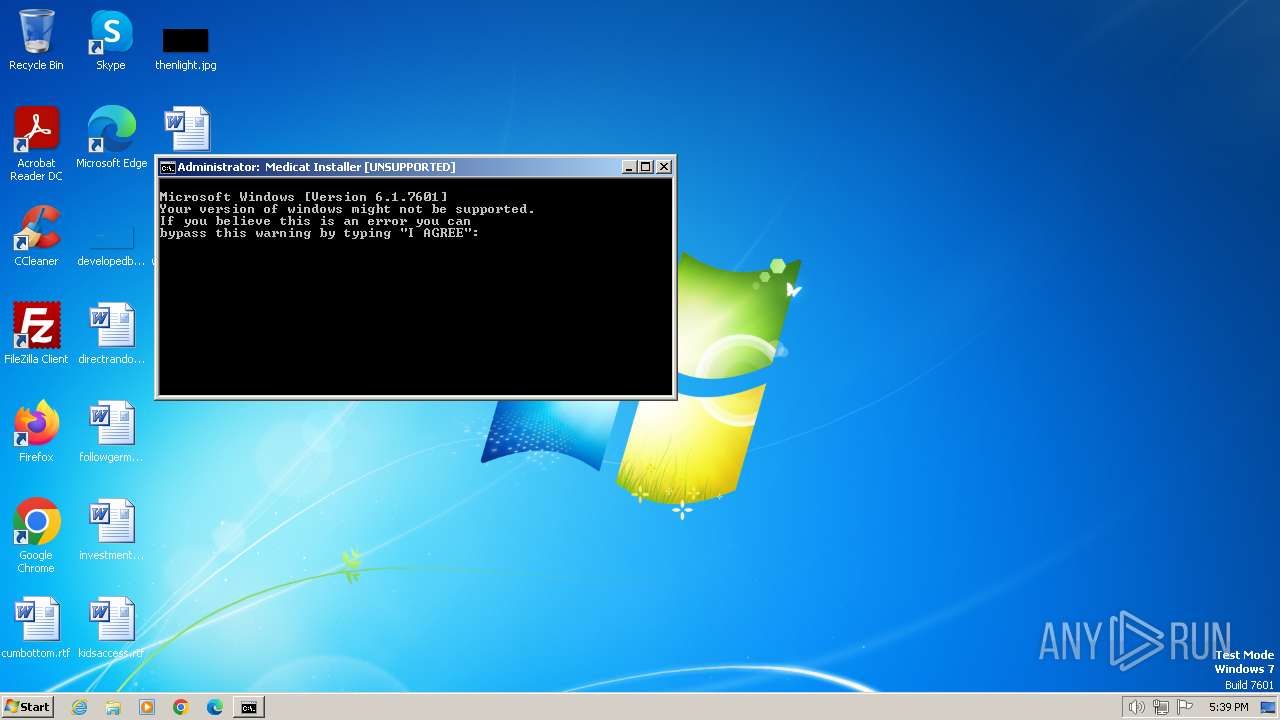
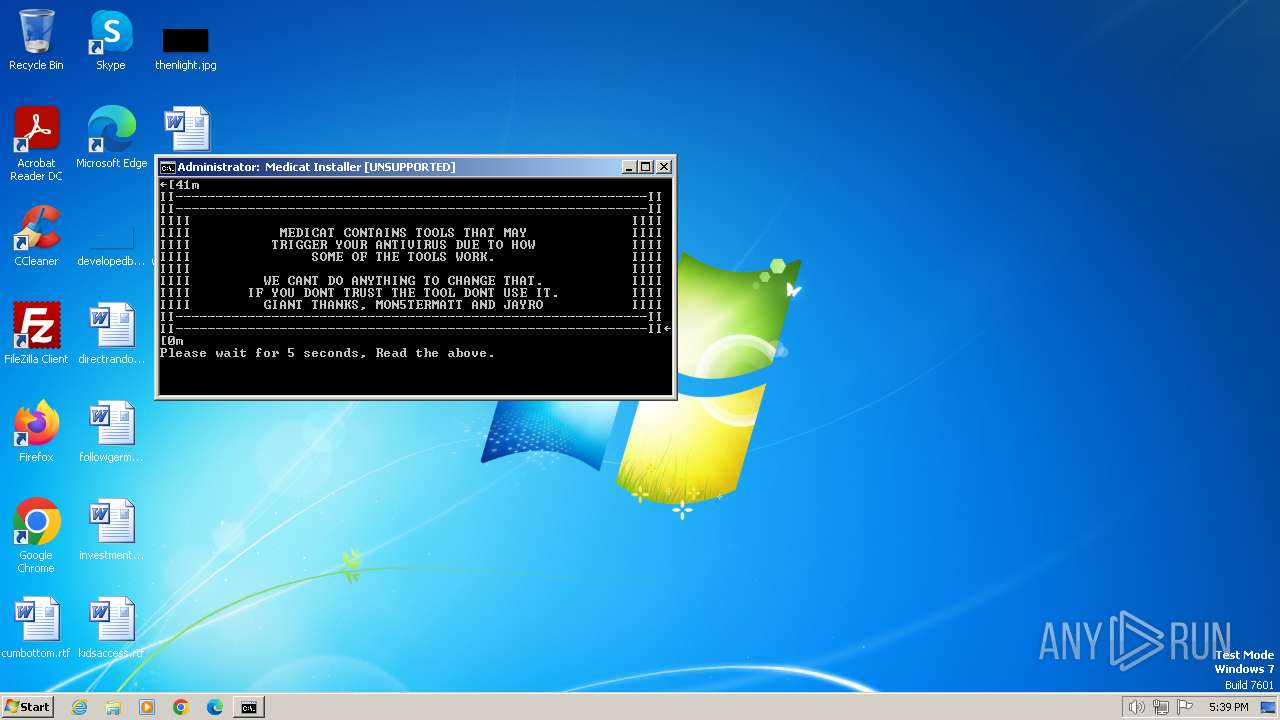
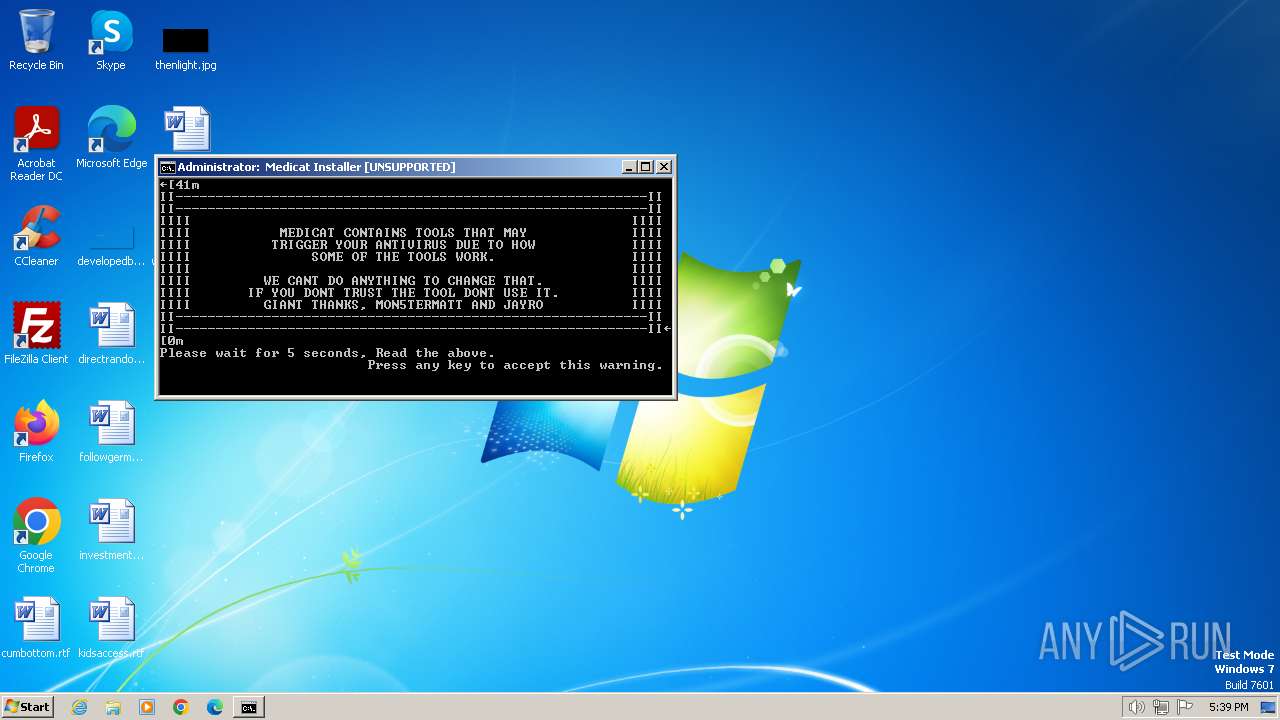
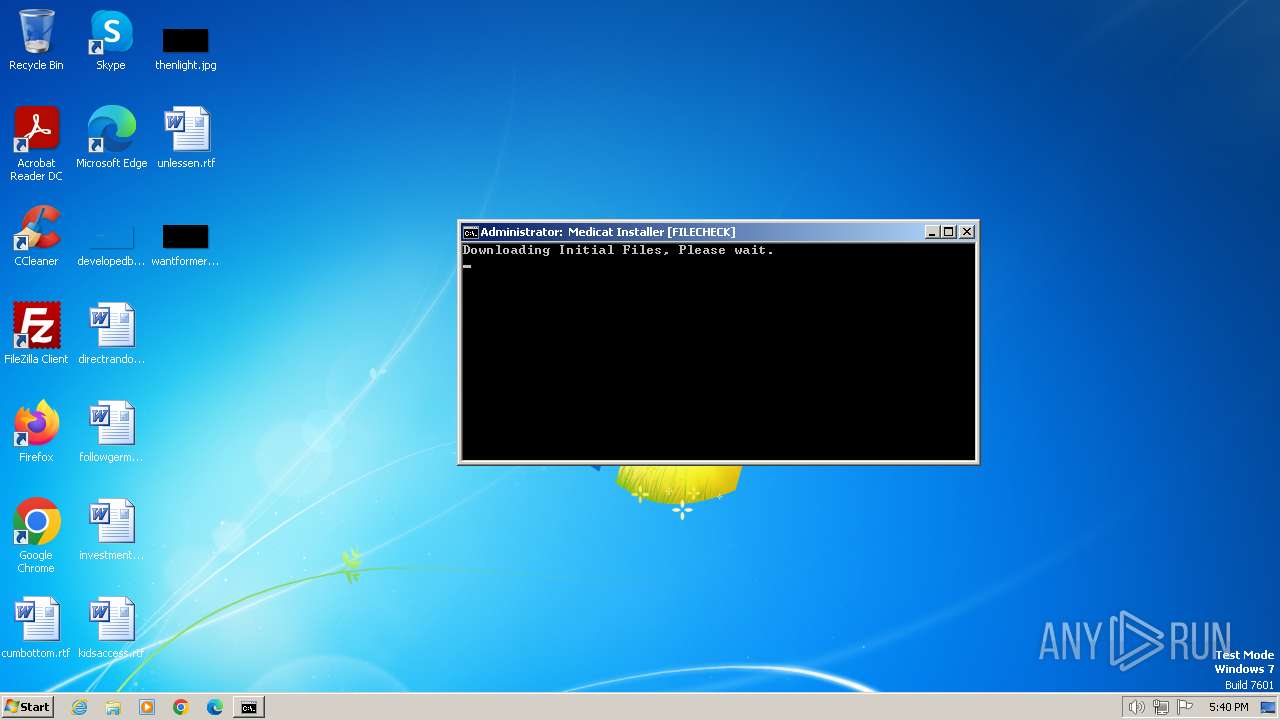
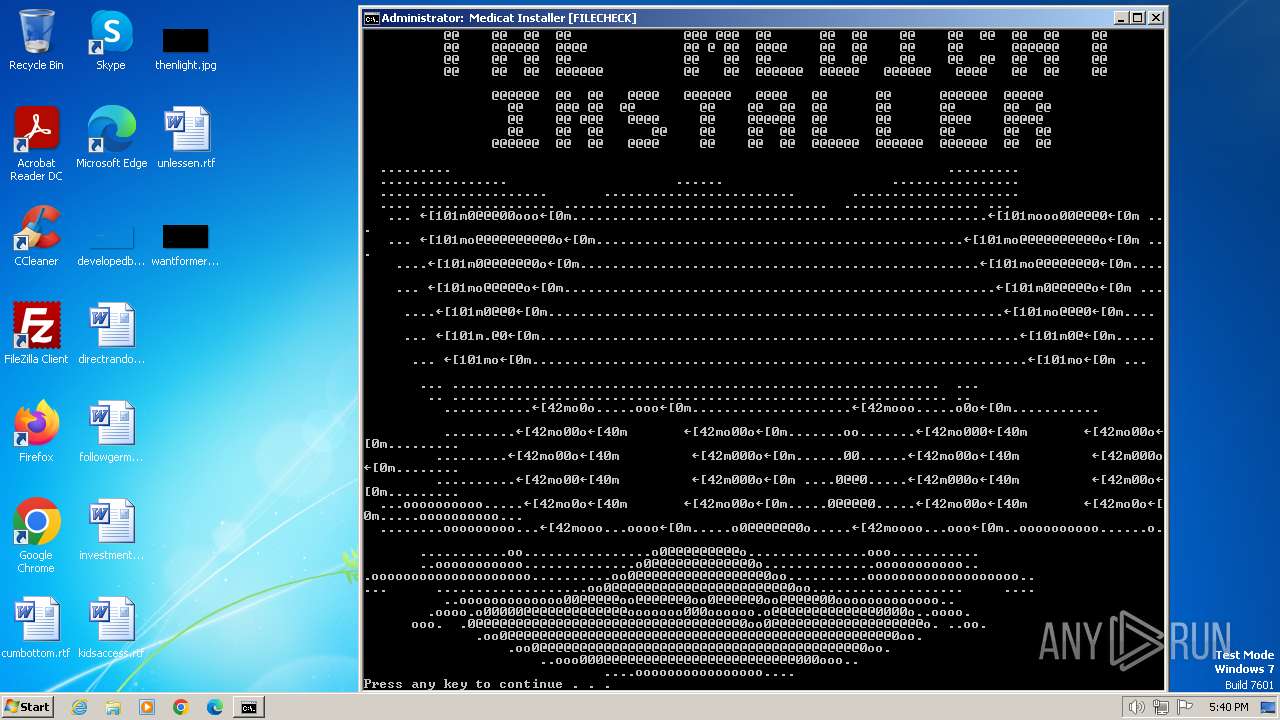
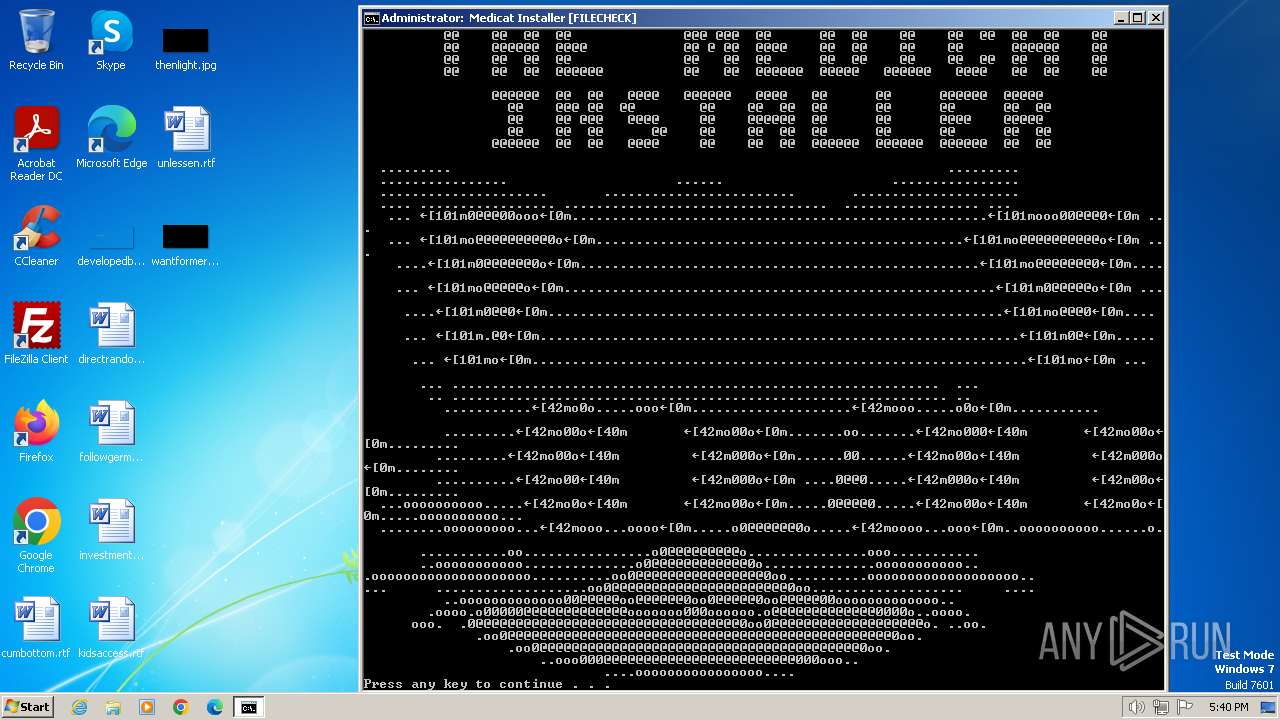
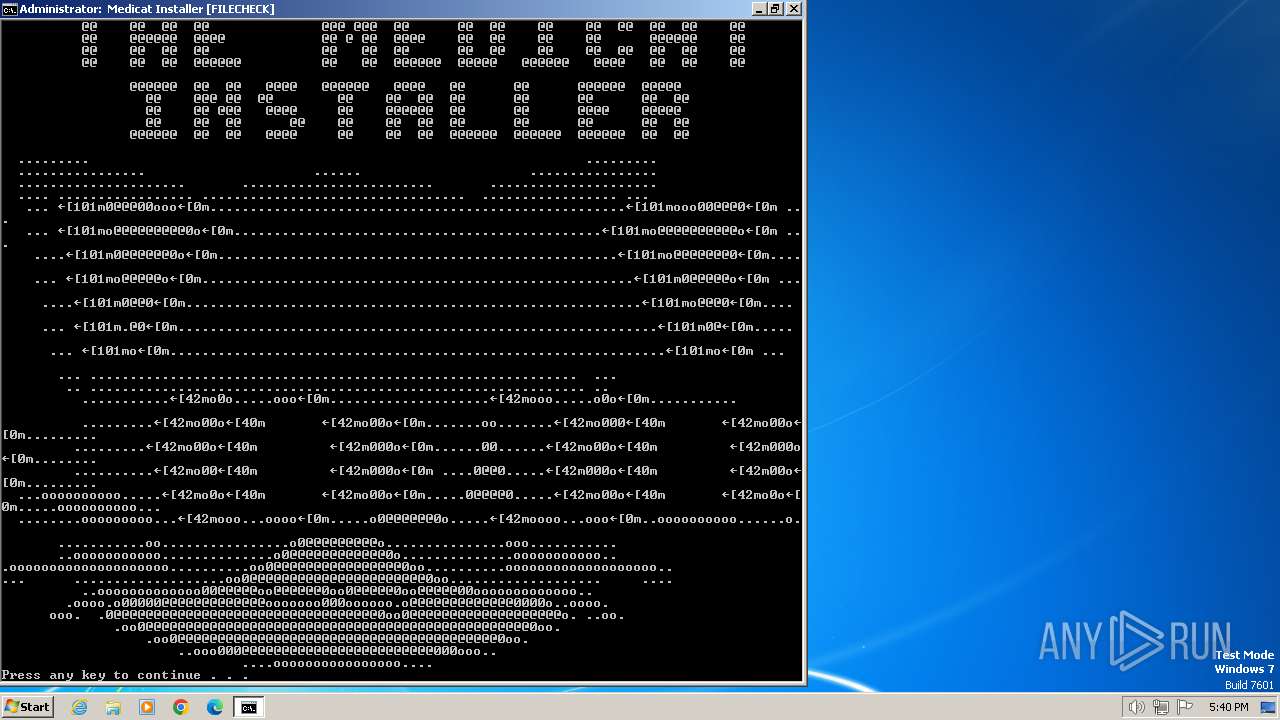
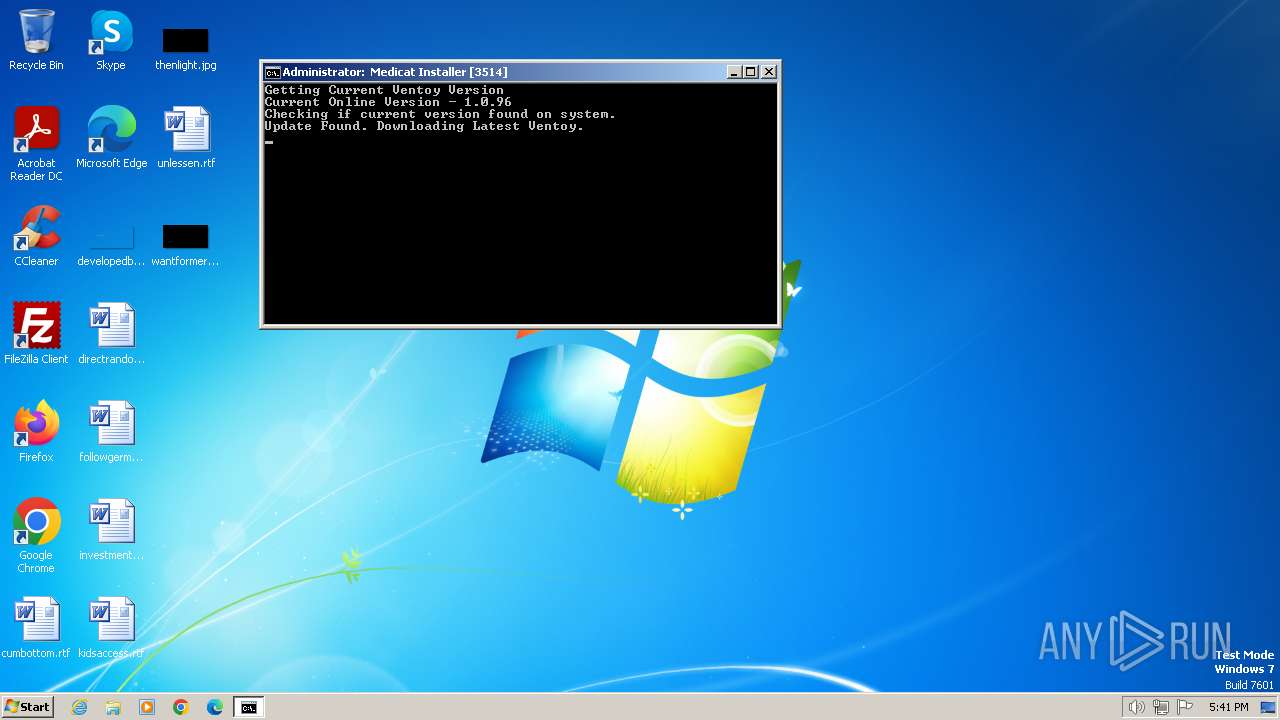
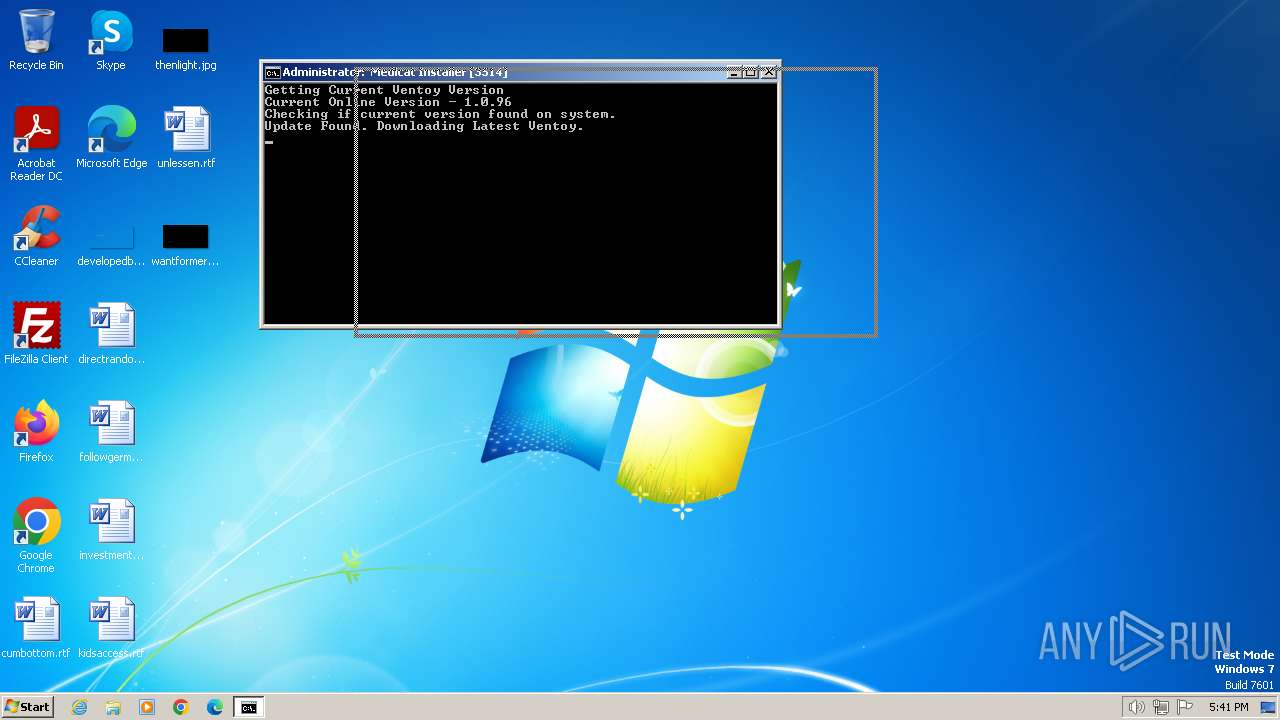
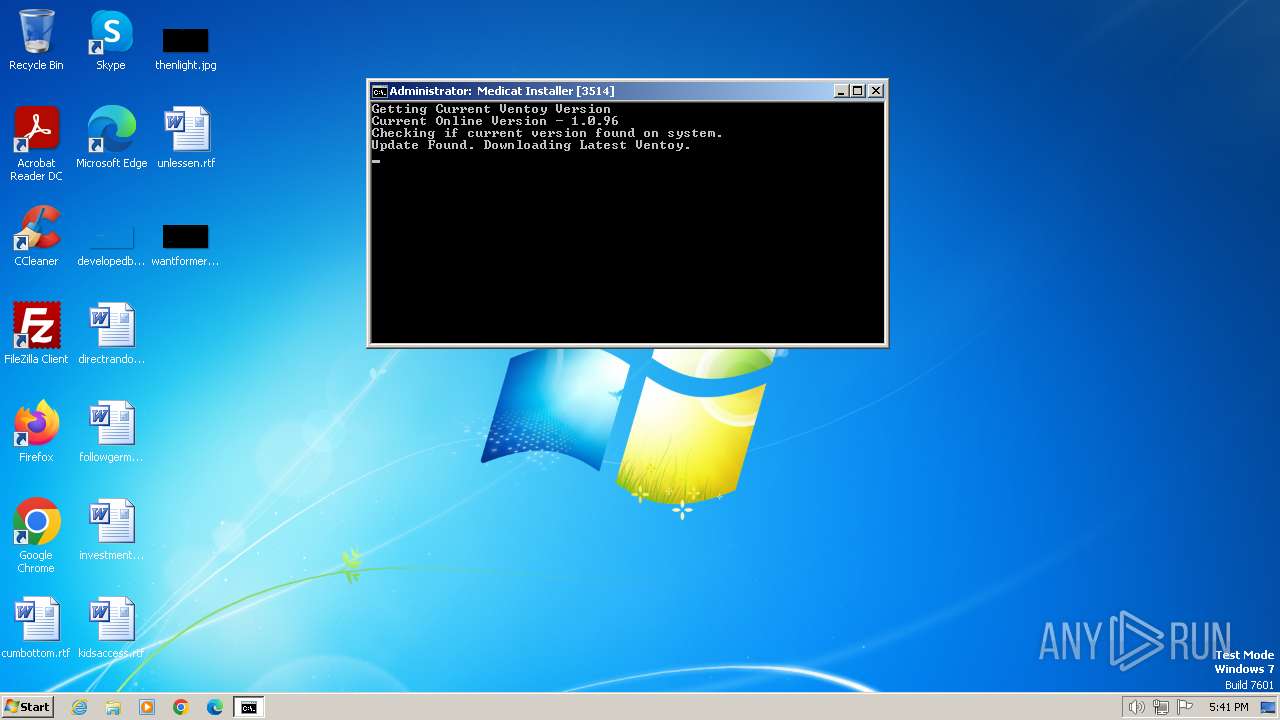
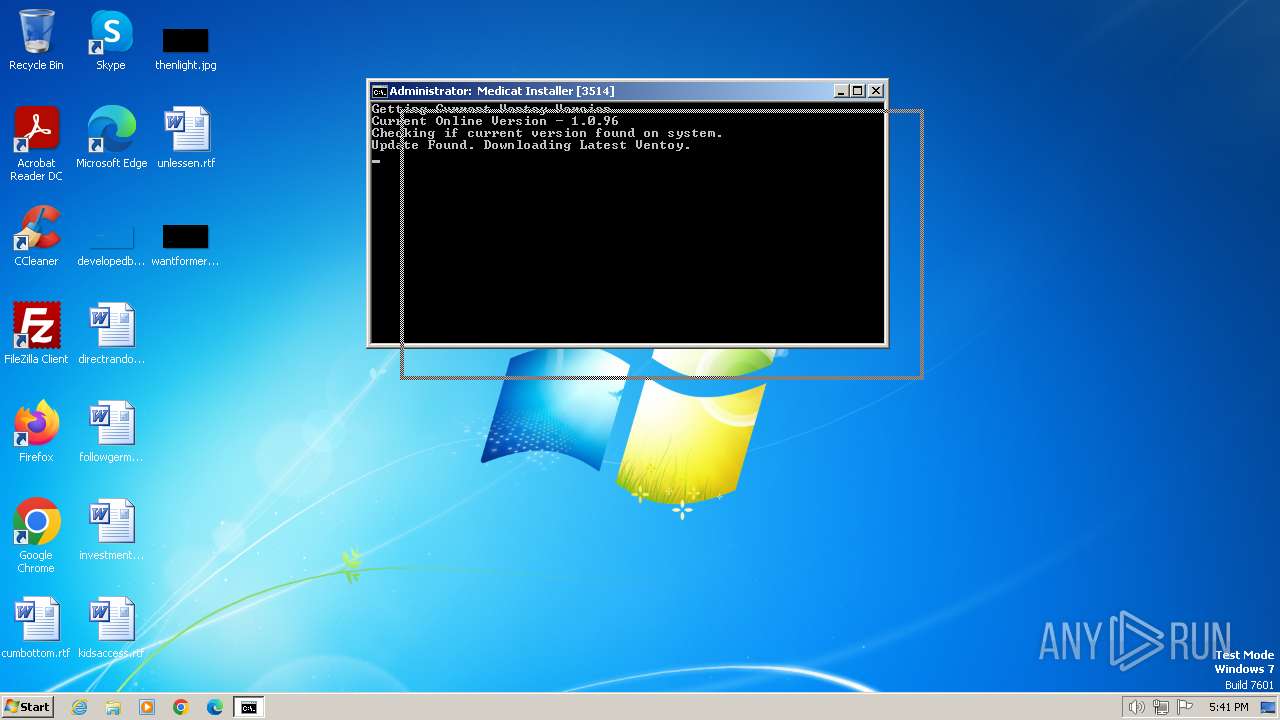
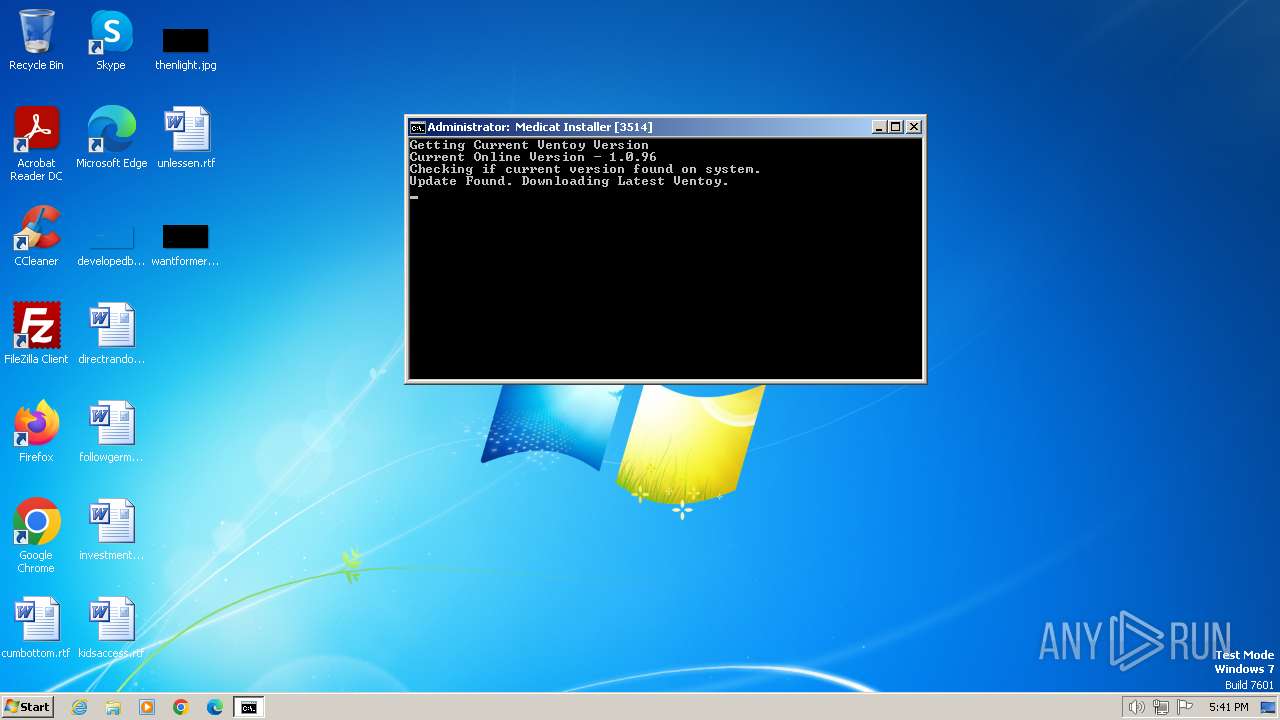
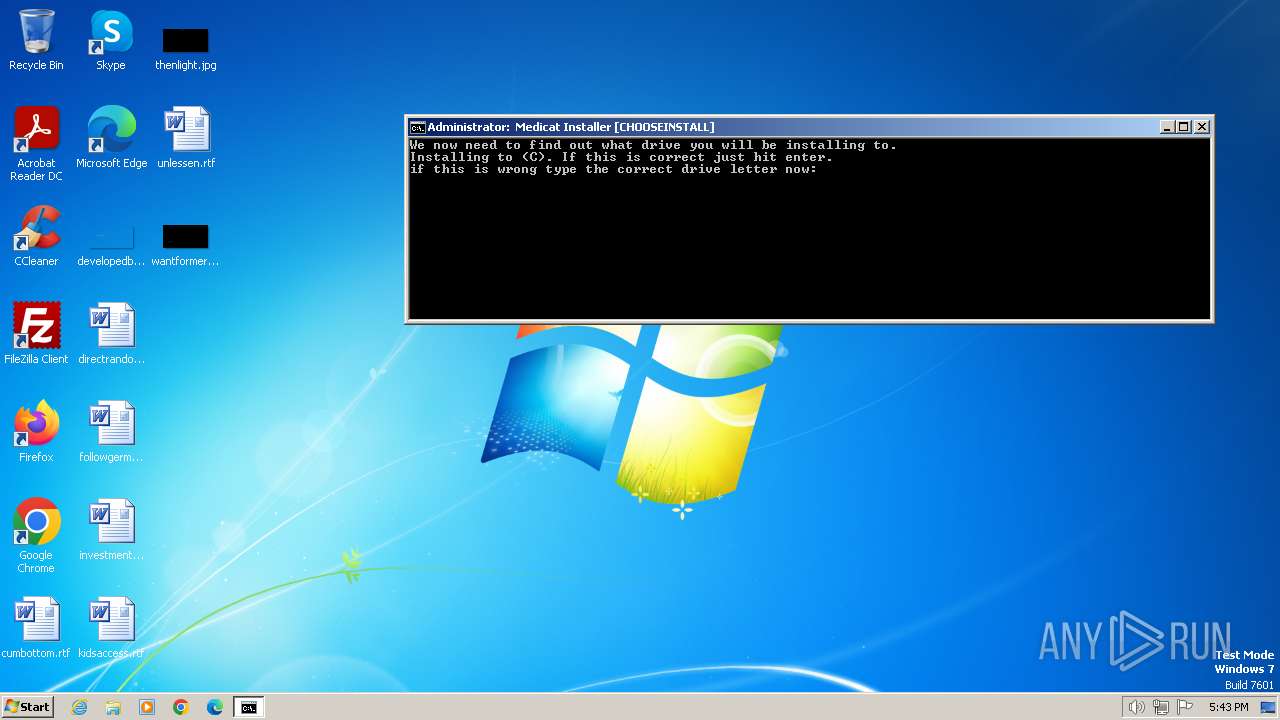
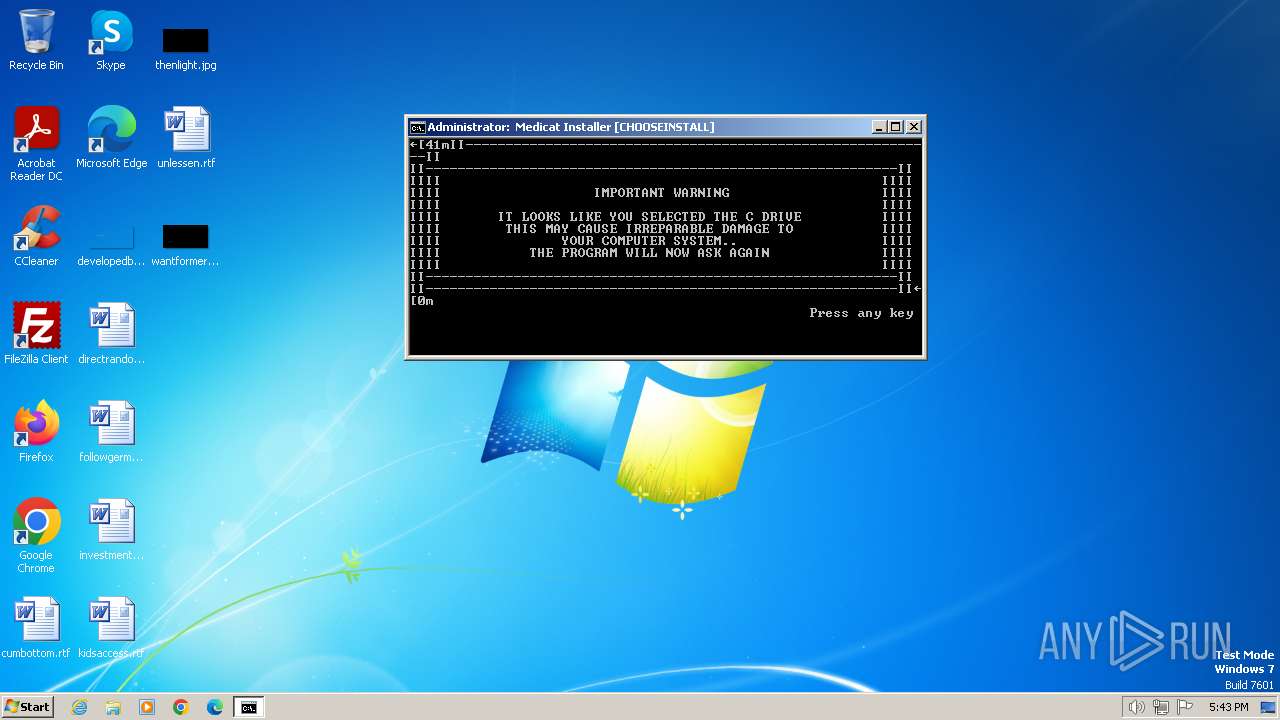
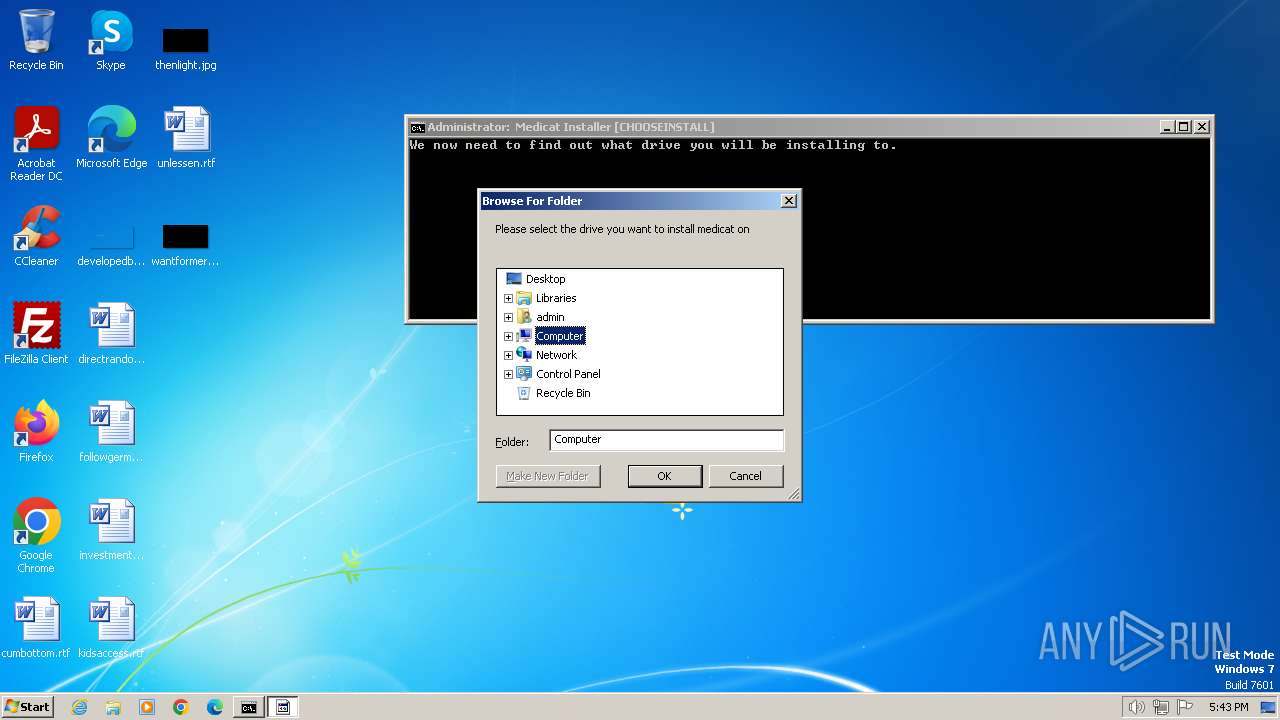
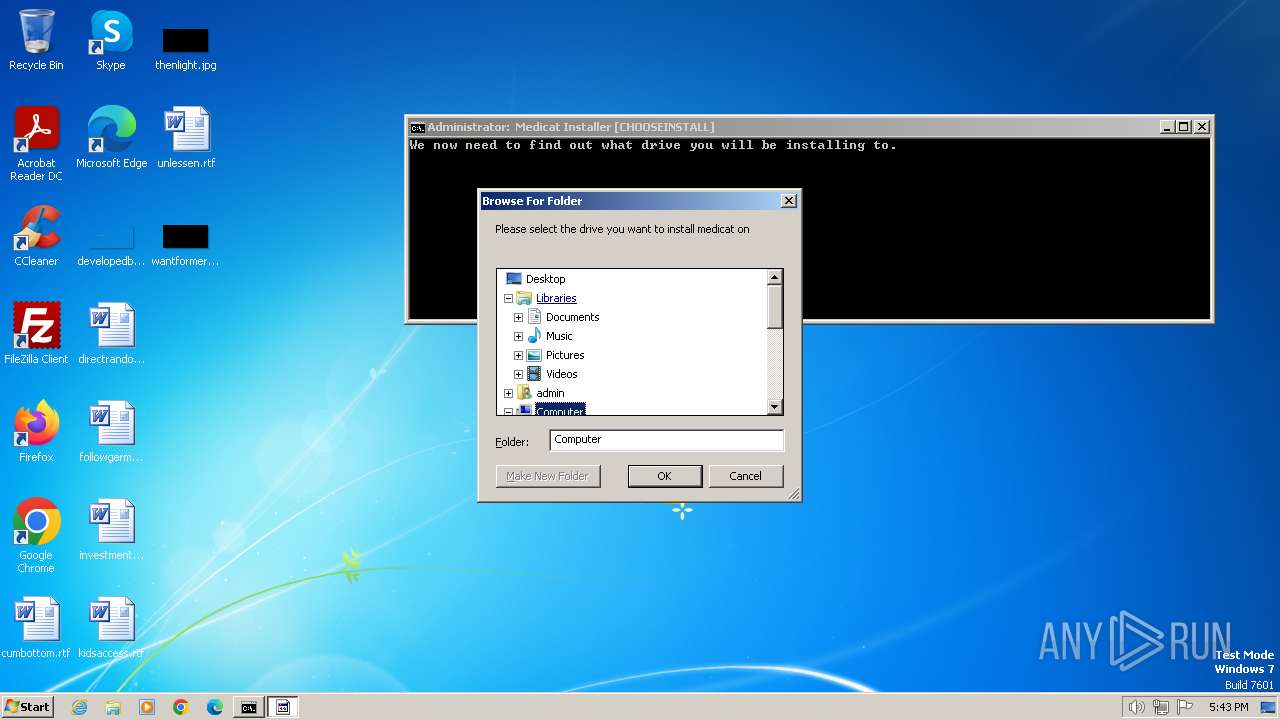
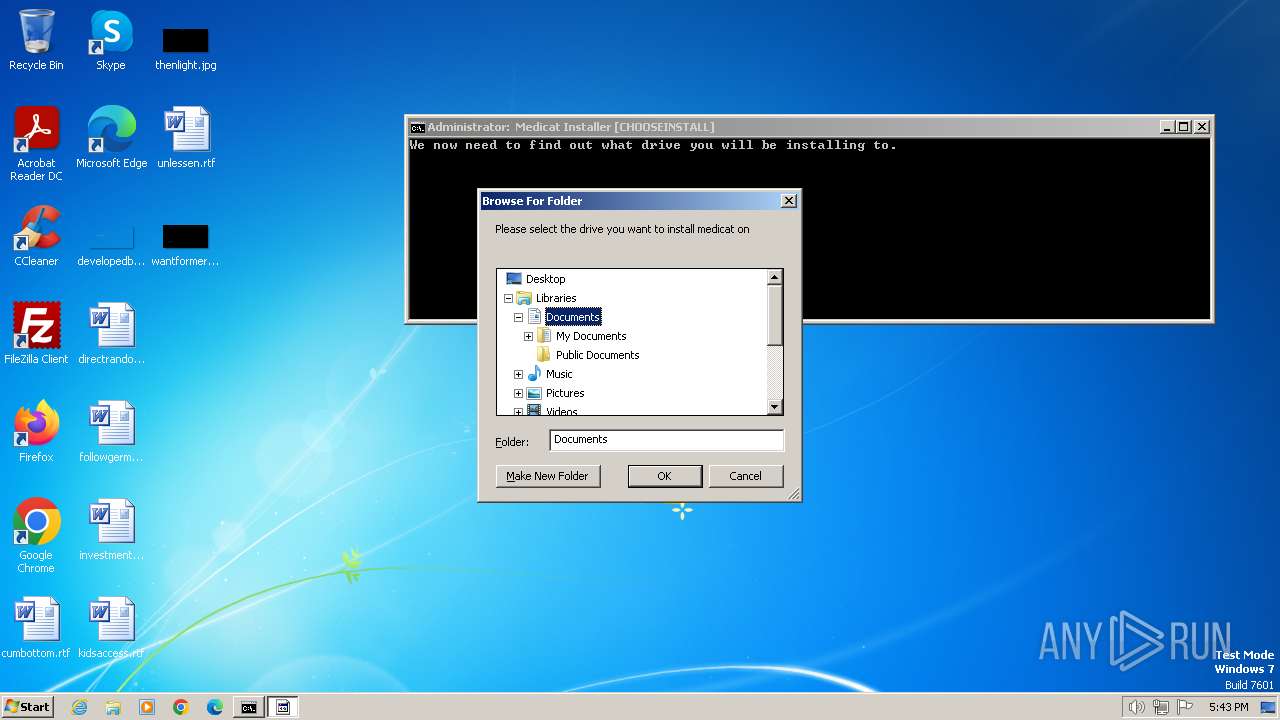
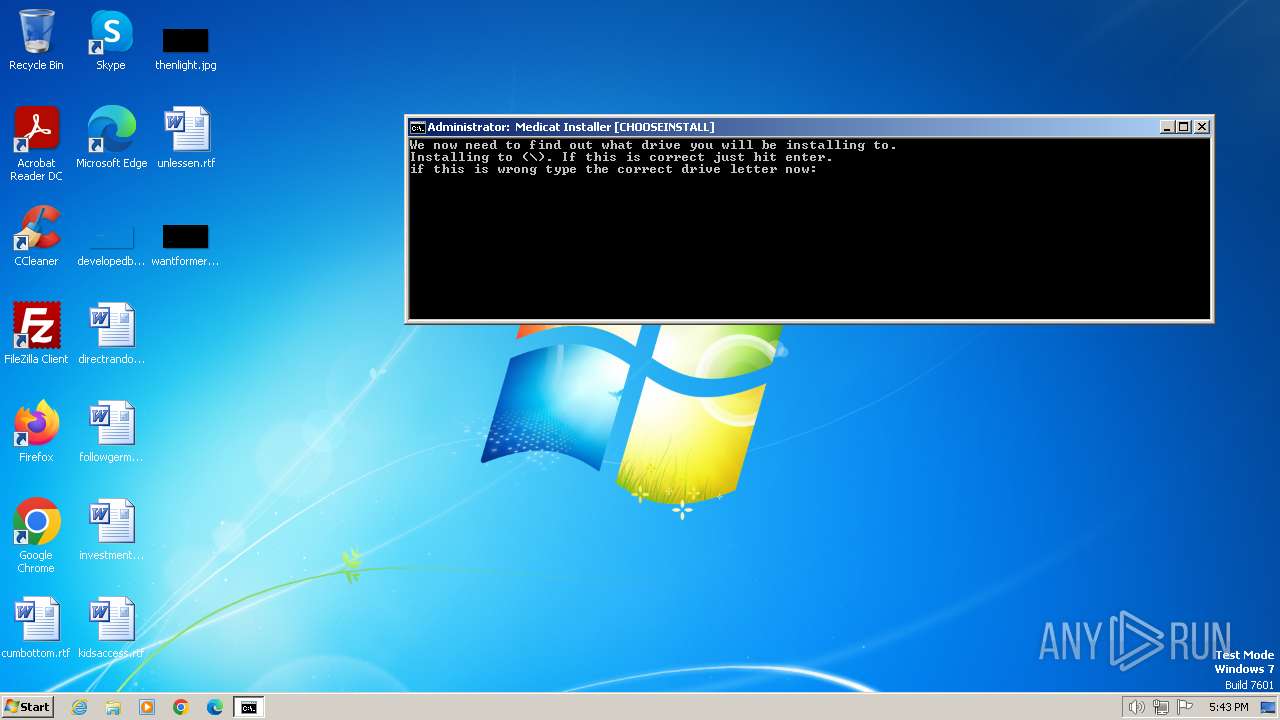
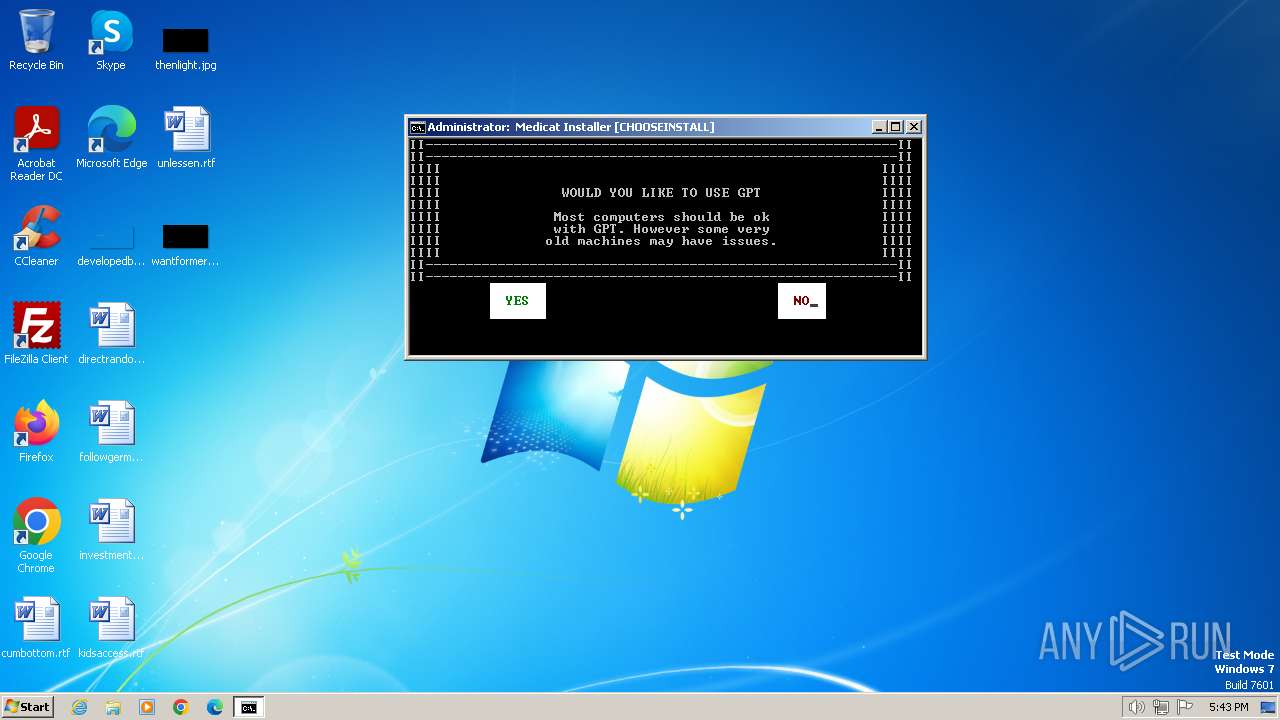
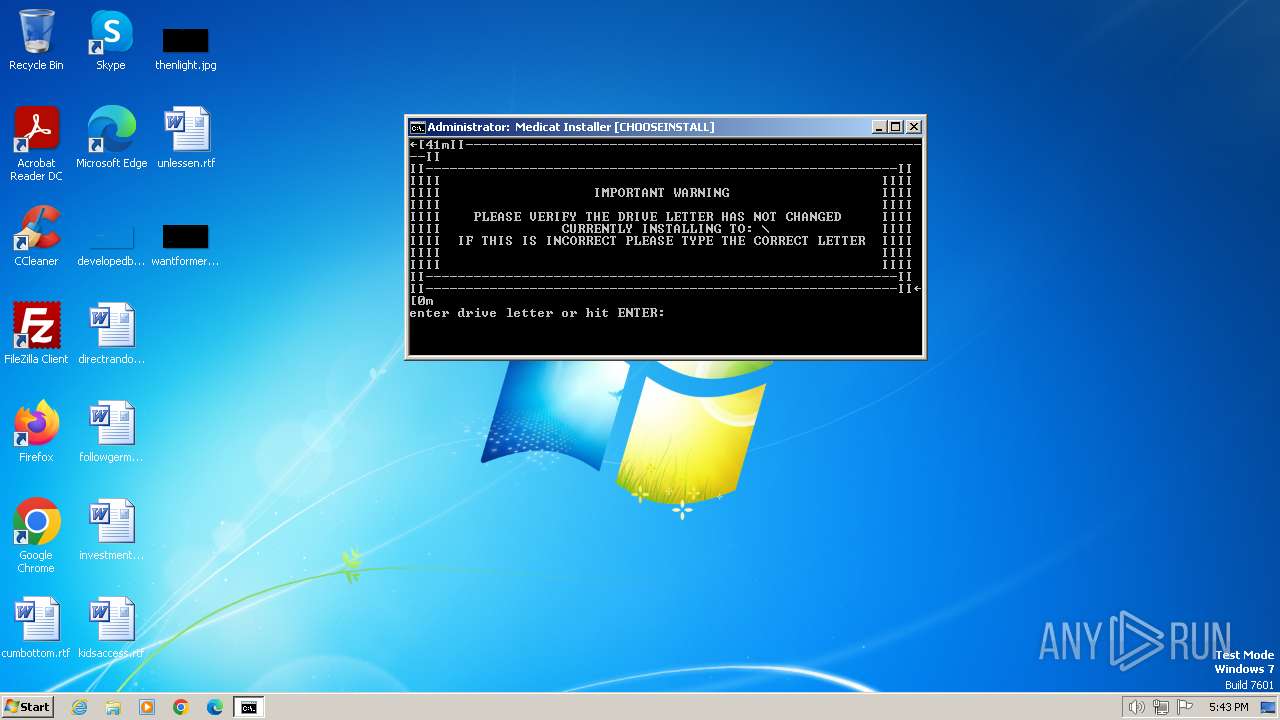
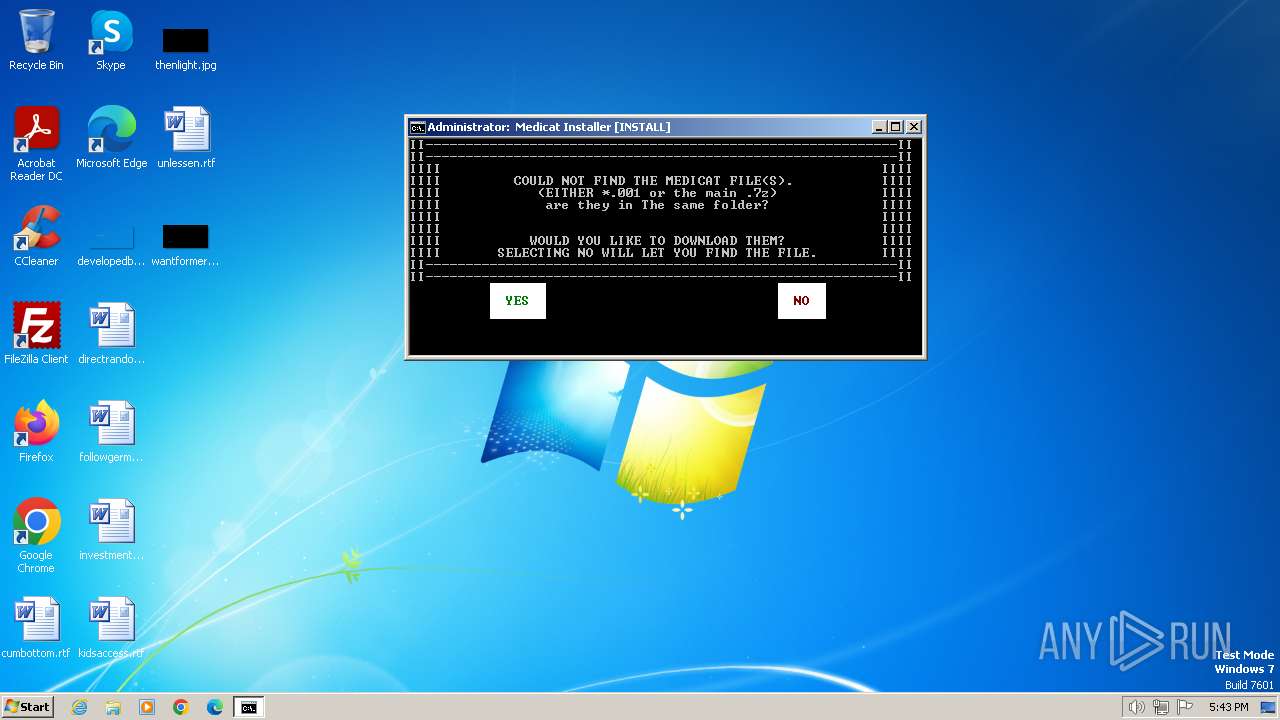
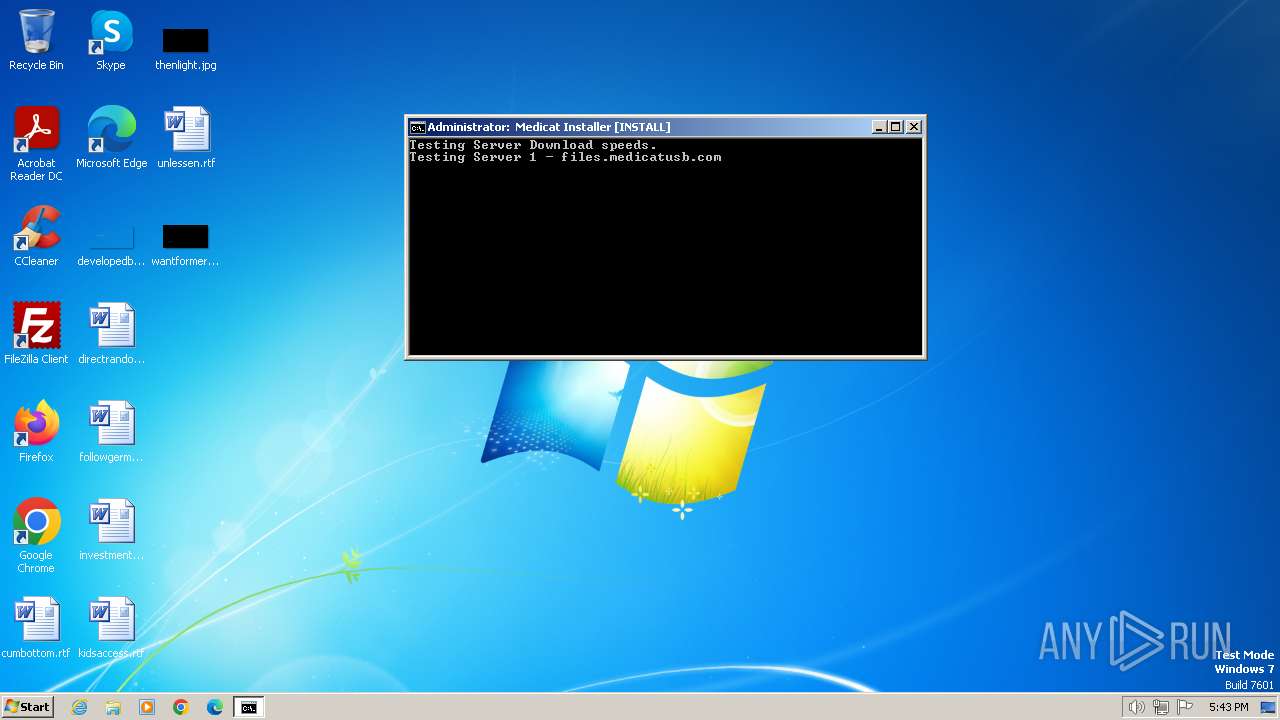
| File name: | Medicat_Installer.bat |
| Full analysis: | https://app.any.run/tasks/15b7b53b-49fb-40da-aca6-2add737bc7a7 |
| Verdict: | Malicious activity |
| Threats: | SystemBC is a Remote Access Trojan (RAT) that can hide communication with the Command and Control server, and deposit other malware strains. |
| Analysis date: | January 02, 2024, 17:39:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with escape sequences |
| MD5: | 683E28700D3CA10C0D7AFE54D35B390F |
| SHA1: | D546C4E64094684545D1000F594B8E03938F3D63 |
| SHA256: | CC3DFB8D5E6041F86784A87EAD4E24E616DBF092A1D5882271BA5804FF343F25 |
| SSDEEP: | 192:NMCY3UbaLF13a7EJIZOTBzmkuEYb+oMGR3EUgXLcHgKjiqNrF8rzGF86kWyz5BVV:nY3KaLxBzmk4cANAEPpNe1+r2tb |
MALICIOUS
SYSTEMBC has been detected (YARA)
- curl.exe (PID: 2472)
- curl.exe (PID: 3696)
- curl.exe (PID: 956)
Changes powershell execution policy (RemoteSigned)
- cmd.exe (PID: 1832)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 116)
- cmd.exe (PID: 1832)
- powershell.exe (PID: 2020)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 116)
- cmd.exe (PID: 1832)
Reads the Internet Settings
- powershell.exe (PID: 2020)
- powershell.exe (PID: 2336)
- powershell.exe (PID: 2548)
- powershell.exe (PID: 2852)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 3260)
- powershell.exe (PID: 3360)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1832)
- cmd.exe (PID: 116)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 1832)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1832)
- cmd.exe (PID: 116)
Download files or web resources using Curl/Wget
- cmd.exe (PID: 1832)
Executing commands from a ".bat" file
- powershell.exe (PID: 2020)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2852)
- powershell.exe (PID: 2548)
The process executes Powershell scripts
- cmd.exe (PID: 1832)
Starts application with an unusual extension
- cmd.exe (PID: 1832)
INFO
Application launched itself
- cmd.exe (PID: 116)
- cmd.exe (PID: 1832)
Checks supported languages
- curl.exe (PID: 2084)
- mode.com (PID: 2248)
- curl.exe (PID: 1636)
- mode.com (PID: 188)
- curl.exe (PID: 2472)
- curl.exe (PID: 1904)
- curl.exe (PID: 2828)
- curl.exe (PID: 1268)
- curl.exe (PID: 2732)
- curl.exe (PID: 2792)
- curl.exe (PID: 2728)
- curl.exe (PID: 2892)
- curl.exe (PID: 2176)
- curl.exe (PID: 2888)
- curl.exe (PID: 1812)
- curl.exe (PID: 2512)
- mode.com (PID: 3000)
- mode.com (PID: 3044)
- mode.com (PID: 3136)
- batbox.exe (PID: 3120)
- batbox.exe (PID: 3008)
- batbox.exe (PID: 604)
- batbox.exe (PID: 3180)
- batbox.exe (PID: 1628)
- curl.exe (PID: 3696)
- mode.com (PID: 1168)
- mode.com (PID: 3764)
- folderbrowse.exe (PID: 4072)
- mode.com (PID: 3812)
- folderbrowse.exe (PID: 840)
- batbox.exe (PID: 296)
- batbox.exe (PID: 2088)
- mode.com (PID: 2408)
- batbox.exe (PID: 2024)
- batbox.exe (PID: 2080)
- batbox.exe (PID: 3004)
- batbox.exe (PID: 1864)
- Ventoy2Disk.exe (PID: 584)
- batbox.exe (PID: 2460)
- mode.com (PID: 392)
- batbox.exe (PID: 1380)
- batbox.exe (PID: 668)
- format.com (PID: 1604)
- batbox.exe (PID: 1044)
- mode.com (PID: 268)
- mode.com (PID: 1652)
- batbox.exe (PID: 2020)
- batbox.exe (PID: 1796)
- curl.exe (PID: 1784)
- batbox.exe (PID: 1792)
- curl.exe (PID: 2308)
- curl.exe (PID: 2296)
- curl.exe (PID: 2384)
- curl.exe (PID: 956)
- 7z.exe (PID: 3852)
Checks operating system version
- cmd.exe (PID: 1832)
The Powershell connects to the Internet
- powershell.exe (PID: 2336)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 3260)
- powershell.exe (PID: 3360)
Reads the computer name
- curl.exe (PID: 2472)
- curl.exe (PID: 1268)
- curl.exe (PID: 1904)
- curl.exe (PID: 2828)
- curl.exe (PID: 2732)
- curl.exe (PID: 2792)
- curl.exe (PID: 2728)
- curl.exe (PID: 2892)
- curl.exe (PID: 1812)
- curl.exe (PID: 2176)
- curl.exe (PID: 2512)
- curl.exe (PID: 3696)
- curl.exe (PID: 2888)
- 7z.exe (PID: 3852)
- folderbrowse.exe (PID: 4072)
- folderbrowse.exe (PID: 840)
- curl.exe (PID: 1784)
- curl.exe (PID: 2308)
- curl.exe (PID: 2296)
- curl.exe (PID: 2384)
- curl.exe (PID: 956)
Unusual connection from system programs
- powershell.exe (PID: 2336)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 3260)
- powershell.exe (PID: 3360)
Drops the executable file immediately after the start
- curl.exe (PID: 2472)
- curl.exe (PID: 2732)
- curl.exe (PID: 2728)
- curl.exe (PID: 2892)
- curl.exe (PID: 2888)
- curl.exe (PID: 2176)
- 7z.exe (PID: 3852)
Create files in a temporary directory
- curl.exe (PID: 1904)
- curl.exe (PID: 2472)
- curl.exe (PID: 1268)
- curl.exe (PID: 2728)
- curl.exe (PID: 2892)
- curl.exe (PID: 2792)
- curl.exe (PID: 2732)
- curl.exe (PID: 2888)
- curl.exe (PID: 2512)
- curl.exe (PID: 2176)
- curl.exe (PID: 1812)
- curl.exe (PID: 2828)
- curl.exe (PID: 3696)
- Ventoy2Disk.exe (PID: 584)
- curl.exe (PID: 1784)
- curl.exe (PID: 2308)
- curl.exe (PID: 2296)
- curl.exe (PID: 2384)
- curl.exe (PID: 956)
- 7z.exe (PID: 3852)
Drops 7-zip archiver for unpacking
- curl.exe (PID: 2888)
- curl.exe (PID: 2176)
The executable file from the user directory is run by the CMD process
- batbox.exe (PID: 3008)
- batbox.exe (PID: 3120)
- batbox.exe (PID: 1628)
- batbox.exe (PID: 2460)
- batbox.exe (PID: 3180)
- batbox.exe (PID: 604)
- GetInput.exe (PID: 3328)
- folderbrowse.exe (PID: 4072)
- folderbrowse.exe (PID: 840)
- 7z.exe (PID: 3852)
- batbox.exe (PID: 296)
- batbox.exe (PID: 2088)
- batbox.exe (PID: 2080)
- GetInput.exe (PID: 2208)
- batbox.exe (PID: 3004)
- batbox.exe (PID: 1864)
- GetInput.exe (PID: 1772)
- Ventoy2Disk.exe (PID: 584)
- batbox.exe (PID: 2024)
- batbox.exe (PID: 1044)
- batbox.exe (PID: 668)
- batbox.exe (PID: 1796)
- GetInput.exe (PID: 1344)
- batbox.exe (PID: 2020)
- batbox.exe (PID: 1380)
- batbox.exe (PID: 1792)
- GetInput.exe (PID: 2172)
Reads the machine GUID from the registry
- folderbrowse.exe (PID: 840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
129
Monitored processes
92
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Medicat_Installer.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 188 | mode con:cols=64 lines=18 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | mode con:cols=64 lines=18 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | batbox /c 0xF2 /g 10 14 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /g 10 13 /a 32 /d " " /a 32 /g 10 12 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /c 0x07 | C:\Users\admin\AppData\Local\Temp\bin\batbox.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 324 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | REG QUERY "HKEY_CURRENT_USER\Control Panel\International" /v "LocaleName" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | mode con:cols=64 lines=18 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | Ventoy2Disk.exe VTOYCLI /I /Drive:\: /NOUSBCheck /GPT | C:\Users\admin\AppData\Local\Temp\Ventoy2Disk\Ventoy2Disk.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Ventoy2Disk Exit code: 1 Version: 1.0.0.3 Modules
| |||||||||||||||
| 604 | Batbox /g 3 3 /c 0xF2 /d "INSTALL MEDICAT" /g 25 3 /c 0x2F /d "TOGGLE DRIVE FORMAT (CURRENTLY Yes)" /g 3 8 /c 0xF9 /d "MEDICAT DISCORD" /g 25 8 /c 0xF9 /d "VISIT SITE" /g 42 8 /c 0xF9 /d "CHECK USB FILES" /c 0x07 | C:\Users\admin\AppData\Local\Temp\bin\batbox.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 668 | batbox /c 0xF4 /g 46 14 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /g 46 13 /a 32 /d " " /a 32 /g 46 12 /a 32 /a 32 /a 32 /a 32 /a 32 /a 32 /c 0x07 | C:\Users\admin\AppData\Local\Temp\bin\batbox.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
21 490
Read events
21 380
Write events
107
Delete events
3
Modification events
| (PID) Process: | (2020) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2020) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2020) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2020) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2336) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2548) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2548) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2548) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2548) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2548) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell |
| Operation: | write | Name: | ExecutionPolicy |
Value: Unrestricted | |||
Executable files
14
Suspicious files
23
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2336 | powershell.exe | C:\Users\admin\AppData\Local\Temp\vfr0bhht.04o.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1268 | curl.exe | C:\Users\admin\AppData\Local\Temp\bin\Box.bat | text | |
MD5:E5CE0008212C431BAACB5B208F2575BD | SHA256:F164716E7B1F98F68F6CE3239345C30B3410ED9812F30B37BB7630F28047EBD9 | |||
| 2828 | curl.exe | C:\Users\admin\AppData\Local\Temp\bin\Button.bat | text | |
MD5:5B727EFF91DE52000CEA8E61694F2A03 | SHA256:03A86F9FCDCCBAA499EA4435434A45178E367639D8FB755C5211F304C70744B5 | |||
| 2020 | powershell.exe | C:\Users\admin\AppData\Local\Temp\vbazol10.2gi.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2020 | powershell.exe | C:\Users\admin\AppData\Local\Temp\3yx301oy.zwm.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2728 | curl.exe | C:\Users\admin\AppData\Local\Temp\bin\batbox.exe | executable | |
MD5:CB4A44BAA20AD26BF74615A7FC515A84 | SHA256:9553BC17FA0FD08E026C1865812B3388E3D5495A5394BBF671E5A8F21C79989A | |||
| 2020 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2472 | curl.exe | C:\Users\admin\AppData\Local\Temp\bin\QuickSFV.exe | executable | |
MD5:4B1D5EC11B2B5DB046233A28DBA73B83 | SHA256:A6371461DA7439F4EF7008ED53331209747CBA960B85C70A902D46451247A29C | |||
| 2512 | curl.exe | C:\Users\admin\AppData\Local\Temp\bin\licence.ps1 | text | |
MD5:B82D701B083CA57E543EB540533B1B1A | SHA256:7BE9BCD4A4FF59E9100B2453AB1D8BCFFD48BF3D4E9A5A57638F0F2386B040B2 | |||
| 2792 | curl.exe | C:\Users\admin\AppData\Local\Temp\bin\Getlen.bat | text | |
MD5:8C1812E76BA7BF09CB87384089A0AB7F | SHA256:83CE5342710A2F2E385A363402661E3426728DD6BCFE9D87E22F2FB858B07BDE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
27
DNS requests
10
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2336 | powershell.exe | 140.82.121.6:443 | api.github.com | GITHUB | US | unknown |
2472 | curl.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
1904 | curl.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
1268 | curl.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2828 | curl.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2732 | curl.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2792 | curl.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.github.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
translate.googleapis.com |
| whitelisted |
github.com |
| shared |
objects.githubusercontent.com |
| shared |
files.medicatusb.com |
| unknown |
mirrors.itrio.xyz |
| unknown |
files.dog |
| unknown |