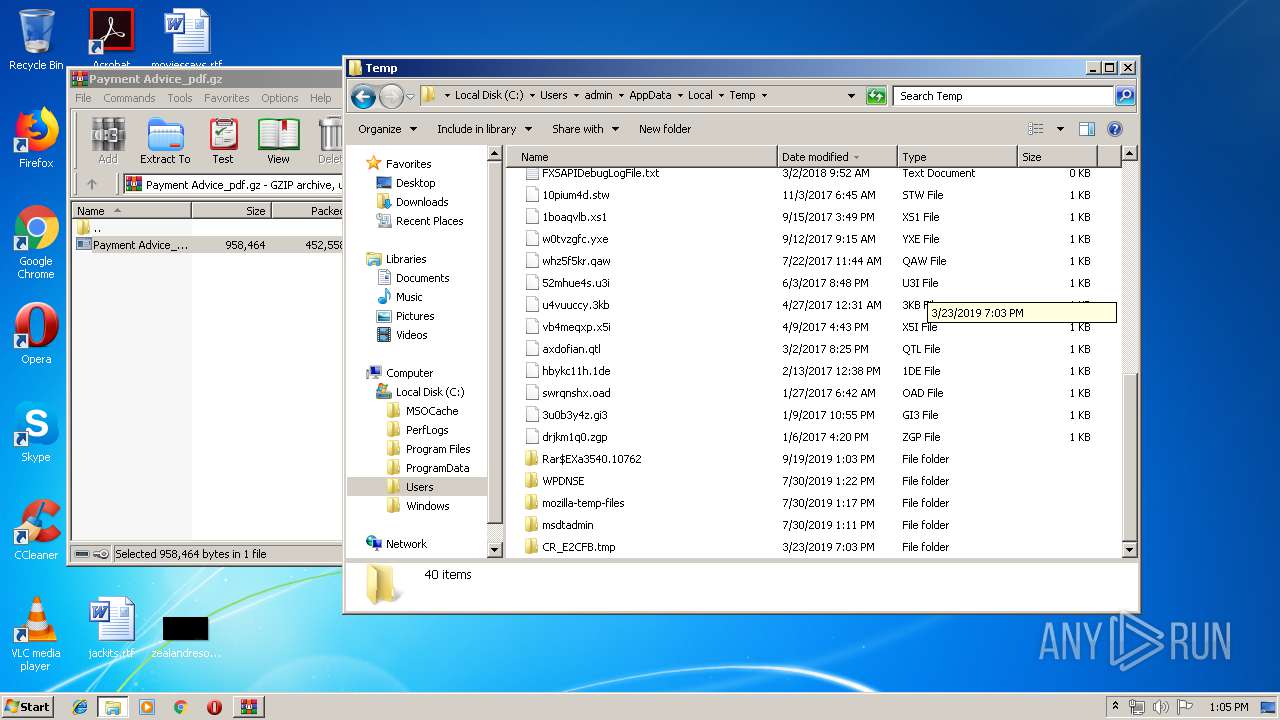
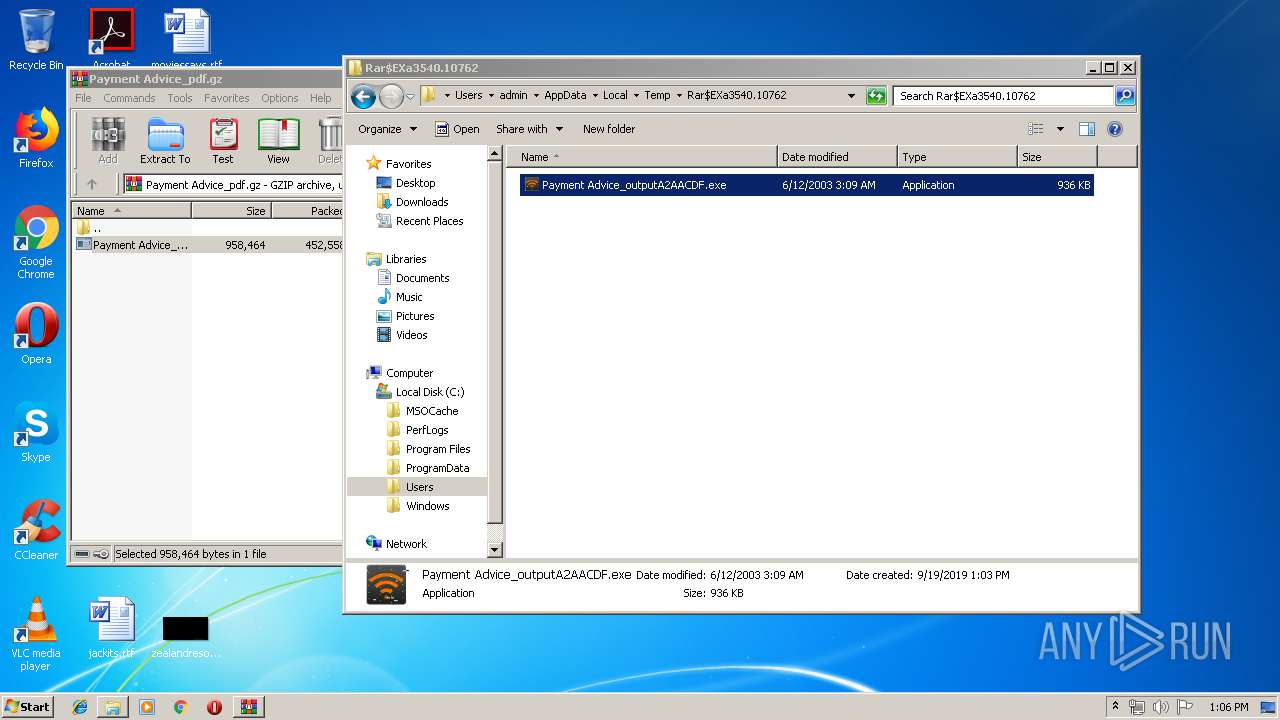
| File name: | Payment Advice_pdf.gz |
| Full analysis: | https://app.any.run/tasks/db43d385-679d-43a9-85ff-c2e7a6e53fbd |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | September 19, 2019, 12:02:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/gzip |
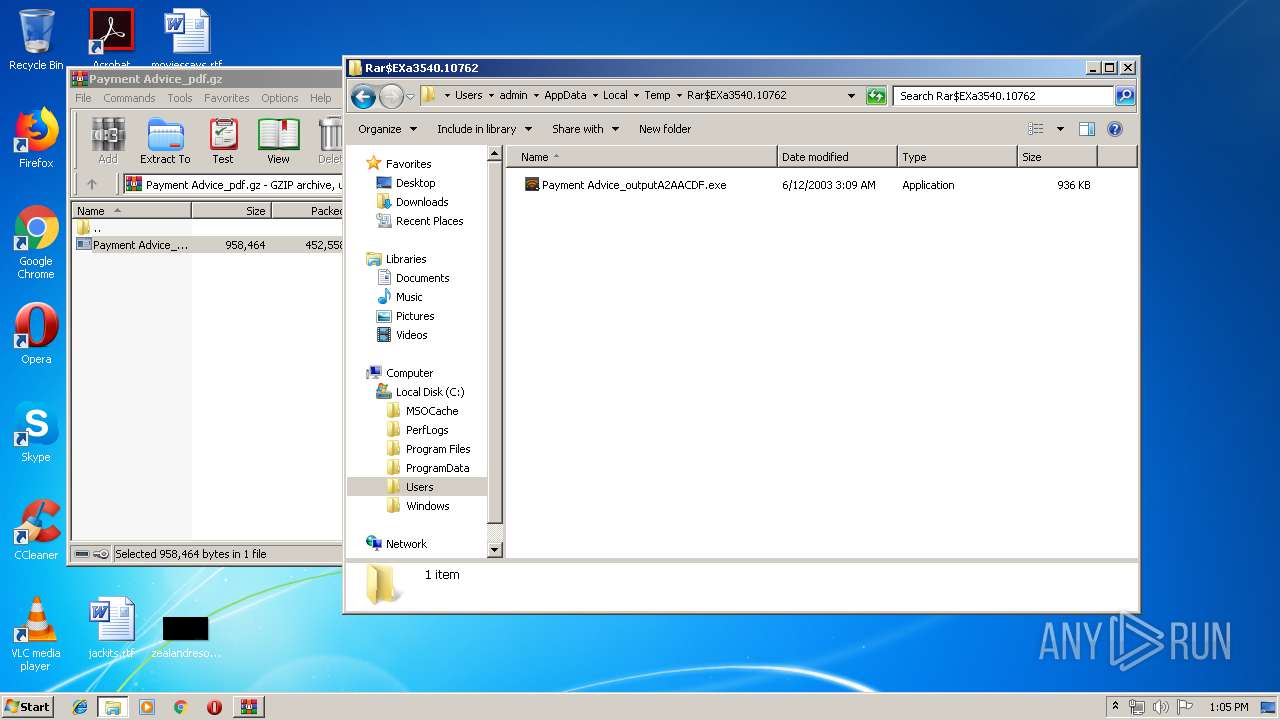
| File info: | gzip compressed data, was "Payment Advice_outputA2AACDF.exe", last modified: Thu Jun 12 02:09:51 2003, max speed, from FAT filesystem (MS-DOS, OS/2, NT) |
| MD5: | FBEE626C9EA17F02522B59233DCD877A |
| SHA1: | 3BF271ACAE26395DFDA308BDB85176F404988BDA |
| SHA256: | CCBBAF7FF3F65905FE017F50642C36F15A39B9193DC75DE261E60AB3AC050646 |
| SSDEEP: | 12288:t7h2E0e+AxZaGgYDP8tU/B0GrXAS3n2vL:tdEs7DPJJ0uXpKL |
MALICIOUS
Application was dropped or rewritten from another process
- Payment Advice_outputA2AACDF.exe (PID: 3500)
- Payment Advice_outputA2AACDF.exe (PID: 2056)
- Payment Advice_outputA2AACDF.exe (PID: 2464)
- Payment Advice_outputA2AACDF.exe (PID: 2432)
AGENTTESLA was detected
- Payment Advice_outputA2AACDF.exe (PID: 2056)
- Payment Advice_outputA2AACDF.exe (PID: 2464)
Actions looks like stealing of personal data
- Payment Advice_outputA2AACDF.exe (PID: 2056)
- Payment Advice_outputA2AACDF.exe (PID: 2464)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3540)
Application launched itself
- Payment Advice_outputA2AACDF.exe (PID: 3500)
- Payment Advice_outputA2AACDF.exe (PID: 2432)
Connects to SMTP port
- Payment Advice_outputA2AACDF.exe (PID: 2056)
- Payment Advice_outputA2AACDF.exe (PID: 2464)
Checks for external IP
- Payment Advice_outputA2AACDF.exe (PID: 2056)
- Payment Advice_outputA2AACDF.exe (PID: 2464)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3540)
Manual execution by user
- explorer.exe (PID: 3480)
- chrome.exe (PID: 872)
- Payment Advice_outputA2AACDF.exe (PID: 2432)
Reads the hosts file
- chrome.exe (PID: 3712)
- chrome.exe (PID: 872)
Application launched itself
- chrome.exe (PID: 872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | FileName |
| ModifyDate: | 2003:06:12 04:09:51+02:00 |
| ExtraFlags: | Fastest Algorithm |
| OperatingSystem: | FAT filesystem (MS-DOS, OS/2, NT/Win32) |
| ArchivedFileName: | Payment Advice_outputA2AACDF.exe |
Total processes
68
Monitored processes
29
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=980,4215310554660908990,4202463221967419516,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18183835720727195321 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2472 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 776 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=980,4215310554660908990,4202463221967419516,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1963110197160001450 --mojo-platform-channel-handle=3456 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 872 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=980,4215310554660908990,4202463221967419516,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2096562759943137183 --mojo-platform-channel-handle=3708 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=980,4215310554660908990,4202463221967419516,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=16229503249011035595 --mojo-platform-channel-handle=3544 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2056 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.10762\Payment Advice_outputA2AACDF.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.10762\Payment Advice_outputA2AACDF.exe | Payment Advice_outputA2AACDF.exe | ||||||||||||
User: admin Company: OverwingINDIANISM0 Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.09.0001 Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.10762\Payment Advice_outputA2AACDF.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.10762\Payment Advice_outputA2AACDF.exe | — | explorer.exe | |||||||||||
User: admin Company: OverwingINDIANISM0 Integrity Level: MEDIUM Exit code: 0 Version: 1.09.0001 Modules
| |||||||||||||||
| 2456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=980,4215310554660908990,4202463221967419516,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5389322373033845265 --mojo-platform-channel-handle=3228 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2464 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.10762\Payment Advice_outputA2AACDF.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.10762\Payment Advice_outputA2AACDF.exe | Payment Advice_outputA2AACDF.exe | ||||||||||||
User: admin Company: OverwingINDIANISM0 Integrity Level: MEDIUM Exit code: 0 Version: 1.09.0001 Modules
| |||||||||||||||
| 2520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=980,4215310554660908990,4202463221967419516,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7026058075795250473 --mojo-platform-channel-handle=3720 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
778
Read events
685
Write events
89
Delete events
4
Modification events
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Payment Advice_pdf.gz | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
1
Suspicious files
32
Text files
176
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF195c8d.TMP | — | |
MD5:— | SHA256:— | |||
| 872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\147339e4-d15d-4c88-83eb-f16ad2048d3b.tmp | — | |
MD5:— | SHA256:— | |||
| 872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.10762\Payment Advice_outputA2AACDF.exe | executable | |
MD5:— | SHA256:— | |||
| 872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF195c8d.TMP | text | |
MD5:— | SHA256:— | |||
| 872 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
24
DNS requests
18
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2464 | Payment Advice_outputA2AACDF.exe | GET | 200 | 3.224.145.145:80 | http://checkip.amazonaws.com/ | US | text | 15 b | malicious |
3712 | chrome.exe | GET | 302 | 172.217.22.78:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 515 b | whitelisted |
3712 | chrome.exe | GET | 200 | 172.217.133.135:80 | http://r2---sn-hpa7znsd.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.128.27.133&mm=28&mn=sn-hpa7znsd&ms=nvh&mt=1568894670&mv=m&mvi=1&pl=24&shardbypass=yes | US | crx | 862 Kb | whitelisted |
2056 | Payment Advice_outputA2AACDF.exe | GET | 200 | 3.224.145.145:80 | http://checkip.amazonaws.com/ | US | text | 15 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2056 | Payment Advice_outputA2AACDF.exe | 3.224.145.145:80 | checkip.amazonaws.com | — | US | shared |
2056 | Payment Advice_outputA2AACDF.exe | 46.21.144.100:587 | server1.monovm.com | Swiftway Sp. z o.o. | NL | malicious |
3712 | chrome.exe | 172.217.23.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
3712 | chrome.exe | 172.217.21.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3712 | chrome.exe | 216.58.207.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3712 | chrome.exe | 172.217.21.225:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
3712 | chrome.exe | 172.217.133.135:80 | r2---sn-hpa7znsd.gvt1.com | Google Inc. | US | whitelisted |
2464 | Payment Advice_outputA2AACDF.exe | 3.224.145.145:80 | checkip.amazonaws.com | — | US | shared |
3712 | chrome.exe | 172.217.18.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2464 | Payment Advice_outputA2AACDF.exe | 46.21.144.100:587 | server1.monovm.com | Swiftway Sp. z o.o. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
checkip.amazonaws.com |
| malicious |
server1.monovm.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2056 | Payment Advice_outputA2AACDF.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
2056 | Payment Advice_outputA2AACDF.exe | A Network Trojan was detected | AV TROJAN Win.Keylogger.AgentTesla variant outbound SMTP connection |
2056 | Payment Advice_outputA2AACDF.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan-Spy.Keylogger.AgentTesla Exfiltration by SMTP |
2464 | Payment Advice_outputA2AACDF.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
5 ETPRO signatures available at the full report