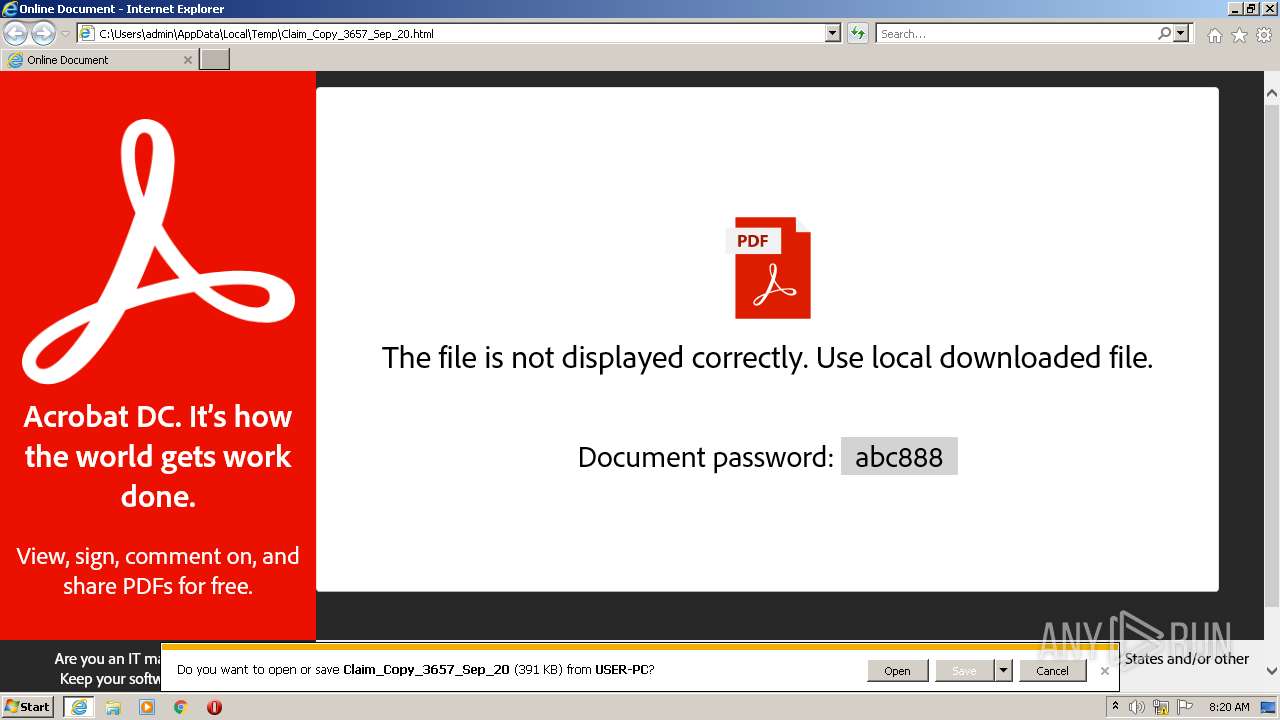
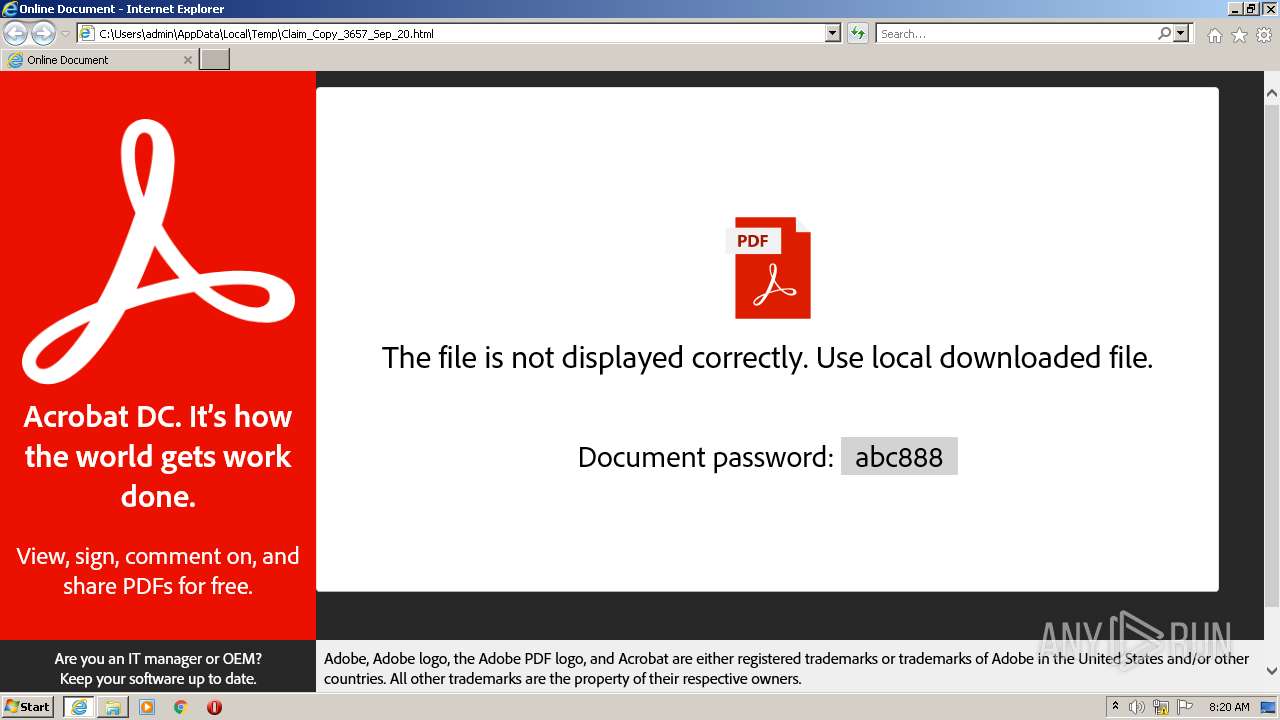
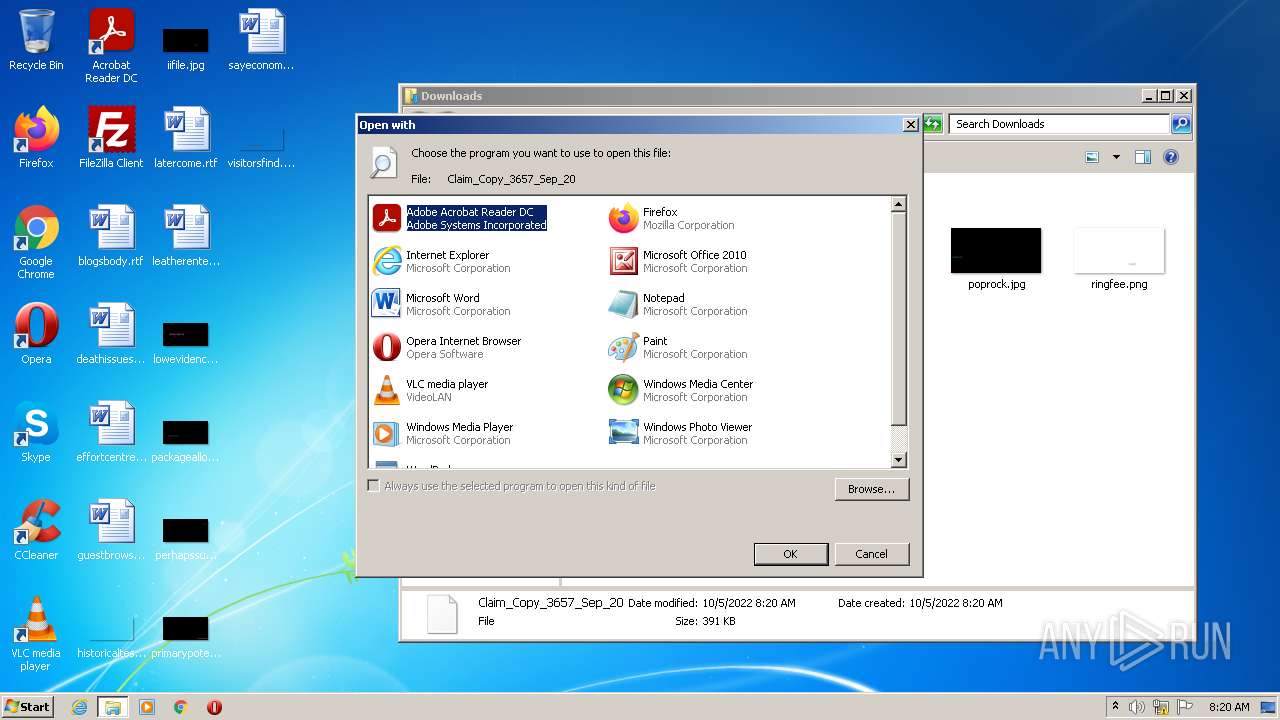
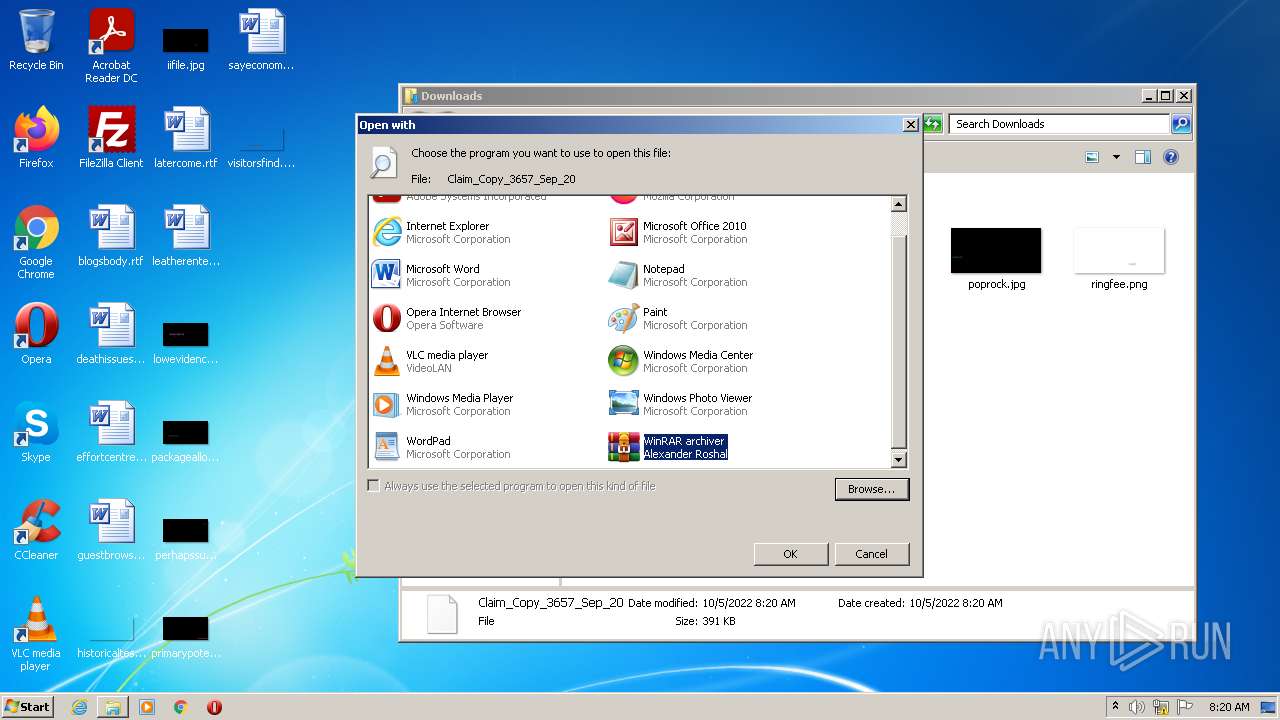
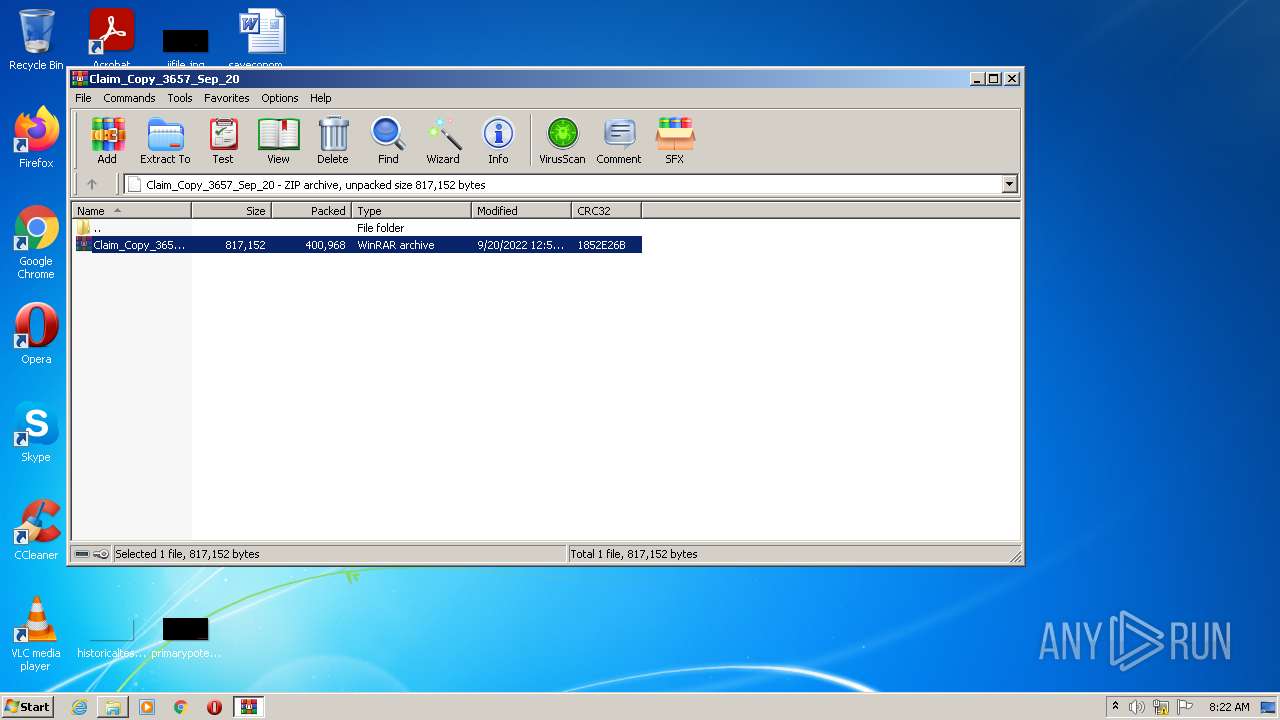
| File name: | Claim_Copy_3657_Sep_20.html |
| Full analysis: | https://app.any.run/tasks/352281e4-0623-49bc-b7c0-7eb010b29deb |
| Verdict: | Malicious activity |
| Threats: | Qbot is a banking Trojan — a malware designed to collect banking information from victims. Qbot targets organizations mostly in the US. It is equipped with various sophisticated evasion and info-stealing functions and worm-like functionality, and a strong persistence mechanism. |
| Analysis date: | October 05, 2022, 07:20:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF line terminators |
| MD5: | D7EA398ADA030C834B54E11387337F97 |
| SHA1: | 1F52A598EB7DEB5E82F1D09F50311A387C3F4A00 |
| SHA256: | C9E38DD0A37E5122F129463AD99188113715FAE3983DE9C10E2E1C139C3773FC |
| SSDEEP: | 12288:zfs8YEtCns3tMEwYtgoCkcnj5Zk0bTcw1eLxvk35IWjXLWjH:DysduNnj9ww1ehk3yWj6 |
MALICIOUS
The DLL Hijacking
- rundll32.exe (PID: 3976)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 3872)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3412)
QBOT detected by memory dumps
- explorer.exe (PID: 1816)
SUSPICIOUS
Reads the machine GUID from the registry
- WinRAR.exe (PID: 404)
Application launched itself
- WinRAR.exe (PID: 404)
Reads Internet Settings
- WinRAR.exe (PID: 404)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3412)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 2904)
INFO
Application launched itself
- iexplore.exe (PID: 276)
- iexplore.exe (PID: 1116)
Modifies the phishing filter of IE
- iexplore.exe (PID: 276)
Manual execution by user
- rundll32.exe (PID: 3976)
- WScript.exe (PID: 2904)
Reads the machine GUID from the registry
- rundll32.exe (PID: 3976)
Checks supported languages
- WinRAR.exe (PID: 404)
- WinRAR.exe (PID: 3412)
Reads the computer name
- WinRAR.exe (PID: 404)
- WinRAR.exe (PID: 3412)
Process checks LSA protection
- WinRAR.exe (PID: 404)
- WinRAR.exe (PID: 3412)
Changes default file association
- rundll32.exe (PID: 3976)
Creates files in the user directory
- WinRAR.exe (PID: 404)
- rundll32.exe (PID: 3976)
- WinRAR.exe (PID: 3412)
- explorer.exe (PID: 1816)
Creates a file in a temporary directory
- WinRAR.exe (PID: 404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Qbot
(PID) Process(1816) explorer.exe
Botnetobama206
Campaign1663660089
Version1027.894
C2 (150)119.82.111.158:443
66.181.164.43:443
181.118.183.123:443
88.245.168.200:2222
70.49.33.200:2222
193.3.19.37:443
99.232.140.205:2222
110.4.255.247:443
134.35.9.144:443
89.211.217.38:995
64.207.215.69:443
83.110.219.59:993
197.94.84.128:443
177.255.14.99:995
41.103.226.172:443
109.155.5.164:993
190.44.40.48:995
187.205.222.100:443
41.107.78.223:995
191.97.234.238:995
76.169.76.44:2222
70.51.132.197:2222
189.19.189.222:32101
72.88.245.71:443
173.218.180.91:443
197.204.243.167:443
68.53.110.74:995
160.176.204.241:443
41.69.103.179:995
68.224.229.42:443
100.1.5.250:995
194.166.205.204:995
88.232.207.24:443
14.183.63.12:443
89.211.223.138:2222
85.98.206.165:995
191.254.74.89:32101
72.66.96.129:995
176.42.245.2:995
31.54.39.153:2078
186.154.92.181:443
88.231.221.198:995
102.38.97.229:995
45.51.148.111:993
87.243.113.104:995
84.38.133.191:443
123.240.131.1:443
180.180.131.95:443
191.84.204.214:995
91.116.160.252:443
151.234.63.48:990
99.253.251.74:443
154.181.203.230:995
85.114.110.108:443
186.105.182.127:443
71.10.27.196:2222
71.10.27.196:2222
47.146.182.110:443
194.49.79.231:443
88.242.228.16:53
88.231.221.198:443
141.164.254.35:443
196.92.172.24:8443
186.50.245.74:995
78.182.113.80:443
41.96.171.218:443
154.246.182.210:443
81.214.220.237:443
95.136.41.50:443
84.38.133.191:443
190.158.58.236:443
105.99.80.23:443
102.184.151.194:995
181.127.138.30:443
167.60.82.242:995
196.112.34.71:443
88.251.38.53:443
37.37.206.87:995
37.76.197.124:443
188.157.6.170:443
68.50.190.55:443
181.111.20.201:443
31.166.116.171:443
84.238.253.171:443
197.49.50.44:443
160.152.135.188:2222
45.160.124.211:995
113.22.102.155:443
211.248.176.4:443
186.167.249.206:443
139.195.132.210:2222
182.213.208.5:443
201.177.163.176:443
45.183.234.180:443
98.180.234.228:443
184.82.110.50:995
179.24.245.193:995
94.99.110.157:995
181.56.125.32:443
119.42.124.18:443
181.231.229.133:443
2.89.78.130:993
70.81.121.237:2222
181.81.116.144:443
197.11.128.156:443
41.142.132.190:443
105.111.60.60:995
154.238.151.197:995
156.219.49.22:995
179.223.89.154:995
102.101.231.141:443
220.116.250.45:443
138.0.114.166:443
62.114.193.186:995
85.98.46.114:443
184.99.123.118:443
186.120.58.88:443
46.186.216.41:32100
156.213.107.29:995
27.73.215.46:32102
68.151.196.147:995
68.129.232.158:443
45.241.140.181:995
212.156.51.194:443
87.75.195.211:443
1.10.253.207:443
87.220.229.164:2222
109.200.165.82:443
41.105.197.244:443
190.59.247.136:995
219.69.103.199:443
61.105.45.244:443
105.105.104.0:443
169.1.47.111:443
210.195.18.76:2222
118.174.200.169:995
88.246.170.2:443
171.248.157.128:995
118.68.220.199:443
139.195.63.45:2222
118.216.99.232:443
181.80.133.202:443
102.40.236.32:995
46.116.229.16:443
61.70.29.53:443
179.108.32.195:443
171.238.230.59:443
81.56.22.251:995
31.32.180.179:443
85.139.203.42:32101
Strings (188)Start screenshot
at.exe %u:%u "%s" /I
powershell.exe -encodedCommand
amstream.dll
Self check
arp -a
c:\ProgramData
nltest /domain_trusts /all_trusts
%s %04x.%u %04x.%u res: %s seh_test: %u consts_test: %d vmdetected: %d createprocess: %d
Self test OK.
SoNuce]ugdiB3c[doMuce2s81*uXmcvP
\System32\WindowsPowerShell\v1.0\powershell.exe
net view
\System32\WindowsPowerShel1\v1.0\powershel1.exe
error res='%s' err=%d len=%u
net share
qwinsta
route print
.lnk
regsvr32.exe
Self test FAILED!!!
ProfileImagePath
schtasks.exe /Delete /F /TN %u
"%s\system32\schtasks.exe" /Create /ST %02u:%02u /RU "NT AUTHORITY\SYSTEM" /SC ONCE /tr "%s" /Z /ET %02u:%02u /tn %s
SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList
netstat -nao
/c ping.exe -n 6 127.0.0.1 & type "%s\System32\calc.exe" > "%s"
nslookup -querytype=ALL -timeout=12 _ldap._tcp.dc._msdcs.%s
/t5
whoami /all
Self check ok!
ProgramData
powershell.exe -encodedCommand %S
89210af9
3c91e639
%s "$%s = \"%s\"; & $%s"
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
ERROR: GetModuleFileNameW() failed with error: %u
ipconfig /all
schtasks.exe /Create /RU "NT AUTHORITY\SYSTEM" /SC ONSTART /TN %u /TR "%s" /NP /F
ERROR: GetModuleFileNameW() failed with error: ERROR_INSUFFICIENT_BUFFER
%s \"$%s = \\\"%s\\\\; & $%s\"
net localgroup
powershell.exe
cmd /c set
Microsoft
SELF_TEST_1
%SystemRoot%\explorer.exe
%ProgramFiles(x86)%\Internet Explorer\iexplore.exe
WBJ_IGNORE
*/*
SELECT * FROM Win32_Processor
root\SecurityCenter2
Caption,Description,DeviceID,Manufacturer,Name,PNPDeviceID,Service,Status
SOFTWARE\Microsoft\Microsoft AntiMalware\SpyNet
\sf2.dll
Win32_Bios
.cfg
wpcap.dll
type=0x%04X
c:\hiberfil.sysss
aaebcdeeifghiiojklmnooupqrstuuyvwxyyaz
bcrypt.dll
Win32_ComputerSystem
%SystemRoot%\SysWOW64\explorer.exe
FALSE
%S.%06d
Win32_Product
abcdefghijklmnopqrstuvwxyz
image/pjpeg
egui.exe;ekrn.exe
https
Create
%SystemRoot%\SysWOW64\msra.exe
SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
SubmitSamplesConsent
%ProgramFiles%\Internet Explorer\iexplore.exe
from
kernel32.dll
%s\system32\
\\.\pipe\
userenv.dll
ntdll.dll
ccSvcHst.exe
LocalLow
NTUSER.DAT
select
avgcsrvx.exe;avgsvcx.exe;avgcsrva.exe
Software\Microsoft
Win32_PhysicalMemory
wtsapi32.dll
ws2_32.dll
shell32.dll
Initializing database...
winsta0\default
S:(ML;;NW;;;LW)
snxhk_border_mywnd
%SystemRoot%\System32\msra.exe
TRUE
image/gif
APPDATA
vbs
image/jpeg
%SystemRoot%\SysWOW64\wermgr.exe
dwengine.exe;dwarkdaemon.exe;dwwatcher.exe
ALLUSERSPROFILE
wininet.dll
urlmon.dll
Packages
SELECT * FROM Win32_OperatingSystem
Winsta0
%SystemRoot%\SysWOW64\explorer.exe
reg.exe ADD "HKLM\%s" /f /t %s /v "%s" /d "%s"
SOFTWARE\Wow6432Node\Microsoft AntiMalware\SpyNet
Caption
ROOT\CIMV2
%SystemRoot%\System32\OneDriveSetup.exe
c:\\
aswhooka.dll
aabcdeefghiijklmnoopqrstuuvwxyyz
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")
errReturn = objProcess.Create("%s", null, nul, nul)
mpr.dll
%SystemRoot%\SysWOW64\xwizard.exe
Name
coreServiceShell.exe;PccNTMon.exe;NTRTScan.exe
Mozilla/5.0 (Windows NT 6.1; rv:77.0) Gecko/20100101 Firefox/77.0
LastBootUpTime
%SystemRoot%\System32\wermgr.exe
avp.exe;kavtray.exe
Win32_Process
1234567890
%SystemRoot%\System32\mobsync.exe
rundll32.exe
fshoster32.exe
SystemRoot
advapi32.dll
SpyNetReporting
t=%s time=[%02d:%02d:%02d-%02d/%02d/%d]
SAVAdminService.exe;SavService.exe
Win32_DiskDrive
cmd.exe
%SystemRoot%\SysWOW64\mobsync.exe
.dat
open
%SystemRoot%\System32\xwizard.exe
{%02X%02X%02X%02X-%02X%02X-%02X%02X-%02X%02X-%02X%02X%02X%02X%02X%02X}
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set colFiles = objWMIService.ExecQuery("Select * From CIM_DataFile Where Name = '%s'")
For Each objFile in colFiles
objFile.Copy("%s")
Next
user32.dll
bdagent.exe;vsserv.exe;vsservppl.exe
SOFTWARE\Microsoft\Microsoft Antimalware\Exclusions\Paths
MsMpEng.exe
Caption,Description,Vendor,Version,InstallDate,InstallSource,PackageName
.dll
setupapi.dll
WRSA.exe
System32
application/x-shockwave-flash
netapi32.dll
SysWOW64
frida-winjector-helper-32.exe;frida-winjector-helper-64.exe;tcpdump.exe;windump.exe;ethereal.exe;wireshark.exe;ettercap.exe;rtsniff.exe;packetcapture.exe;capturenet.exe;qak_proxy;dumpcap.exe;CFF Explorer.exe;not_rundll32.exe;ProcessHacker.exe;tcpview.exe;filemon.exe;procmon.exe;idaq64.exe;PETools.ex...
WScript.Sleep %u
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")
errReturn = objProcess.Create("%s", null, nul, nul)
WSCript.Sleep 2000
Set fso = CreateObject("Scripting.FileSystemObject")...
vkise.exe;isesrv.exe;cmdagent.exe
MBAMService.exe;mbamgui.exe
iphlpapi.dll
SOFTWARE\Microsoft\Windows Defender\SpyNet
CommandLine
wbj.go
shlwapi.dll
Win32_PnPEntity
cscript.exe
LOCALAPPDATA
C:\INTERNAL\__empty
SELECT * FROM AntiVirusProduct
aswhookx.dll
%SystemRoot%\explorer.exe
mcshield.exe
.exe
pstorec.dll
%SystemRoot%\SysWOW64\OneDriveSetup.exe
wmic process call create 'expand "%S" "%S"'
fmon.exe
Content-Type: application/x-www-form-urlencoded
displayName
AvastSvc.exe
ByteFence.exe
SOFTWARE\Wow6432Node\Microsoft\Windows Defender\Spynet
WQL
crypt32.dll
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
Total processes
49
Monitored processes
10
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | "C:\Program Files\Internet Explorer\iexplore.exe" "C:\Users\admin\AppData\Local\Temp\Claim_Copy_3657_Sep_20.html" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
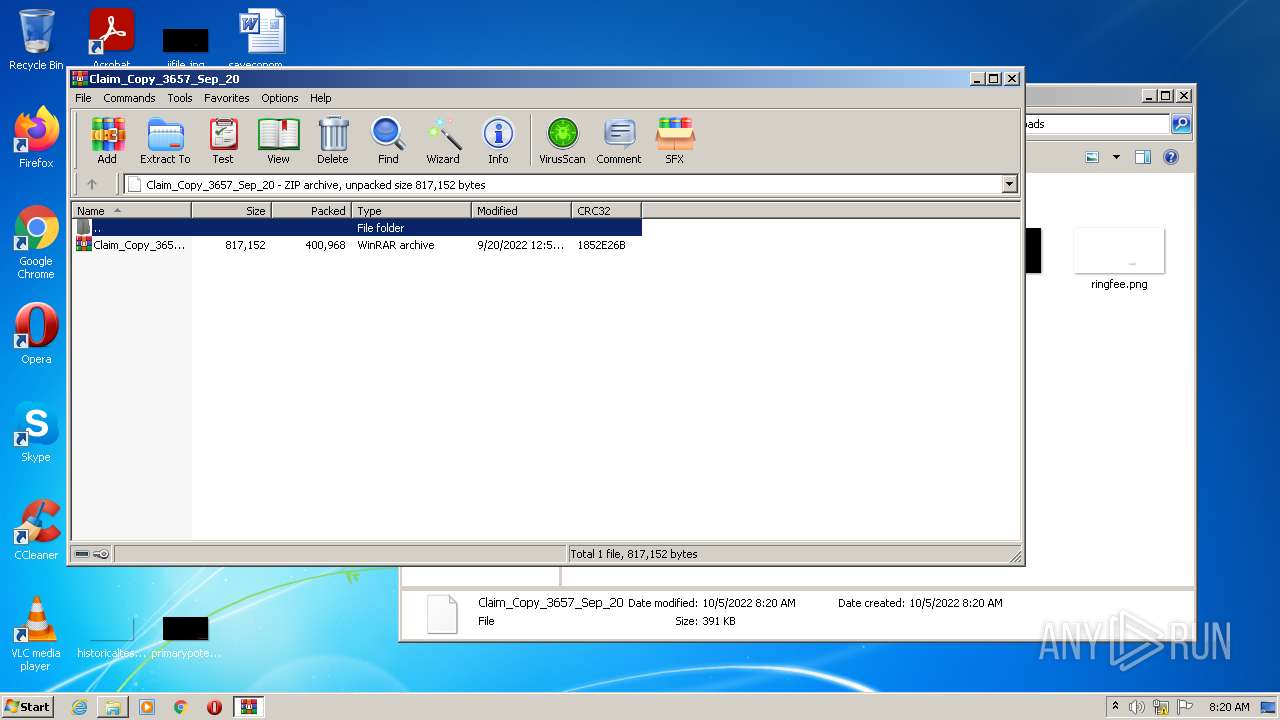
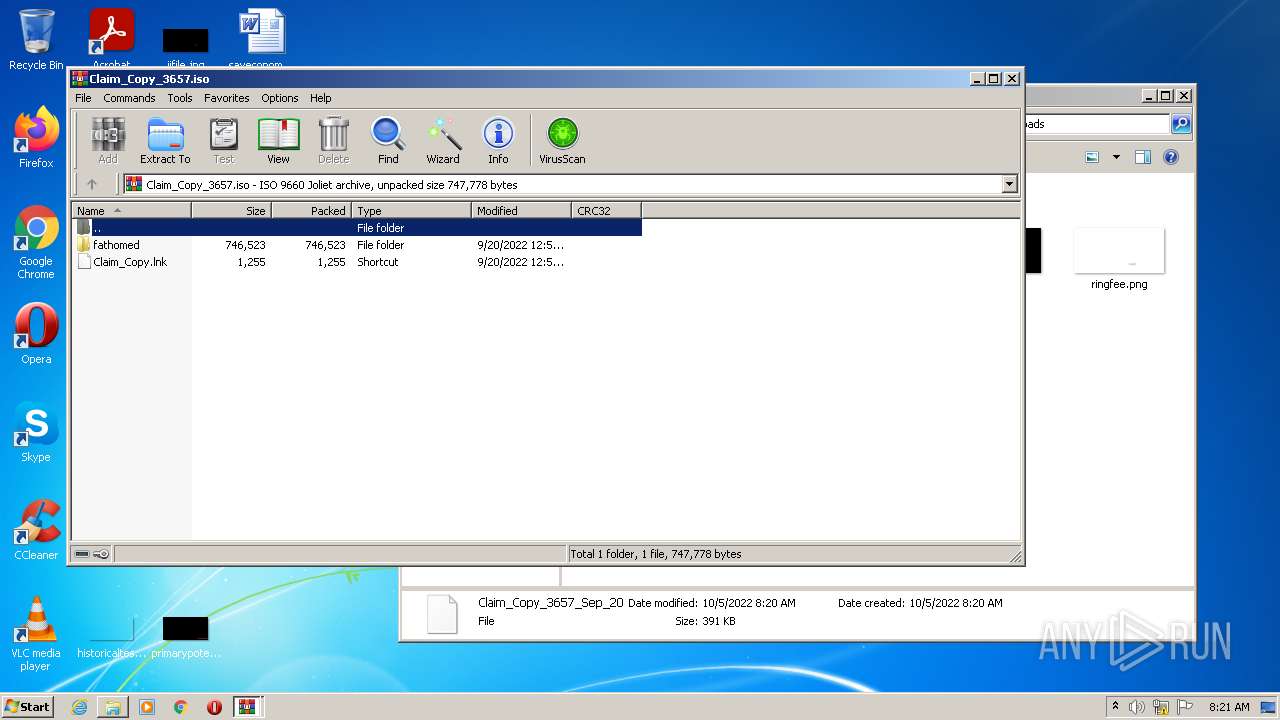
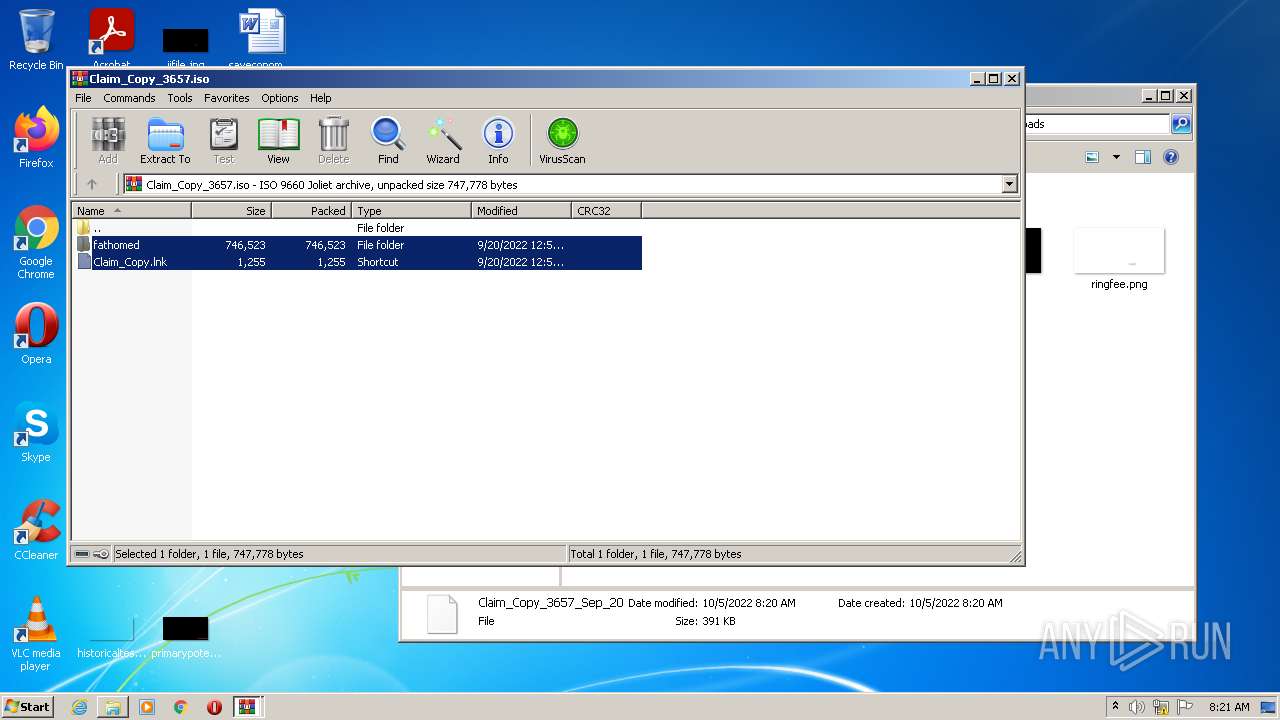
| 404 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Claim_Copy_3657_Sep_20" | C:\Program Files\WinRAR\WinRAR.exe | — | rundll32.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 684 | regsvr32 fathomed\colloquia.db | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:276 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1816 | C:\Windows\explorer.exe | C:\Windows\explorer.exe | regsvr32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
Qbot(PID) Process(1816) explorer.exe Botnetobama206 Campaign1663660089 Version1027.894 C2 (150)119.82.111.158:443 66.181.164.43:443 181.118.183.123:443 88.245.168.200:2222 70.49.33.200:2222 193.3.19.37:443 99.232.140.205:2222 110.4.255.247:443 134.35.9.144:443 89.211.217.38:995 64.207.215.69:443 83.110.219.59:993 197.94.84.128:443 177.255.14.99:995 41.103.226.172:443 109.155.5.164:993 190.44.40.48:995 187.205.222.100:443 41.107.78.223:995 191.97.234.238:995 76.169.76.44:2222 70.51.132.197:2222 189.19.189.222:32101 72.88.245.71:443 173.218.180.91:443 197.204.243.167:443 68.53.110.74:995 160.176.204.241:443 41.69.103.179:995 68.224.229.42:443 100.1.5.250:995 194.166.205.204:995 88.232.207.24:443 14.183.63.12:443 89.211.223.138:2222 85.98.206.165:995 191.254.74.89:32101 72.66.96.129:995 176.42.245.2:995 31.54.39.153:2078 186.154.92.181:443 88.231.221.198:995 102.38.97.229:995 45.51.148.111:993 87.243.113.104:995 84.38.133.191:443 123.240.131.1:443 180.180.131.95:443 191.84.204.214:995 91.116.160.252:443 151.234.63.48:990 99.253.251.74:443 154.181.203.230:995 85.114.110.108:443 186.105.182.127:443 71.10.27.196:2222 71.10.27.196:2222 47.146.182.110:443 194.49.79.231:443 88.242.228.16:53 88.231.221.198:443 141.164.254.35:443 196.92.172.24:8443 186.50.245.74:995 78.182.113.80:443 41.96.171.218:443 154.246.182.210:443 81.214.220.237:443 95.136.41.50:443 84.38.133.191:443 190.158.58.236:443 105.99.80.23:443 102.184.151.194:995 181.127.138.30:443 167.60.82.242:995 196.112.34.71:443 88.251.38.53:443 37.37.206.87:995 37.76.197.124:443 188.157.6.170:443 68.50.190.55:443 181.111.20.201:443 31.166.116.171:443 84.238.253.171:443 197.49.50.44:443 160.152.135.188:2222 45.160.124.211:995 113.22.102.155:443 211.248.176.4:443 186.167.249.206:443 139.195.132.210:2222 182.213.208.5:443 201.177.163.176:443 45.183.234.180:443 98.180.234.228:443 184.82.110.50:995 179.24.245.193:995 94.99.110.157:995 181.56.125.32:443 119.42.124.18:443 181.231.229.133:443 2.89.78.130:993 70.81.121.237:2222 181.81.116.144:443 197.11.128.156:443 41.142.132.190:443 105.111.60.60:995 154.238.151.197:995 156.219.49.22:995 179.223.89.154:995 102.101.231.141:443 220.116.250.45:443 138.0.114.166:443 62.114.193.186:995 85.98.46.114:443 184.99.123.118:443 186.120.58.88:443 46.186.216.41:32100 156.213.107.29:995 27.73.215.46:32102 68.151.196.147:995 68.129.232.158:443 45.241.140.181:995 212.156.51.194:443 87.75.195.211:443 1.10.253.207:443 87.220.229.164:2222 109.200.165.82:443 41.105.197.244:443 190.59.247.136:995 219.69.103.199:443 61.105.45.244:443 105.105.104.0:443 169.1.47.111:443 210.195.18.76:2222 118.174.200.169:995 88.246.170.2:443 171.248.157.128:995 118.68.220.199:443 139.195.63.45:2222 118.216.99.232:443 181.80.133.202:443 102.40.236.32:995 46.116.229.16:443 61.70.29.53:443 179.108.32.195:443 171.238.230.59:443 81.56.22.251:995 31.32.180.179:443 85.139.203.42:32101 Strings (188)Start screenshot at.exe %u:%u "%s" /I powershell.exe -encodedCommand amstream.dll Self check arp -a c:\ProgramData nltest /domain_trusts /all_trusts %s %04x.%u %04x.%u res: %s seh_test: %u consts_test: %d vmdetected: %d createprocess: %d Self test OK. SoNuce]ugdiB3c[doMuce2s81*uXmcvP \System32\WindowsPowerShell\v1.0\powershell.exe net view \System32\WindowsPowerShel1\v1.0\powershel1.exe error res='%s' err=%d len=%u net share qwinsta route print .lnk regsvr32.exe Self test FAILED!!! ProfileImagePath schtasks.exe /Delete /F /TN %u "%s\system32\schtasks.exe" /Create /ST %02u:%02u /RU "NT AUTHORITY\SYSTEM" /SC ONCE /tr "%s" /Z /ET %02u:%02u /tn %s SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList netstat -nao /c ping.exe -n 6 127.0.0.1 & type "%s\System32\calc.exe" > "%s" nslookup -querytype=ALL -timeout=12 _ldap._tcp.dc._msdcs.%s /t5 whoami /all Self check ok! ProgramData powershell.exe -encodedCommand %S 89210af9 3c91e639 %s "$%s = \"%s\"; & $%s" SOFTWARE\Microsoft\Windows\CurrentVersion\Run ERROR: GetModuleFileNameW() failed with error: %u ipconfig /all schtasks.exe /Create /RU "NT AUTHORITY\SYSTEM" /SC ONSTART /TN %u /TR "%s" /NP /F ERROR: GetModuleFileNameW() failed with error: ERROR_INSUFFICIENT_BUFFER %s \"$%s = \\\"%s\\\\; & $%s\" net localgroup powershell.exe cmd /c set Microsoft SELF_TEST_1 %SystemRoot%\explorer.exe %ProgramFiles(x86)%\Internet Explorer\iexplore.exe WBJ_IGNORE */* SELECT * FROM Win32_Processor root\SecurityCenter2 Caption,Description,DeviceID,Manufacturer,Name,PNPDeviceID,Service,Status SOFTWARE\Microsoft\Microsoft AntiMalware\SpyNet \sf2.dll Win32_Bios .cfg wpcap.dll type=0x%04X c:\hiberfil.sysss aaebcdeeifghiiojklmnooupqrstuuyvwxyyaz bcrypt.dll Win32_ComputerSystem %SystemRoot%\SysWOW64\explorer.exe FALSE %S.%06d Win32_Product abcdefghijklmnopqrstuvwxyz image/pjpeg egui.exe;ekrn.exe https Create %SystemRoot%\SysWOW64\msra.exe SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths SubmitSamplesConsent %ProgramFiles%\Internet Explorer\iexplore.exe from kernel32.dll %s\system32\ \\.\pipe\ userenv.dll ntdll.dll ccSvcHst.exe LocalLow NTUSER.DAT select avgcsrvx.exe;avgsvcx.exe;avgcsrva.exe Software\Microsoft Win32_PhysicalMemory wtsapi32.dll ws2_32.dll shell32.dll Initializing database... winsta0\default S:(ML;;NW;;;LW) snxhk_border_mywnd %SystemRoot%\System32\msra.exe TRUE image/gif APPDATA vbs image/jpeg %SystemRoot%\SysWOW64\wermgr.exe dwengine.exe;dwarkdaemon.exe;dwwatcher.exe ALLUSERSPROFILE wininet.dll urlmon.dll Packages SELECT * FROM Win32_OperatingSystem Winsta0 %SystemRoot%\SysWOW64\explorer.exe reg.exe ADD "HKLM\%s" /f /t %s /v "%s" /d "%s" SOFTWARE\Wow6432Node\Microsoft AntiMalware\SpyNet Caption ROOT\CIMV2 %SystemRoot%\System32\OneDriveSetup.exe c:\\ aswhooka.dll aabcdeefghiijklmnoopqrstuuvwxyyz Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")
errReturn = objProcess.Create("%s", null, nul, nul) mpr.dll %SystemRoot%\SysWOW64\xwizard.exe Name coreServiceShell.exe;PccNTMon.exe;NTRTScan.exe Mozilla/5.0 (Windows NT 6.1; rv:77.0) Gecko/20100101 Firefox/77.0 LastBootUpTime %SystemRoot%\System32\wermgr.exe avp.exe;kavtray.exe Win32_Process 1234567890 %SystemRoot%\System32\mobsync.exe rundll32.exe fshoster32.exe SystemRoot advapi32.dll SpyNetReporting t=%s time=[%02d:%02d:%02d-%02d/%02d/%d] SAVAdminService.exe;SavService.exe Win32_DiskDrive cmd.exe %SystemRoot%\SysWOW64\mobsync.exe .dat open %SystemRoot%\System32\xwizard.exe {%02X%02X%02X%02X-%02X%02X-%02X%02X-%02X%02X-%02X%02X%02X%02X%02X%02X} Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set colFiles = objWMIService.ExecQuery("Select * From CIM_DataFile Where Name = '%s'")
For Each objFile in colFiles
objFile.Copy("%s")
Next user32.dll bdagent.exe;vsserv.exe;vsservppl.exe SOFTWARE\Microsoft\Microsoft Antimalware\Exclusions\Paths MsMpEng.exe Caption,Description,Vendor,Version,InstallDate,InstallSource,PackageName .dll setupapi.dll WRSA.exe System32 application/x-shockwave-flash netapi32.dll SysWOW64 frida-winjector-helper-32.exe;frida-winjector-helper-64.exe;tcpdump.exe;windump.exe;ethereal.exe;wireshark.exe;ettercap.exe;rtsniff.exe;packetcapture.exe;capturenet.exe;qak_proxy;dumpcap.exe;CFF Explorer.exe;not_rundll32.exe;ProcessHacker.exe;tcpview.exe;filemon.exe;procmon.exe;idaq64.exe;PETools.ex... WScript.Sleep %u
Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\%coot\cimv2")
Set objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")
errReturn = objProcess.Create("%s", null, nul, nul)
WSCript.Sleep 2000
Set fso = CreateObject("Scripting.FileSystemObject")... vkise.exe;isesrv.exe;cmdagent.exe MBAMService.exe;mbamgui.exe iphlpapi.dll SOFTWARE\Microsoft\Windows Defender\SpyNet CommandLine wbj.go shlwapi.dll Win32_PnPEntity cscript.exe LOCALAPPDATA C:\INTERNAL\__empty SELECT * FROM AntiVirusProduct aswhookx.dll %SystemRoot%\explorer.exe mcshield.exe .exe pstorec.dll %SystemRoot%\SysWOW64\OneDriveSetup.exe wmic process call create 'expand "%S" "%S"' fmon.exe Content-Type: application/x-www-form-urlencoded displayName AvastSvc.exe ByteFence.exe SOFTWARE\Wow6432Node\Microsoft\Windows Defender\Spynet WQL crypt32.dll | |||||||||||||||
| 2904 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\fathomed\hibernatesCrowd.js" | C:\Windows\System32\WScript.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3164 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:276 CREDAT:333057 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
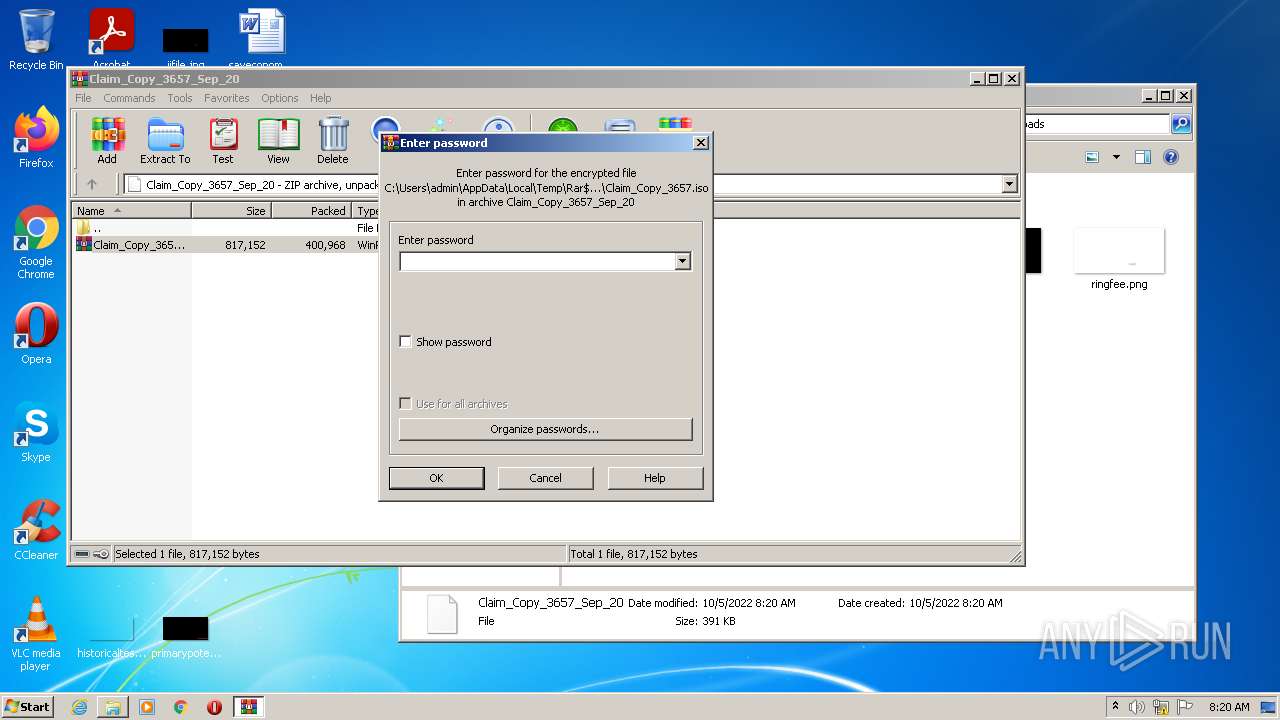
| 3412 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb404.10338\Claim_Copy_3657.iso | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3872 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\fathomed\bulkedBussing.cmd" regsv" | C:\Windows\system32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3976 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Downloads\Claim_Copy_3657_Sep_20 | C:\Windows\system32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
23 119
Read events
22 745
Write events
371
Delete events
3
Modification events
| (PID) Process: | (276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30988426 | |||
| (PID) Process: | (276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30988426 | |||
| (PID) Process: | (276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (276) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
13
Text files
8
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:— | SHA256:— | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | der | |
MD5:— | SHA256:— | |||
| 276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\d[1] | woff | |
MD5:EE10AE517D40542F597A9E0E2852B52B | SHA256:ED1815F9829E1F6A710FCDC182613F614F4887E39281E095360BEEC1CCC72348 | |||
| 1116 | iexplore.exe | C:\Users\admin\Downloads\Claim_Copy_3657_Sep_20.gytlj9w.partial | compressed | |
MD5:— | SHA256:— | |||
| 276 | iexplore.exe | C:\Users\admin\Downloads\Claim_Copy_3657_Sep_20 | compressed | |
MD5:— | SHA256:— | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Claim_Copy_3657_Sep_20[1] | compressed | |
MD5:— | SHA256:— | |||
| 276 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1116 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | US | der | 471 b | whitelisted |
276 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
276 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
1116 | iexplore.exe | GET | 200 | 23.216.77.80:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b9ada3503f7f829e | US | compressed | 4.70 Kb | whitelisted |
1116 | iexplore.exe | GET | 200 | 23.216.77.80:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?831122cd13fc2ce2 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1116 | iexplore.exe | 184.24.77.156:443 | use.typekit.net | Akamai International B.V. | DE | suspicious |
1116 | iexplore.exe | 23.216.77.80:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | suspicious |
1116 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
276 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
276 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
276 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
use.typekit.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |