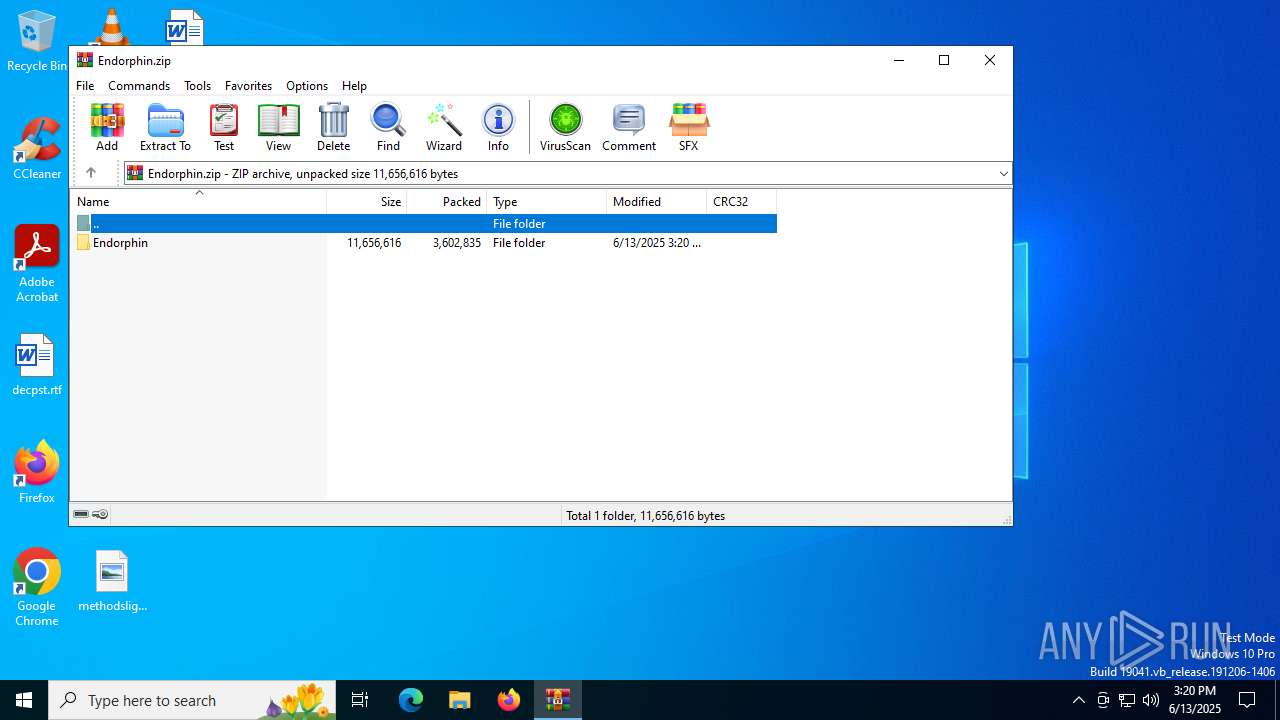
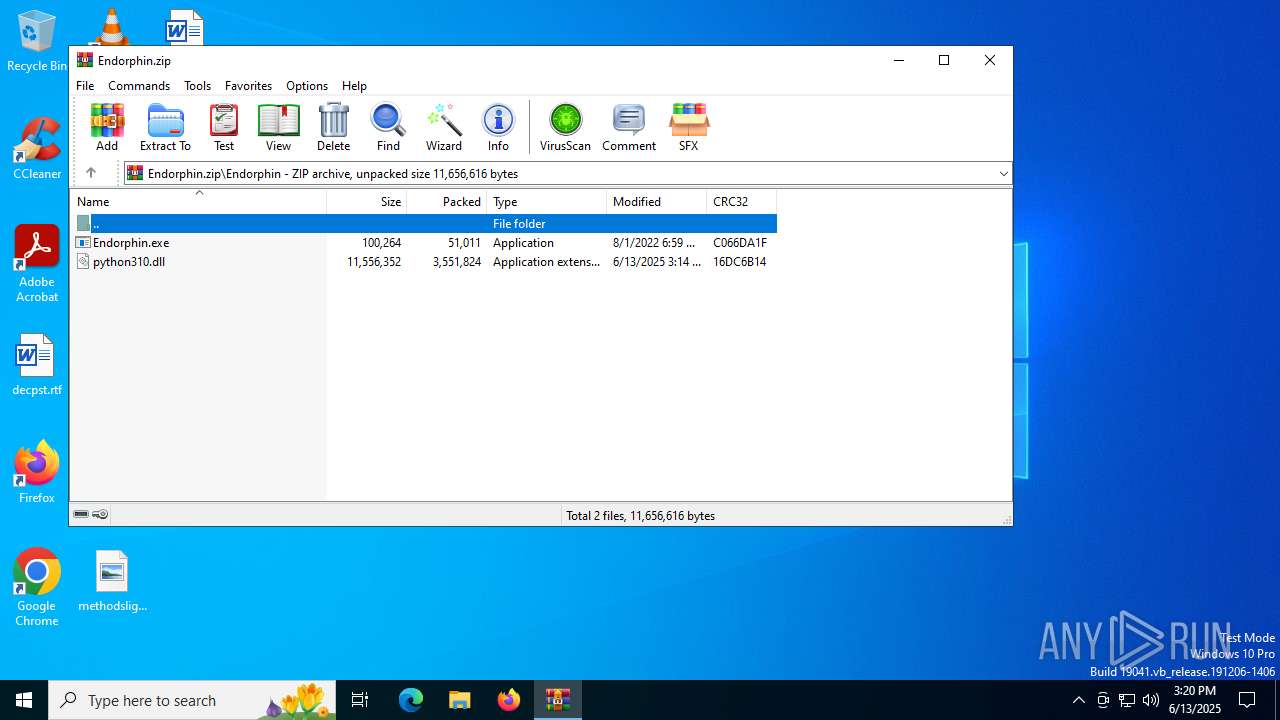
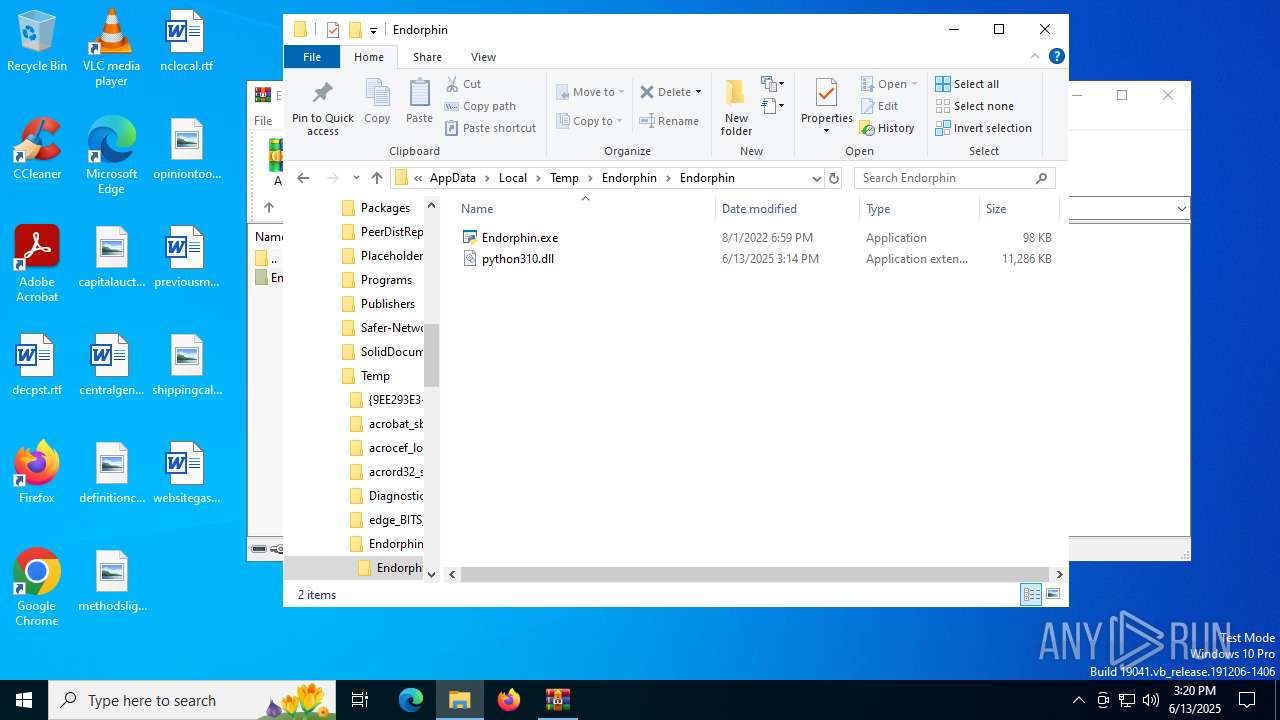
| File name: | Endorphin.zip |
| Full analysis: | https://app.any.run/tasks/0be32276-fb01-4bf0-94ba-c3b6d7a71416 |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | June 13, 2025, 15:20:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 9083037FD5CF7A99C040FB4628A982CC |
| SHA1: | 59FC5D6E2005317B18C3104735DC1B0916379F75 |
| SHA256: | C9C14B26A09336BBECCB7BED5F031381934F9D16E2A480C0D3BA0E8D820870F6 |
| SSDEEP: | 98304:UE3N8oKBagZnhBIpL9YLpZEd9k+kxlfO5djifihe0XbclD7XvQz30PenT+IvxYeR:a4qHe1sEb |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2792)
RHADAMANTHYS has been detected (YARA)
- OOBE-Maintenance.exe (PID: 6636)
Actions looks like stealing of personal data
- OOBE-Maintenance.exe (PID: 6636)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2792)
- msedge.exe (PID: 4020)
Executes application which crashes
- winhlp32.exe (PID: 1132)
- OOBE-Maintenance.exe (PID: 6636)
The process checks if it is being run in the virtual environment
- OpenWith.exe (PID: 5952)
Reads Mozilla Firefox installation path
- msedge.exe (PID: 4020)
Loads DLL from Mozilla Firefox
- OOBE-Maintenance.exe (PID: 6636)
Searches for installed software
- OOBE-Maintenance.exe (PID: 6636)
Connects to unusual port
- dllhost.exe (PID: 7640)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 2792)
Manual execution by a user
- Endorphin.exe (PID: 856)
- OOBE-Maintenance.exe (PID: 6636)
- OpenWith.exe (PID: 5952)
Checks supported languages
- Endorphin.exe (PID: 856)
- chrome.exe (PID: 592)
- msedge.exe (PID: 4020)
- wmlaunch.exe (PID: 7604)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2792)
Python executable
- Endorphin.exe (PID: 856)
Create files in a temporary directory
- OOBE-Maintenance.exe (PID: 6636)
- chrome.exe (PID: 592)
- msedge.exe (PID: 4020)
Reads the computer name
- chrome.exe (PID: 592)
- msedge.exe (PID: 4020)
Application launched itself
- chrome.exe (PID: 592)
- msedge.exe (PID: 4020)
Reads Environment values
- chrome.exe (PID: 592)
- msedge.exe (PID: 4020)
Reads the machine GUID from the registry
- chrome.exe (PID: 592)
- msedge.exe (PID: 4020)
- wmlaunch.exe (PID: 7604)
Process checks computer location settings
- chrome.exe (PID: 592)
- msedge.exe (PID: 4020)
Checks proxy server information
- chrome.exe (PID: 592)
- msedge.exe (PID: 4020)
- slui.exe (PID: 1036)
Process checks whether UAC notifications are on
- msedge.exe (PID: 4020)
Reads the software policy settings
- slui.exe (PID: 1036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:06:13 11:20:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Endorphin/ |
Total processes
183
Monitored processes
51
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4044,i,5324784885192486848,1322275291500093737,262144 --variations-seed-version --mojo-platform-channel-handle=4060 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 592 | --user-data-dir="C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp" --explicitly-allowed-ports=8000 --disable-gpu --new-window "http://127.0.0.1:8000/2550cfd0/03a0677f" | C:\Program Files\Google\Chrome\Application\chrome.exe | OOBE-Maintenance.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 620 | "C:\Windows\winhlp32.exe" | C:\Windows\winhlp32.exe | — | Endorphin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Winhlp32 Stub Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Users\admin\AppData\Local\Temp\Endorphin\Endorphin\Endorphin.exe" | C:\Users\admin\AppData\Local\Temp\Endorphin\Endorphin\Endorphin.exe | — | explorer.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.10.6 Modules
| |||||||||||||||
| 1036 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\Windows\winhlp32.exe" | C:\Windows\winhlp32.exe | Endorphin.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Winhlp32 Stub Exit code: 3221225477 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=133.0.6943.127 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc44a0fff8,0x7ffc44a10004,0x7ffc44a10010 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --string-annotations --always-read-main-dll --field-trial-handle=4212,i,5324784885192486848,1322275291500093737,262144 --variations-seed-version --mojo-platform-channel-handle=5888 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1472 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3544,i,5324784885192486848,1322275291500093737,262144 --variations-seed-version --mojo-platform-channel-handle=3552 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1840 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --always-read-main-dll --field-trial-handle=4596,i,5324784885192486848,1322275291500093737,262144 --variations-seed-version --mojo-platform-channel-handle=4536 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
13 365
Read events
13 322
Write events
29
Delete events
14
Modification events
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Endorphin.zip | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
132
Text files
71
Unknown types
107
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 592 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\segmentation_platform\ukm_db-journal | binary | |
MD5:465B2231399DE72920A2EC61C48D4B93 | SHA256:61DF7EC6D7979A004762B773A0E35D8921194D61CAF4432AEA47EBA5E6D93F50 | |||
| 592 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\Default\Site Characteristics Database\MANIFEST-000001 | binary | |
MD5:5AF87DFD673BA2115E2FCF5CFDB727AB | SHA256:F9D31B278E215EB0D0E9CD709EDFA037E828F36214AB7906F612160FEAD4B2B4 | |||
| 592 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\Default\History-journal | — | |
MD5:— | SHA256:— | |||
| 592 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\Default\79eb85f8-fb09-4e67-af7d-09df587227c5.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 592 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\Default\Site Characteristics Database\000001.dbtmp | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
| 592 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\Default\Code Cache\js\index | binary | |
MD5:54CB446F628B2EA4A5BCE5769910512E | SHA256:FBCFE23A2ECB82B7100C50811691DDE0A33AA3DA8D176BE9882A9DB485DC0F2D | |||
| 592 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\Default\Site Characteristics Database\CURRENT | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
| 592 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\Crashpad\settings.dat | binary | |
MD5:604FE68DB3699442598AC4EAC7FB071F | SHA256:1C67719582F749446988C62EC6A417F750A7C1FF3C6150141E7A77B26DF1B936 | |||
| 592 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\Last Version | text | |
MD5:D18CE7F480944AE4E61A969D8C1E5003 | SHA256:E0CB362A73D69BAD940A018881701B5F2A8527C13C3F5ACBBEA43B8820DFC199 | |||
| 592 | chrome.exe | C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp\06c1e979-ad75-4251-b601-f9ad3c171f4f.tmp | binary | |
MD5:51D4C3678604798850F6F8403DD717BA | SHA256:B7623A89BDC75460EB6A83126A2769817B3E36DDF470381B545C7217F61EECF4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
56
DNS requests
61
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6900 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
768 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
768 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2680 | chrome.exe | GET | 200 | 216.58.206.78:80 | http://clients2.google.com/time/1/current?cup2key=8:C7hlvyNUdcwhiVz8CXjrVV_QckjOJQgNc1LZu0s9GXc&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2680 | chrome.exe | GET | 302 | 142.250.184.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | unknown | — | — | whitelisted |
3800 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:IAGT2aMSPDqh10BV4VXcO4wiqjSdnsMUJ9tOY-vPazs&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6900 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6900 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
768 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
768 | SIHClient.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5952 | OpenWith.exe | Misc activity | ET INFO Cloudflare DNS Over HTTPS Certificate Inbound |
2680 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2680 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2680 | chrome.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrB7F1.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrCC45.tmp directory exists )
|