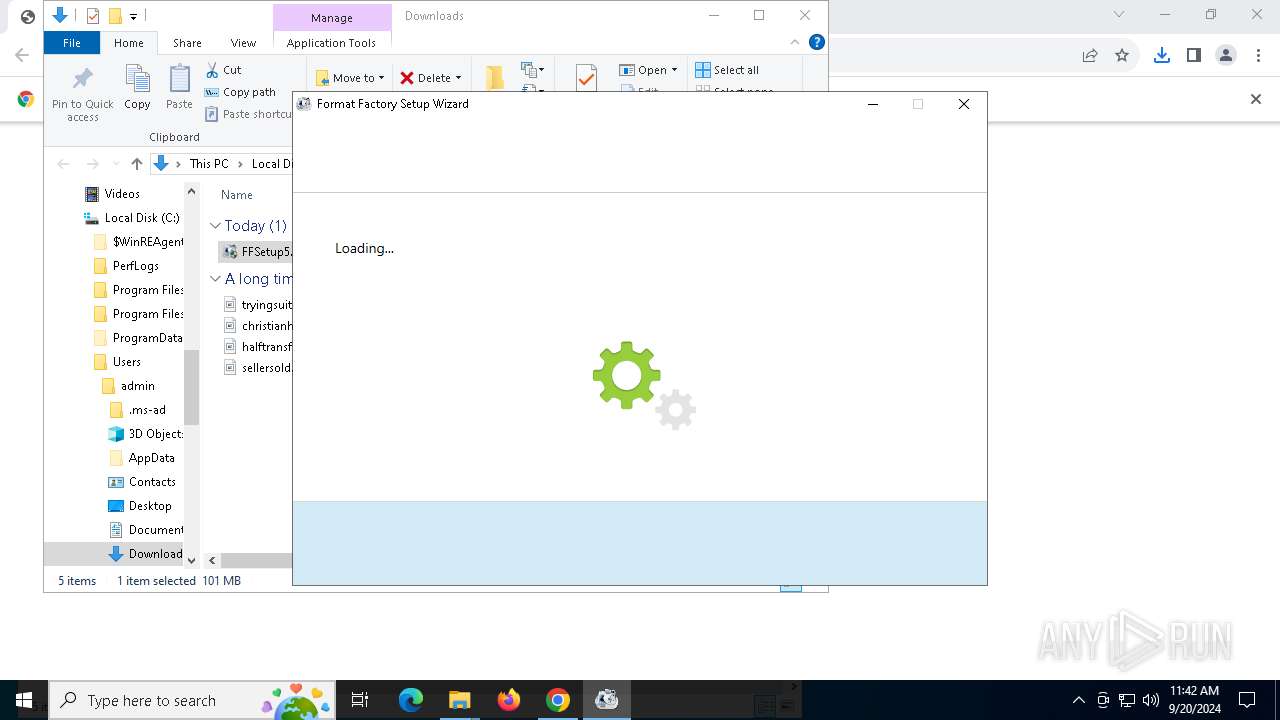
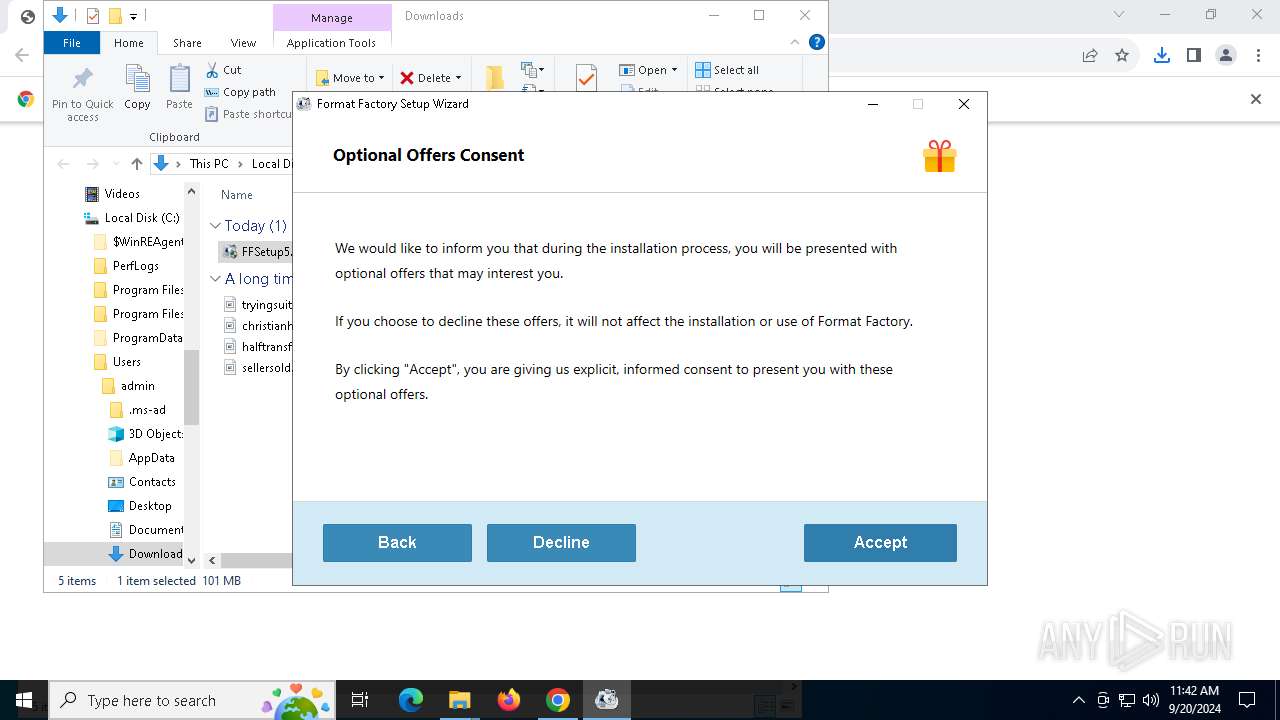
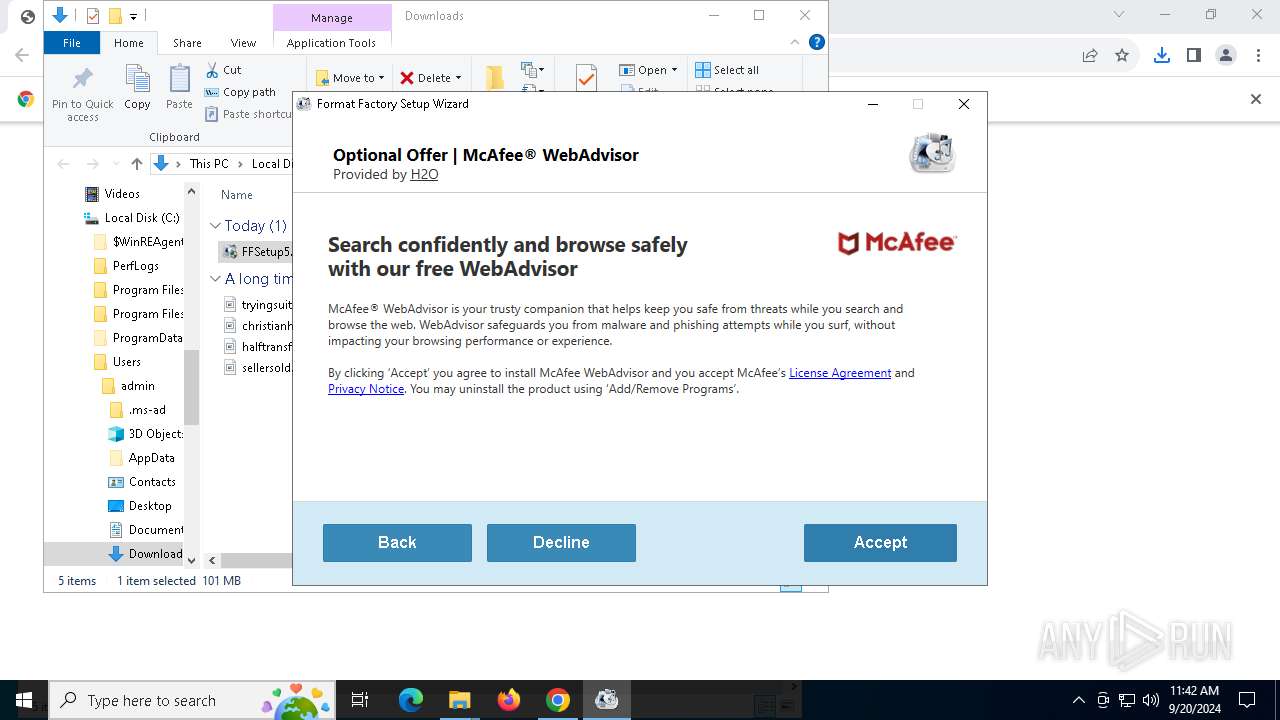
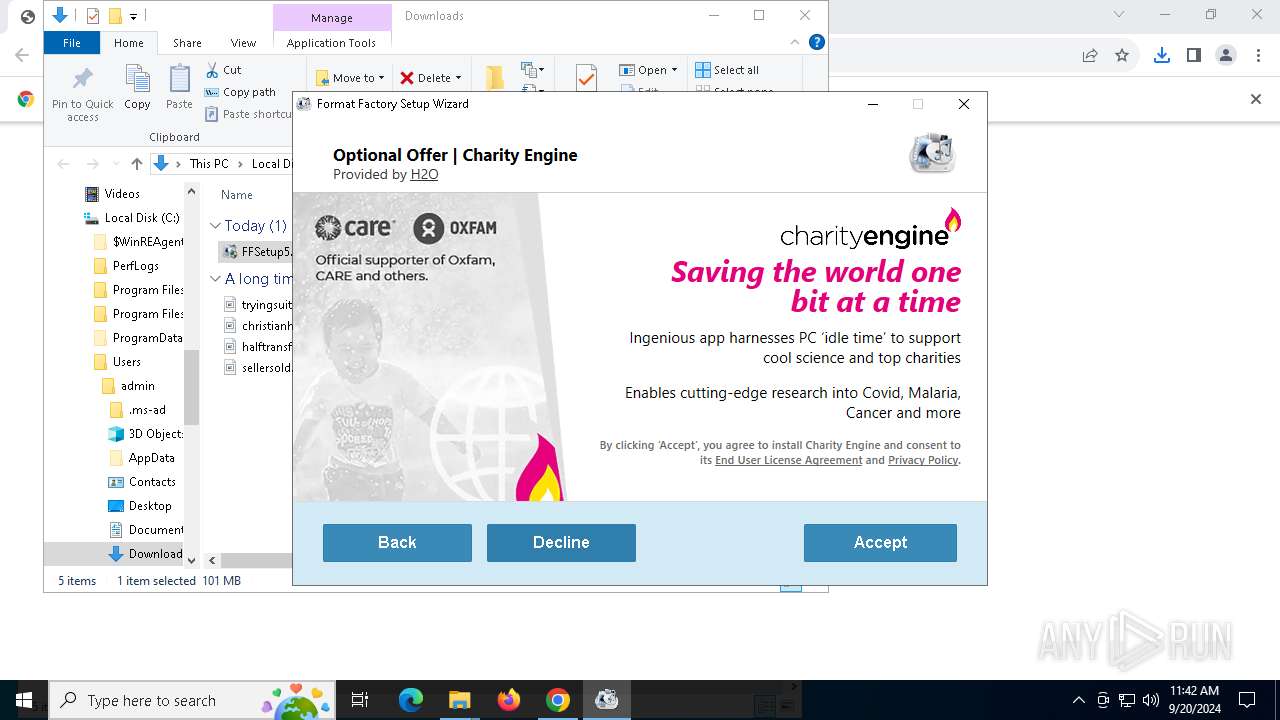
| URL: | https://sdl.adaware.com/?bundleid=FF001&savename=FFSetup5.17.0.0.exe |
| Full analysis: | https://app.any.run/tasks/73b90cad-8bc0-44d3-af83-5a5fb6f02de5 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | September 20, 2024, 11:40:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1EDF798E1EEA9B9FBD81C6413920C0CA |
| SHA1: | 8059F521E5338585DA183AAEC1893EBE56FFB9B4 |
| SHA256: | CD45F38C27F5E96F7DAFF59F332F647F1B8F1717239CFEC4DAAC4574DC924A78 |
| SSDEEP: | 3:N8M7ALdBDvUHEM9BbPX4A:2M7uXj4EMbPX4A |
MALICIOUS
ADWARE has been detected (SURICATA)
- FFSetup5.17.0.0.exe (PID: 2900)
SUSPICIOUS
Process drops legitimate windows executable
- FFSetup5.17.0.0.exe (PID: 2900)
- Carrier.exe (PID: 7320)
- FFInst.exe (PID: 7376)
Executes application which crashes
- FFSetup5.17.0.0.exe (PID: 360)
Executable content was dropped or overwritten
- FFSetup5.17.0.0.exe (PID: 2900)
- Carrier.exe (PID: 7320)
- FFInst.exe (PID: 7376)
- net_updater64.exe (PID: 8104)
The process drops C-runtime libraries
- FFSetup5.17.0.0.exe (PID: 2900)
- Carrier.exe (PID: 7320)
- FFInst.exe (PID: 7376)
Malware-specific behavior (creating "System.dll" in Temp)
- Carrier.exe (PID: 7320)
Executes as Windows Service
- WmiApSrv.exe (PID: 4044)
- net_updater64.exe (PID: 8104)
Process drops python dynamic module
- Carrier.exe (PID: 7320)
Uses NETSH.EXE to add a firewall rule or allowed programs
- FFInst.exe (PID: 7376)
Uses TASKKILL.EXE to kill process
- FFInst.exe (PID: 7376)
Drops 7-zip archiver for unpacking
- Carrier.exe (PID: 7320)
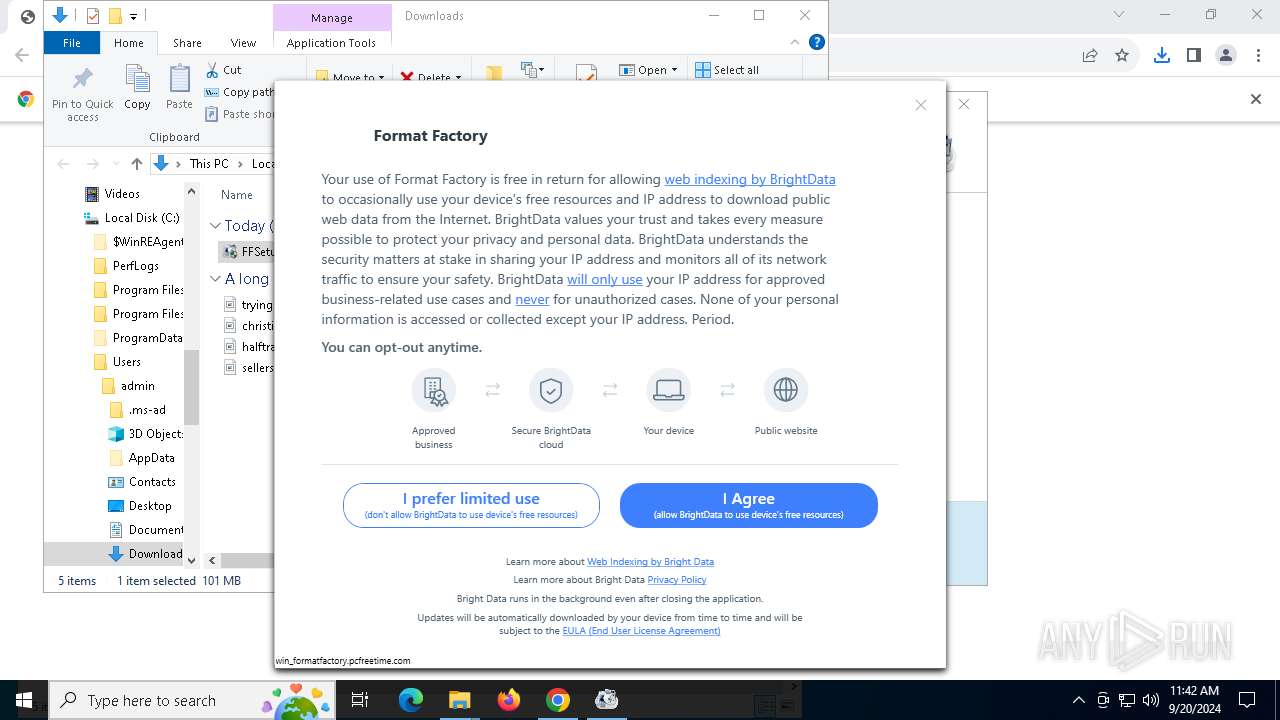
Access to an unwanted program domain was detected
- FFSetup5.17.0.0.exe (PID: 2900)
INFO
Manual execution by a user
- FFSetup5.17.0.0.exe (PID: 5388)
- FFSetup5.17.0.0.exe (PID: 360)
Executable content was dropped or overwritten
- chrome.exe (PID: 5916)
Drops a (possible) Coronavirus decoy
- Carrier.exe (PID: 7320)
Application launched itself
- chrome.exe (PID: 5916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
187
Monitored processes
52
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 360 | "C:\Users\admin\Downloads\FFSetup5.17.0.0.exe" | C:\Users\admin\Downloads\FFSetup5.17.0.0.exe | explorer.exe | ||||||||||||
User: admin Company: Free Time Co., Ltd Integrity Level: HIGH Description: Format Factory Video/Audio/Picture Converter Exit code: 3762504530 Version: 5.17.0.0 Modules
| |||||||||||||||
| 508 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | idle_report.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3024 --field-trial-handle=1872,i,16680922590077244917,17241974263372564255,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2096 | C:\ProgramData\BrightData\d71ae678248c6f808fef312e7563ca8a3655c744\test_wpf.exe | C:\ProgramData\BrightData\d71ae678248c6f808fef312e7563ca8a3655c744\test_wpf.exe | — | net_updater64.exe | |||||||||||
User: SYSTEM Company: BrightData Ltd. Integrity Level: SYSTEM Description: test_wpf Exit code: 0 Version: 1.429.308 | |||||||||||||||
| 2396 | C:\ProgramData\BrightData\d71ae678248c6f808fef312e7563ca8a3655c744\brightdata.exe --appid win_formatfactory.pcfreetime.com | C:\ProgramData\BrightData\d71ae678248c6f808fef312e7563ca8a3655c744\brightdata.exe | — | net_updater64.exe | |||||||||||
User: admin Company: BrightData Ltd. Integrity Level: MEDIUM Description: BrightData service allows free use of certain features in an app you installed Version: 1.429.308 | |||||||||||||||
| 2424 | "C:\Users\admin\Downloads\FFSetup5.17.0.0.exe" | C:\Users\admin\Downloads\FFSetup5.17.0.0.exe | — | chrome.exe | |||||||||||
User: admin Company: Free Time Co., Ltd Integrity Level: MEDIUM Description: Format Factory Video/Audio/Picture Converter Exit code: 3221226540 Version: 5.17.0.0 Modules
| |||||||||||||||
| 2900 | "C:\Users\admin\Downloads\FFSetup5.17.0.0.exe" | C:\Users\admin\Downloads\FFSetup5.17.0.0.exe | chrome.exe | ||||||||||||
User: admin Company: Free Time Co., Ltd Integrity Level: HIGH Description: Format Factory Video/Audio/Picture Converter Version: 5.17.0.0 Modules
| |||||||||||||||
| 3552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5304 --field-trial-handle=1872,i,16680922590077244917,17241974263372564255,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 | |||||||||||||||
| 3900 | netsh advfirewall firewall add rule name="Format Factory" dir=in action=allow program="C:\Program Files (x86)\FormatFactory\FormatFactory.exe" enable=yes | C:\Windows\System32\netsh.exe | — | FFInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 690
Read events
23 479
Write events
198
Delete events
13
Modification events
| (PID) Process: | (5916) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5916) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5916) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5916) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5916) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (8148) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000F90CF711520BDB01 | |||
| (PID) Process: | (2900) FFSetup5.17.0.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 897424053A4A887AC098380291034D885C8714B9 |
Value: | |||
| (PID) Process: | (2900) FFSetup5.17.0.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\897424053A4A887AC098380291034D885C8714B9 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000003A07E20B54916395FD01E57B71AA46BE0F0000000100000040000000F9E4BD19674BF9924D2D527BE02A77CA045B818F0FB627C6AA3344F3BB09CBD346D02C7530389E58A22355CA95280F134B83E7FA08D59B961B0F9A05347855A0030000000100000014000000897424053A4A887AC098380291034D885C8714B91D000000010000001000000023787A60050FFA2D3210923F0F56237114000000010000001400000082BAD63D97CE9FCF71E89237AFFDB3B5693557CF090000000100000016000000301406082B0601050507030306082B06010505070308620000000100000020000000B80847FDA453BF6ED876CA7BC046A2481909E15B6ED376E665E7AD09F3864E710B000000010000007400000045006E0074007200750073007400200043006F006400650020005300690067006E0069006E006700200052006F006F0074002000430065007200740069006600690063006100740069006F006E00200041007500740068006F00720069007400790020002D002000430053004200520031000000190000000100000010000000188A164A11CAA2378C0BCDEC471F26732000000001000000A6050000308205A23082038AA00302010202147FF1A8F9F43AE8876E2DC6FF5E433DB2EE30A643300D06092A864886F70D01010D05003069310B300906035504061302555331163014060355040A0C0D456E74727573742C20496E632E3142304006035504030C39456E747275737420436F6465205369676E696E6720526F6F742043657274696669636174696F6E20417574686F72697479202D204353425231301E170D3231303530373133323633365A170D3430313233303133323633365A3069310B300906035504061302555331163014060355040A0C0D456E74727573742C20496E632E3142304006035504030C39456E747275737420436F6465205369676E696E6720526F6F742043657274696669636174696F6E20417574686F72697479202D20435342523130820222300D06092A864886F70D01010105000382020F003082020A0282020100A7818FF71445B66243F2D8AED3255E484F51BFC57D9F501C35D1D67E612A94196D2746A4A61A5DF754516A8022C6A866754D5483C95E681BABF65B64B0ADAD20BD54EF466B6D02E745AE75F68E8AB9322E8BB8771C524D79885FA53A18C9502C97272DBFDA007D637FEF32EC468763DB9A9FC35A21367BF99BD5CAA06E722CFCE1F19E704D0856156F90ABFB48BAB9D7C1827885652E7FB5C9C0E214B737114106E28AE0A8F6E57EB6780501C360ED4F07412E0A1349E3909B7FDDBDFAACBF6451D15C9BB4F55CE75CFF3B9BA5A01AD77D09B2C2B7FF6E1CBCC87DE6E92BFC72B314E94A5512849C4425751DF62AF04FA5203D6825EB61977C0FE5B63DF3AEC3C111BC1B8ECCE047305E42008671E358AC06CA651F7B94A64B57670C7E5EAD78675B55E35EEBC7D8EC4C6E86CBF3DCF89F87AA7258120F7DA6F8F842393B3C2CE4324D498CE0E100C238A09CFA843E41DC6E56AEC61A5BF467680501CD1BBFAE87BC9D53F62EE8B66BE499DEC54F8758A8D2651EC81FD5726EEE591C573B09729DD7CAB790C6CD7B45929142034C7D3FCAF2AAB8C20E86F3109F462EA46686685A68187029381180606B8A43A3736CE3B36B37FFE69D67019286DF2F48D1FB5060D55CFE21D3014263FEEF70B417C08FA8EED3C14B5F12EAFDFD2E0E874460E3A9F4C218A3E3FDCE0C84220DF3A778DA93F3DB38CFB92F33C6FF073C5EBE45D30203010001A3423040301D0603551D0E0416041482BAD63D97CE9FCF71E89237AFFDB3B5693557CF300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020186300D06092A864886F70D01010D0500038202010012EF38A188E1A1A3D665DC479CF3BCDCCFAC4B8C3C1ABE2BF4F7D0671768864D70A8F2CDD03102577DA90C8A3B57399EF06EF724220567D1C196C1BED1F0F856670BDEBAD7889B8DD76B0876F55891D9B5C340531AA4F185CD3F004E3F4E933B78B9D20752640C86696DE854655617E80053848AF3DBFBB3CE0B55628FCD4C4906387F52C3F31CD73DF733CA32ADC1A9AF6FEB11CBEEAC51BFB0269A7A4E23B44AF669B44269D6A08DB68C474A3B2037B74107EF2F20D8661C6997A86C307C77435E6BBE2698830F3AD6C7702A16462D25548663655742F72341E9506A0743CE4EB5E91F68D8D8D6094AA8E8B2FC906792E49026F347FAD620FB8980E2447339F78A86330BF8AAA9E74DECDC6FD5CF314DAB8E1F9040D67C5C820FAE175271E9ACE74D38ED2AD8767987AD17A34CABB74257BF06ACE5D04D30E9554FE345CAF3E06A21348DC79F1CA3634892D29607BEA5473EC22A9938A78EDA217C516DDCCB3D07E9A9BD49D45D355F5B8C0451EA9A5890BA1BAF6878B1160F94293B8F9B2A8FC920F071424C5C4DAB318CABE97F266869A0A5160D81C4D1050CC38766E50763AA1B4EFFB207414FA5224650AC660087526C3CB23B9C97A146B45BDECFC26A5955078CA3A4D177356746042FD938B946AFBA8E1B7226022F7654EF83C22F2C7770CC771092AA03ADCACCE04FE98346E5B33C196F7A7987B6389ABD42CEA462 | |||
| (PID) Process: | (2900) FFSetup5.17.0.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\897424053A4A887AC098380291034D885C8714B9 |
| Operation: | write | Name: | Blob |
Value: 5C000000010000000400000000100000190000000100000010000000188A164A11CAA2378C0BCDEC471F26730B000000010000007400000045006E0074007200750073007400200043006F006400650020005300690067006E0069006E006700200052006F006F0074002000430065007200740069006600690063006100740069006F006E00200041007500740068006F00720069007400790020002D002000430053004200520031000000620000000100000020000000B80847FDA453BF6ED876CA7BC046A2481909E15B6ED376E665E7AD09F3864E71090000000100000016000000301406082B0601050507030306082B0601050507030814000000010000001400000082BAD63D97CE9FCF71E89237AFFDB3B5693557CF1D000000010000001000000023787A60050FFA2D3210923F0F562371030000000100000014000000897424053A4A887AC098380291034D885C8714B90F0000000100000040000000F9E4BD19674BF9924D2D527BE02A77CA045B818F0FB627C6AA3344F3BB09CBD346D02C7530389E58A22355CA95280F134B83E7FA08D59B961B0F9A05347855A00400000001000000100000003A07E20B54916395FD01E57B71AA46BE2000000001000000A6050000308205A23082038AA00302010202147FF1A8F9F43AE8876E2DC6FF5E433DB2EE30A643300D06092A864886F70D01010D05003069310B300906035504061302555331163014060355040A0C0D456E74727573742C20496E632E3142304006035504030C39456E747275737420436F6465205369676E696E6720526F6F742043657274696669636174696F6E20417574686F72697479202D204353425231301E170D3231303530373133323633365A170D3430313233303133323633365A3069310B300906035504061302555331163014060355040A0C0D456E74727573742C20496E632E3142304006035504030C39456E747275737420436F6465205369676E696E6720526F6F742043657274696669636174696F6E20417574686F72697479202D20435342523130820222300D06092A864886F70D01010105000382020F003082020A0282020100A7818FF71445B66243F2D8AED3255E484F51BFC57D9F501C35D1D67E612A94196D2746A4A61A5DF754516A8022C6A866754D5483C95E681BABF65B64B0ADAD20BD54EF466B6D02E745AE75F68E8AB9322E8BB8771C524D79885FA53A18C9502C97272DBFDA007D637FEF32EC468763DB9A9FC35A21367BF99BD5CAA06E722CFCE1F19E704D0856156F90ABFB48BAB9D7C1827885652E7FB5C9C0E214B737114106E28AE0A8F6E57EB6780501C360ED4F07412E0A1349E3909B7FDDBDFAACBF6451D15C9BB4F55CE75CFF3B9BA5A01AD77D09B2C2B7FF6E1CBCC87DE6E92BFC72B314E94A5512849C4425751DF62AF04FA5203D6825EB61977C0FE5B63DF3AEC3C111BC1B8ECCE047305E42008671E358AC06CA651F7B94A64B57670C7E5EAD78675B55E35EEBC7D8EC4C6E86CBF3DCF89F87AA7258120F7DA6F8F842393B3C2CE4324D498CE0E100C238A09CFA843E41DC6E56AEC61A5BF467680501CD1BBFAE87BC9D53F62EE8B66BE499DEC54F8758A8D2651EC81FD5726EEE591C573B09729DD7CAB790C6CD7B45929142034C7D3FCAF2AAB8C20E86F3109F462EA46686685A68187029381180606B8A43A3736CE3B36B37FFE69D67019286DF2F48D1FB5060D55CFE21D3014263FEEF70B417C08FA8EED3C14B5F12EAFDFD2E0E874460E3A9F4C218A3E3FDCE0C84220DF3A778DA93F3DB38CFB92F33C6FF073C5EBE45D30203010001A3423040301D0603551D0E0416041482BAD63D97CE9FCF71E89237AFFDB3B5693557CF300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020186300D06092A864886F70D01010D0500038202010012EF38A188E1A1A3D665DC479CF3BCDCCFAC4B8C3C1ABE2BF4F7D0671768864D70A8F2CDD03102577DA90C8A3B57399EF06EF724220567D1C196C1BED1F0F856670BDEBAD7889B8DD76B0876F55891D9B5C340531AA4F185CD3F004E3F4E933B78B9D20752640C86696DE854655617E80053848AF3DBFBB3CE0B55628FCD4C4906387F52C3F31CD73DF733CA32ADC1A9AF6FEB11CBEEAC51BFB0269A7A4E23B44AF669B44269D6A08DB68C474A3B2037B74107EF2F20D8661C6997A86C307C77435E6BBE2698830F3AD6C7702A16462D25548663655742F72341E9506A0743CE4EB5E91F68D8D8D6094AA8E8B2FC906792E49026F347FAD620FB8980E2447339F78A86330BF8AAA9E74DECDC6FD5CF314DAB8E1F9040D67C5C820FAE175271E9ACE74D38ED2AD8767987AD17A34CABB74257BF06ACE5D04D30E9554FE345CAF3E06A21348DC79F1CA3634892D29607BEA5473EC22A9938A78EDA217C516DDCCB3D07E9A9BD49D45D355F5B8C0451EA9A5890BA1BAF6878B1160F94293B8F9B2A8FC920F071424C5C4DAB318CABE97F266869A0A5160D81C4D1050CC38766E50763AA1B4EFFB207414FA5224650AC660087526C3CB23B9C97A146B45BDECFC26A5955078CA3A4D177356746042FD938B946AFBA8E1B7226022F7654EF83C22F2C7770CC771092AA03ADCACCE04FE98346E5B33C196F7A7987B6389ABD42CEA462 | |||
| (PID) Process: | (2900) FFSetup5.17.0.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 8CF427FD790C3AD166068DE81E57EFBB932272D4 |
Value: | |||
Executable files
156
Suspicious files
1 849
Text files
1 759
Unknown types
188
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5916 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5916 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5916 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5916 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1fb714.TMP | — | |
MD5:— | SHA256:— | |||
| 5916 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5916 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5916 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1fb714.TMP | — | |
MD5:— | SHA256:— | |||
| 5916 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5916 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:723783C35EAEEE1492EDB30847AE6750 | SHA256:C29323F784CF873BF34992E7A2B4630B19641BF42980109E31D5AF2D487DF6F8 | |||
| 5916 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
101
DNS requests
54
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5148 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5148 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
4168 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7972 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7972 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5148 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
5148 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
2900 | FFSetup5.17.0.0.exe | GET | 200 | 2.23.198.32:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRr2bwARTxMtEy9aspRAZg5QFhagQQUgrrWPZfOn89x6JI3r%2F2ztWk1V88CEDWvt3udNB9q%2FI%2BERqsxNSs%3D | unknown | — | — | whitelisted |
2900 | FFSetup5.17.0.0.exe | GET | 200 | 2.23.198.32:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTLXNCzDvBhHecWjg70iJhBW0InywQUanImetAe733nO2lR1GyNn5ASZqsCEE5A5DdU7eaMAAAAAFHTlH8%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5212 | svchost.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6784 | RUXIMICS.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
— | — | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
4492 | chrome.exe | 104.16.212.94:443 | sdl.adaware.com | CLOUDFLARENET | — | whitelisted |
5916 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
sdl.adaware.com |
| whitelisted |
accounts.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.google.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
FFSetup5.17.0.0.exe | Error: File not found - sciterwrapper:console.tis
|
FFSetup5.17.0.0.exe | at sciter:init-script.tis
|
FFSetup5.17.0.0.exe | |
FFSetup5.17.0.0.exe | |
FFSetup5.17.0.0.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|
FFSetup5.17.0.0.exe | Error: File not found - sciterwrapper:console.tis
|
FFSetup5.17.0.0.exe | at sciter:init-script.tis
|
FFSetup5.17.0.0.exe | |
FFSetup5.17.0.0.exe | |
FFSetup5.17.0.0.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|