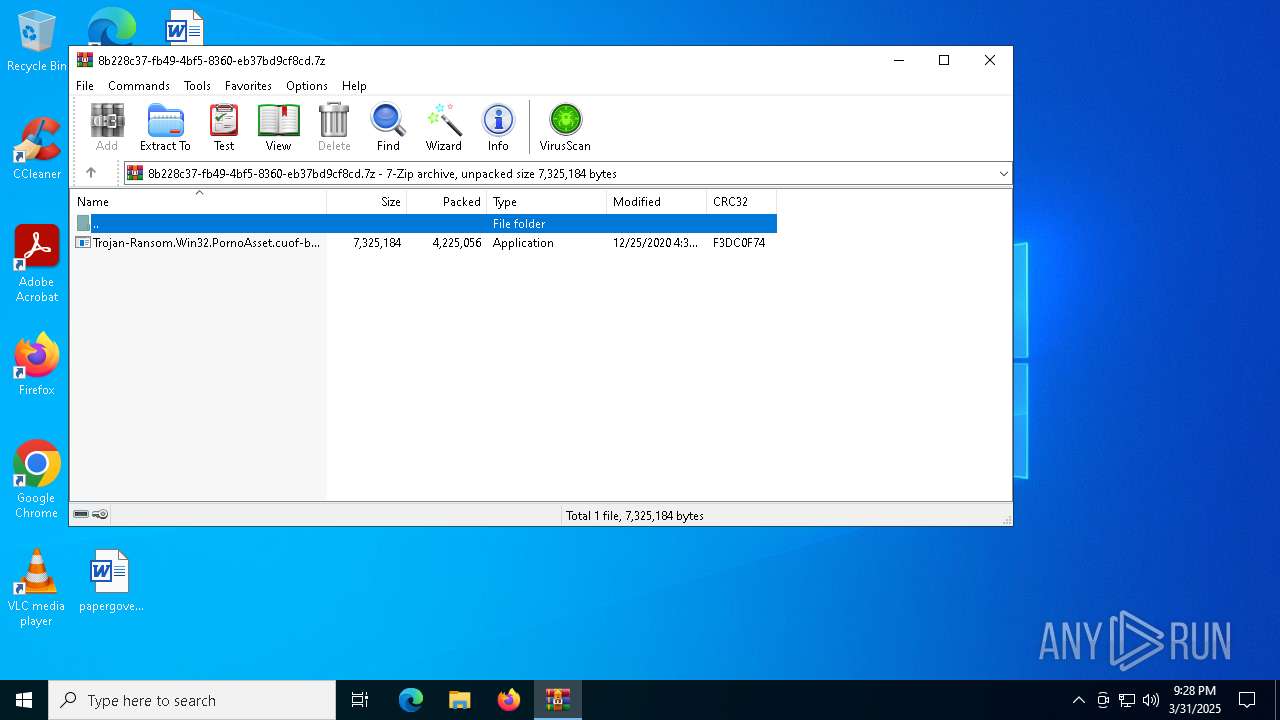
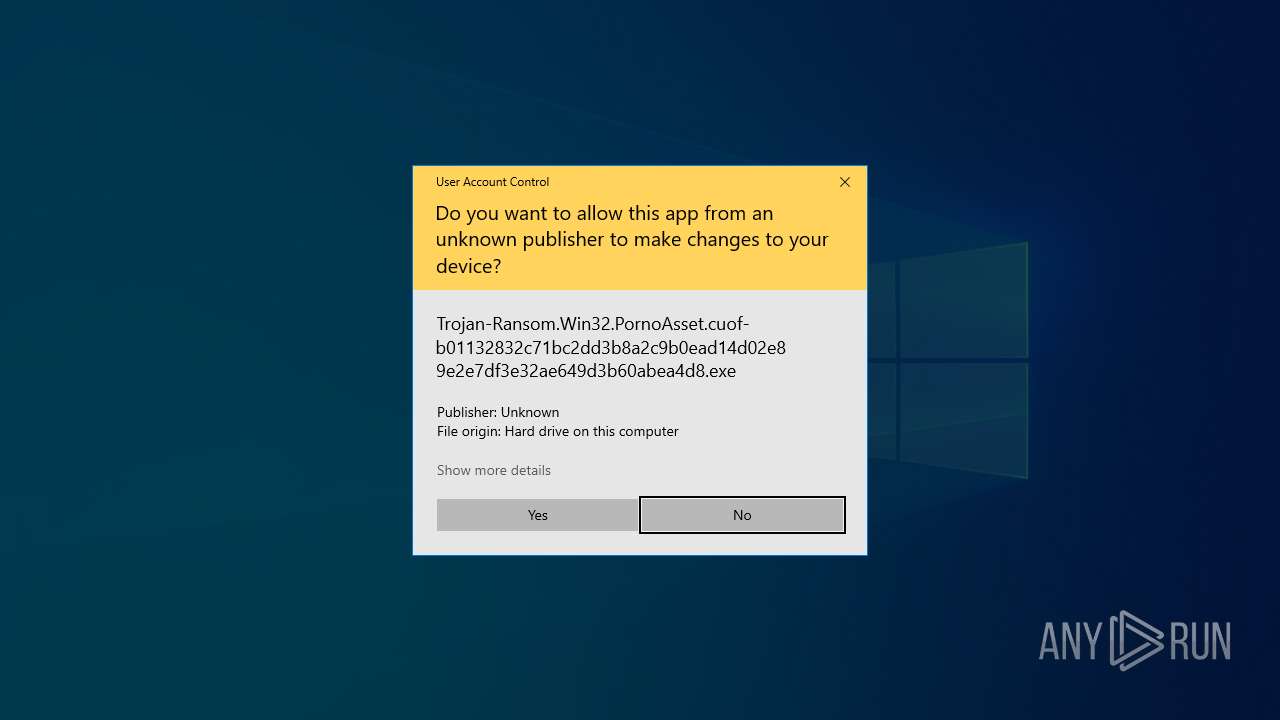
| File name: | Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.7z |
| Full analysis: | https://app.any.run/tasks/8b228c37-fb49-4bf5-8360-eb37bd9cf8cd |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | March 31, 2025, 21:28:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 57D132E4304DBD2B3D28FD0B10DA85A8 |
| SHA1: | 874ECCDE2621C73E39B018D304D88A60D09B1C48 |
| SHA256: | CBB8DABF436705E740C4C06D63E4E4345ED8171333D9159D5DA231E8DE42DB6D |
| SSDEEP: | 98304:lRrS6zfuOP9WglxIpeBvX9sGCYaaTMhC7FPKAGs5hJOrYvg/gNI/APZIjjKPFq9y:Cyx+MbN |
MALICIOUS
Changes image file execution options
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
RHADAMANTHYS has been detected (YARA)
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
SUSPICIOUS
Uses WMIC.EXE to obtain service application data
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Uses TASKKILL.EXE to kill process
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Uses WMIC.EXE to obtain Windows Installer data
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Executes as Windows Service
- KMSService.exe (PID: 4724)
Executable content was dropped or overwritten
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 736)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Reads data from a file (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
The process executes VB scripts
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Changes charset (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 736)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
INFO
Checks supported languages
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
- KMSService.exe (PID: 4724)
- SppExtComObjPatcher.exe (PID: 1096)
Manual execution by a user
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
The sample compiled with english language support
- WinRAR.exe (PID: 6032)
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6032)
Reads the machine GUID from the registry
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
- KMSService.exe (PID: 4724)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5204)
- WMIC.exe (PID: 1628)
- WMIC.exe (PID: 1012)
- cscript.exe (PID: 5400)
- WMIC.exe (PID: 1128)
- WMIC.exe (PID: 5256)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
- WMIC.exe (PID: 2320)
- WMIC.exe (PID: 5404)
- WMIC.exe (PID: 6660)
- WMIC.exe (PID: 5344)
- WMIC.exe (PID: 4212)
- WMIC.exe (PID: 1760)
- WMIC.exe (PID: 5176)
- WMIC.exe (PID: 6676)
- WMIC.exe (PID: 668)
- WMIC.exe (PID: 1912)
- WMIC.exe (PID: 3396)
- cscript.exe (PID: 5776)
Reads the computer name
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
- KMSService.exe (PID: 4724)
Reads Microsoft Office registry keys
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Reads the software policy settings
- cscript.exe (PID: 5400)
- cscript.exe (PID: 4740)
- cscript.exe (PID: 4944)
- cscript.exe (PID: 6372)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 4736)
- cscript.exe (PID: 6824)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 896)
- cscript.exe (PID: 2148)
- cscript.exe (PID: 6268)
- cscript.exe (PID: 7036)
- cscript.exe (PID: 736)
- cscript.exe (PID: 5548)
- cscript.exe (PID: 6752)
- cscript.exe (PID: 5552)
- cscript.exe (PID: 1660)
- cscript.exe (PID: 1180)
- cscript.exe (PID: 5508)
- cscript.exe (PID: 4068)
- cscript.exe (PID: 5776)
- cscript.exe (PID: 6512)
- cscript.exe (PID: 4452)
- cscript.exe (PID: 2980)
- cscript.exe (PID: 5176)
- cscript.exe (PID: 6944)
- cscript.exe (PID: 2420)
- cscript.exe (PID: 5964)
- cscript.exe (PID: 5360)
- cscript.exe (PID: 6256)
Checks proxy server information
- cscript.exe (PID: 5400)
Creates files or folders in the user directory
- cscript.exe (PID: 5400)
VMProtect protector has been detected
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Compiled with Borland Delphi (YARA)
- Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe (PID: 1188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Rhadamanthys
(PID) Process(1188) Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe
C2&VR4!E:j}BxY><
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2020:12:25 16:38:06+00:00 |
| ArchivedFileName: | Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe |
Total processes
238
Monitored processes
106
Malicious processes
31
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | wmic path SoftwareLicensingProduct where ID='3f1afc82-f8ac-4f6c-8005-1d233e606eee' call Activate | C:\Windows\SysWOW64\wbem\WMIC.exe | — | Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 3221549076 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | cscript "C:\Program Files\Microsoft Office\Office16\OSPP.VBS" /inslic:"C:\Program Files\Microsoft Office\root\Licenses16\ProjectProVL_KMS_Client-ppd.xrm-ms" | C:\Windows\SysWOW64\cscript.exe | — | Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | cscript "C:\Program Files\Microsoft Office\Office16\OSPP.VBS" /inslic:"C:\Program Files\Microsoft Office\root\Licenses16\OneNoteVL_KMS_Client-ul.xrm-ms" | C:\Windows\SysWOW64\cscript.exe | — | Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 960 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | wmic path SoftwareLicensingService where version='10.0.19041.3996' call SetKeyManagementServicePort 1688 | C:\Windows\SysWOW64\wbem\WMIC.exe | — | Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | SppExtComObjPatcher.exe C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObjPatcher.exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Integrity Level: SYSTEM Modules
| |||||||||||||||
Total events
102 573
Read events
102 547
Write events
26
Delete events
0
Modification events
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\8b228c37-fb49-4bf5-8360-eb37bd9cf8cd.7z | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
4
Suspicious files
3
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1188 | Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe | C:\Windows\KMSService.exe | executable | |
MD5:1FF5AB4F6F3A3EE4BE333E66181C0525 | SHA256:48108862B5FAE94609F2A7542FD47A945DF49224825FA58A8482433549DC1978 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6032.31551\Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe | executable | |
MD5:D70CA5E28116ABFA668B6ABCC1BD0672 | SHA256:B01132832C71BC2DD3B8A2C9B0EAD14D02E89E2E7DF3E32AE649D3B60ABEA4D8 | |||
| 5400 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:86BEC7A51419CF6F8277608E79B2B807 | SHA256:1AE99C253A484A9CB6814FB52AFD40E347DFE2CD6273E50B245695B87C1BC6E5 | |||
| 5400 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:BEAEE66878FB87A813BA46396FC02A18 | SHA256:734144B21DBB621C7B08E2018B72837B90E398FBEA6202797B2EA51957C47EBF | |||
| 1188 | Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe | C:\Windows\System32\SppExtComObjPatcher.exe | executable | |
MD5:94FEF1EEBF8B9EA06F49D7F8B7814826 | SHA256:E4F6906C800671EB0DD1C10DAC364714902B02FE68CCF6BDB08052BDCDAC2543 | |||
| 5400 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\36AC0BE60E1243344AE145F746D881FE | der | |
MD5:36B0182C996DC13725E0A8DE669E848C | SHA256:84BF6684AB6246B9180C30727191203619FF653F885C7D0C57B1FC638178FD1E | |||
| 1188 | Trojan-Ransom.Win32.PornoAsset.cuof-b01132832c71bc2dd3b8a2c9b0ead14d02e89e2e7df3e32ae649d3b60abea4d8.exe | C:\Windows\System32\SppExtComObjHook.dll | executable | |
MD5:427DB5DDB8196C2229326050D7D2E983 | SHA256:F3CDE32406C79FCCC3446BBF27475F34C887E62AE7320570B906A16E86259059 | |||
| 5400 | cscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:AEB17F45047B4F7446B3D68EE94DD59B | SHA256:D47CFE445343E5DAFBD2520D6334CCE8F45252D5B28E9BF8C81538071909E3C7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
21
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5400 | cscript.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5400 | cscript.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
1328 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1328 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 20.10.31.115:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5400 | cscript.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1328 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1328 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
tongji.227237.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
validation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |