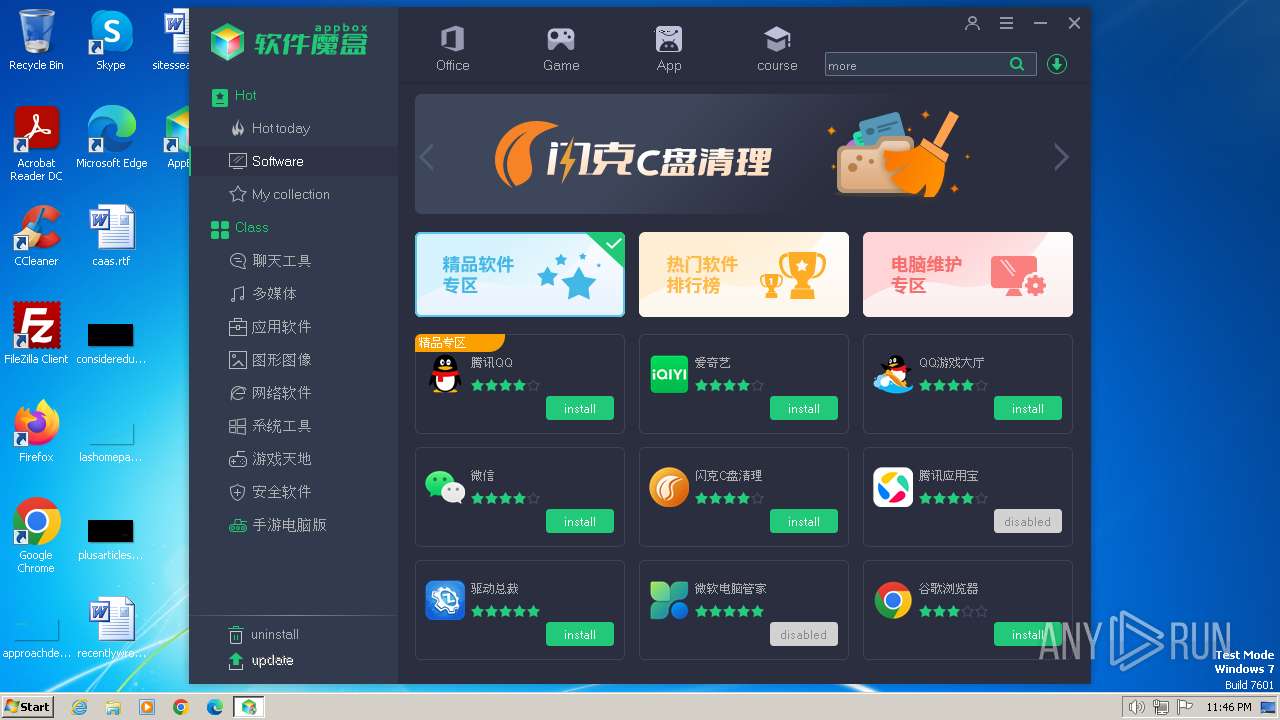
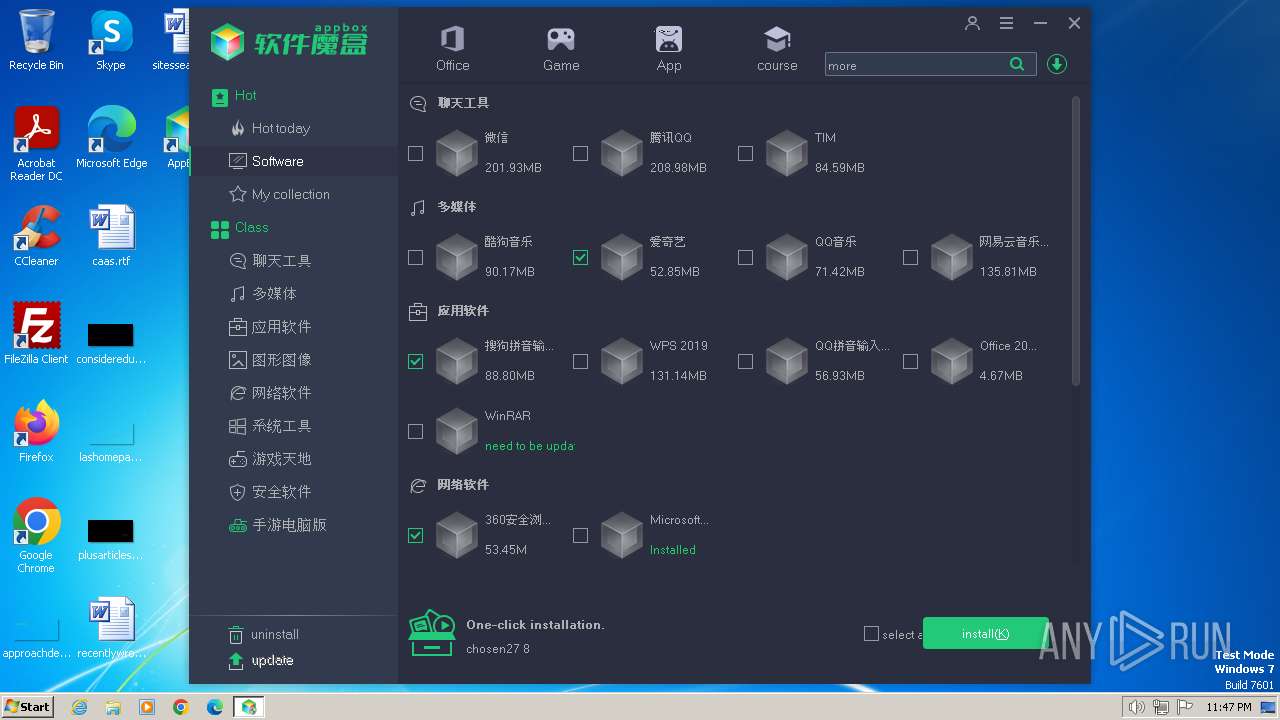
| File name: | mbox.exe |
| Full analysis: | https://app.any.run/tasks/605209e9-f16a-4f78-9557-82a6813febd7 |
| Verdict: | Malicious activity |
| Threats: | Metamorfo is a trojan malware family that has been active since 2018. It remains a top threat, focusing on stealing victims’ financial information, including banking credentials and other data. The malware is known for targeting users in Brazil. |
| Analysis date: | December 18, 2023, 23:45:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 524910187825D4C94AACF496D9515572 |
| SHA1: | B3728A62F0378EE29E1943F82CABCCB00A091B48 |
| SHA256: | CBC53973B5666CA75959AAABD0034016F511C8226821ACCC61C36E3CC0F2555F |
| SSDEEP: | 98304:s0gU5jeW3lzQm6+OI8zJYWuduI5XEXWNb/AM8Uoqqzcq+AtUpkeuVrHz9pajjAFv:I8UOR6KTgXNhq3+/D7X45Z8I6 |
MALICIOUS
Drops the executable file immediately after the start
- mbox.exe (PID: 1072)
- mbox.exe (PID: 316)
- mbox.tmp (PID: 480)
METAMORFO has been detected (YARA)
- AppBox.exe (PID: 696)
SUSPICIOUS
Reads the Windows owner or organization settings
- mbox.tmp (PID: 480)
Drops 7-zip archiver for unpacking
- mbox.tmp (PID: 480)
Reads the Internet Settings
- AppBox.exe (PID: 696)
- Counter.exe (PID: 1544)
Reads Microsoft Outlook installation path
- Counter.exe (PID: 1544)
Checks Windows Trust Settings
- Counter.exe (PID: 1544)
Adds/modifies Windows certificates
- Counter.exe (PID: 1544)
Reads Internet Explorer settings
- Counter.exe (PID: 1544)
Reads security settings of Internet Explorer
- Counter.exe (PID: 1544)
Searches for installed software
- AppBox.exe (PID: 696)
Reads settings of System Certificates
- Counter.exe (PID: 1544)
INFO
Create files in a temporary directory
- mbox.exe (PID: 1072)
- mbox.exe (PID: 316)
- mbox.tmp (PID: 480)
Checks supported languages
- mbox.tmp (PID: 1308)
- mbox.exe (PID: 1072)
- mbox.exe (PID: 316)
- mbox.tmp (PID: 480)
- AppBox.exe (PID: 696)
- Counter.exe (PID: 1544)
Reads the computer name
- mbox.tmp (PID: 1308)
- Counter.exe (PID: 1544)
- AppBox.exe (PID: 696)
- mbox.tmp (PID: 480)
Checks proxy server information
- AppBox.exe (PID: 696)
- Counter.exe (PID: 1544)
Creates files in the program directory
- AppBox.exe (PID: 696)
- mbox.tmp (PID: 480)
Creates files or folders in the user directory
- Counter.exe (PID: 1544)
Reads the machine GUID from the registry
- Counter.exe (PID: 1544)
- AppBox.exe (PID: 696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:06:14 15:27:46+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 108032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1181c |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.0.0.30 |
| ProductVersionNumber: | 3.0.0.30 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
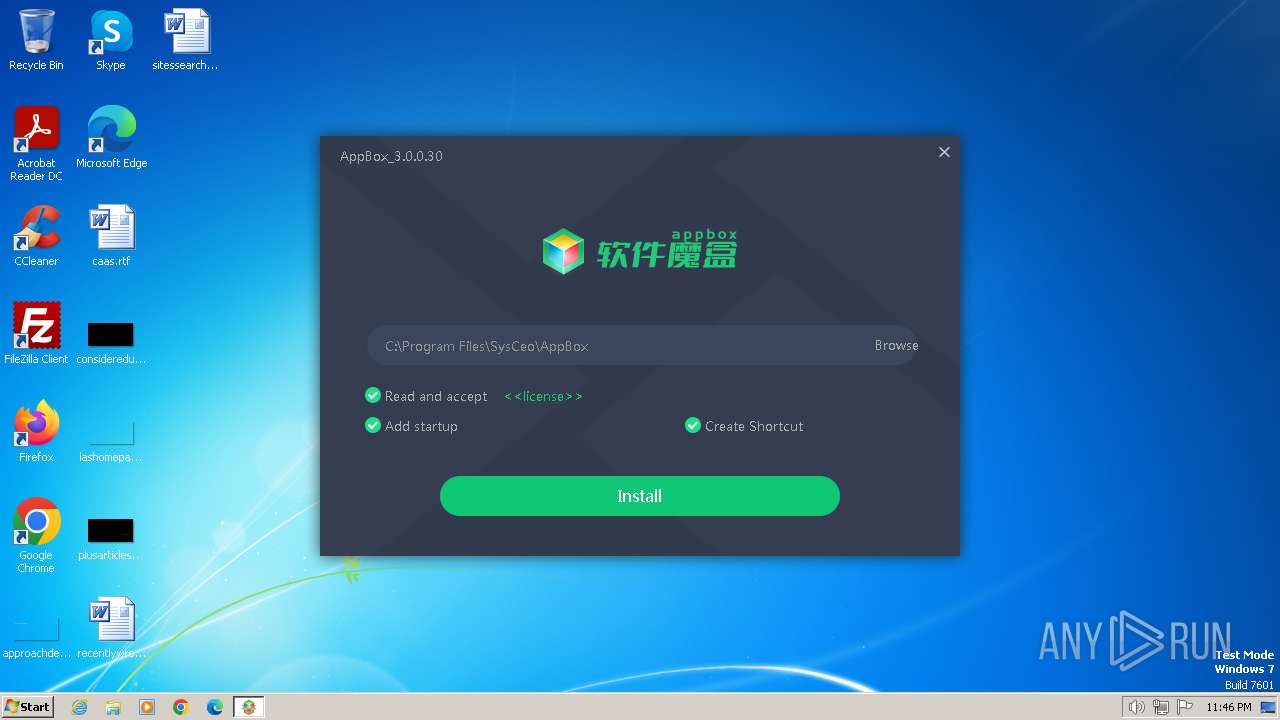
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Sysceo.com |
| FileDescription: | 软件魔盒 |
| FileVersion: | 3.0.0.30 |
| LegalCopyright: | © Jiangmen Eyun Corporation. All rights reserved. |
| ProductName: | |
| ProductVersion: | 3.0.0.30 |
Total processes
44
Monitored processes
6
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Users\admin\AppData\Local\Temp\mbox.exe" /SPAWNWND=$501B2 /NOTIFYWND=$301AA | C:\Users\admin\AppData\Local\Temp\mbox.exe | mbox.tmp | ||||||||||||
User: admin Company: Sysceo.com Integrity Level: HIGH Description: 软件魔盒 Exit code: 0 Version: 3.0.0.30 Modules
| |||||||||||||||
| 480 | "C:\Users\admin\AppData\Local\Temp\is-JCPF2.tmp\mbox.tmp" /SL5="$501AC,15561217,175616,C:\Users\admin\AppData\Local\Temp\mbox.exe" /SPAWNWND=$501B2 /NOTIFYWND=$301AA | C:\Users\admin\AppData\Local\Temp\is-JCPF2.tmp\mbox.tmp | — | mbox.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 696 | "C:\Program Files\SysCeo\AppBox\AppBox.exe" | C:\Program Files\SysCeo\AppBox\AppBox.exe | mbox.tmp | ||||||||||||
User: admin Company: SysCeo.com Integrity Level: HIGH Description: 软件魔盒 Exit code: 0 Version: 3.0.0.30 Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\AppData\Local\Temp\mbox.exe" | C:\Users\admin\AppData\Local\Temp\mbox.exe | — | explorer.exe | |||||||||||
User: admin Company: Sysceo.com Integrity Level: MEDIUM Description: 软件魔盒 Exit code: 0 Version: 3.0.0.30 Modules
| |||||||||||||||
| 1308 | "C:\Users\admin\AppData\Local\Temp\is-SSGT8.tmp\mbox.tmp" /SL5="$301AA,15561217,175616,C:\Users\admin\AppData\Local\Temp\mbox.exe" | C:\Users\admin\AppData\Local\Temp\is-SSGT8.tmp\mbox.tmp | — | mbox.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\SysCeo\AppBox\plug\Counter.exe" /bd | C:\Program Files\SysCeo\AppBox\plug\Counter.exe | AppBox.exe | ||||||||||||
User: admin Company: Sysceo.com Integrity Level: HIGH Description: Counter_BD Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
Total events
7 999
Read events
7 956
Write events
43
Delete events
0
Modification events
| (PID) Process: | (480) mbox.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 115 | |||
| (PID) Process: | (480) mbox.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 116 | |||
| (PID) Process: | (480) mbox.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 117 | |||
| (PID) Process: | (696) AppBox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (696) AppBox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1544) Counter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1544) Counter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1544) Counter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1544) Counter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1544) Counter.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
32
Suspicious files
21
Text files
509
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | mbox.exe | C:\Users\admin\AppData\Local\Temp\is-SSGT8.tmp\mbox.tmp | executable | |
MD5:8D69B52373F6F4CCB684A509C49FEBA2 | SHA256:BB116A02F2AB7129754F9C5AFCF5C45CBF2AE4FDFCF7F3B5240EC49A6812E702 | |||
| 480 | mbox.tmp | C:\Users\admin\AppData\Local\Temp\is-AJVTI.tmp\CheckBox.png | image | |
MD5:2F3AB30C9E89340FDAC31FCD3780E12F | SHA256:455A65939885949F04E6CBE083F9786DE5EDD0EC07242CF1C8F876131609F561 | |||
| 480 | mbox.tmp | C:\Users\admin\AppData\Local\Temp\is-AJVTI.tmp\probar_bg.png | image | |
MD5:70BEAE0D4790BDB2EAEBCB5204E25FFF | SHA256:509748B15B8B0F2601737D1ABE9491730B1F00572882C1D11D0DE78AFD0A0128 | |||
| 480 | mbox.tmp | C:\Users\admin\AppData\Local\Temp\is-AJVTI.tmp\QuickInstallBtn.png | image | |
MD5:8C7308761B21BFCBAF9197C7DD50E6BD | SHA256:A3A192F748007B5330F6FA8A760CE4C2D4256FD7FAF323124C228DCAA878A589 | |||
| 480 | mbox.tmp | C:\Users\admin\AppData\Local\Temp\is-AJVTI.tmp\MinBtn.png | image | |
MD5:42BB428BCB24D708CEF755EBE360E209 | SHA256:41FF374B0284DACE5AEFA7BA348FA7BC95F46F589F7DD01B7B871BBCD4F02ABF | |||
| 480 | mbox.tmp | C:\Users\admin\AppData\Local\Temp\is-AJVTI.tmp\CloseBtn.png | image | |
MD5:7AB2AD23CB1777E8810277936275A7AB | SHA256:3A6AD0F494F9432B13DC8DDE4564FF7E60C9AC91598D51F293A2234AB700E4A9 | |||
| 480 | mbox.tmp | C:\Users\admin\AppData\Local\Temp\is-AJVTI.tmp\DirEdit.png | image | |
MD5:091F7A66C001B03160F8322C9C8F59F5 | SHA256:C9BD49D39C3EB981E87ECE6E81AAE7F90B531345BC7709265B567A426A4CC6E9 | |||
| 480 | mbox.tmp | C:\Users\admin\AppData\Local\Temp\is-AJVTI.tmp\SetupLogo.png | image | |
MD5:8A38DB0F408310075B3E72824B6BF9BB | SHA256:FF899326CCD7052F5628B5D2C85A98414FE32E77B737135B6E704A67EF4907F4 | |||
| 480 | mbox.tmp | C:\Users\admin\AppData\Local\Temp\is-AJVTI.tmp\install3.png | image | |
MD5:E4DAC53E65E0CA2816A9539C6FE5F2CD | SHA256:A5131E22978632D7AF6534DF09AFD921117AD62FD0F3F31D63FF40044A246B60 | |||
| 480 | mbox.tmp | C:\Users\admin\AppData\Local\Temp\is-AJVTI.tmp\bg.png | image | |
MD5:4007C445781C5F11BD0025CDB68AF7BD | SHA256:0580FBA0CF388125B5D5C07E076D4DD0BFFCB63E66CECB01D1908973309AA49C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
71
TCP/UDP connections
92
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
696 | AppBox.exe | GET | — | 58.218.215.155:80 | http://api.sysceo.net/uploads/20220530/8beff8e9830d5fabc8431b4ef7de4b59.png | unknown | — | — | unknown |
1544 | Counter.exe | GET | 200 | 1.193.146.35:80 | http://tongji.sejai.com/mbox.html | unknown | html | 345 b | unknown |
696 | AppBox.exe | GET | — | 58.218.215.155:80 | http://api.sysceo.net/uploads/20231202/7625501d0c6fffcb40ba0187383f7b01.png | unknown | — | — | unknown |
696 | AppBox.exe | GET | — | 58.218.215.155:80 | http://api.sysceo.net/uploads/20220920/7eb35280d6da4ec927293c4c0ed3e53d.png | unknown | — | — | unknown |
696 | AppBox.exe | GET | — | 58.218.215.155:80 | http://api.sysceo.net/uploads/20221027/049db36f4938ecd406c41edc9e08050b.png | unknown | — | — | unknown |
696 | AppBox.exe | GET | — | 58.218.215.155:80 | http://api.sysceo.net/uploads/20230103/06dcf54c730bb166c25a554a4e49ad44.png | unknown | — | — | unknown |
696 | AppBox.exe | GET | — | 58.218.215.155:80 | http://api.sysceo.net/uploads/20231201/278feb8009e74bd65e73482a1db2f949.png | unknown | — | — | unknown |
1544 | Counter.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | unknown | binary | 1.41 Kb | unknown |
696 | AppBox.exe | GET | — | 58.218.215.155:80 | http://api.sysceo.net/uploads/20220915/ed62d6bbddbe6325579d18bc748dec79.png | unknown | — | — | unknown |
696 | AppBox.exe | GET | — | 58.218.215.155:80 | http://api.sysceo.net/uploads/20220420/0dbb9fda1213ea5bba79b1153d8eed8f.png | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
696 | AppBox.exe | 58.218.215.155:443 | api.sysceo.net | Chinanet | CN | unknown |
1544 | Counter.exe | 1.193.146.35:80 | tongji.sejai.com | Henan Luoyang IDC | CN | unknown |
1544 | Counter.exe | 103.235.46.191:443 | hm.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | unknown |
696 | AppBox.exe | 58.218.215.155:80 | api.sysceo.net | Chinanet | CN | unknown |
1544 | Counter.exe | 104.18.20.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
1544 | Counter.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.sysceo.net |
| unknown |
tongji.sejai.com |
| unknown |
hm.baidu.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |