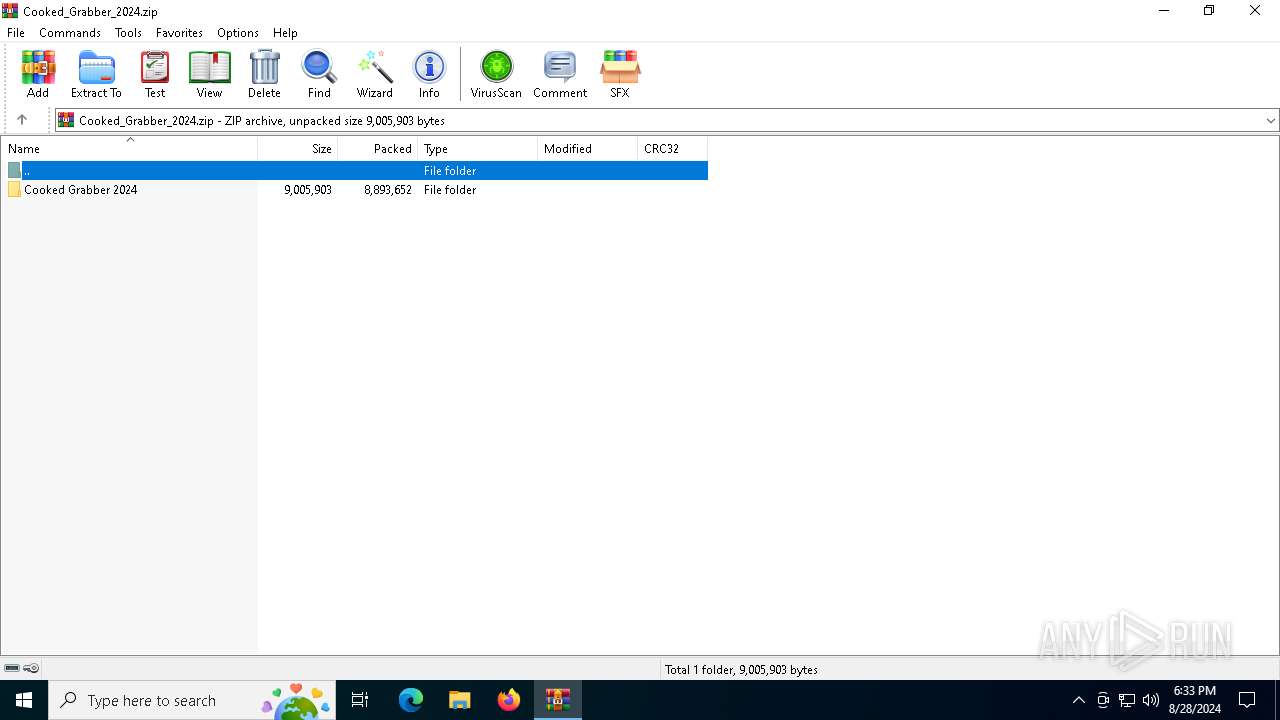
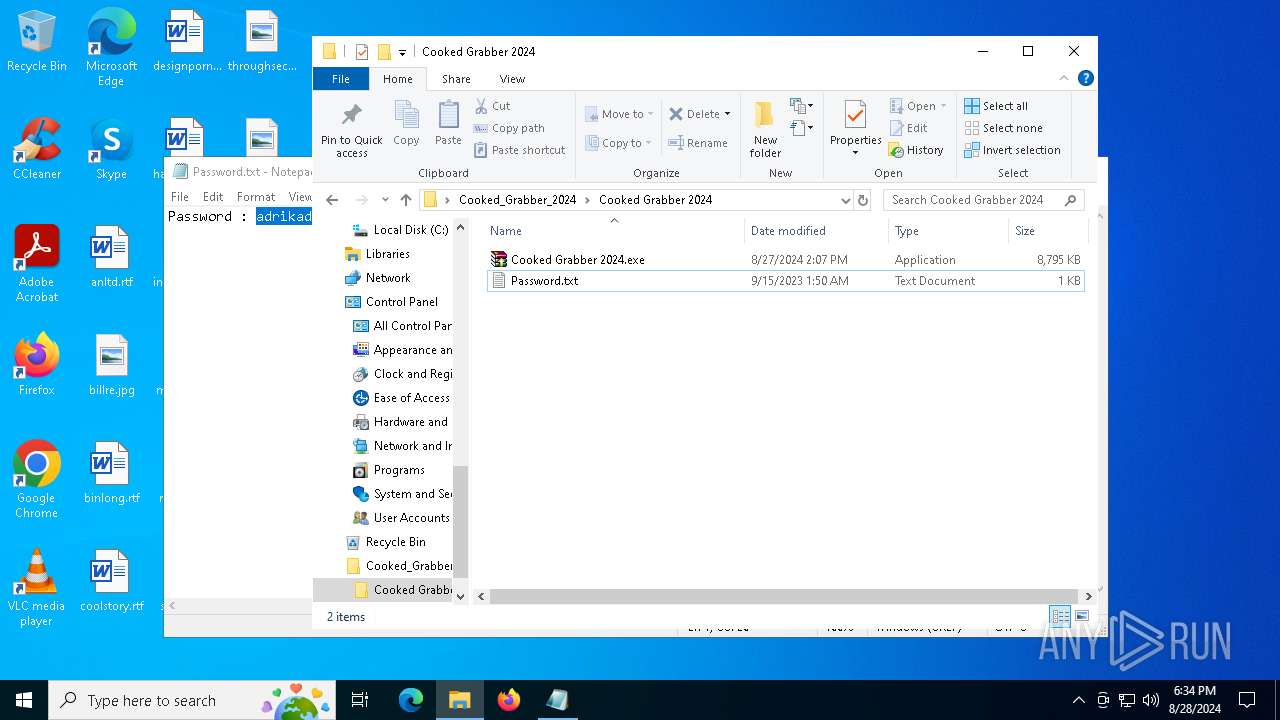
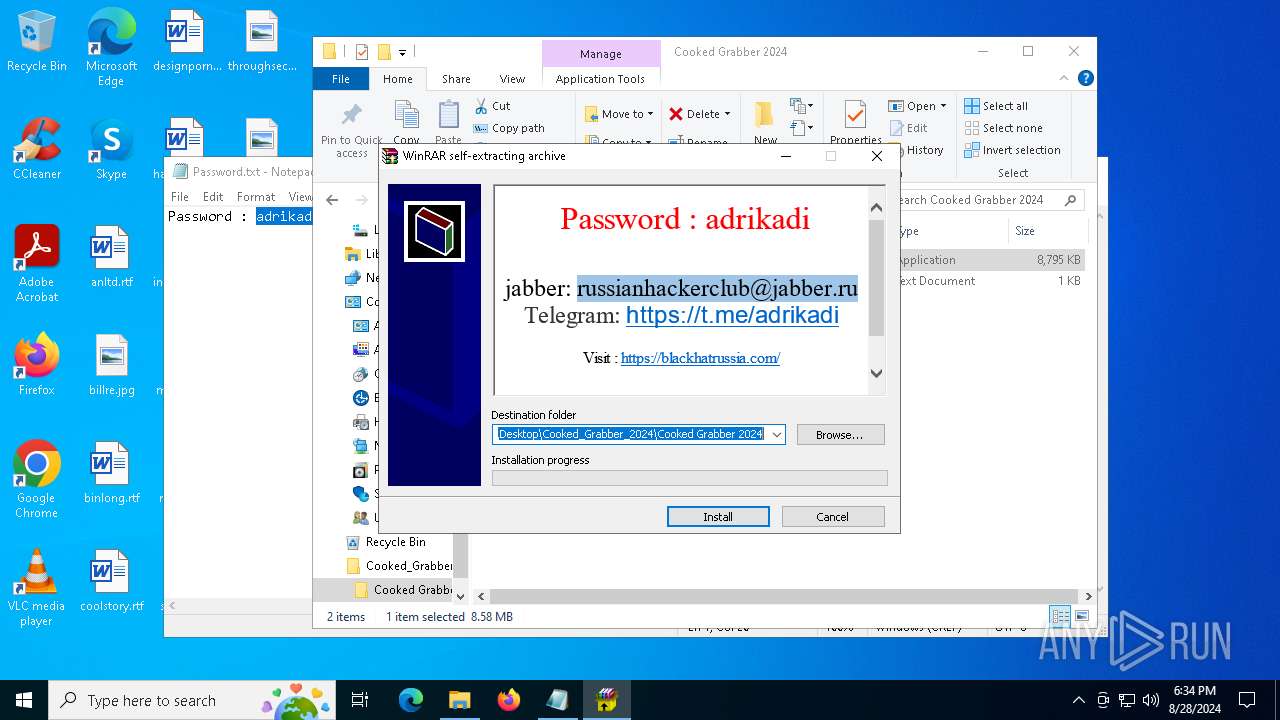
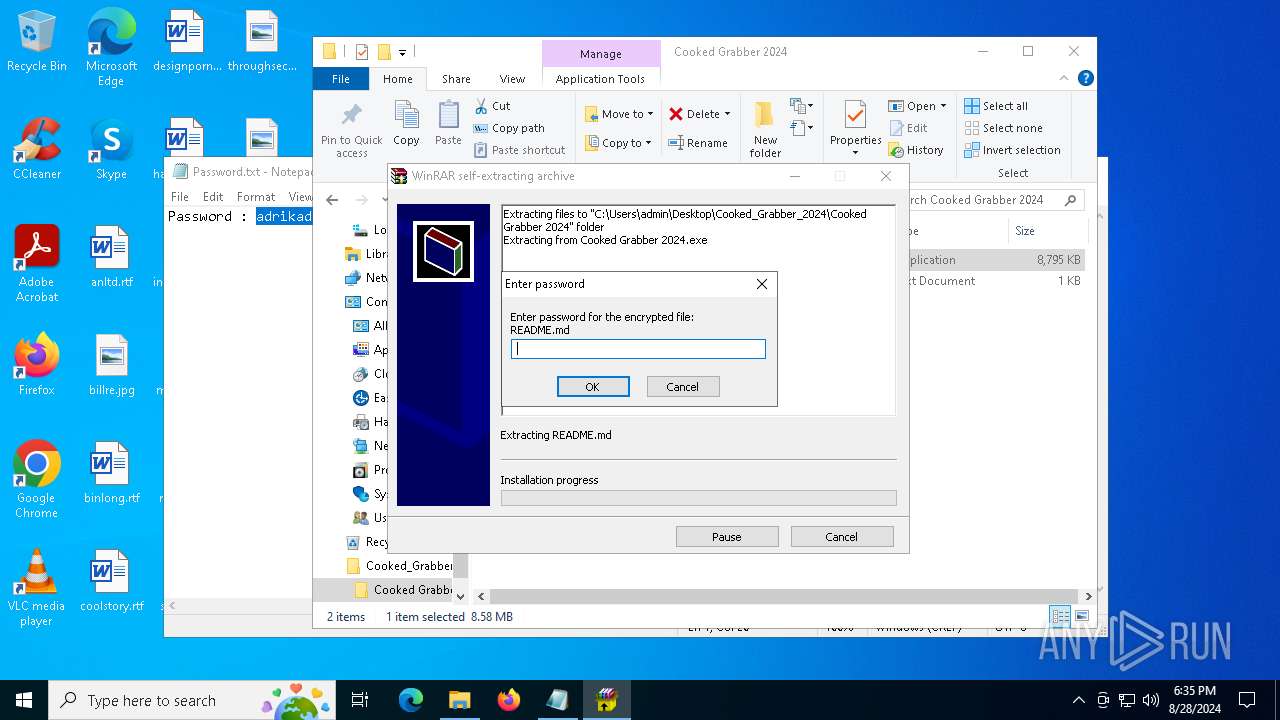
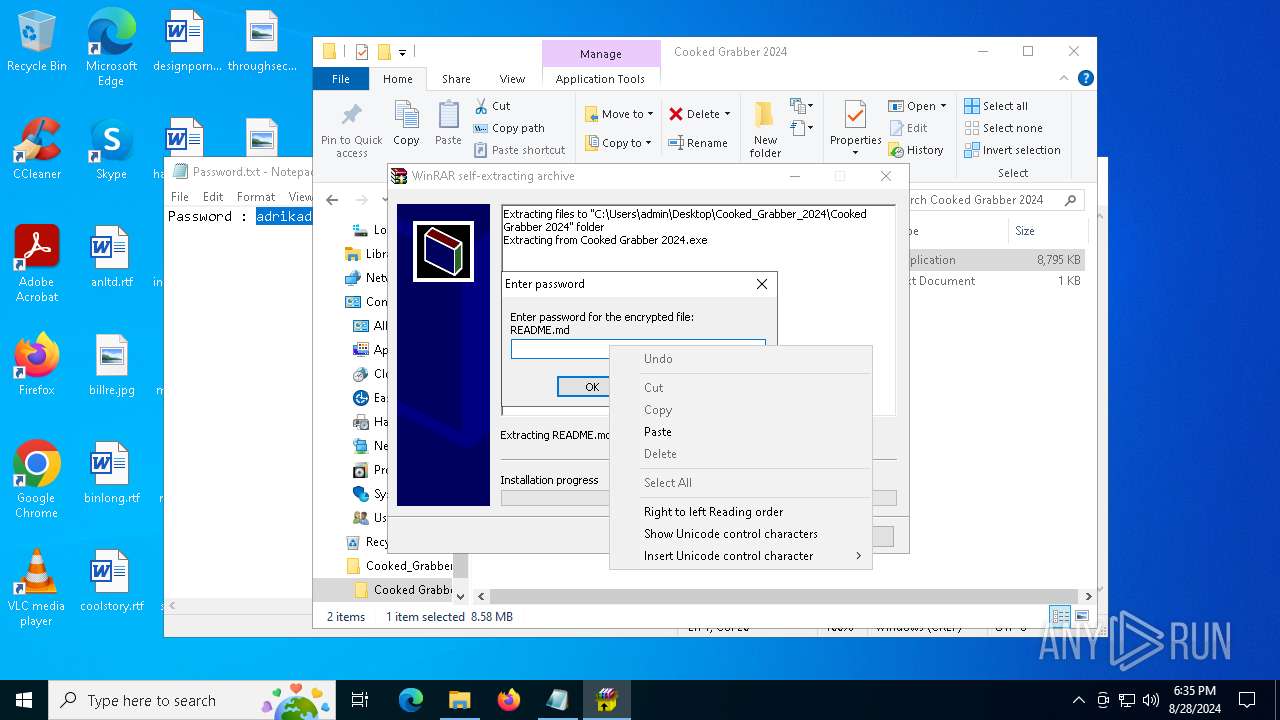
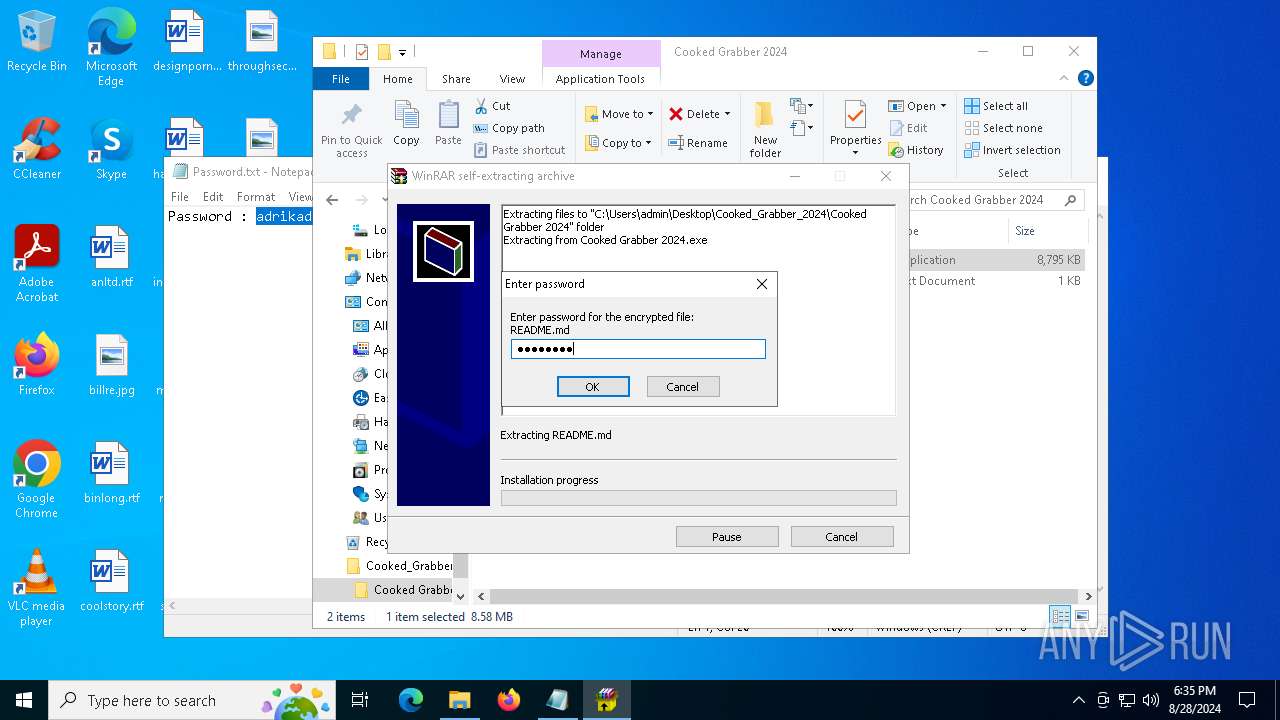
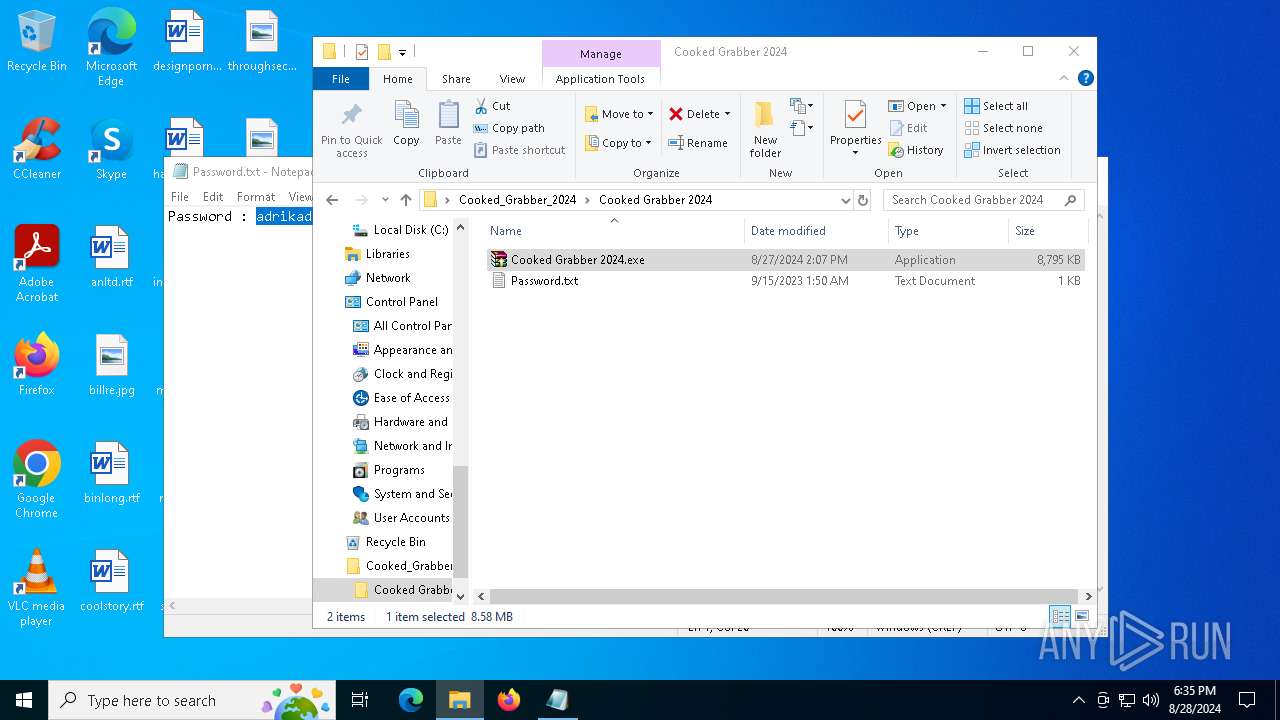
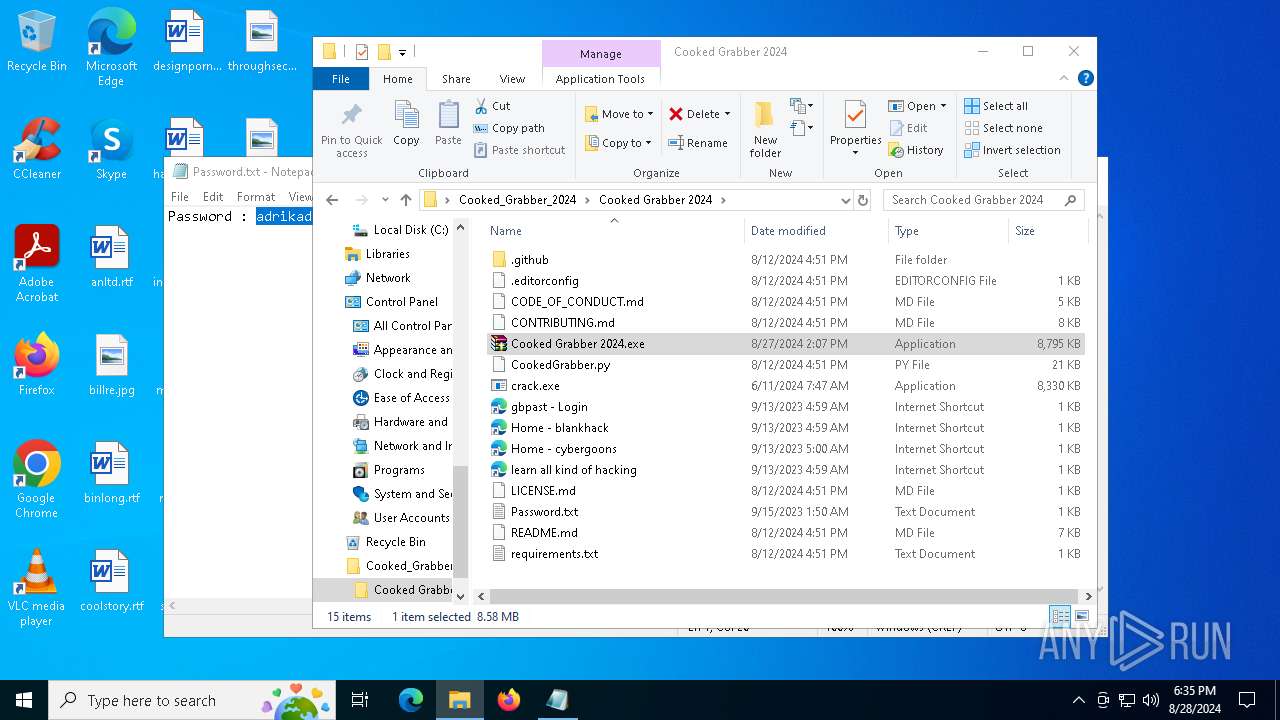
| File name: | Cooked_Grabber_2024.zip |
| Full analysis: | https://app.any.run/tasks/f6477d2f-841b-4bd6-9478-358343b5f80c |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | August 28, 2024, 18:33:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4B073709C757A3D60E266998D33AFD69 |
| SHA1: | AF9965CC0A2AA78A10869ABDFE0F68C4BB9903B9 |
| SHA256: | C8EF2CD6D64087397C64CE96442EB4DC9B6B24DB58C8AE7FE3854CC7A9D1CACF |
| SSDEEP: | 98304:Ku2m3xWjlrZ9tuElX6XL1sr7DHJtWpve//WV2GPjerV3OApj9PG7Zv0Hq/LQ8JDm:omcyJhxN+0P0X6EUEvkKp |
MALICIOUS
BlankGrabber has been detected
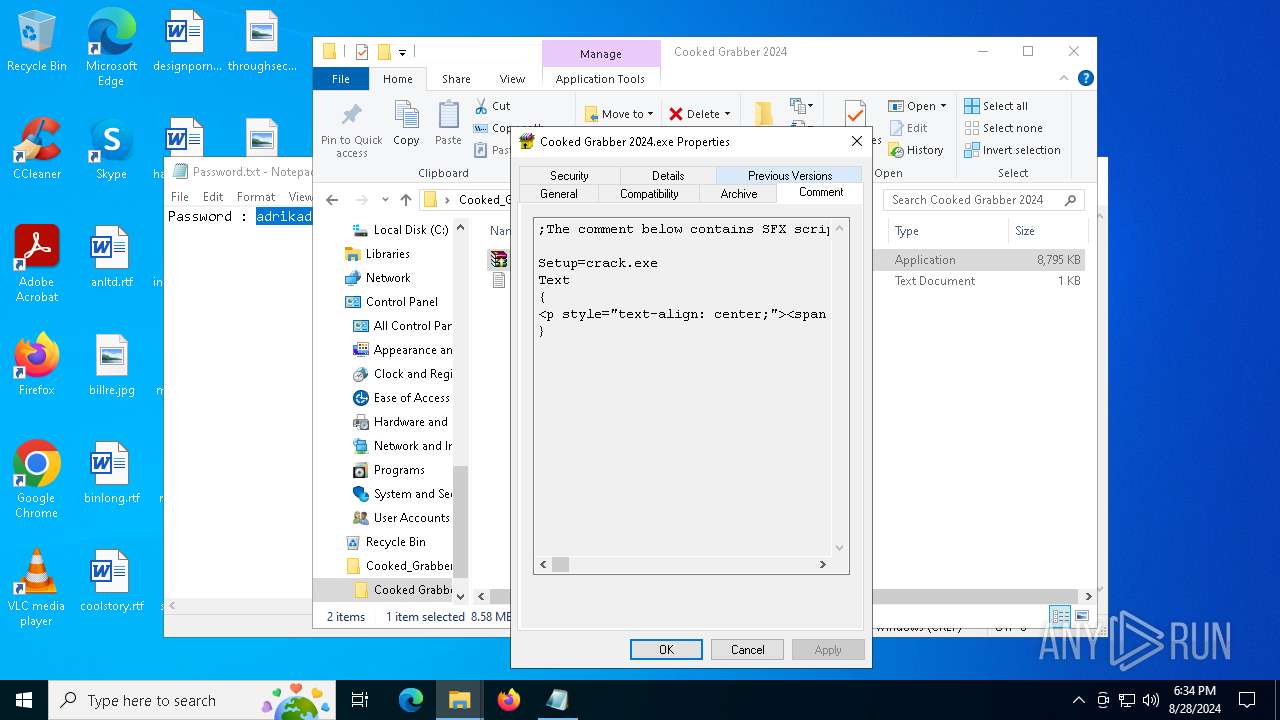
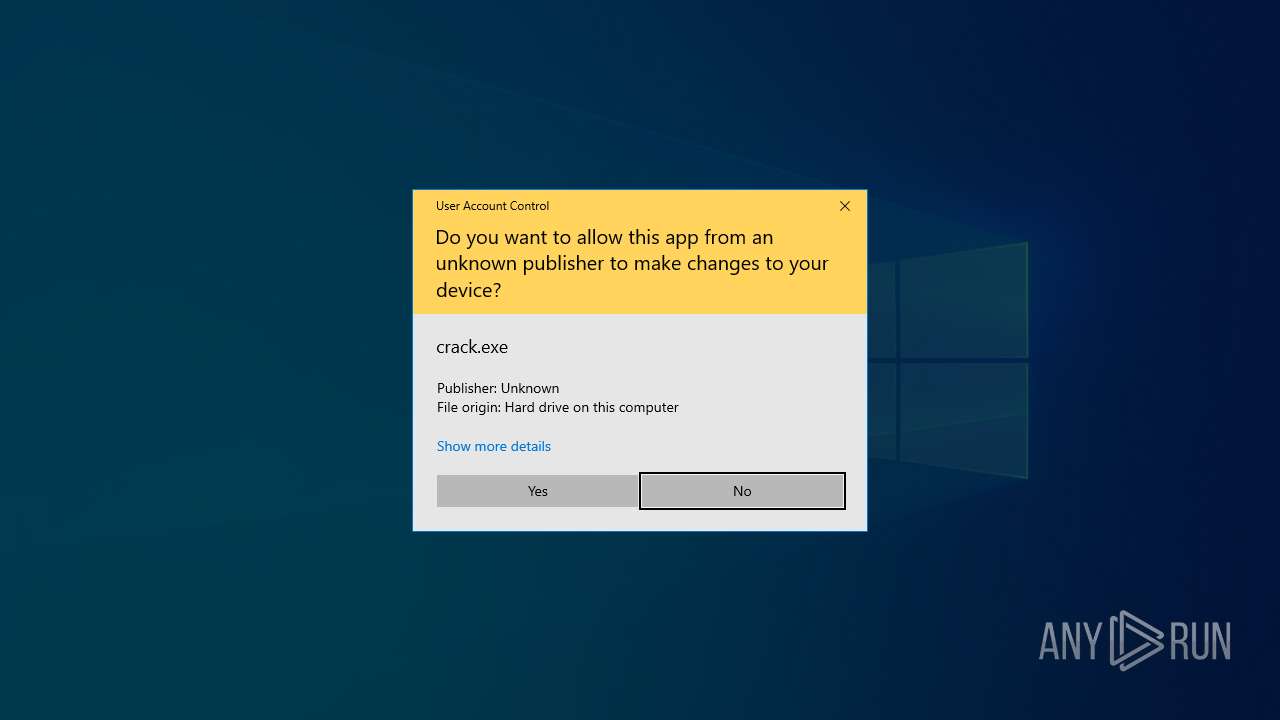
- crack.exe (PID: 6320)
- crack.exe (PID: 5612)
Create files in the Startup directory
- Payload.exe (PID: 2108)
- crack.exe (PID: 6312)
DISCORDGRABBER has been detected (YARA)
- crack.exe (PID: 4068)
- crack.exe (PID: 6312)
GROWTOPIA has been detected (YARA)
- crack.exe (PID: 4068)
- crack.exe (PID: 6312)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 2468)
- crack.exe (PID: 6312)
- cmd.exe (PID: 5624)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 2520)
- MpCmdRun.exe (PID: 1448)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 2520)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 2476)
Bypass execution policy to execute commands
- powershell.exe (PID: 3648)
Actions looks like stealing of personal data
- crack.exe (PID: 6312)
BLANKGRABBER has been detected (SURICATA)
- crack.exe (PID: 6312)
Stealers network behavior
- crack.exe (PID: 6312)
SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6744)
- Cooked Grabber 2024.exe (PID: 7156)
- crack.exe (PID: 6560)
- crack.exe (PID: 6320)
- Payload.exe (PID: 2108)
- crack.exe (PID: 5612)
- crack.exe (PID: 6312)
- csc.exe (PID: 4392)
Reads Microsoft Outlook installation path
- Cooked Grabber 2024.exe (PID: 7156)
Reads Internet Explorer settings
- Cooked Grabber 2024.exe (PID: 7156)
Reads security settings of Internet Explorer
- Cooked Grabber 2024.exe (PID: 7156)
- crack.exe (PID: 6560)
- crack.exe (PID: 4068)
Reads the date of Windows installation
- Cooked Grabber 2024.exe (PID: 7156)
- crack.exe (PID: 6560)
- crack.exe (PID: 4068)
Executable content was dropped or overwritten
- Cooked Grabber 2024.exe (PID: 7156)
- crack.exe (PID: 6560)
- Payload.exe (PID: 2108)
- crack.exe (PID: 6320)
- crack.exe (PID: 5612)
- crack.exe (PID: 6312)
- csc.exe (PID: 4392)
Base64-obfuscated command line is found
- crack.exe (PID: 6560)
- cmd.exe (PID: 2476)
BASE64 encoded PowerShell command has been detected
- crack.exe (PID: 6560)
- cmd.exe (PID: 2476)
Starts POWERSHELL.EXE for commands execution
- crack.exe (PID: 6560)
- cmd.exe (PID: 2520)
- cmd.exe (PID: 2468)
- cmd.exe (PID: 5624)
- cmd.exe (PID: 2476)
- cmd.exe (PID: 4364)
- cmd.exe (PID: 6328)
- cmd.exe (PID: 1944)
- cmd.exe (PID: 5160)
- cmd.exe (PID: 5768)
The process drops C-runtime libraries
- crack.exe (PID: 6320)
- crack.exe (PID: 5612)
Process drops legitimate windows executable
- crack.exe (PID: 6560)
- crack.exe (PID: 6320)
- crack.exe (PID: 5612)
- crack.exe (PID: 6312)
Starts a Microsoft application from unusual location
- crack.exe (PID: 6320)
- crack.exe (PID: 4068)
- crack.exe (PID: 5612)
- crack.exe (PID: 6312)
Process drops python dynamic module
- crack.exe (PID: 6320)
- crack.exe (PID: 5612)
Application launched itself
- crack.exe (PID: 6320)
- crack.exe (PID: 4068)
- crack.exe (PID: 5612)
Found regular expressions for crypto-addresses (YARA)
- Payload.exe (PID: 2108)
Starts CMD.EXE for commands execution
- crack.exe (PID: 6312)
Found strings related to reading or modifying Windows Defender settings
- crack.exe (PID: 6312)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 2520)
Script disables Windows Defender's IPS
- cmd.exe (PID: 2520)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 2468)
- cmd.exe (PID: 5624)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 6456)
Get information on the list of running processes
- cmd.exe (PID: 6040)
- crack.exe (PID: 6312)
- cmd.exe (PID: 6016)
- cmd.exe (PID: 5304)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 252)
- cmd.exe (PID: 6040)
Starts application with an unusual extension
- cmd.exe (PID: 6320)
- cmd.exe (PID: 5288)
- cmd.exe (PID: 2400)
- cmd.exe (PID: 2524)
- cmd.exe (PID: 5744)
- cmd.exe (PID: 4168)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 2476)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 3908)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 7020)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 3964)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 5212)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 5064)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 2876)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 4668)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 5760)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 1280)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 2960)
Checks for external IP
- crack.exe (PID: 6312)
- svchost.exe (PID: 2256)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- crack.exe (PID: 6312)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2384)
Manual execution by a user
- WinRAR.exe (PID: 2384)
- WinRAR.exe (PID: 1104)
- notepad.exe (PID: 208)
- Cooked Grabber 2024.exe (PID: 7156)
Reads security settings of Internet Explorer
- notepad.exe (PID: 208)
- WMIC.exe (PID: 3964)
- WMIC.exe (PID: 2876)
- WMIC.exe (PID: 2960)
- WMIC.exe (PID: 3104)
- WMIC.exe (PID: 5760)
Process checks Internet Explorer phishing filters
- Cooked Grabber 2024.exe (PID: 7156)
Checks proxy server information
- Cooked Grabber 2024.exe (PID: 7156)
- slui.exe (PID: 5548)
Reads the software policy settings
- slui.exe (PID: 3984)
- slui.exe (PID: 5548)
Checks supported languages
- Cooked Grabber 2024.exe (PID: 7156)
- crack.exe (PID: 6560)
- Payload.exe (PID: 2108)
- crack.exe (PID: 6320)
- crack.exe (PID: 4068)
- crack.exe (PID: 5612)
- crack.exe (PID: 6312)
- tree.com (PID: 4316)
- tree.com (PID: 368)
- tree.com (PID: 5492)
- tree.com (PID: 2584)
- tree.com (PID: 3964)
- csc.exe (PID: 4392)
- MpCmdRun.exe (PID: 1448)
- tree.com (PID: 5088)
- cvtres.exe (PID: 7072)
- rar.exe (PID: 5212)
Reads the computer name
- Cooked Grabber 2024.exe (PID: 7156)
- Payload.exe (PID: 2108)
- crack.exe (PID: 6320)
- crack.exe (PID: 6560)
- crack.exe (PID: 4068)
- crack.exe (PID: 5612)
- crack.exe (PID: 6312)
- MpCmdRun.exe (PID: 1448)
Process checks computer location settings
- Cooked Grabber 2024.exe (PID: 7156)
- crack.exe (PID: 6560)
- crack.exe (PID: 4068)
Create files in a temporary directory
- crack.exe (PID: 6560)
- crack.exe (PID: 4068)
- crack.exe (PID: 6320)
- crack.exe (PID: 5612)
- crack.exe (PID: 6312)
- MpCmdRun.exe (PID: 1448)
- csc.exe (PID: 4392)
- cvtres.exe (PID: 7072)
- rar.exe (PID: 5212)
Creates files or folders in the user directory
- Payload.exe (PID: 2108)
Reads the machine GUID from the registry
- Payload.exe (PID: 2108)
- csc.exe (PID: 4392)
- rar.exe (PID: 5212)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2628)
- powershell.exe (PID: 2648)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 6456)
- powershell.exe (PID: 5700)
- powershell.exe (PID: 1104)
PyInstaller has been detected (YARA)
- crack.exe (PID: 6320)
- crack.exe (PID: 4068)
- crack.exe (PID: 5612)
- crack.exe (PID: 6312)
Found Base64 encoded reflection usage via PowerShell (YARA)
- crack.exe (PID: 4068)
- crack.exe (PID: 6312)
UPX packer has been detected
- crack.exe (PID: 4068)
- crack.exe (PID: 6312)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2628)
- powershell.exe (PID: 2648)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 6456)
Creates files in the program directory
- crack.exe (PID: 6312)
The Powershell gets current clipboard
- powershell.exe (PID: 4440)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 4680)
Attempting to use instant messaging service
- svchost.exe (PID: 2256)
- crack.exe (PID: 6312)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:27 14:07:52 |
| ZipCRC: | 0xb69b76e1 |
| ZipCompressedSize: | 8893633 |
| ZipUncompressedSize: | 9005884 |
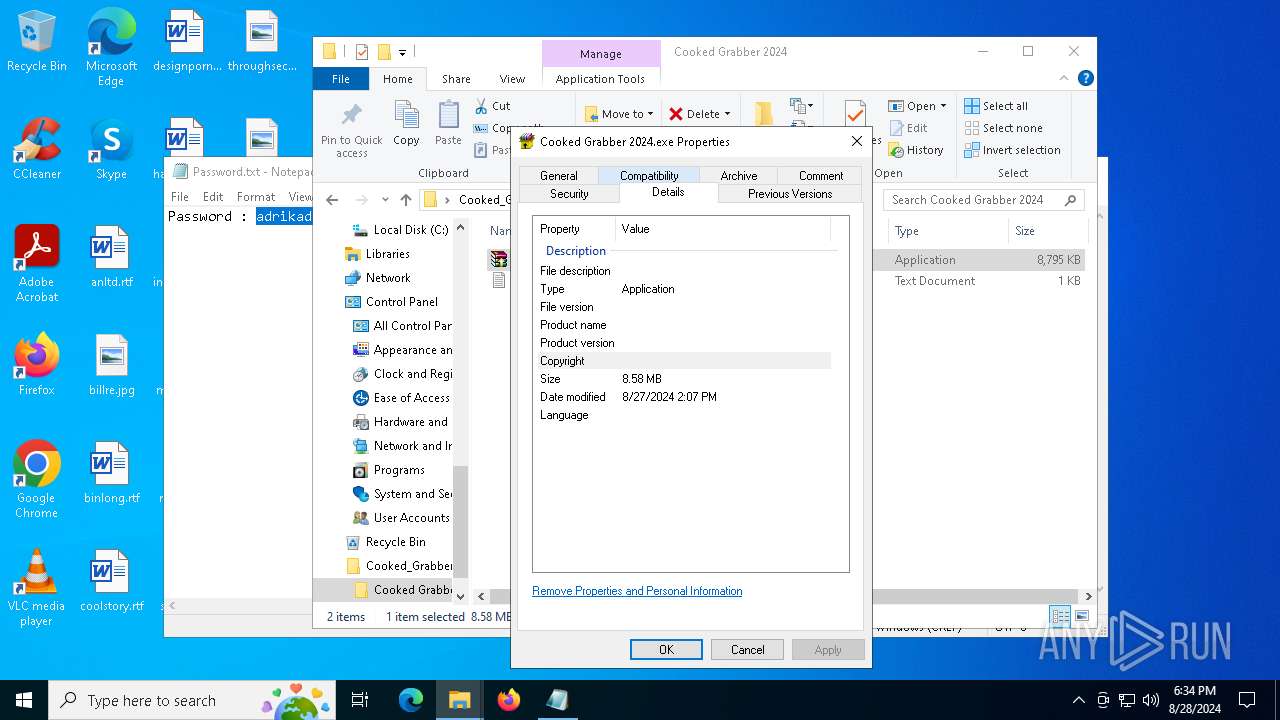
| ZipFileName: | Cooked Grabber 2024/Cooked Grabber 2024.exe |
Total processes
231
Monitored processes
103
Malicious processes
8
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
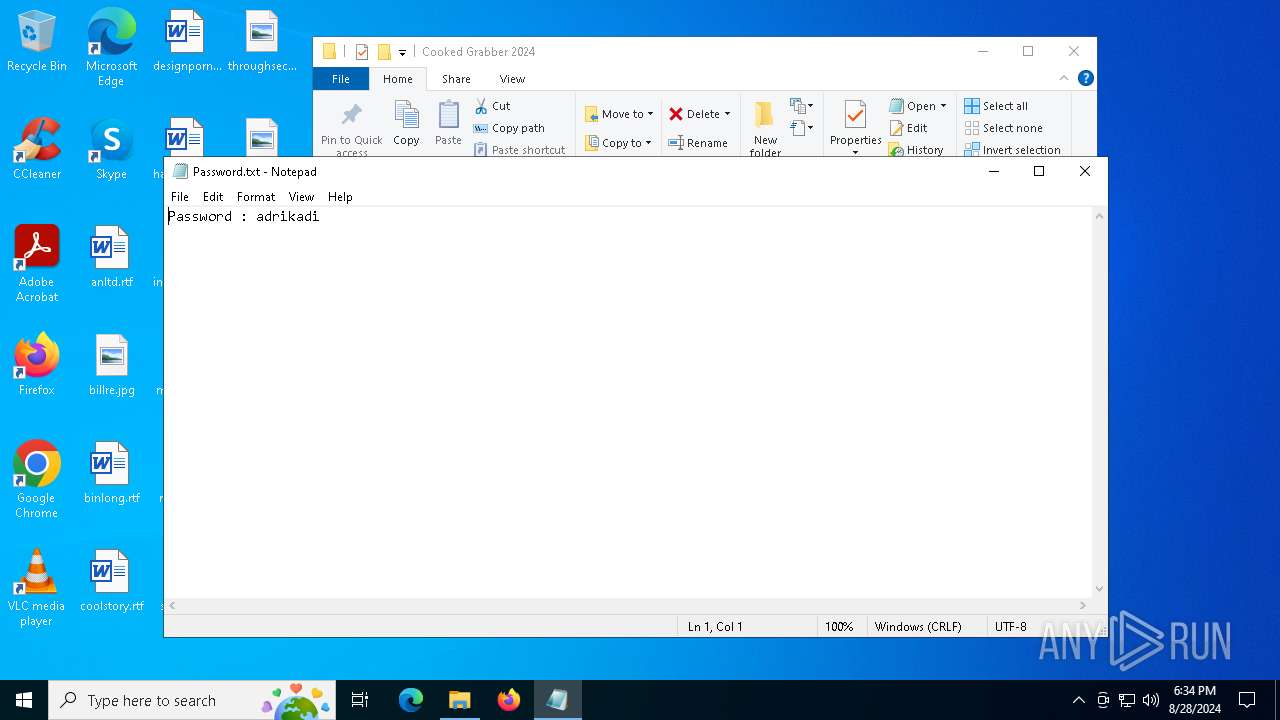
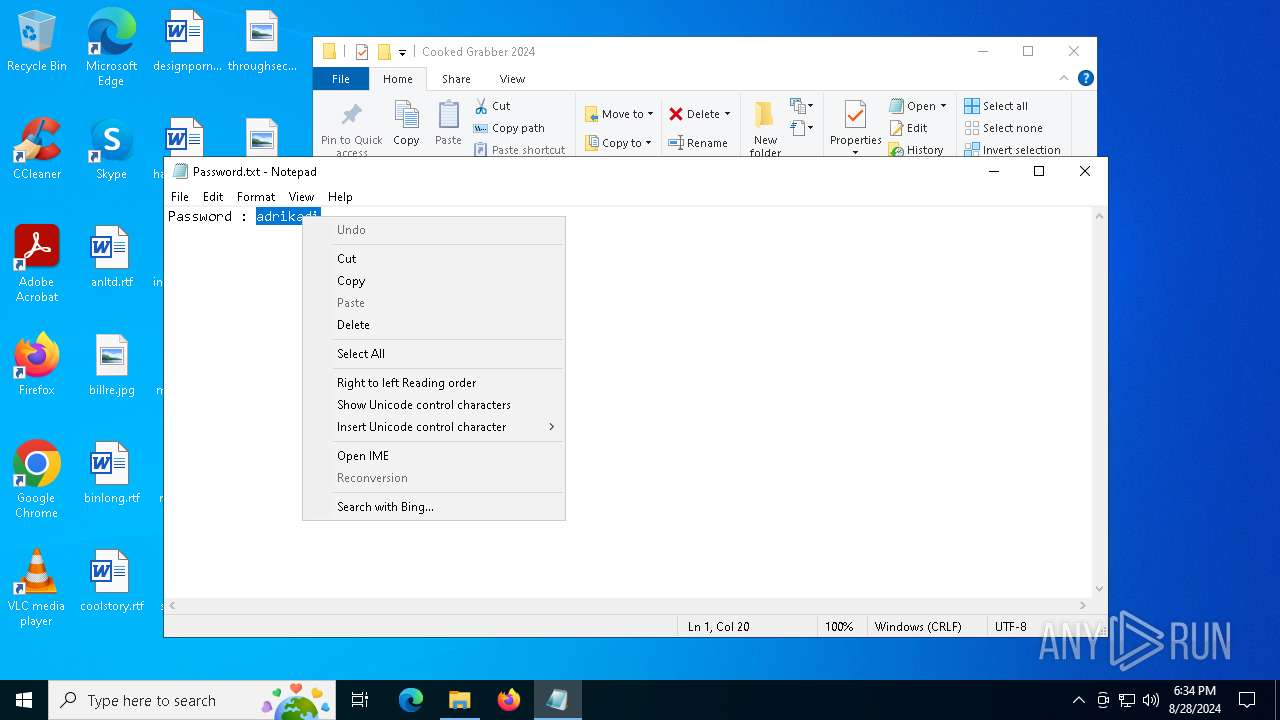
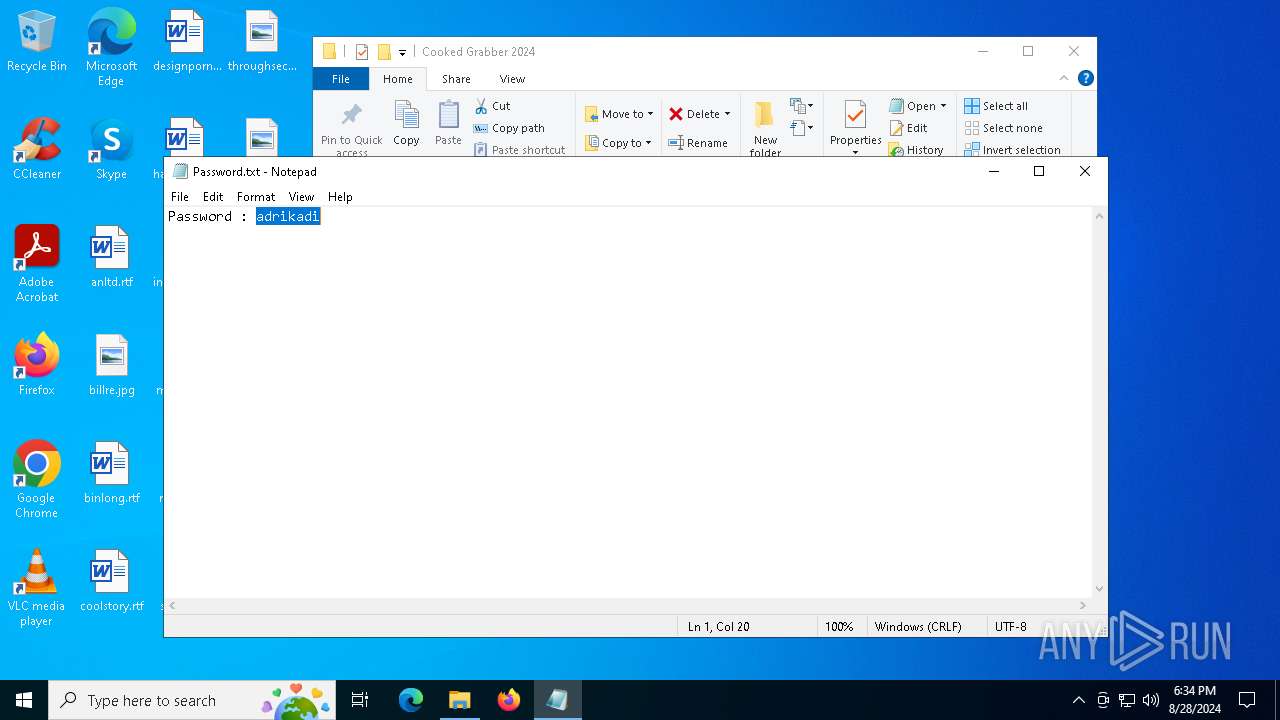
| 208 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\Password.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 252 | C:\WINDOWS\system32\cmd.exe /c "WMIC /Node:localhost /Namespace:\\root\SecurityCenter2 Path AntivirusProduct Get displayName" | C:\Windows\System32\cmd.exe | — | crack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 368 | tree /A /F | C:\Windows\System32\tree.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Tree Walk Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 568 | netsh wlan show profile | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1104 | "C:\Program Files\WinRAR\WinRAR.exe" cw -y -scuc "C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\Cooked Grabber 2024.exe" "C:\Users\admin\AppData\Local\Temp\Rar$CS4552.38810" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1104 | powershell Get-ItemPropertyValue -Path HKLM:SOFTWARE\Roblox\RobloxStudioBrowser\roblox.com -Name .ROBLOSECURITY | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | C:\WINDOWS\system32\cmd.exe /c "wmic path win32_VideoController get name" | C:\Windows\System32\cmd.exe | — | crack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1372 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
88 584
Read events
88 510
Write events
72
Delete events
2
Modification events
| (PID) Process: | (6744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Cooked_Grabber_2024.zip | |||
| (PID) Process: | (6744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6744) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
121
Suspicious files
20
Text files
72
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7156 | Cooked Grabber 2024.exe | C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\.editorconfig | text | |
MD5:E206366438DB16806C365B63C22047BF | SHA256:C94AEB56979F189CEF705FE8AB2C308B5C518CC2E11C8DF27E7C0A94C5BE2A87 | |||
| 2384 | WinRAR.exe | C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\Cooked Grabber 2024.exe | executable | |
MD5:C37DA2A7900972E5B895FA78D9C9160E | SHA256:B10020A93FDC703A964ED4C06AF3A85D4BE38865D07A646924F48A675192F5B8 | |||
| 7156 | Cooked Grabber 2024.exe | C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\CookedGrabber.py | text | |
MD5:A8350FF018BFFA5A5D2EF577DE669445 | SHA256:32F29635FC7D0A24394CE8A97574E356A43DB82F931EF02D202CBF2ED7DD228C | |||
| 2384 | WinRAR.exe | C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\Password.txt | text | |
MD5:74C1D4C44F8B390B493A4328332D079B | SHA256:D62B8A03A0EE992D25266B477ED200B15F7AF793319A5A914B9FBC4680E1BAB6 | |||
| 7156 | Cooked Grabber 2024.exe | C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\.github\ISSUE_TEMPLATE\feature_request.md | text | |
MD5:183208D06FB1A5F6D80DE9B22521B578 | SHA256:72A5F467B083C24507B1E848BBB958800F783FE1D313A8CA017F2A2673ACAD47 | |||
| 7156 | Cooked Grabber 2024.exe | C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\gbpast - Login.url | binary | |
MD5:4A4F5BE9370E206241BB73BFC2367F3C | SHA256:210F2EE620FE51ACDBE59BBA7BB4ACBDE397034818B09156F6F0874B016A5B18 | |||
| 7156 | Cooked Grabber 2024.exe | C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\Home - blankhack.url | binary | |
MD5:4A4418C24D2F2A9DEEE8046363BDD28F | SHA256:55DFE247F8FD6A8B0B66B3CB61FEEAE96D0B357338CD95771E89897AAC1A6839 | |||
| 7156 | Cooked Grabber 2024.exe | C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\LICENSE.md | text | |
MD5:9351D230613BDCD6F9089FE0F27DF004 | SHA256:C83D5230F3FF8324213F136A21AEA0D96693F6F6E71E00B59768E3F066D1D50B | |||
| 7156 | Cooked Grabber 2024.exe | C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\requirements.txt | text | |
MD5:DA7D26C156F0959E808F78440CCE62C6 | SHA256:B4B510F1347DF259B349A30979453B660A4CACEC3DF986F91398651F94E8DDE5 | |||
| 7156 | Cooked Grabber 2024.exe | C:\Users\admin\Desktop\Cooked_Grabber_2024\Cooked Grabber 2024\Home - cybergoons.url | binary | |
MD5:EF51820E228C5BBCF9AABE92E747782E | SHA256:59AC2D12EA4559253FA25F2D367F75B7689BB7B772965101903063F646AE9B4D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
32
DNS requests
18
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1076 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1076 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6312 | crack.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.119.249.228:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
— | — | 40.119.249.228:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
4132 | svchost.exe | 40.119.249.228:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
— | — | 20.7.1.246:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
8 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
8 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4132 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2256 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
2256 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6312 | crack.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
6312 | crack.exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |
6312 | crack.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |