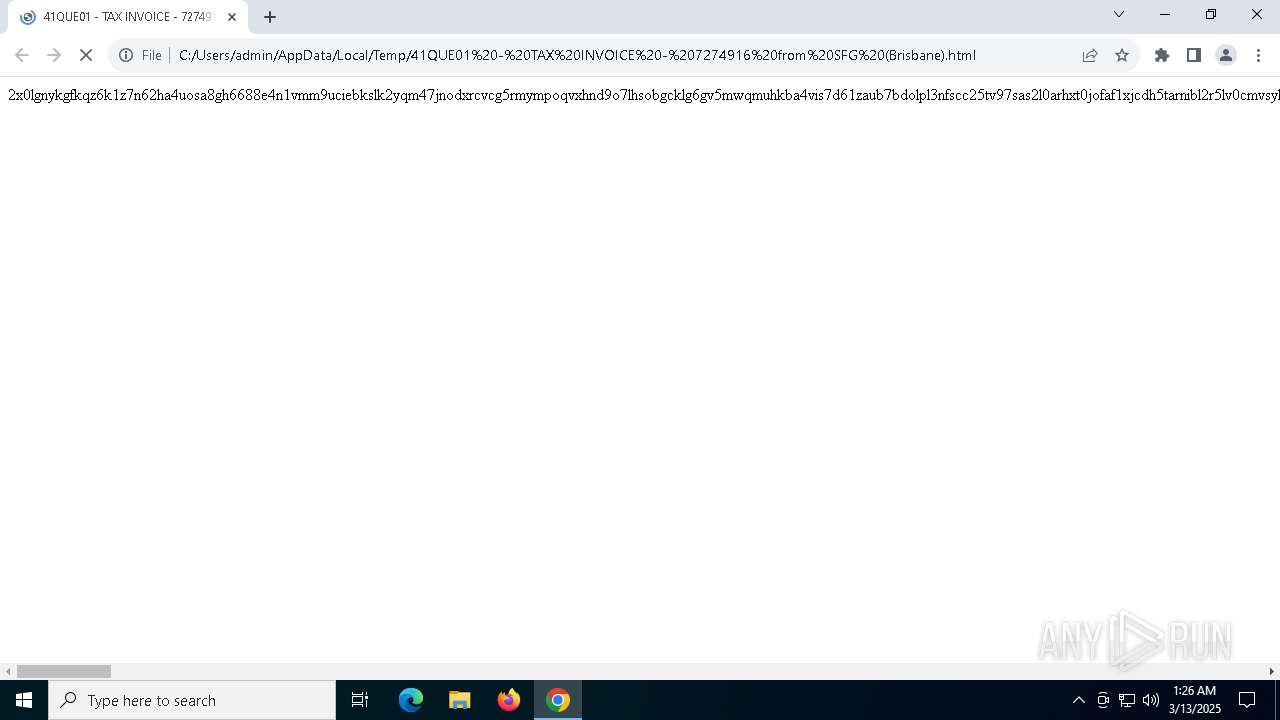
| File name: | 41QUE01 - TAX INVOICE - 7274916 from SFG (Brisbane).html |
| Full analysis: | https://app.any.run/tasks/2b2bdc8d-b8c6-4318-bf5e-fdb6f22b6b5d |
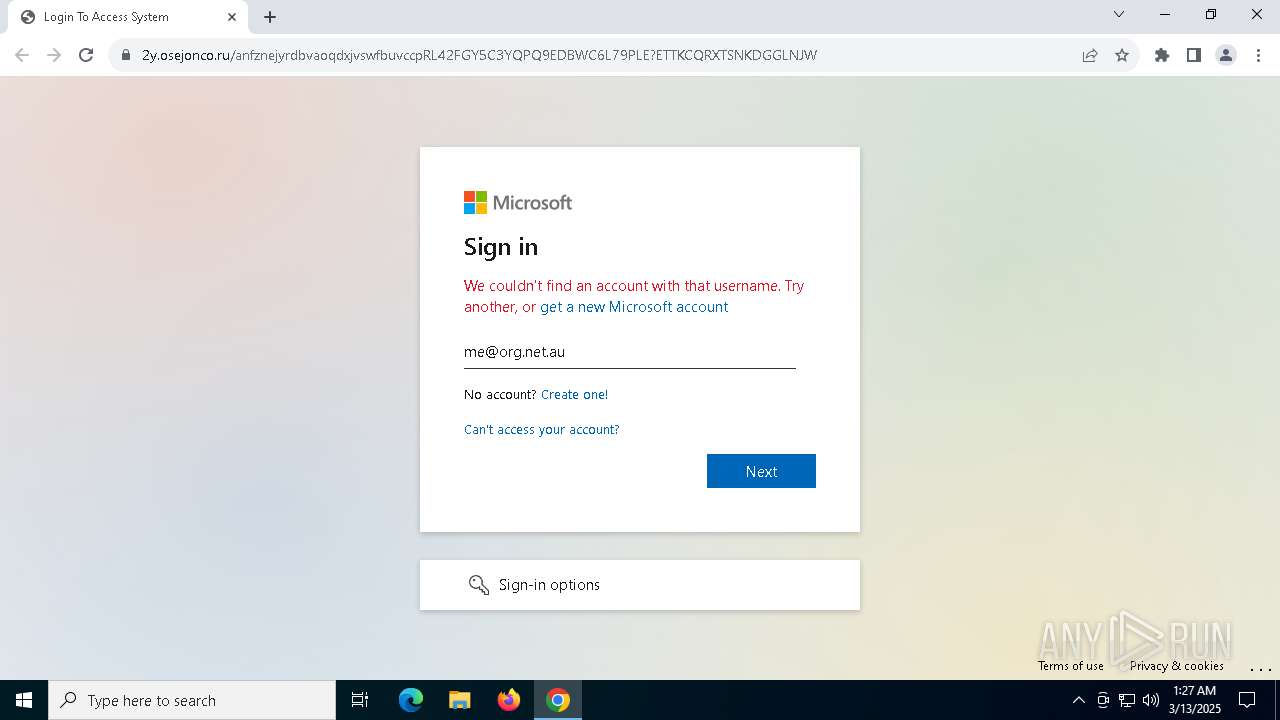
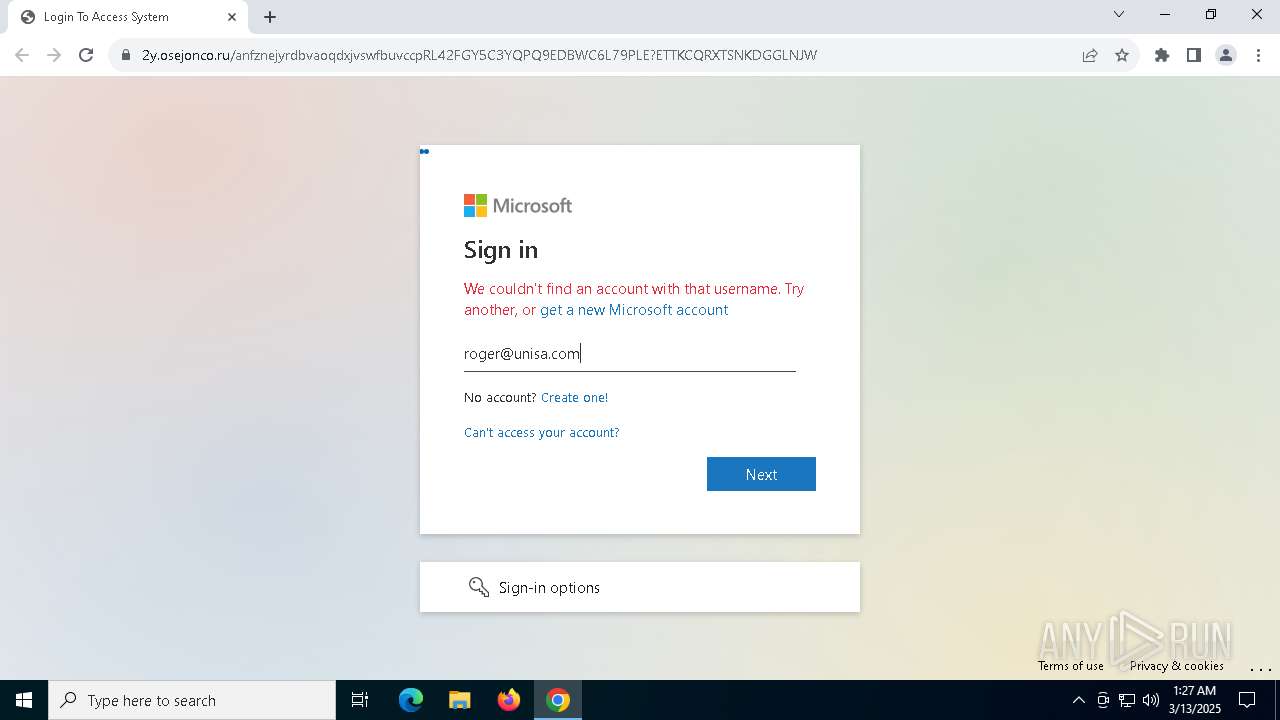
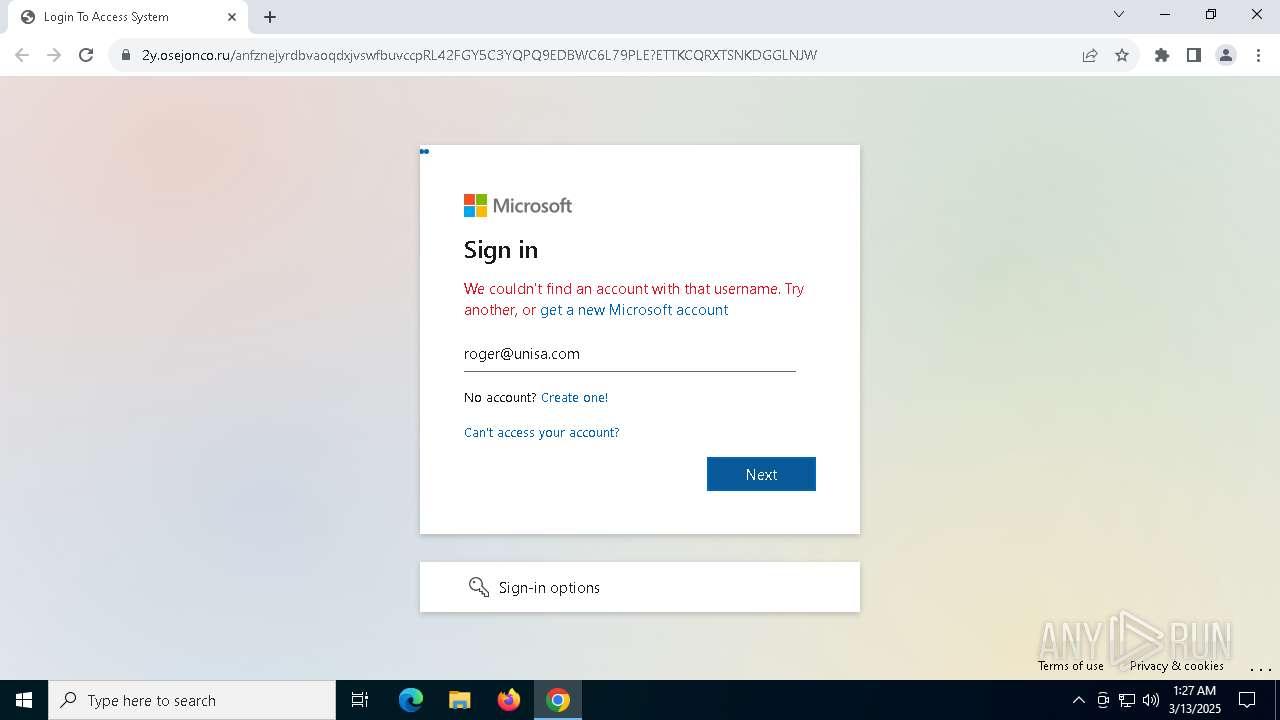
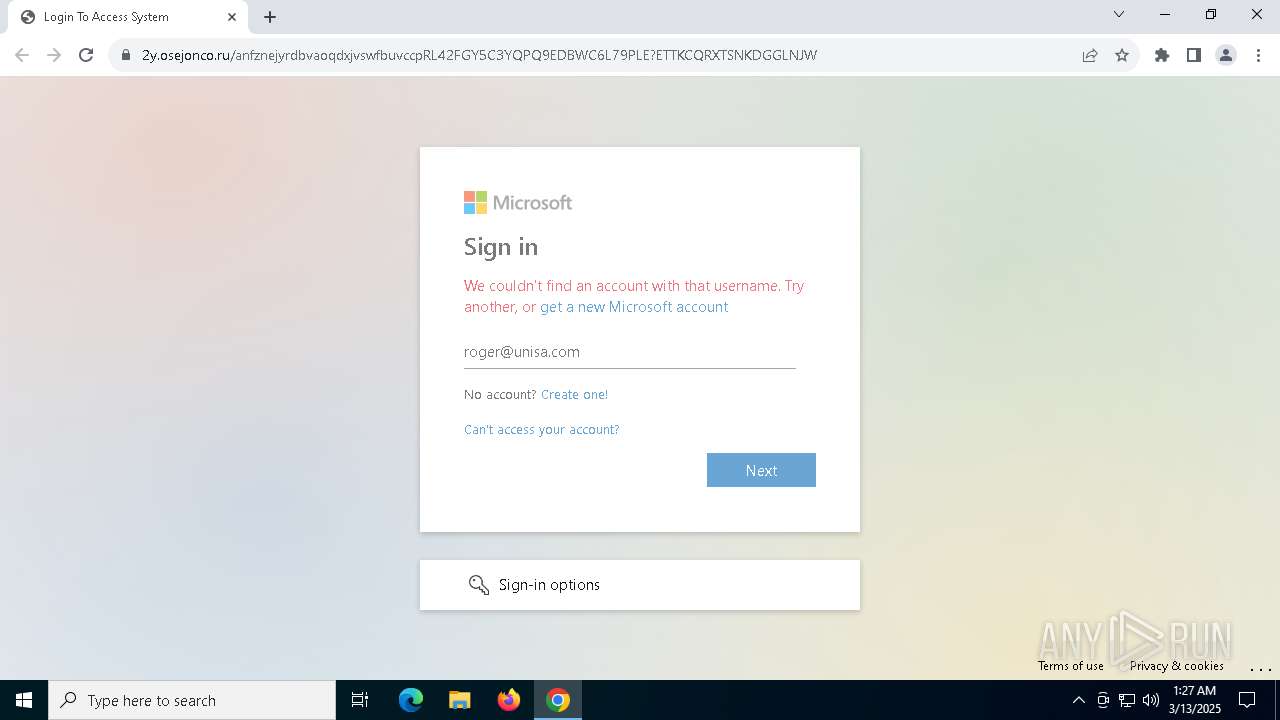
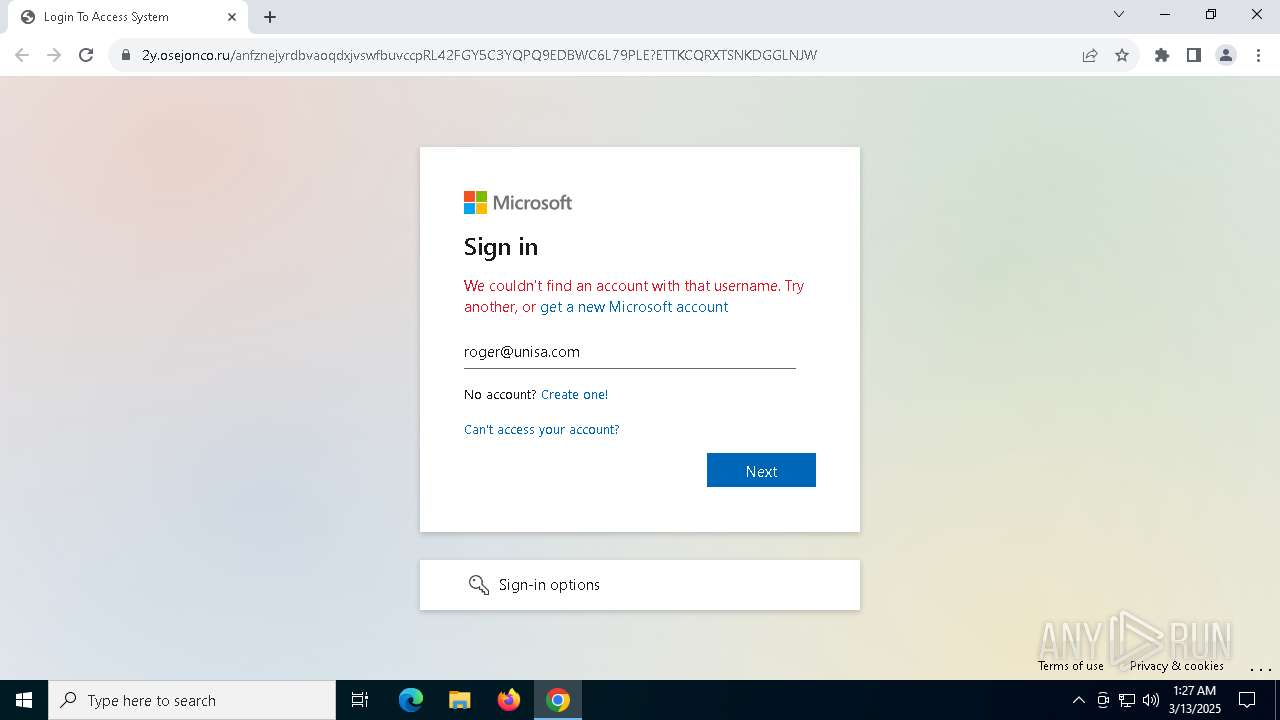
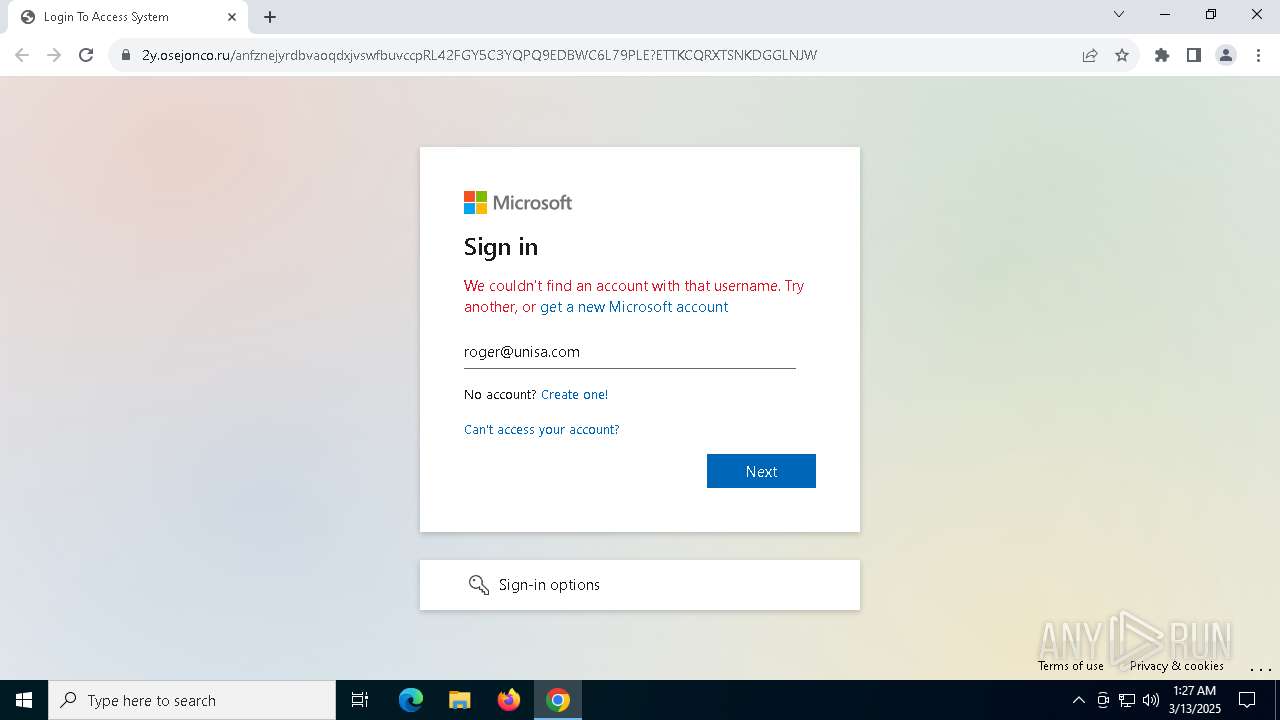
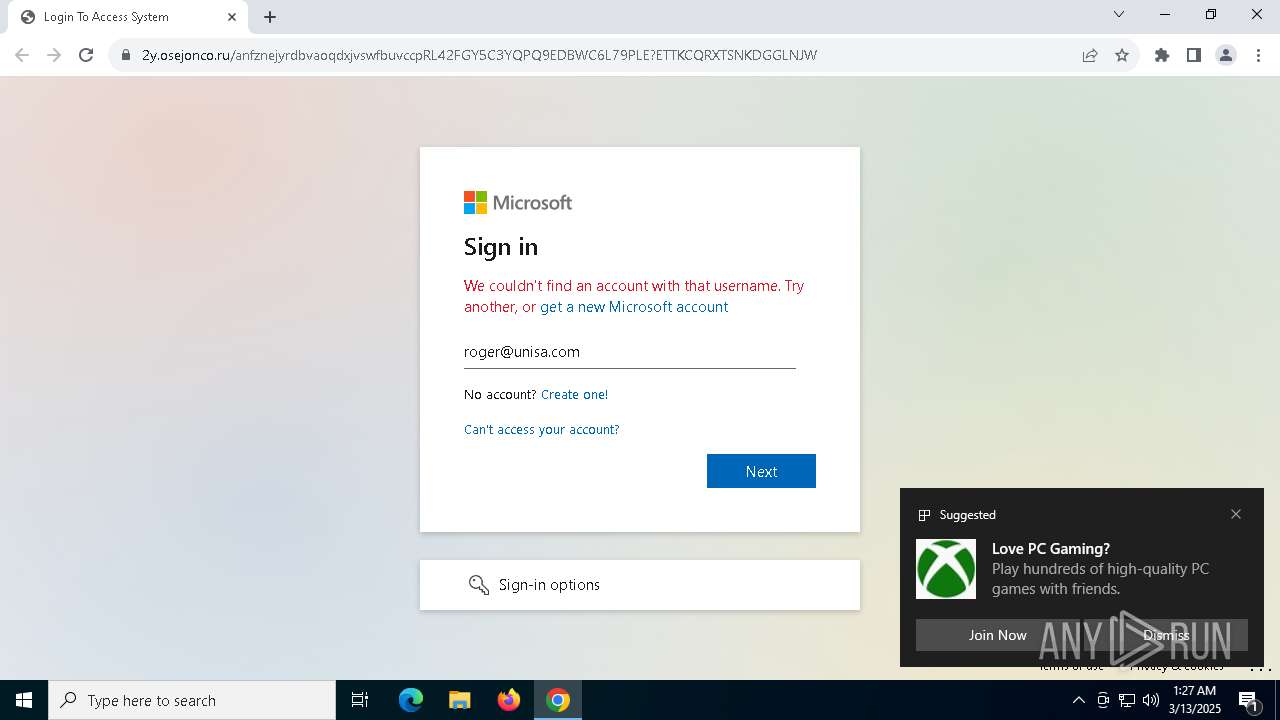
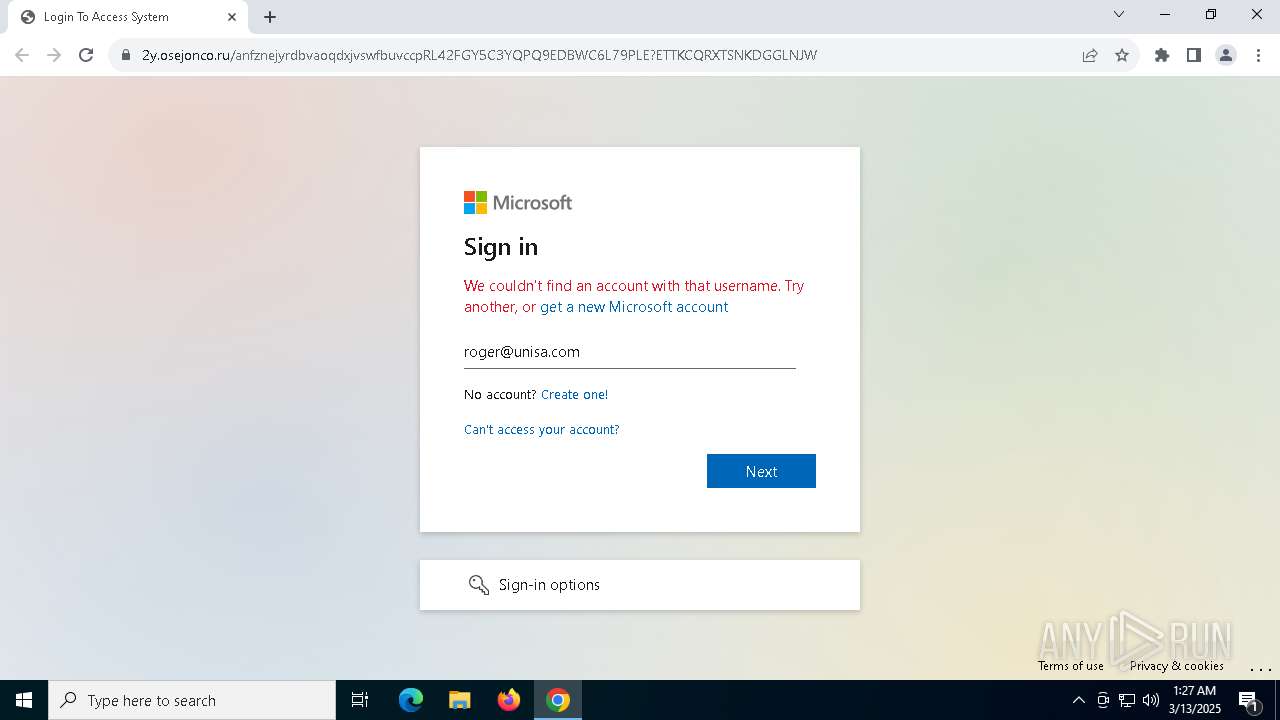
| Verdict: | Malicious activity |
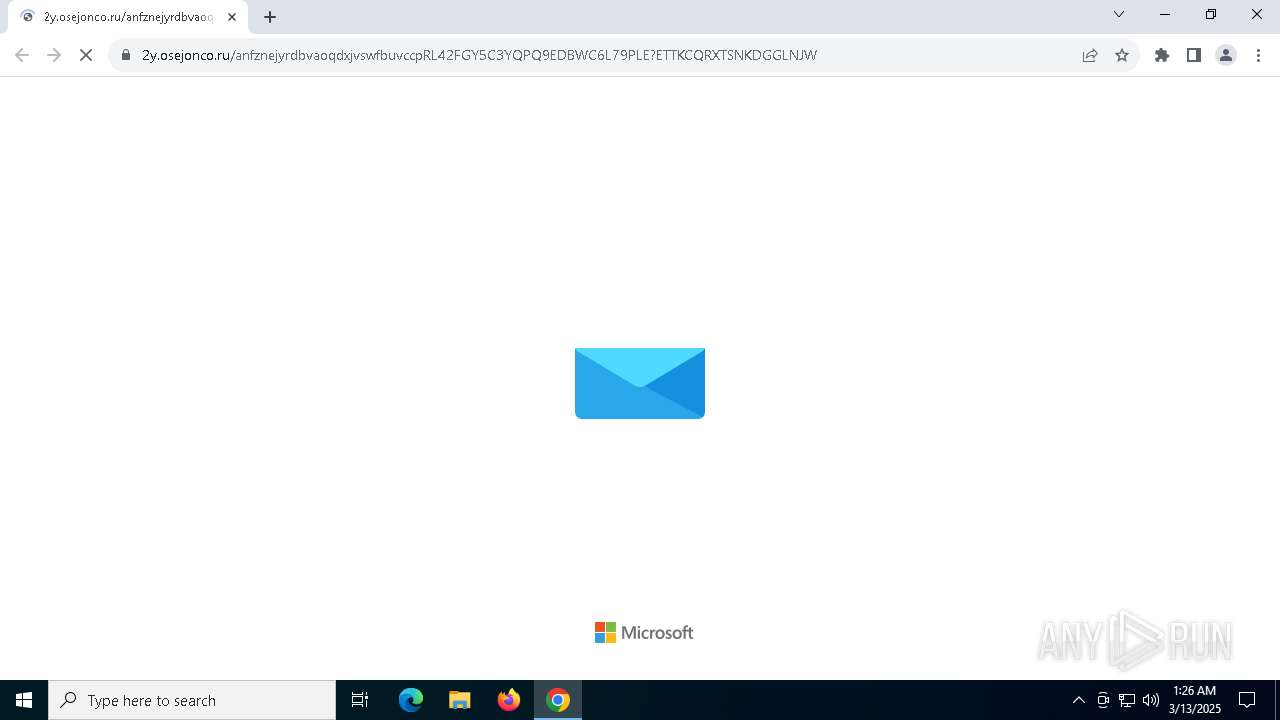
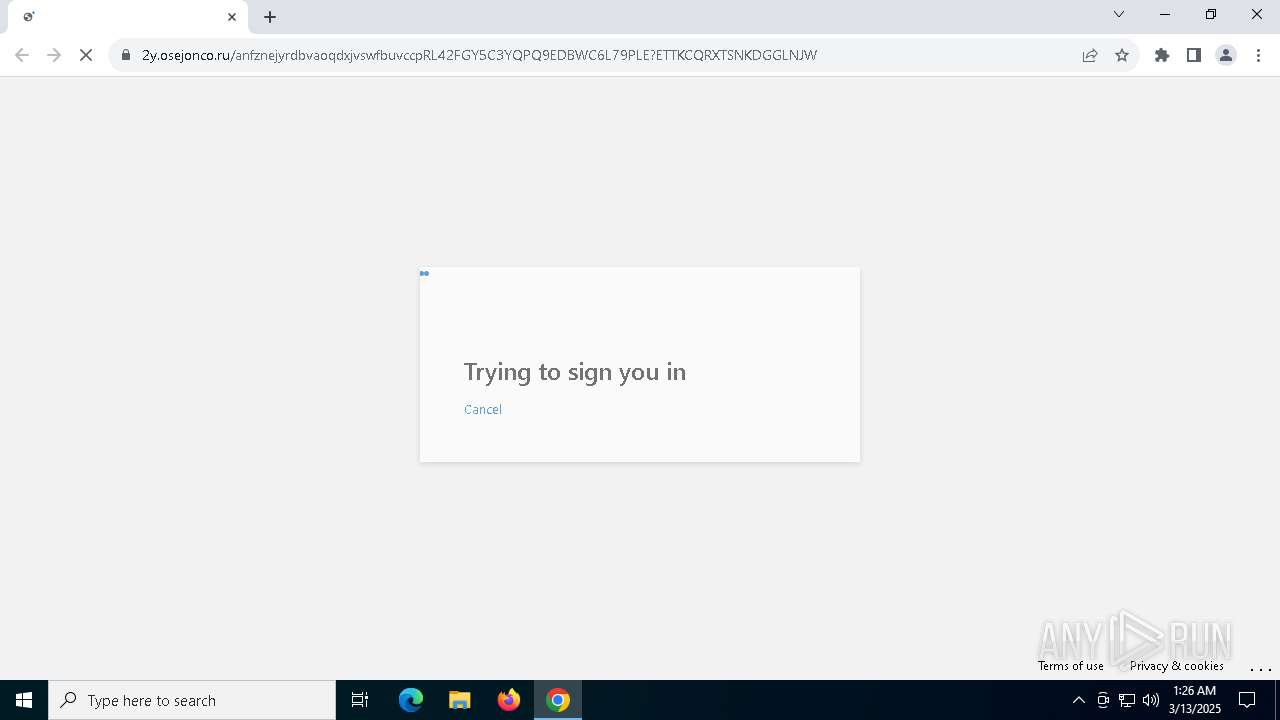
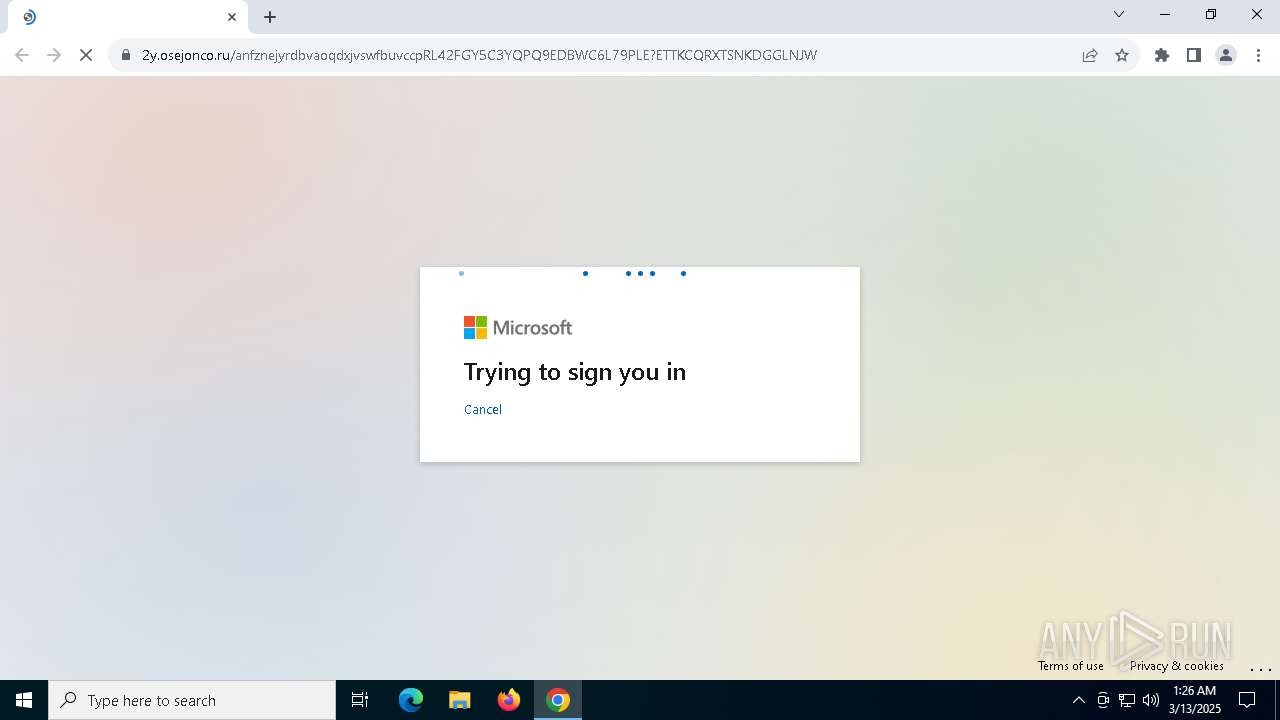
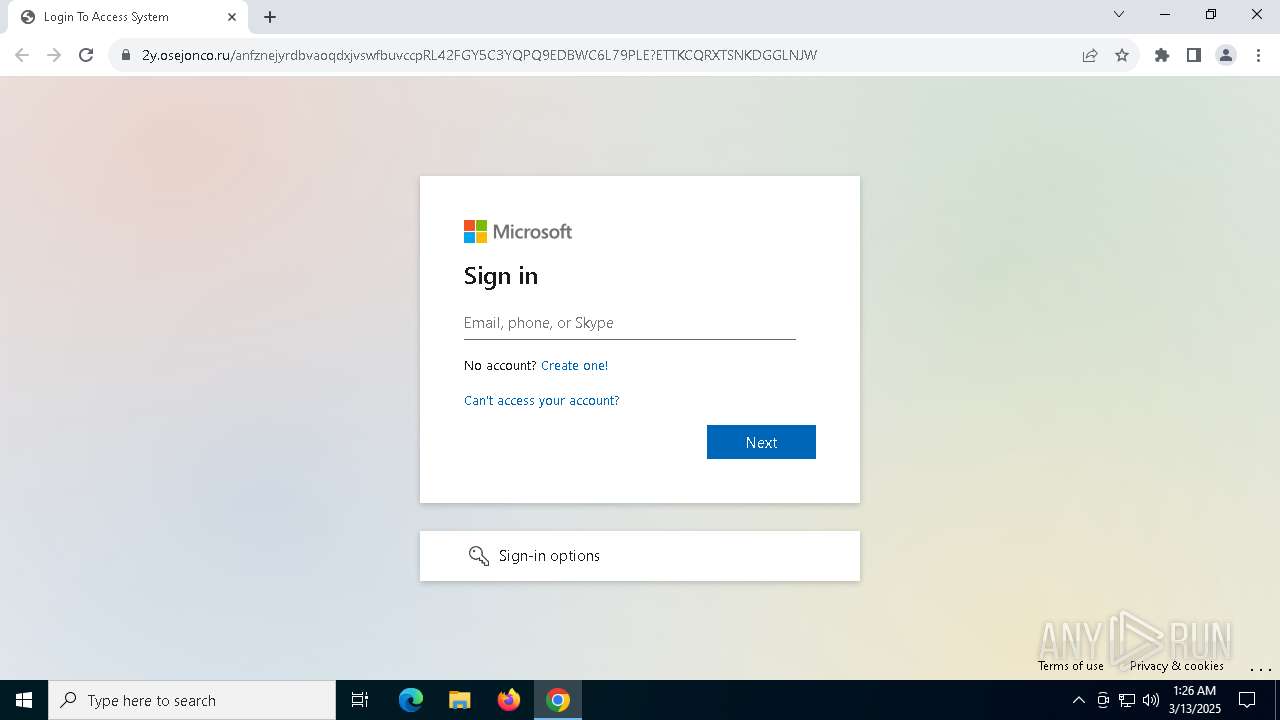
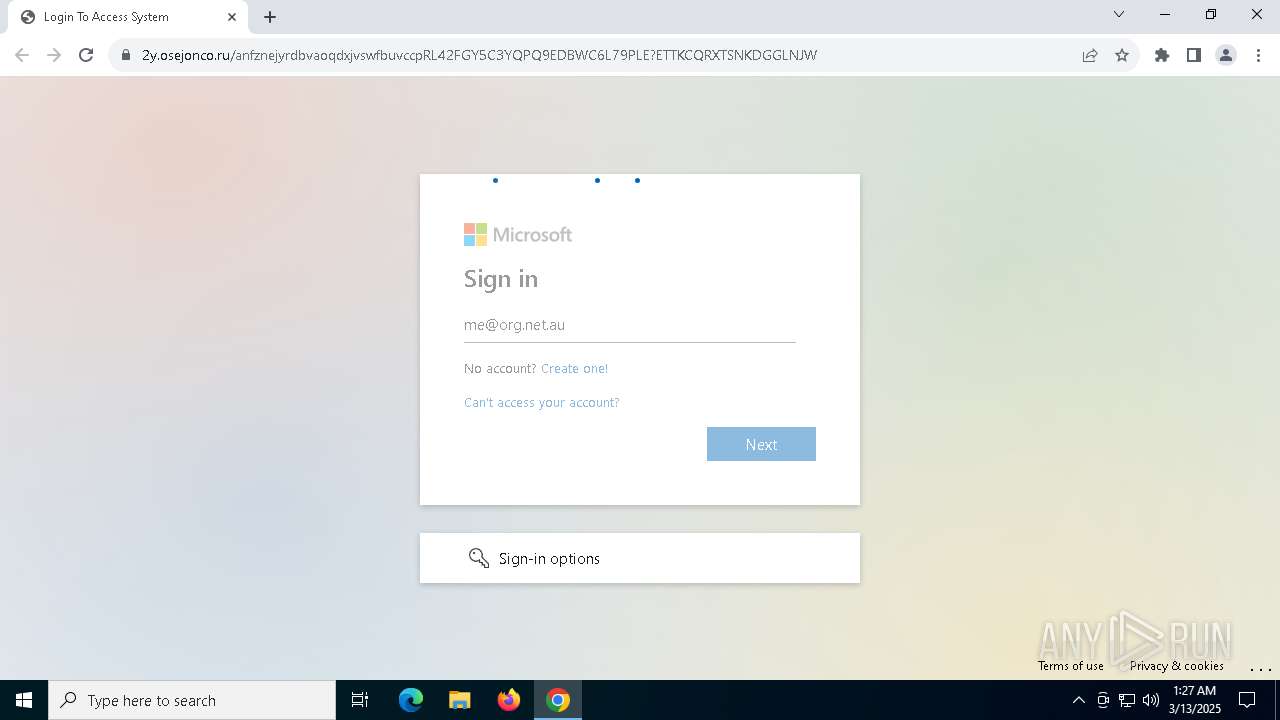
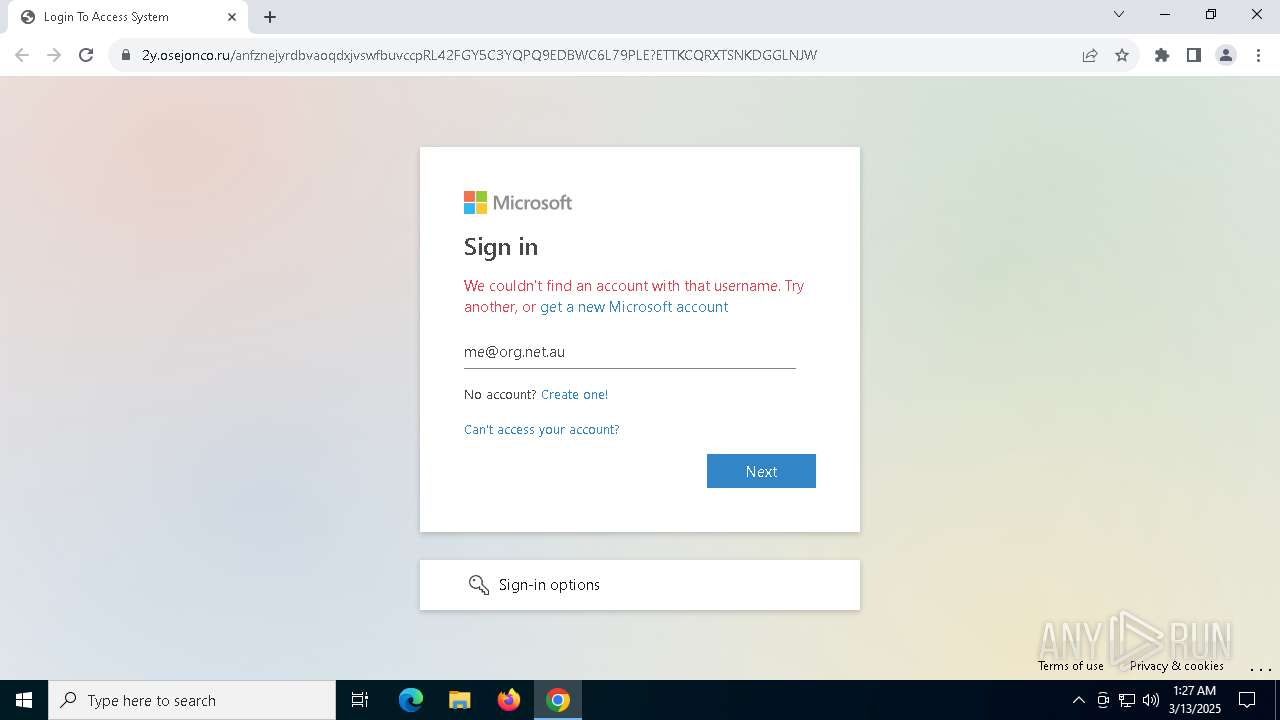
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | March 13, 2025, 01:26:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines (63052), with CRLF line terminators |
| MD5: | 8844F6D6EB425279A1005F5E7F98B33F |
| SHA1: | 393FF27F17989E331A089FD8FC49E5C0925506A3 |
| SHA256: | CB85E33FBC84B1D2F7551E496858F56041BADE91C60CB9E28975D011F0C60552 |
| SSDEEP: | 1536:U8vsJGUE4xeAIYGF73RZ69u3NilX87k4DtsByk:8EAL+F73olX87k4DtsBT |
MALICIOUS
PHISHING has been detected (SURICATA)
- chrome.exe (PID: 7264)
SUSPICIOUS
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 6808)
INFO
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 2516)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 7852)
- BackgroundTransferHost.exe (PID: 2516)
- BackgroundTransferHost.exe (PID: 6592)
- BackgroundTransferHost.exe (PID: 1812)
- BackgroundTransferHost.exe (PID: 4008)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 2516)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 2516)
- slui.exe (PID: 7888)
Reads the computer name
- ShellExperienceHost.exe (PID: 6808)
Application launched itself
- chrome.exe (PID: 6040)
Checks supported languages
- ShellExperienceHost.exe (PID: 6808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
Total processes
174
Monitored processes
36
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3840 --field-trial-handle=1876,i,6373554923169383055,10331982329133736103,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5188 --field-trial-handle=1876,i,6373554923169383055,10331982329133736103,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4972 --field-trial-handle=1876,i,6373554923169383055,10331982329133736103,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1812 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2516 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5224 --field-trial-handle=1876,i,6373554923169383055,10331982329133736103,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 5984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5136 --field-trial-handle=1876,i,6373554923169383055,10331982329133736103,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "C:\Users\admin\AppData\Local\Temp\41QUE01 - TAX INVOICE - 7274916 from SFG (Brisbane).html" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 6048 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x224,0x228,0x22c,0x48,0x230,0x7ffc8829dc40,0x7ffc8829dc4c,0x7ffc8829dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
14 654
Read events
14 587
Write events
42
Delete events
25
Modification events
| (PID) Process: | (6040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6040) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7500) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000B74EE6F6B693DB01 | |||
| (PID) Process: | (6040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | ahfgeienlihckogmohjhadlkjgocpleb |
Value: 3B08F722C14555E595AF269F140EE426CE8DEBAD90D03EE9FF33B95CB34233F6 | |||
| (PID) Process: | (6040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | bjbddleefiddlmdfdfbgodgacjjldihj |
Value: 5CFE6AD362B9AABBD07085580BC6C063CF1C79A0B22ECB6BCBA21EECA68BA07F | |||
| (PID) Process: | (6040) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\PreferenceMACs\Default\extensions.settings |
| Operation: | write | Name: | mhjfbmdgcfjbbpaeojofohoefgiehjai |
Value: F6EE482B70E472BD0FE04C8E130D7E2A0D87334BDC8F199AD874C100863BC5BE | |||
Executable files
3
Suspicious files
149
Text files
40
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10bfa8.TMP | — | |
MD5:— | SHA256:— | |||
| 6040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10bfa8.TMP | — | |
MD5:— | SHA256:— | |||
| 6040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10bfa8.TMP | — | |
MD5:— | SHA256:— | |||
| 6040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10bfa8.TMP | — | |
MD5:— | SHA256:— | |||
| 6040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10bfb8.TMP | — | |
MD5:— | SHA256:— | |||
| 6040 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10bfb8.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
67
DNS requests
72
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7700 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2516 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8144 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8144 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1228 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/pmztx7tk73bjttcb4b6ys6fixq_2025.1.3.1202/ggkkehgbnfjpeggfpleeakpidbkibbmn_2025.1.3.1202_all_afljkosaafpr5gqm7ftppqz7zq.crx3 | unknown | — | — | whitelisted |
1228 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/pmztx7tk73bjttcb4b6ys6fixq_2025.1.3.1202/ggkkehgbnfjpeggfpleeakpidbkibbmn_2025.1.3.1202_all_afljkosaafpr5gqm7ftppqz7zq.crx3 | unknown | — | — | whitelisted |
1228 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/pmztx7tk73bjttcb4b6ys6fixq_2025.1.3.1202/ggkkehgbnfjpeggfpleeakpidbkibbmn_2025.1.3.1202_all_afljkosaafpr5gqm7ftppqz7zq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6040 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7264 | chrome.exe | 142.250.184.195:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
7264 | chrome.exe | 142.251.173.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
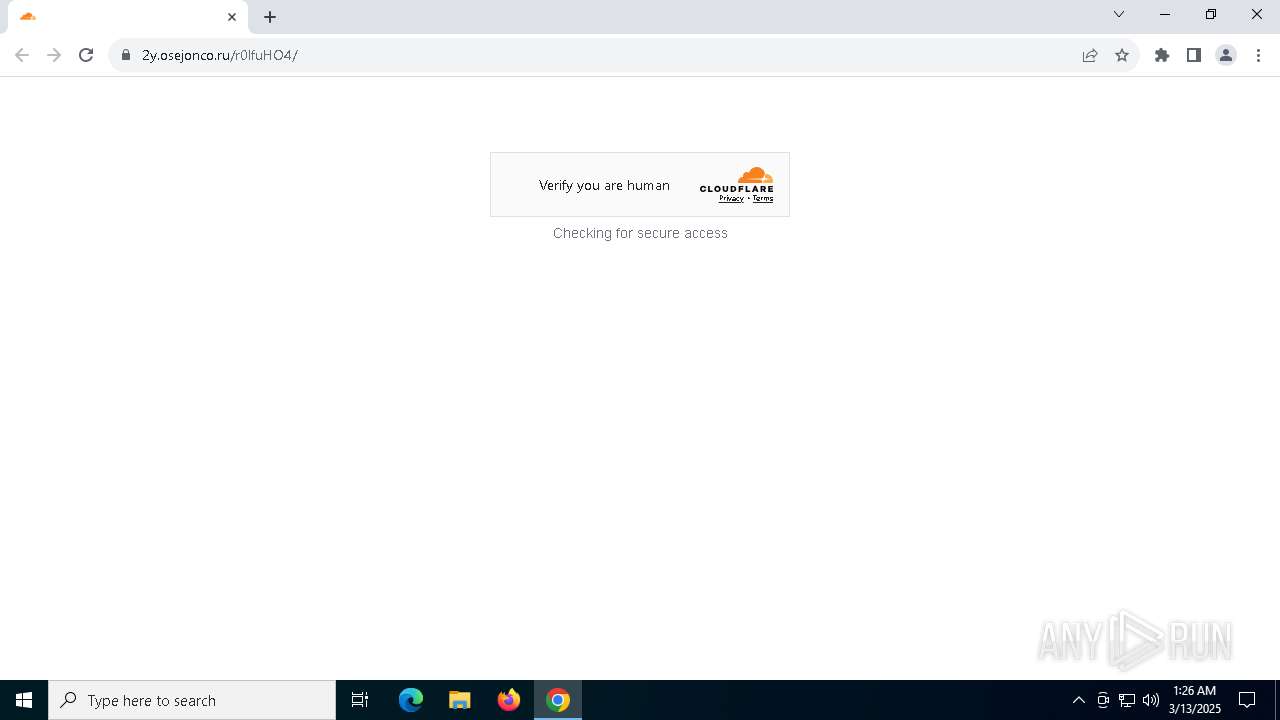
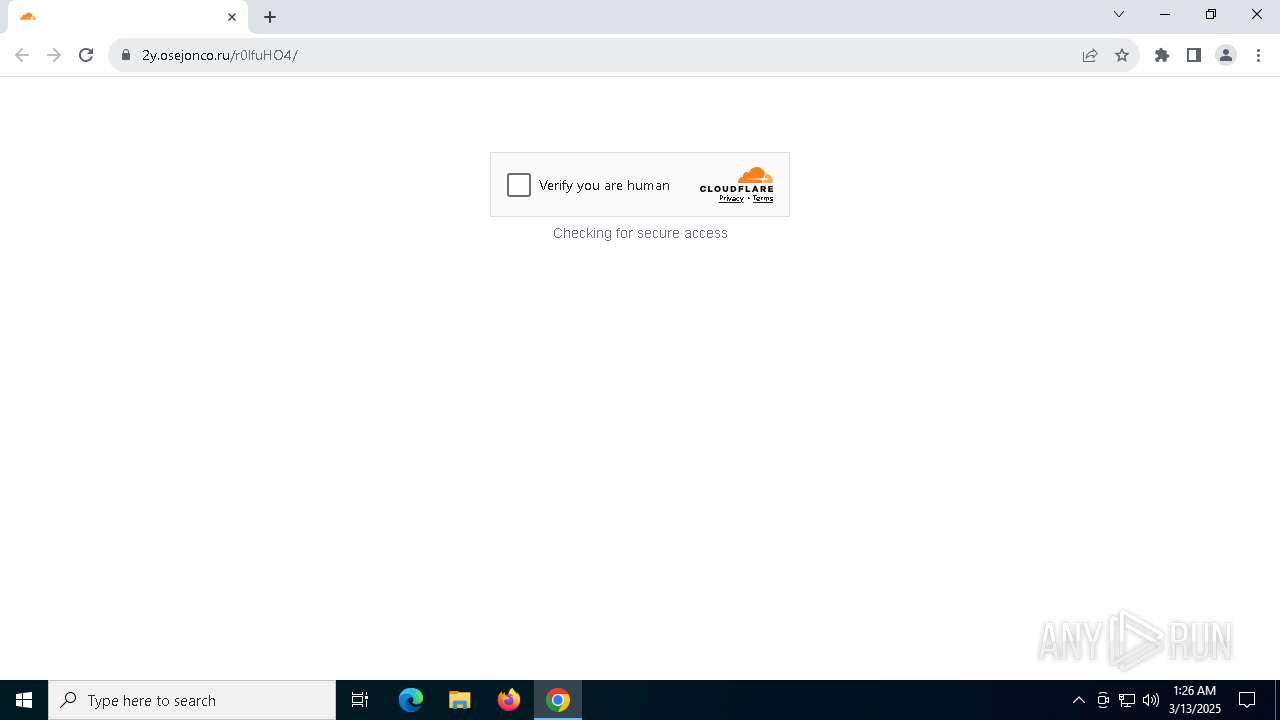
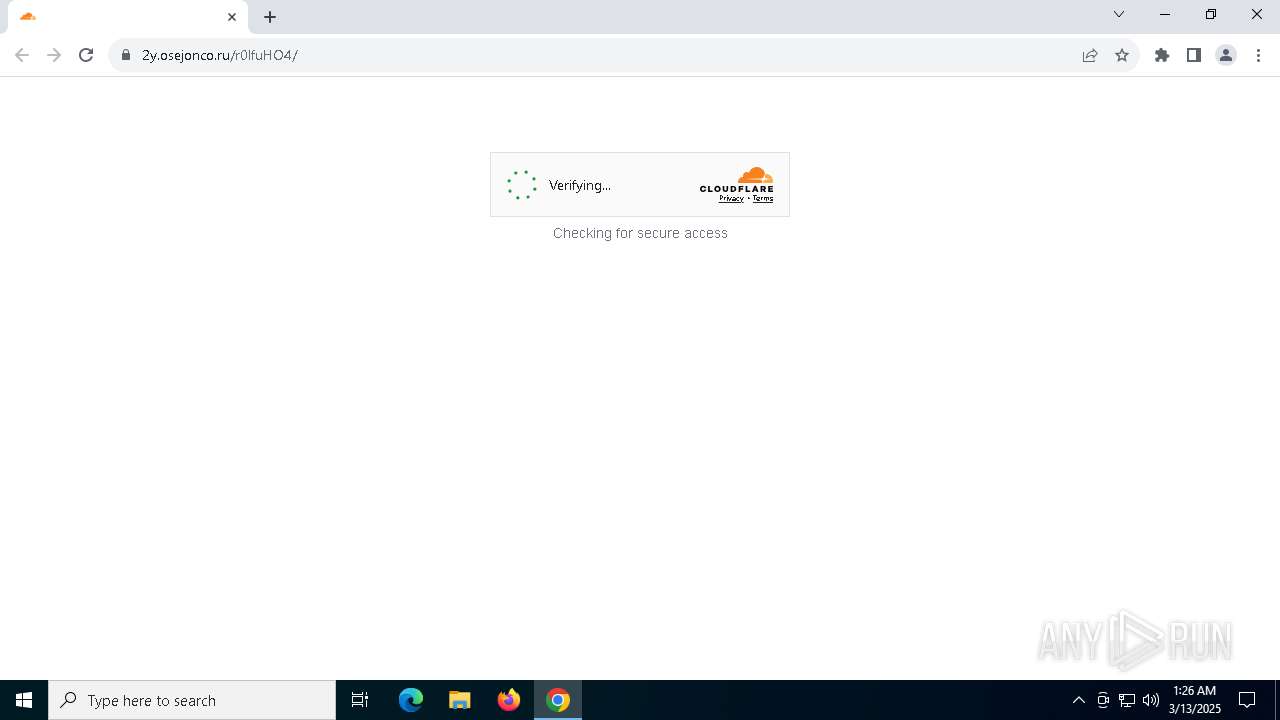
7264 | chrome.exe | 104.21.84.165:443 | 2y.osejonco.ru | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
2y.osejonco.ru |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
code.jquery.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7264 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7264 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7264 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7264 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7264 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7264 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7264 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7264 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7264 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7264 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (tjezyf .ru) |