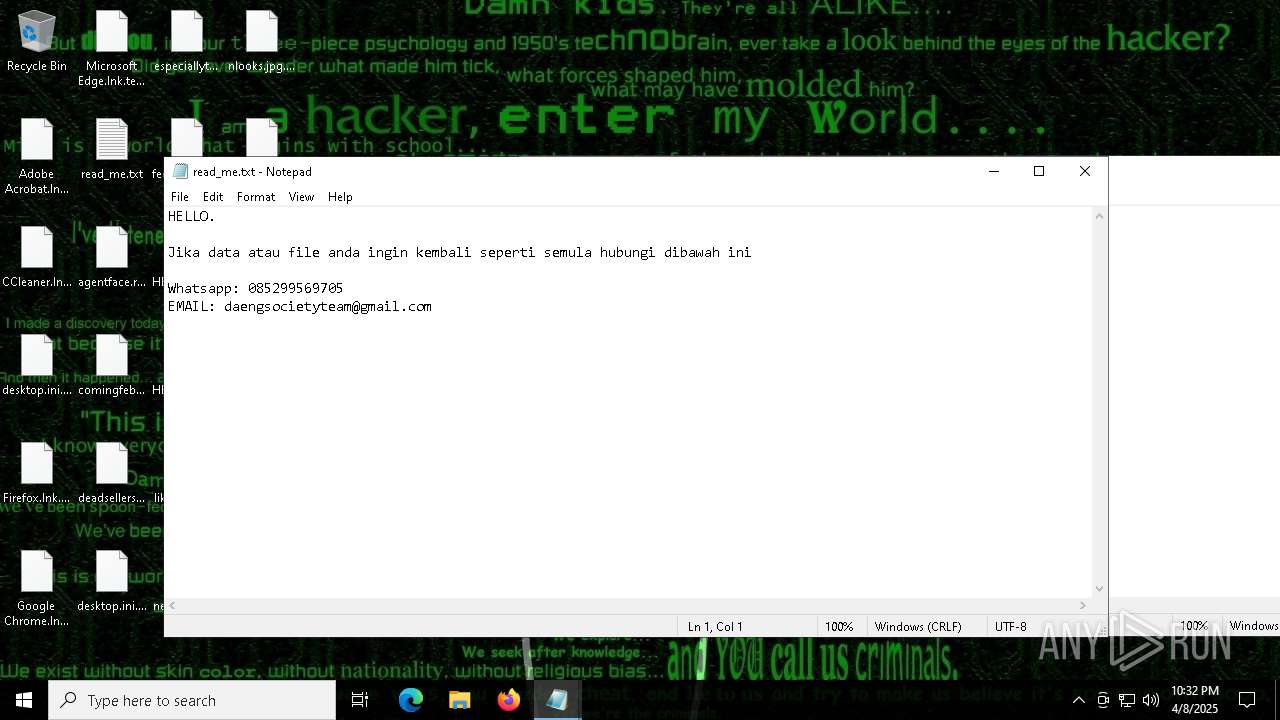
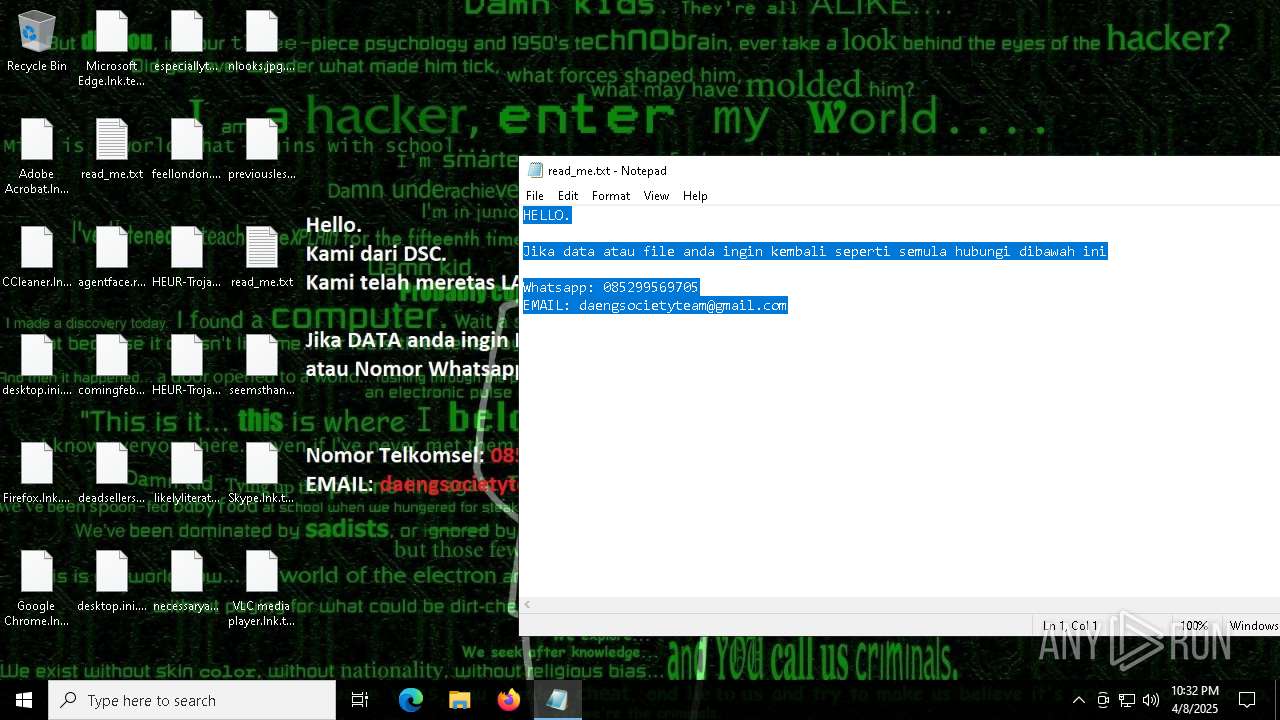
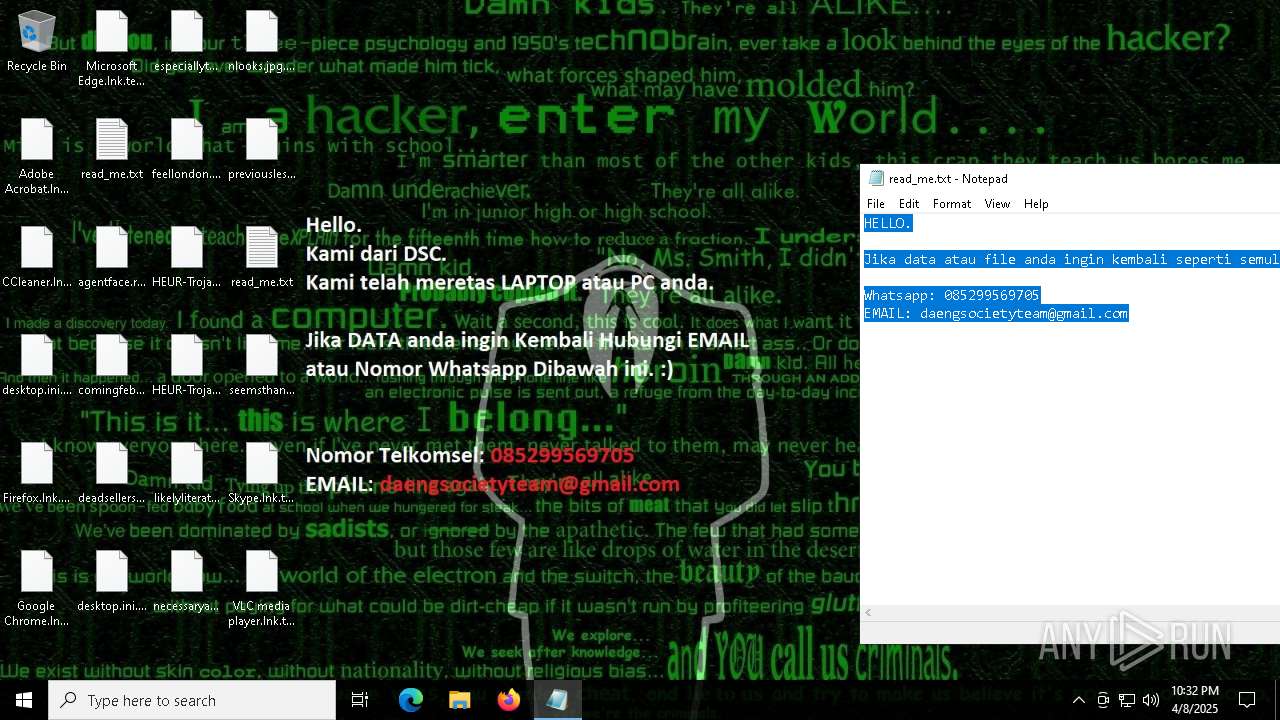
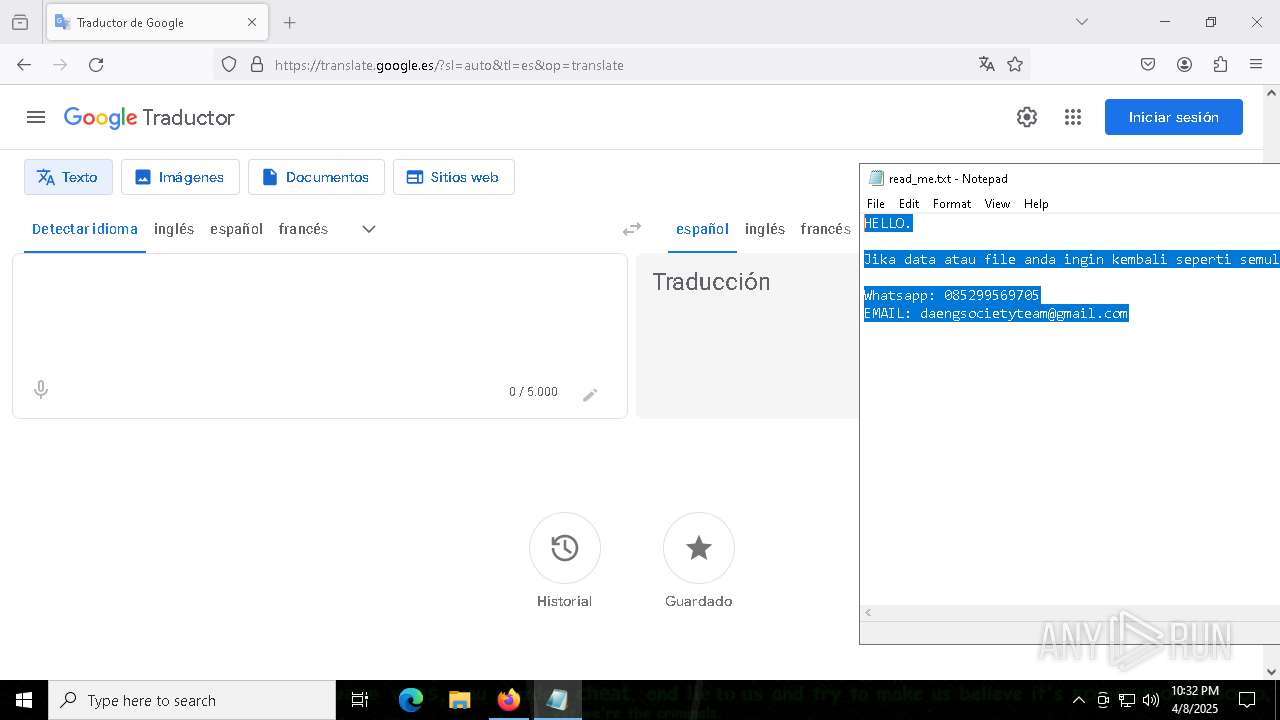
Start notepad (likely ransomware note)
- getbinomo.exe (PID: 7960)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4300)
Manual execution by a user
- HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe (PID: 7852)
- notepad.exe (PID: 8080)
- firefox.exe (PID: 7752)
Creates files or folders in the user directory
- HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe (PID: 7852)
- getbinomo.exe (PID: 7960)
Reads the computer name
- HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe (PID: 7852)
- getbinomo.exe (PID: 7960)
Checks supported languages
- HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe (PID: 7852)
- getbinomo.exe (PID: 7960)
Process checks computer location settings
- HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe (PID: 7852)
- getbinomo.exe (PID: 7960)
Reads the machine GUID from the registry
- getbinomo.exe (PID: 7960)
Reads security settings of Internet Explorer
- notepad.exe (PID: 8080)
- WMIC.exe (PID: 5504)
- notepad.exe (PID: 7772)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6516)
- getbinomo.exe (PID: 7960)
Create files in a temporary directory
- getbinomo.exe (PID: 7960)
Application launched itself
- firefox.exe (PID: 7752)
- firefox.exe (PID: 7832)
Reads the software policy settings
- slui.exe (PID: 7256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2021:09:25 12:04:58+00:00 |
| ArchivedFileName: | HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe |
Total processes
171
Monitored processes
38
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Windows\System32\cmd.exe" /C vssadmin delete shadows /all /quiet & wmic shadowcopy delete | C:\Windows\System32\cmd.exe | — | getbinomo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2644 -childID 3 -isForBrowser -prefsHandle 2696 -prefMapHandle 2692 -prefsLen 23241 -prefMapSize 240682 -jsInitHandle 1264 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {74f21e4e-0b75-43d1-9cf1-7f50b5f2070d} 7832 "\\.\pipe\gecko-crash-server-pipe.7832" 12ad42a4bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1600 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | "C:\WINDOWS\system32\wbengine.exe" | C:\Windows\System32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Block Level Backup Engine Service EXE Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | "C:\Windows\System32\cmd.exe" /C wbadmin delete catalog -quiet | C:\Windows\System32\cmd.exe | — | getbinomo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4336 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2016 -parentBuildID 20240213221259 -prefsHandle 2332 -prefMapHandle 2320 -prefsLen 20775 -prefMapSize 240682 -appDir "C:\Program Files\Mozilla Firefox\browser" - {c9e26f98-8b3b-4e87-90f0-b91811d2640f} 7832 "\\.\pipe\gecko-crash-server-pipe.7832" 12ace2cb610 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
21 573
Read events
21 518
Write events
37
Delete events
18
Modification events
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.7z | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
4
Suspicious files
186
Text files
681
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4300.29888\HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.exe | executable | |
MD5:5B61E933FB4B526837A23637FF6BEF7E | SHA256:0D683D2E4FA69E5A5780FFCEC285131DF7D3467D0F5483AD7D1E918160817886 | |||
| 7960 | getbinomo.exe | C:\Users\admin\Desktop\deadsellers.rtf.terkunci | text | |
MD5:29F780AB5E1DC679B1C968B7A93F9CFA | SHA256:56717AAB368240147848062B4BA2F3D9B86BDD180E46FCD5D9BCBF3A614CFCD1 | |||
| 7960 | getbinomo.exe | C:\Users\admin\Desktop\comingfeb.rtf.terkunci | text | |
MD5:30677183033D1FB1BCA53FC38C844F79 | SHA256:B7AF2CAEF882C2C35B6FF9D8D126799A6DD87817204BE1B4F167A0DFA06432F2 | |||
| 7960 | getbinomo.exe | C:\Users\admin\Desktop\agentface.rtf.terkunci | text | |
MD5:6F0C024095222D8B1DE05F5D41A5F03C | SHA256:A1241BF2EC85B836E54281DB04B0C20D8AB07184DA2E9ED352AB4CB98AEA8CA0 | |||
| 7960 | getbinomo.exe | C:\Users\admin\Desktop\comingfeb.rtf | text | |
MD5:30677183033D1FB1BCA53FC38C844F79 | SHA256:B7AF2CAEF882C2C35B6FF9D8D126799A6DD87817204BE1B4F167A0DFA06432F2 | |||
| 7960 | getbinomo.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\getbinomo.url | binary | |
MD5:E3179074EE9DBD51D649E382A53EC21A | SHA256:7466F4AC30E5896D85E788E6EE089CC9CCCB6B72B50D3D6E57495EE1B6E9E60C | |||
| 7960 | getbinomo.exe | C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-0d683d2e4fa69e5a5780ffcec285131df7d3467d0f5483ad7d1e918160817886.7z | text | |
MD5:E32DBCFEE8F768F452C7CFDD709F7B7E | SHA256:2ED3D87D067BD99D20D7B9A554D2DFB7EC781F9334F8BCA4C2141C24A1834361 | |||
| 7960 | getbinomo.exe | C:\Users\admin\Desktop\agentface.rtf | text | |
MD5:6F0C024095222D8B1DE05F5D41A5F03C | SHA256:A1241BF2EC85B836E54281DB04B0C20D8AB07184DA2E9ED352AB4CB98AEA8CA0 | |||
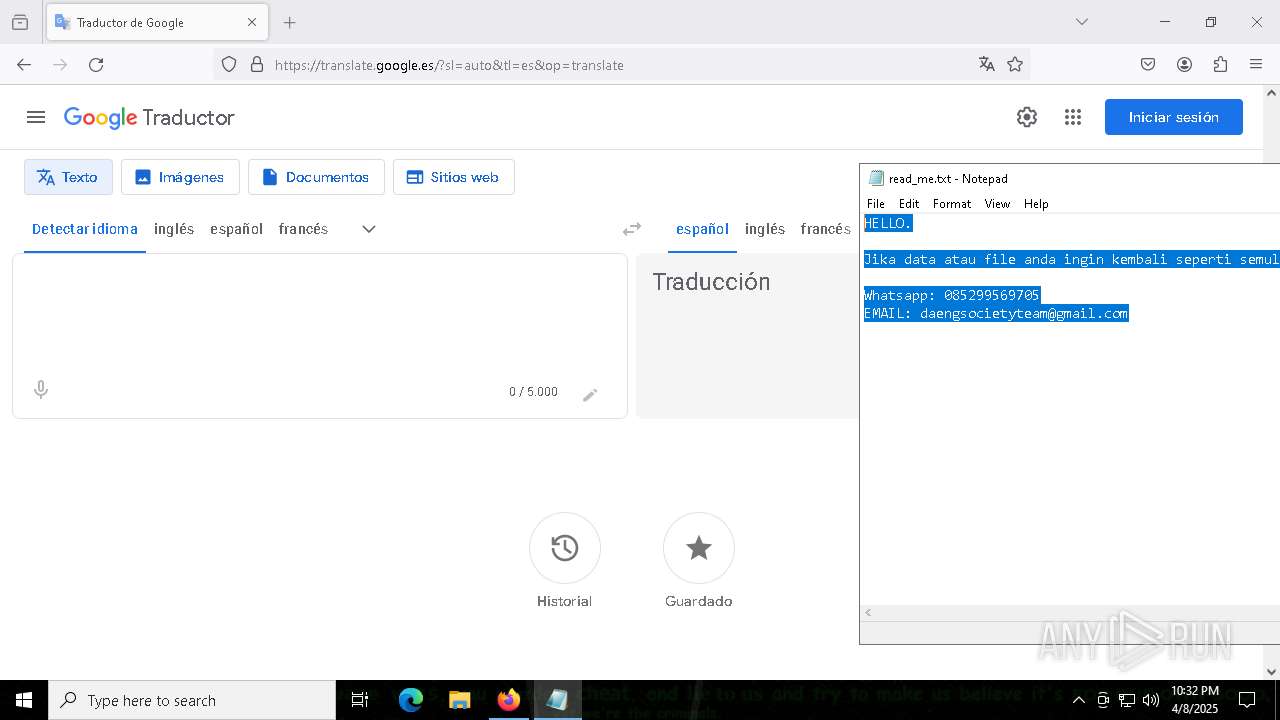
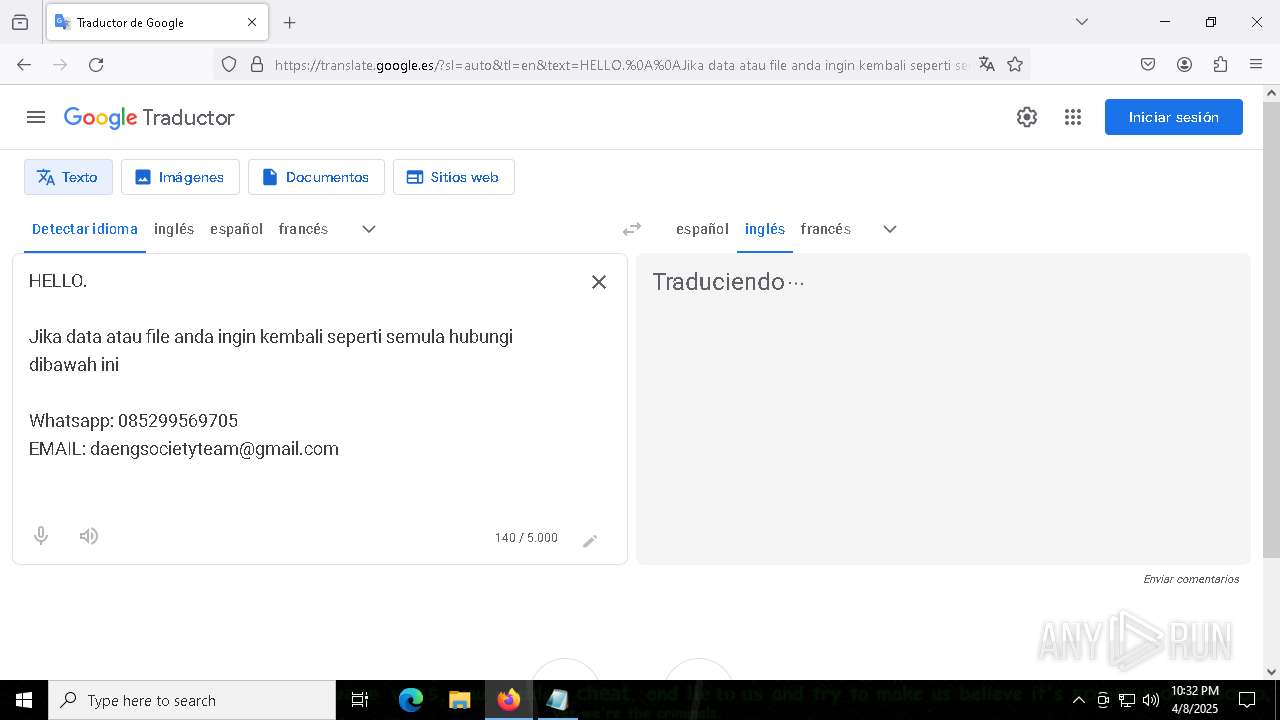
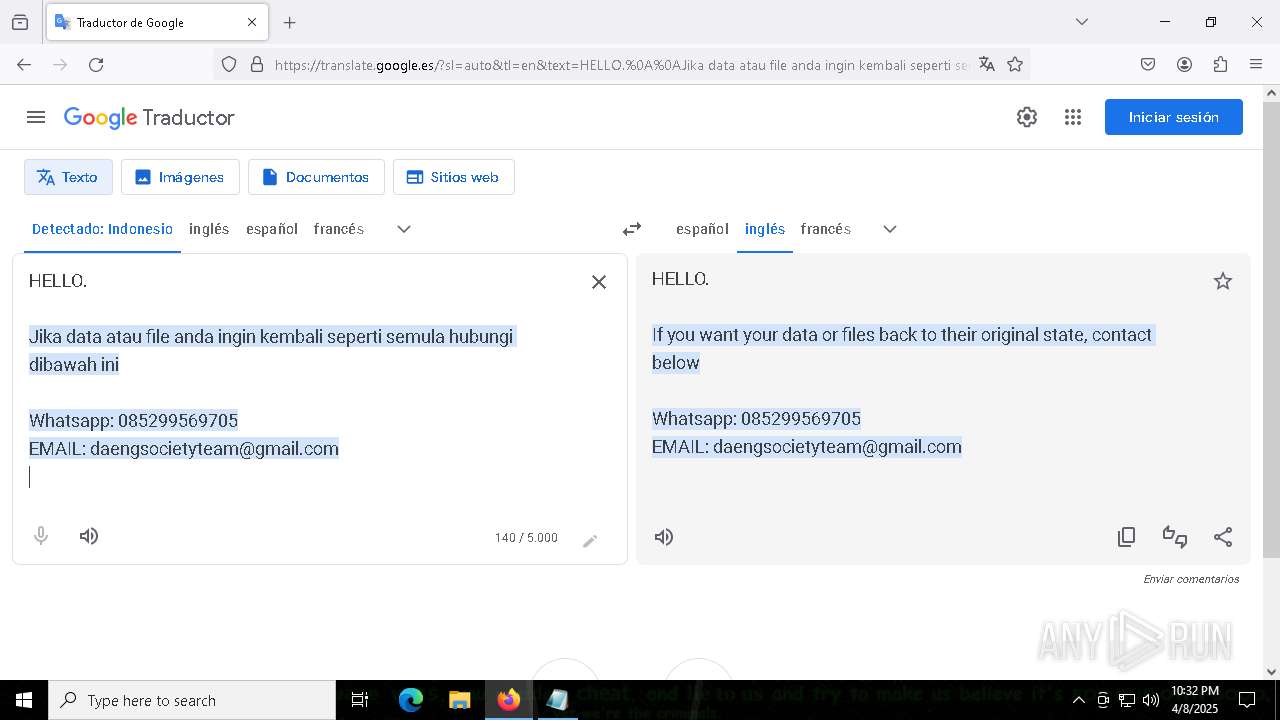
| 7960 | getbinomo.exe | C:\Users\admin\Desktop\read_me.txt | text | |
MD5:D8DD22720A31E4DA09A7BA0EF4CE91D5 | SHA256:EEA8683B94ED210CEE610259D1EF2AE07859B09C80D79C789CD1E6E3E17C14EE | |||
| 7960 | getbinomo.exe | C:\Users\admin\Desktop\deadsellers.rtf | text | |
MD5:29F780AB5E1DC679B1C968B7A93F9CFA | SHA256:56717AAB368240147848062B4BA2F3D9B86BDD180E46FCD5D9BCBF3A614CFCD1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
126
DNS requests
146
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8172 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
8172 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7832 | firefox.exe | POST | 200 | 2.16.2.73:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7832 | firefox.exe | POST | 200 | 2.16.2.73:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7832 | firefox.exe | POST | 200 | 2.16.2.73:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7832 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7832 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |