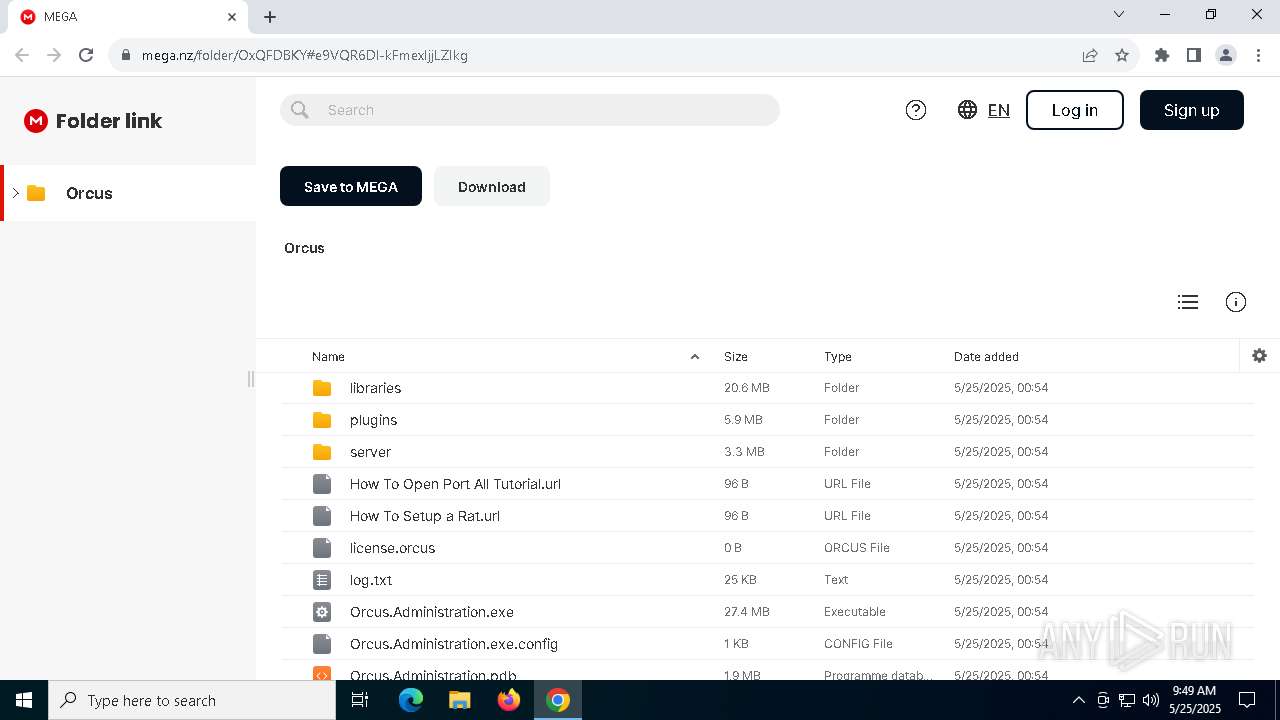
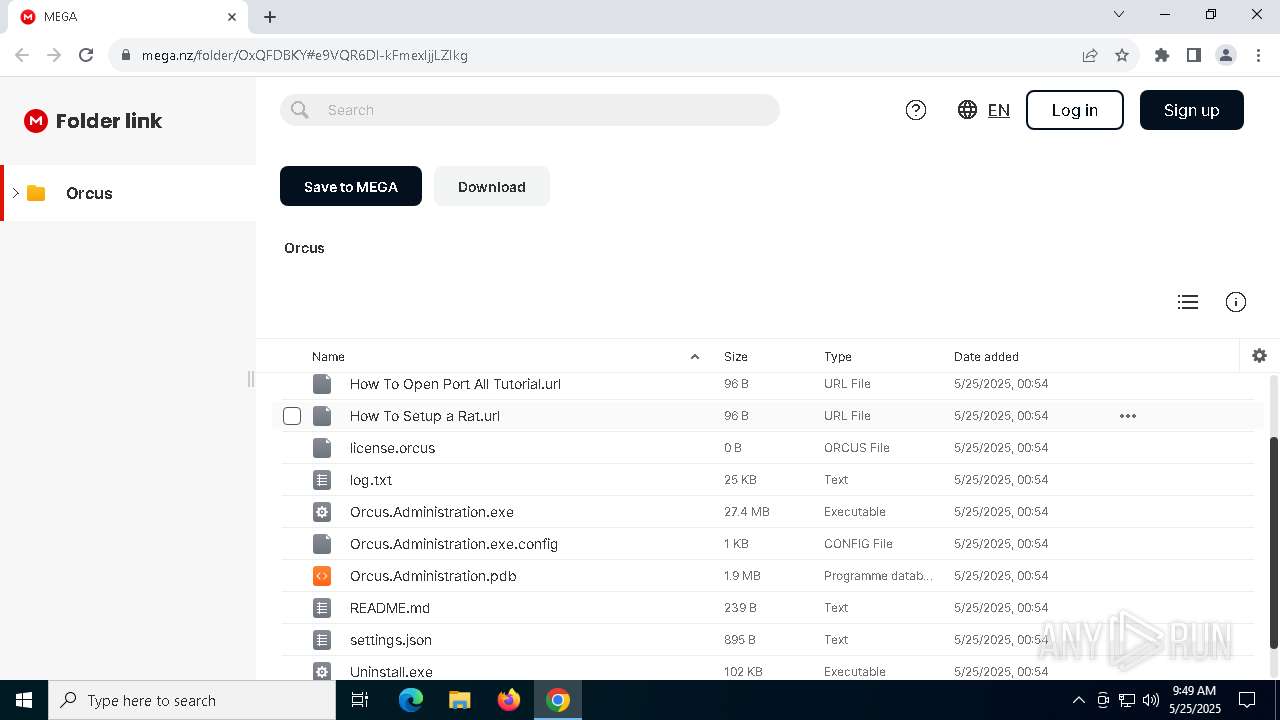
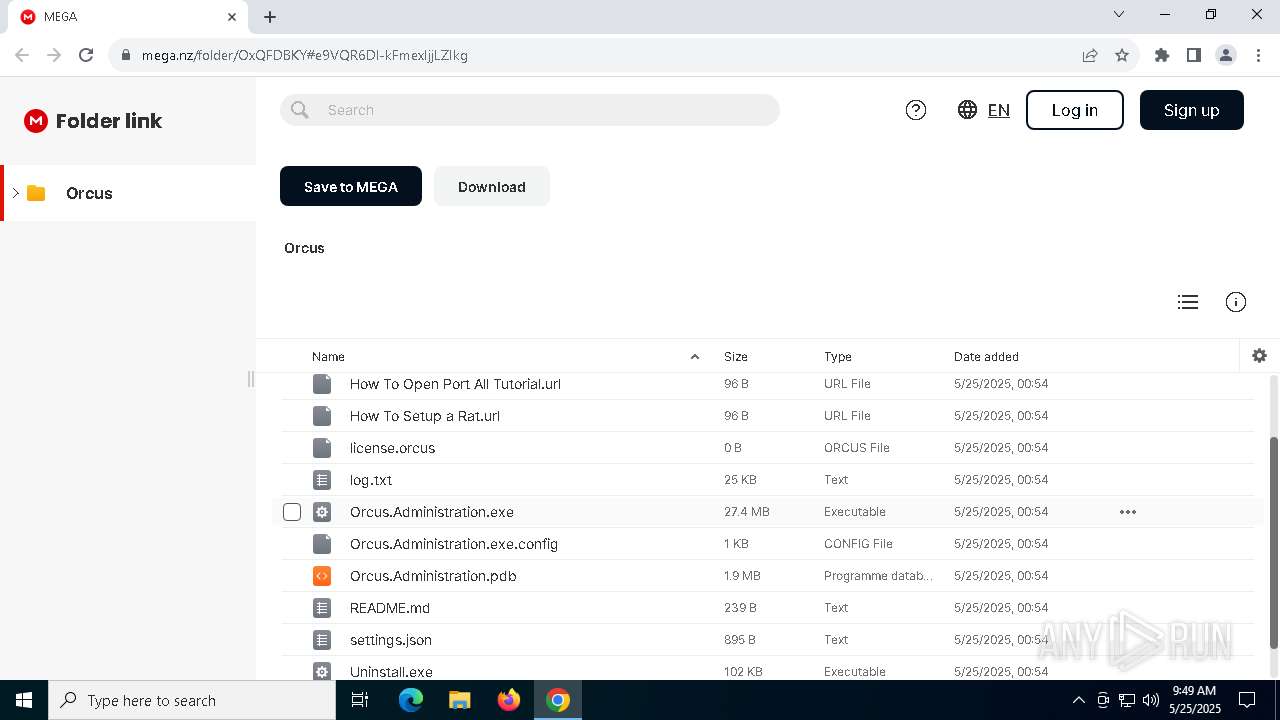
| URL: | https://tinyurl.com/OrcusTool |
| Full analysis: | https://app.any.run/tasks/6b2fb828-0103-4cdc-b681-c9f6f9a8e193 |
| Verdict: | Malicious activity |
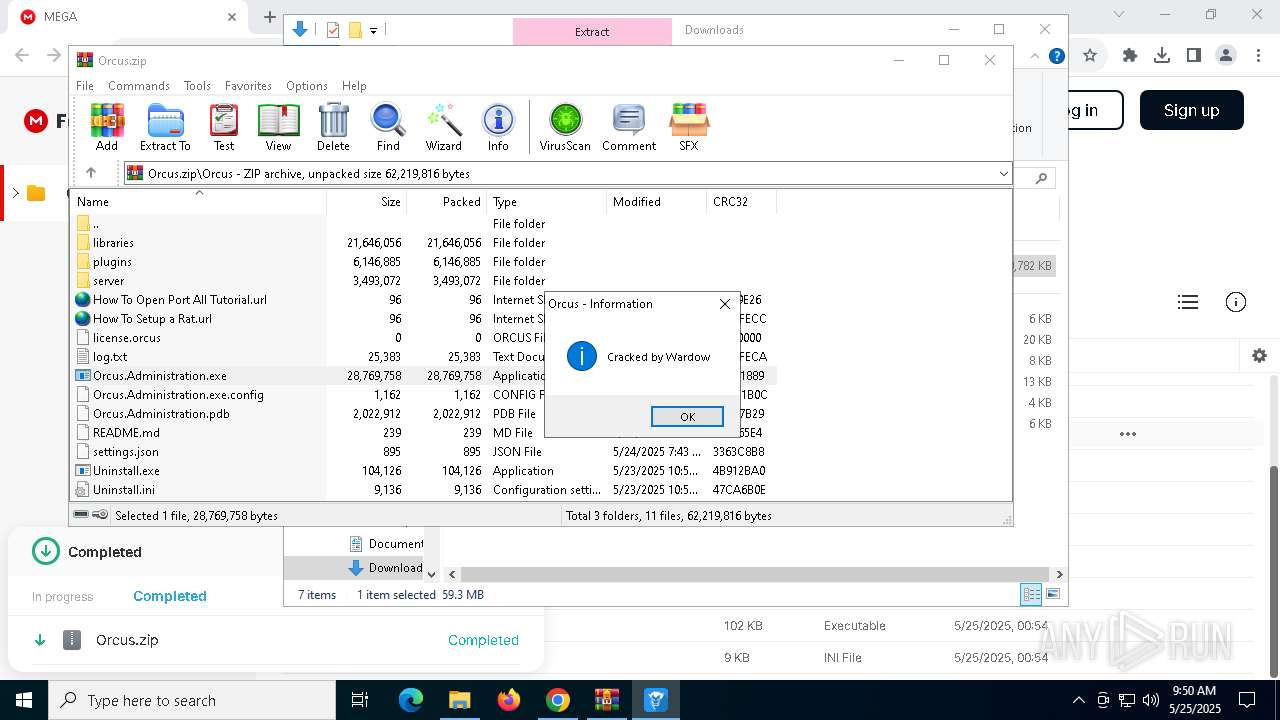
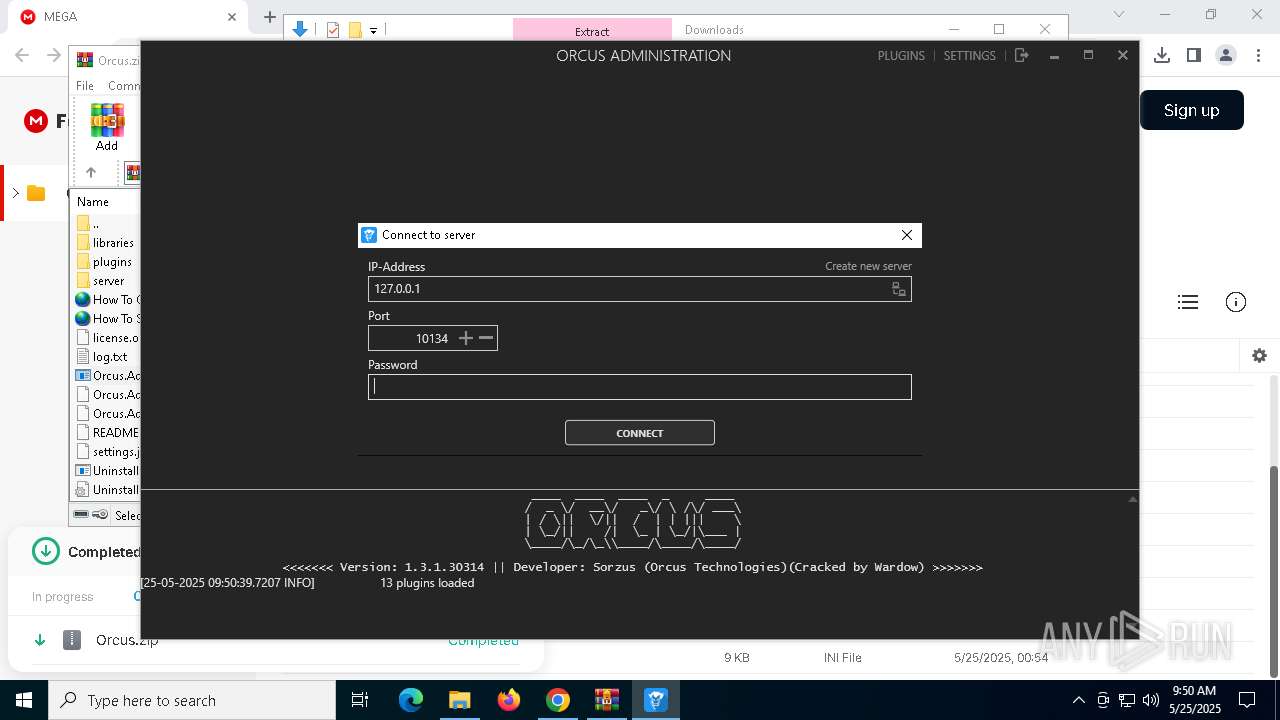
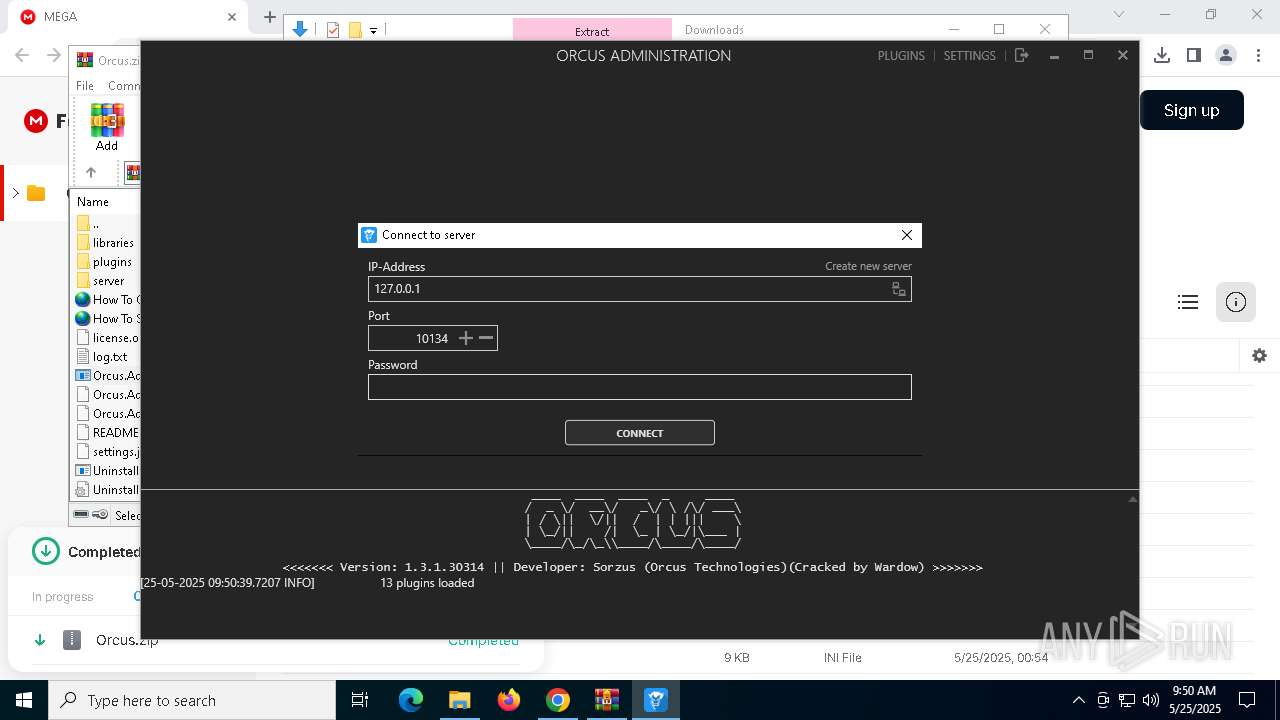
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | May 25, 2025, 09:49:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 23187A133E3FDC430CD1EB0BB5CFBD01 |
| SHA1: | A5708D885A0D5EDA09927317361797B7820B1309 |
| SHA256: | CC5C765B69C7F60D114514A7DB72119AB652AA63EE114B717B27D23D0F1792DB |
| SSDEEP: | 3:N8EzLdIgDMS:2End3D9 |
MALICIOUS
Orcus is detected
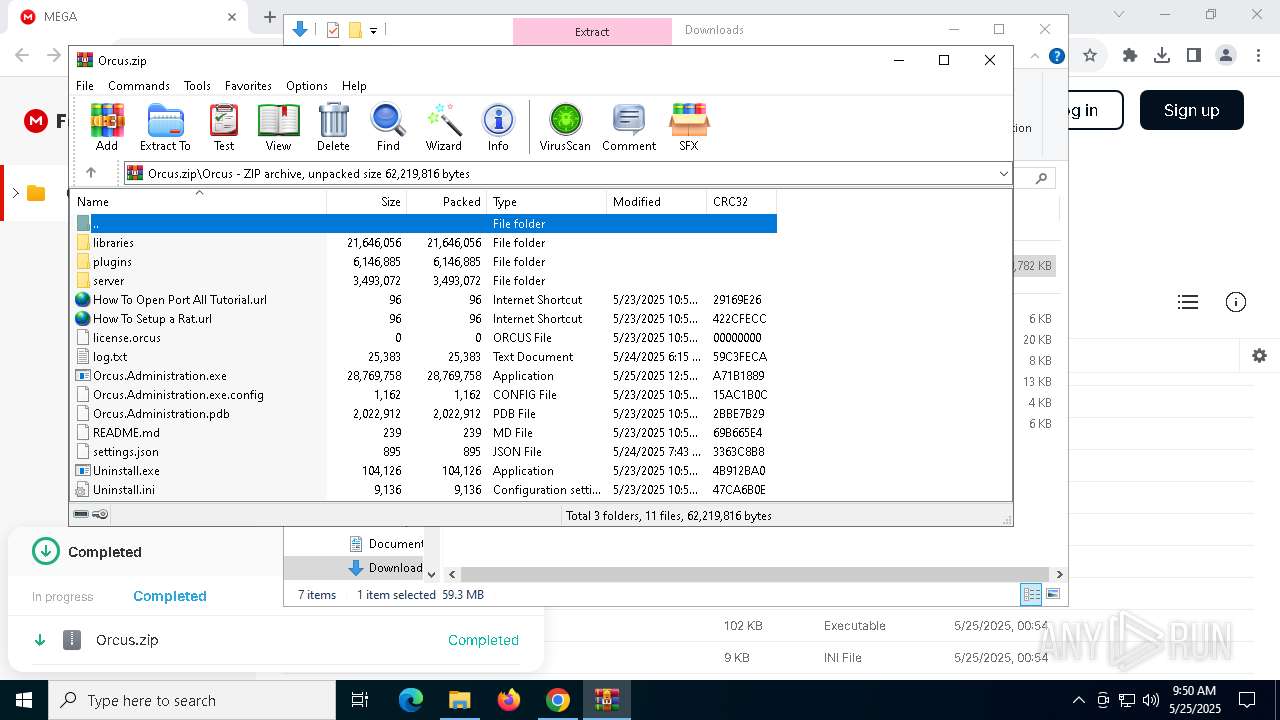
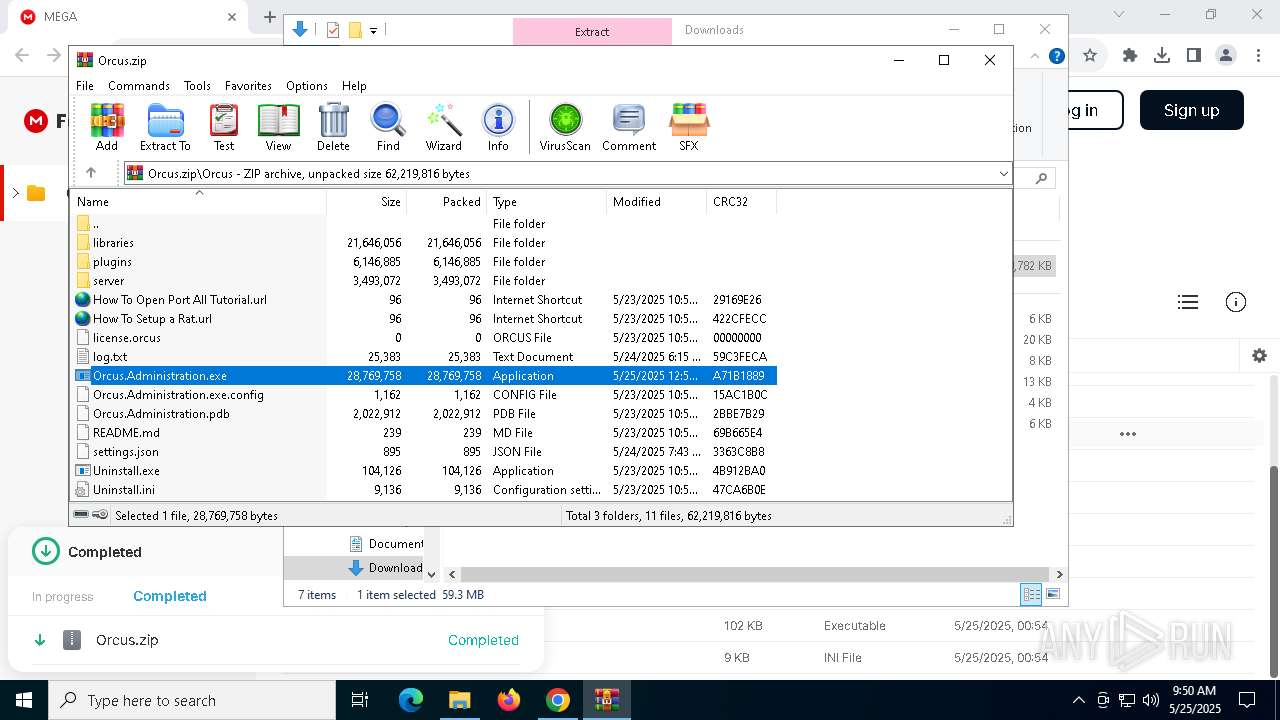
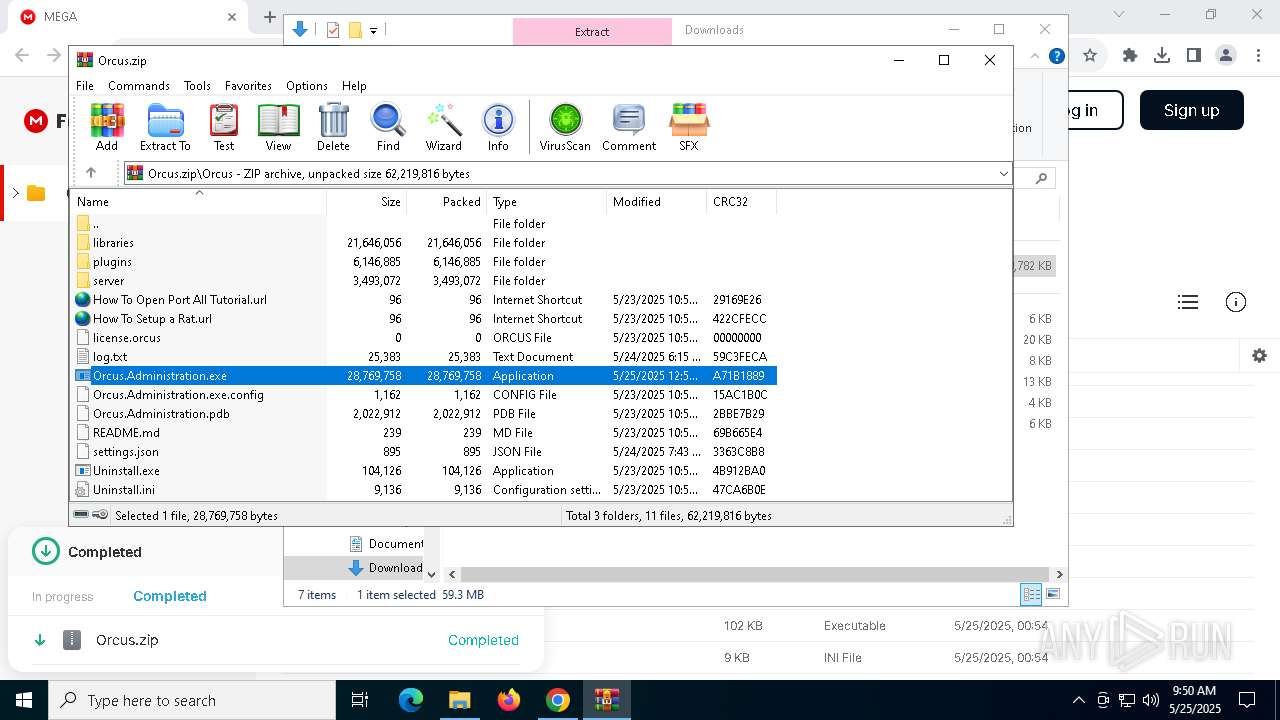
- Orcus.Administration.exe (PID: 6564)
- syhadow.exe (PID: 3140)
SUSPICIOUS
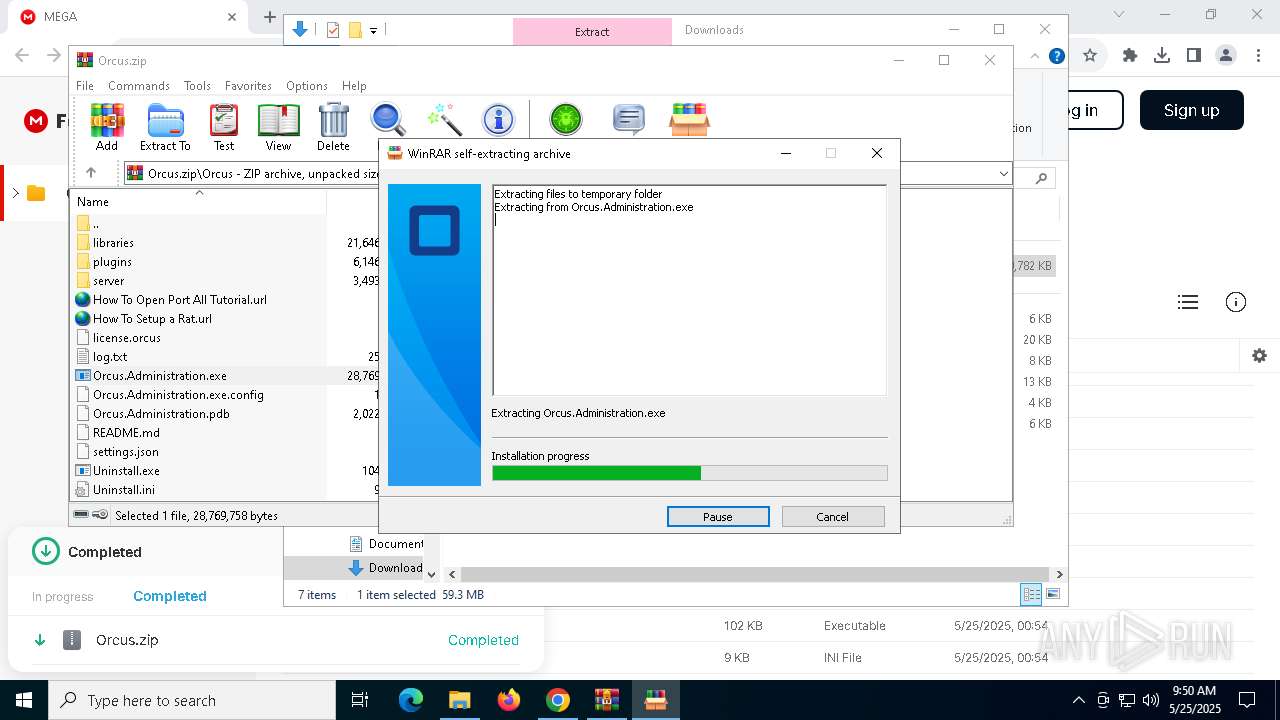
Process drops legitimate windows executable
- WinRAR.exe (PID: 7876)
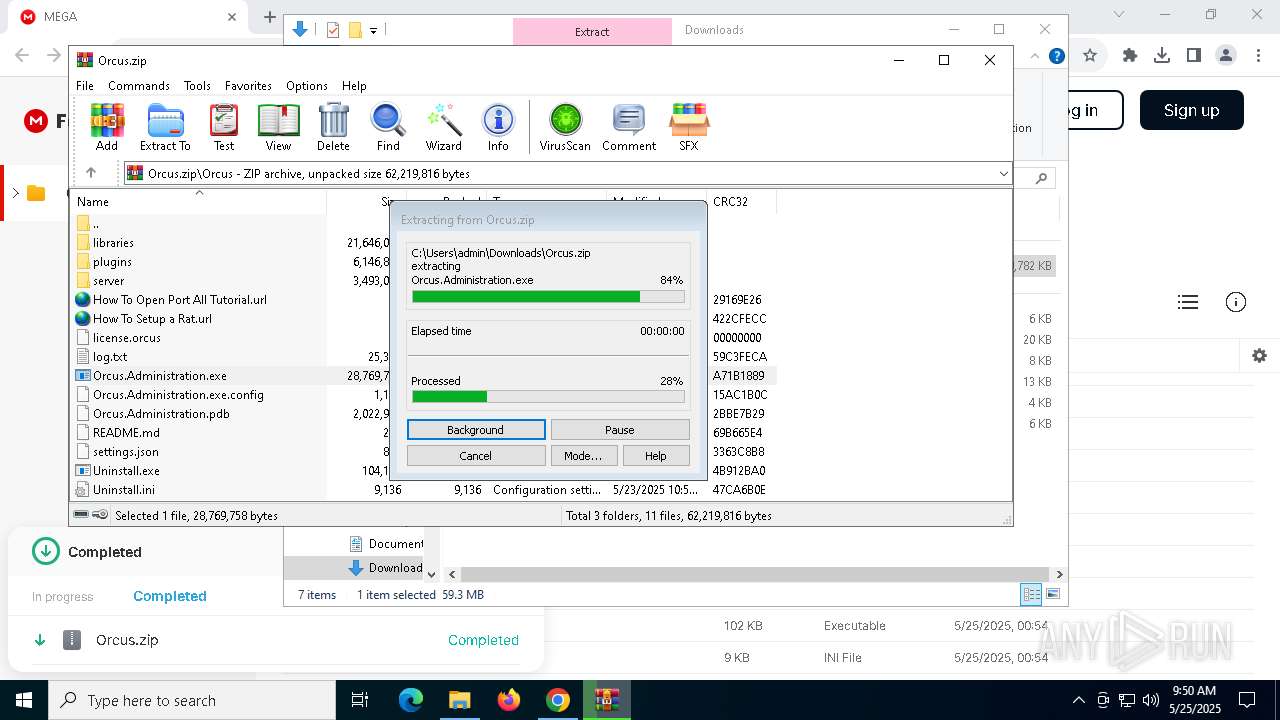
- Orcus.Administration.exe (PID: 3884)
Executable content was dropped or overwritten
- Orcus.Administration.exe (PID: 3884)
- Orcus.Administration.exe (PID: 6564)
- 4pm.unnyf.exe (PID: 2284)
- Notthatguy11.exe (PID: 7896)
- Uninstall.exe (PID: 7992)
- Crackhead.exe (PID: 2392)
- syhadow.exe (PID: 3140)
- AudioDriver.exe (PID: 3156)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7876)
- Orcus.Administration.exe (PID: 3884)
- Orcus.Administration.exe (PID: 6564)
- 4pm.unnyf.exe (PID: 2284)
- Uninstall.exe (PID: 7992)
- Crackhead.exe (PID: 2392)
- Notthatguy11.exe (PID: 7896)
- syhadow.exe (PID: 3140)
Reads the date of Windows installation
- Orcus.Administration.exe (PID: 3884)
- 4pm.unnyf.exe (PID: 2284)
- Notthatguy11.exe (PID: 7896)
- Crackhead.exe (PID: 2392)
Starts itself from another location
- 4pm.unnyf.exe (PID: 2284)
- Notthatguy11.exe (PID: 7896)
- Uninstall.exe (PID: 7992)
- syhadow.exe (PID: 3140)
INFO
Application launched itself
- chrome.exe (PID: 4436)
Manual execution by a user
- WinRAR.exe (PID: 7876)
Checks supported languages
- Orcus.Administration.exe (PID: 3884)
- Orcus.Administration.exe (PID: 6564)
- 4pm.unnyf.exe (PID: 2284)
- Notthatguy11.exe (PID: 7896)
- Uninstall.exe (PID: 7992)
- Uninstall.exe (PID: 5048)
- Crackhead.exe (PID: 2392)
- syhadow.exe (PID: 3140)
Reads the computer name
- Orcus.Administration.exe (PID: 3884)
- Orcus.Administration.exe (PID: 6564)
- 4pm.unnyf.exe (PID: 2284)
- Notthatguy11.exe (PID: 7896)
- Crackhead.exe (PID: 2392)
- Uninstall.exe (PID: 7992)
- syhadow.exe (PID: 3140)
Create files in a temporary directory
- Orcus.Administration.exe (PID: 3884)
- Orcus.Administration.exe (PID: 6564)
- 4pm.unnyf.exe (PID: 2284)
- Notthatguy11.exe (PID: 7896)
- Crackhead.exe (PID: 2392)
- Uninstall.exe (PID: 7992)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7876)
Reads the software policy settings
- slui.exe (PID: 7920)
- Orcus.Administration.exe (PID: 6564)
Process checks computer location settings
- Orcus.Administration.exe (PID: 3884)
- 4pm.unnyf.exe (PID: 2284)
- Notthatguy11.exe (PID: 7896)
- Uninstall.exe (PID: 7992)
- Crackhead.exe (PID: 2392)
- syhadow.exe (PID: 3140)
Creates files or folders in the user directory
- syhadow.exe (PID: 3140)
Reads the machine GUID from the registry
- syhadow.exe (PID: 3140)
- Orcus.Administration.exe (PID: 6564)
Disables trace logs
- Orcus.Administration.exe (PID: 6564)
Checks proxy server information
- Orcus.Administration.exe (PID: 6564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
165
Monitored processes
33
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\4pm.unnyf.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\4pm.unnyf.exe | Orcus.Administration.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2392 | "C:\Users\admin\AppData\Local\Temp\RarSFX2\Crackhead.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX2\Crackhead.exe | Notthatguy11.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3140 | "C:\Users\admin\AppData\Local\Temp\RarSFX3\syhadow.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX3\syhadow.exe | Crackhead.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3156 | "C:\Users\admin\AppData\Roaming\Microsoft\Speech\AudioDriver.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Speech\AudioDriver.exe | syhadow.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 3884 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7876.43314\Orcus\Orcus.Administration.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7876.43314\Orcus\Orcus.Administration.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4708 --field-trial-handle=1880,i,12782142265943628214,14951835569197414521,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://tinyurl.com/OrcusTool" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 5048 | "C:\Users\admin\AppData\Local\Temp\Uninstall.exe" end | C:\Users\admin\AppData\Local\Temp\Uninstall.exe | — | Uninstall.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
13 070
Read events
13 019
Write events
45
Delete events
6
Modification events
| (PID) Process: | (4436) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4436) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4436) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4436) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4436) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (8176) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000006E6AE2645ACDDB01 | |||
| (PID) Process: | (7876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
128
Suspicious files
240
Text files
490
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4436 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10e011.TMP | — | |
MD5:— | SHA256:— | |||
| 4436 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10e011.TMP | — | |
MD5:— | SHA256:— | |||
| 4436 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10e011.TMP | — | |
MD5:— | SHA256:— | |||
| 4436 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4436 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4436 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10e021.TMP | — | |
MD5:— | SHA256:— | |||
| 4436 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4436 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4436 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10e011.TMP | — | |
MD5:— | SHA256:— | |||
| 4436 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10e040.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
184
DNS requests
119
Threats
100
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2284 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2284 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1388 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/mu3drl5l7dxjtwqd2bv72hybhi_2025.5.23.1/jflhchccmppkfebkiaminageehmchikm_2025.05.23.01_all_ac7lhpo4vvfmv4pn37jw6qxv2xma.crx3 | unknown | — | — | whitelisted |
1388 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/mu3drl5l7dxjtwqd2bv72hybhi_2025.5.23.1/jflhchccmppkfebkiaminageehmchikm_2025.05.23.01_all_ac7lhpo4vvfmv4pn37jw6qxv2xma.crx3 | unknown | — | — | whitelisted |
1388 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/mu3drl5l7dxjtwqd2bv72hybhi_2025.5.23.1/jflhchccmppkfebkiaminageehmchikm_2025.05.23.01_all_ac7lhpo4vvfmv4pn37jw6qxv2xma.crx3 | unknown | — | — | whitelisted |
1388 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/mu3drl5l7dxjtwqd2bv72hybhi_2025.5.23.1/jflhchccmppkfebkiaminageehmchikm_2025.05.23.01_all_ac7lhpo4vvfmv4pn37jw6qxv2xma.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4436 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7328 | chrome.exe | 104.18.111.161:443 | tinyurl.com | CLOUDFLARENET | — | whitelisted |
7328 | chrome.exe | 108.177.15.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
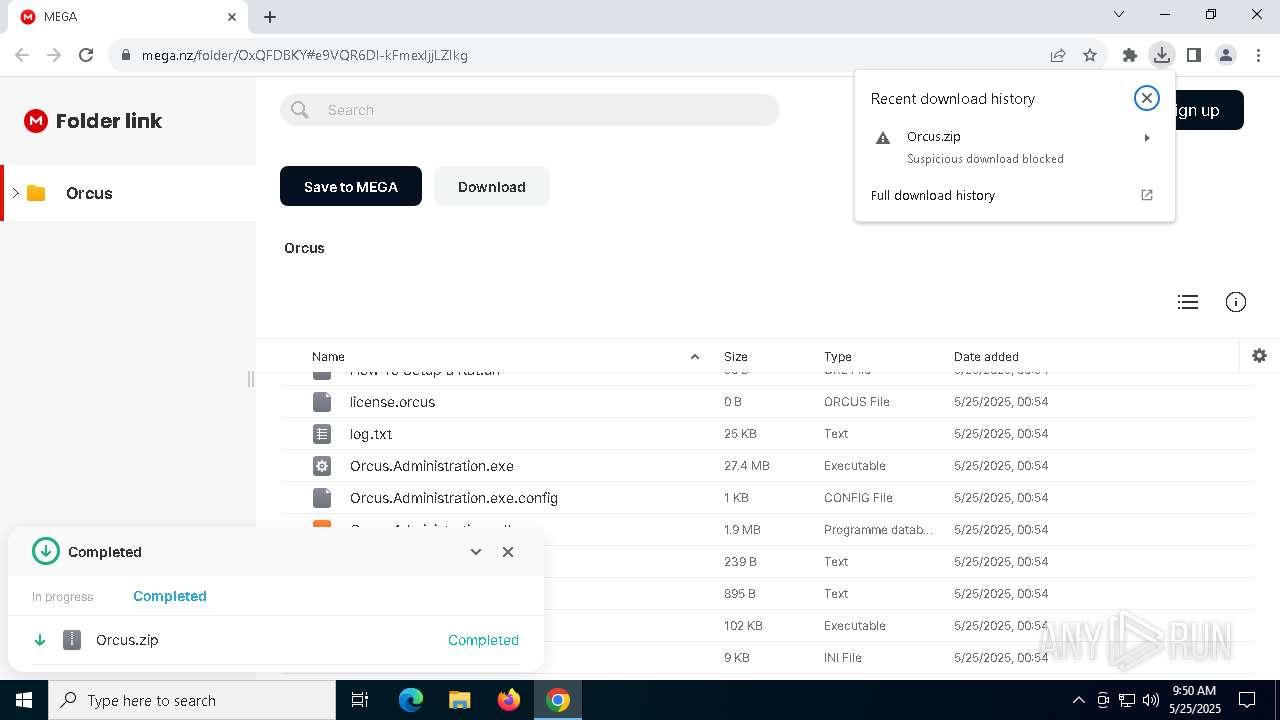
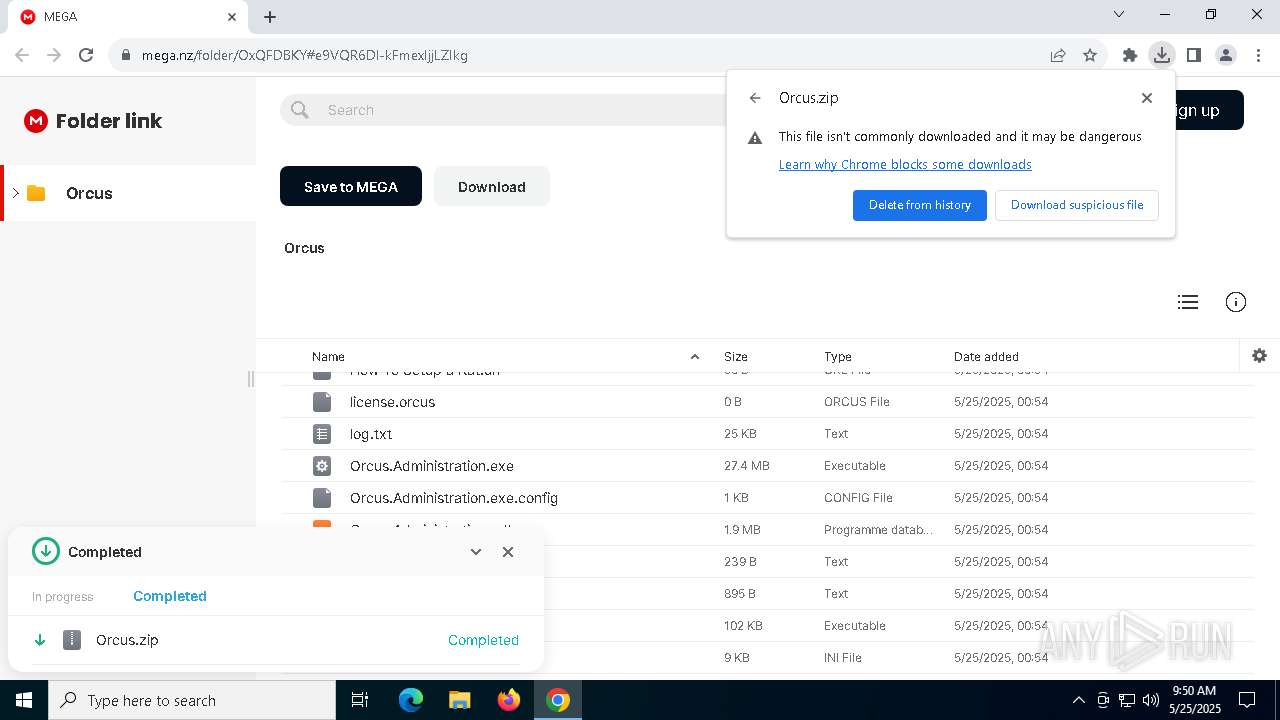
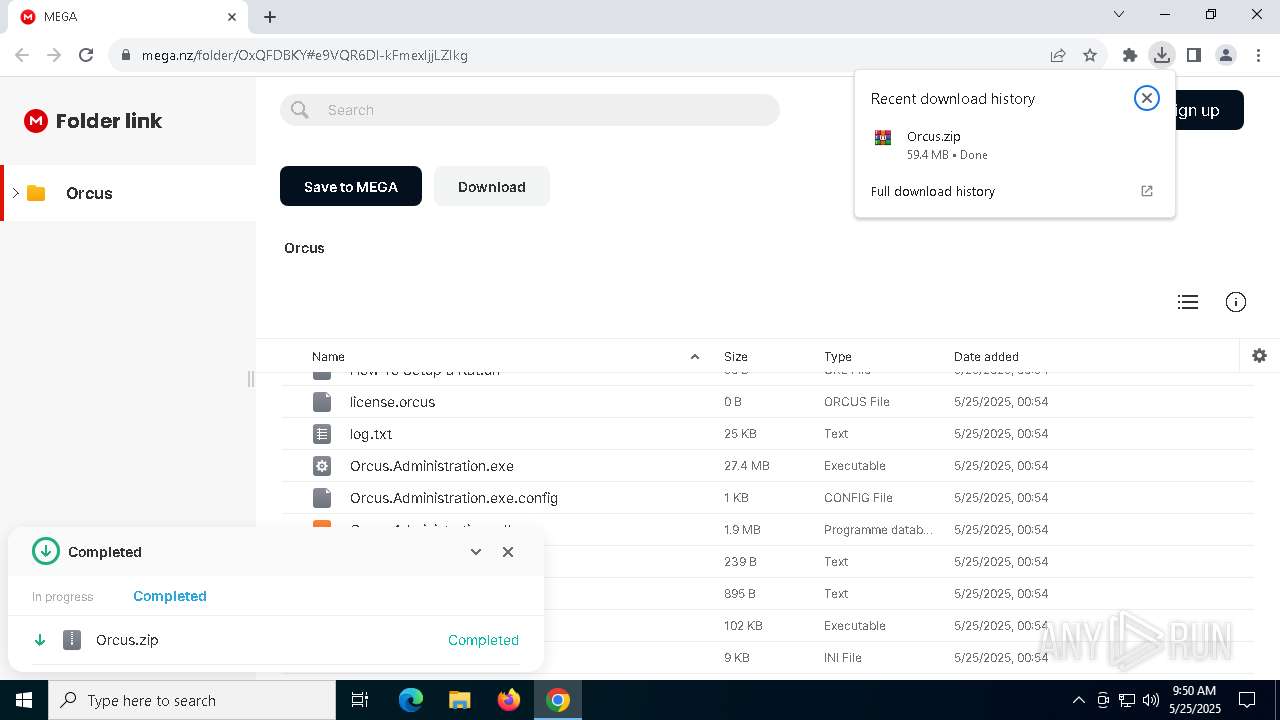
7328 | chrome.exe | 31.216.144.5:443 | mega.nz | Datacenter Luxembourg S.A. | LU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
tinyurl.com |
| whitelisted |
accounts.google.com |
| whitelisted |
mega.nz |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
na.static.mega.co.nz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7328 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
7328 | chrome.exe | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
7328 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] URL Shortener TinyURL (tinyurl .com) |
7328 | chrome.exe | Misc activity | INFO [ANY.RUN] Possible short link service (tinyurl .com) |
7328 | chrome.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
7328 | chrome.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
7328 | chrome.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
7328 | chrome.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
7328 | chrome.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
7328 | chrome.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |