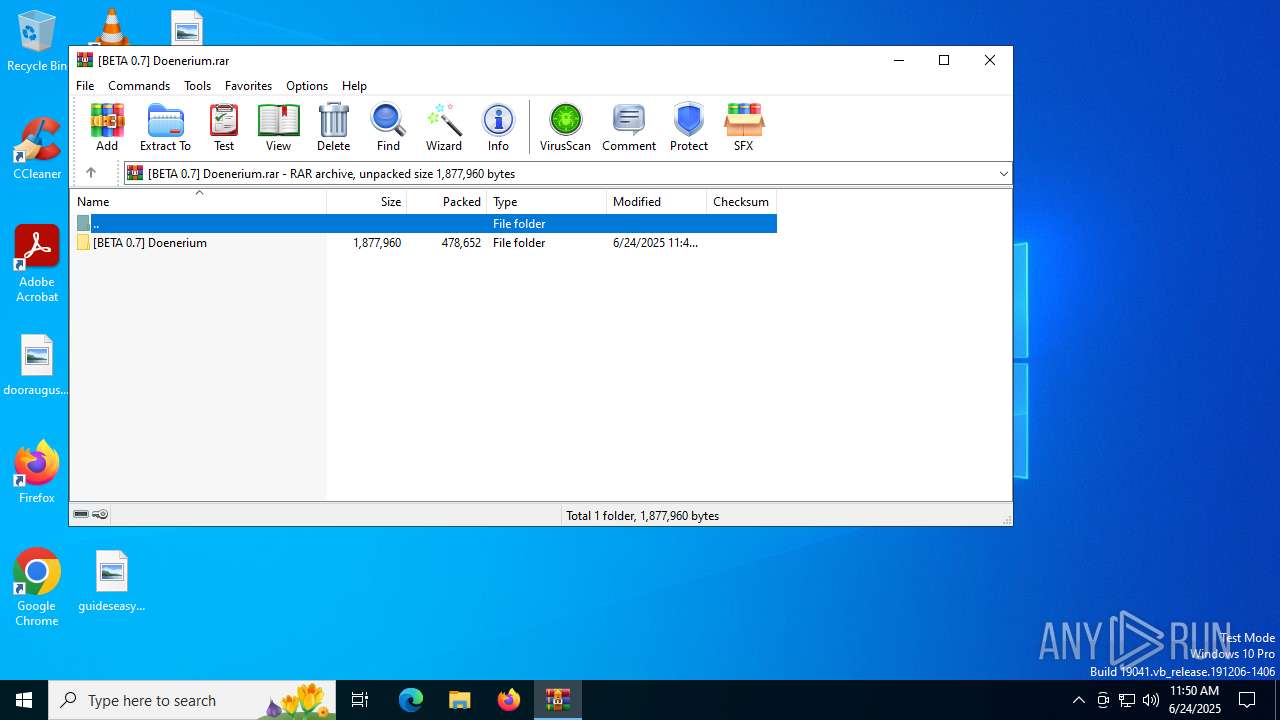
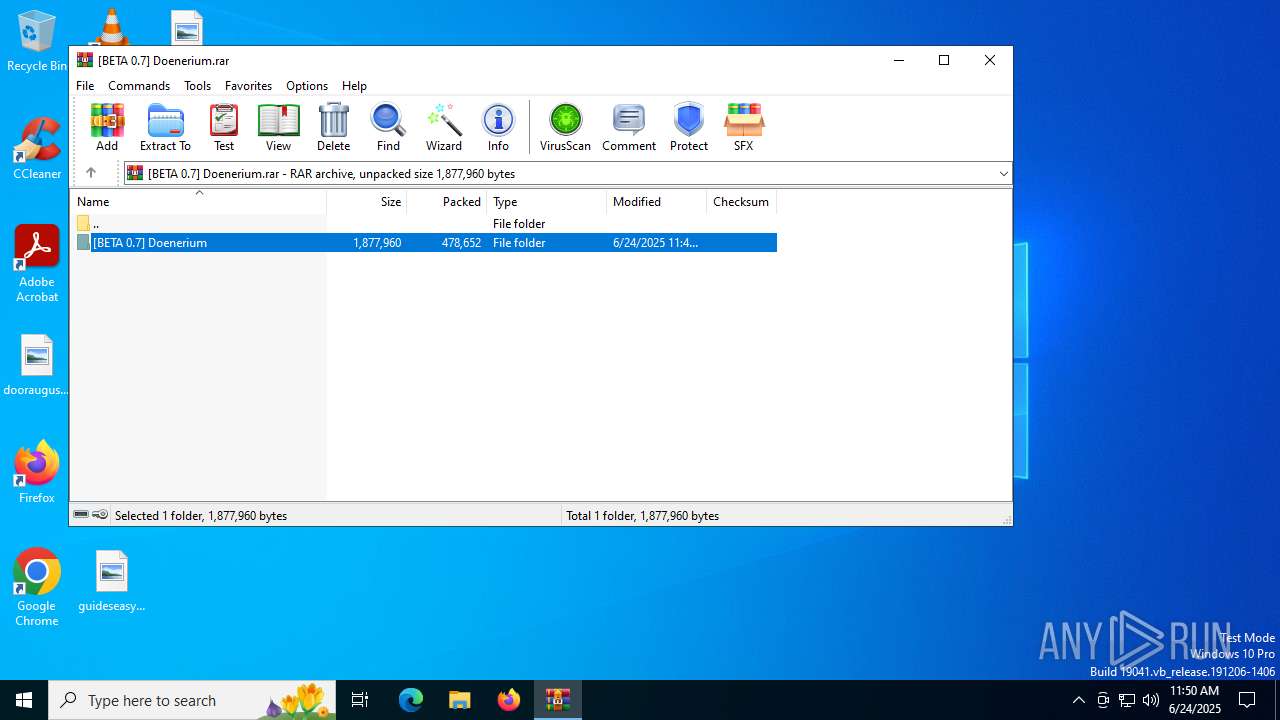
| File name: | [BETA 0.7] Doenerium.rar |
| Full analysis: | https://app.any.run/tasks/7e1e6414-5243-4e3e-b291-1098ffdd5f0e |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 24, 2025, 11:50:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A8F3A954545D0D827D2782BC3DB2C077 |
| SHA1: | 09F3ECC0BCA498FE7AC108F805BFA1B3C7BE4D22 |
| SHA256: | CA2E5E47434E991D085CBC07F67287739BC2379AF356159732EA75DF00C83880 |
| SSDEEP: | 24576:Bkb3JhUID8Sk+8ekMQHusNly3I2iMZ7K64ZUBZe:yb3JhnD8Sk+8ekMQHusNly3JiMZ7K6Mx |
MALICIOUS
Changes the autorun value in the registry
- stub.exe (PID: 5808)
Generic archive extractor
- WinRAR.exe (PID: 6528)
ASYNCRAT has been detected (YARA)
- system.exe (PID: 1964)
SUSPICIOUS
Starts CMD.EXE for commands execution
- stub.exe (PID: 5808)
The process creates files with name similar to system file names
- stub.exe (PID: 5808)
Executing commands from a ".bat" file
- stub.exe (PID: 5808)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2780)
The executable file from the user directory is run by the CMD process
- system.exe (PID: 1964)
Executable content was dropped or overwritten
- stub.exe (PID: 5808)
Connects to unusual port
- system.exe (PID: 1964)
INFO
Launching a file from a Registry key
- stub.exe (PID: 5808)
Reads the machine GUID from the registry
- stub.exe (PID: 5808)
- system.exe (PID: 1964)
- stub.exe (PID: 4100)
- stub.exe (PID: 6348)
- stub.exe (PID: 2512)
Create files in a temporary directory
- stub.exe (PID: 5808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6528)
Reads the computer name
- stub.exe (PID: 5808)
- system.exe (PID: 1964)
- stub.exe (PID: 4100)
- stub.exe (PID: 6348)
- stub.exe (PID: 2512)
Checks supported languages
- stub.exe (PID: 5808)
- system.exe (PID: 1964)
- stub.exe (PID: 4100)
- stub.exe (PID: 6348)
- stub.exe (PID: 2512)
Manual execution by a user
- cmd.exe (PID: 7080)
- cmd.exe (PID: 3632)
- cmd.exe (PID: 6732)
- cmd.exe (PID: 5104)
Creates files or folders in the user directory
- stub.exe (PID: 5808)
Checks proxy server information
- slui.exe (PID: 4816)
Reads the software policy settings
- slui.exe (PID: 4816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(1964) system.exe
C2 (1)act-fluid.gl.at.ply.gg
Ports (1)43955
Version
Options
AutoRuntrue
MutexdΗCrתt勒CبωΔYA吉tTr迪cΑΔdΘ9
InstallFolder%AppData%
Certificates
Cert1MIICKTCCAZKgAwIBAgIVANuipMOb3bgqlyteV84QDUFElFzvMA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBUVCT0xBMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjIwODI1MjE1OTI0WhcNMzMwNjAzMjE1OTI0WjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA...
Server_SignatureawddJZ934LMG4AsRbTa6pIYbTKaAy8xpwQBYqIxirQwX96V3TUahbZ35pxctnKcRI+g5ZT5IwSwH588jNX+S5OEWTydOgyPuShluDhMRIH63WQoYWVZDtPcJu3zxBoK0nf/LRjZD7INGT5afd0Eze6hszcA/lSerHZSLc4sb1TU=
Keys
AES475b96a784d13678b57fb842dae17bc91d7daf14324ee27b1e2a3b13bc199a69
SaltDcRatByqwqdanchun
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1064 |
| UncompressedSize: | 3416 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | [BETA 0.7] Doenerium/[BETA 0.7] Doenerium/build/build.js |
Total processes
159
Monitored processes
20
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | timeout 3 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | "C:\Users\admin\AppData\Roaming\system.exe" | C:\Users\admin\AppData\Roaming\system.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 3.6.0.0 Modules
AsyncRat(PID) Process(1964) system.exe C2 (1)act-fluid.gl.at.ply.gg Ports (1)43955 Version Options AutoRuntrue MutexdΗCrתt勒CبωΔYA吉tTr迪cΑΔdΘ9 InstallFolder%AppData% Certificates Cert1MIICKTCCAZKgAwIBAgIVANuipMOb3bgqlyteV84QDUFElFzvMA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBUVCT0xBMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjIwODI1MjE1OTI0WhcNMzMwNjAzMjE1OTI0WjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA... Server_SignatureawddJZ934LMG4AsRbTa6pIYbTKaAy8xpwQBYqIxirQwX96V3TUahbZ35pxctnKcRI+g5ZT5IwSwH588jNX+S5OEWTydOgyPuShluDhMRIH63WQoYWVZDtPcJu3zxBoK0nf/LRjZD7INGT5afd0Eze6hszcA/lSerHZSLc4sb1TU= Keys AES475b96a784d13678b57fb842dae17bc91d7daf14324ee27b1e2a3b13bc199a69 SaltDcRatByqwqdanchun | |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2512 | "C:\Users\admin\Desktop\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\stub\stub.exe" | C:\Users\admin\Desktop\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\stub\stub.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3.6.0.0 Modules
| |||||||||||||||
| 2780 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmp9B26.tmp.bat"" | C:\Windows\System32\cmd.exe | — | stub.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3632 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\install.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3636 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 788
Read events
8 769
Write events
19
Delete events
0
Modification events
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\[BETA 0.7] Doenerium.rar | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6528) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
2
Suspicious files
9
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6528.14788\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\build\build.js | binary | |
MD5:43A17F9F54F87D1C483D1A3F6BF5726C | SHA256:CB3E91FE5F70F01C74C5F7FE152559074F5A36FAFBE2416E987C8149ABD204EE | |||
| 6528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6528.14788\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\build.bat | text | |
MD5:F4A5865541FC975CD7F12DA3FB0C1B5C | SHA256:6DA093D57CE03AD27A07824C31BA9B2C22B31ED0CB5DFB616717548A2925AD62 | |||
| 6528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6528.14788\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\install.bat | text | |
MD5:4416DBEF6489E123AB45F72E6A5E4D87 | SHA256:6B1E159A935BD22AF9440FC0E456294EA83DECAD4CCE0481E9198556FC41F235 | |||
| 6528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6528.14788\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\icon\steam.ico | image | |
MD5:077AC253DDE237F3998B57153AF03E18 | SHA256:72179C46B0E0082AAFE2AEF640C142AD5F68EEC40C3D72787D49B9BF23C5A179 | |||
| 6528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6528.14788\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\icon\timer.ico | image | |
MD5:3D1104EEE656D18B52EBE5B3F610DC19 | SHA256:632CED79B603C34F94C48A9EC6F294279635F6EA3D4A53F636B25F1F7D1953B2 | |||
| 6528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6528.14788\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\setup.bat | text | |
MD5:1B0EC2913B705F75C3ED535693999730 | SHA256:0122AE4B3C41181B9E2F616D80991E9F5FAFD899FABAB353DE7B062A7F1BDBB5 | |||
| 6528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6528.14788\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\icon\default.ico | image | |
MD5:F74503B22273AEF038C811447B0727E7 | SHA256:709ACDA0DBF33AE8E1F3FBFF9DD7173BE9B317F9D0BC5E9CDE044F1587FA8DB7 | |||
| 6528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6528.14788\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\icon\chrome.ico | image | |
MD5:8280054D1069F314B93DD99A418F1F0B | SHA256:A277CD9B5A4322F59BBE59B0B5A23B3B03D1313DCD16BF786AAE81ADF2AEE3E6 | |||
| 6528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6528.14788\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\icon\edge.ico | image | |
MD5:CD39617876127AE39166642CCD050EEC | SHA256:792A31F03553CFB1B05FB0E833EA559F33B388198726AE5B5D313A0335219CC2 | |||
| 6528 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6528.14788\[BETA 0.7] Doenerium\[BETA 0.7] Doenerium\build\ressources.mjs | binary | |
MD5:62E396661533311AFB6F814534128936 | SHA256:7D2A9F9ADB9D0837CC5C99DAC731597EFF1E104E6AE332EDE8B3AA5059B9C1DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
43
DNS requests
18
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6024 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1964 | system.exe | 147.185.221.18:43955 | act-fluid.gl.at.ply.gg | PLAYIT-GG | US | suspicious |
1192 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4816 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
act-fluid.gl.at.ply.gg |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected domain Associated with Malware Distribution (.ply .gg) |
2200 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES Tunneling Service in DNS Lookup (* .ply .gg) |
2200 | svchost.exe | Potentially Bad Traffic | ET INFO playit .gg Tunneling Domain in DNS Lookup |