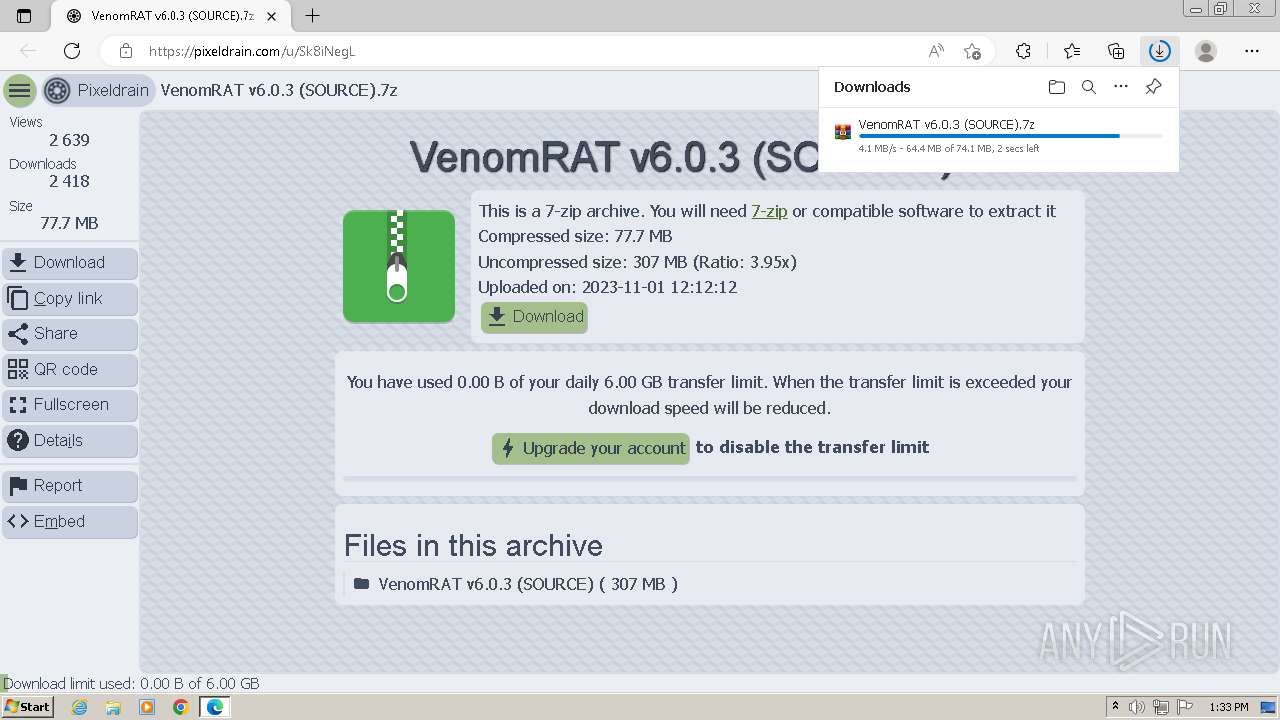
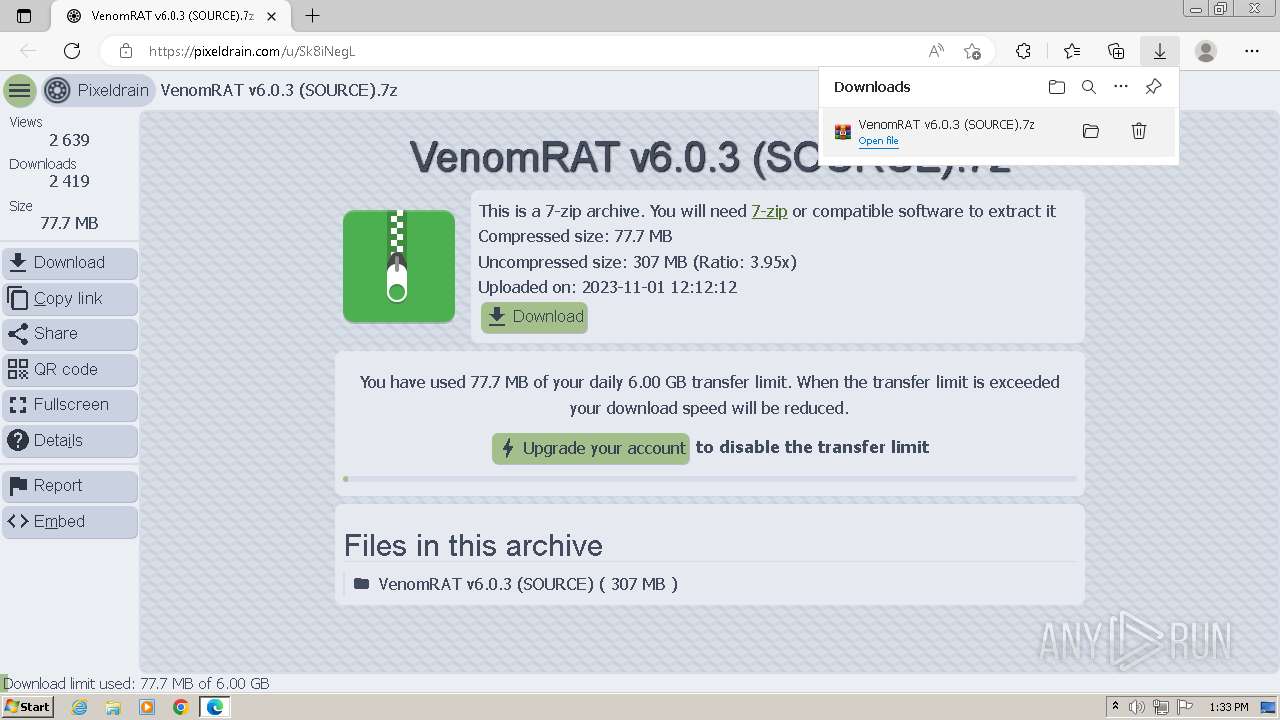
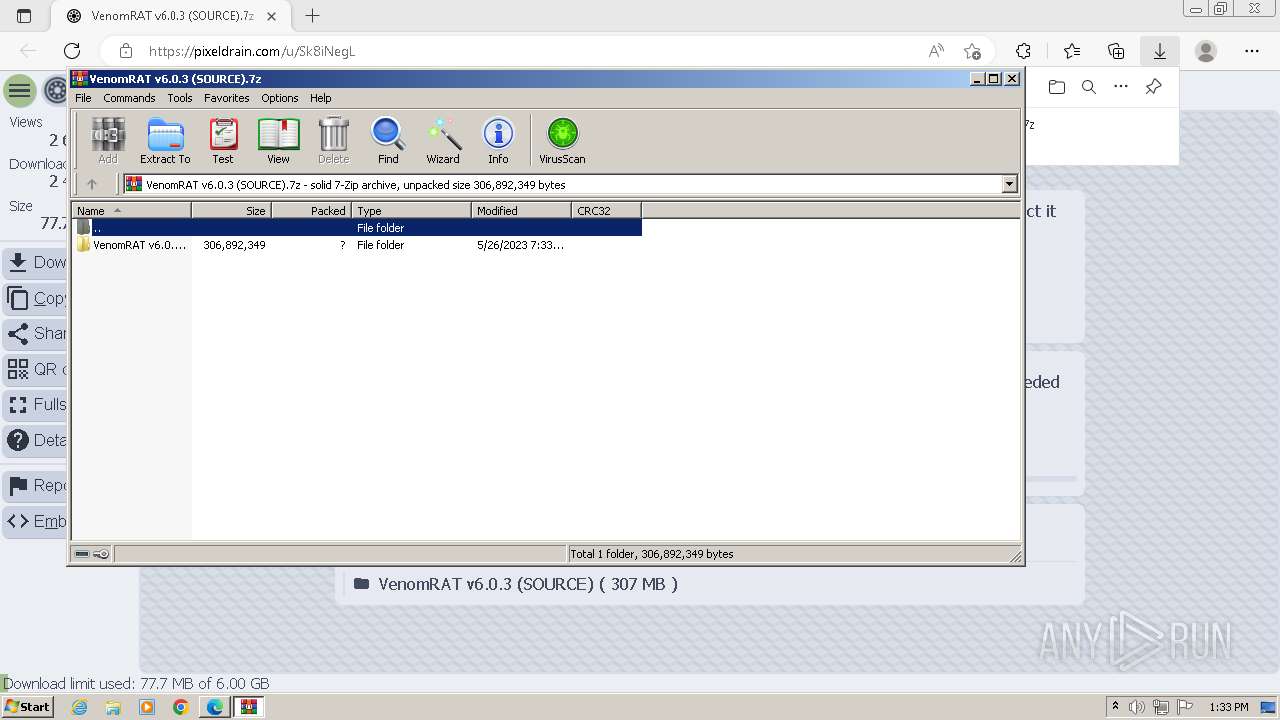
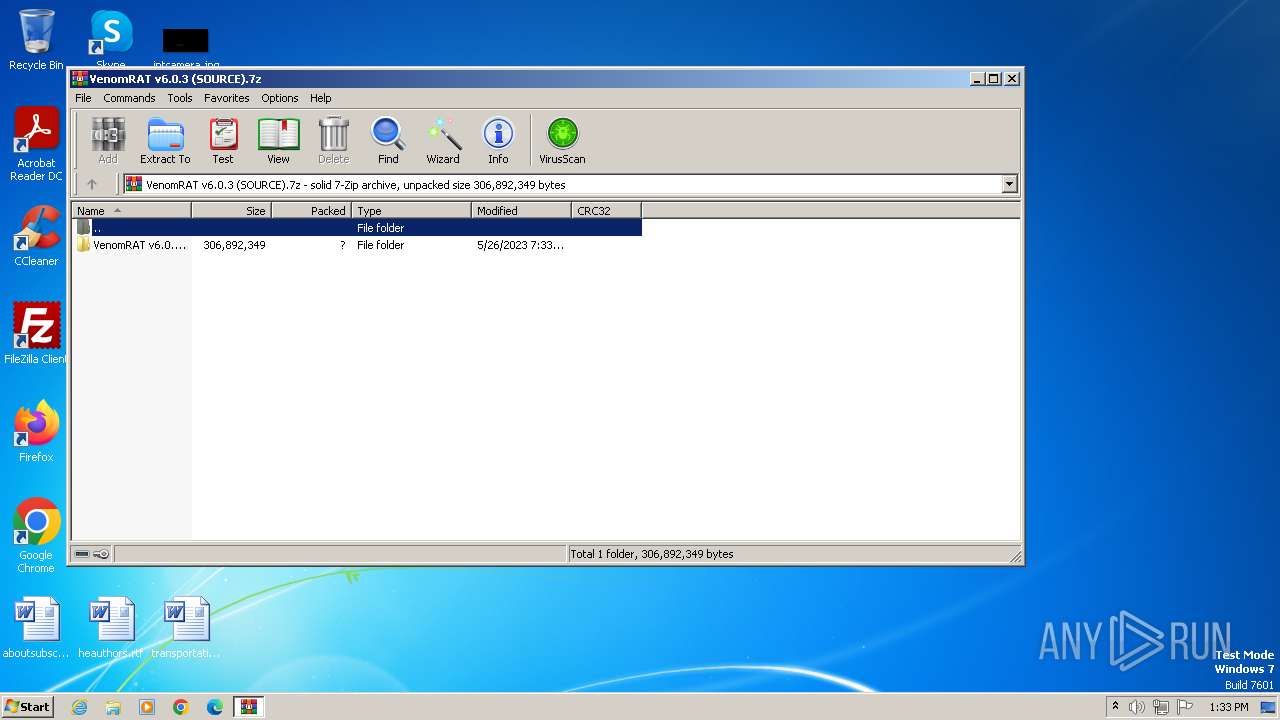
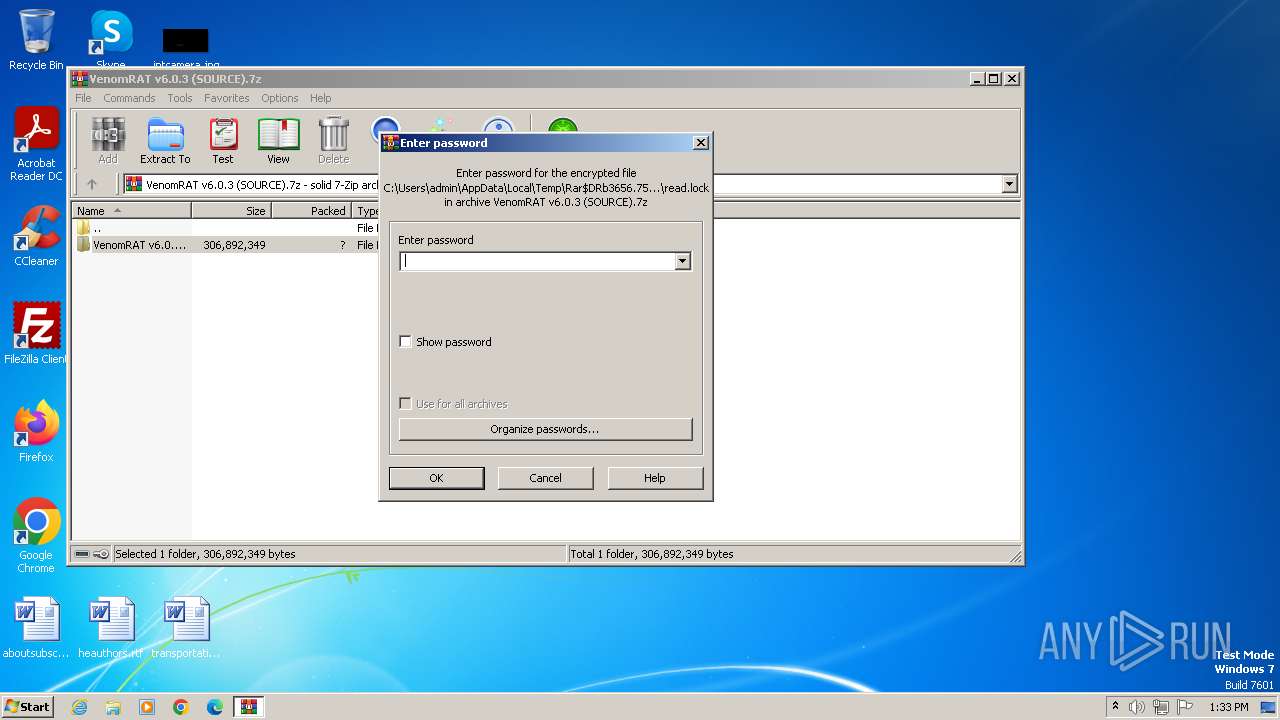
| URL: | https://pixeldrain.com/u/Sk8iNegL |
| Full analysis: | https://app.any.run/tasks/38952d5c-8a9d-4833-9631-3e3c690d3758 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | January 08, 2025, 13:32:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3D5B97F4C21301274F9DD32C4A768D33 |
| SHA1: | F5EBEFEA59A38011DD48A985E37D70B1D1C019BC |
| SHA256: | CE0E35A78686830F780ACBB7CFE8D6DEC1206C82BF2303D05F9D159BDD0CDAEF |
| SSDEEP: | 3:N8Icl/GKg8Orpn:2IG/dgNrpn |
MALICIOUS
ASYNCRAT has been detected (YARA)
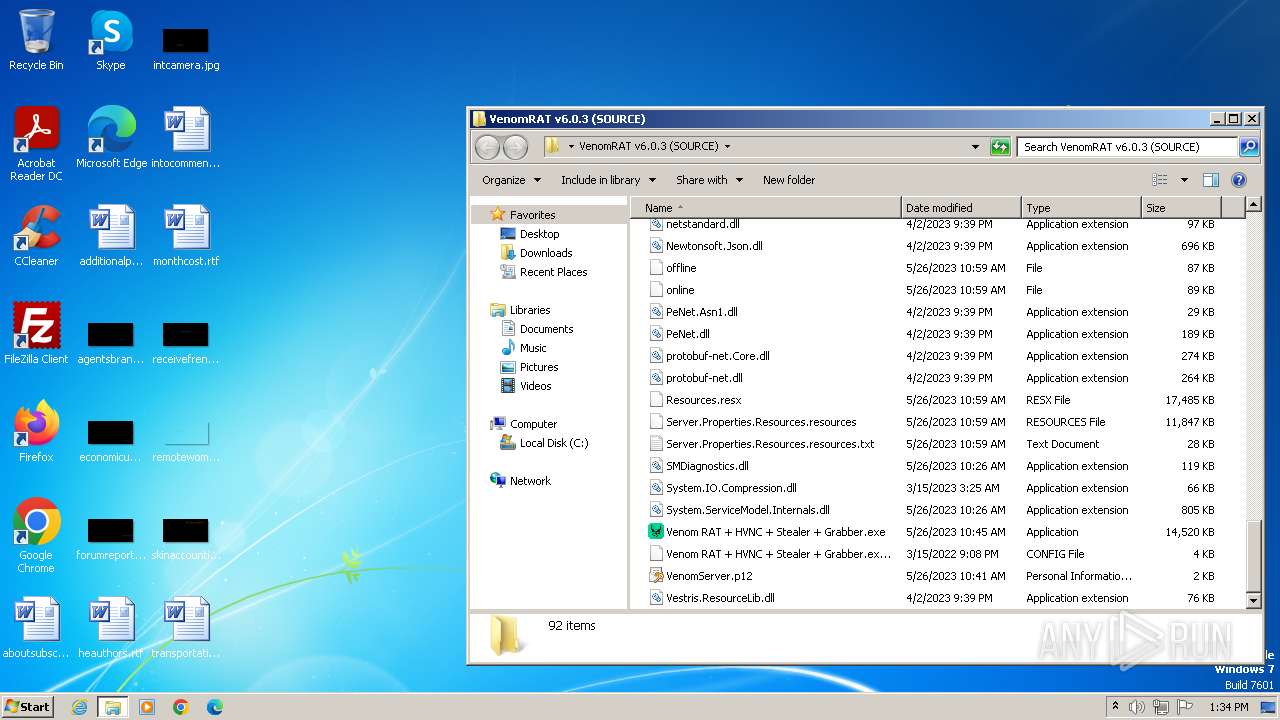
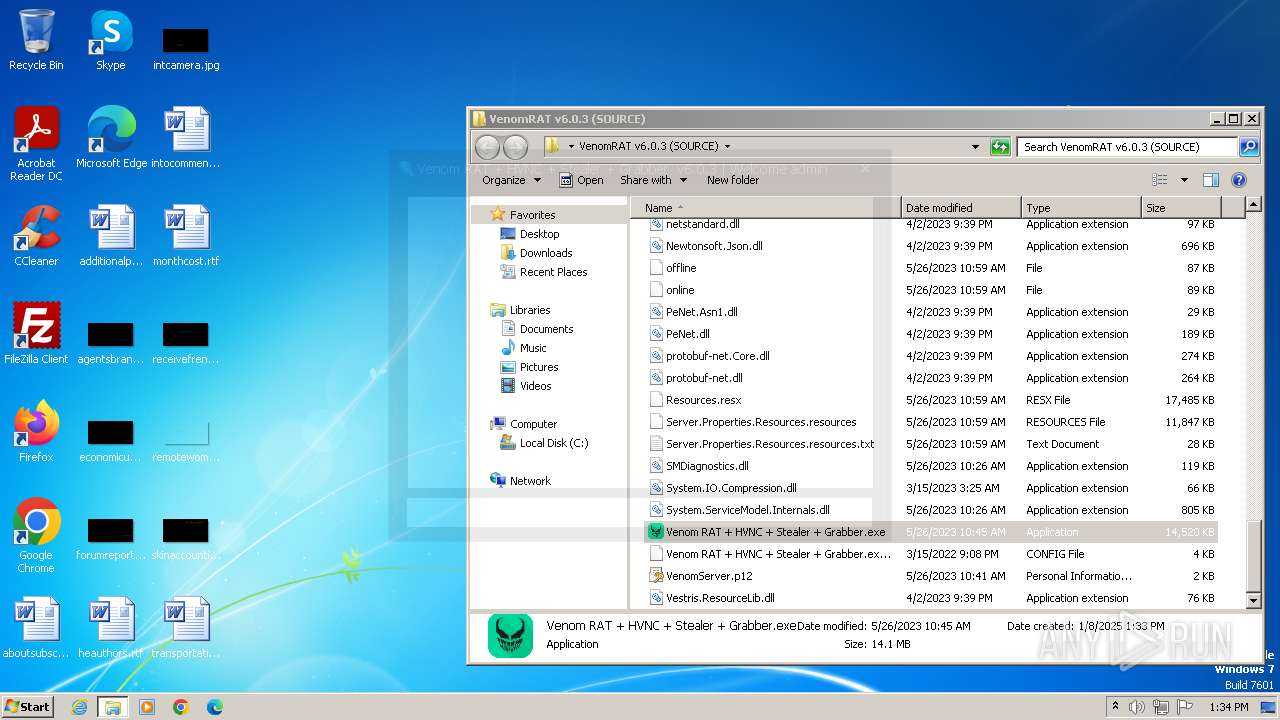
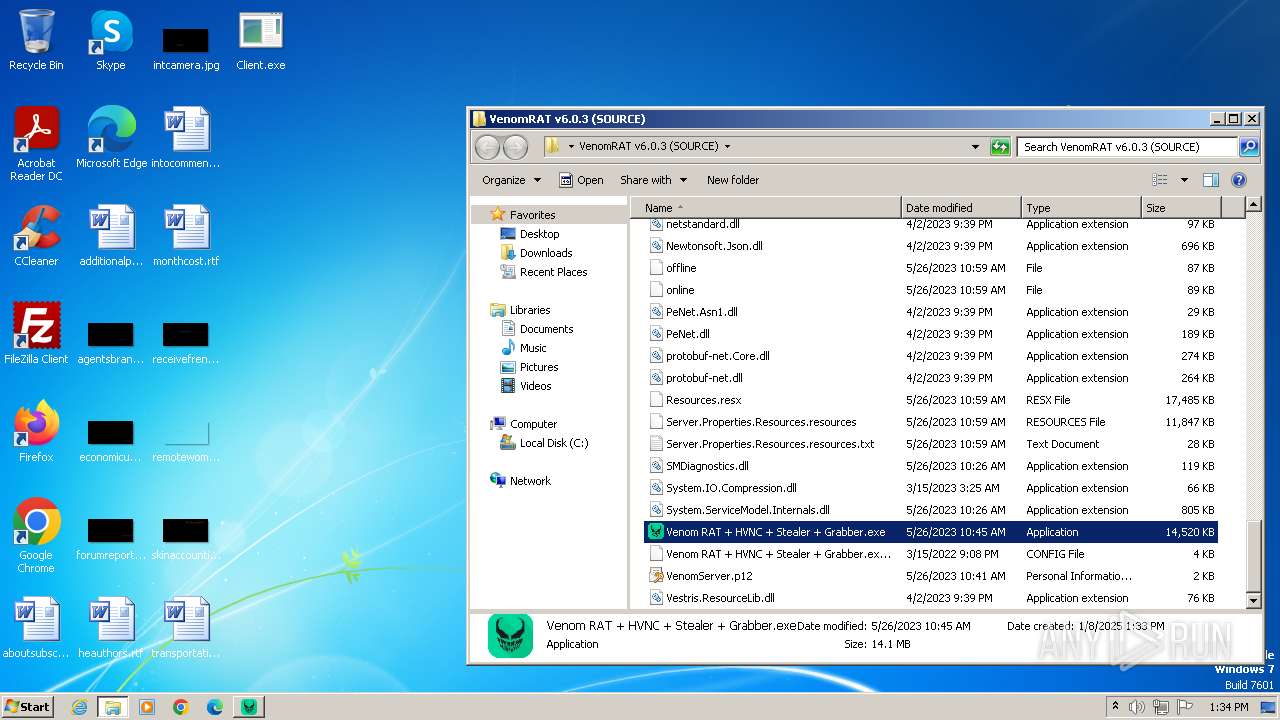
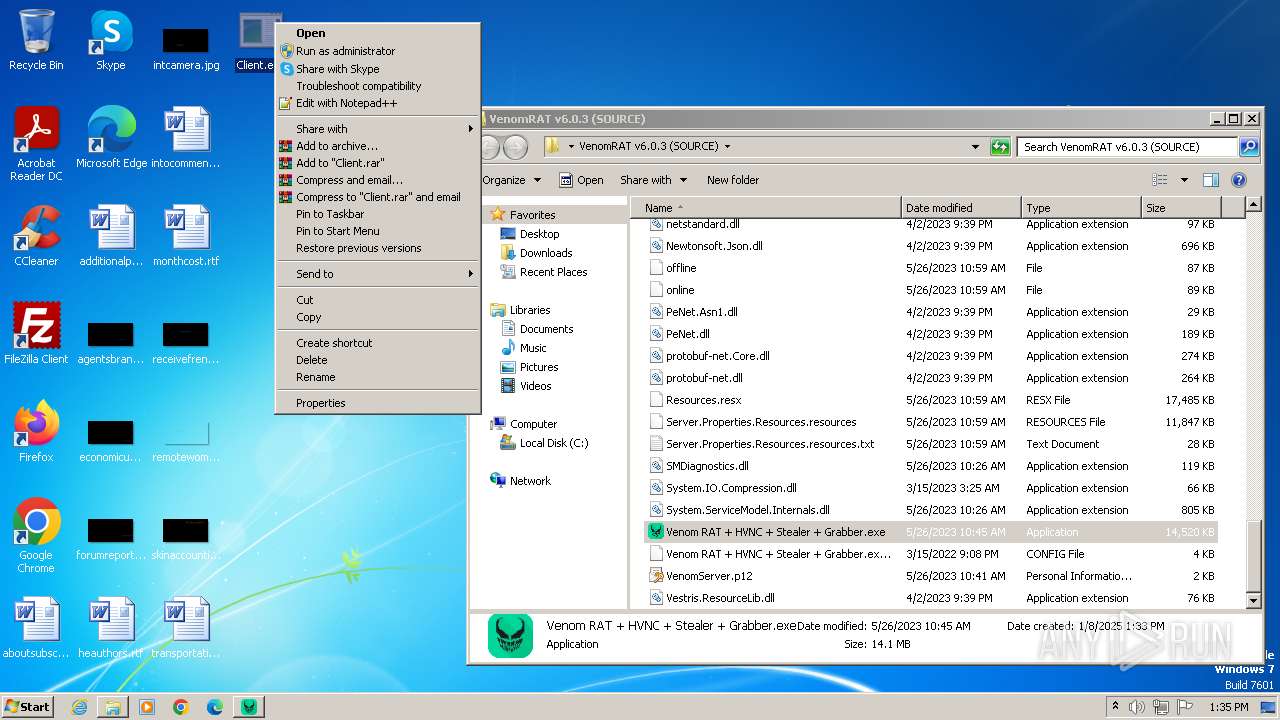
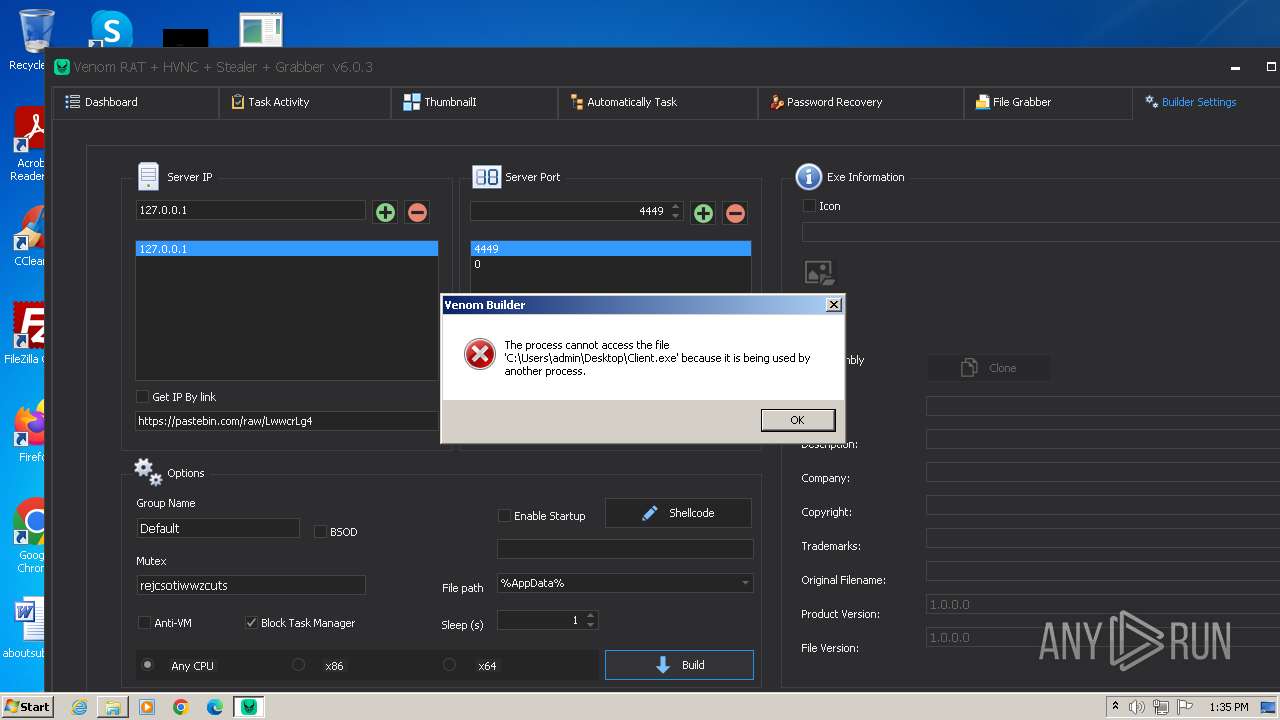
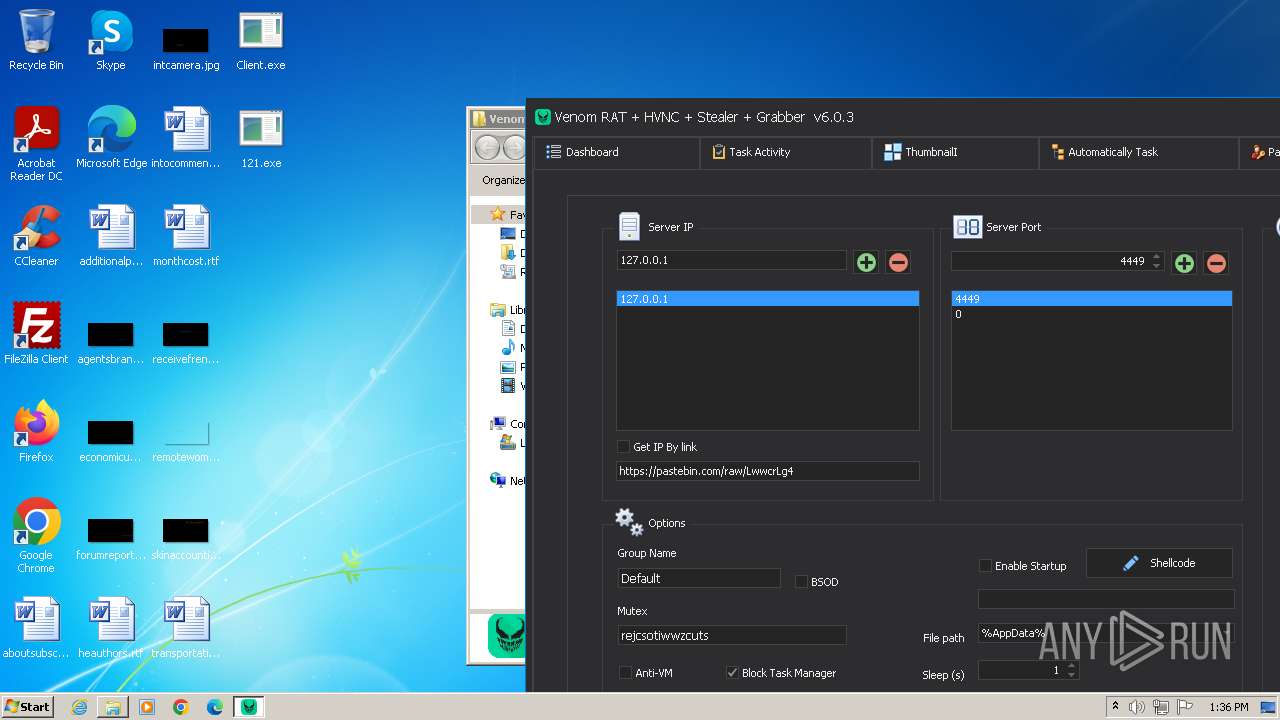
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
- Client.exe (PID: 2568)
SUSPICIOUS
Reads security settings of Internet Explorer
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3656)
Possible usage of Discord/Telegram API has been detected (YARA)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
Executable content was dropped or overwritten
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
There is functionality for taking screenshot (YARA)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
Reads settings of System Certificates
- Client.exe (PID: 2568)
Searches for installed software
- Client.exe (PID: 2568)
Reads Microsoft Outlook installation path
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3656)
Reads the Internet Settings
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 848)
- wmpnscfg.exe (PID: 1388)
- Client.exe (PID: 2568)
- 121.exe (PID: 992)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
Checks supported languages
- wmpnscfg.exe (PID: 1388)
- wmpnscfg.exe (PID: 848)
- Client.exe (PID: 2568)
- 121.exe (PID: 992)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
The process uses the downloaded file
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
- msedge.exe (PID: 3200)
- WinRAR.exe (PID: 3656)
Reads the machine GUID from the registry
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
- Client.exe (PID: 2568)
- 121.exe (PID: 992)
Manual execution by a user
- wmpnscfg.exe (PID: 848)
- wmpnscfg.exe (PID: 1388)
- Client.exe (PID: 2568)
- 121.exe (PID: 992)
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
Application launched itself
- msedge.exe (PID: 1016)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3656)
Reads Microsoft Office registry keys
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
Themida protector has been detected
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
Reads Environment values
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
- Client.exe (PID: 2568)
- 121.exe (PID: 992)
Reads product name
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
Reads the software policy settings
- Client.exe (PID: 2568)
Creates files or folders in the user directory
- Venom RAT + HVNC + Stealer + Grabber.exe (PID: 3960)
- Client.exe (PID: 2568)
The sample compiled with english language support
- WinRAR.exe (PID: 3656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
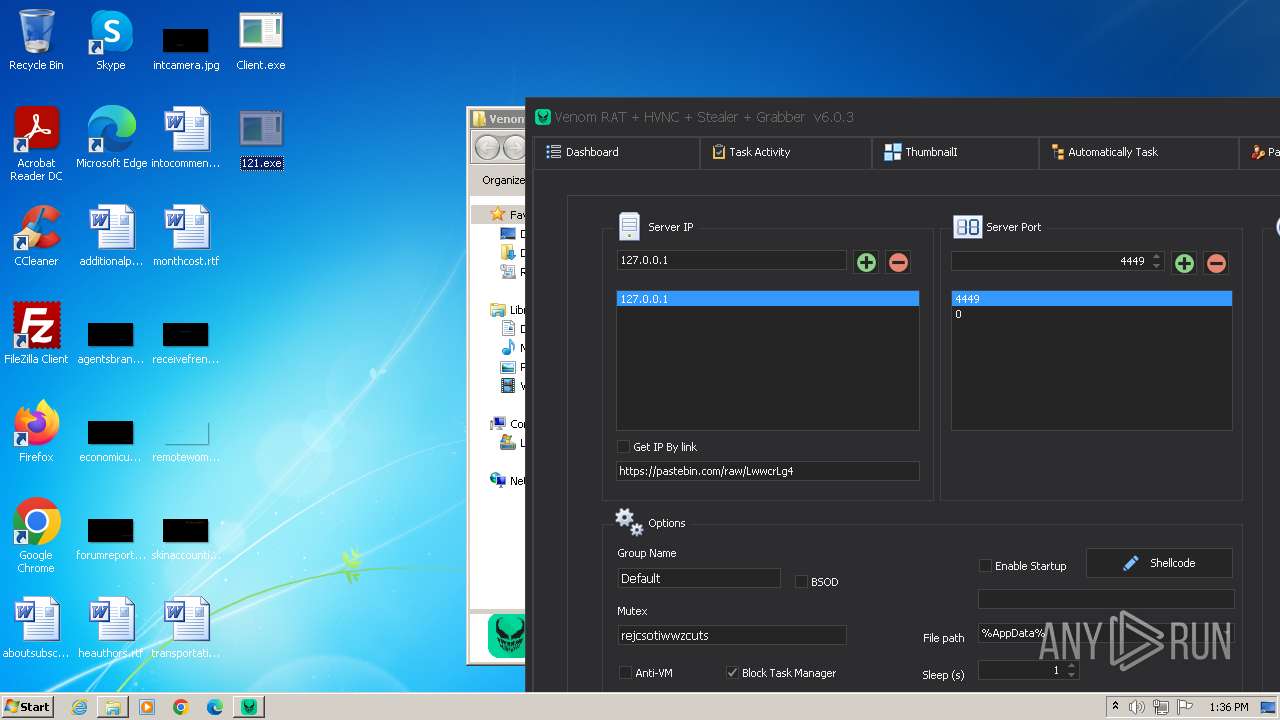
(PID) Process(3960) Venom RAT + HVNC + Stealer + Grabber.exe
Telegram-Tokens (1)5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ
Telegram-Info-Links
5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ
Get info about bothttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getMe
Get incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getUpdates
Get webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5819716395:AAEP-yuJ_QA22yswxx2C-lVY5yPkxnaxFMQ/deleteWebhook?drop_pending_updates=true
Discord-Webhook-Tokens (1)1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Discord-Info-Links
1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Get Webhook Infohttps://discord.com/api/webhooks/1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Discord-Webhook-Tokens (1)1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Discord-Info-Links
1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
Get Webhook Infohttps://discord.com/api/webhooks/1016614786533969920/fMJOOjA1pZqjV8_s0JC86KN9Fa0FeGPEHaEak8WTADC18s5Xnk3vl2YBdVD37L0qTWnM
AsyncRat
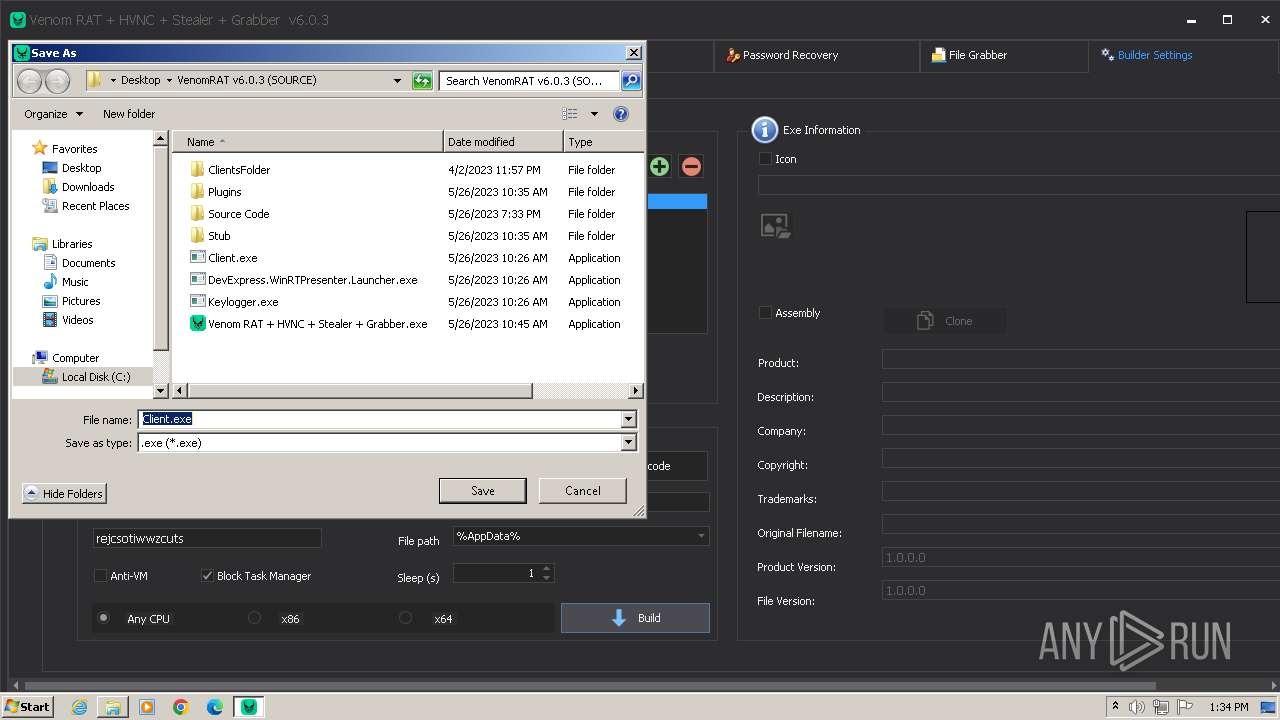
(PID) Process(2568) Client.exe
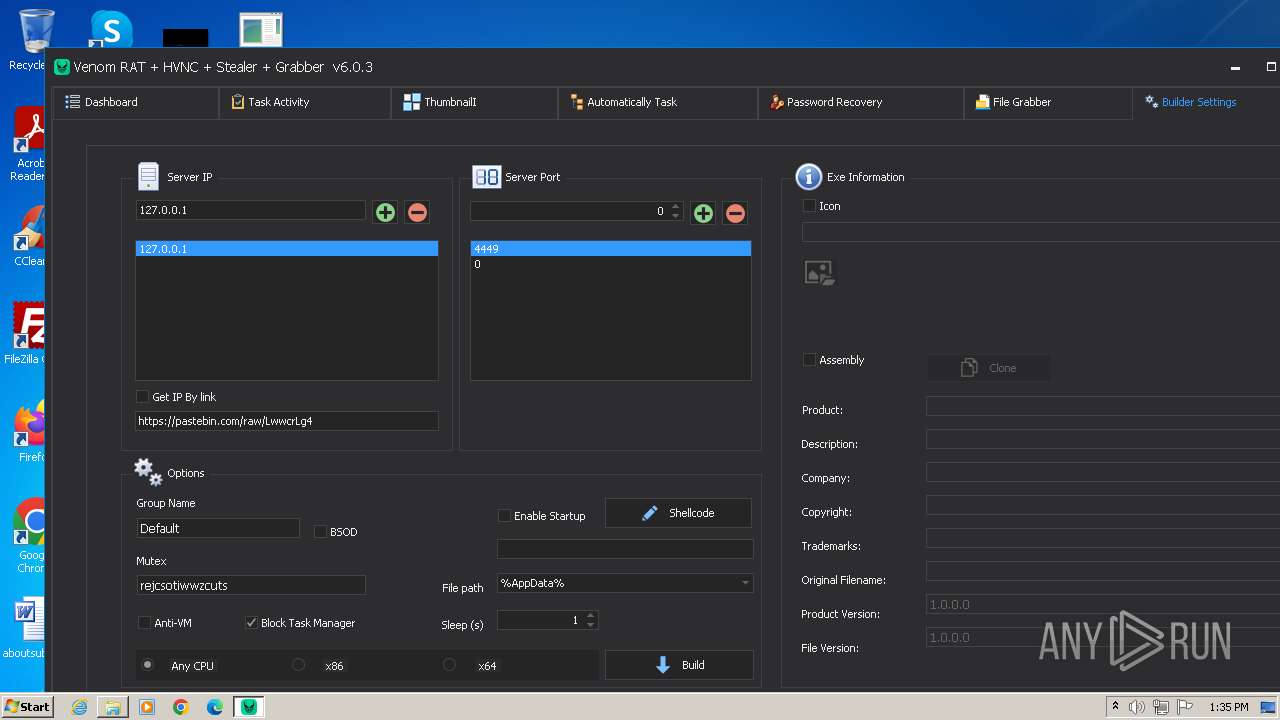
C2 (1)127.0.0.1
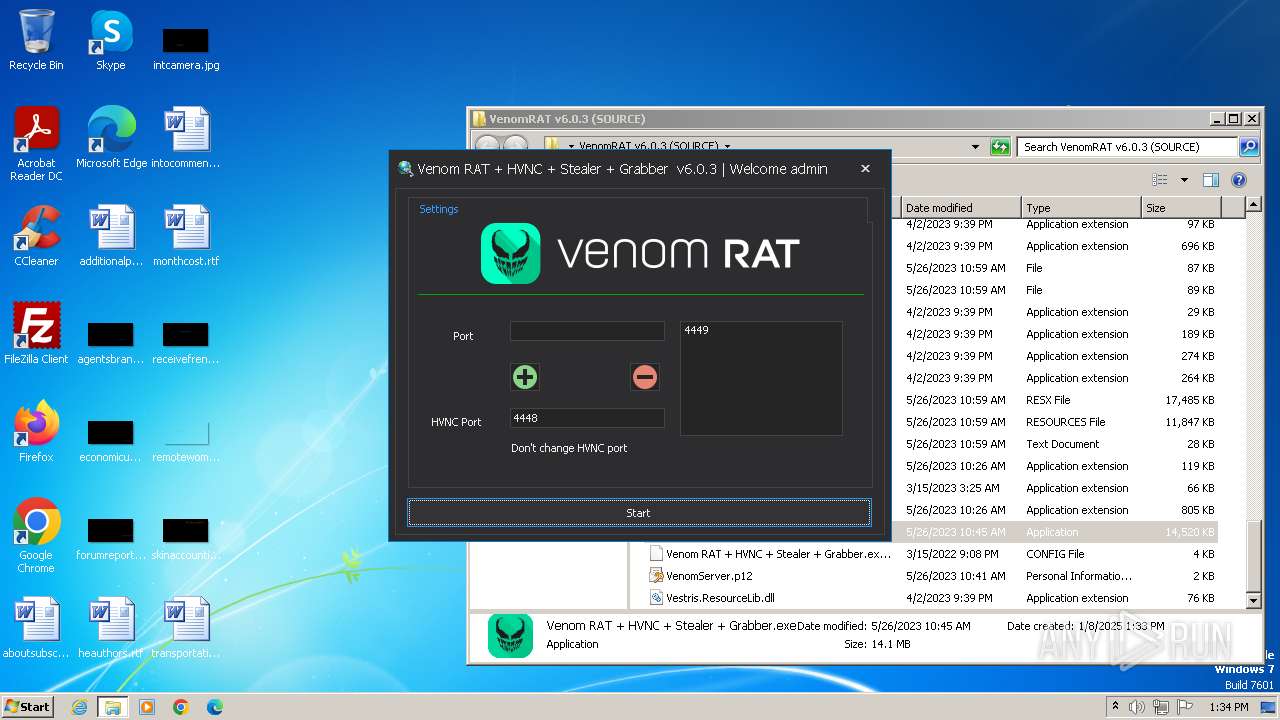
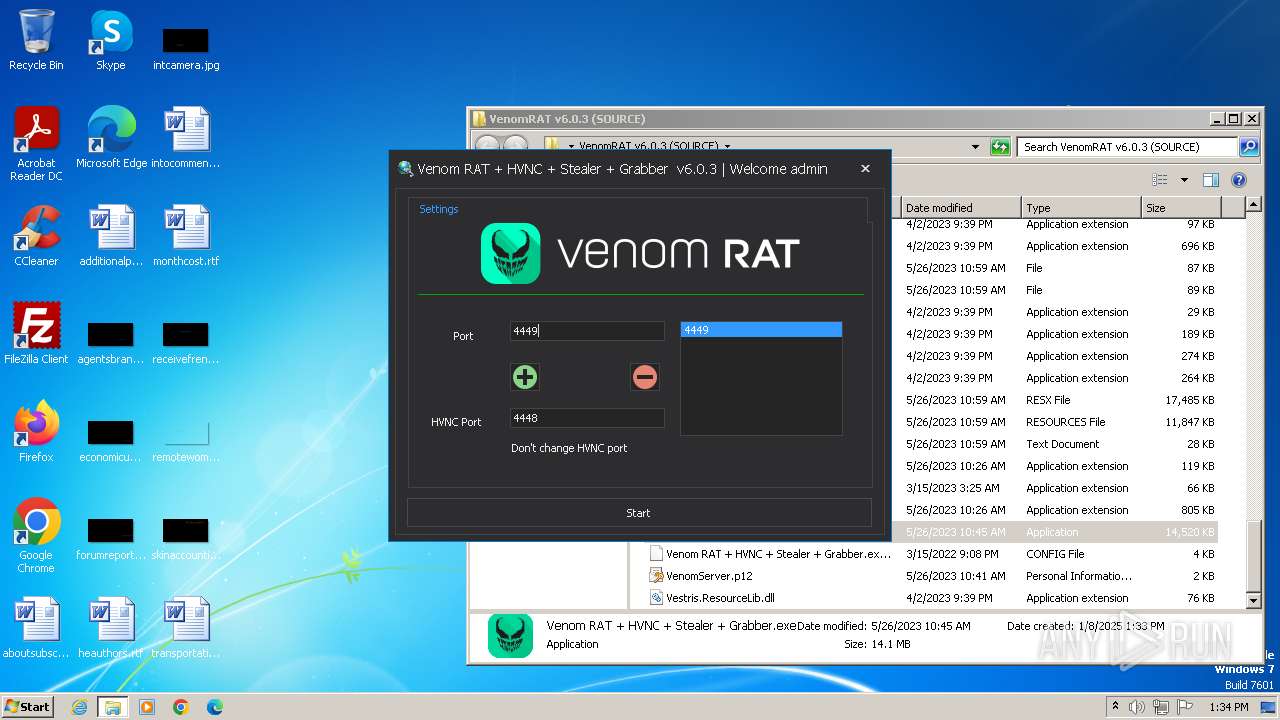
Ports (2)4449
0
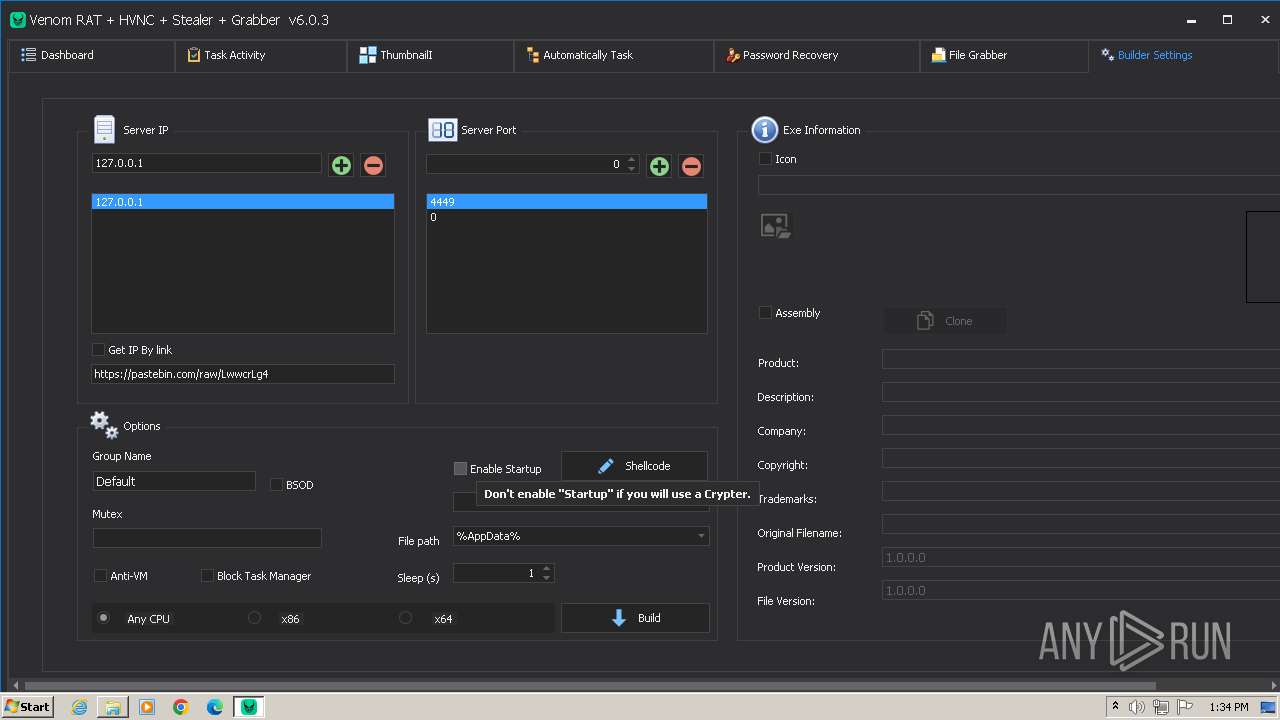
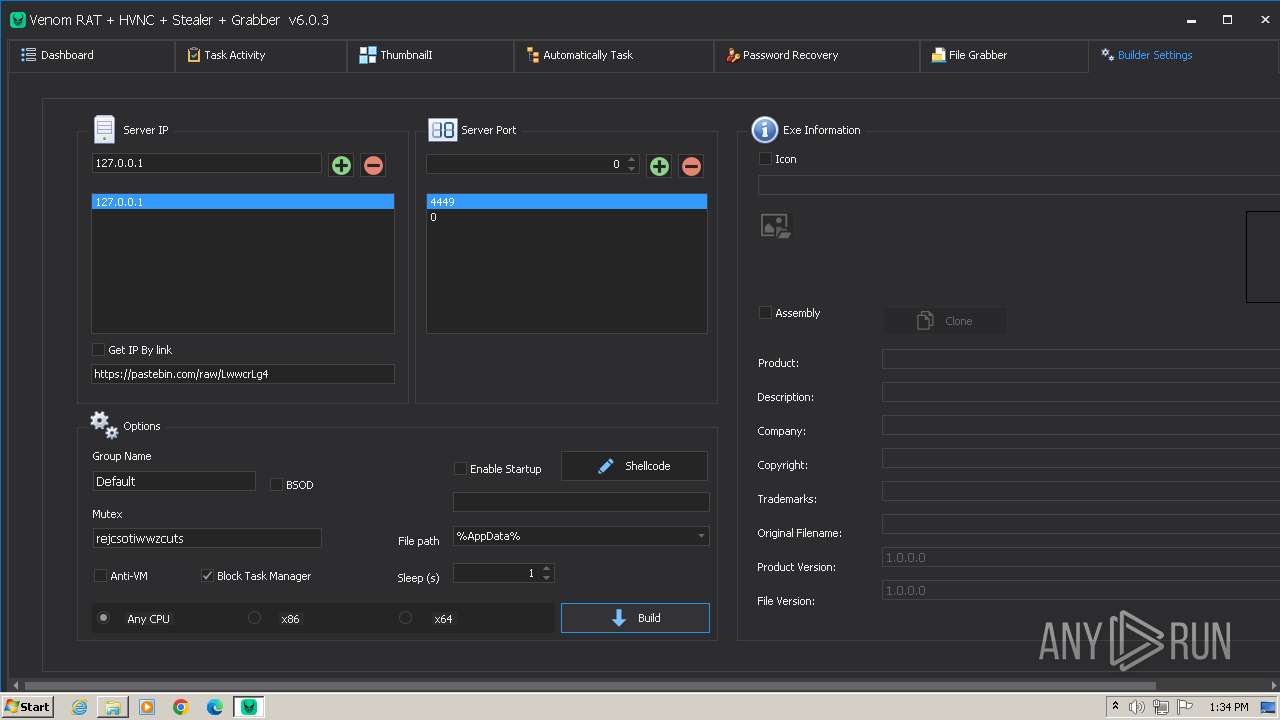
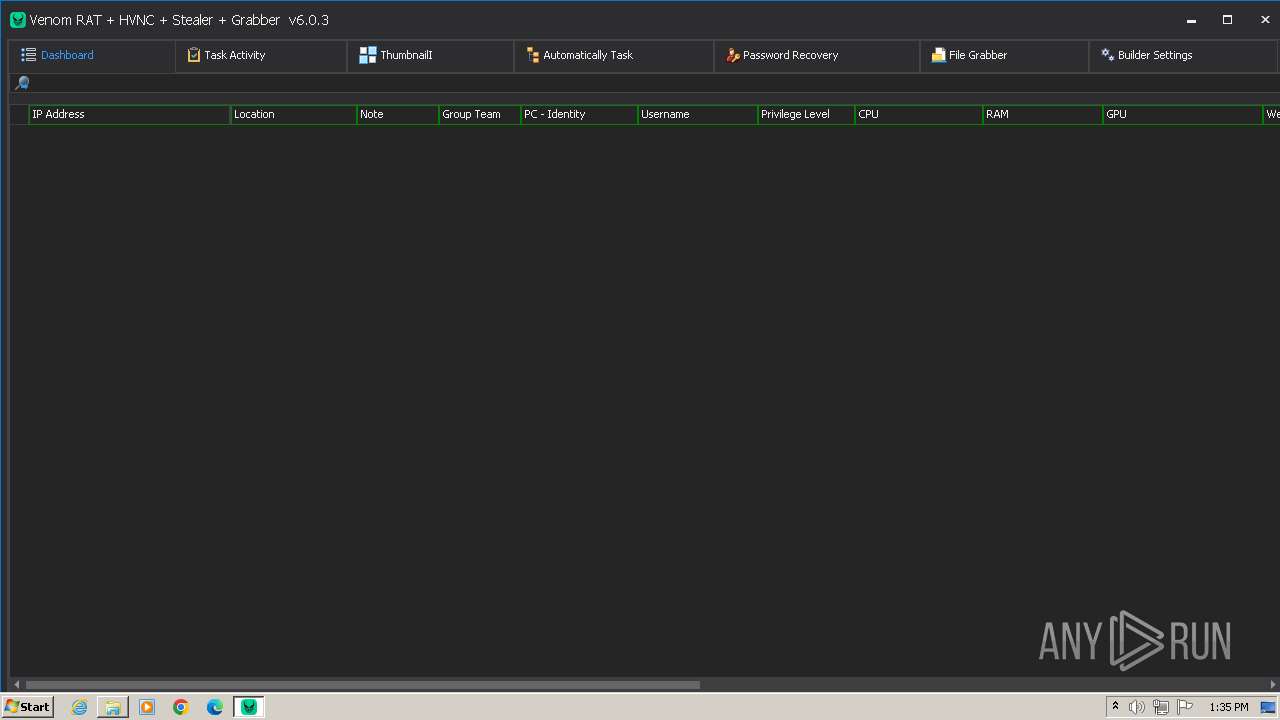
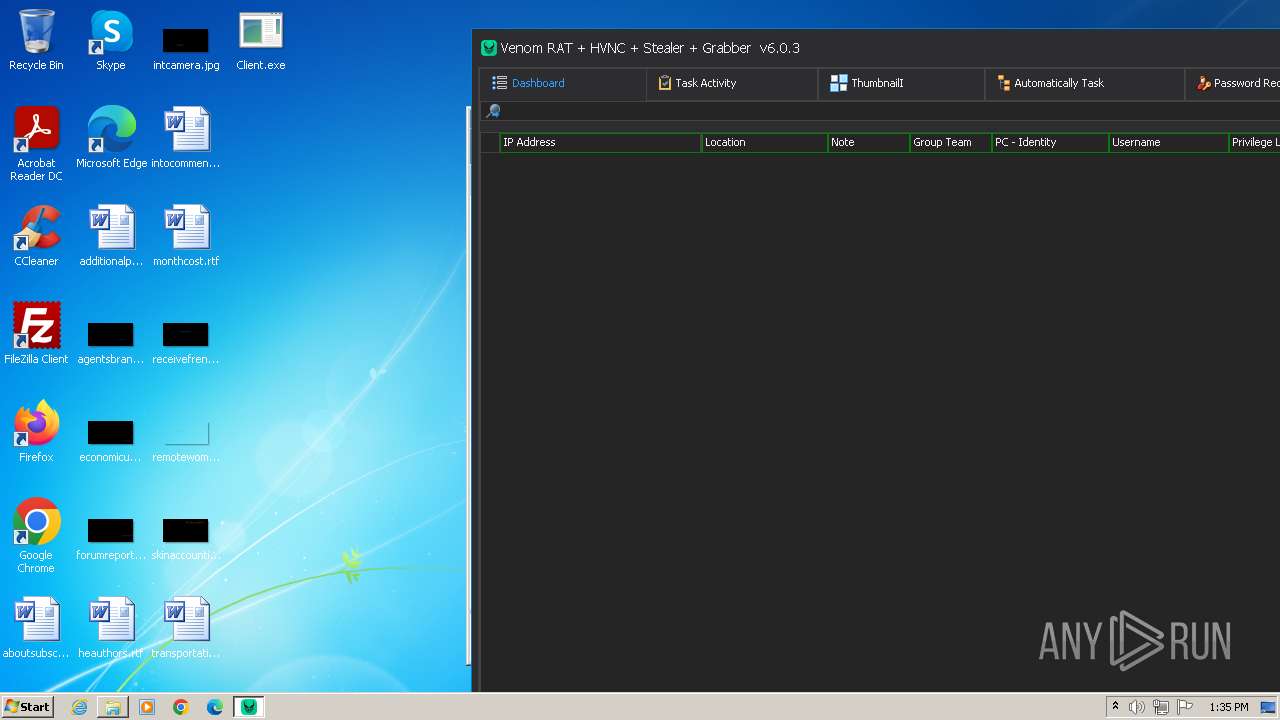
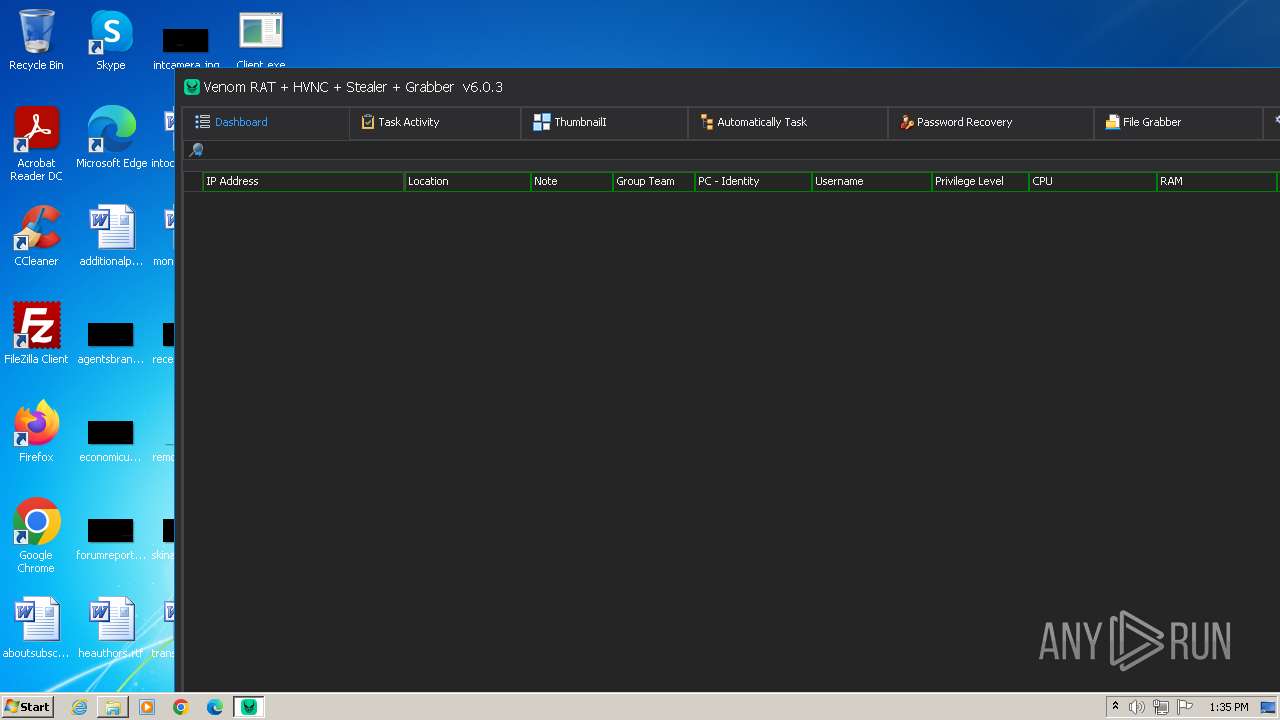
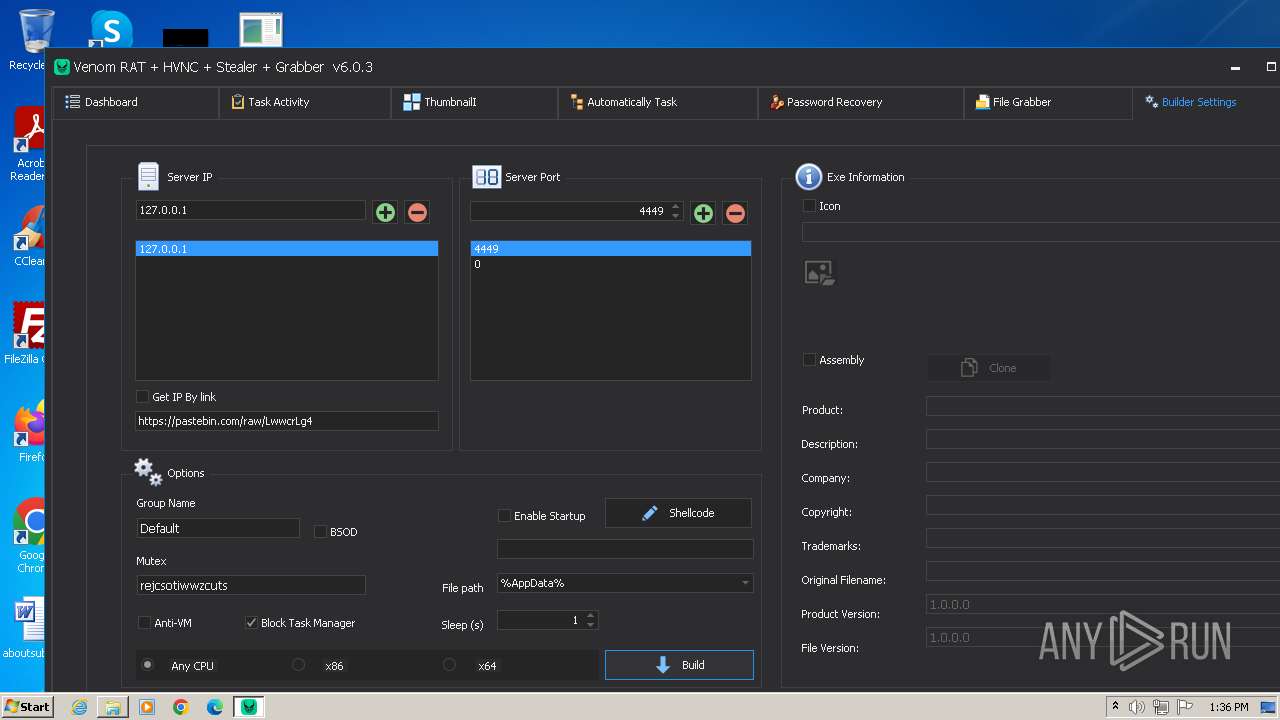
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
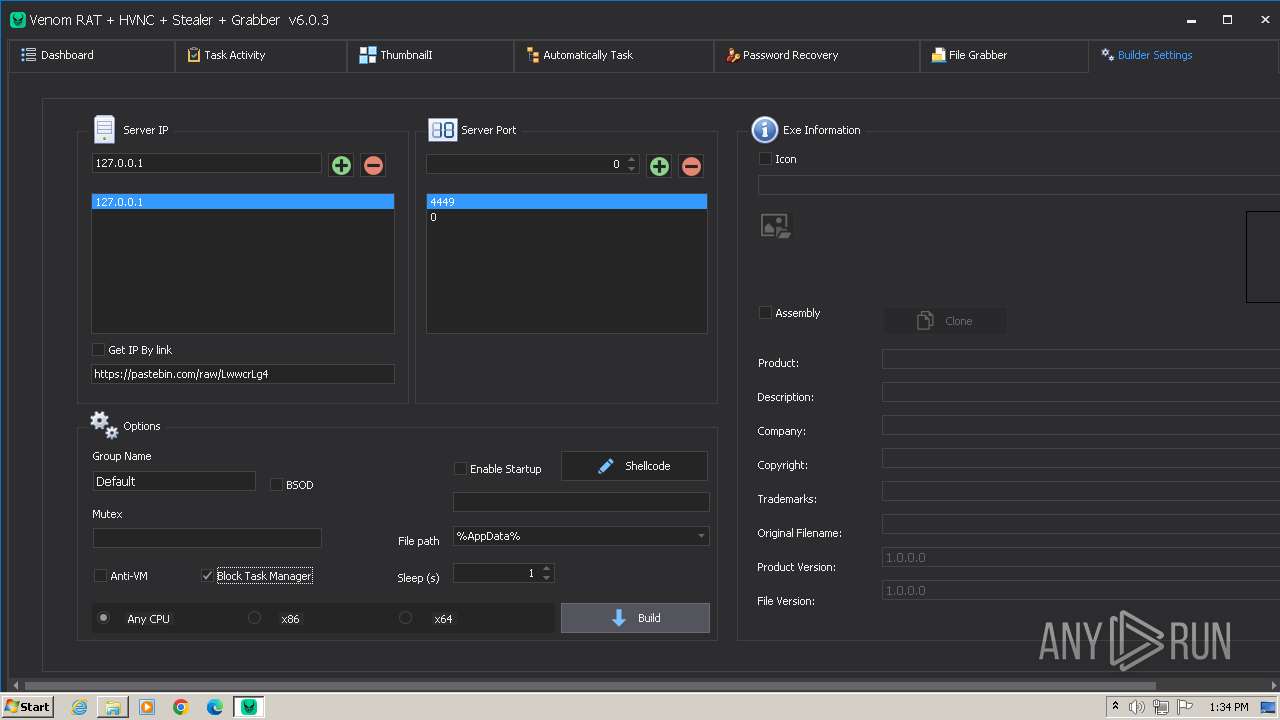
Options
AutoRunfalse
Mutexrejcsotiwwzcuts
InstallFolder%AppData%
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureIJtJpXtyzOuXS5zg87XzlSoM3E/5LF7+cwvdapfEwXVJLixrNpWtdjJNfQ8QmBIflRrK4+z19TJJRv424SYOpd2Ew0WfJQd5pn8Lrq7w8wutfMN58BLUxiQlT+/458uxWDcKZGY2tljRhANVCl18Nip3X85xT82eZw6ut7la8+w=
Keys
AES93d7a88ec6b28dd75727779ce80dce0796932af0852477986b5f1bfa2225e184
SaltVenomRATByVenom
Total processes
68
Monitored processes
21
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1328 --field-trial-handle=1260,i,9065690813893235808,433348091830358165,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1424 --field-trial-handle=1260,i,9065690813893235808,433348091830358165,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 992 | "C:\Users\admin\Desktop\121.exe" | C:\Users\admin\Desktop\121.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 6.0.1 | |||||||||||||||
| 1016 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" "https://pixeldrain.com/u/Sk8iNegL" | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1080 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2204 --field-trial-handle=1260,i,9065690813893235808,433348091830358165,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=3896 --field-trial-handle=1260,i,9065690813893235808,433348091830358165,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1280 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3556 --field-trial-handle=1260,i,9065690813893235808,433348091830358165,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1332 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6ccef598,0x6ccef5a8,0x6ccef5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1388 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
56 116
Read events
55 765
Write events
318
Delete events
33
Modification events
| (PID) Process: | (1016) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1016) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: AE09612EC8892F00 | |||
| (PID) Process: | (1016) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (1016) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (1016) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 1 | |||
| (PID) Process: | (1016) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 1 | |||
| (PID) Process: | (1016) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\IEToEdge |
| Operation: | delete value | Name: | DisabledPendingAutoUpdateConsent |
Value: | |||
| (PID) Process: | (1016) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1016) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1016) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
Executable files
111
Suspicious files
92
Text files
197
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1016 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10882d.TMP | — | |
MD5:— | SHA256:— | |||
| 1016 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1016 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10884c.TMP | — | |
MD5:— | SHA256:— | |||
| 1016 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1016 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF108937.TMP | — | |
MD5:— | SHA256:— | |||
| 1016 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1016 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:C782147434522F2D11132EDC5ABD4ED8 | SHA256:5D7501D5B5E6537D56B518A1EF57410DFFCF6AD8EE67DEB77DF91C060FEE324B | |||
| 1016 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old~RF10882d.TMP | text | |
MD5:CE86C8F851C5C62FD3B245514A656CC3 | SHA256:E59B71835032C5D6C65BA4BB15A1676C7287241388CBE117F3C16F601B84E3D0 | |||
| 1332 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 1016 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:34E5EAD530AB9B83DC9A97EF692C43DA | SHA256:08C1ED902B6CBCED9EABBA790AEAD31EB32972D703B6971165662E6F7C0369BE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
15
DNS requests
12
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
484 | lsass.exe | GET | 200 | 217.20.57.20:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fb3aafa6014dc079 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1016 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
856 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
856 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
856 | msedge.exe | 203.23.179.10:443 | pixeldrain.com | GSL Networks Pty LTD | DE | whitelisted |
856 | msedge.exe | 2.23.227.205:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
1016 | msedge.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
pixeldrain.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
— | — | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
856 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
856 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (pixeldrain .com) |