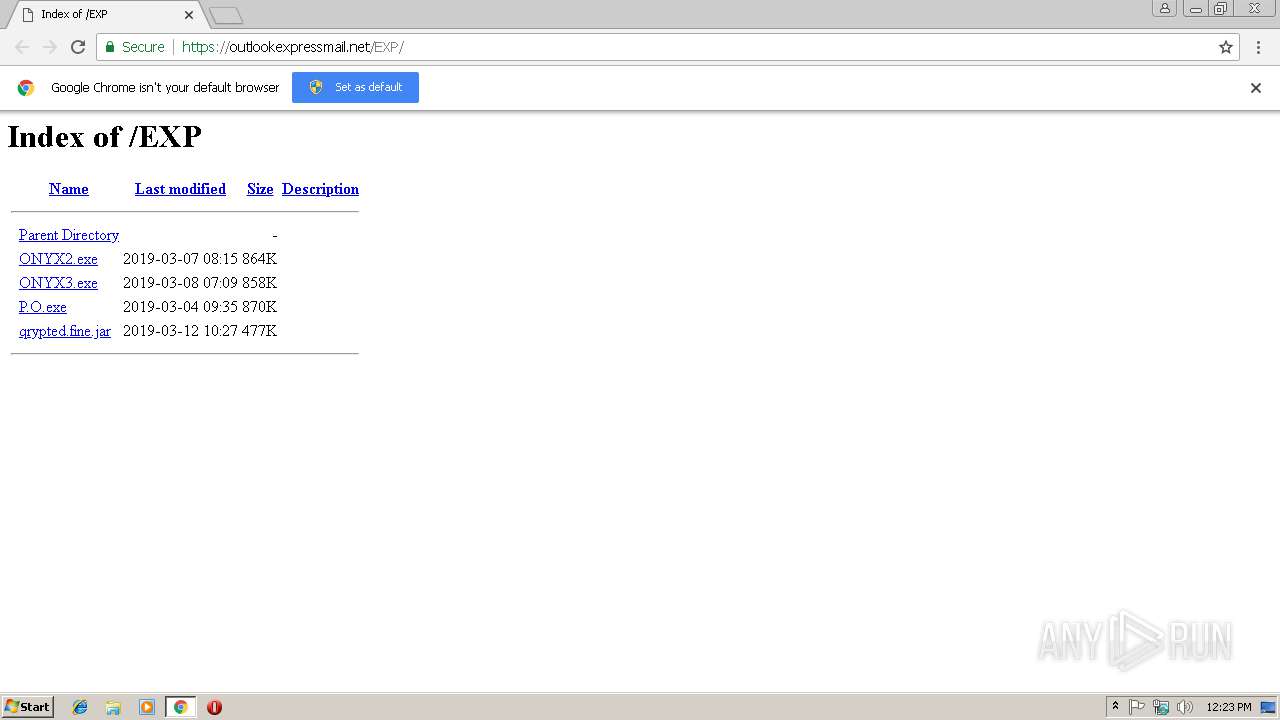
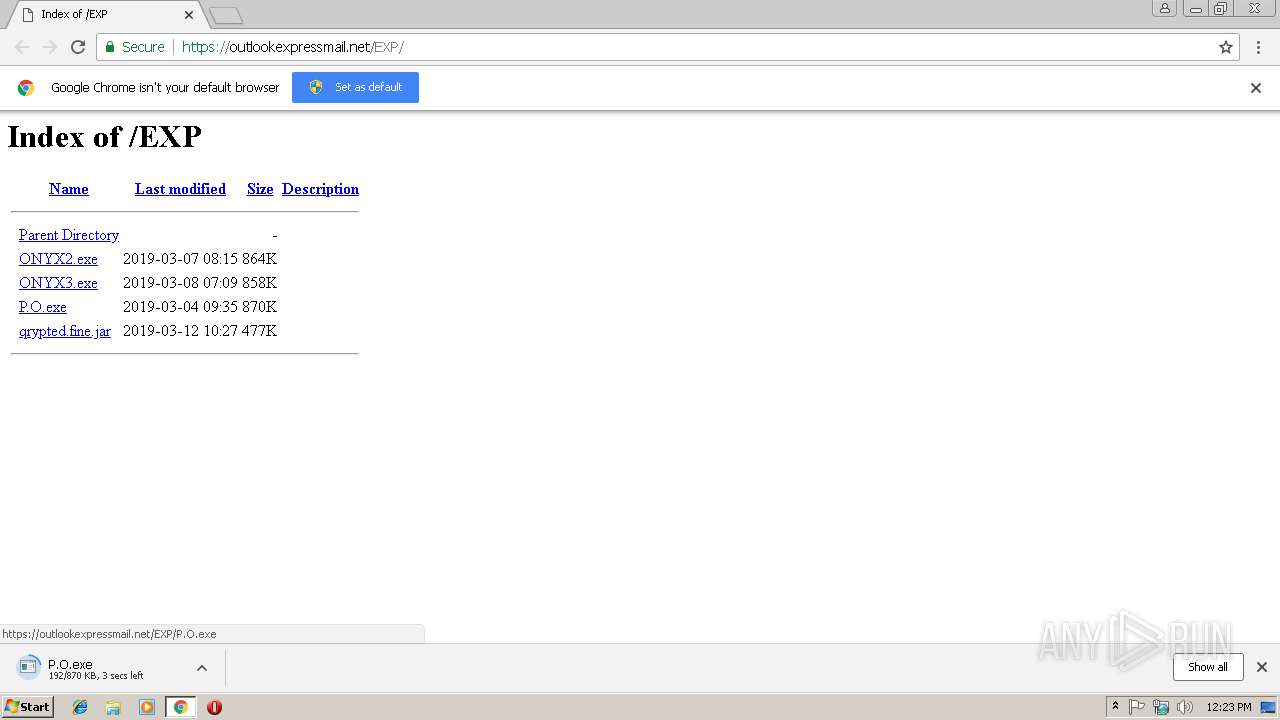
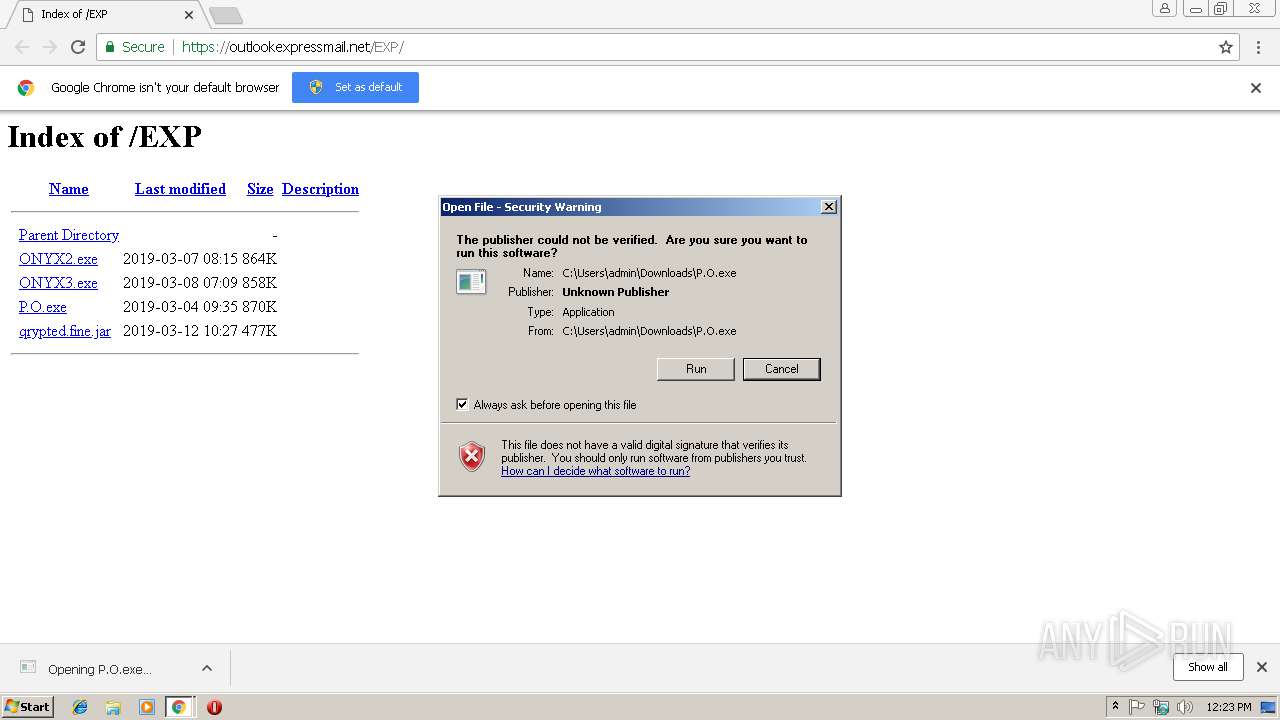
| URL: | https://outlookexpressmail.net/EXP/ |
| Full analysis: | https://app.any.run/tasks/837505f5-e890-4bfd-b49c-6d55b5f9eed4 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | March 14, 2019, 12:23:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 364315C322D30289AC586A4214F2F4A1 |
| SHA1: | 2530436E711563334B7C3E691AAFF813E27A205B |
| SHA256: | C86FA33C58C4D146157B83E186ED7255F251E4FFA049B7B720E9EE6E95AFEE7B |
| SSDEEP: | 3:N8ZRRVXA4JLoen:277 |
MALICIOUS
Actions looks like stealing of personal data
- vbc.exe (PID: 2872)
- vbc.exe (PID: 1920)
Connects to CnC server
- RegAsm.exe (PID: 3940)
Stealing of credential data
- vbc.exe (PID: 2872)
- vbc.exe (PID: 1920)
Application was dropped or rewritten from another process
- P.O.exe (PID: 3336)
- 655.exe (PID: 3376)
Changes the autorun value in the registry
- 655.exe (PID: 3376)
Detected Hawkeye Keylogger
- RegAsm.exe (PID: 3940)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3536)
- cmd.exe (PID: 2184)
Connects to SMTP port
- RegAsm.exe (PID: 3940)
Starts CMD.EXE for commands execution
- P.O.exe (PID: 3336)
Cleans NTFS data-stream (Zone Identifier)
- P.O.exe (PID: 3336)
Executes scripts
- RegAsm.exe (PID: 3940)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 2872)
INFO
Application launched itself
- chrome.exe (PID: 3536)
Reads Internet Cache Settings
- chrome.exe (PID: 3536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
13
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1920 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmp4588.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 2184 | "C:\Windows\System32\cmd.exe" /c copy "C:\Users\admin\Downloads\P.O.exe" "C:\Users\admin\AppData\Local\655.exe" | C:\Windows\System32\cmd.exe | P.O.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2228 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6fe300b0,0x6fe300c0,0x6fe300cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=936,7358489227563244169,12394431903020360121,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=8593F8F35E58DC355323114D3D5705DE --mojo-platform-channel-handle=996 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2744 | "C:\Windows\System32\cmd.exe" /c, "C:\Users\admin\AppData\Local\655.exe" | C:\Windows\System32\cmd.exe | — | P.O.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2872 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmp1BD7.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 3336 | "C:\Users\admin\Downloads\P.O.exe" | C:\Users\admin\Downloads\P.O.exe | — | chrome.exe | |||||||||||
User: admin Company: FINDER ECHIPAMENTE SRL Integrity Level: MEDIUM Description: Outlook Express Backup plugin Exit code: 0 Version: 15.10.19.1 Modules
| |||||||||||||||
| 3376 | "C:\Users\admin\AppData\Local\655.exe" | C:\Users\admin\AppData\Local\655.exe | cmd.exe | ||||||||||||
User: admin Company: FINDER ECHIPAMENTE SRL Integrity Level: MEDIUM Description: Outlook Express Backup plugin Exit code: 0 Version: 15.10.19.1 Modules
| |||||||||||||||
| 3384 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=936,7358489227563244169,12394431903020360121,131072 --enable-features=PasswordImport --service-pipe-token=D0B8B9D179219C3E61B73DB195BB9AA8 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=D0B8B9D179219C3E61B73DB195BB9AA8 --renderer-client-id=4 --mojo-platform-channel-handle=1896 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3540 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
595
Read events
532
Write events
60
Delete events
3
Modification events
| (PID) Process: | (3468) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3536-13197039798561875 |
Value: 259 | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3536-13197039798561875 |
Value: 259 | |||
| (PID) Process: | (3536) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
3
Suspicious files
27
Text files
65
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\f5be564f-133c-4618-9f7f-cee17226846f.tmp | — | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\72ce728c-b5c4-491e-ae88-d1a07d3371be.tmp | — | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF1addde.TMP | text | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3536 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2228 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:B59113C2DCD2D346F31A64F231162ADA | SHA256:1D97C69AEA85D3B06787458EA47576B192CE5C5DB9940E5EAA514FF977CE2DC2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
8
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3940 | RegAsm.exe | GET | 200 | 66.171.248.178:80 | http://bot.whatismyipaddress.com/ | US | text | 15 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3536 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3536 | chrome.exe | 69.64.54.205:443 | outlookexpressmail.net | server4you Inc. | US | unknown |
3536 | chrome.exe | 216.58.208.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3536 | chrome.exe | 216.58.210.14:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
3536 | chrome.exe | 172.217.18.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
3940 | RegAsm.exe | 66.171.248.178:80 | bot.whatismyipaddress.com | Alchemy Communications, Inc. | US | malicious |
3940 | RegAsm.exe | 208.91.198.143:587 | smtp.bestbirdss.com | PDR | US | shared |
3536 | chrome.exe | 216.58.207.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.gstatic.com |
| whitelisted |
outlookexpressmail.net |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
sb-ssl.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
bot.whatismyipaddress.com |
| shared |
smtp.bestbirdss.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3940 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Spy.HawkEye IP Check |
3940 | RegAsm.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3940 | RegAsm.exe | A Network Trojan was detected | ET TROJAN HawkEye Keylogger Report SMTP |
3940 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] HawkEye Reborn8 Stealing Data via SMTP |
3 ETPRO signatures available at the full report