| File name: | 0b2c34471fa6372be907560cad2a0b73.exe |
| Full analysis: | https://app.any.run/tasks/b46af9ff-92d5-48e9-92bf-3af5945e5cf9 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | December 06, 2024, 09:54:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 0B2C34471FA6372BE907560CAD2A0B73 |
| SHA1: | 25B4978FA938C9D8347FE132927EC992438B7C0A |
| SHA256: | C8A83C6C8F797E36EB7A5EDF0E5F85A8D985895C82932422B95BF628F4106DFB |
| SSDEEP: | 98304:lKPrXTlkZ0rHhMxlV6rw5fLxChNpwWyUb85jeoB/JiW5+TdKFh3h66tGWdrWm9Y+:BBqI9U+olPsm9B/YQSCv |
MALICIOUS
Create files in the Startup directory
- xcopy.exe (PID: 6892)
Connects to the CnC server
- xmrig.exe (PID: 7144)
MINER has been detected (SURICATA)
- xmrig.exe (PID: 7144)
XMRig has been detected
- xmrig.exe (PID: 7144)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- 0b2c34471fa6372be907560cad2a0b73.exe (PID: 6772)
Starts a Microsoft application from unusual location
- 0b2c34471fa6372be907560cad2a0b73.exe (PID: 6772)
Process drops legitimate windows executable
- 0b2c34471fa6372be907560cad2a0b73.exe (PID: 6772)
Executable content was dropped or overwritten
- 0b2c34471fa6372be907560cad2a0b73.exe (PID: 6772)
- xcopy.exe (PID: 6892)
- xcopy.exe (PID: 6916)
- xcopy.exe (PID: 7012)
Starts CMD.EXE for commands execution
- 0b2c34471fa6372be907560cad2a0b73.exe (PID: 6772)
- win.exe (PID: 7036)
Executing commands from a ".bat" file
- 0b2c34471fa6372be907560cad2a0b73.exe (PID: 6772)
- win.exe (PID: 7036)
Process copies executable file
- cmd.exe (PID: 6832)
The executable file from the user directory is run by the CMD process
- win.exe (PID: 7036)
- xmrig.exe (PID: 7144)
Connects to unusual port
- xmrig.exe (PID: 7144)
Potential Corporate Privacy Violation
- xmrig.exe (PID: 7144)
Crypto Currency Mining Activity Detected
- xmrig.exe (PID: 7144)
INFO
Reads the computer name
- 0b2c34471fa6372be907560cad2a0b73.exe (PID: 6772)
- win.exe (PID: 7036)
- xmrig.exe (PID: 7144)
Checks supported languages
- 0b2c34471fa6372be907560cad2a0b73.exe (PID: 6772)
- win.exe (PID: 7036)
- xmrig.exe (PID: 7144)
Create files in a temporary directory
- 0b2c34471fa6372be907560cad2a0b73.exe (PID: 6772)
- win.exe (PID: 7036)
Creates files or folders in the user directory
- xcopy.exe (PID: 6892)
- xcopy.exe (PID: 6916)
- xcopy.exe (PID: 7012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2062:07:25 12:18:00+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.2 |
| CodeSize: | 31744 |
| InitializedDataSize: | 17347584 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8200 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.19041.1 |
| ProductVersionNumber: | 11.0.19041.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 11.00.19041.1 (WinBuild.160101.0800) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | Internet Explorer |
| ProductVersion: | 11.00.19041.1 |
Total processes
136
Monitored processes
13
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6772 | "C:\Users\admin\AppData\Local\Temp\0b2c34471fa6372be907560cad2a0b73.exe" | C:\Users\admin\AppData\Local\Temp\0b2c34471fa6372be907560cad2a0b73.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6832 | cmd /c run.bat | C:\Windows\System32\cmd.exe | — | 0b2c34471fa6372be907560cad2a0b73.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6892 | xcopy /y "win.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup" | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6916 | xcopy /y "win.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows" | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
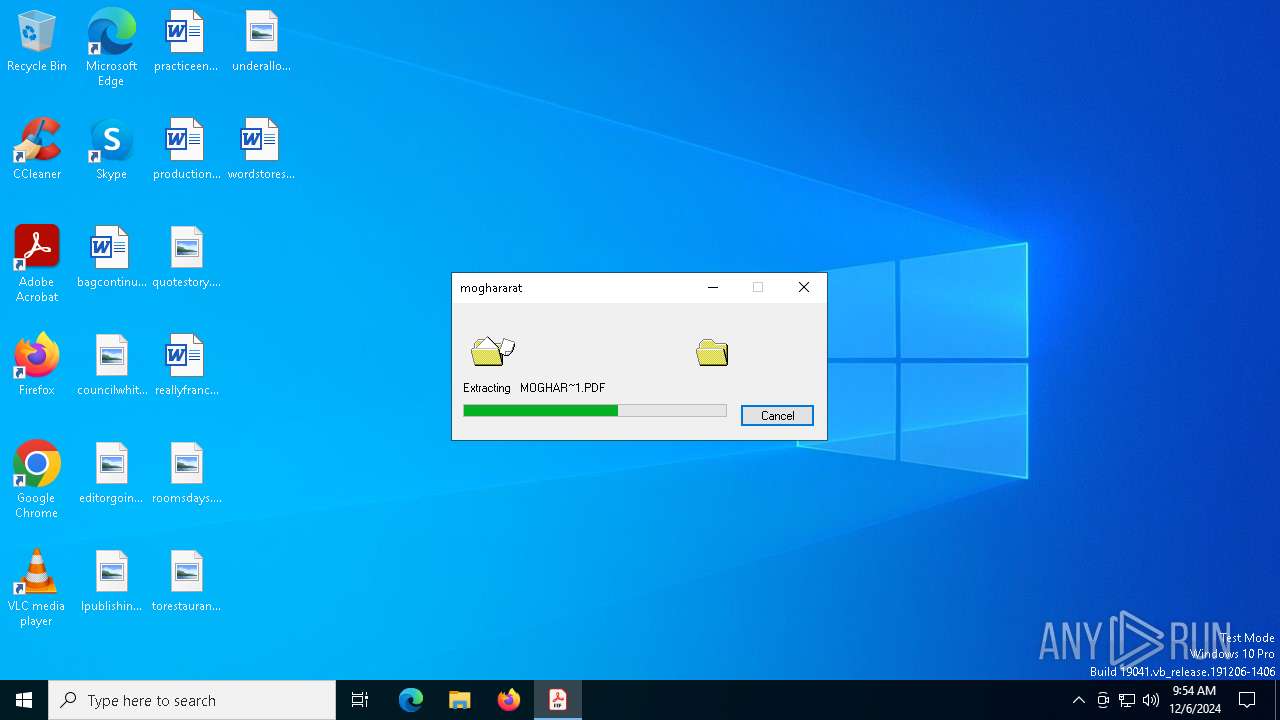
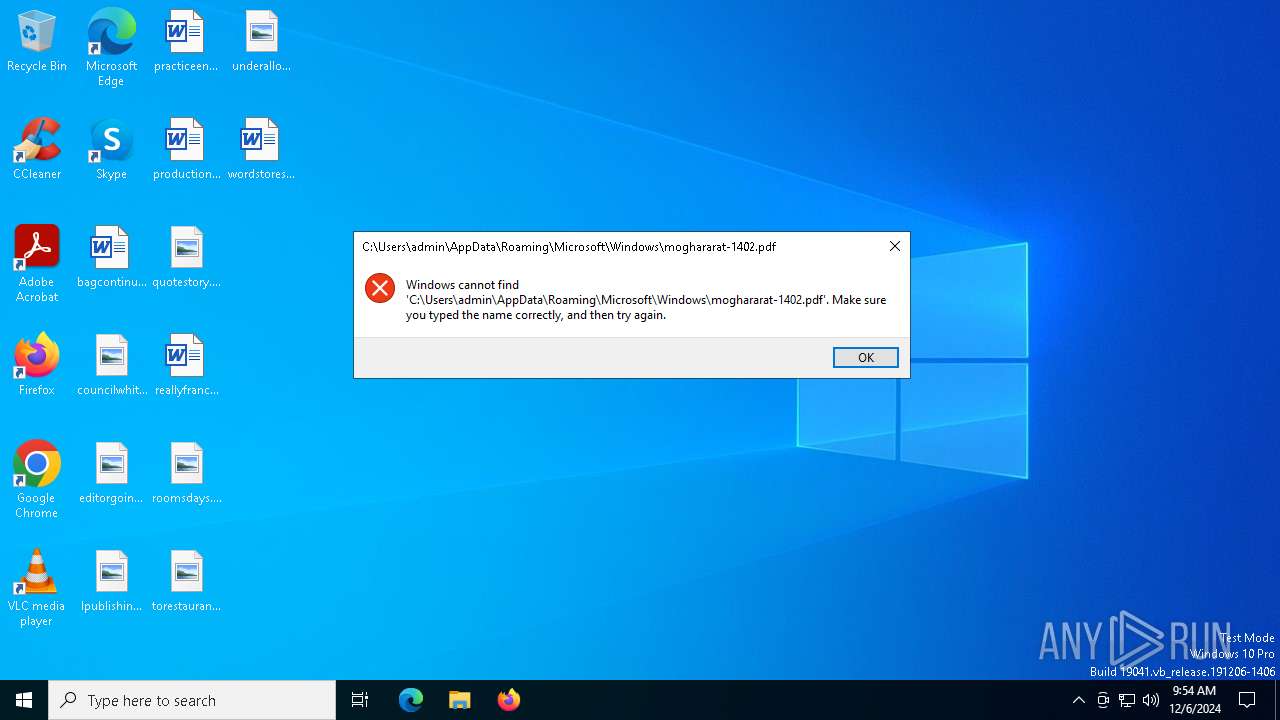
| 6940 | xcopy /y "moghararat-1402.pdf" "C:\Users\admin\AppData\Roaming\Microsoft\Windows" | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6964 | xcopy /y "config.json" "C:\Users\admin\AppData\Roaming\Microsoft\Windows" | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6988 | xcopy /y "WinRing0x64.sys" "C:\Users\admin\AppData\Roaming\Microsoft\Windows" | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7012 | xcopy /y "xmrig.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows" | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7036 | C:\Users\admin\AppData\Roaming\Microsoft\Windows\win.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\win.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
561
Read events
561
Write events
0
Delete events
0
Modification events
Executable files
6
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6772 | 0b2c34471fa6372be907560cad2a0b73.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\MOGHAR~1.PDF | — | |
MD5:— | SHA256:— | |||
| 6772 | 0b2c34471fa6372be907560cad2a0b73.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\run.bat | text | |
MD5:304199F5B3C8F124500A8E12380A6623 | SHA256:C72351011095048B6B9DCE1C72D329A2BBA75B45DC45E7410464801C85F85F22 | |||
| 7036 | win.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\win.bat | text | |
MD5:2A12B47E3AC83AD845965C07E5D31877 | SHA256:1B3AC1EA3F223BC8780B75659A832CC9E5C32D12F64FE2D489B3B5B821CC297A | |||
| 6772 | 0b2c34471fa6372be907560cad2a0b73.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\win.exe | executable | |
MD5:DB07FBB43F5F0CDD925EB00C254ADBE3 | SHA256:D630134DEA1D8BE1120648244F8E3AE2FDCA4721157528902BF5F421C2D26223 | |||
| 6892 | xcopy.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\win.exe | executable | |
MD5:DB07FBB43F5F0CDD925EB00C254ADBE3 | SHA256:D630134DEA1D8BE1120648244F8E3AE2FDCA4721157528902BF5F421C2D26223 | |||
| 6772 | 0b2c34471fa6372be907560cad2a0b73.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\CONFIG~1.JSO | binary | |
MD5:4D0A3C7B1D91B72C63EA5F8D4BC90FC1 | SHA256:D707A022E8C7873DA268FDB5F0E98699A557244B82860BAA93284D23089268B4 | |||
| 7012 | xcopy.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\xmrig.exe | executable | |
MD5:D6C24BDFF1CB0F2FCBE5AE63C42C7D92 | SHA256:E5CD22FFE8725FBABF32AE2BA993D5B791E65E2EF159AD32AD260505F2E22480 | |||
| 6772 | 0b2c34471fa6372be907560cad2a0b73.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\xmrig.exe | executable | |
MD5:D6C24BDFF1CB0F2FCBE5AE63C42C7D92 | SHA256:E5CD22FFE8725FBABF32AE2BA993D5B791E65E2EF159AD32AD260505F2E22480 | |||
| 6916 | xcopy.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\win.exe | executable | |
MD5:DB07FBB43F5F0CDD925EB00C254ADBE3 | SHA256:D630134DEA1D8BE1120648244F8E3AE2FDCA4721157528902BF5F421C2D26223 | |||
| 6772 | 0b2c34471fa6372be907560cad2a0b73.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\WINRIN~1.SYS | executable | |
MD5:0C0195C48B6B8582FA6F6373032118DA | SHA256:11BD2C9F9E2397C9A16E0990E4ED2CF0679498FE0FD418A3DFDAC60B5C160EE5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
30
DNS requests
15
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3724 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3724 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.152:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3508 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
zeph.kryptex.network |
| malicious |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7144 | xmrig.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
7144 | xmrig.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
1 ETPRO signatures available at the full report