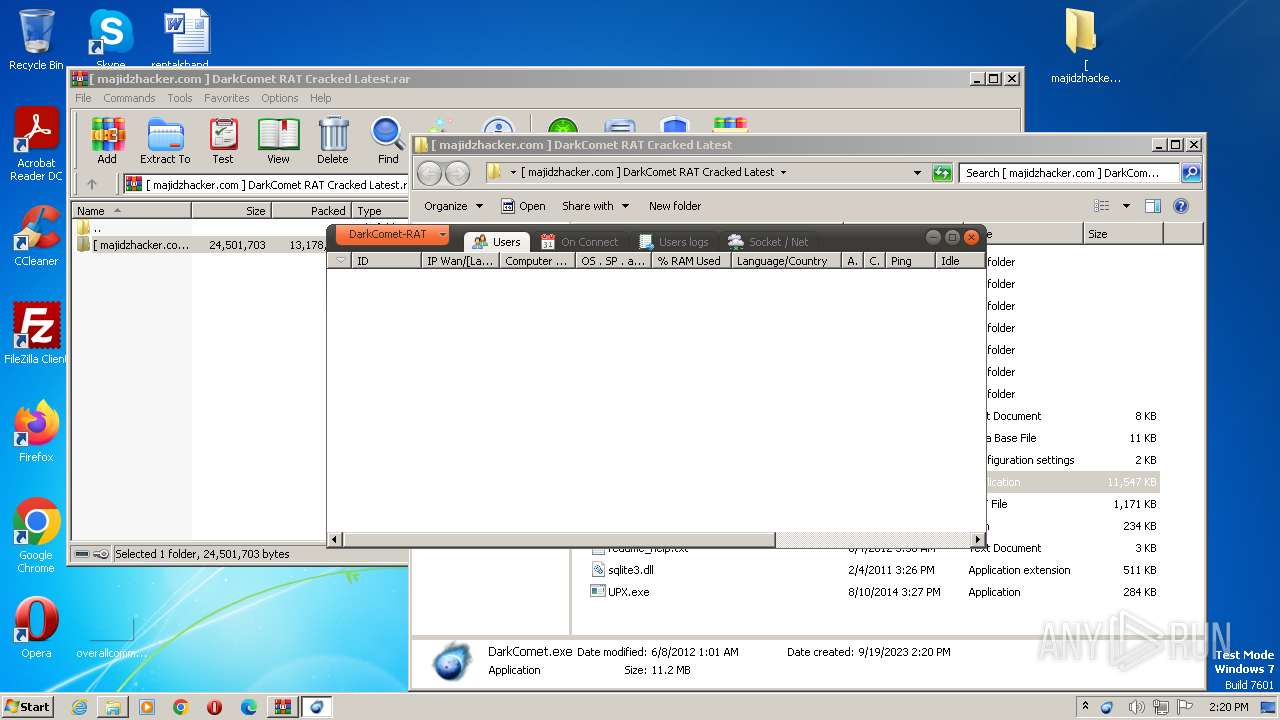
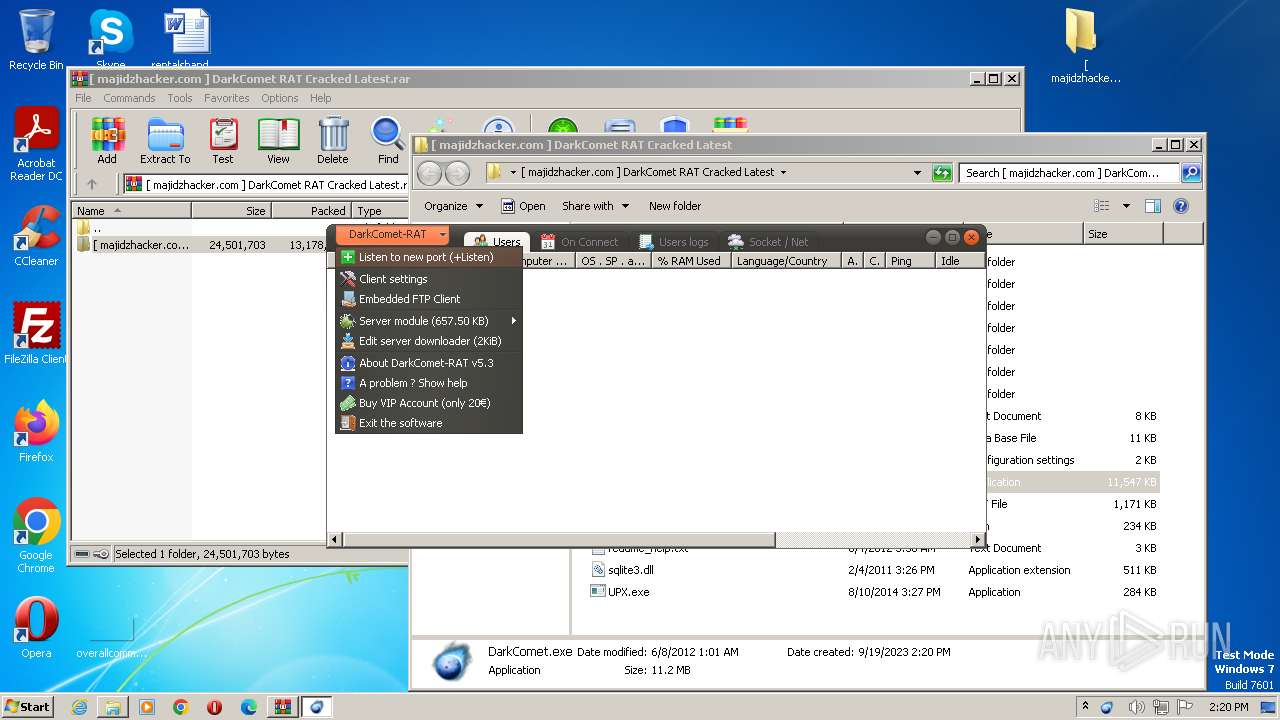
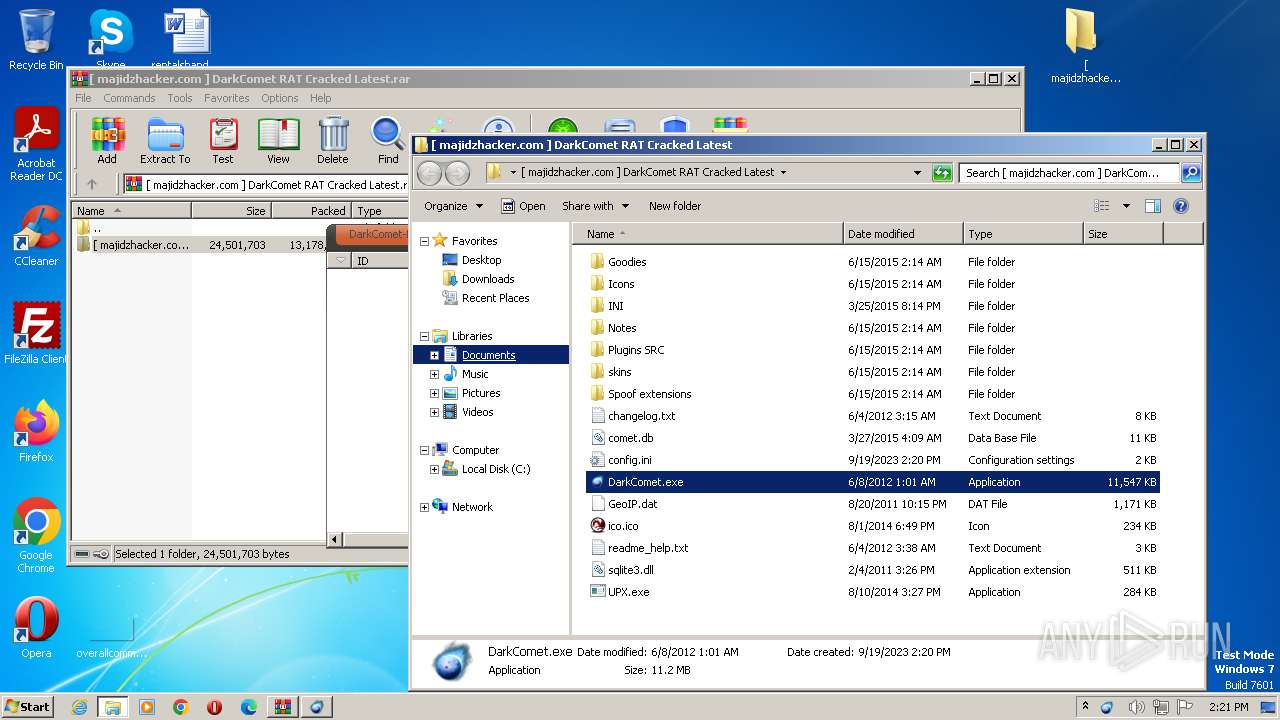
| File name: | [ majidzhacker.com ] DarkComet RAT Cracked Latest.rar |
| Full analysis: | https://app.any.run/tasks/fcaa6884-45d4-47e6-9280-d33bf2267460 |
| Verdict: | Malicious activity |
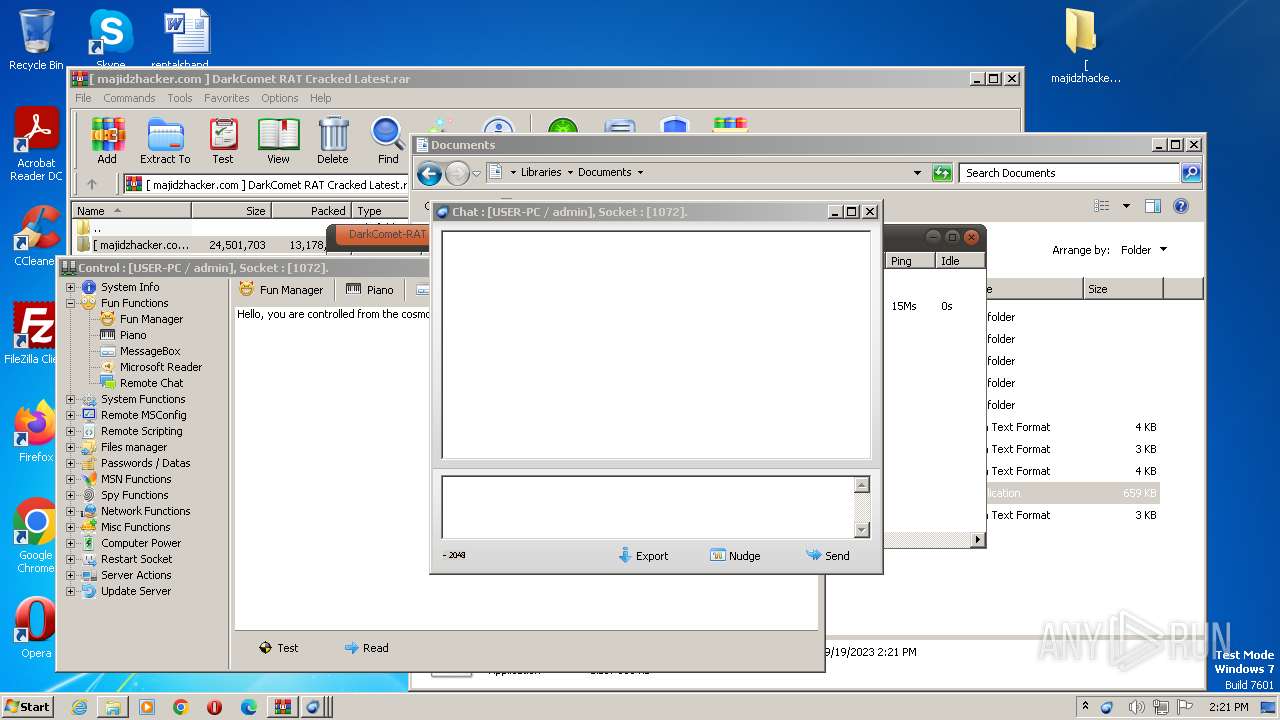
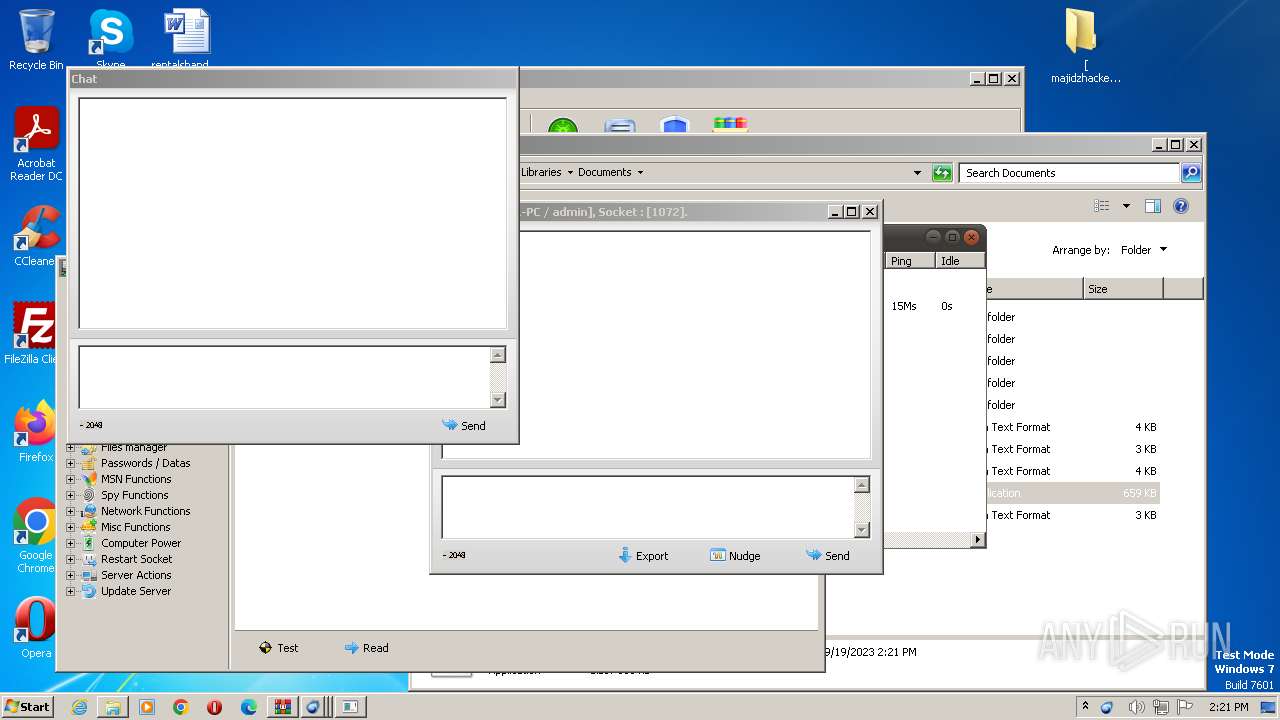
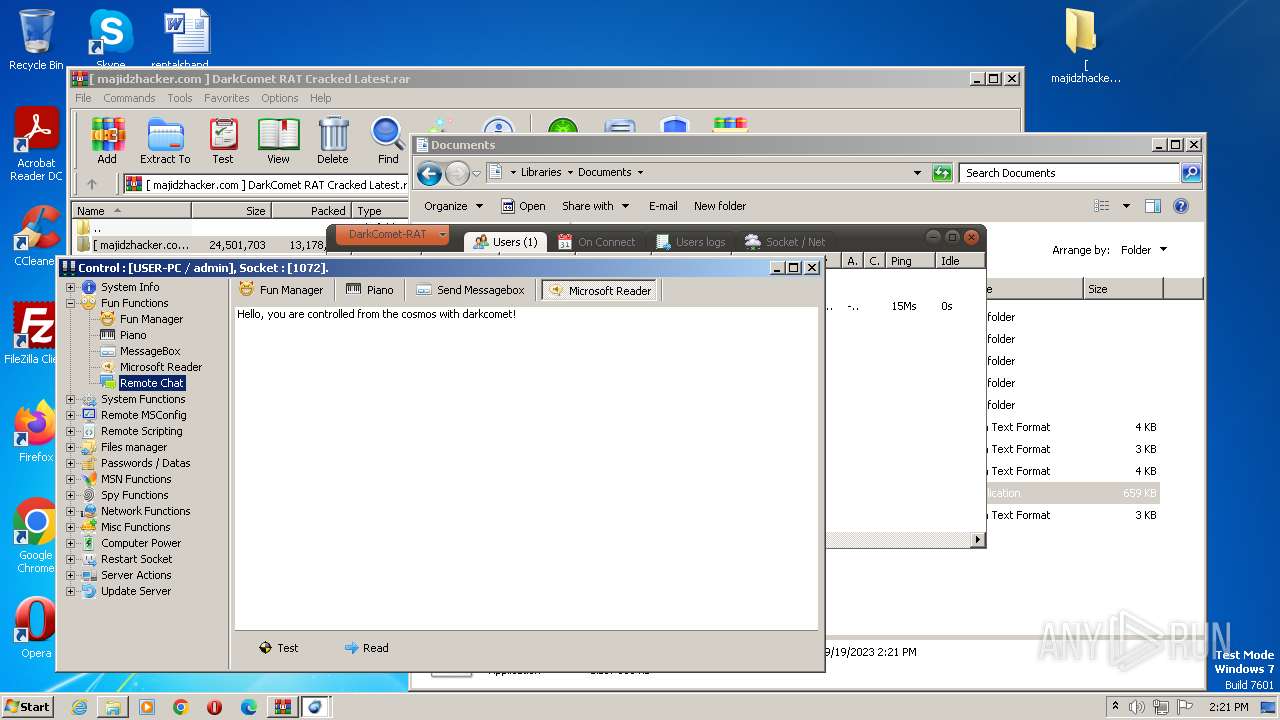
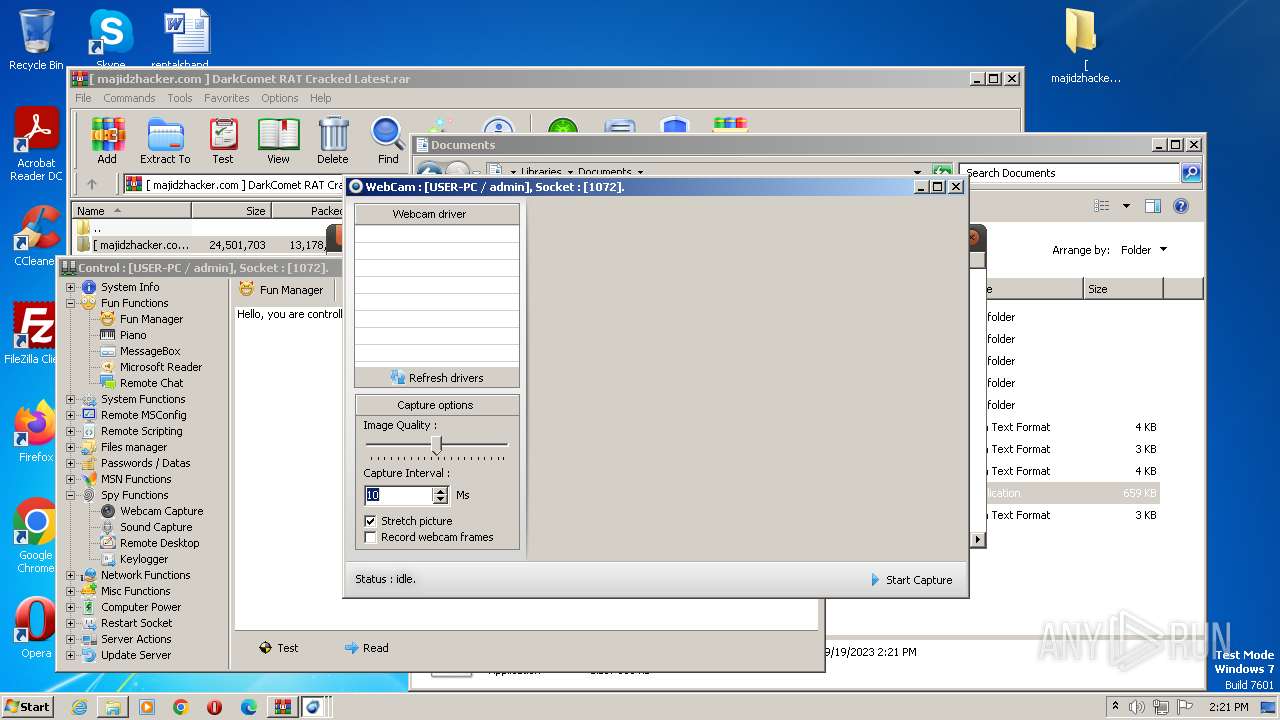
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | September 19, 2023, 13:20:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 20420580C71562F08CB87382049EE48C |
| SHA1: | 0A52CBE0D8C8EE83704706EE3AE8C65CAB2E09F7 |
| SHA256: | CE64CEE73FBA8539362109372A29DF065E111E30B3E3793F01916C1131C7F6E3 |
| SSDEEP: | 393216:DseJjjCMXXnmUVcsZ+VyNH5iMEcYngvgOuByEXOuz:DseJjjCY3mURZ+EZ7E+PGOuz |
MALICIOUS
Application was dropped or rewritten from another process
- DarkComet.exe (PID: 1848)
- upnp.exe (PID: 3800)
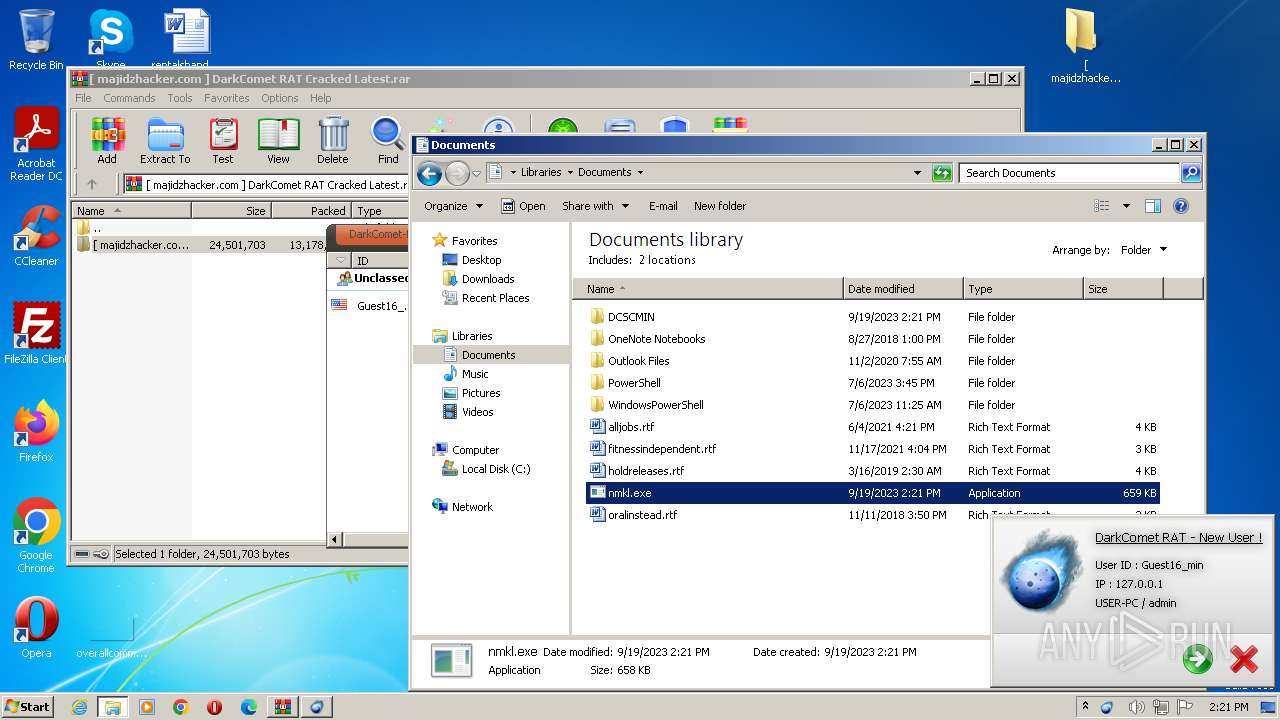
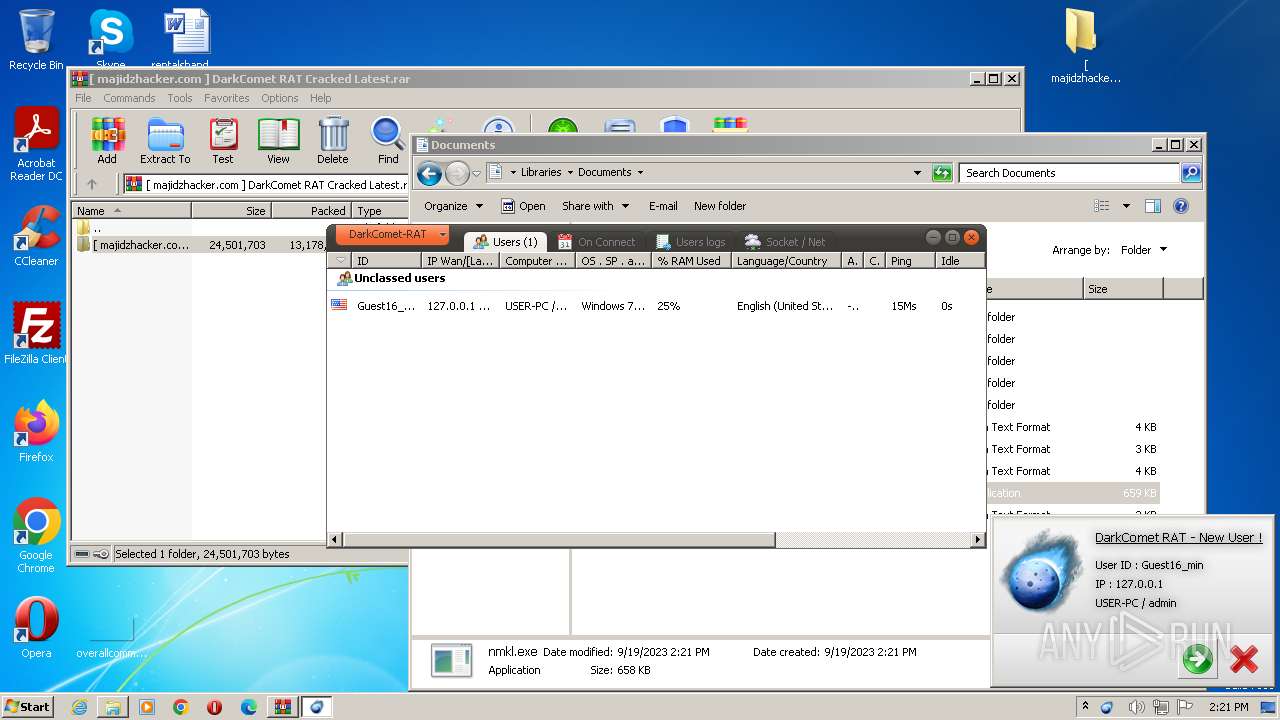
- nmkl.exe (PID: 2992)
- IMDCSC.exe (PID: 2468)
Loads dropped or rewritten executable
- DarkComet.exe (PID: 1848)
DARKCOMET detected by memory dumps
- DarkComet.exe (PID: 1848)
- IMDCSC.exe (PID: 2468)
Changes the login/logoff helper path in the registry
- nmkl.exe (PID: 2992)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 3740)
Reads the Internet Settings
- DarkComet.exe (PID: 1848)
- nmkl.exe (PID: 2992)
Starts itself from another location
- nmkl.exe (PID: 2992)
INFO
Checks supported languages
- DarkComet.exe (PID: 1848)
- upnp.exe (PID: 3800)
- nmkl.exe (PID: 2992)
- IMDCSC.exe (PID: 2468)
Manual execution by a user
- DarkComet.exe (PID: 1848)
- nmkl.exe (PID: 2992)
Reads the computer name
- DarkComet.exe (PID: 1848)
- upnp.exe (PID: 3800)
- nmkl.exe (PID: 2992)
- IMDCSC.exe (PID: 2468)
Create files in a temporary directory
- DarkComet.exe (PID: 1848)
Reads the machine GUID from the registry
- DarkComet.exe (PID: 1848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
42
Monitored processes
6
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1848 | "C:\Users\admin\Desktop\[ majidzhacker.com ] DarkComet RAT Cracked Latest\DarkComet.exe" | C:\Users\admin\Desktop\[ majidzhacker.com ] DarkComet RAT Cracked Latest\DarkComet.exe | explorer.exe | ||||||||||||
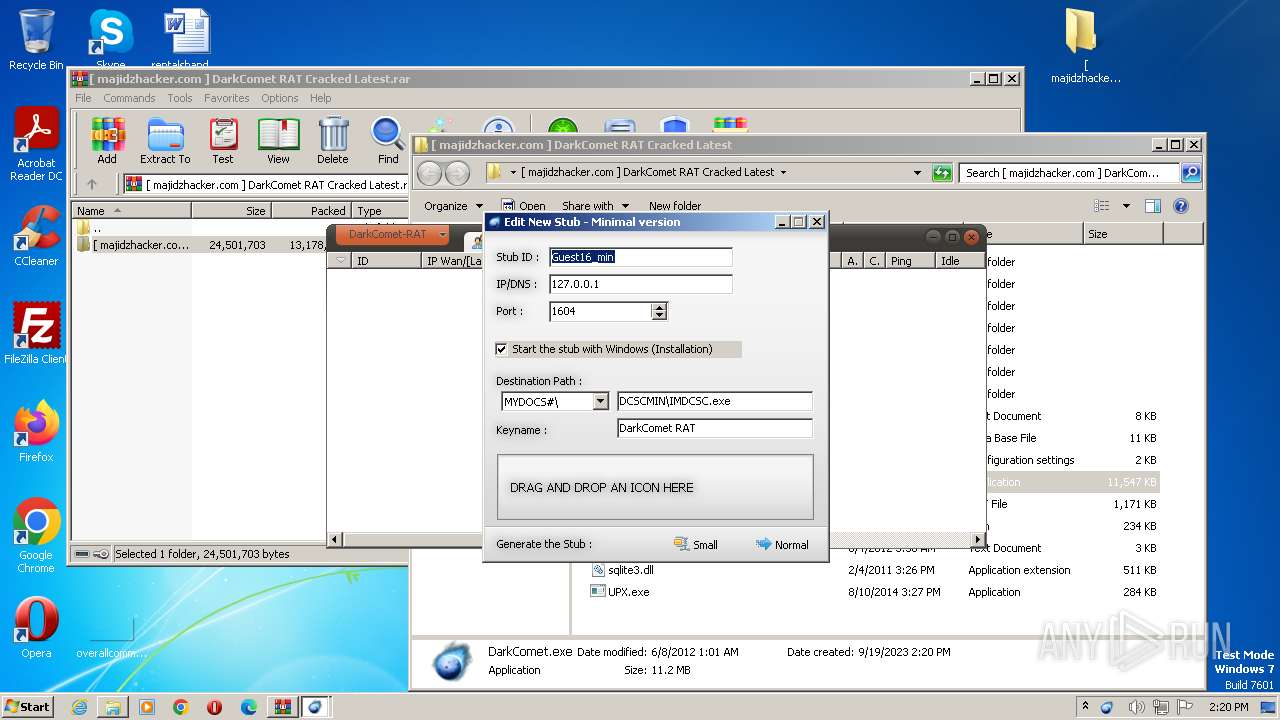
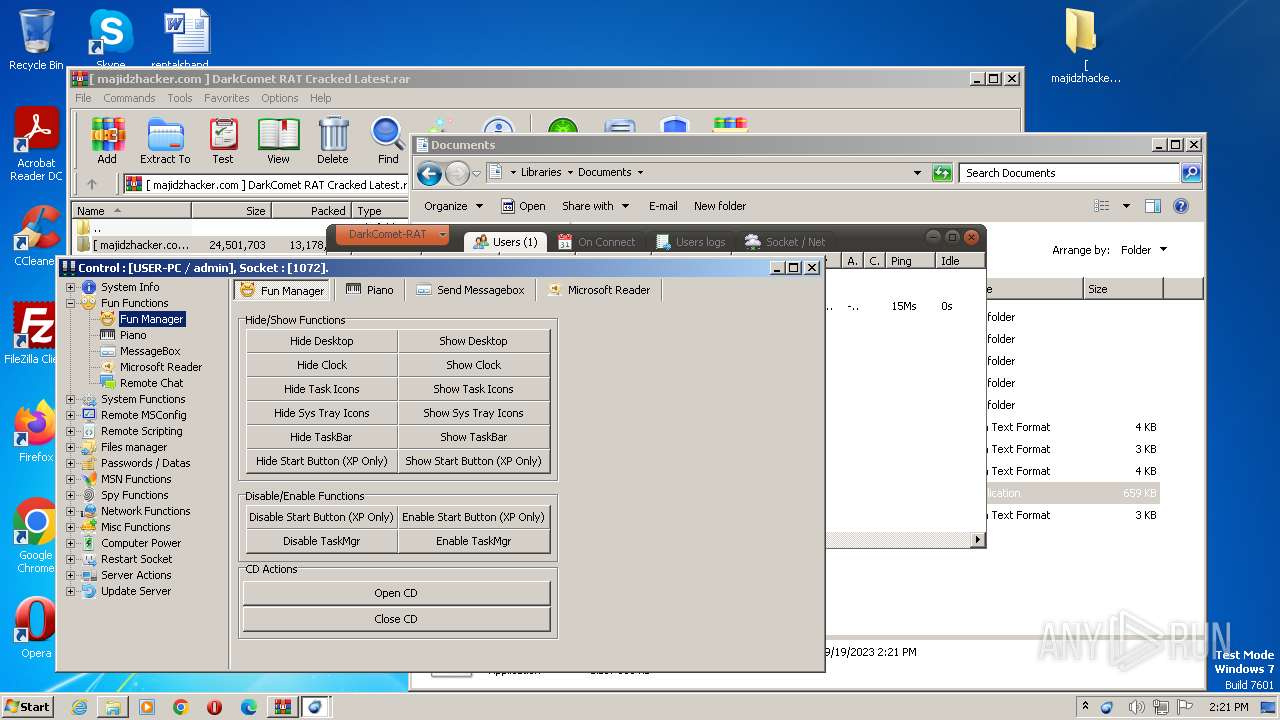
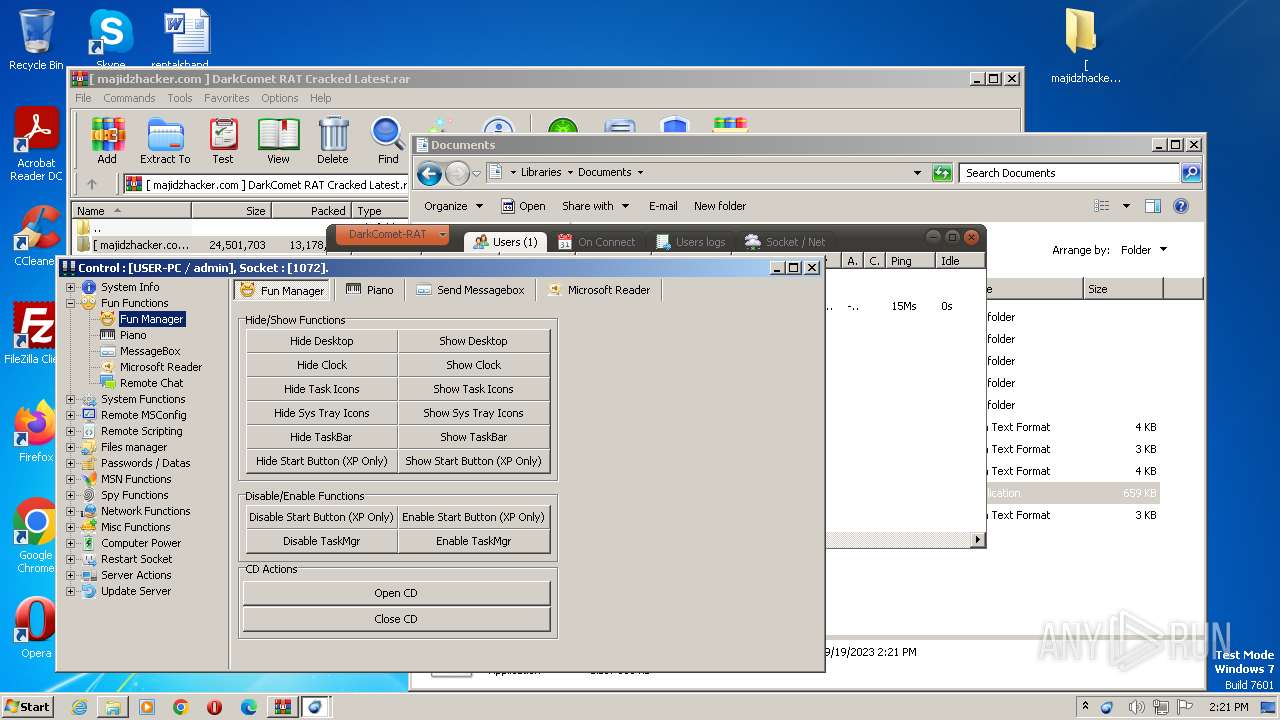
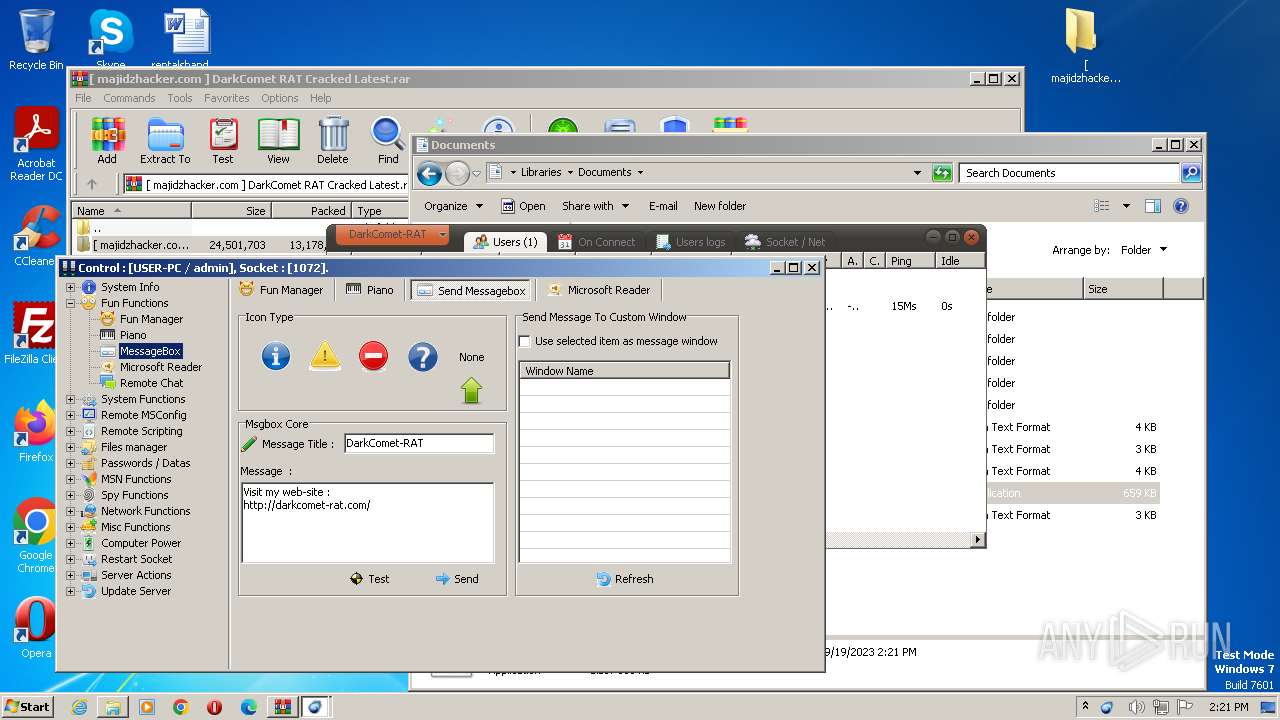
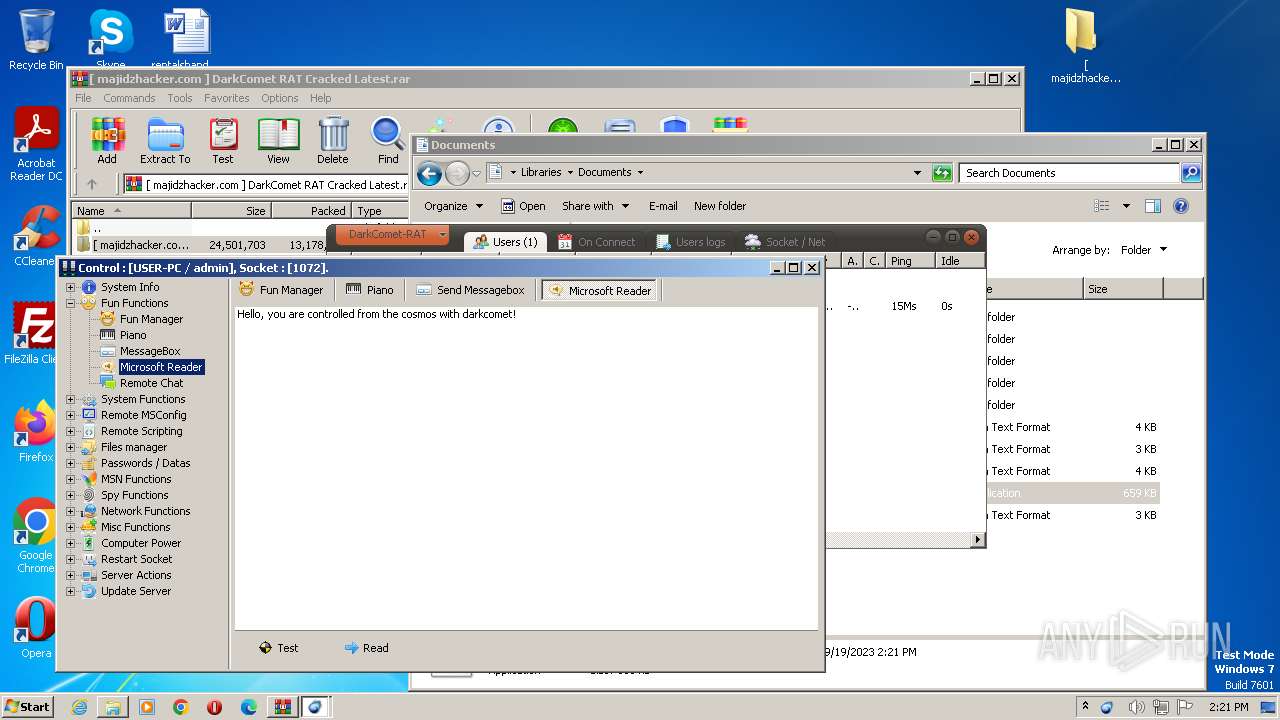
User: admin Company: Unremote.org Integrity Level: MEDIUM Description: A remote administration tool from the cosmos Exit code: 0 Version: 4.2.0.28 Modules
| |||||||||||||||
| 2004 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
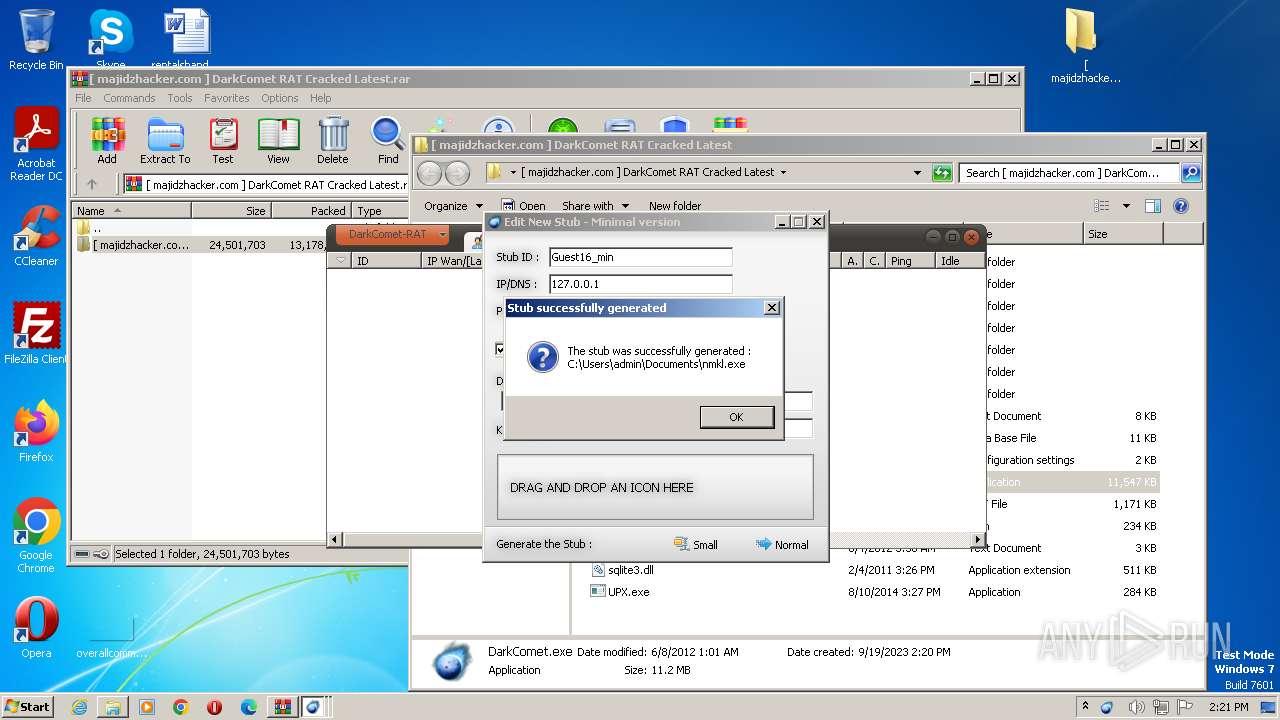
| 2468 | "C:\Users\admin\Documents\DCSCMIN\IMDCSC.exe" | C:\Users\admin\Documents\DCSCMIN\IMDCSC.exe | nmkl.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2992 | "C:\Users\admin\Documents\nmkl.exe" | C:\Users\admin\Documents\nmkl.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corp. Integrity Level: MEDIUM Description: Remote Service Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3740 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\[ majidzhacker.com ] DarkComet RAT Cracked Latest.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
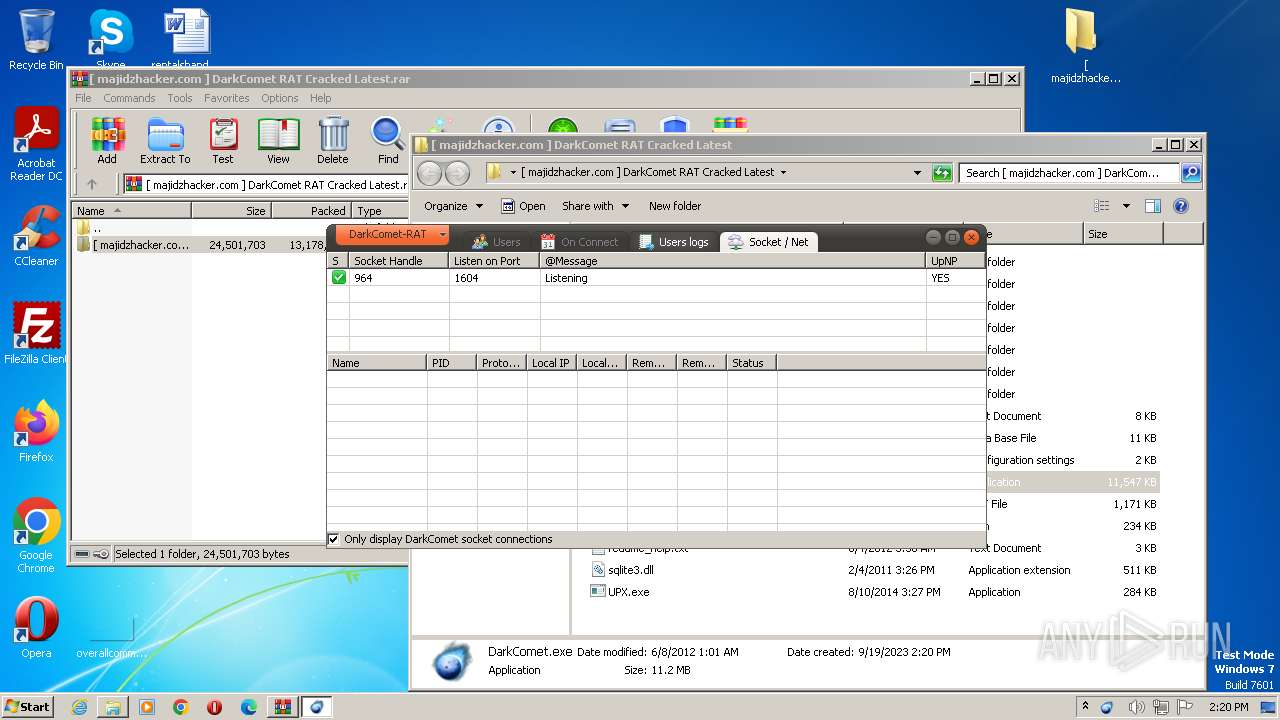
| 3800 | "C:\Users\admin\AppData\Local\Temp\upnp.exe" -a 192.168.100.22 1604 1604 TCP | C:\Users\admin\AppData\Local\Temp\upnp.exe | DarkComet.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
4 421
Read events
4 368
Write events
51
Delete events
2
Modification events
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3740) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2004) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1848) DarkComet.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
11
Suspicious files
135
Text files
37
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.11767\[ majidzhacker.com ] DarkComet RAT Cracked Latest\GeoIP.dat | binary | |
MD5:B64EA0C3E9617CCD2F22D8568676A325 | SHA256:432E12E688449C2CF1B184C94E2E964F9E09398C194888A7FE1A5B1F8CF3059B | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.11767\[ majidzhacker.com ] DarkComet RAT Cracked Latest\config.ini | text | |
MD5:E199C4E709880EFD06D4B4C95A23907A | SHA256:79699DFEF4001B7551E0772515B73439D4333C77CA94F369896A8C5A2C73DD58 | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.11767\[ majidzhacker.com ] DarkComet RAT Cracked Latest\Goodies\wallpaper_1.jpg | image | |
MD5:F72131120657B33655E6EC741FC2C407 | SHA256:9C53C010DB6E61ED6CA7A484D3FFB23BA1BD8B6EEE6CFA652F1C5647ADDC2280 | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.11767\[ majidzhacker.com ] DarkComet RAT Cracked Latest\comet.db | binary | |
MD5:55BABB7E2ED20A578379A79C50720AFD | SHA256:741557AE4F8E0839A366E9D30679573E15907BC722DEB3BBA86618B55027D781 | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.11767\[ majidzhacker.com ] DarkComet RAT Cracked Latest\Icons\againzip.ico | image | |
MD5:B87DBD32F31532EA8F7AF9D28EE7800C | SHA256:C3C3B009CB602535C18ED168C0BC448441A62B63C69FF27E3F9C2D8973411250 | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.11767\[ majidzhacker.com ] DarkComet RAT Cracked Latest\ico.ico | image | |
MD5:E287273CBE56DE53258E42B735A04FE6 | SHA256:EC4BEDE8CBBCA42BB99BBF24303B8CACB18D5FBF29B2EAC95A8D8316B4EF60C4 | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.11767\[ majidzhacker.com ] DarkComet RAT Cracked Latest\Goodies\wallpaper_2.jpg | image | |
MD5:11D20F268B9A0DBC43F95C93ABD30E30 | SHA256:0A62D0CE4F2ECDEC5CE2F7596BBBF97ED14FD8793C247C32B65A91BA6084BDD9 | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.11767\[ majidzhacker.com ] DarkComet RAT Cracked Latest\changelog.txt | text | |
MD5:7A23E5B811DD52E99CBDB72A7FE4CE12 | SHA256:7CF268D2FBBC3BB3E1CE2019D53F7C88B42F3BBCD4833AC69798D34FBD809DFE | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.11767\[ majidzhacker.com ] DarkComet RAT Cracked Latest\Desktop.ini | text | |
MD5:6141A814C5B4B2C8E68568533BB63FEE | SHA256:2834EA632EB413998AEAF63B6588C99427FEA5B78164D36C070D10E9B9ED19D3 | |||
| 3740 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3740.11767\[ majidzhacker.com ] DarkComet RAT Cracked Latest\Icons\cubic.ico | image | |
MD5:F273CF2C932B6D768BB2D1D62E9D2A4A | SHA256:713CC5EDE2B35AE4933AD31B02B7C4BDA1255C9709B219A13162B72F228DF652 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3800 | upnp.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |