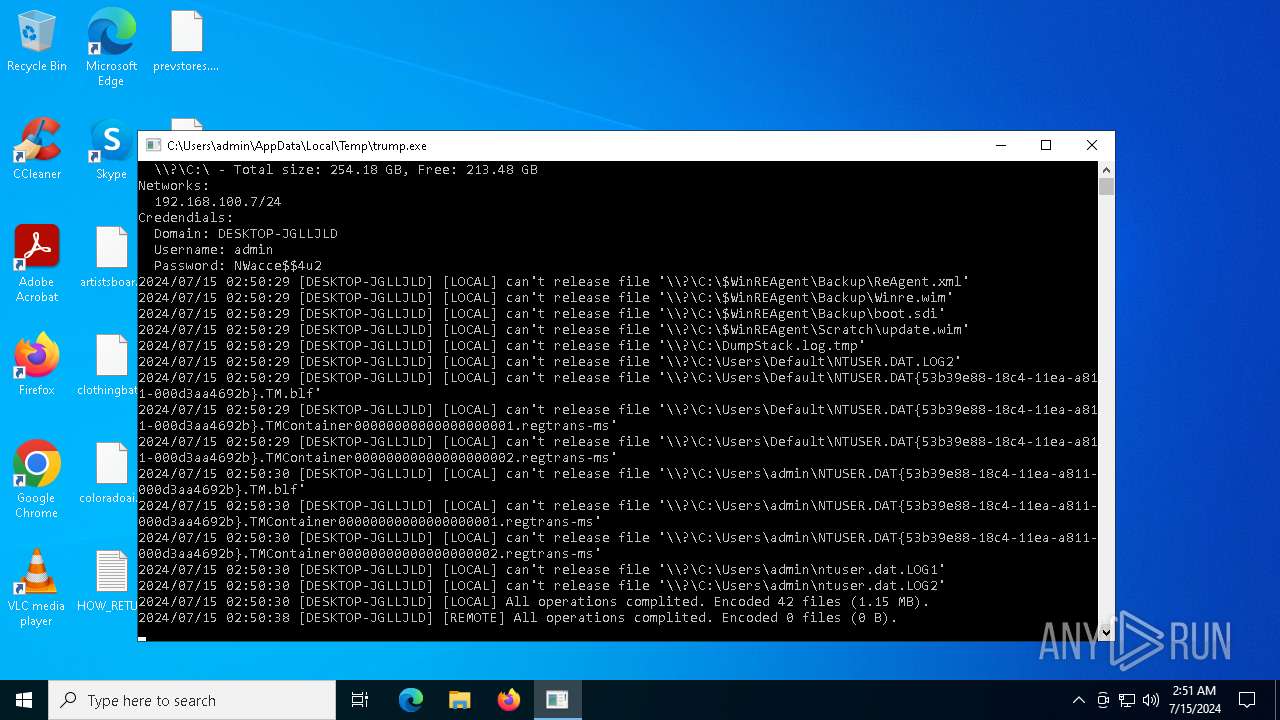
| File name: | trump |
| Full analysis: | https://app.any.run/tasks/6edadaec-01ee-4ed7-9e95-9053189f39f8 |
| Verdict: | Malicious activity |
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | July 15, 2024, 02:50:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows |
| MD5: | 315A9D36ED86894269E0126B649FB3D6 |
| SHA1: | CAAA1F85DD333C9D19767B5DE527152D5ACBC2A4 |
| SHA256: | CB0B9E509A0F16EB864277CD76C4DCAA5016A356DD62C04DFF8F8D96736174A7 |
| SSDEEP: | 98304:ZKkthGMwyeIxaOhUjKwvcPOiVpdZSCEgJ:F |
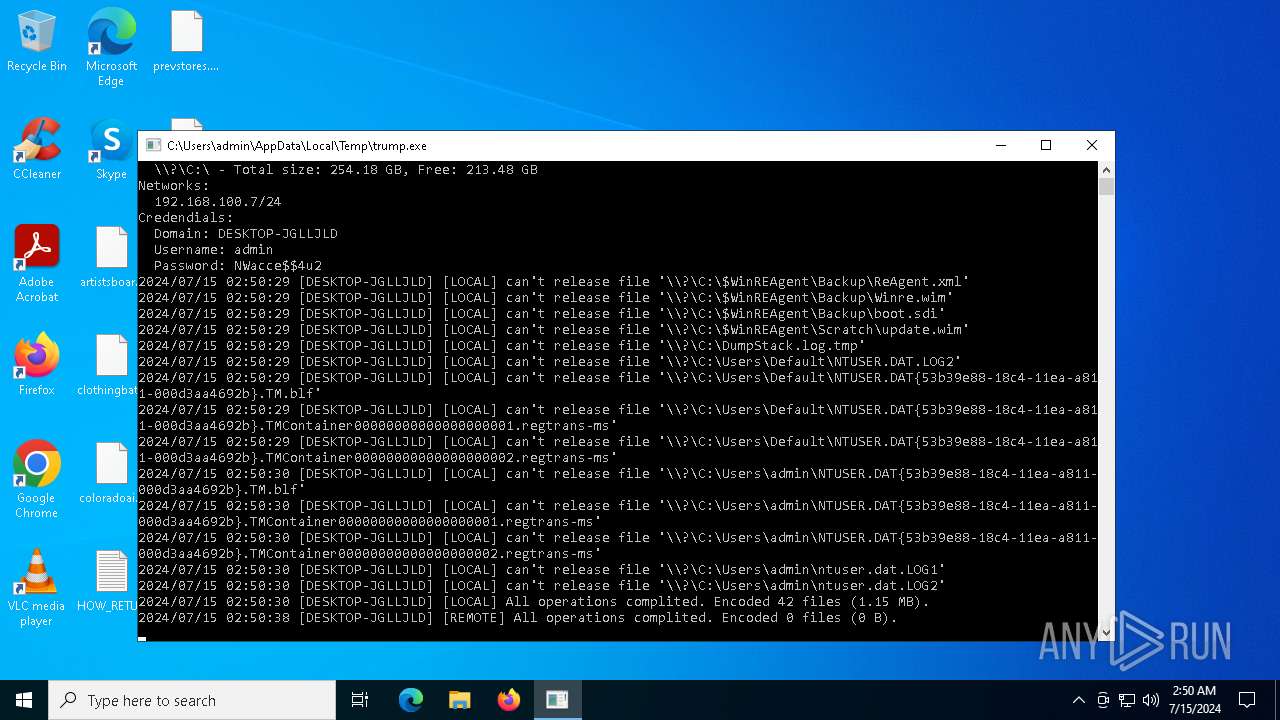
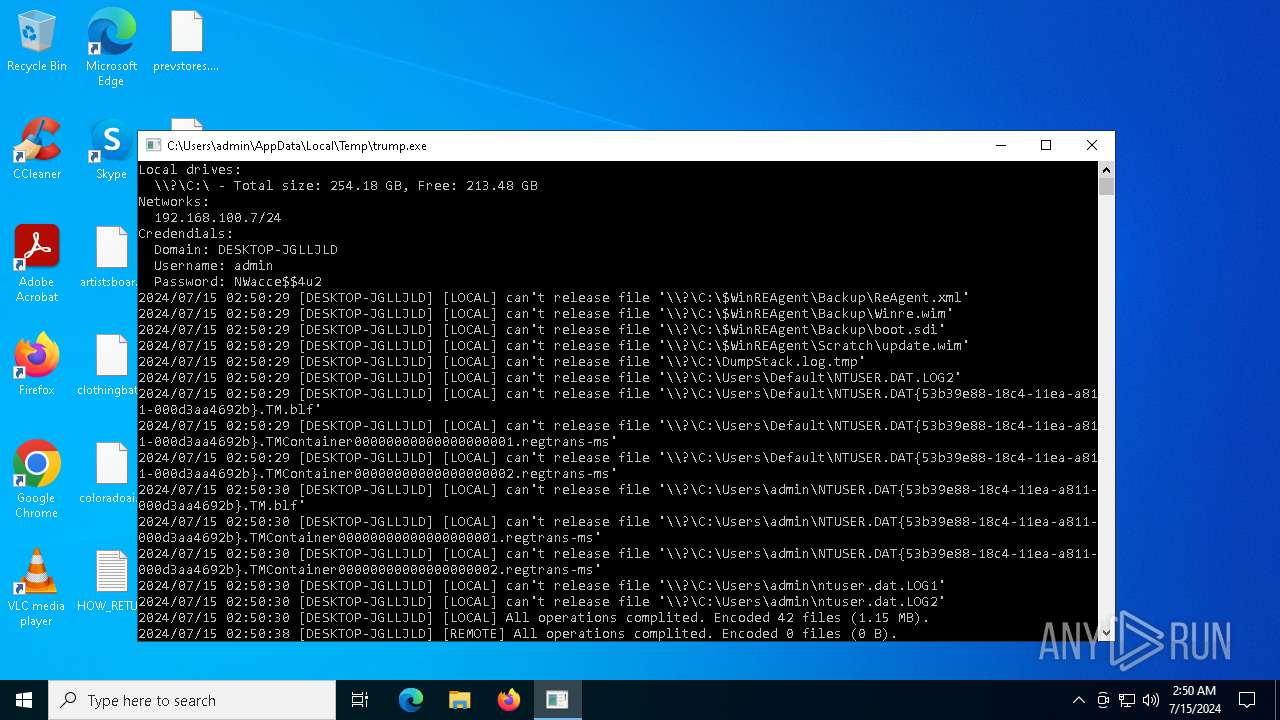
MALICIOUS
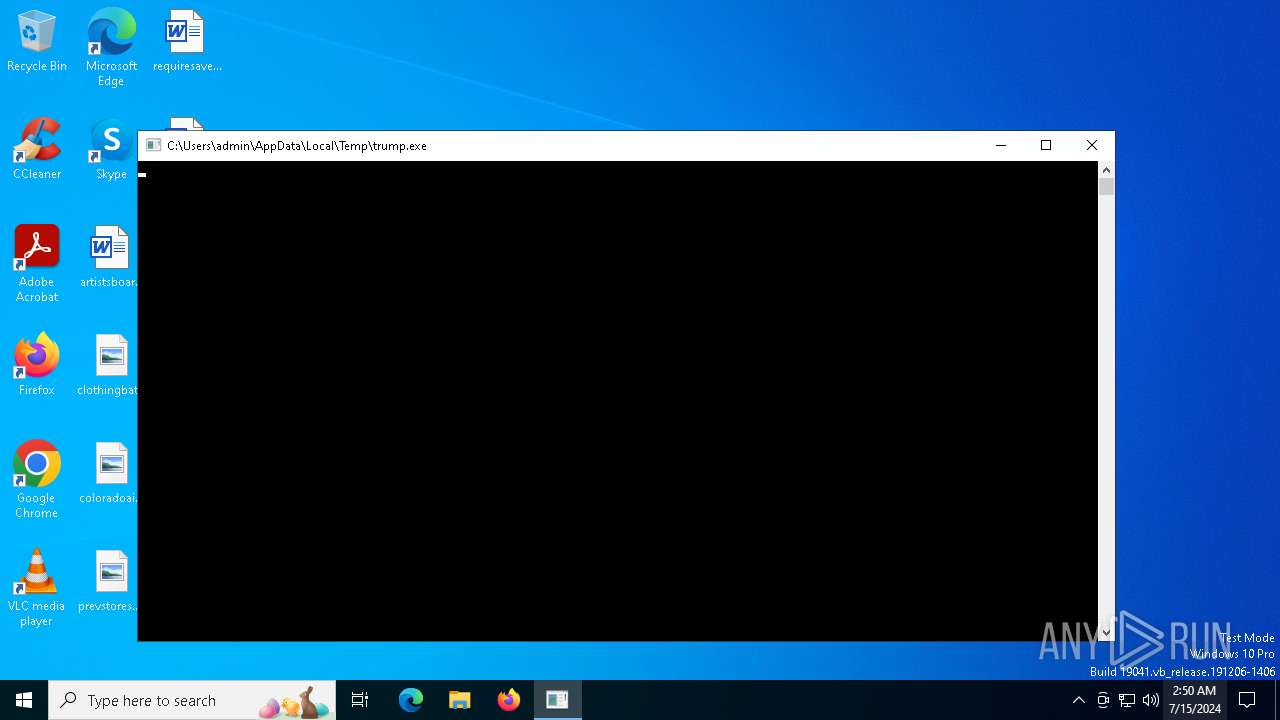
Drops the executable file immediately after the start
- trump.exe (PID: 5988)
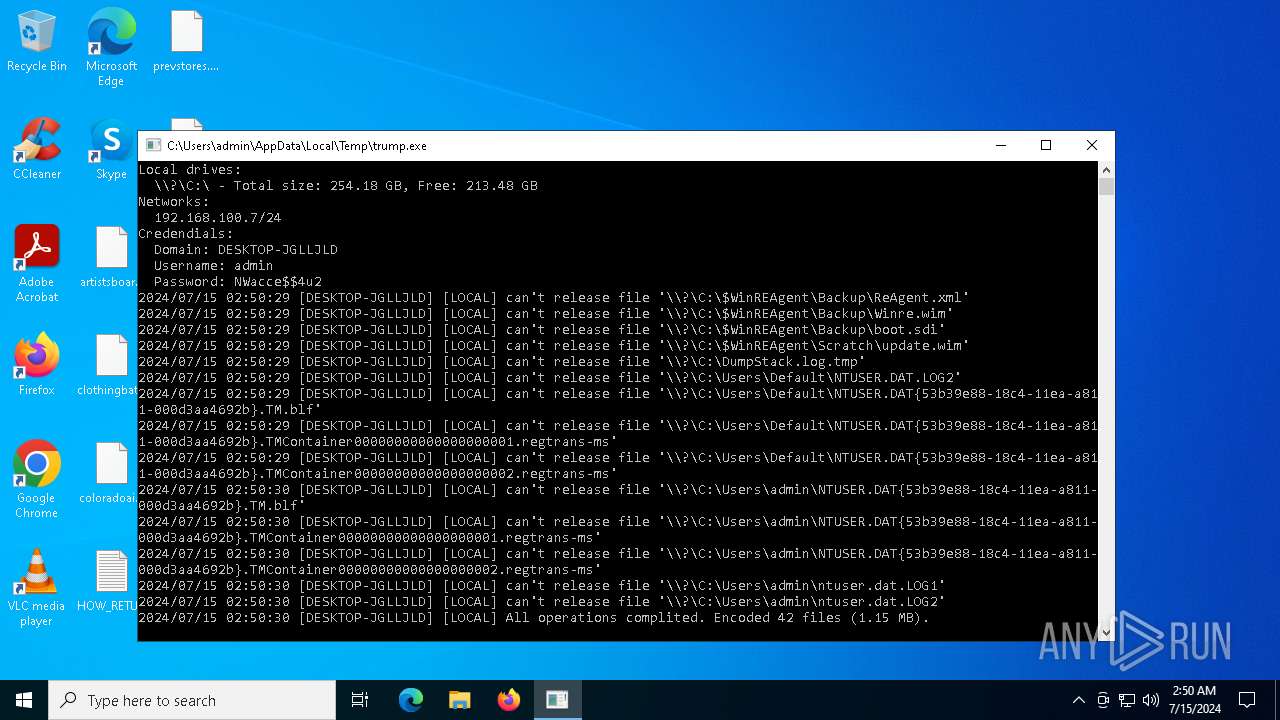
Renames files like ransomware
- trump.exe (PID: 5988)
SUSPICIOUS
Starts CMD.EXE for commands execution
- trump.exe (PID: 5988)
Starts application with an unusual extension
- cmd.exe (PID: 5220)
Creates files like ransomware instruction
- trump.exe (PID: 5988)
INFO
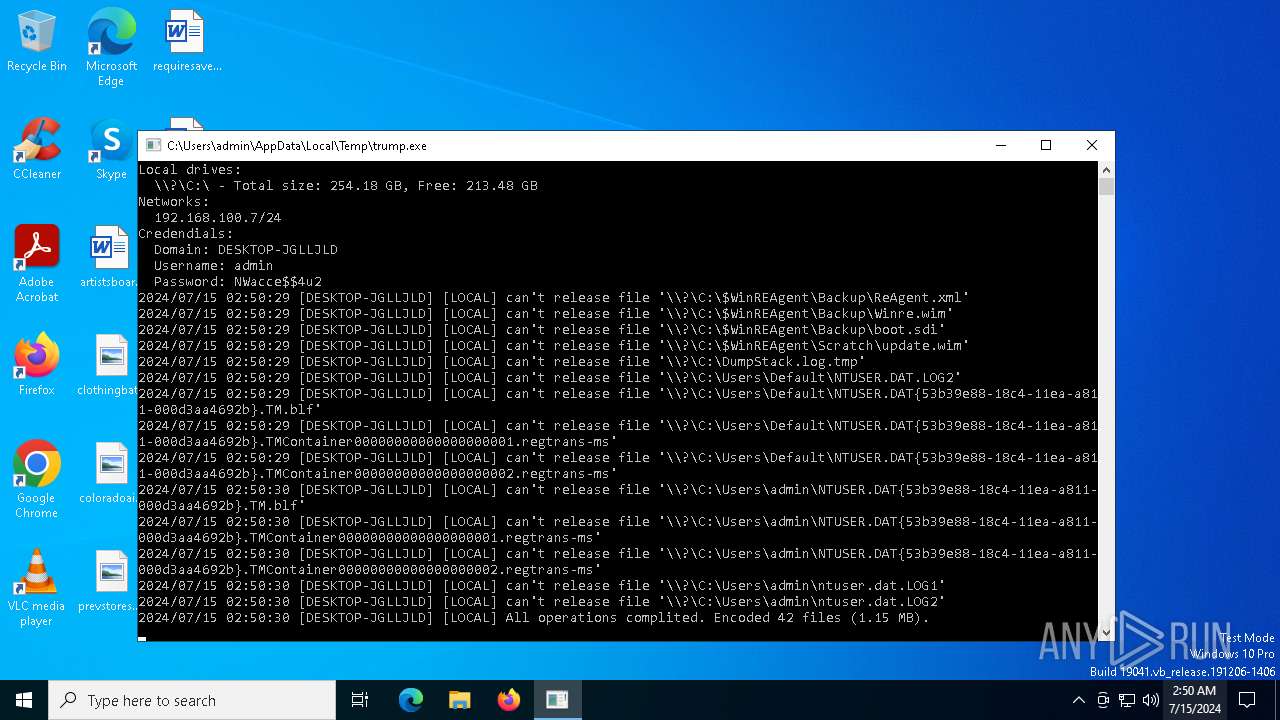
Dropped object may contain TOR URL's
- trump.exe (PID: 5988)
Checks supported languages
- trump.exe (PID: 5988)
- chcp.com (PID: 2704)
Reads the computer name
- trump.exe (PID: 5988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 2674688 |
| InitializedDataSize: | 248832 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x66e40 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
143
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1048 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | trump.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2704 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3068 | systeminfo" | C:\Windows\System32\systeminfo.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays system information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5220 | cmd "/c chcp 65001 & systeminfo" | C:\Windows\System32\cmd.exe | — | trump.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5396 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5988 | "C:\Users\admin\AppData\Local\Temp\trump.exe" | C:\Users\admin\AppData\Local\Temp\trump.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6316 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 493
Read events
7 084
Write events
325
Delete events
84
Modification events
| (PID) Process: | (3068) systeminfo.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\mlang.dll,-4386 |
Value: English (United States) | |||
| (PID) Process: | (1048) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SideBySide |
| Operation: | write | Name: | LastScavengingStarvationReport |
Value: 961D8DBE61D6DA01 | |||
| (PID) Process: | (1048) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31118945 | |||
| (PID) Process: | (1048) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
| (PID) Process: | (5988) trump.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 641700009495F9BC61D6DA01 | |||
| (PID) Process: | (5988) trump.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: BE098F84E0A274B85AD7E17204E730EE8C79B8312F1481F346AE82998C376015 | |||
| (PID) Process: | (5988) trump.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (5988) trump.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: \\?\C:\$WinREAgent\Backup\ReAgent.xml | |||
| (PID) Process: | (5988) trump.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 56A2B92B7DCF3C90C541CAB69FB0A3DE65AA3BB08F194934C03176409B326546 | |||
| (PID) Process: | (5988) trump.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: ꉖ⮹콽逼䇅뛊낟�ꩥ뀻ᦏ㑉㇀䁶㊛䙥 | |||
Executable files
0
Suspicious files
80
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5988 | trump.exe | C:\Users\admin\Desktop\HOW_RETURN_YOUR_DATA.TXT | text | |
MD5:01C5A6F383606B0FBF6B0BF6601DE701 | SHA256:C5341BD3A2BA2AC369E5C48D3CA970DA67141D15F502040FD8793AAD051FEB17 | |||
| 5988 | trump.exe | C:\Users\admin\Desktop\prevstores.jpg | binary | |
MD5:994BFECD02E031A0173BB6CF78312941 | SHA256:50DE9DFFD268E34238EEDDD2C598392A0635A1671C93CC1CFF169A2B09769DED | |||
| 5988 | trump.exe | C:\Users\admin\Desktop\artistsboards.rtf | binary | |
MD5:DAF5CF3589E593C7DDA576F15B591AE9 | SHA256:64B20E3F04F4D0F0360A4155EE84F10737394B8E9AA39598032CC1812B6EE3E6 | |||
| 5988 | trump.exe | C:\Users\admin\Desktop\coloradoaid.png.00000001 | binary | |
MD5:C8B4AD66266049FCCE0CEB1D747C3D9B | SHA256:3BA0495CDB2FA54E5C486F8531E5C67EB52EE0CF72A351D5FCC86E38D68DF1DD | |||
| 5988 | trump.exe | C:\Users\admin\Desktop\artistsboards.rtf.00000001 | binary | |
MD5:DAF5CF3589E593C7DDA576F15B591AE9 | SHA256:64B20E3F04F4D0F0360A4155EE84F10737394B8E9AA39598032CC1812B6EE3E6 | |||
| 5988 | trump.exe | C:\Users\Public\Documents\HOW_RETURN_YOUR_DATA.TXT | text | |
MD5:01C5A6F383606B0FBF6B0BF6601DE701 | SHA256:C5341BD3A2BA2AC369E5C48D3CA970DA67141D15F502040FD8793AAD051FEB17 | |||
| 5988 | trump.exe | C:\Users\Default\Desktop\HOW_RETURN_YOUR_DATA.TXT | text | |
MD5:01C5A6F383606B0FBF6B0BF6601DE701 | SHA256:C5341BD3A2BA2AC369E5C48D3CA970DA67141D15F502040FD8793AAD051FEB17 | |||
| 5988 | trump.exe | C:\Users\admin\Desktop\coloradoaid.png | binary | |
MD5:C8B4AD66266049FCCE0CEB1D747C3D9B | SHA256:3BA0495CDB2FA54E5C486F8531E5C67EB52EE0CF72A351D5FCC86E38D68DF1DD | |||
| 5988 | trump.exe | C:\Users\admin\Desktop\threecivil.rtf | binary | |
MD5:1EE44C60ADB9A74906BCE3561F3ED8BC | SHA256:27692AAF953719C4C4076F5ADDE04C4FA04E725D9CAFCC91828CD914360D70BB | |||
| 5988 | trump.exe | C:\Users\admin\Desktop\clothingbattery.png | binary | |
MD5:30FB1B0AFA0E55E6CAB349BE2346B807 | SHA256:84FD0D381106CA5A846F2845AA6BC834A63E2FADD0EDD8F3147DD5097C9767EE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
107
DNS requests
18
Threats
42
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1972 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1320 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3680 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6812 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6812 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1972 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2972 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1776 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1292 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1972 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1972 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5988 | trump.exe | 173.44.141.152:443 | — | Eonix Corporation | US | unknown |
4656 | SearchApp.exe | 104.126.37.176:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5988 | trump.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 30 |
41 ETPRO signatures available at the full report