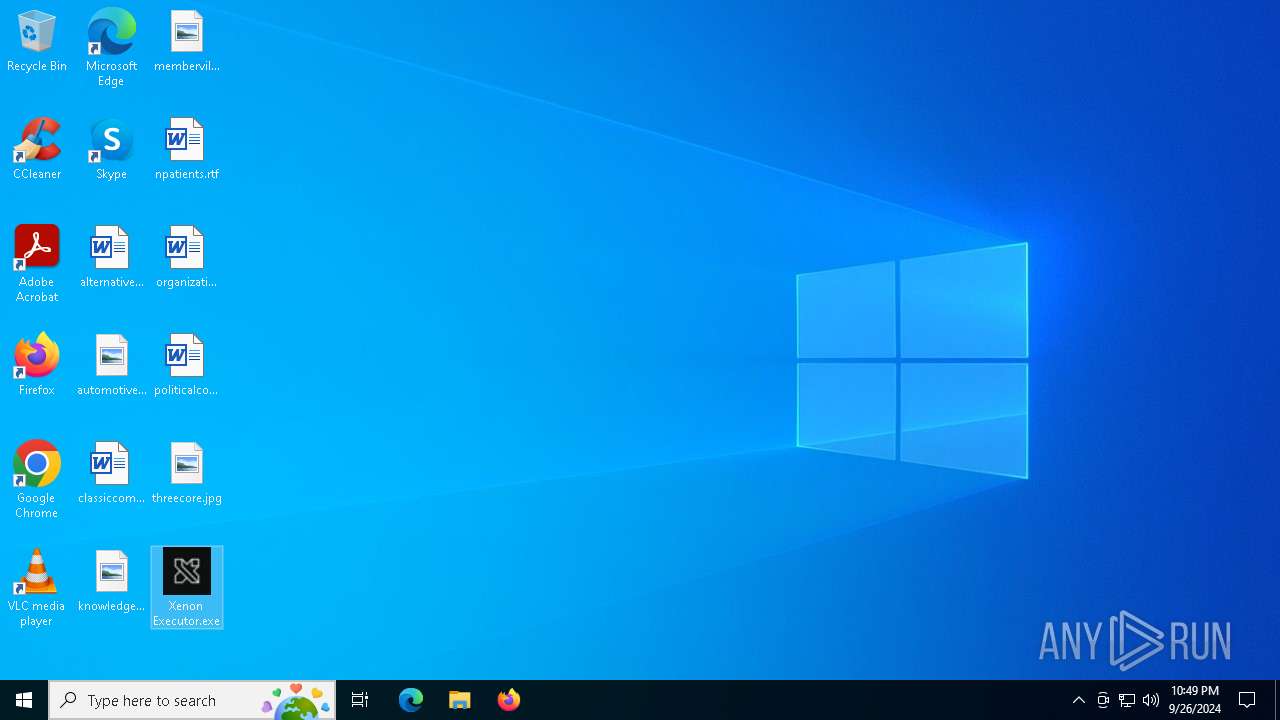
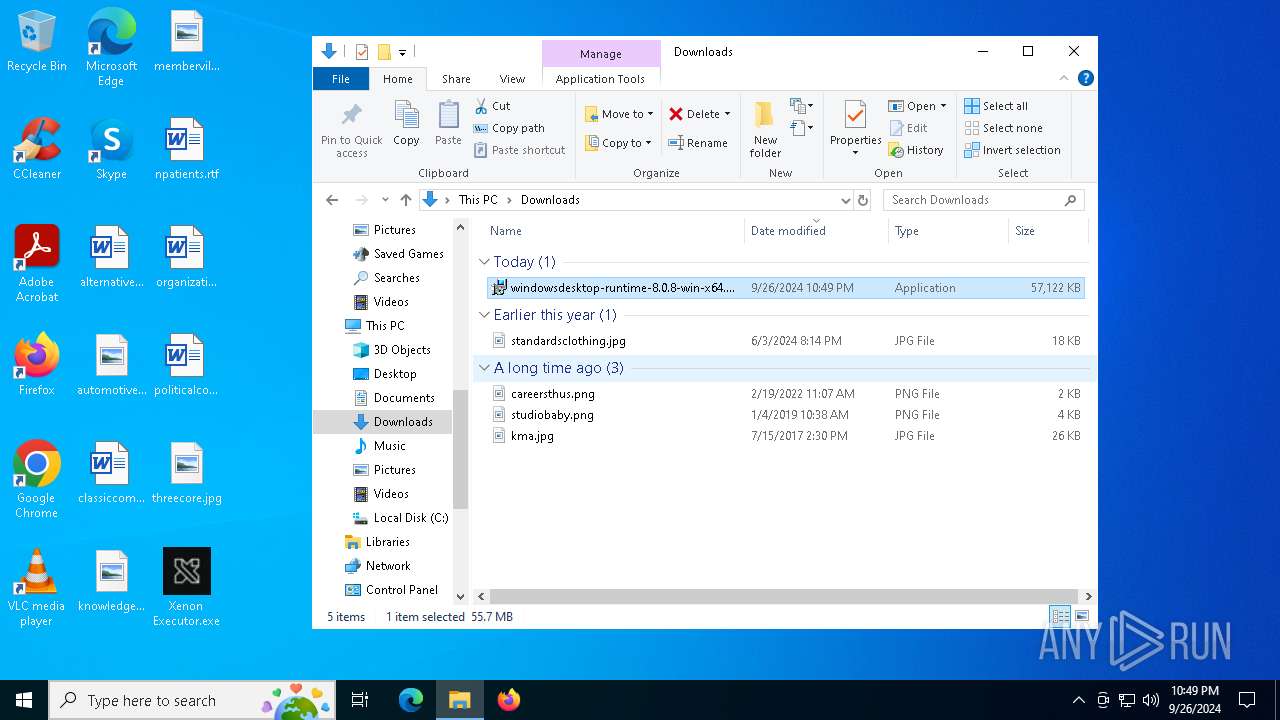
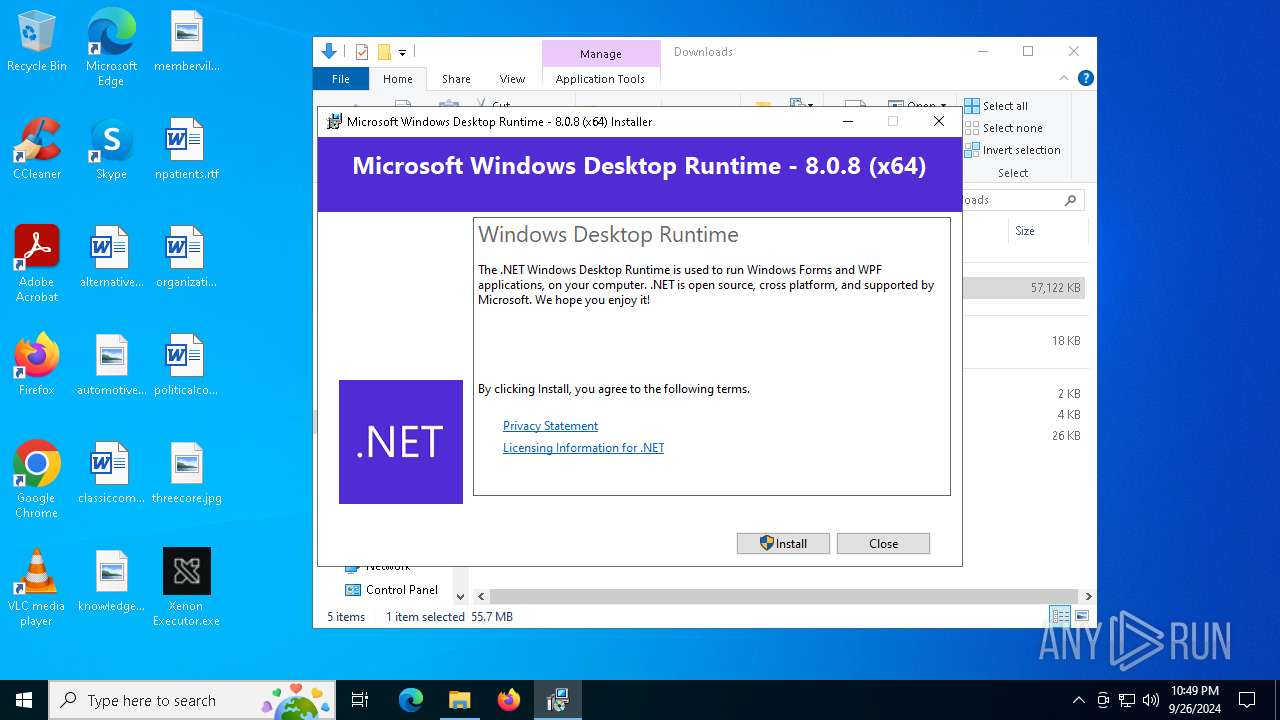
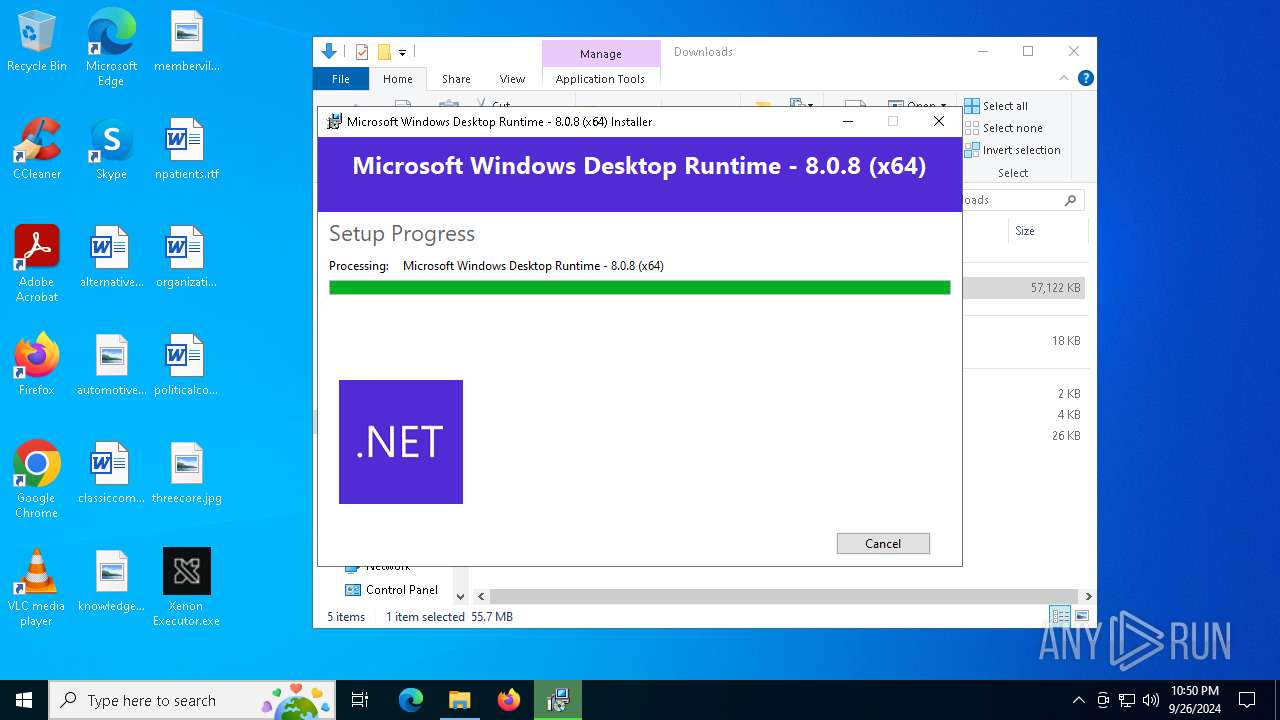
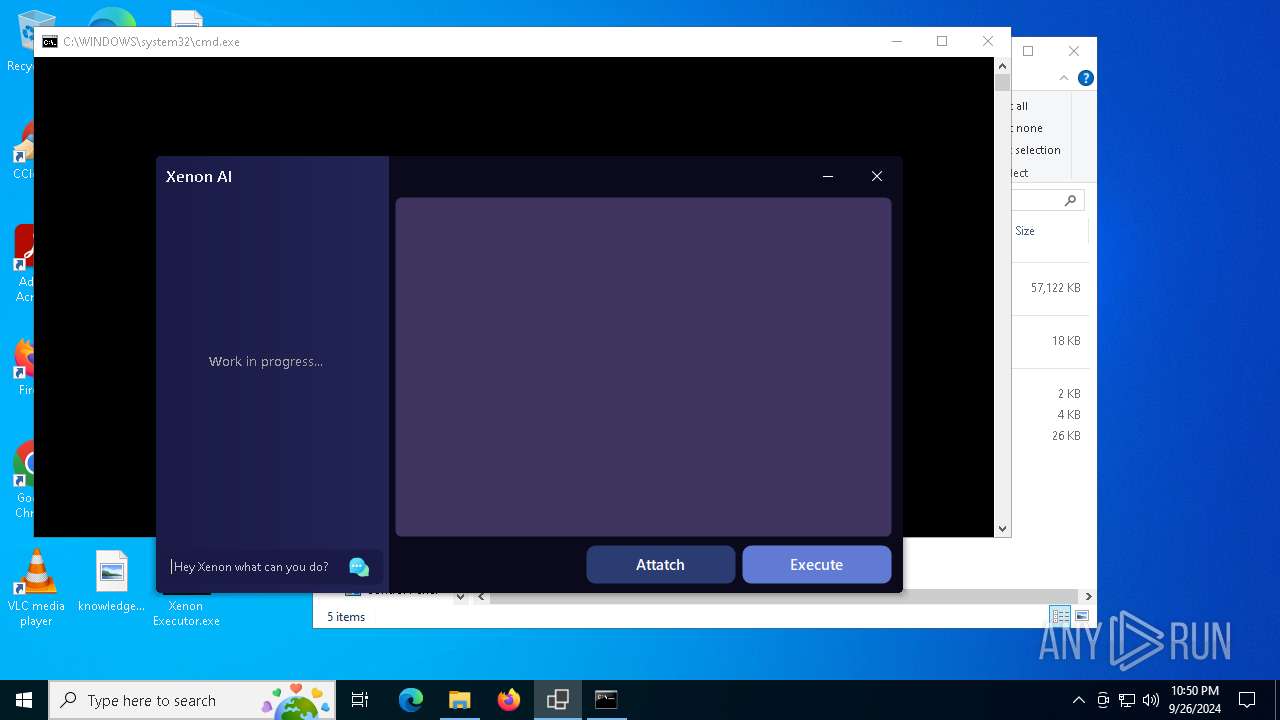
| File name: | Xenon Executor.exe |
| Full analysis: | https://app.any.run/tasks/c4e1f96a-adf4-4405-877b-6f991fd255db |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | September 26, 2024, 22:48:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | CFDD1106713A2DB9801B86EC3B6DAE52 |
| SHA1: | DF5D44D5A61292BFA8F9155A7AB28386F316A32C |
| SHA256: | CC64C748D92B82C538E1AB4011197813028BCF8CDFA240B9DF37A1BC14ABF75F |
| SSDEEP: | 98304:0BbOJjiT3YjvbHskSWhIrG+jKBp3/fG7diV76zROrBdOStLbHQ7U5Sr90vZUn8vK:dpYep |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 2568)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 3552)
SUSPICIOUS
Reads security settings of Internet Explorer
- Xenon Executor.exe (PID: 6348)
- Xenon Executor.exe (PID: 5900)
Reads the date of Windows installation
- Xenon Executor.exe (PID: 6348)
- Xenon Executor.exe (PID: 5900)
Executable content was dropped or overwritten
- Xenon Executor.exe (PID: 6348)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 2148)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 6736)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 368)
Process drops legitimate windows executable
- Xenon Executor.exe (PID: 6348)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 6736)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 2148)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 368)
- msiexec.exe (PID: 6764)
Starts a Microsoft application from unusual location
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 2148)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 368)
Starts itself from another location
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 2148)
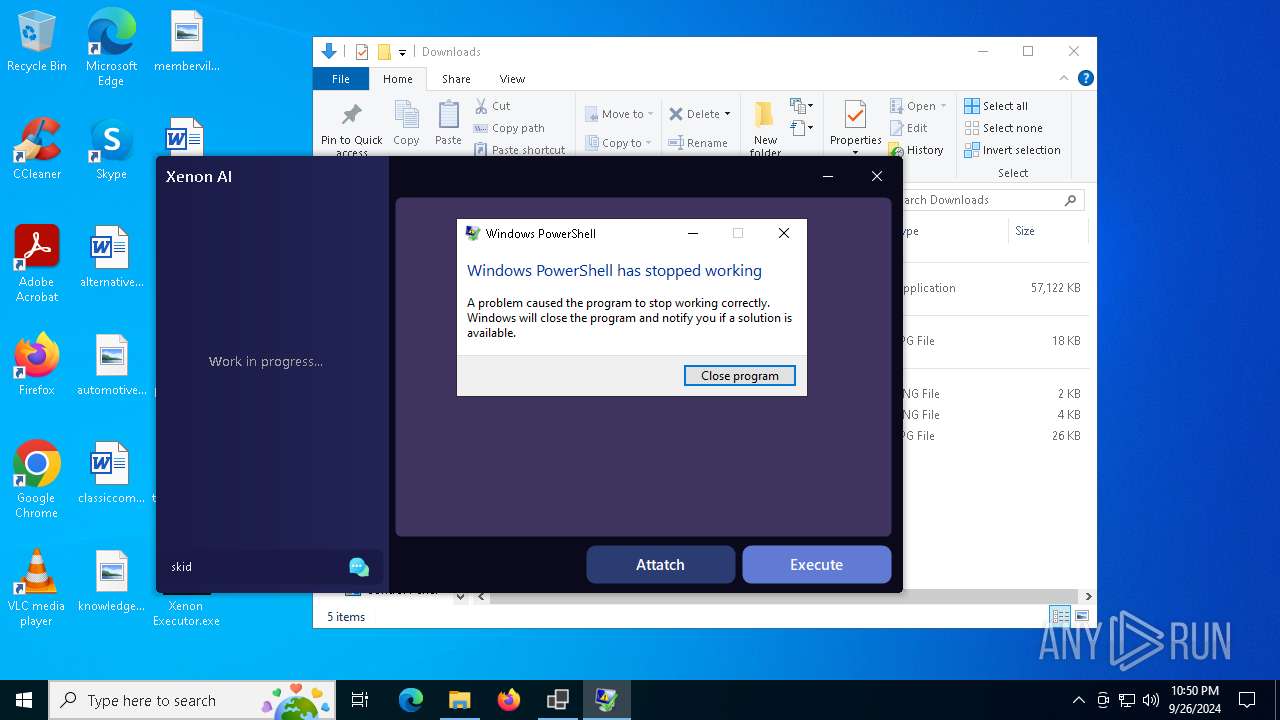
Executes application which crashes
- Xenon Executor.exe (PID: 7800)
- Xenon Executor.exe (PID: 7644)
- powershell.exe (PID: 7040)
Executing commands from a ".bat" file
- Xenon Executor.exe (PID: 4152)
- cmd.exe (PID: 892)
- cmd.exe (PID: 1644)
- cmd.exe (PID: 4704)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 892)
- cmd.exe (PID: 1644)
- cmd.exe (PID: 4704)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 892)
- cmd.exe (PID: 1644)
- cmd.exe (PID: 4704)
Application launched itself
- cmd.exe (PID: 892)
- cmd.exe (PID: 1644)
- cmd.exe (PID: 4704)
Cryptography encrypted command line is found
- cmd.exe (PID: 4128)
- cmd.exe (PID: 4824)
- cmd.exe (PID: 6052)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 892)
- Xenon Executor.exe (PID: 4152)
- cmd.exe (PID: 4704)
- cmd.exe (PID: 1644)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 892)
- cmd.exe (PID: 1644)
- cmd.exe (PID: 4704)
The process drops C-runtime libraries
- msiexec.exe (PID: 6764)
INFO
Reads the machine GUID from the registry
- Xenon Executor.exe (PID: 6348)
- Xenon Executor.exe (PID: 5900)
Checks supported languages
- Xenon Executor.exe (PID: 6348)
- Xenon Executor.exe (PID: 6892)
- Xenon Executor.exe (PID: 5900)
Reads the computer name
- Xenon Executor.exe (PID: 6348)
- Xenon Executor.exe (PID: 6892)
- Xenon Executor.exe (PID: 5900)
Create files in a temporary directory
- Xenon Executor.exe (PID: 6348)
- Xenon Executor.exe (PID: 5900)
Process checks computer location settings
- Xenon Executor.exe (PID: 6348)
- Xenon Executor.exe (PID: 5900)
The process uses the downloaded file
- Xenon Executor.exe (PID: 6348)
- Xenon Executor.exe (PID: 5900)
Manual execution by a user
- Xenon Executor.exe (PID: 5900)
- windowsdesktop-runtime-8.0.8-win-x64.exe (PID: 6736)
- Xenon Executor.exe (PID: 7644)
- Xenon Executor.exe (PID: 4688)
- Xenon Executor.exe (PID: 7800)
Sends debugging messages
- Xenon Executor.exe (PID: 6892)
Executable content was dropped or overwritten
- msedge.exe (PID: 7036)
- msiexec.exe (PID: 6764)
Application launched itself
- msedge.exe (PID: 7776)
- msedge.exe (PID: 7036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:09:26 21:10:05+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 2801152 |
| InitializedDataSize: | 7168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2adcce |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Xenon Executor for Gorilla Tag |
| CompanyName: | Xenon Tech |
| FileDescription: | Xenon Executor |
| FileVersion: | 1,0,0,0 |
| InternalName: | Xenon Executor.exe |
| LegalCopyright: | R_0 @ 2024 |
| LegalTrademarks: | R_0 @ 2024 |
| OriginalFileName: | Xenon Executor.exe |
| ProductName: | Xenon Executor |
| ProductVersion: | 1,0,0,0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
234
Monitored processes
98
Malicious processes
5
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | "C:\Users\admin\AppData\Local\Temp\{89EA4DD9-E738-4BA9-96E6-88CEB01DE378}\.be\windowsdesktop-runtime-8.0.8-win-x64.exe" -q -burn.elevated BurnPipe.{4C48FADB-1DDA-4FC3-8336-1666A66B66B4} {72A8F072-2F8B-4C1A-A2DE-2472AD769C96} 2148 | C:\Users\admin\AppData\Local\Temp\{89EA4DD9-E738-4BA9-96E6-88CEB01DE378}\.be\windowsdesktop-runtime-8.0.8-win-x64.exe | windowsdesktop-runtime-8.0.8-win-x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Desktop Runtime - 8.0.8 (x64) Exit code: 0 Version: 8.0.8.33916 Modules
| |||||||||||||||
| 788 | wmic diskdrive get Model | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4660 --field-trial-handle=2352,i,6079513838096208730,16018402200628472883,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Roaming\uLyEXTcs.bat"" | C:\Windows\System32\cmd.exe | — | Xenon Executor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 964 | C:\Windows\syswow64\MsiExec.exe -Embedding 5F5830714220375B31D1357ECAE92451 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1124 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6360 --field-trial-handle=2380,i,2148701238483743026,523985321722102041,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1232 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --no-appcompat-clear --mojo-platform-channel-handle=3776 --field-trial-handle=2380,i,2148701238483743026,523985321722102041,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1280 | C:\WINDOWS\system32\WerFault.exe -u -p 7040 -s 2652 | C:\Windows\System32\WerFault.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
50 383
Read events
49 431
Write events
908
Delete events
44
Modification events
| (PID) Process: | (6524) Xenon Executor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6524) Xenon Executor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6524) Xenon Executor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6524) Xenon Executor.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7036) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 24CDB6D3A3812F00 | |||
| (PID) Process: | (7036) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BC2DBED3A3812F00 | |||
Executable files
492
Suspicious files
193
Text files
125
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF25b61d.TMP | — | |
MD5:— | SHA256:— | |||
| 7036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF25b61d.TMP | — | |
MD5:— | SHA256:— | |||
| 7036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF25b63c.TMP | — | |
MD5:— | SHA256:— | |||
| 7036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF25b65b.TMP | — | |
MD5:— | SHA256:— | |||
| 7036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6348 | Xenon Executor.exe | C:\Users\admin\AppData\Local\Temp\Xenon Executor.exe | executable | |
MD5:027DF923646BDEE85F27A5A35EB4B929 | SHA256:33C219F720D8400CE8C0C7CC3256FB07050900CAD507C3C00017487EB308FFAC | |||
| 7036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:01ACA0E8A9E83C35F5FC4BDF1AFBD2BA | SHA256:F14B5290A0316A2C3ED21D66096D6158E46A993610F7ADA54A94926AB9C5BC37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
91
DNS requests
81
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6572 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7504 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7036 | msedge.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
7504 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5408 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/85cb4666-0aaf-4393-9c3a-aa0e3c026076?P1=1727994119&P2=404&P3=2&P4=XSO9CJvylEzhYCluQ%2fQBf6krwL01axAdF0PTq6aKyU9CcBnK2f5iBoyWZxPWyQojKLStUrGbApL3sW4QNrTASA%3d%3d | unknown | — | — | whitelisted |
2968 | svchost.exe | GET | 200 | 2.16.168.7:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5408 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/85cb4666-0aaf-4393-9c3a-aa0e3c026076?P1=1727994119&P2=404&P3=2&P4=XSO9CJvylEzhYCluQ%2fQBf6krwL01axAdF0PTq6aKyU9CcBnK2f5iBoyWZxPWyQojKLStUrGbApL3sW4QNrTASA%3d%3d | unknown | — | — | whitelisted |
5408 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/85cb4666-0aaf-4393-9c3a-aa0e3c026076?P1=1727994119&P2=404&P3=2&P4=XSO9CJvylEzhYCluQ%2fQBf6krwL01axAdF0PTq6aKyU9CcBnK2f5iBoyWZxPWyQojKLStUrGbApL3sW4QNrTASA%3d%3d | unknown | — | — | whitelisted |
2968 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1072 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3036 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2056 | svchost.exe | 184.30.17.189:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6196 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
aka.ms |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO Commonly Abused File Sharing Domain in DNS Lookup (filetransfer .io) |
4152 | Xenon Executor.exe | Potentially Bad Traffic | ET INFO Commonly Abused File Sharing Domain (filetransfer .io in TLS SNI) |
Process | Message |
|---|---|
Xenon Executor.exe | The application to execute does not exist: 'C:\Users\admin\AppData\Local\Temp\Xenon Executor.dll'. |
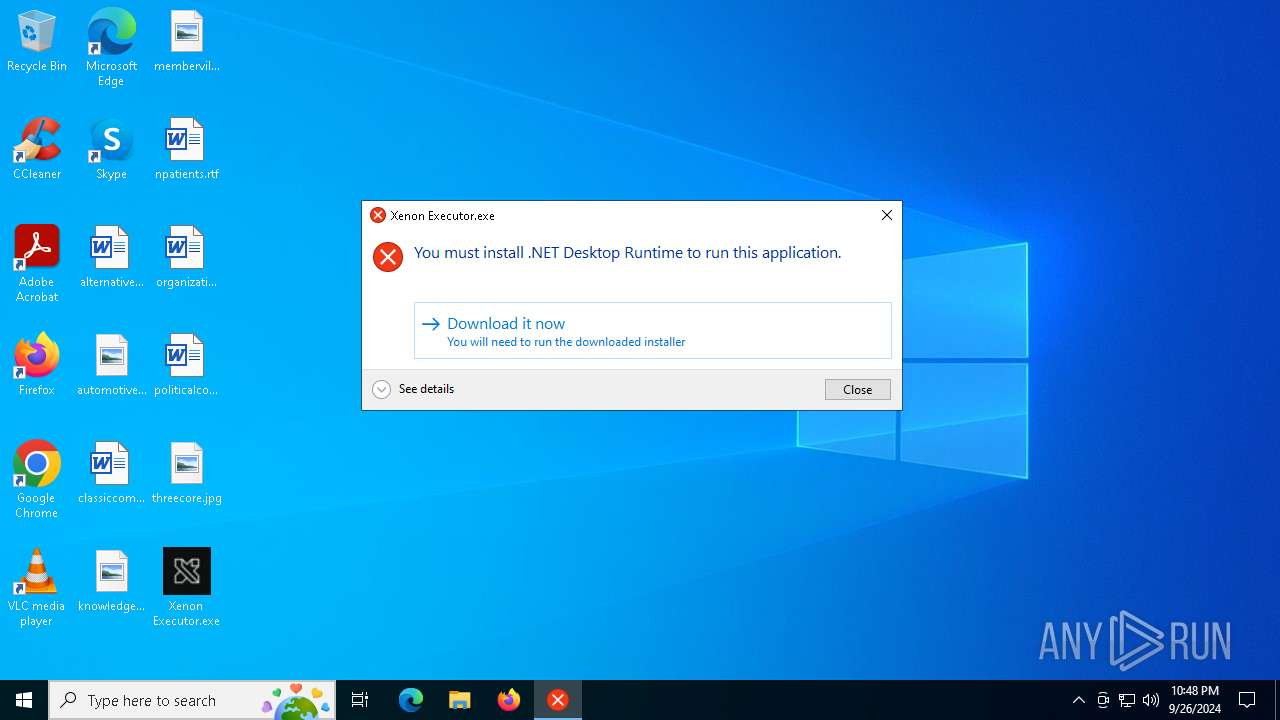
Xenon Executor.exe | You must install .NET to run this application.
App: C:\Users\admin\AppData\Local\Temp\Xenon Executor.exe
Architecture: x64
App host version: 8.0.8
.NET location: Not found
Learn more:
https://aka.ms/dotnet/app-launch-failed
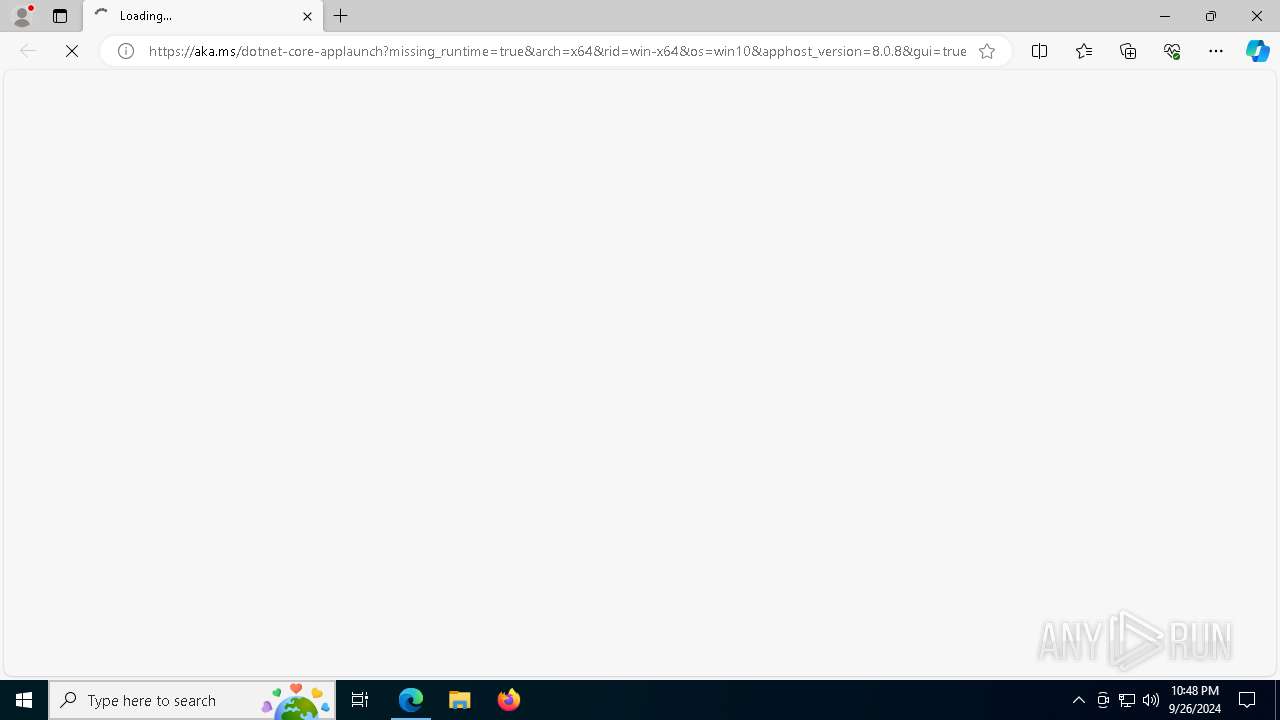
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win-x64&os=win10&apphost_version=8.0.8 |